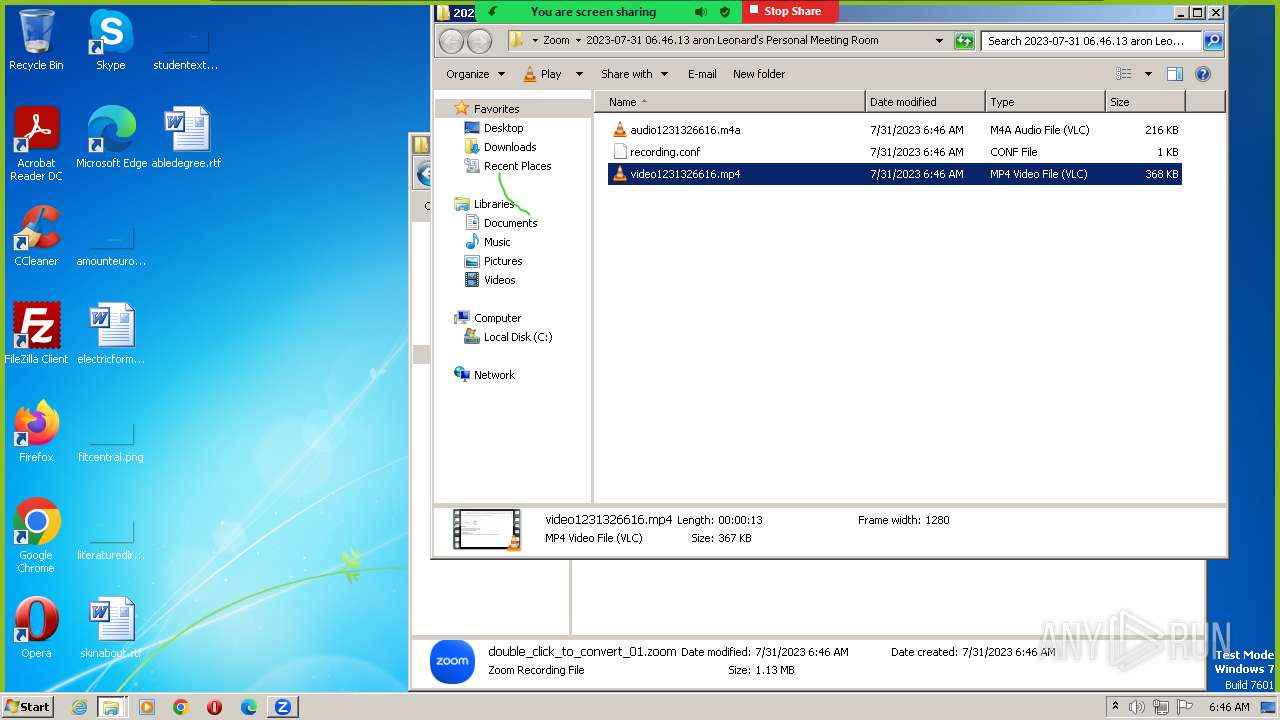
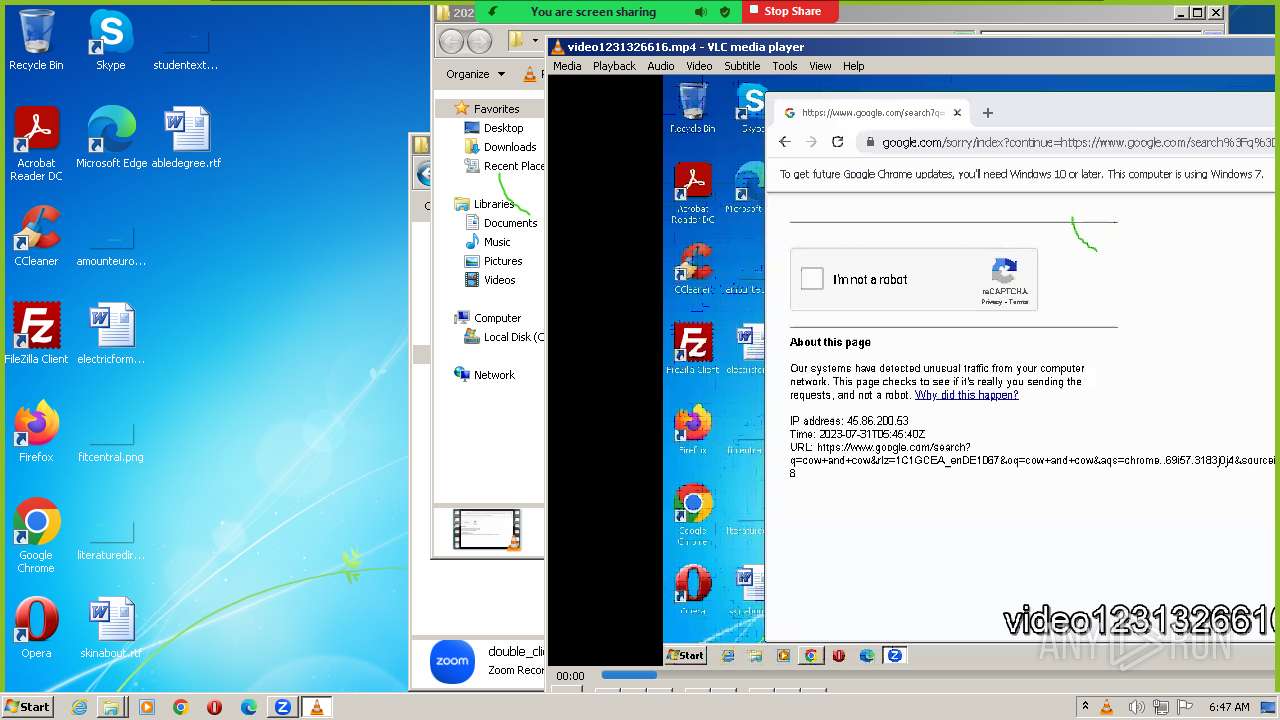
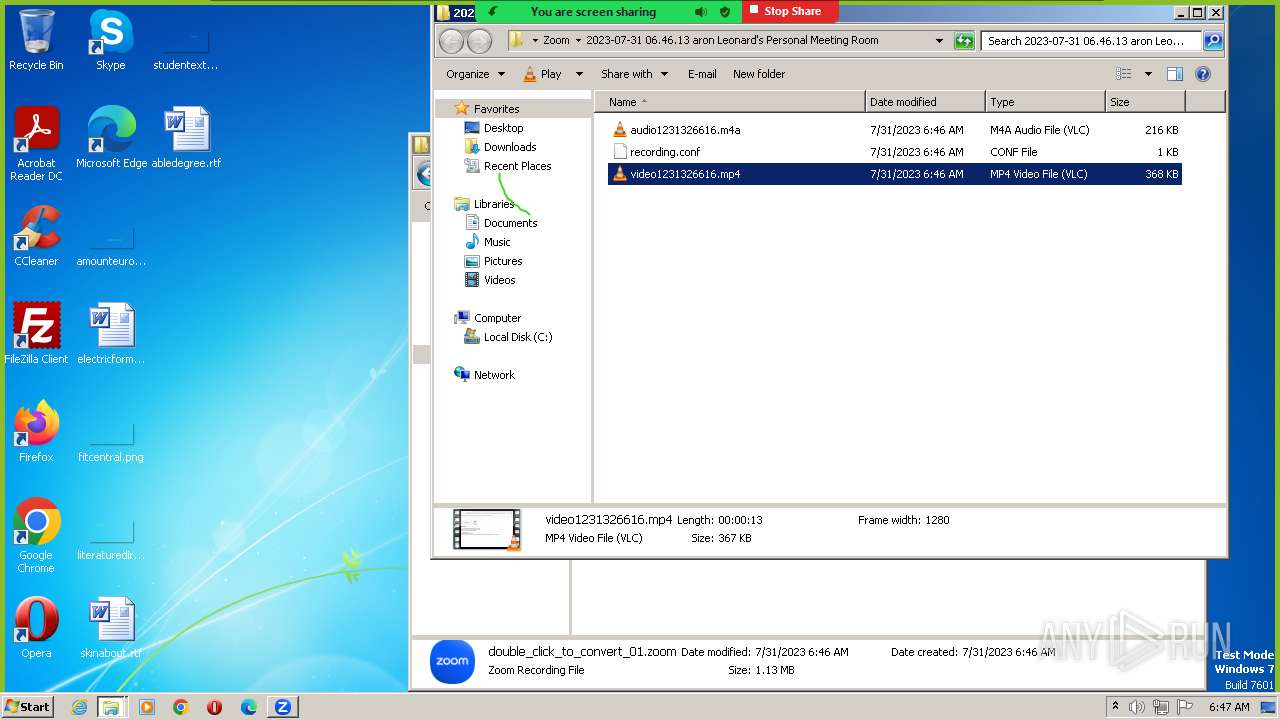
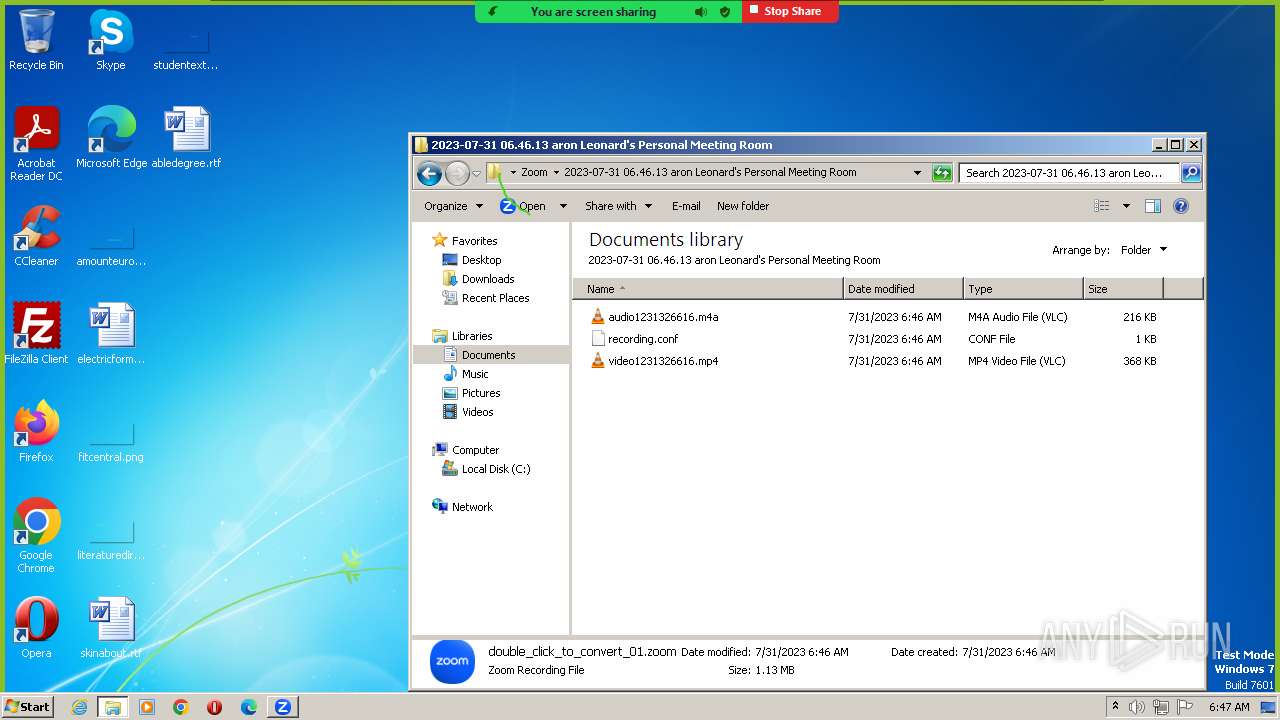
| URL: | https://us04web.zoom.us/j/4594279774?pwd=GJJ3qhoVAa4YRA9xDvhxjymuS2jX6s.1 |
| Full analysis: | https://app.any.run/tasks/ebcbea90-e863-4c8c-87a1-cf68e259dca2 |
| Verdict: | Malicious activity |
| Analysis date: | July 31, 2023, 05:42:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 9EA6FDB3BFA1FC3F4F7C5B93B268BA28 |
| SHA1: | 708E1E34BB205D21B77C903F85D6F06621DA0A27 |
| SHA256: | 4148F61209C80BB20DBD796E657CA1345CF3C87CDD252AA7170B493D9D265A81 |
| SSDEEP: | 3:N8VeKILQNTgXvhiukR8n++P9ag:2j9Efhih8n+e |
MALICIOUS
Application was dropped or rewritten from another process
- Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe (PID: 1644)
- Installer.exe (PID: 3028)
- Installer.exe (PID: 348)
- Zoom.exe (PID: 2580)
- zm3C87.tmp (PID: 2240)
- Zoom.exe (PID: 3848)
- CptHost.exe (PID: 3804)
- zWebview2Agent.exe (PID: 3632)
- zTscoder.exe (PID: 2080)
Loads dropped or rewritten executable
- Installer.exe (PID: 3028)
- Zoom.exe (PID: 2580)
- Zoom.exe (PID: 3848)
- CptHost.exe (PID: 3804)
- zWebview2Agent.exe (PID: 3632)
- zTscoder.exe (PID: 2080)
SUSPICIOUS
Reads the Internet Settings
- Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe (PID: 1644)
- Installer.exe (PID: 3028)
- Zoom.exe (PID: 2580)
- Zoom.exe (PID: 3848)
Reads security settings of Internet Explorer
- Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe (PID: 1644)
- Installer.exe (PID: 3028)
- Zoom.exe (PID: 2580)
- Zoom.exe (PID: 3848)
- CptHost.exe (PID: 3804)
- zWebview2Agent.exe (PID: 3632)
Checks Windows Trust Settings
- Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe (PID: 1644)
- Installer.exe (PID: 3028)
- Zoom.exe (PID: 2580)
- Zoom.exe (PID: 3848)
- CptHost.exe (PID: 3804)
- zWebview2Agent.exe (PID: 3632)
Reads settings of System Certificates
- Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe (PID: 1644)
- Installer.exe (PID: 3028)
- Zoom.exe (PID: 2580)
- Zoom.exe (PID: 3848)
- CptHost.exe (PID: 3804)
- zWebview2Agent.exe (PID: 3632)
Executable content was dropped or overwritten
- Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe (PID: 1644)
- Installer.exe (PID: 3028)
- Zoom.exe (PID: 2580)
- zWebview2Agent.exe (PID: 3632)
Adds/modifies Windows certificates
- iexplore.exe (PID: 2604)
The process creates files with name similar to system file names
- Installer.exe (PID: 3028)
- Zoom.exe (PID: 2580)
Application launched itself
- Installer.exe (PID: 3028)
- Zoom.exe (PID: 2580)
Starts application with an unusual extension
- Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe (PID: 1644)
Starts itself from another location
- Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe (PID: 1644)
INFO
Executable content was dropped or overwritten
- iexplore.exe (PID: 2808)
- iexplore.exe (PID: 2604)
Application launched itself
- iexplore.exe (PID: 2604)
- chrome.exe (PID: 3332)
Checks supported languages
- Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe (PID: 1644)
- Installer.exe (PID: 3028)
- Installer.exe (PID: 348)
- Zoom.exe (PID: 2580)
- zm3C87.tmp (PID: 2240)
- Zoom.exe (PID: 3848)
- wmpnscfg.exe (PID: 3956)
- CptHost.exe (PID: 3804)
- zWebview2Agent.exe (PID: 3632)
- zTscoder.exe (PID: 2080)
- vlc.exe (PID: 2872)
Reads the computer name
- Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe (PID: 1644)
- Installer.exe (PID: 3028)
- Installer.exe (PID: 348)
- Zoom.exe (PID: 2580)
- Zoom.exe (PID: 3848)
- wmpnscfg.exe (PID: 3956)
- CptHost.exe (PID: 3804)
- zWebview2Agent.exe (PID: 3632)
- zTscoder.exe (PID: 2080)
- vlc.exe (PID: 2872)
The process uses the downloaded file
- iexplore.exe (PID: 2604)
- Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe (PID: 1644)
- chrome.exe (PID: 4088)
- chrome.exe (PID: 3188)
Checks proxy server information
- Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe (PID: 1644)
Creates files or folders in the user directory
- Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe (PID: 1644)
- Installer.exe (PID: 3028)
- Zoom.exe (PID: 2580)
- Zoom.exe (PID: 3848)
- zWebview2Agent.exe (PID: 3632)
Reads the machine GUID from the registry
- Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe (PID: 1644)
- Installer.exe (PID: 3028)
- Zoom.exe (PID: 2580)
- Zoom.exe (PID: 3848)
- wmpnscfg.exe (PID: 3956)
- CptHost.exe (PID: 3804)
- zWebview2Agent.exe (PID: 3632)
- zTscoder.exe (PID: 2080)
- vlc.exe (PID: 2872)
The process checks LSA protection
- Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe (PID: 1644)
- Installer.exe (PID: 3028)
- Zoom.exe (PID: 2580)
- Zoom.exe (PID: 3848)
- wmpnscfg.exe (PID: 3956)
- CptHost.exe (PID: 3804)
- explorer.exe (PID: 2916)
- zWebview2Agent.exe (PID: 3632)
- zTscoder.exe (PID: 2080)
- vlc.exe (PID: 2872)
Dropped object may contain TOR URL's
- Installer.exe (PID: 3028)
Create files in a temporary directory
- Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe (PID: 1644)
- Zoom.exe (PID: 2580)
Process checks computer location settings
- Zoom.exe (PID: 2580)
- Zoom.exe (PID: 3848)
Manual execution by a user
- wmpnscfg.exe (PID: 3956)
- chrome.exe (PID: 3332)
- explorer.exe (PID: 2916)
- zTscoder.exe (PID: 2080)
- vlc.exe (PID: 2872)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
78
Monitored processes
31
Malicious processes
8
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 348 | "C:\Users\admin\AppData\Roaming\Zoom\ZoomDownload\Installer.exe" /addfwexception --bin_home="C:\Users\admin\AppData\Roaming\Zoom\bin" | C:\Users\admin\AppData\Roaming\Zoom\ZoomDownload\Installer.exe | Installer.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: HIGH Description: Zoom Installer Exit code: 0 Version: 5,15,5,19404 Modules
| |||||||||||||||
| 916 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=3952 --field-trial-handle=1200,i,14629465572573202910,3338897987857584388,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1060 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1340 --field-trial-handle=1200,i,14629465572573202910,3338897987857584388,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1644 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe | iexplore.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Opener Exit code: 0 Version: 5,15,5,23 Modules
| |||||||||||||||
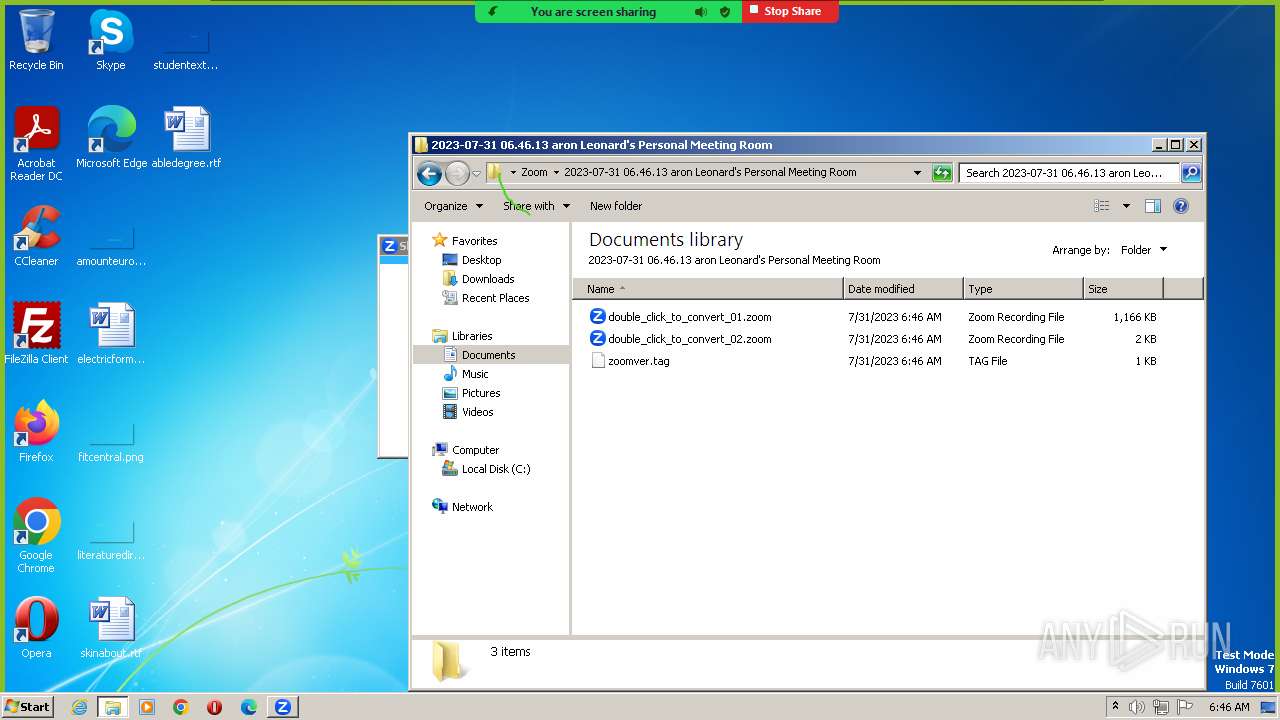
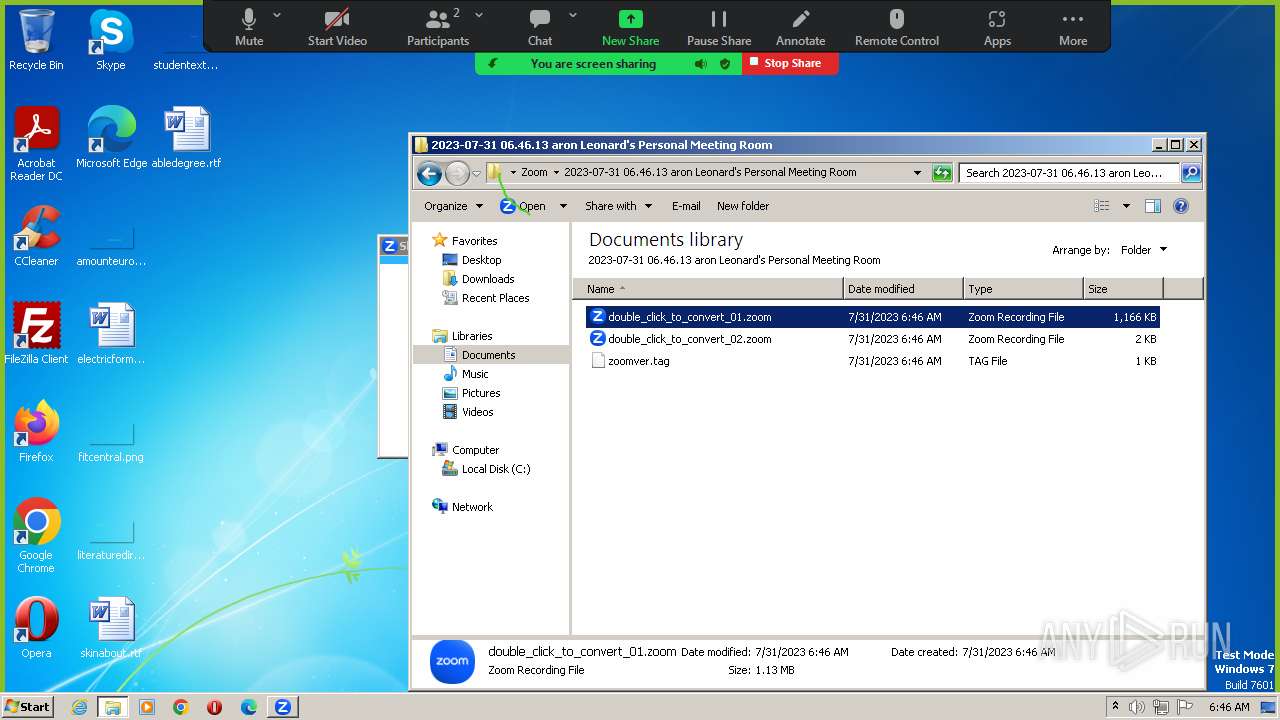
| 2080 | "C:\Users\admin\AppData\Roaming\Zoom\bin\zTscoder.exe" "C:\Users\admin\Documents\Zoom\2023-07-31 06.46.13 aron Leonard's Personal Meeting Room\double_click_to_convert_01.zoom" | C:\Users\admin\AppData\Roaming\Zoom\bin\zTscoder.exe | explorer.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Exit code: 0 Version: 5,15,5,19404 Modules
| |||||||||||||||
| 2084 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=3684 --field-trial-handle=1200,i,14629465572573202910,3338897987857584388,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2240 | "C:\Users\admin\AppData\Local\Temp\zm3C87.tmp" -DAF8C715436E44649F1312698287E6A5=C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe | C:\Users\admin\AppData\Local\Temp\zm3C87.tmp | — | Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe | |||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Opener Exit code: 0 Version: 5,15,5,23 Modules
| |||||||||||||||
| 2316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=2128 --field-trial-handle=1200,i,14629465572573202910,3338897987857584388,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2384 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1044 --field-trial-handle=1200,i,14629465572573202910,3338897987857584388,131072 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2580 | "C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe" "--url=zoommtg://win.launch?h.domain=us04web.zoom.us&h.path=join&confid=dXNzPWJXUVdHTW1XOW5QOUNyTjlScGJ6dk1JVHdIX0JwQmk1UW1vODJUTDJmWHBUZ0RIMllEVkdjZ0hJU3NUSl9WcHRaUjBvR0VvMzVGbGxNM3dZRFFqRlBVQ0xZTmRRR3cuSXFsVjlNQTZwdjMyM1ZxaCZ0aWQ9NDNlMDgzMzRlNjk5NGFjNzlkMTIyMGIwNWQxZjVjZTc%3D&mcv=0.92.11227.0929&stype=0&zc=0&browser=msie&action=join&confno=4594279774&pwd=GJJ3qhoVAa4YRA9xDvhxjymuS2jX6s.1" | C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe | Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Meetings Exit code: 0 Version: 5,15,5,19404 Modules
| |||||||||||||||
Total events
68 919
Read events
68 638
Write events
273
Delete events
8
Modification events
| (PID) Process: | (2604) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2604) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2604) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2604) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2604) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2604) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2604) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2604) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2604) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2604) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
323
Suspicious files
437
Text files
872
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2808 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 2808 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\NCINDLV3.txt | text | |
MD5:A2A38FFCEEA106F33F5E003F7C0201BB | SHA256:DFC954434101DB1740BFC4D28B3A4617E6F9C0FFA7FE490FA4777066B7D7F306 | |||
| 2808 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\QVID4JPW.txt | text | |
MD5:27A514B0CC09EAD4A1D98DC36C33FED2 | SHA256:5C46FEAB45631A8606E0D9456AA3DA691C8E83EC968953E587CC3E7E8FF0CA6F | |||
| 2808 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\5GJRB6NB.txt | text | |
MD5:9627F5FAC733BFA30B44E55A602269B6 | SHA256:3498738F464083273CAE77AF1F25A04F68B49ECFD6EBFE5DEFDCAFB5096E0D07 | |||
| 2808 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:DBA0DFB90230CAF59A6DA0CC25D298D5 | SHA256:2CCA042971584575A739AA03282D5CBD93A41C24EE7EE58694DA15DB542AB5A6 | |||
| 2808 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:1F6677F114980D6EA1942B8BA9B517FB | SHA256:3662F7D987582467424C1397FE65FC354DA56CA4D69F24DB4699A8FF93481914 | |||
| 2808 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | der | |
MD5:41E243A4A8D185BA36B8F3788CA2F434 | SHA256:D4C0F8A40818E10EBAD7CF9B9A93C8E17E60C907ED536D92EE4E0E8B83AF1DE5 | |||
| 2808 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C11083FD8BAD269CF864618FA59583AC_1891403E774E171AB4237C0ED2A81174 | binary | |
MD5:0631AA273D777A1E5D85028D90A13FD1 | SHA256:C96F5557D91F7996B5A275AE31255B22ADDE0AAD2CC42DC9E07E9E65726EDD1B | |||
| 2808 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\QXRMR3GZ.txt | text | |
MD5:33800C02D814DA304BE0114122D14293 | SHA256:7DCADB57DD2F622952388FC6F76506346F3F9EA25DBD9A663CC66F0B5ACD6873 | |||
| 2808 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80237EE4964FC9C409AAF55BF996A292_FB287BEB63DB9E8D59A799779773B97C | binary | |
MD5:1AA24B32A5E96F88B52EFABABF82873F | SHA256:0125DB26125515EA933966BF92B7B4C0B60F2662B0B30EF67987BA0E83DA513F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
94
DNS requests
82
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1644 | Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe | GET | 304 | 95.140.236.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?86906236b7a32f9e | GB | — | — | whitelisted |
2808 | iexplore.exe | GET | — | 142.250.186.163:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | — | — | whitelisted |
1088 | svchost.exe | GET | 304 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c97f70885be7117c | US | — | — | whitelisted |
2808 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCECGEtHKlH4FiCZ6hjx99NRk%3D | US | binary | 471 b | whitelisted |
2808 | iexplore.exe | GET | — | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCECfSiZiMUmuQCbhUYwWCvAY%3D | US | — | — | whitelisted |
2808 | iexplore.exe | GET | — | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGPef2tM%2FnYdCoqO9D1VE%2BU%3D | US | — | — | whitelisted |
2808 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | binary | 471 b | whitelisted |
2808 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | binary | 1.47 Kb | whitelisted |
2808 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAhflMAthXvozBT%2FU%2B2iPio%3D | US | der | 471 b | whitelisted |
2808 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSnxLiz3Fu1WB6n1%2FE6xWn1b0jXiQQUdIWAwGbH3zfez70pN6oDHb7tzRcCEAbCsehAv%2FkAxBfkV5KvfLI%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2808 | iexplore.exe | 95.140.236.128:80 | ctldl.windowsupdate.com | LLNW | US | malicious |
2808 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2808 | iexplore.exe | 52.84.151.30:443 | us04st3.zoom.us | AMAZON-02 | US | suspicious |
2808 | iexplore.exe | 34.98.108.207:443 | cdn.solvvy.com | GOOGLE | US | unknown |
2640 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2604 | iexplore.exe | 184.86.251.28:443 | www.bing.com | Akamai International B.V. | DE | suspicious |
2808 | iexplore.exe | 104.18.28.38:443 | geolocation.onetrust.com | CLOUDFLARENET | — | unknown |
1644 | Zoom_cm_fo42lnktZ9vvrZo4_mUGtl+ErSxWZtR-rPp7SHJUrFfY0cuNzTh8Y@eKYBFOuaLt6NxAwe_kdd06bf3d34c79a86_.exe | 170.114.52.4:443 | — | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
cdn.solvvy.com |
| shared |
us04st3.zoom.us |
| whitelisted |
st1.zoom.us |
| whitelisted |
log-gateway.zoom.us |
| unknown |
cdn.cookielaw.org |
| whitelisted |
geolocation.onetrust.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Installer.exe | [ProductPathHelper::RecursiveRemoveDirA] Path is: |
Installer.exe | C:\Users\admin\AppData\Roaming\Zoom\zoom_install_src |
Installer.exe | |
Installer.exe | [ProductPathHelper::RecursiveRemoveDirA] Path is: |
Installer.exe | |
Installer.exe | C:\Users\admin\AppData\Roaming\Zoom\tmp_bin |
Installer.exe | C:\Users\admin\AppData\Roaming\Zoom\tmp_uninstall |
Installer.exe | |
Installer.exe | [ProductPathHelper::RecursiveRemoveDirA] Path is: |
Installer.exe | [ProductPathHelper::RecursiveRemoveDirA] Path is: |