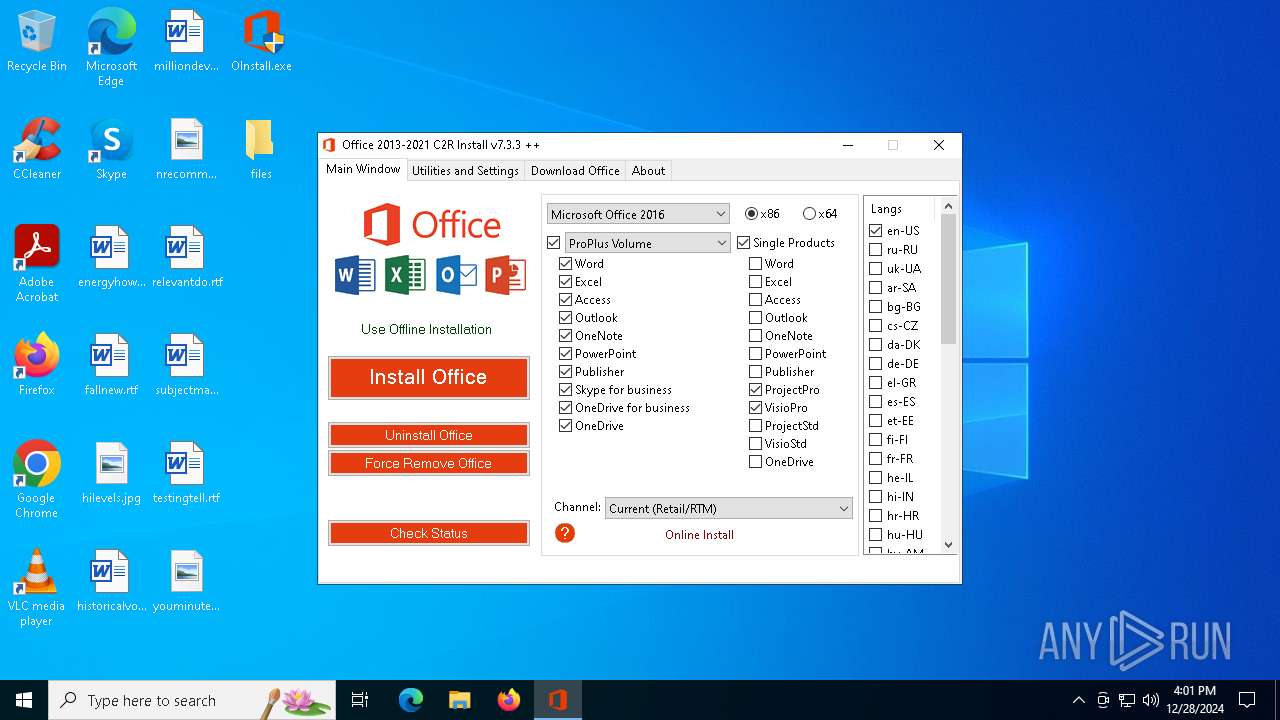
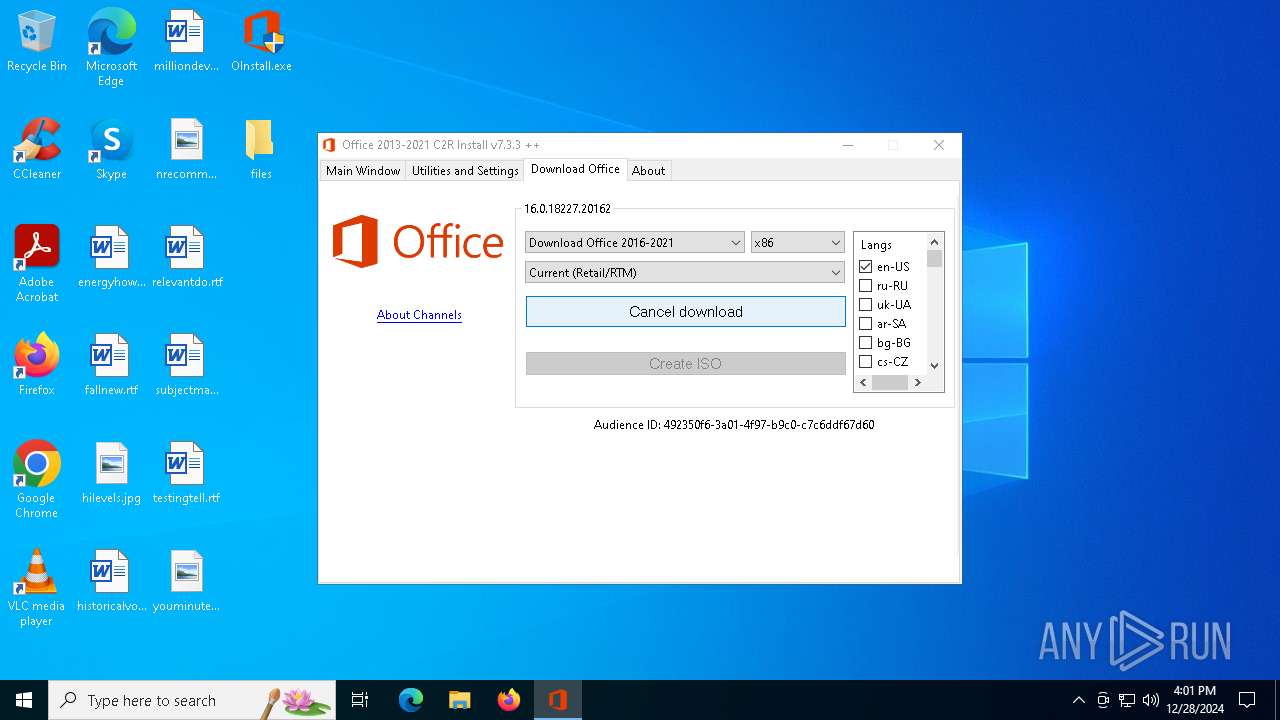
| File name: | OInstall.exe |
| Full analysis: | https://app.any.run/tasks/87b85cfc-8cc4-454d-9301-9a1b4f762843 |
| Verdict: | Malicious activity |
| Analysis date: | December 28, 2024, 16:01:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | EBC58647462AD9C76395EF451064D115 |
| SHA1: | 14E470812F13B278B2694A4CEC5737A39784E9DD |
| SHA256: | 414155BF11893EC64BA0F4FFB7DE92885090845A0761CF8F6743462AA5991D5E |
| SSDEEP: | 196608:2ZnMGjZsDEsCaYsGEHy61bgUhufRswPU2/V8Gd83/PALDP0PiaQxhwf+9zYul28S:WnjZhsCOU6ZgfPPPuGdnv0fzfoDYtB |
MALICIOUS
Executing a file with an untrusted certificate
- OInstall.exe (PID: 6640)
Uses WMIC.EXE to add exclusions to the Windows Defender
- cmd.exe (PID: 6876)
- cmd.exe (PID: 6692)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 6188)
- powershell.exe (PID: 5000)
SUSPICIOUS
Found strings related to reading or modifying Windows Defender settings
- OInstall.exe (PID: 6640)
Starts CMD.EXE for commands execution
- OInstall.exe (PID: 6640)
Process drops legitimate windows executable
- OInstall.exe (PID: 6640)
- files.dat (PID: 7056)
Drops 7-zip archiver for unpacking
- OInstall.exe (PID: 6640)
Executable content was dropped or overwritten
- OInstall.exe (PID: 6640)
- files.dat (PID: 7056)
Starts application with an unusual extension
- cmd.exe (PID: 7000)
The process drops C-runtime libraries
- files.dat (PID: 7056)
Starts POWERSHELL.EXE for commands execution
- OInstall.exe (PID: 6640)
Unpacks CAB file
- expand.exe (PID: 4704)
- expand.exe (PID: 5036)
Uses TASKKILL.EXE to kill process
- OInstall.exe (PID: 6640)
Probably download files using WebClient
- OInstall.exe (PID: 6640)
INFO
Reads Environment values
- OInstall.exe (PID: 6640)
Checks supported languages
- OInstall.exe (PID: 6640)
- files.dat (PID: 7056)
- expand.exe (PID: 4704)
- expand.exe (PID: 5036)
- aria2_oinstall.exe (PID: 5316)
- extrac32.exe (PID: 6872)
Reads the computer name
- OInstall.exe (PID: 6640)
- aria2_oinstall.exe (PID: 5316)
- extrac32.exe (PID: 6872)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6772)
- WMIC.exe (PID: 6940)
The sample compiled with english language support
- OInstall.exe (PID: 6640)
- files.dat (PID: 7056)
Checks proxy server information
- powershell.exe (PID: 6188)
- powershell.exe (PID: 5000)
UPX packer has been detected
- OInstall.exe (PID: 6640)
Disables trace logs
- powershell.exe (PID: 6188)
- powershell.exe (PID: 5000)
Create files in a temporary directory
- expand.exe (PID: 4704)
- expand.exe (PID: 5036)
Reads the machine GUID from the registry
- expand.exe (PID: 4704)
- expand.exe (PID: 5036)
- aria2_oinstall.exe (PID: 5316)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (76) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.6) |
| .exe | | | Generic Win/DOS Executable (5.6) |
| .exe | | | DOS Executable Generic (5.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:08 08:23:35+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 11350016 |
| InitializedDataSize: | 90112 |
| UninitializedDataSize: | 11218944 |
| EntryPoint: | 0x1585eb0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.3.3.0 |
| ProductVersionNumber: | 7.3.3.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| ProductName: | Office 2013-2021 C2R Install |
| FileDescription: | Office 2013-2021 C2R Install |
Total processes
149
Monitored processes
30
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2324 | "taskkill.exe" /t /f /IM aria2_oinstall.exe | C:\Windows\System32\taskkill.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2744 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3208 | "powershell" -command "& { Get-Content C:\Users\admin\AppData\Local\Temp\over833005\VersionDescriptor.xml | Set-Content -Encoding ASCII v32.txt } | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4704 | "expand" v32.cab -F:VersionDescriptor.xml C:\Users\admin\AppData\Local\Temp\over833005 | C:\Windows\SysWOW64\expand.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: LZ Expansion Utility Exit code: 0 Version: 5.00 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5000 | "powershell" -command "& { (New-Object Net.WebClient).DownloadFile('http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32.cab', 'C:\Users\admin\AppData\Local\Temp\over112296\v32.cab') }" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | OInstall.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5036 | "expand" v32.cab -F:VersionDescriptor.xml C:\Users\admin\AppData\Local\Temp\over112296 | C:\Windows\SysWOW64\expand.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: LZ Expansion Utility Exit code: 0 Version: 5.00 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5316 | "C:\Users\admin\Desktop\files\aria2_oinstall.exe" --console-log-level=info --check-certificate=false -x16 -s16 -j1 -c -R -Ztrue -dOffice\Data http://officecdn.microsoft.com.edgesuite.net/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32.cab | C:\Users\admin\Desktop\files\aria2_oinstall.exe | OInstall.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 5536 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | expand.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5872 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
19 875
Read events
19 859
Write events
16
Delete events
0
Modification events
| (PID) Process: | (6188) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6188) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6188) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6188) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6188) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6188) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (6188) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (6188) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6188) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6188) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
7
Suspicious files
6
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7056 | files.dat | C:\Users\admin\Desktop\files\x64\cleanospp.exe | executable | |
MD5:162AB955CB2F002A73C1530AA796477F | SHA256:5CE462E5F34065FC878362BA58617FAB28C22D631B9D836DDDCF43FB1AD4DE6E | |||
| 6188 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qiovdwew.h4k.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6188 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ovjesxob.hol.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6188 | powershell.exe | C:\Users\admin\AppData\Local\Temp\over833005\v32.cab | compressed | |
MD5:6B195A82741D9857C7C3022CCE25FA77 | SHA256:8F700A6D88A17B83938D9A6B23A08CBA973A9185C7BD844B21BA039BBFEE094B | |||
| 7056 | files.dat | C:\Users\admin\Desktop\files\x64\msvcr100.dll | executable | |
MD5:DF3CA8D16BDED6A54977B30E66864D33 | SHA256:1D1A1AE540BA132F998D60D3622F0297B6E86AE399332C3B47462D7C0F560A36 | |||
| 7056 | files.dat | C:\Users\admin\Desktop\files\x86\cleanospp.exe | executable | |
MD5:5FD363D52D04AC200CD24F3BCC903200 | SHA256:3FDEFE2AD092A9A7FE0EDF0AC4DC2DE7E5B9CE6A0804F6511C06564194966CF9 | |||
| 6640 | OInstall.exe | C:\Users\admin\Desktop\files\files.dat | executable | |
MD5:55D21B2C272A5D6B9F54FA9ED82BF9EB | SHA256:7A1C82E264258470D14CA345EA1A9B6FC34FA19B393A92077A01BE5F1AD08F47 | |||
| 6640 | OInstall.exe | C:\Users\admin\Desktop\files\setup.exe | executable | |
MD5:072A2EFEA576956E465AFF2492A1C7F4 | SHA256:EE3875ABD5D49A1891C8818820F61A1E5D0382DF37B5A5B72E175B2B6C70A9C2 | |||
| 6640 | OInstall.exe | C:\Users\admin\Desktop\files\Configure.xml | text | |
MD5:AC6BE84084E31DBB0E08D188B6C86EC8 | SHA256:1879F7DE537C2AA70292C61EBEF9C6477D36E25B2E6A639E318B159E0A22B0FC | |||
| 3208 | powershell.exe | C:\Users\admin\AppData\Local\Temp\over833005\v32.txt | xml | |
MD5:5C7EA307674247A2443B5E2E3A180616 | SHA256:731C40F93AB2C713287C1C362D339AC2EA7DA25EBD77331C3EAC96C3684F74D1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
23
DNS requests
9
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2356 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2356 | svchost.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6188 | powershell.exe | GET | 200 | 2.16.168.114:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32.cab | unknown | — | — | whitelisted |
5000 | powershell.exe | GET | 200 | 2.16.168.114:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32.cab | unknown | — | — | whitelisted |
5316 | aria2_oinstall.exe | GET | 200 | 2.22.50.135:80 | http://officecdn.microsoft.com.edgesuite.net/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32.cab | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2356 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.21.110.146:443 | www.bing.com | AKAMAI-AS | DE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2356 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2356 | svchost.exe | 23.37.237.227:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3976 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6188 | powershell.exe | 2.16.168.114:80 | officecdn.microsoft.com | Akamai International B.V. | RU | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officecdn.microsoft.com |
| whitelisted |
officecdn.microsoft.com.edgesuite.net |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5316 | aria2_oinstall.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |