| File name: | zip |
| Full analysis: | https://app.any.run/tasks/f4fec5c6-5fc8-4483-8c8d-0099a6b9e55e |
| Verdict: | Malicious activity |
| Analysis date: | July 17, 2019, 12:09:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 6BC05B78FA336B8D30FB6477E52E1A53 |
| SHA1: | D8E96A6E5DE70901BA6B43F8B2E4601A03D7DF92 |
| SHA256: | 41AFFA2CB39B53901567A3548968C2DCCC946959749D6F68BD273F9BA6E1CB8E |
| SSDEEP: | 384:gl4gov7ToCbfxnf91tKSKyVXlQm34lxfWNrbapZT:Q4pjnb5f913tV2WVbsT |
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3000)
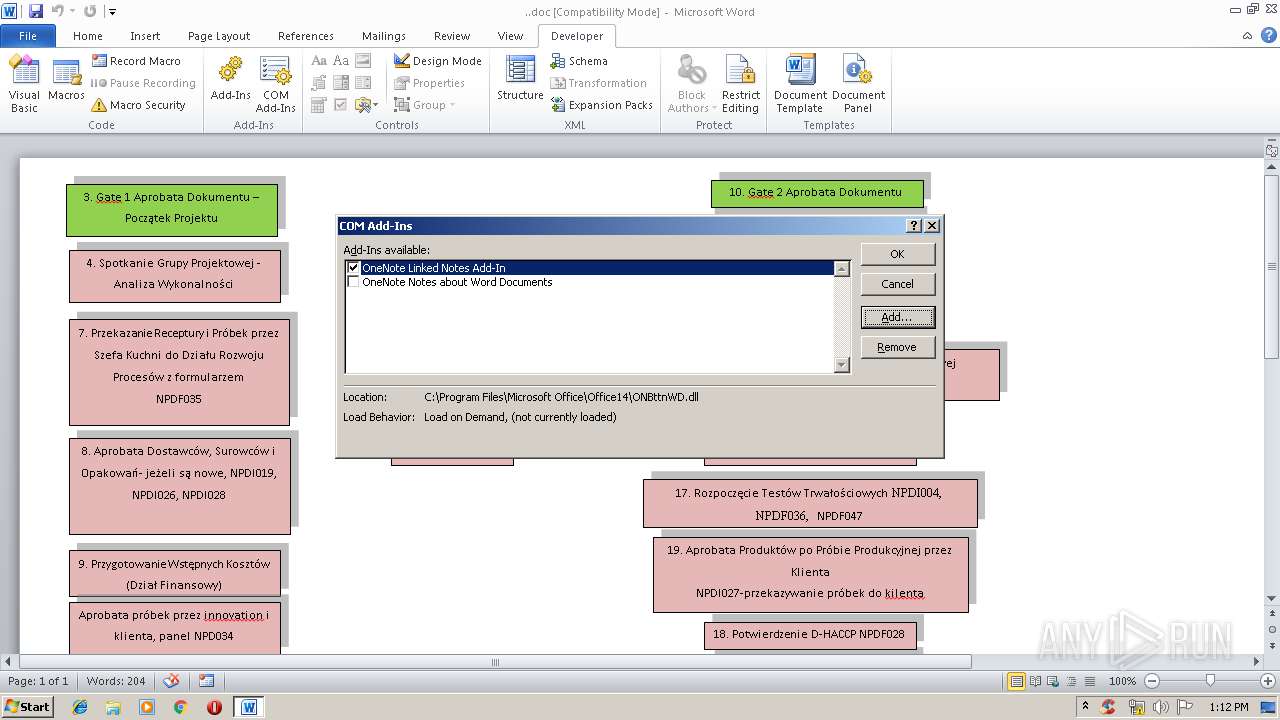
Loads the Task Scheduler COM API
- CCleaner.exe (PID: 836)
- CCleaner.exe (PID: 1936)
- CCleaner.exe (PID: 2704)
- CCleaner.dll (PID: 2948)
Changes the autorun value in the registry
- CCleaner.exe (PID: 1936)
Actions looks like stealing of personal data
- CCleaner.exe (PID: 952)
- CCleaner.exe (PID: 1936)
- CCleaner.exe (PID: 2796)
Application was dropped or rewritten from another process
- CCleaner.exe (PID: 1936)
- CCleaner.exe (PID: 836)
- CCleaner.exe (PID: 2796)
- CCleaner.exe (PID: 2704)
- CCleaner.dll (PID: 2948)
- CCleaner.exe (PID: 952)
Loads dropped or rewritten executable
- WINWORD.EXE (PID: 3000)
- explorer.exe (PID: 284)
- svchost.exe (PID: 852)
SUSPICIOUS
Reads Internet Cache Settings
- explorer.exe (PID: 284)
Creates files in the user directory
- explorer.exe (PID: 284)
- CCleaner.exe (PID: 2796)
- CCleaner.exe (PID: 952)
Executed via Task Scheduler
- CCleaner.exe (PID: 2796)
- CCleaner.exe (PID: 952)
Reads the cookies of Mozilla Firefox
- CCleaner.exe (PID: 2796)
Application launched itself
- CCleaner.exe (PID: 2796)
Reads the cookies of Google Chrome
- CCleaner.exe (PID: 2796)
Reads internet explorer settings
- CCleaner.exe (PID: 2796)
- CCleaner.exe (PID: 952)
- CCleaner.exe (PID: 1936)
Low-level read access rights to disk partition
- CCleaner.exe (PID: 2796)
- CCleaner.exe (PID: 952)
Executed via COM
- DllHost.exe (PID: 2300)
Executable content was dropped or overwritten
- DllHost.exe (PID: 2300)
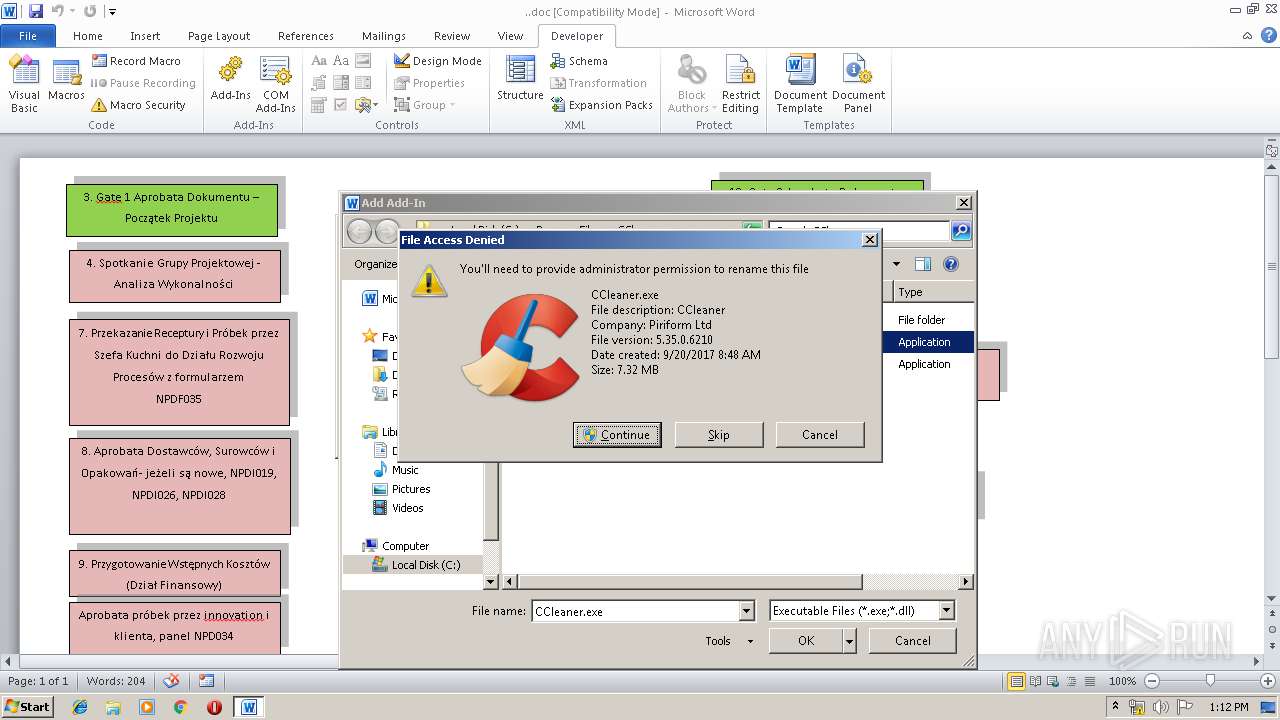
Starts application with an unusual extension
- WINWORD.EXE (PID: 3000)
INFO
Manual execution by user
- WINWORD.EXE (PID: 3000)
Starts Microsoft Office Application
- explorer.exe (PID: 284)
Creates files in the user directory
- WINWORD.EXE (PID: 3000)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3000)
Reads settings of System Certificates
- CCleaner.exe (PID: 2796)
- CCleaner.exe (PID: 952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:02:12 09:20:01 |
| ZipCRC: | 0xab0c1c15 |
| ZipCompressedSize: | 17606 |
| ZipUncompressedSize: | 76800 |
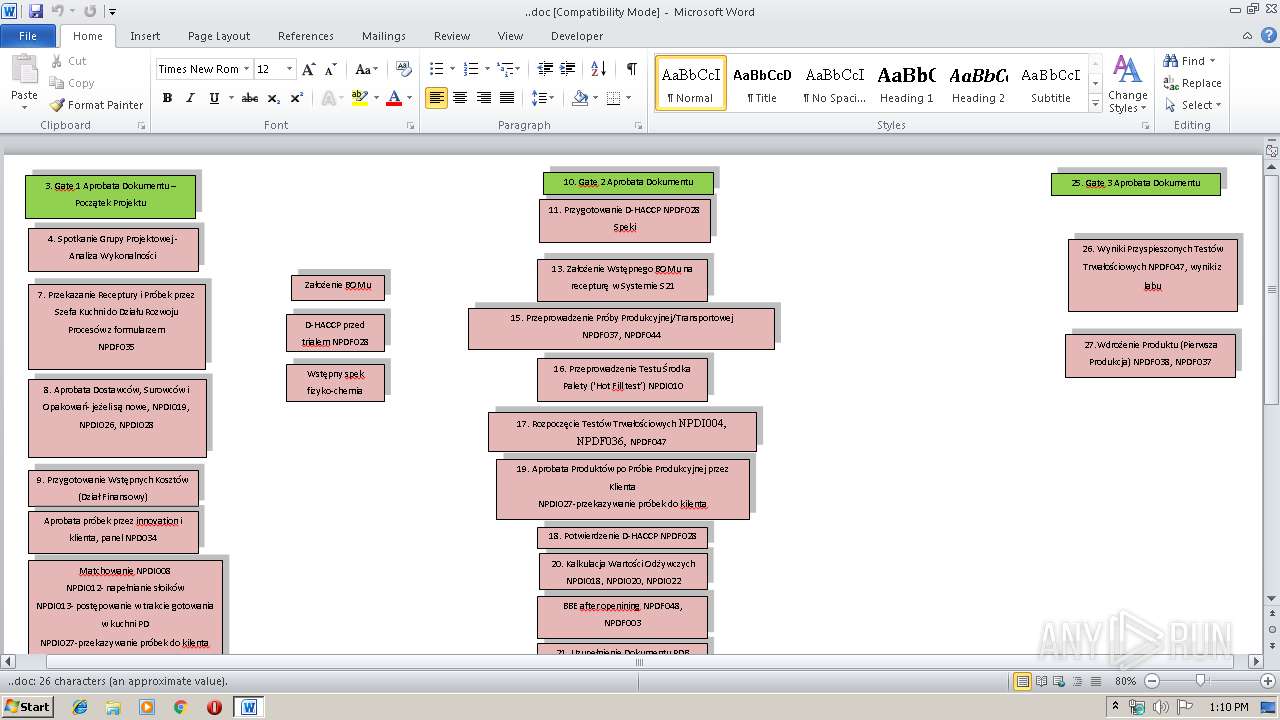
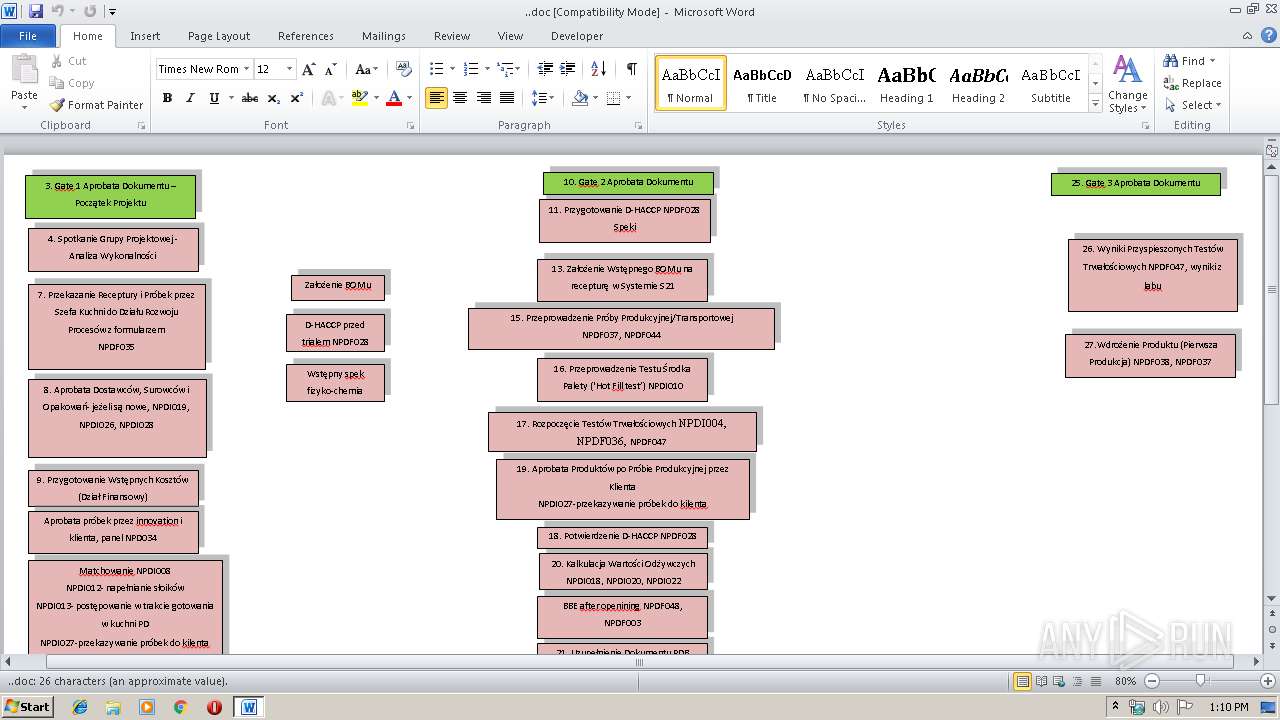
| ZipFileName: | ..doc |
Total processes
52
Monitored processes
11
Malicious processes
7
Suspicious processes
0
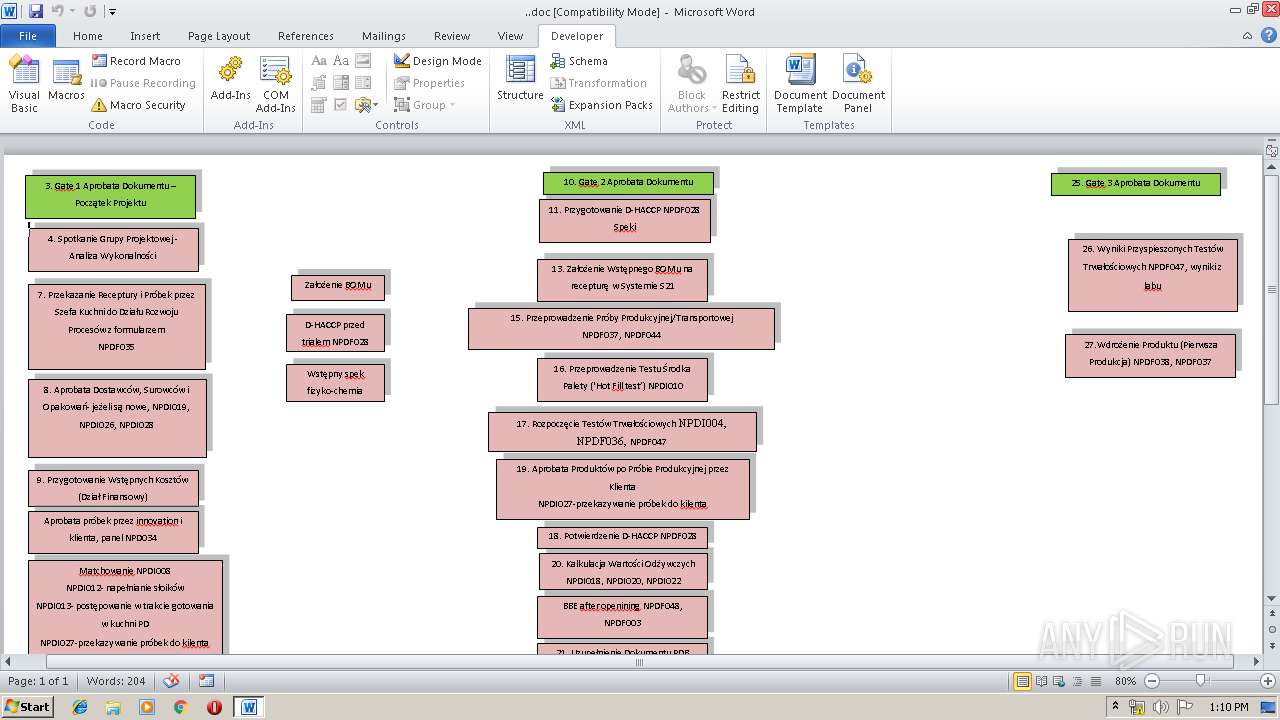
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
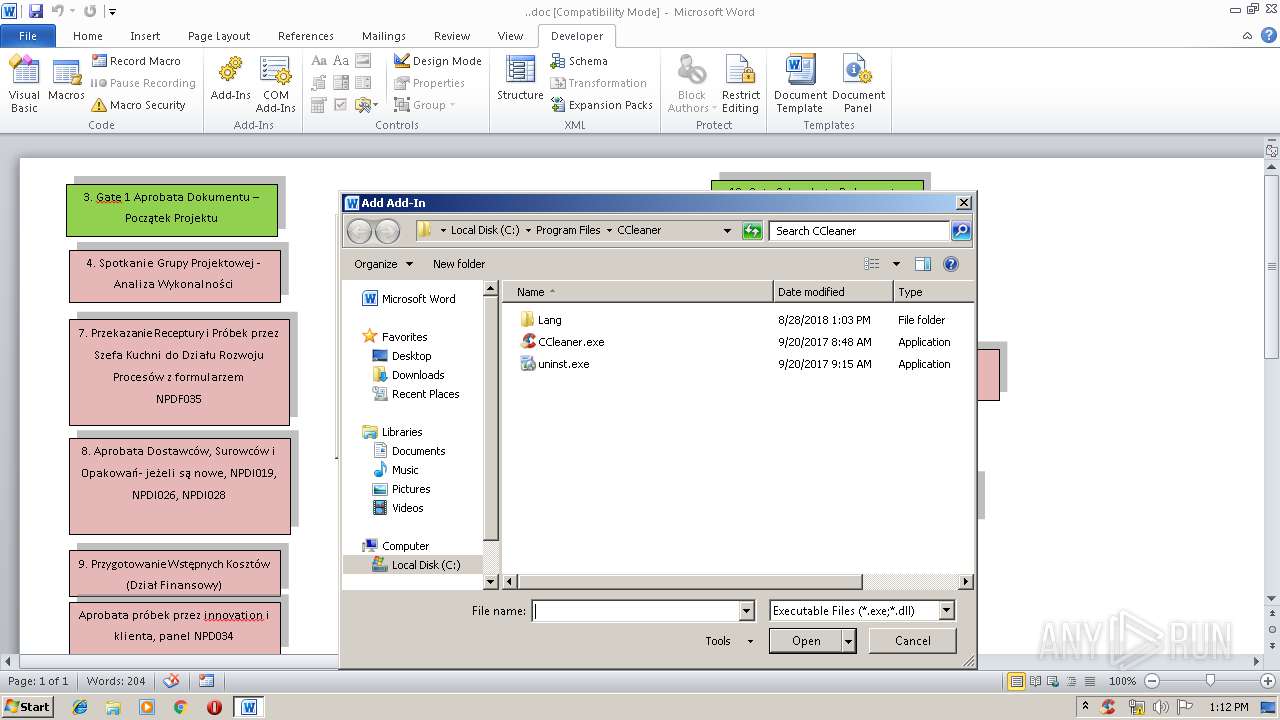
| 836 | "C:\Program Files\CCleaner\CCleaner.exe" /RegServer | C:\Program Files\CCleaner\CCleaner.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Piriform Ltd Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 5, 35, 0, 6210 Modules
| |||||||||||||||
| 852 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 952 | "C:\Program Files\CCleaner\CCleaner.exe" /RegServer /uac | C:\Program Files\CCleaner\CCleaner.exe | taskeng.exe | ||||||||||||
User: admin Company: Piriform Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 5, 35, 0, 6210 Modules
| |||||||||||||||
| 1936 | "C:\Program Files\CCleaner\CCleaner.exe" /monitor | C:\Program Files\CCleaner\CCleaner.exe | CCleaner.exe | ||||||||||||
User: admin Company: Piriform Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 5, 35, 0, 6210 Modules
| |||||||||||||||
| 2300 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\system32\DllHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2704 | "C:\Program Files\CCleaner\CCleaner.exe" /RegServer | C:\Program Files\CCleaner\CCleaner.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Piriform Ltd Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 5, 35, 0, 6210 Modules
| |||||||||||||||
| 2796 | "C:\Program Files\CCleaner\CCleaner.exe" /RegServer /uac | C:\Program Files\CCleaner\CCleaner.exe | taskeng.exe | ||||||||||||
User: admin Company: Piriform Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 5, 35, 0, 6210 Modules
| |||||||||||||||
| 2896 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\zip.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2948 | "C:\Program Files\CCleaner\CCleaner.dll" /RegServer | C:\Program Files\CCleaner\CCleaner.dll | — | WINWORD.EXE | |||||||||||
User: admin Company: Piriform Ltd Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 5, 35, 0, 6210 Modules
| |||||||||||||||
Total events
5 213
Read events
3 970
Write events
1 226
Delete events
17
Modification events
| (PID) Process: | (2896) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2896) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2896) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2896) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\zip.zip | |||
| (PID) Process: | (2896) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2896) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2896) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2896) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
1
Suspicious files
10
Text files
2
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2896 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2896.39228\..doc | — | |
MD5:— | SHA256:— | |||
| 3000 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR3F17.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2796 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 2796 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\webappsstore.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 2796 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\16UGJ3SXPAS4055YCEKM.temp | — | |
MD5:— | SHA256:— | |||
| 2796 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\KKRFJ1YNIB12K06I3ZCE.temp | — | |
MD5:— | SHA256:— | |||
| 2796 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\G9SAPP5VO288Z1IMVIR9.temp | — | |
MD5:— | SHA256:— | |||
| 952 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\U9FQOV3PSK32FQMB28IN.temp | — | |
MD5:— | SHA256:— | |||
| 952 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\6KWUO91270HCWSTL43ZI.temp | — | |
MD5:— | SHA256:— | |||
| 952 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\XZSLYZWVL7U355JP62VE.temp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
12
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2796 | CCleaner.exe | GET | 301 | 151.101.0.64:80 | http://www.piriform.com/auto?a=0&p=cc&v=5.35.6210&l=1033&lk=&mk=IJR6-W5SV-5KYR-QBZD-6BY4-RN5Z-WAV9-RVK2-VJCA&o=6.1W3&au=1&mx=97B7721C4994E2556FF6A439510F665DB45337A341A47E15F4997584423BF714&gu=00000000-0000-4000-8000-d6f7f2be5127 | US | — | — | whitelisted |
952 | CCleaner.exe | GET | 301 | 151.101.0.64:80 | http://www.piriform.com/auto?a=0&p=cc&v=5.35.6210&l=1033&lk=&mk=IJR6-W5SV-5KYR-QBZD-6BY4-RN5Z-WAV9-RVK2-VJCA&o=6.1W3&au=1&mx=97B7721C4994E2556FF6A439510F665DB45337A341A47E15F4997584423BF714&gu=00000000-0000-4000-8000-d6f7f2be5127 | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 151.101.0.64:80 | www.piriform.com | Fastly | US | whitelisted |
— | — | 151.101.0.64:443 | www.piriform.com | Fastly | US | whitelisted |
2796 | CCleaner.exe | 151.101.0.64:443 | www.piriform.com | Fastly | US | whitelisted |
2796 | CCleaner.exe | 151.101.2.202:443 | www.ccleaner.com | Fastly | US | suspicious |
952 | CCleaner.exe | 151.101.0.64:443 | www.piriform.com | Fastly | US | whitelisted |
952 | CCleaner.exe | 151.101.0.64:80 | www.piriform.com | Fastly | US | whitelisted |
952 | CCleaner.exe | 151.101.2.202:443 | www.ccleaner.com | Fastly | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.piriform.com |
| whitelisted |
www.ccleaner.com |
| whitelisted |