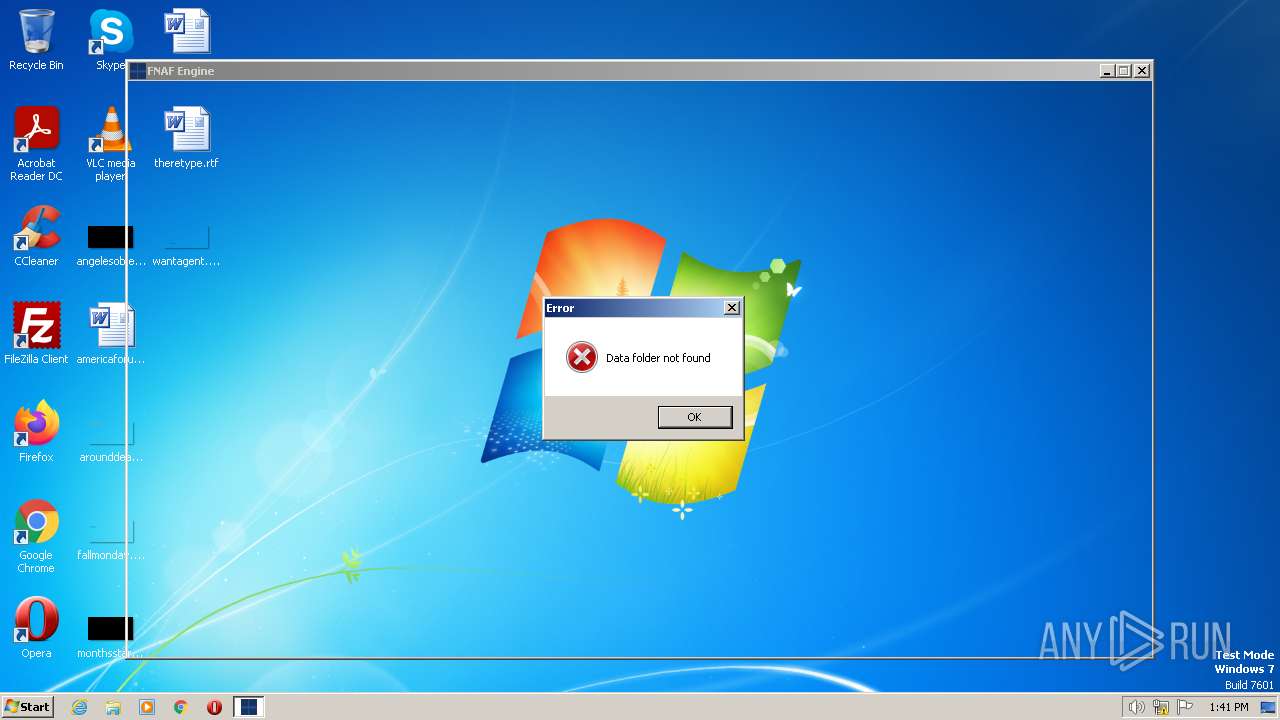
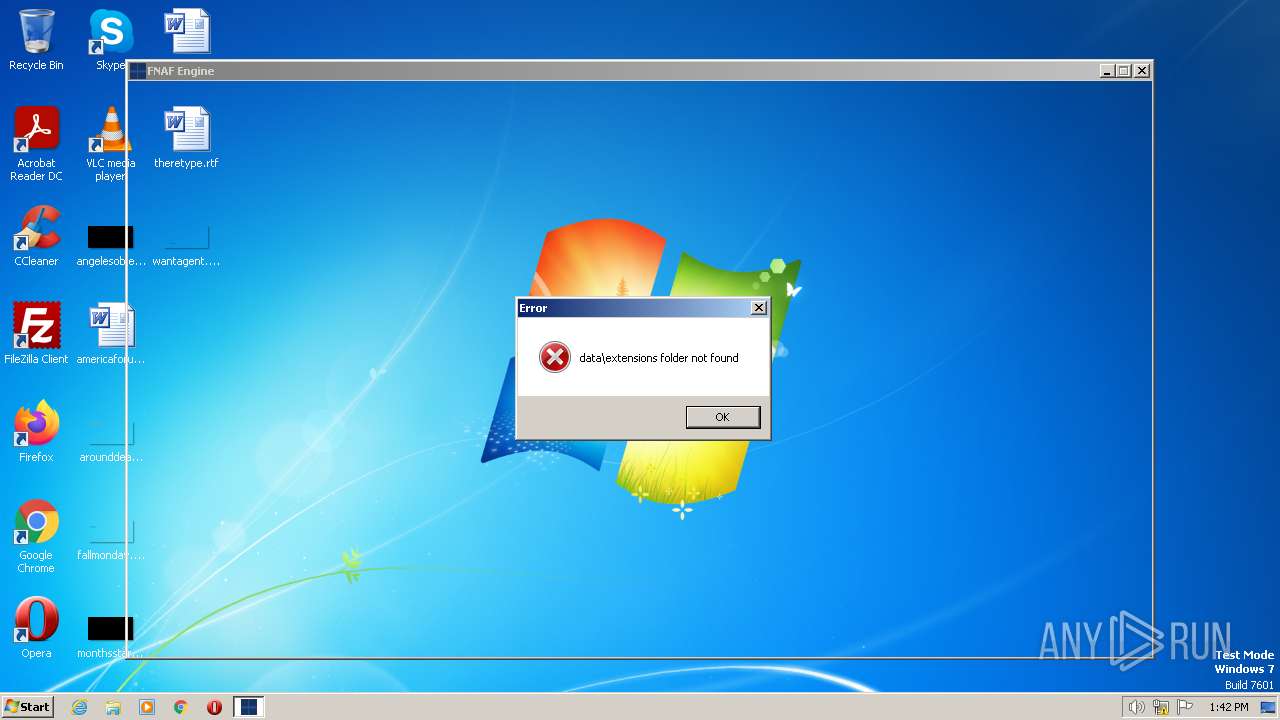
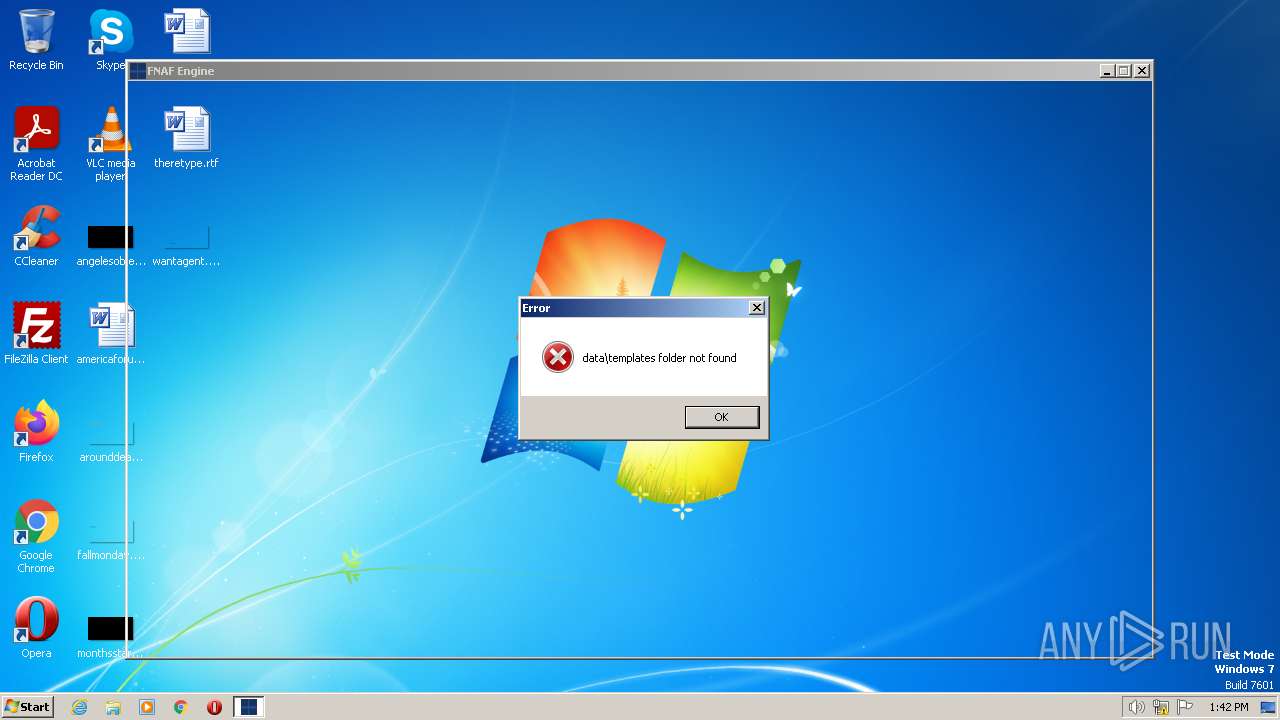
| File name: | FNAF Engine.exe |
| Full analysis: | https://app.any.run/tasks/1e5ba7fc-f8bc-45ed-837a-0270fbbd3b4f |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2023, 12:41:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 02DDA90F1ABCFE80F11F3168CCB88481 |
| SHA1: | 3A3380B00B791D637688FAE6E4FA48699449FEE7 |
| SHA256: | 41576B168E33AE067B7E5387BF0F602B90D7699E2869A259224A2DD18D59BD1B |
| SSDEEP: | 98304:h4LGJJ5VAFAsaqLKZ5hwaA6o06cZR/19oPSswajCov0xsvKk3BZPZgc5:q9aCKZDRAvERN9oPBsO0xnk3LPZJ |
MALICIOUS
Loads dropped or rewritten executable
- FNAF Engine.exe (PID: 2524)
SUSPICIOUS
Executable content was dropped or overwritten
- FNAF Engine.exe (PID: 2524)
Reads the Internet Settings
- FNAF Engine.exe (PID: 2524)
Changes Internet Explorer settings (feature browser emulation)
- FNAF Engine.exe (PID: 2524)
INFO
Create files in a temporary directory
- FNAF Engine.exe (PID: 2524)
Reads the computer name
- FNAF Engine.exe (PID: 2524)
Checks supported languages
- FNAF Engine.exe (PID: 2524)
Reads the machine GUID from the registry
- FNAF Engine.exe (PID: 2524)
Checks proxy server information
- FNAF Engine.exe (PID: 2524)
The process checks LSA protection
- FNAF Engine.exe (PID: 2524)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| LegalCopyright: | - |
|---|---|
| FileVersion: | - |
| FileDescription: | - |
| CompanyName: | - |
| CharacterSet: | Unicode |
| LanguageCode: | Process default |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Windows NT 32-bit |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 3.0.293.1 |
| FileVersionNumber: | 3.0.293.1 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 5.1 |
| ImageVersion: | - |
| OSVersion: | 5.1 |
| EntryPoint: | 0x5faa5 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 435712 |
| CodeSize: | 525312 |
| LinkerVersion: | 14.16 |
| PEType: | PE32 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| TimeStamp: | 2020:12:10 16:58:55+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 10-Dec-2020 16:58:55 |
| Detected languages: |
|
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | - |
| LegalCopyright: | - |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000110 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 10-Dec-2020 16:58:55 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000803FC | 0x00080400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.59939 |
.rdata | 0x00082000 | 0x0001A266 | 0x0001A400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.04398 |
.data | 0x0009D000 | 0x000027CC | 0x00001A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.03914 |
.rsrc | 0x000A0000 | 0x000484F0 | 0x00048600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.3853 |
.reloc | 0x000E9000 | 0x0000617C | 0x00006200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.71946 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.40062 | 1333 | Latin 1 / Western European | Process Default Language | RT_MANIFEST |
2 | 3.99773 | 2216 | Latin 1 / Western European | Process Default Language | RT_ICON |
3 | 3.58939 | 1384 | Latin 1 / Western European | Process Default Language | RT_ICON |
4 | 3.14796 | 270376 | Latin 1 / Western European | Process Default Language | RT_ICON |
5 | 3.331 | 9640 | Latin 1 / Western European | Process Default Language | RT_ICON |
6 | 3.31805 | 4264 | Latin 1 / Western European | Process Default Language | RT_ICON |
7 | 3.15519 | 1128 | Latin 1 / Western European | Process Default Language | RT_ICON |
11 | 4.22193 | 20 | Latin 1 / Western European | Process Default Language | RT_RCDATA |
13 | 3.34415 | 860 | Latin 1 / Western European | Process Default Language | RT_STRING |
100 | 2.71787 | 104 | Latin 1 / Western European | Process Default Language | RT_GROUP_ICON |
Imports
COMCTL32.dll |
COMDLG32.dll |
GDI32.dll |
KERNEL32.dll |
MMFS2.dll (delay-loaded) |
SHELL32.dll |
USER32.dll |
WINMM.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
AmdPowerXpressRequestHighPerformance | 1 | 0x0009E24C |
NvOptimusEnablement | 2 | 0x0009E250 |
Total processes
38
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2524 | "C:\Users\admin\AppData\Local\Temp\FNAF Engine.exe" | C:\Users\admin\AppData\Local\Temp\FNAF Engine.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
319
Read events
300
Write events
17
Delete events
2
Modification events
| (PID) Process: | (2524) FNAF Engine.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Explorer.EXE | |||
| (PID) Process: | (2524) FNAF Engine.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BROWSER_EMULATION |
| Operation: | write | Name: | FNAF Engine.exe |
Value: 11001 | |||
| (PID) Process: | (2524) FNAF Engine.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BROWSER_EMULATION |
| Operation: | write | Name: | FNAF Engine.vhost.exe |
Value: 11001 | |||
| (PID) Process: | (2524) FNAF Engine.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2524) FNAF Engine.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003D010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2524) FNAF Engine.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2524) FNAF Engine.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2524) FNAF Engine.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2524) FNAF Engine.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2524) FNAF Engine.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
72
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2524 | FNAF Engine.exe | C:\Users\admin\AppData\Local\Temp\e9dd5791-7c28-4a1e-a446-4d1a52dca9d9.FusionApp\CalcRect.mfx | executable | |
MD5:49654E589A72C00BFBFBF353D90AE0CE | SHA256:5100136FB7F025AF193DAAF39189C746299BDBA640867465FAF52BA2125DF066 | |||
| 2524 | FNAF Engine.exe | C:\Users\admin\AppData\Local\Temp\e9dd5791-7c28-4a1e-a446-4d1a52dca9d9.FusionApp\Blowfish.mfx | executable | |
MD5:46B4E07996614B78DFEDE54705B97091 | SHA256:6923E91A2EA3D49B9BF807ACE894016A0F03C2B5AEDB9B2E7DA23AAB58F83FC7 | |||
| 2524 | FNAF Engine.exe | C:\Users\admin\AppData\Local\Temp\e9dd5791-7c28-4a1e-a446-4d1a52dca9d9.FusionApp\KcButton.mfx | executable | |
MD5:F38AFA3809F84935DC3044493F30AC55 | SHA256:12E974EB1BDCDFD93B99B64CCCAF5AB90C57B21918EA758FE212300F4BAC89B5 | |||
| 2524 | FNAF Engine.exe | C:\Users\admin\AppData\Local\Temp\e9dd5791-7c28-4a1e-a446-4d1a52dca9d9.FusionApp\KcBoxA.mfx | executable | |
MD5:CC056A1B7F3F5FFCD7BF6B3CEFFEE60C | SHA256:5B86022F2F80F0FF5B5D937A17B33F7C046390B79E91E5D7E6FCD657742794DC | |||
| 2524 | FNAF Engine.exe | C:\Users\admin\AppData\Local\Temp\e9dd5791-7c28-4a1e-a446-4d1a52dca9d9.FusionApp\TreeControl.mfx | executable | |
MD5:72489DFD9398C8F0DA5458E3D743014D | SHA256:3EB6510731A2CFB05B45CADFA1F430DB8D61524F391E4DEA1EA1C46C0E07CFA7 | |||
| 2524 | FNAF Engine.exe | C:\Users\admin\AppData\Local\Temp\e9dd5791-7c28-4a1e-a446-4d1a52dca9d9.FusionApp\kcpop.mfx | executable | |
MD5:44557BF7FF780CFA6019C0C4119FB54A | SHA256:28726AE556CBE1E2B4995AB135DA1BFC72D0BC4E4F56D821E95DAB738EED61A6 | |||
| 2524 | FNAF Engine.exe | C:\Users\admin\AppData\Local\Temp\e9dd5791-7c28-4a1e-a446-4d1a52dca9d9.FusionApp\kccombo.mfx | executable | |
MD5:76B8BB3C495971EBE35BC295028C16C3 | SHA256:88A9E2D3142B05899B6B2333948BBBED60BCCBBE7906AB6DFE2829709D337166 | |||
| 2524 | FNAF Engine.exe | C:\Users\admin\AppData\Local\Temp\e9dd5791-7c28-4a1e-a446-4d1a52dca9d9.FusionApp\mmf2d3d8.dll | executable | |
MD5:FA439EDEB7D0BF6F637670F14CEBD157 | SHA256:B558A04FD67D0D7CD71170A2B7A1BFD004F0B5BCC268E7B38C3A12FE72CA26D8 | |||
| 2524 | FNAF Engine.exe | C:\Users\admin\AppData\Local\Temp\e9dd5791-7c28-4a1e-a446-4d1a52dca9d9.FusionApp\mmfs2.dll | executable | |
MD5:09FEB373CFCF9FD9A618D0A38759E297 | SHA256:4DE2B0753A286D3572574D6C03F769176973B9E2EB53F5B6645B32854983EFF0 | |||
| 2524 | FNAF Engine.exe | C:\Users\admin\AppData\Local\Temp\e9dd5791-7c28-4a1e-a446-4d1a52dca9d9.FusionApp\xlua.mfx | executable | |
MD5:7EBF30A8F141D2E3147DF95183CF61AA | SHA256:6FC403434AEF71199DF48B329F2F05D19858BD0CAA4F480FD6D60FBC31324DC5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
5
DNS requests
1
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2524 | FNAF Engine.exe | GET | 404 | 35.173.69.207:80 | http://sealedapi.pythonanywhere.com/fe_ext | US | html | 2.86 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2524 | FNAF Engine.exe | 35.173.69.207:80 | sealedapi.pythonanywhere.com | AMAZON-AES | US | malicious |
1476 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
sealedapi.pythonanywhere.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1076 | svchost.exe | Potential Corporate Privacy Violation | AV POLICY PythonAnywhere Observed DNS Query |
2524 | FNAF Engine.exe | Misc activity | ET INFO Observed HTTP Request to *.pythonanywhere .com Domain |
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
FNAF Engine.exe | Start app
|
FNAF Engine.exe | Start app
|
FNAF Engine.exe | Start app
|
FNAF Engine.exe | Start Frame 0
|
FNAF Engine.exe | Start Frame 0
|
FNAF Engine.exe | Start app
|
FNAF Engine.exe | Start app
|
FNAF Engine.exe | Start app
|
FNAF Engine.exe | Start Frame 2
|
FNAF Engine.exe | Start Frame 2
|