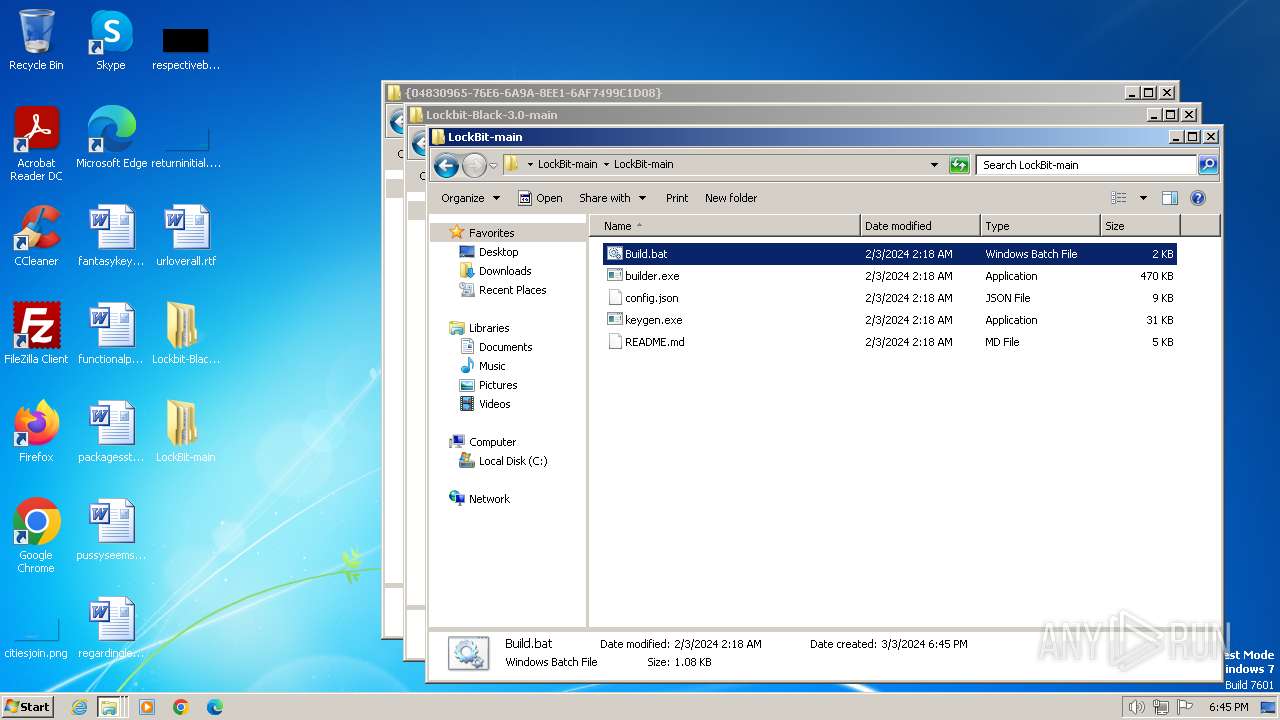
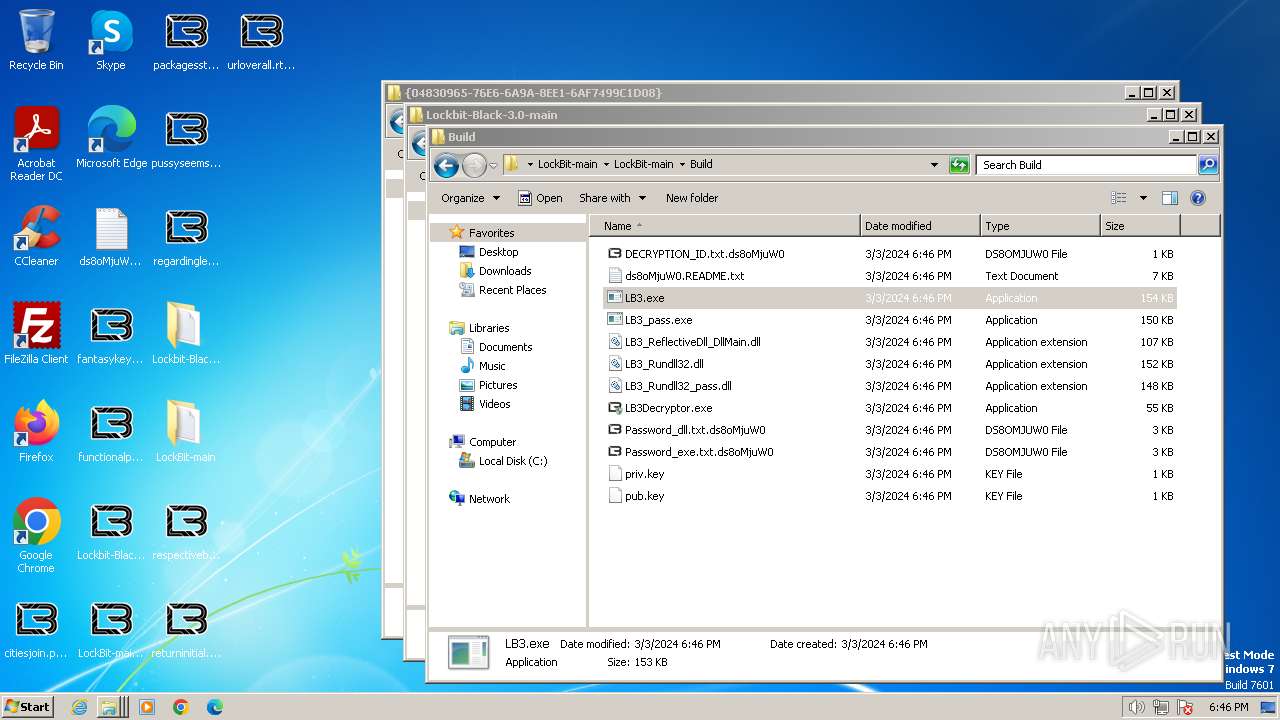
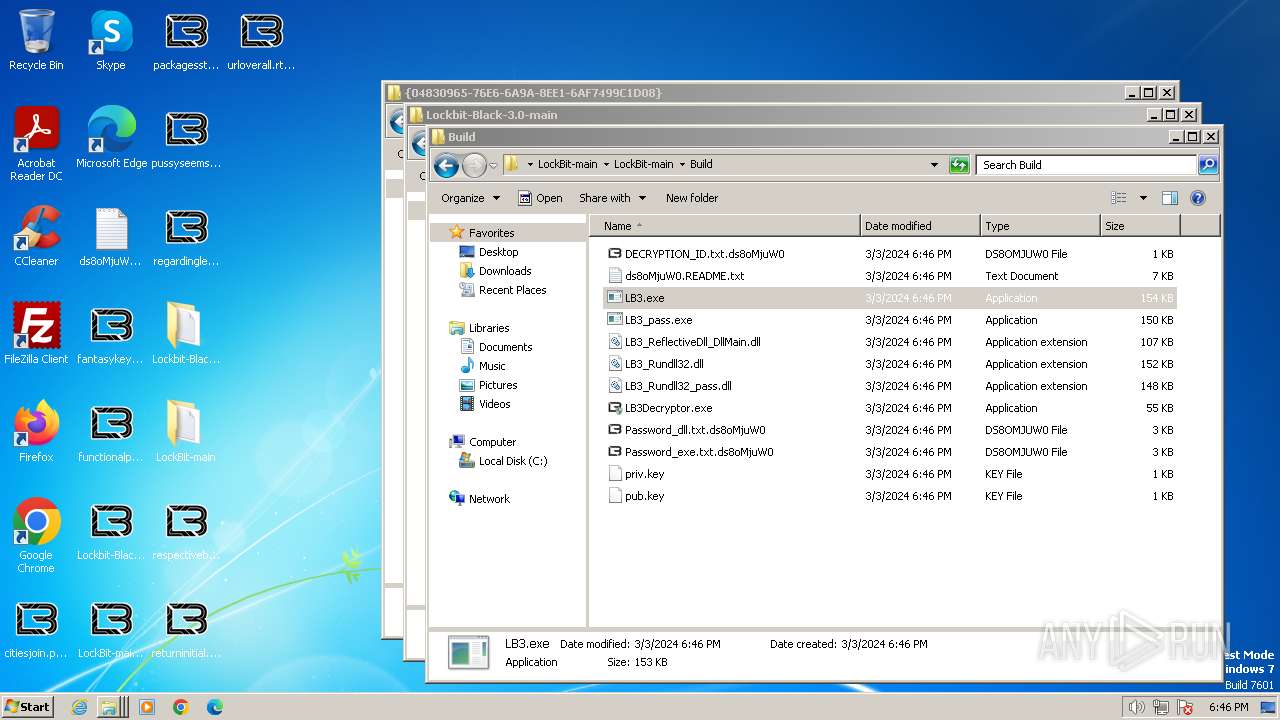
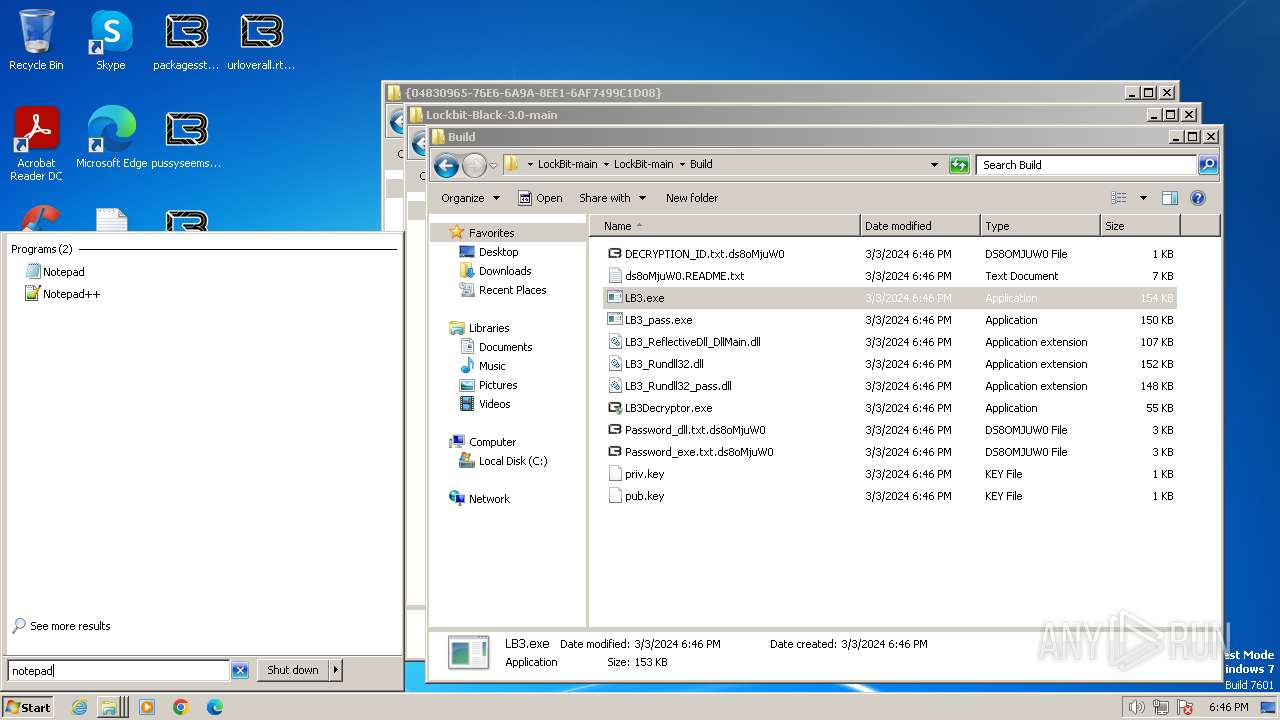
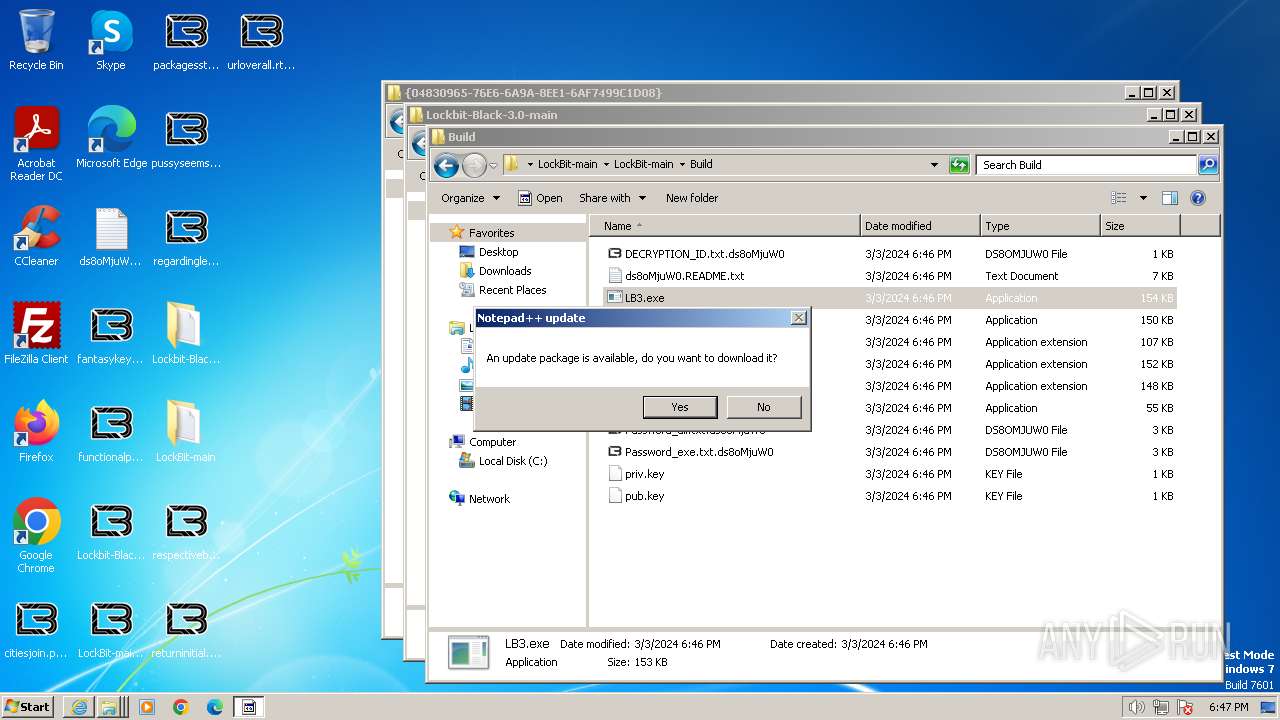
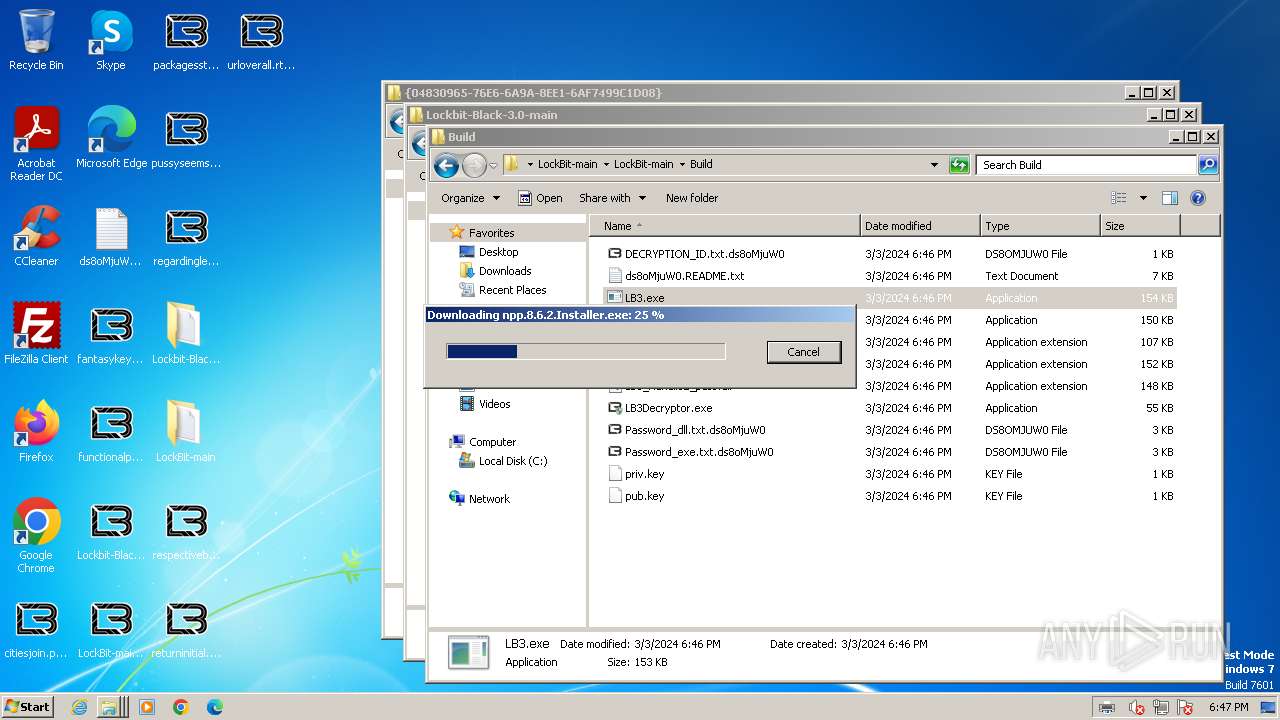
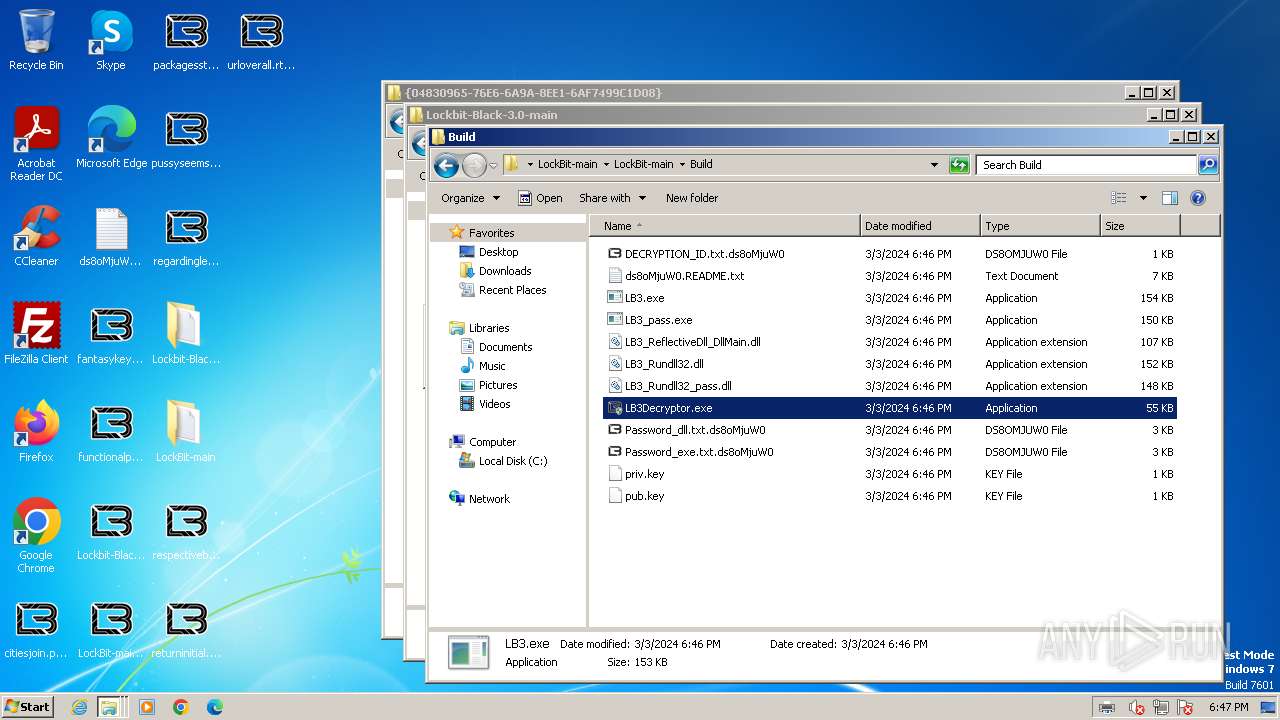
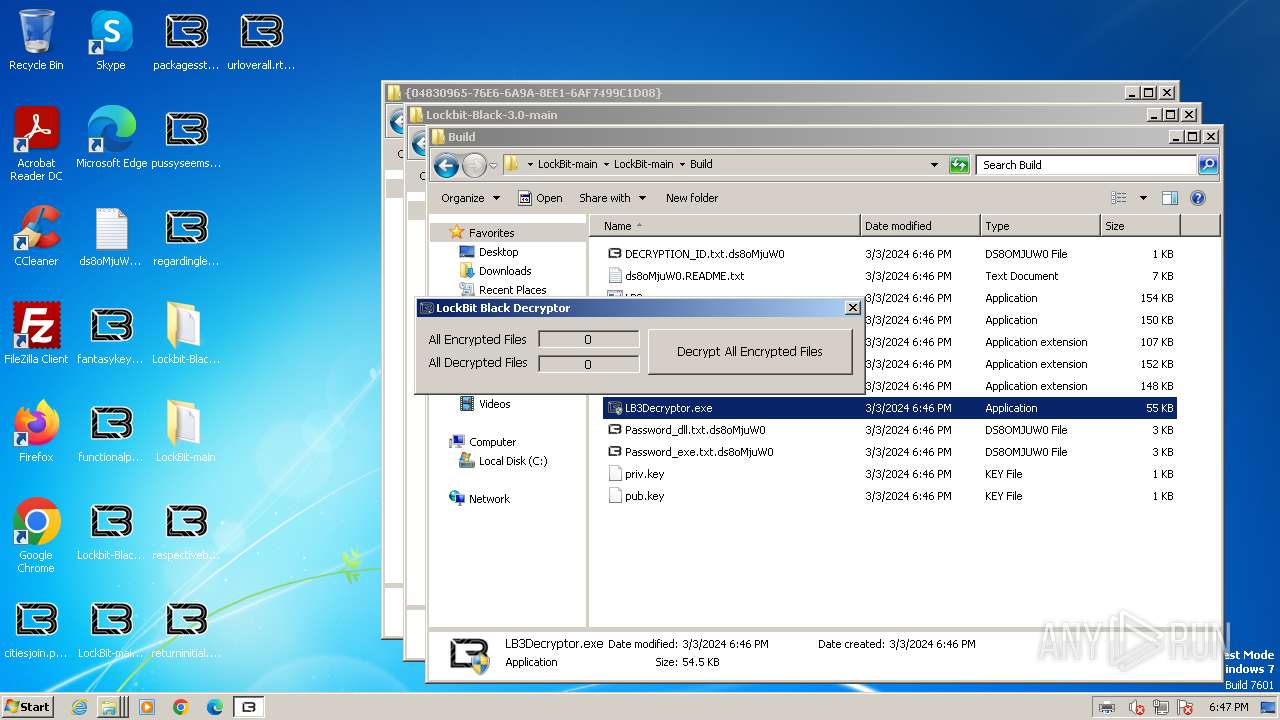
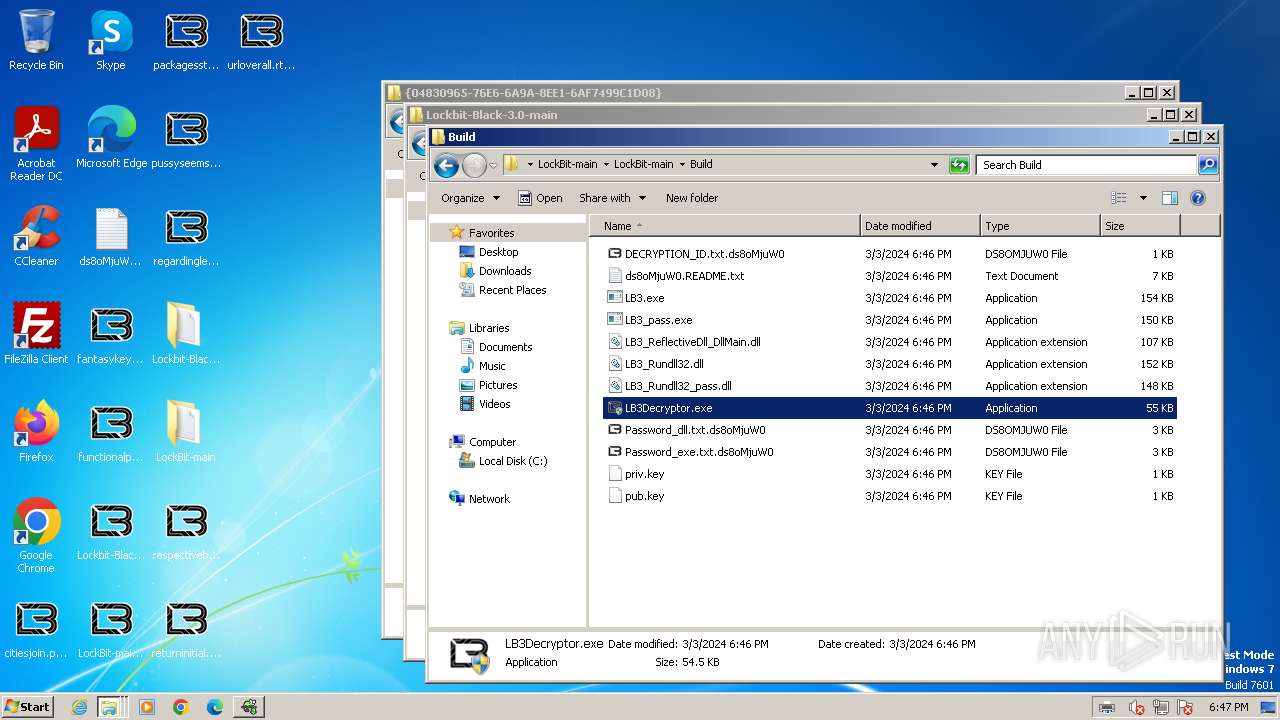
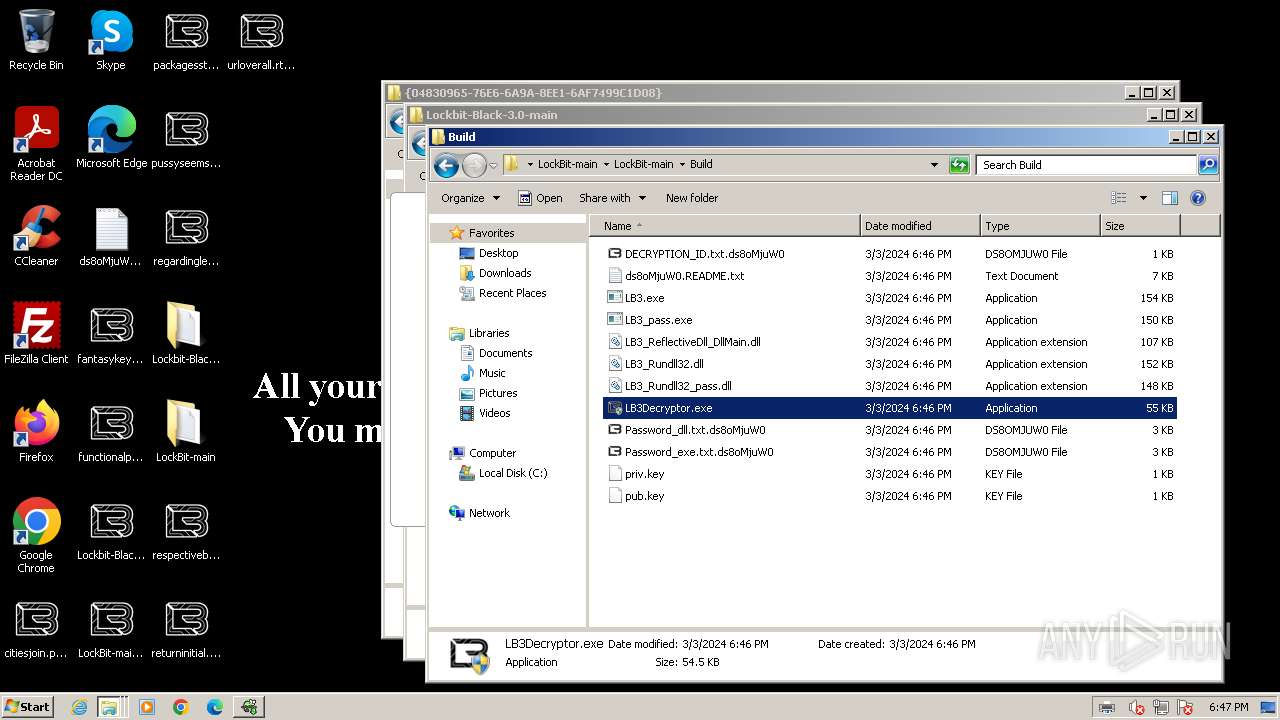
| File name: | Lockbit 3.0.rar |
| Full analysis: | https://app.any.run/tasks/8209f733-27d7-444c-add5-e9a18a96c9a0 |
| Verdict: | Malicious activity |
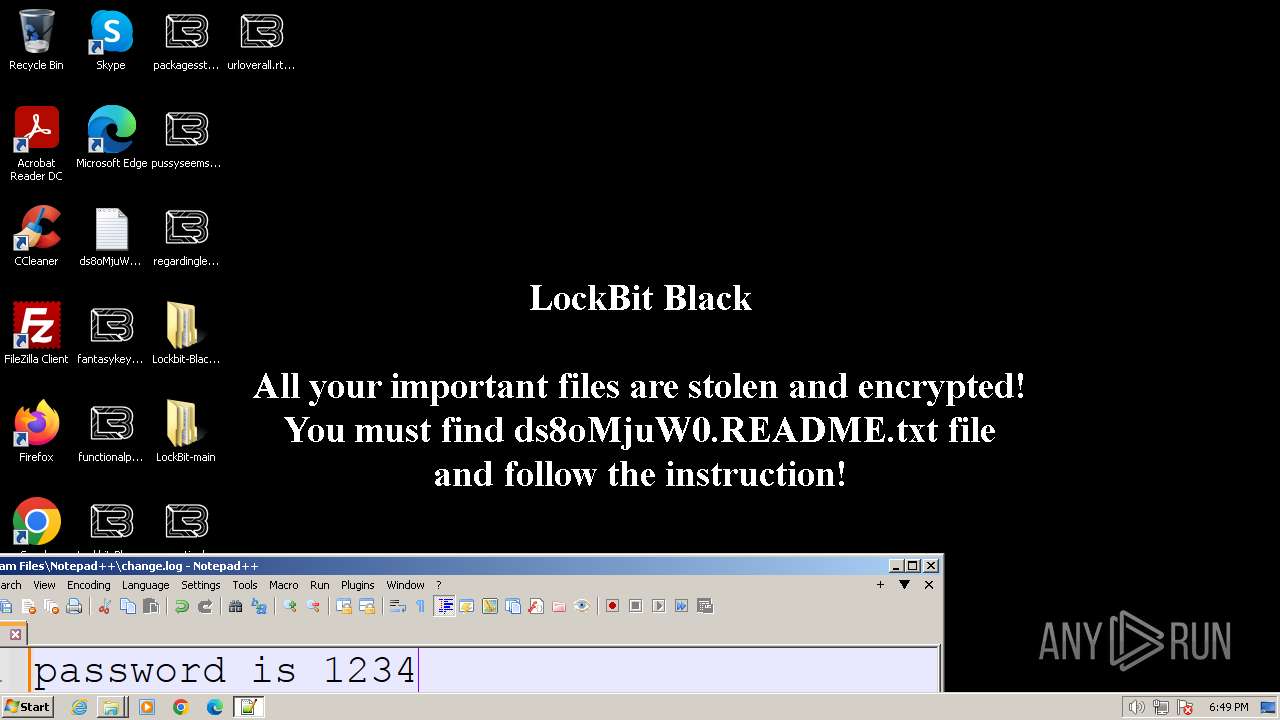
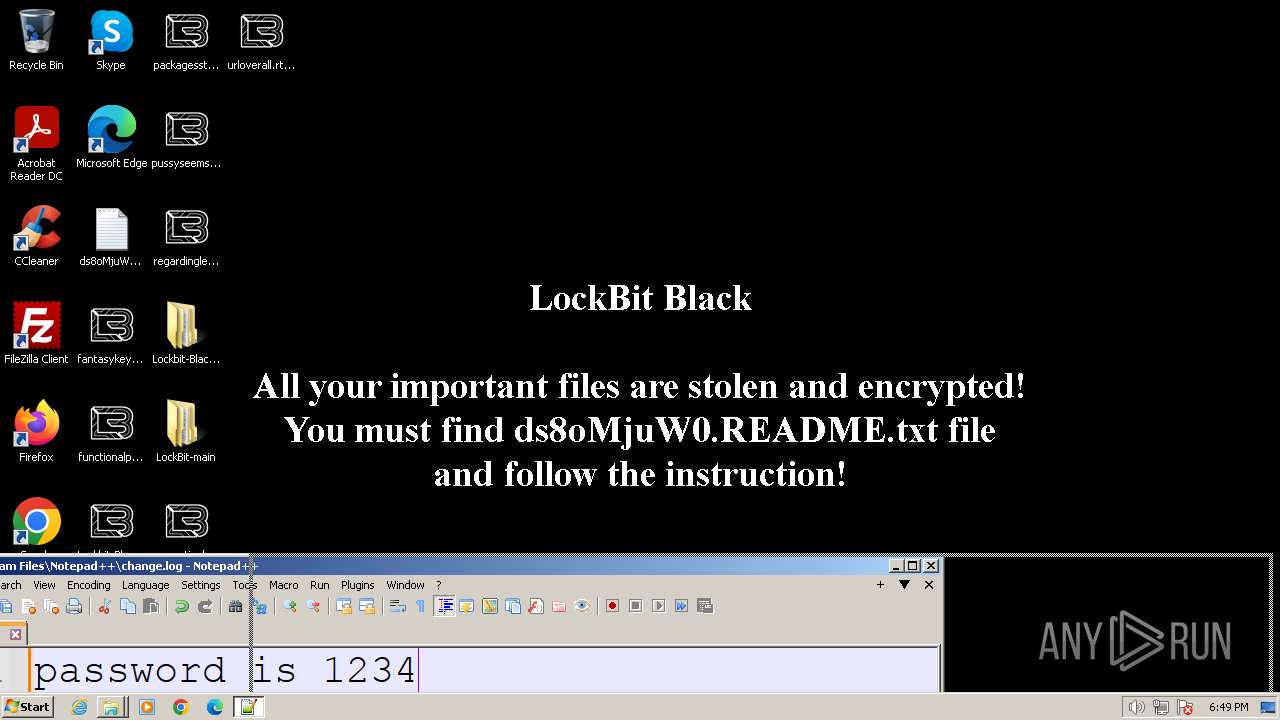
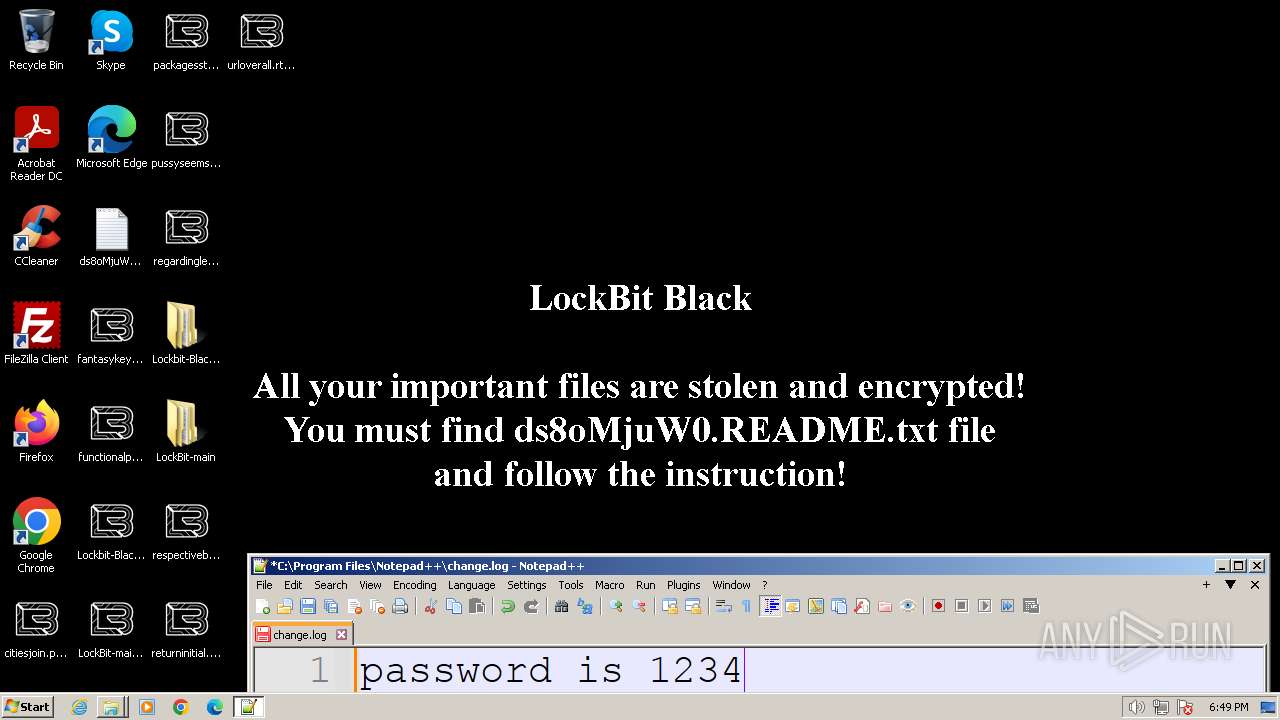
| Threats: | LockBit, a ransomware variant, encrypts data on infected machines, demanding a ransom payment for decryption. Used in targeted attacks, It's a significant risk to organizations. |
| Analysis date: | March 03, 2024, 18:44:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | FEB587492965E27725F12CEBFE9C0F63 |
| SHA1: | 043FA82CD179A0C0D33D958534D0AC4A266AF4FE |
| SHA256: | 41A698EB7C58022975DDB16D80E444234A71B1A3DFB3E017AD80A6AC8C541063 |
| SSDEEP: | 98304:SHa1WDt8gGmfDa1fkRm6YF92H0TJ6FvJ9OIlpYUIdL0hi3UIYEJWxJXk783f3xKy:OUbnW27w50JU |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3672)
- builder.exe (PID: 296)
- builder.exe (PID: 3036)
- builder.exe (PID: 1584)
- builder.exe (PID: 2348)
- builder.exe (PID: 2588)
- builder.exe (PID: 128)
- LB3.exe (PID: 1264)
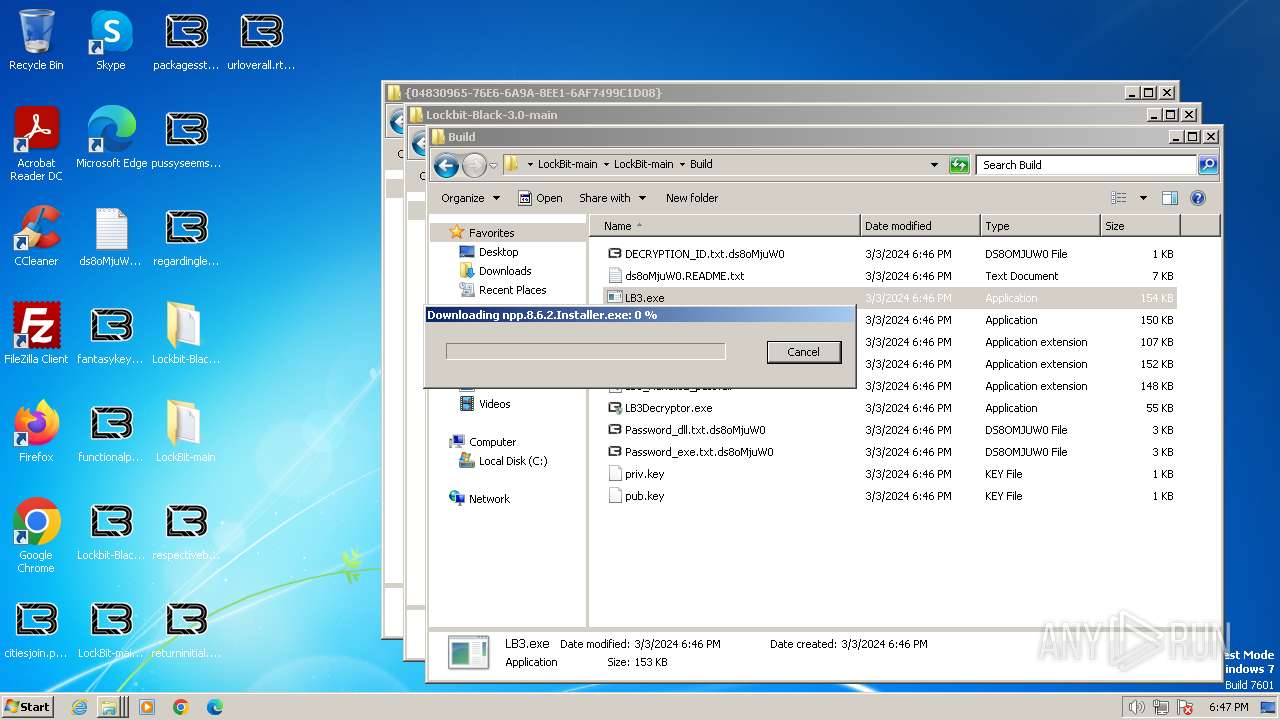
- GUP.exe (PID: 1168)
- npp.8.6.2.Installer.exe (PID: 2060)
Known privilege escalation attack
- dllhost.exe (PID: 1820)
Creates a writable file in the system directory
- LB3.exe (PID: 1264)
- printfilterpipelinesvc.exe (PID: 2296)
Renames files like ransomware
- LB3.exe (PID: 1264)
Steals credentials from Web Browsers
- LB3.exe (PID: 1264)
[YARA] LockBit is detected
- LB3.exe (PID: 1264)
Registers / Runs the DLL via REGSVR32.EXE
- npp.8.6.2.Installer.exe (PID: 2060)
Actions looks like stealing of personal data
- LB3.exe (PID: 1264)
SUSPICIOUS
Executable content was dropped or overwritten
- builder.exe (PID: 296)
- builder.exe (PID: 3036)
- builder.exe (PID: 1584)
- builder.exe (PID: 2348)
- builder.exe (PID: 2588)
- builder.exe (PID: 128)
- LB3.exe (PID: 1264)
- GUP.exe (PID: 1168)
- npp.8.6.2.Installer.exe (PID: 2060)
The process creates files with name similar to system file names
- builder.exe (PID: 1584)
- npp.8.6.2.Installer.exe (PID: 2060)
Write to the desktop.ini file (may be used to cloak folders)
- LB3.exe (PID: 1264)
Reads security settings of Internet Explorer
- notepad++.exe (PID: 3012)
- GUP.exe (PID: 1168)
- 81E4.tmp (PID: 680)
- notepad++.exe (PID: 1404)
Reads the Internet Settings
- printfilterpipelinesvc.exe (PID: 2296)
- 81E4.tmp (PID: 680)
Creates files like ransomware instruction
- LB3.exe (PID: 1264)
Reads browser cookies
- LB3.exe (PID: 1264)
Changes the desktop background image
- LB3.exe (PID: 1264)
Starts CMD.EXE for commands execution
- 81E4.tmp (PID: 680)
Malware-specific behavior (creating "System.dll" in Temp)
- npp.8.6.2.Installer.exe (PID: 2060)
Starts application with an unusual extension
- LB3.exe (PID: 1264)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 2992)
Searches for installed software
- npp.8.6.2.Installer.exe (PID: 2060)
Explorer used for Indirect Command Execution
- explorer.exe (PID: 2884)
Creates a software uninstall entry
- npp.8.6.2.Installer.exe (PID: 2060)
INFO
Manual execution by a user
- WinRAR.exe (PID: 2036)
- WinRAR.exe (PID: 3964)
- {04830965-76E6-6A9A-8EE1-6AF7499C1D08}.exe (PID: 2440)
- cmd.exe (PID: 2040)
- WinRAR.exe (PID: 3848)
- cmd.exe (PID: 480)
- LB3.exe (PID: 3172)
- notepad.exe (PID: 3356)
- notepad++.exe (PID: 3012)
- notepad.exe (PID: 3080)
- LB3Decryptor.exe (PID: 1560)
- LB3Decryptor.exe (PID: 1496)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3848)
- WinRAR.exe (PID: 3964)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3848)
- WinRAR.exe (PID: 3964)
Checks supported languages
- {04830965-76E6-6A9A-8EE1-6AF7499C1D08}.exe (PID: 2440)
- keygen.exe (PID: 2760)
- builder.exe (PID: 296)
- builder.exe (PID: 128)
- builder.exe (PID: 3036)
- builder.exe (PID: 2348)
- builder.exe (PID: 2588)
- builder.exe (PID: 1584)
- LB3.exe (PID: 1264)
- LB3.exe (PID: 3172)
- npp.8.6.2.Installer.exe (PID: 2060)
- LB3Decryptor.exe (PID: 1560)
- 81E4.tmp (PID: 680)
- ONENOTE.EXE (PID: 2780)
Dropped object may contain TOR URL's
- WinRAR.exe (PID: 3848)
- npp.8.6.2.Installer.exe (PID: 2060)
- LB3.exe (PID: 1264)
Reads the machine GUID from the registry
- LB3.exe (PID: 1264)
- LB3.exe (PID: 3172)
- ONENOTE.EXE (PID: 2780)
Reads the computer name
- LB3.exe (PID: 1264)
- LB3.exe (PID: 3172)
- npp.8.6.2.Installer.exe (PID: 2060)
- ONENOTE.EXE (PID: 2780)
- 81E4.tmp (PID: 680)
Checks transactions between databases Windows and Oracle
- LB3.exe (PID: 3172)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 1820)
- explorer.exe (PID: 2952)
Creates files in the program directory
- LB3.exe (PID: 1264)
- npp.8.6.2.Installer.exe (PID: 2060)
Create files in a temporary directory
- LB3.exe (PID: 1264)
- GUP.exe (PID: 1168)
- npp.8.6.2.Installer.exe (PID: 2060)
- ONENOTE.EXE (PID: 2780)
Creates files or folders in the user directory
- printfilterpipelinesvc.exe (PID: 2296)
- LB3.exe (PID: 1264)
- npp.8.6.2.Installer.exe (PID: 2060)
Reads Environment values
- npp.8.6.2.Installer.exe (PID: 2060)
- ONENOTE.EXE (PID: 2780)
Reads Microsoft Office registry keys
- ONENOTE.EXE (PID: 2780)
Process checks computer location settings
- ONENOTE.EXE (PID: 2780)
Reads the Internet Settings
- explorer.exe (PID: 2952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
100
Monitored processes
35
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
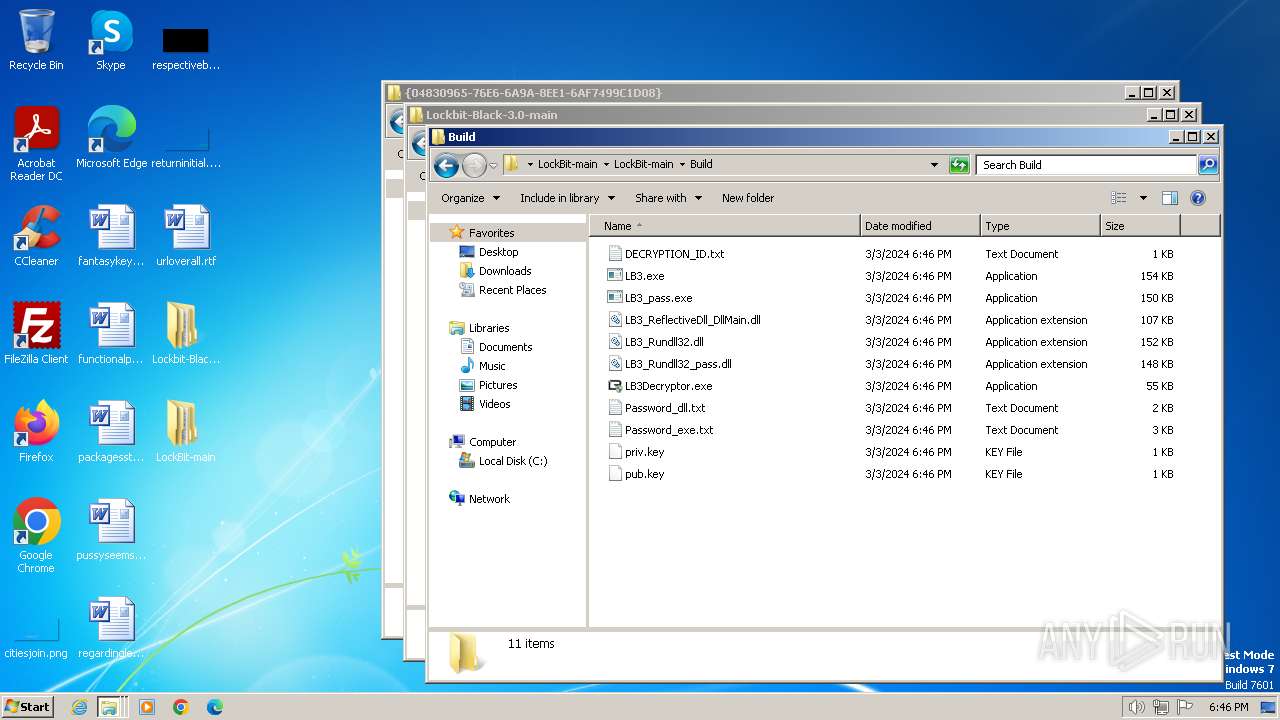
| 128 | builder -type enc -exe -pubkey Build\pub.key -config config.json -ofile Build\LB3.exe | C:\Users\admin\Desktop\LockBit-main\LockBit-main\builder.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 296 | builder -type dec -privkey Build\priv.key -config config.json -ofile Build\LB3Decryptor.exe | C:\Users\admin\Desktop\LockBit-main\LockBit-main\builder.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
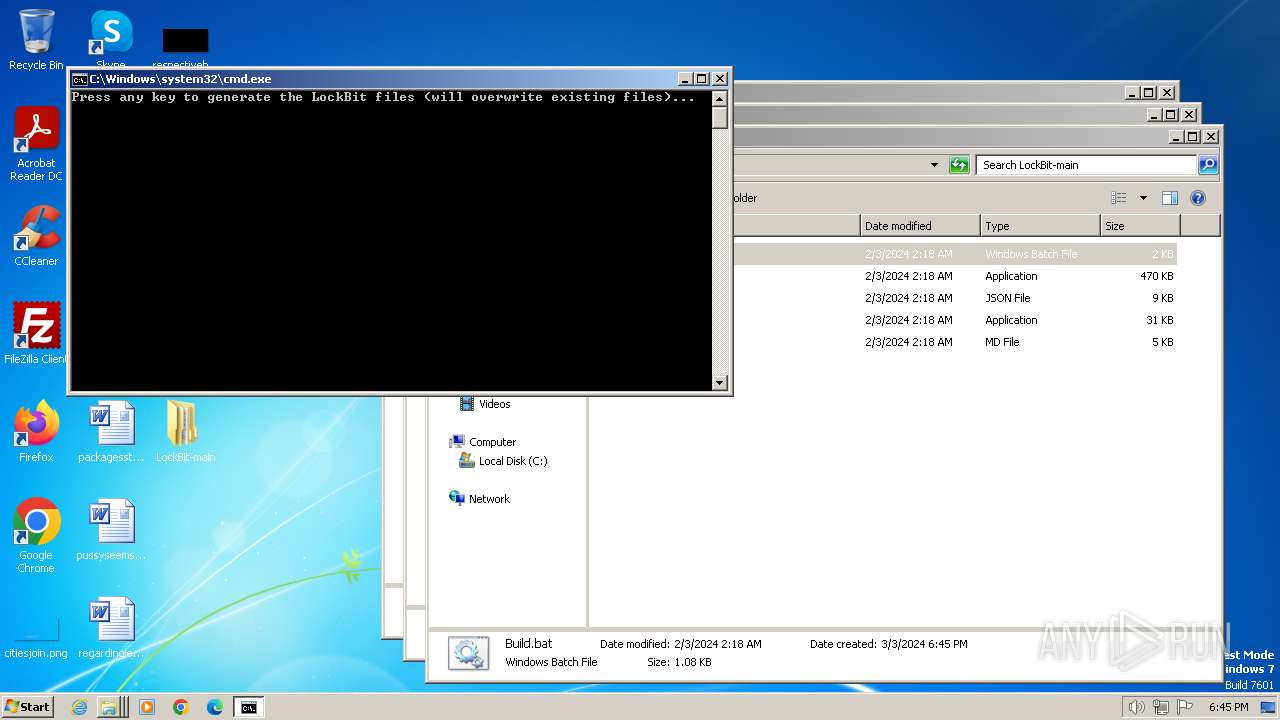
| 480 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\LockBit-main\LockBit-main\Build.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 680 | "C:\ProgramData\81E4.tmp" | C:\ProgramData\81E4.tmp | — | LB3.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1168 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.91 | C:\Program Files\Notepad++\updater\GUP.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: WinGup for Notepad++ Exit code: 0 Version: 5.11 Modules
| |||||||||||||||
| 1264 | "C:\Users\admin\Desktop\LockBit-main\LockBit-main\Build\LB3.exe" | C:\Users\admin\Desktop\LockBit-main\LockBit-main\Build\LB3.exe | dllhost.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1404 | "C:\Program Files\Notepad++\notepad++.exe" | C:\Program Files\Notepad++\notepad++.exe | — | explorer.exe | |||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ Exit code: 0 Version: 8.6.2 Modules
| |||||||||||||||
| 1496 | "C:\Users\admin\Desktop\LockBit-main\LockBit-main\Build\LB3Decryptor.exe" | C:\Users\admin\Desktop\LockBit-main\LockBit-main\Build\LB3Decryptor.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1560 | "C:\Users\admin\Desktop\LockBit-main\LockBit-main\Build\LB3Decryptor.exe" | C:\Users\admin\Desktop\LockBit-main\LockBit-main\Build\LB3Decryptor.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1584 | builder -type enc -dll -pubkey Build\pub.key -config config.json -ofile Build\LB3_Rundll32.dll | C:\Users\admin\Desktop\LockBit-main\LockBit-main\builder.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
17 415
Read events
16 028
Write events
1 380
Delete events
7
Modification events
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Lockbit 3.0.rar | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
41
Suspicious files
604
Text files
1 187
Unknown types
810
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2036 | WinRAR.exe | C:\Users\admin\Desktop\Lockbit-Black-3.0-main\Lockbit-Black-3.0-main\{04830965-76E6-6A9A-8EE1-6AF7499C1D08}.zip | compressed | |
MD5:BA9AD420B3560110B323B1145212FA0F | SHA256:B711D6247A467D516C23151639608177E37C80E80D09D6AFD4766A7DAAC1637E | |||
| 3672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3672.48592\Lockbit-Black-3.0-main.zip | compressed | |
MD5:8ED5B7350F54EC24D149C0340ECA0C50 | SHA256:2F0C8E67B946B4472CDA418E6E637E66DC179E92B14F2F5D8A42115A9E61449A | |||
| 2036 | WinRAR.exe | C:\Users\admin\Desktop\Lockbit-Black-3.0-main\Lockbit-Black-3.0-main\LICENSE | text | |
MD5:86D3F3A95C324C9479BD8986968F4327 | SHA256:C71D239DF91726FC519C6EB72D318EC65820627232B2F796219E87DCF35D0AB4 | |||
| 128 | builder.exe | C:\Users\admin\Desktop\LockBit-main\LockBit-main\Build\LB3.exe | executable | |
MD5:07A93743CA109BC7224386408D694DA0 | SHA256:F0571DB909B16394EE213D1368A75E2B24E4EEC1A80B87411B8C6EE304A202B1 | |||
| 2760 | keygen.exe | C:\Users\admin\Desktop\LockBit-main\LockBit-main\Build\DECRYPTION_ID.txt | text | |
MD5:CFA63B6FAA8054F636CAD8579A883122 | SHA256:E31D672EACDC02C5F412A9A6F822A7C6253522526482CC7297A3D7D29B66DE80 | |||
| 3964 | WinRAR.exe | C:\Users\admin\Desktop\Lockbit-Black-3.0-main\Lockbit-Black-3.0-main\{04830965-76E6-6A9A-8EE1-6AF7499C1D08}\{04830965-76E6-6A9A-8EE1-6AF7499C1D08}.exe | executable | |
MD5:38745539B71CF201BB502437F891D799 | SHA256:80E8DEFA5377018B093B5B90DE0F2957F7062144C83A09A56BBA1FE4EDA932CE | |||
| 2760 | keygen.exe | C:\Users\admin\Desktop\LockBit-main\LockBit-main\Build\priv.key | text | |
MD5:AAF4BF548D1E29011E20E9CC3AD2C8D9 | SHA256:DA62FEE424BA4C92D6B13CC49C09B614C7E17769D97FCEB9AE19974E260A5378 | |||
| 2760 | keygen.exe | C:\Users\admin\Desktop\LockBit-main\LockBit-main\Build\pub.key | text | |
MD5:C9D0182D1258B8AF3690DE0D735D8958 | SHA256:C4615FE892CC3575AF81A9D92056ADEA7273430AE8F1151B23B9D3E5CB69C805 | |||
| 3848 | WinRAR.exe | C:\Users\admin\Desktop\LockBit-main\LockBit-main\Build.bat | text | |
MD5:B8F24EFD1D30AAC9D360DB90C8717AEE | SHA256:95DF1D82137315708931F1FC3411E891CD42D1CAB413D4380B479788729248ED | |||
| 2036 | WinRAR.exe | C:\Users\admin\Desktop\Lockbit-Black-3.0-main\Lockbit-Black-3.0-main\README.md | text | |
MD5:D8F21BB32D72CA834C905F02A4EFB8F8 | SHA256:A312A7D1BE8455B617B7C1463CF48C941E7E4CCD6C4CC912B0F490F4C8B0B3CA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
9
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
488 | lsass.exe | GET | 200 | 23.214.95.209:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?144111b1a3e00b48 | unknown | compressed | 67.5 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1168 | GUP.exe | 179.61.189.170:443 | notepad-plus-plus.org | Hostinger International Limited | AE | unknown |
488 | lsass.exe | 23.214.95.209:80 | ctldl.windowsupdate.com | AKAMAI-AS | BR | unknown |
1168 | GUP.exe | 140.82.121.4:443 | github.com | GITHUB | US | unknown |
1168 | GUP.exe | 185.199.110.133:443 | objects.githubusercontent.com | FASTLY | US | unknown |
3528 | GUP.exe | 185.77.97.139:443 | notepad-plus-plus.org | Hostinger International Limited | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
notepad-plus-plus.org |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
github.com |
| shared |
objects.githubusercontent.com |
| shared |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|