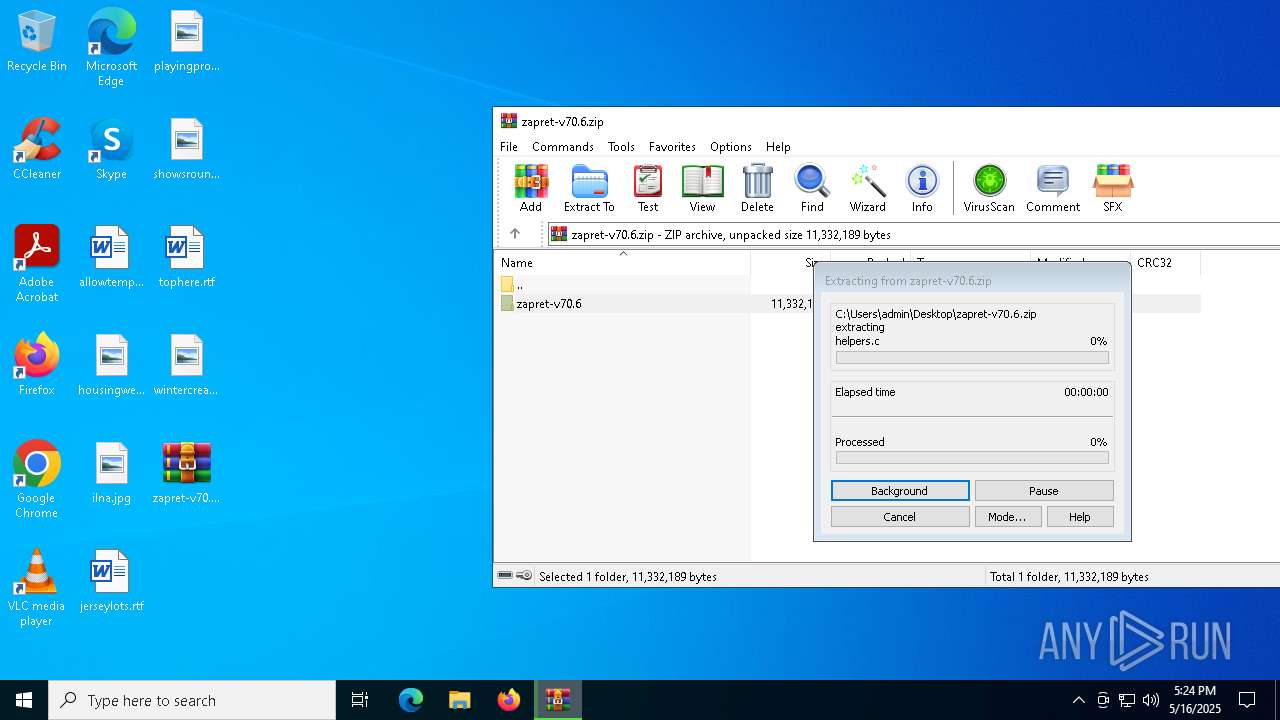
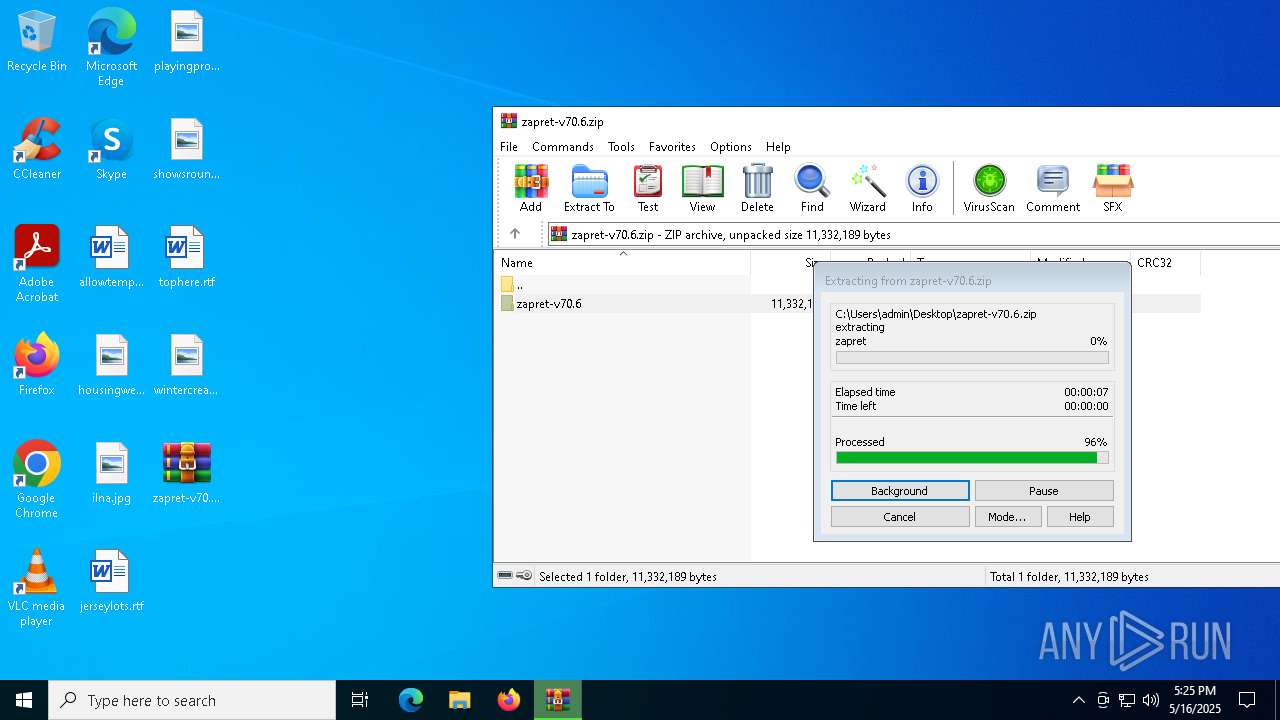
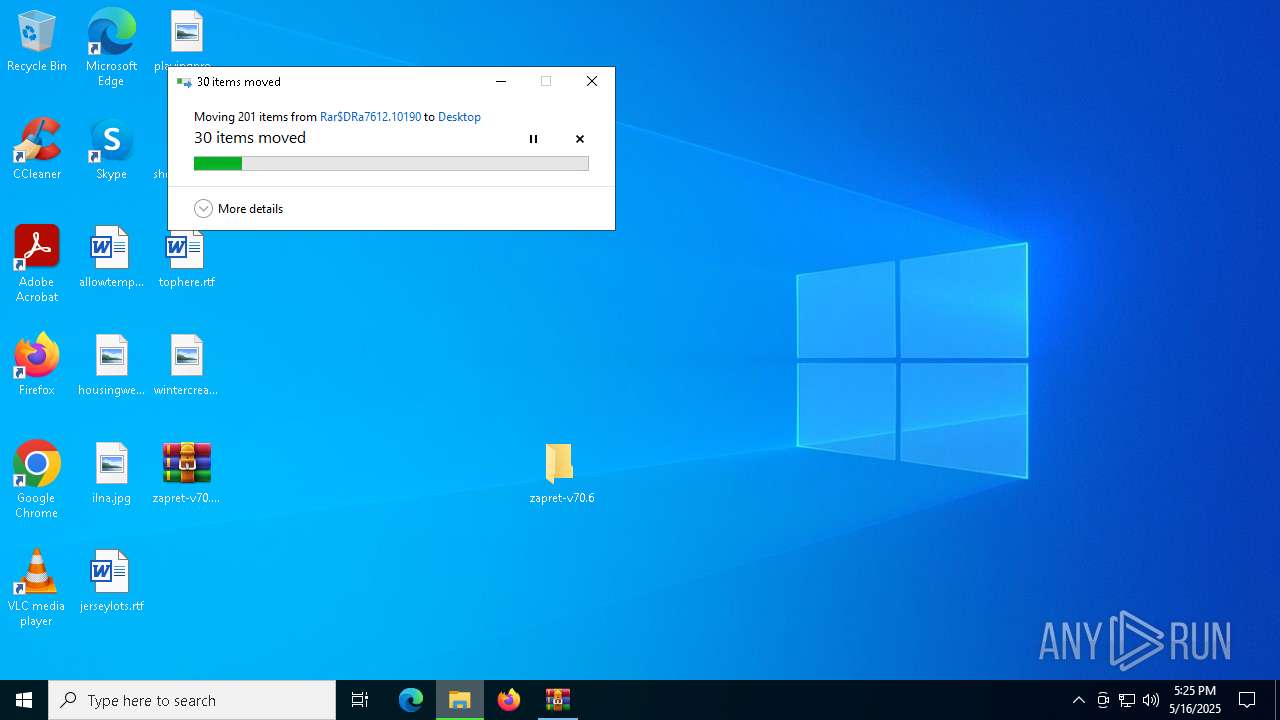
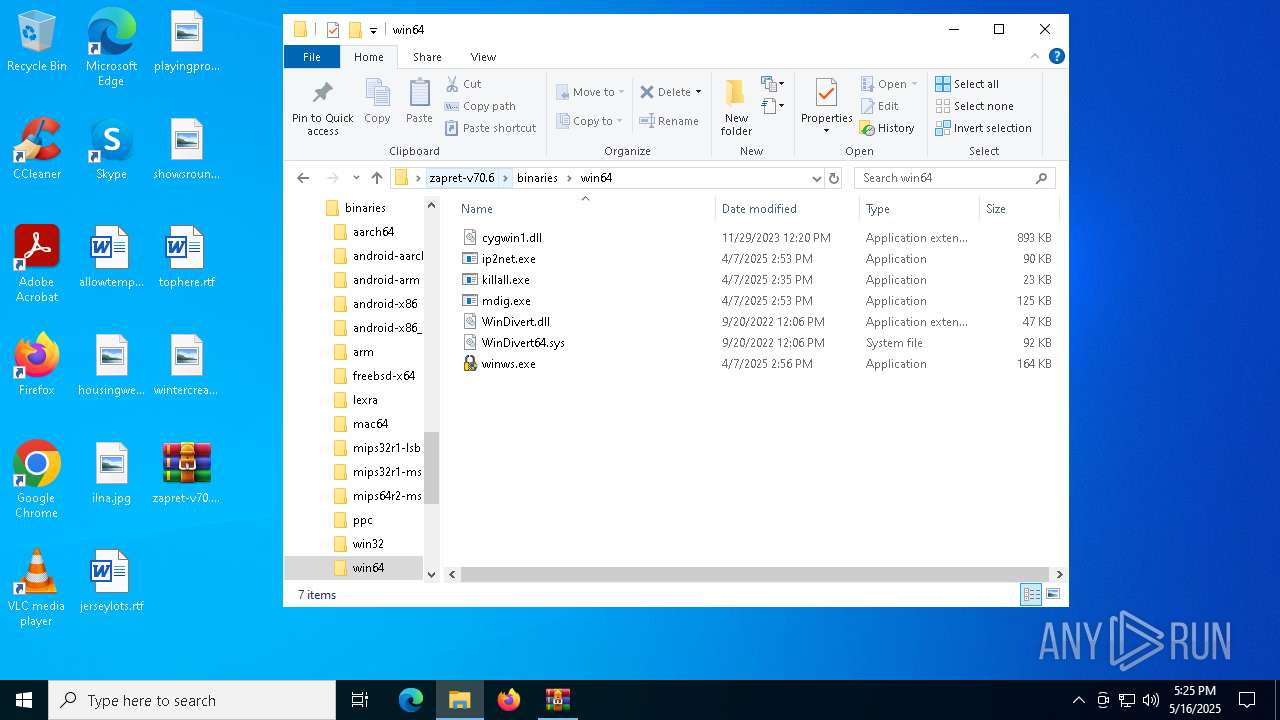
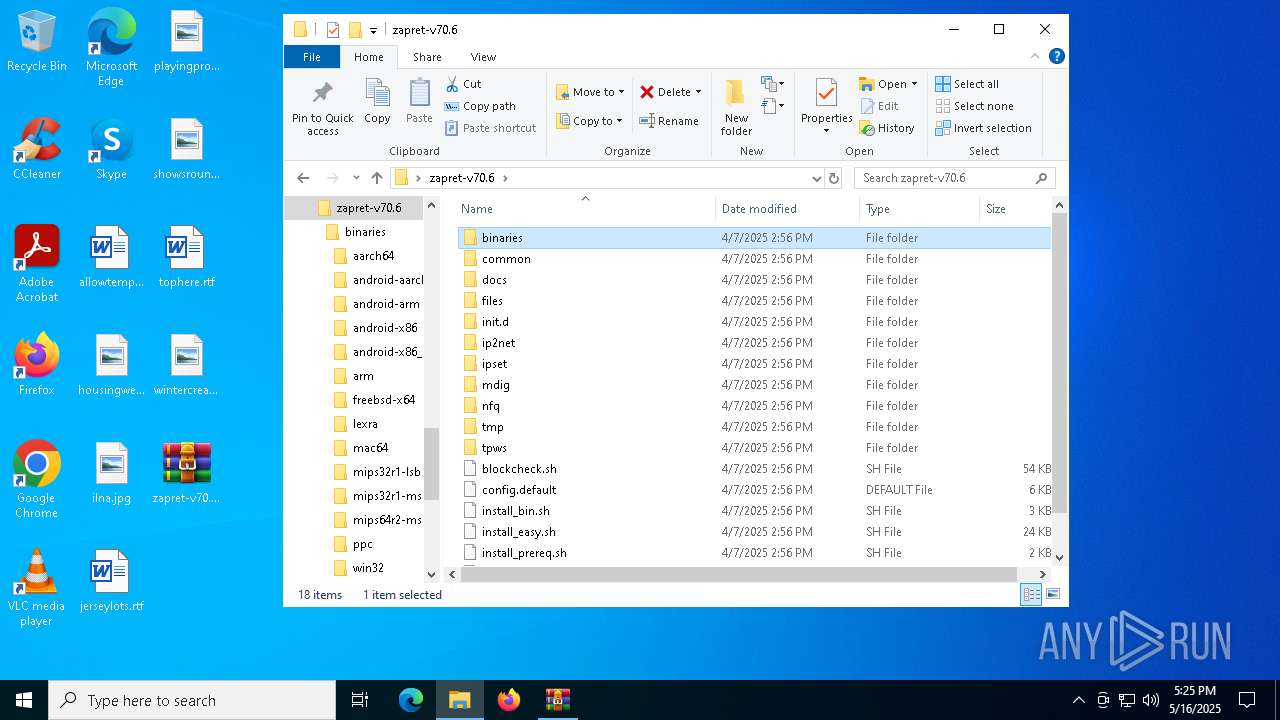
| File name: | zapret-v70.6.zip |
| Full analysis: | https://app.any.run/tasks/b36f7a70-0f53-4d85-b4fb-1c23802fe15e |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 17:24:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | FFA89A8EF385CC95832F8A9CD7E9F65C |
| SHA1: | 2B6BAB8FDE2ACB33E0F0FBB36760A82FB9625B02 |
| SHA256: | 414E8A270541E463920F69B735F04A9222F1437648AFF6EDF073BA4F51012D4C |
| SSDEEP: | 98304:nQmbKJ4JYkVxYwCupQUVQo3PMu5HGKnIBFI62/lq6TkAC2GysPgwWMKU0oivS+Wc:zJowePpnppRxnc+ovvtge/+aH |
MALICIOUS
Malicious driver has been detected
- WinRAR.exe (PID: 7612)
Detects Cygwin installation
- WinRAR.exe (PID: 7612)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 7612)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 7612)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:04:07 14:56:30 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | zapret-v70.6/ |
Total processes
129
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7612 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\zapret-v70.6.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 8176 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 328
Read events
1 320
Write events
8
Delete events
0
Modification events
| (PID) Process: | (7612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\zapret-v70.6.zip | |||
| (PID) Process: | (7612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
28
Suspicious files
194
Text files
424
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7612.9265\zapret-v70.6\ip2net\qsort.h | text | |
MD5:EEB34EF16D0B8F1281BA5E0ACB134006 | SHA256:9EA5083D64557D408183C4F17138EB223D9EF21403F4A74624BEA4BD101A4FB0 | |||
| 7612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7612.9265\zapret-v70.6\ip2net\qsort.c | text | |
MD5:585AFE08CDD547C5685C6B91A240FD26 | SHA256:4CFF8CA795F749AD7631307E51948EA7B916629FEF3B4F30A1DA09DA5783486B | |||
| 7612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7612.9265\zapret-v70.6\tpws\Makefile | text | |
MD5:115DF731BEF5409541CB322FAE9D9E6D | SHA256:04019EB5D6AE86FF62D9E54D7B549EBEE34B770D3FE9334DA648D6EF774B5B3E | |||
| 7612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7612.9265\zapret-v70.6\install_bin.sh | text | |
MD5:7AD578DE20601F77BD3CFA28765F785F | SHA256:B2C4F84FF70E17DEBD3B80AD5EC84EACB981C43DEDF0B957897BE00B8B9489E3 | |||
| 7612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7612.9265\zapret-v70.6\Makefile | text | |
MD5:03320A6BD01B3FFEAFDE8774AB6CCE62 | SHA256:9286336D75E44BA16E0206286E1F0F3D95B398E1FBEB3DAF34F4BC8D3FBA3DE3 | |||
| 7612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7612.9265\zapret-v70.6\ip2net\Makefile | text | |
MD5:5BEA9499A626B9C7E1CCA4A060A927B8 | SHA256:C5C55C47691A89294BA789CCB1AE2734B0EBE5CEB963164E8A5538AF24046B46 | |||
| 7612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7612.9265\zapret-v70.6\config.default | text | |
MD5:B54641BD260965B7AFDFB6EDF9A306EA | SHA256:81B92CD724356F7A7C8E279A6FC927335EA0F453C173282AE21AF60DA7CE281A | |||
| 7612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7612.9265\zapret-v70.6\mdig\Makefile | text | |
MD5:744A56B7C27F78BFC23E352DA48A44BE | SHA256:B6EA7ECE2199593F33F9FEB73411158EDE4A59800F824A1877AC52C356F3D89A | |||
| 7612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7612.9265\zapret-v70.6\ip2net\ip2net.c | text | |
MD5:01169A12BD5B1D51FAA1185A684B6F46 | SHA256:C89B42F6C92DF79CB55C71D00EA32FC23C3A30AEF1A5DE0363A80FDFB1BC7C16 | |||
| 7612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7612.9265\zapret-v70.6\mdig\mdig.c | text | |
MD5:C013D2AB28585B66A10BA35DE5F3BD36 | SHA256:07E9521E99350816A64E0B12D26EEDD7A6CF54A24FDF9931172EA7350B5387D9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
16
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7960 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7960 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4628 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7960 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7960 | SIHClient.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |