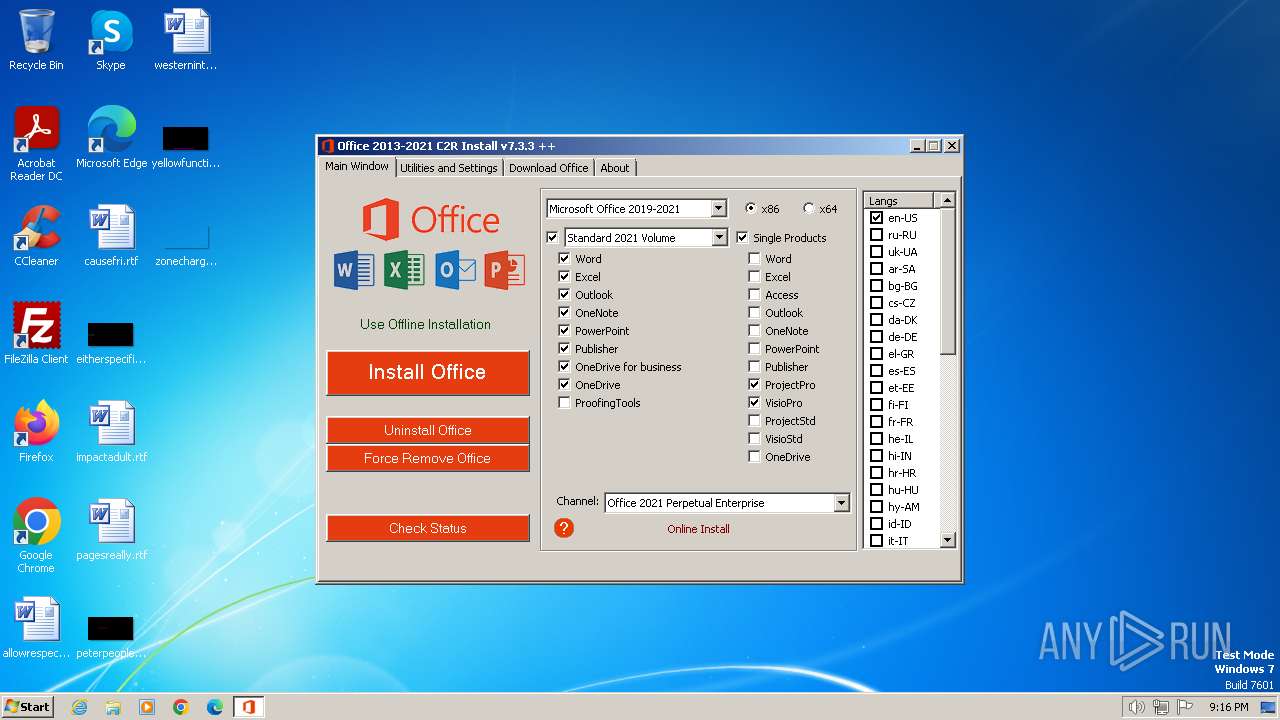
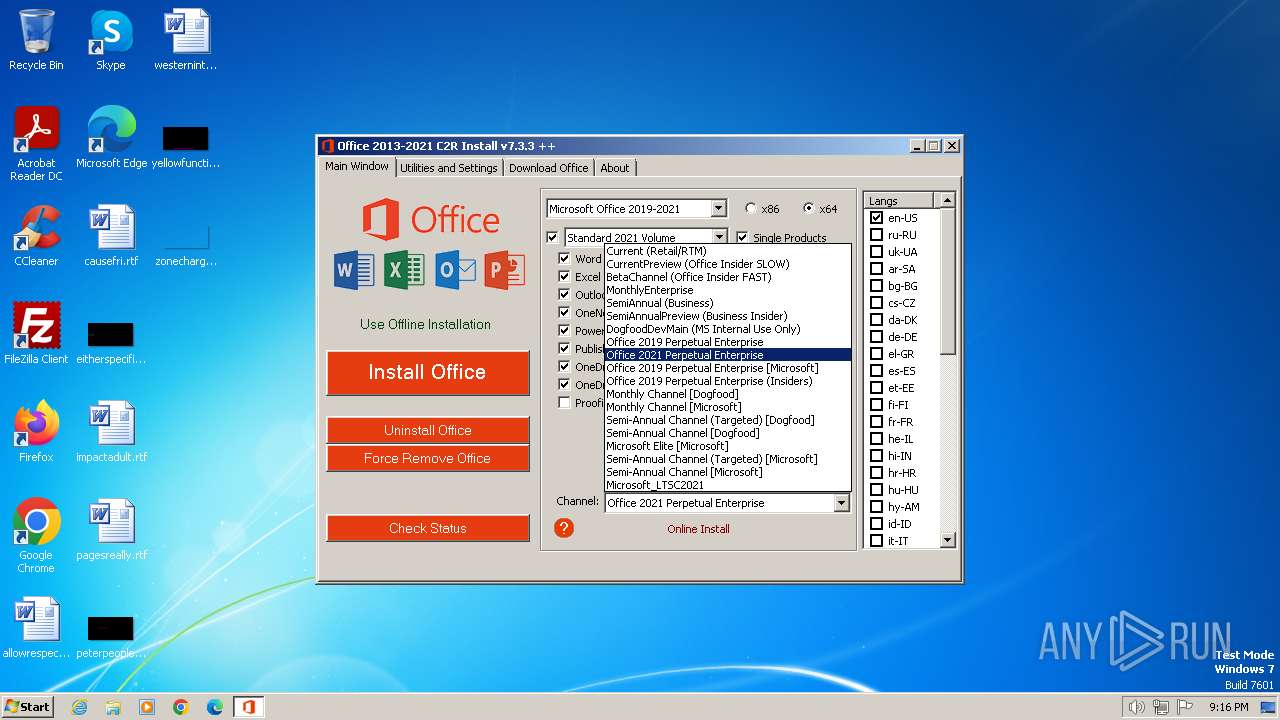
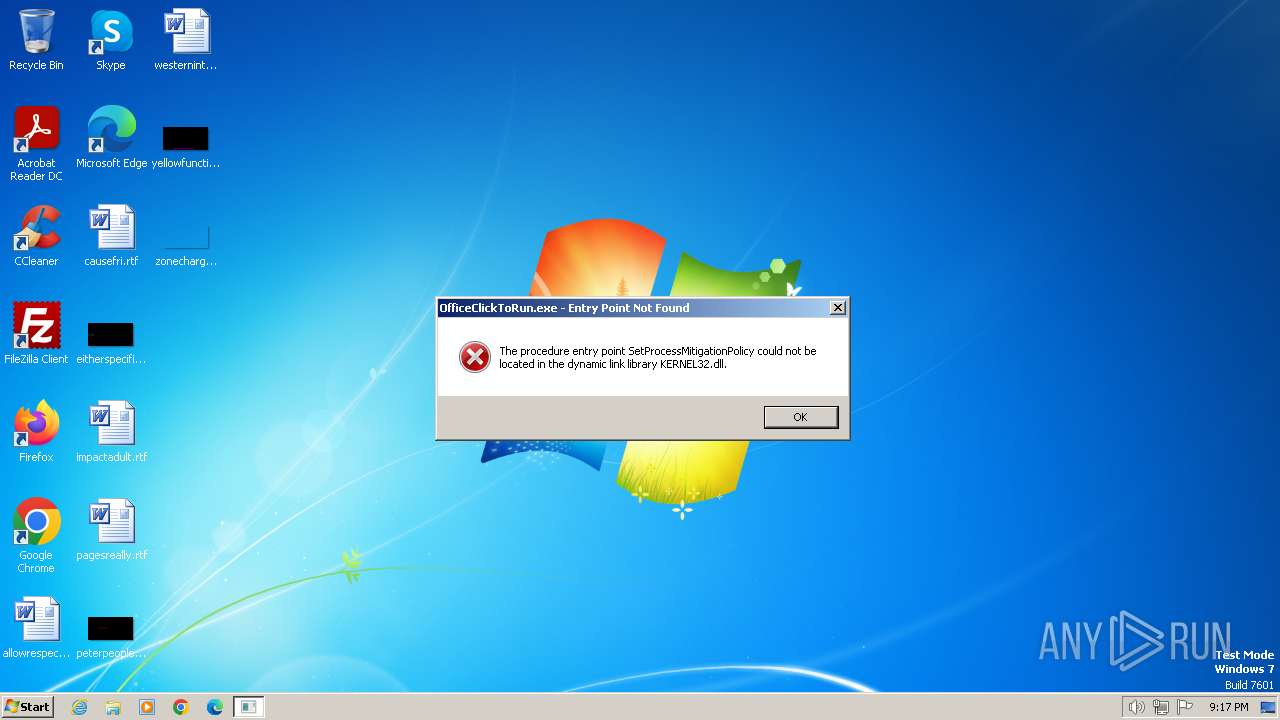
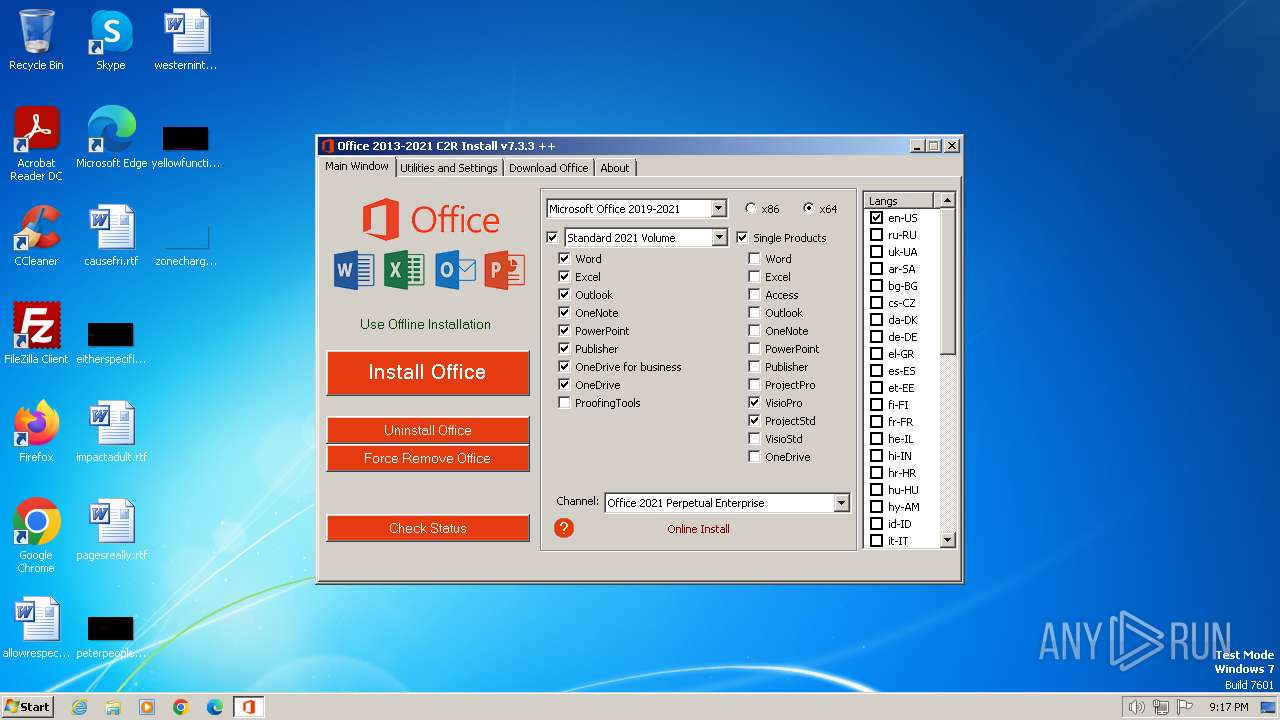
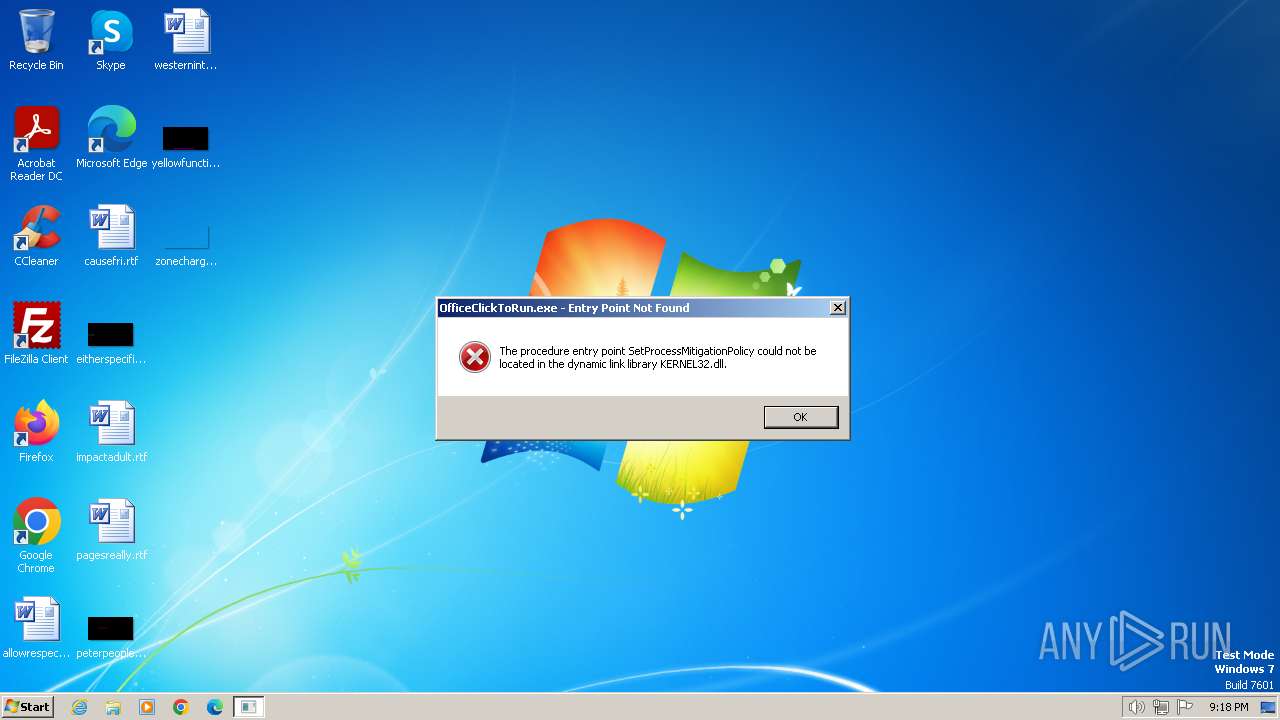
| File name: | OInstall.exe |
| Full analysis: | https://app.any.run/tasks/0c6e6125-e74b-4471-9daf-1b1899d9f9f7 |
| Verdict: | Malicious activity |
| Analysis date: | March 09, 2024, 21:15:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | EBC58647462AD9C76395EF451064D115 |
| SHA1: | 14E470812F13B278B2694A4CEC5737A39784E9DD |
| SHA256: | 414155BF11893EC64BA0F4FFB7DE92885090845A0761CF8F6743462AA5991D5E |
| SSDEEP: | 196608:2ZnMGjZsDEsCaYsGEHy61bgUhufRswPU2/V8Gd83/PALDP0PiaQxhwf+9zYul28S:WnjZhsCOU6ZgfPPPuGdnv0fzfoDYtB |
MALICIOUS
Drops the executable file immediately after the start
- OInstall.exe (PID: 2036)
- files.dat (PID: 1876)
SUSPICIOUS
Process drops legitimate windows executable
- OInstall.exe (PID: 2036)
- files.dat (PID: 1876)
- expand.exe (PID: 568)
- expand.exe (PID: 3228)
- expand.exe (PID: 1584)
Executable content was dropped or overwritten
- OInstall.exe (PID: 2036)
- files.dat (PID: 1876)
- expand.exe (PID: 568)
- expand.exe (PID: 3228)
- expand.exe (PID: 1584)
Drops 7-zip archiver for unpacking
- OInstall.exe (PID: 2036)
The executable file from the user directory is run by the CMD process
- files.dat (PID: 1876)
Starts application with an unusual extension
- cmd.exe (PID: 2840)
Starts CMD.EXE for commands execution
- OInstall.exe (PID: 2036)
The process drops C-runtime libraries
- files.dat (PID: 1876)
- expand.exe (PID: 568)
- expand.exe (PID: 3228)
- expand.exe (PID: 1584)
Uses REG/REGEDIT.EXE to modify registry
- OInstall.exe (PID: 2036)
- cmd.exe (PID: 2640)
- cmd.exe (PID: 2068)
- cmd.exe (PID: 2936)
- cmd.exe (PID: 3520)
- cmd.exe (PID: 2568)
- cmd.exe (PID: 2300)
- cmd.exe (PID: 1928)
- cmd.exe (PID: 2152)
- cmd.exe (PID: 2908)
- cmd.exe (PID: 2184)
Probably download files using WebClient
- OInstall.exe (PID: 2036)
Starts POWERSHELL.EXE for commands execution
- OInstall.exe (PID: 2036)
Reads the Internet Settings
- powershell.exe (PID: 1900)
- powershell.exe (PID: 2972)
- powershell.exe (PID: 2672)
- powershell.exe (PID: 3112)
- powershell.exe (PID: 3284)
- powershell.exe (PID: 2356)
- powershell.exe (PID: 3836)
- powershell.exe (PID: 1844)
- powershell.exe (PID: 2560)
The Powershell connects to the Internet
- powershell.exe (PID: 2672)
- powershell.exe (PID: 1900)
- powershell.exe (PID: 2972)
- powershell.exe (PID: 3112)
- powershell.exe (PID: 3284)
- powershell.exe (PID: 2356)
- powershell.exe (PID: 1844)
- powershell.exe (PID: 3836)
- powershell.exe (PID: 2560)
Unusual connection from system programs
- powershell.exe (PID: 1900)
- powershell.exe (PID: 2672)
- powershell.exe (PID: 2972)
- powershell.exe (PID: 3112)
- powershell.exe (PID: 3284)
- powershell.exe (PID: 2356)
- powershell.exe (PID: 1844)
- powershell.exe (PID: 3836)
- powershell.exe (PID: 2560)
Starts SC.EXE for service management
- cmd.exe (PID: 3440)
- cmd.exe (PID: 1540)
Uses TASKKILL.EXE to kill process
- OInstall.exe (PID: 2036)
INFO
Checks supported languages
- OInstall.exe (PID: 2036)
- files.dat (PID: 1876)
Reads Environment values
- OInstall.exe (PID: 2036)
Reads the computer name
- OInstall.exe (PID: 2036)
Create files in a temporary directory
- files.dat (PID: 1876)
- OInstall.exe (PID: 2036)
- expand.exe (PID: 2184)
- expand.exe (PID: 3456)
- expand.exe (PID: 3680)
Creates files in the program directory
- OInstall.exe (PID: 2036)
- expand.exe (PID: 568)
- expand.exe (PID: 2172)
- expand.exe (PID: 2976)
- expand.exe (PID: 3228)
- expand.exe (PID: 1584)
- expand.exe (PID: 3272)
Reads Microsoft Office registry keys
- reg.exe (PID: 3504)
- reg.exe (PID: 948)
- reg.exe (PID: 1796)
- reg.exe (PID: 2396)
- reg.exe (PID: 3312)
- reg.exe (PID: 1496)
- reg.exe (PID: 2408)
- reg.exe (PID: 3516)
- reg.exe (PID: 1352)
- OInstall.exe (PID: 2036)
- reg.exe (PID: 2072)
Drops the executable file immediately after the start
- expand.exe (PID: 568)
- expand.exe (PID: 3228)
- expand.exe (PID: 1584)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (76) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.6) |
| .exe | | | Generic Win/DOS Executable (5.6) |
| .exe | | | DOS Executable Generic (5.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:08 08:23:35+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 11350016 |
| InitializedDataSize: | 90112 |
| UninitializedDataSize: | 11218944 |
| EntryPoint: | 0x1585eb0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.3.3.0 |
| ProductVersionNumber: | 7.3.3.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
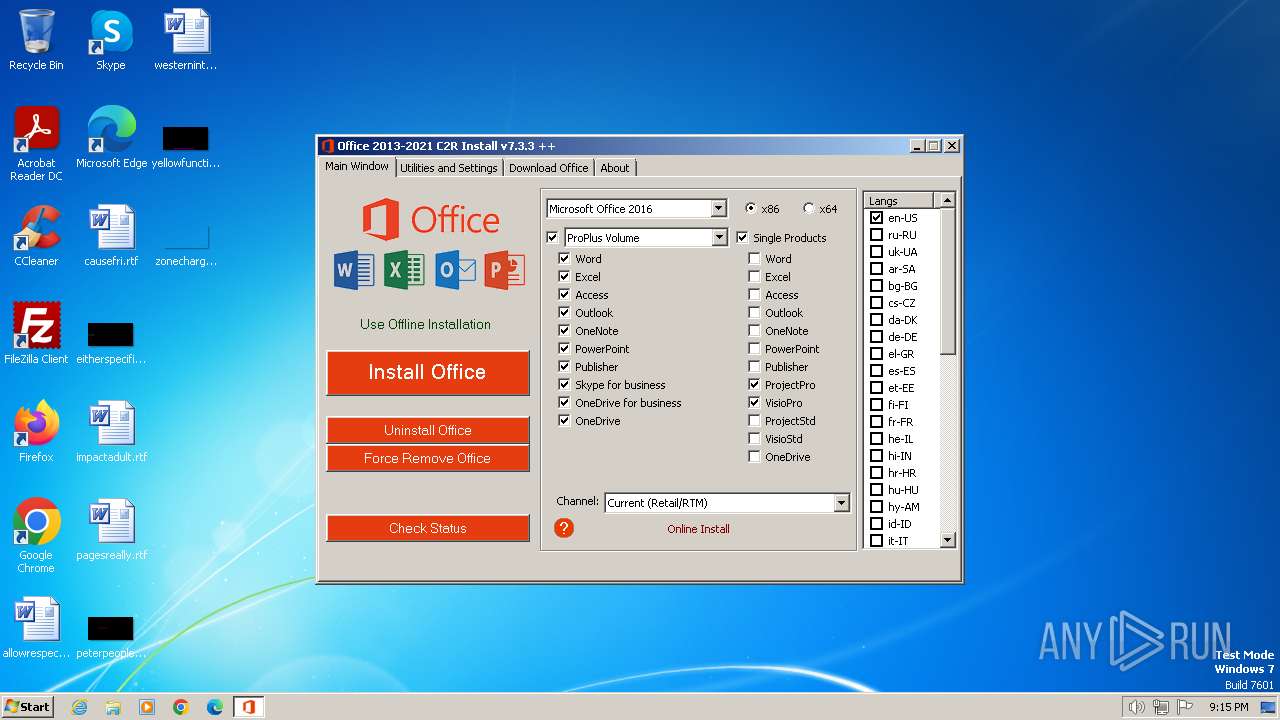
| ProductName: | Office 2013-2021 C2R Install |
| FileDescription: | Office 2013-2021 C2R Install |
Total processes
143
Monitored processes
61
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
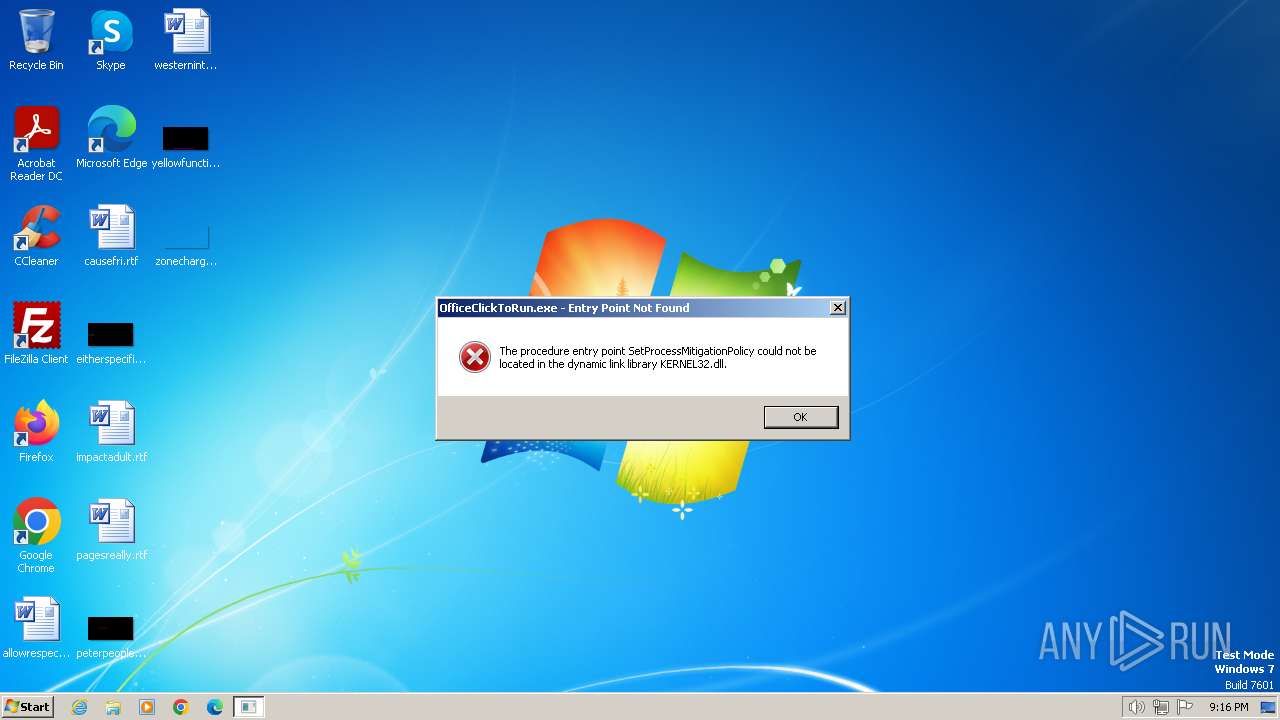
| 448 | "C:\Program Files\Common Files\microsoft shared\ClickToRun\OfficeClickToRun.exe" deliverymechanism=5030841d-c919-4594-8d2d-84ae4f96e58e platform=x86 productreleaseid=none culture=en-us defaultplatform=False lcid=1033 b= storeid= forceupgrade=True piniconstotaskbar=False pidkeys=FTNWT-C6WBT-8HMGF-K9PRX-QV9H8,KNH8D-FGHT4-T8RK3-CTDYJ-K2HT4,KDX7X-BNVR8-TXXGX-4Q7Y8-78VT3 forceappshutdown=True autoactivate=1 productstoadd=Standard2021Volume.16_en-us_x-none|ProjectPro2021Volume.16_en-us_x-none|VisioPro2021Volume.16_en-us_x-none scenario=unknown updatesenabled.16=True acceptalleulas.16=True cdnbaseurl.16=http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e version.16=16.0.14332.20637 mediatype.16=CDN baseurl.16=http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e sourcetype.16=CDN displaylevel=True uninstallpreviousversion=True Standard2021Volume.excludedapps.16=onedrive,teams ProjectPro2021Volume.excludedapps.16=onedrive,teams VisioPro2021Volume.excludedapps.16=onedrive,teams | C:\Program Files\Common Files\microsoft shared\ClickToRun\OfficeClickToRun.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office Click-to-Run (SxS) Exit code: 3221225785 Version: 16.0.14332.20631 Modules
| |||||||||||||||
| 568 | "expand" i320.cab -F:* "C:\Program Files\Common Files\microsoft Shared\ClickToRun" | C:\Windows\System32\expand.exe | OInstall.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: LZ Expansion Utility Exit code: 0 Version: 6.1.7601.24535 (win7sp1_ldr_escrow.191105-1059) Modules
| |||||||||||||||
| 948 | reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun\Configuration" /f /v "UpdateChannelChanged" /t REG_SZ /d True | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1352 | reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun\Configuration" /f /v "UpdateUrl" /t REG_SZ /d http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1496 | reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun\Configuration" /f /v "CDNBaseUrl" /t REG_SZ /d http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1540 | "C:\Windows\System32\cmd.exe" /c sc.exe stop ClickToRunSvc | C:\Windows\System32\cmd.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1060 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1584 | "expand" i320.cab -F:* "C:\Program Files\Common Files\microsoft Shared\ClickToRun" | C:\Windows\System32\expand.exe | OInstall.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: LZ Expansion Utility Exit code: 0 Version: 6.1.7601.24535 (win7sp1_ldr_escrow.191105-1059) Modules
| |||||||||||||||
| 1796 | reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun\Configuration" /f /v "AudienceId" /t REG_SZ /d 5030841d-c919-4594-8d2d-84ae4f96e58e | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1844 | "powershell" -command "& { (New-Object Net.WebClient).DownloadFile('http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/v32.cab', 'C:\Users\admin\AppData\Local\Temp\over718241\v32.cab') }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | OInstall.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1876 | files.dat -y -pkmsauto | C:\Users\admin\AppData\Local\Temp\files\files.dat | cmd.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7z Console SFX Exit code: 0 Version: 9.20 Modules
| |||||||||||||||
Total events
25 539
Read events
25 524
Write events
15
Delete events
0
Modification events
| (PID) Process: | (2036) OInstall.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MediaResources\DirectSound\Speaker Configuration |
| Operation: | write | Name: | Speaker Configuration |
Value: 4 | |||
| (PID) Process: | (2292) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Office\16.0\Common\OfficeUpdate |
| Operation: | write | Name: | UpdateBranch |
Value: PerpetualVL2021 | |||
| (PID) Process: | (1796) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun\Configuration |
| Operation: | write | Name: | AudienceId |
Value: 5030841d-c919-4594-8d2d-84ae4f96e58e | |||
| (PID) Process: | (2396) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun\Configuration |
| Operation: | write | Name: | CDNBaseUrl |
Value: http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e | |||
| (PID) Process: | (3504) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun\Configuration |
| Operation: | write | Name: | UpdateChannel |
Value: http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e | |||
| (PID) Process: | (948) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun\Configuration |
| Operation: | write | Name: | UpdateChannelChanged |
Value: True | |||
| (PID) Process: | (3312) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun\Configuration |
| Operation: | write | Name: | UpdateUrl |
Value: http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e | |||
| (PID) Process: | (3132) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Office\16.0\Common\OfficeUpdate |
| Operation: | write | Name: | UpdateBranch |
Value: PerpetualVL2021 | |||
| (PID) Process: | (2408) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun\Configuration |
| Operation: | write | Name: | AudienceId |
Value: 5030841d-c919-4594-8d2d-84ae4f96e58e | |||
| (PID) Process: | (1496) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun\Configuration |
| Operation: | write | Name: | CDNBaseUrl |
Value: http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e | |||
Executable files
642
Suspicious files
36
Text files
80
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2036 | OInstall.exe | C:\Users\admin\AppData\Local\Temp\files\setup.exe | executable | |
MD5:072A2EFEA576956E465AFF2492A1C7F4 | SHA256:EE3875ABD5D49A1891C8818820F61A1E5D0382DF37B5A5B72E175B2B6C70A9C2 | |||
| 1900 | powershell.exe | C:\Users\admin\AppData\Local\Temp\over947638\i320.cab | — | |
MD5:— | SHA256:— | |||
| 1876 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x86\msvcr100.dll | executable | |
MD5:BF38660A9125935658CFA3E53FDC7D65 | SHA256:60C06E0FA4449314DA3A0A87C1A9D9577DF99226F943637E06F61188E5862EFA | |||
| 1876 | files.dat | C:\Users\admin\AppData\Local\Temp\files\Uninstall.xml | text | |
MD5:364F86F97324EA82FE0D142CD01CF6DD | SHA256:09D5B42140BAB13165BA97FBD0E77792304C3C93555BE02C3DCE21A7A69C66DD | |||
| 1876 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x64\cleanospp.exe | executable | |
MD5:162AB955CB2F002A73C1530AA796477F | SHA256:5CE462E5F34065FC878362BA58617FAB28C22D631B9D836DDDCF43FB1AD4DE6E | |||
| 2036 | OInstall.exe | C:\Users\admin\AppData\Local\Temp\files\files.dat | executable | |
MD5:55D21B2C272A5D6B9F54FA9ED82BF9EB | SHA256:7A1C82E264258470D14CA345EA1A9B6FC34FA19B393A92077A01BE5F1AD08F47 | |||
| 2672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\zvktkcxz.ogw.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2184 | expand.exe | C:\Windows\Logs\DPX\setupact.log | text | |
MD5:491ED09B7D09382B2C70587D96CB9C6D | SHA256:16A2EA2CD610DD441E014B433341D329A6C5A4ED77DAD3EEACB45B81BC870935 | |||
| 2672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\over947638\v32.cab | compressed | |
MD5:1AD6AF824B8037B08AF260E37C207D74 | SHA256:9C90643BC7B4530767249C423F64D12E3CD8EFF5ACC1E8678139E18CDC219072 | |||
| 2184 | expand.exe | C:\Users\admin\AppData\Local\Temp\over947638\VersionDescriptor.xml | xml | |
MD5:5D5045E8360E54A97C3AD3B6A4EA9689 | SHA256:0038B52FA587E4534519FD491FFF160999D1C6942B12805D89789759E1C04BB3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
13
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1900 | powershell.exe | GET | 200 | 178.79.242.181:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20637/i320.cab | unknown | compressed | 23.5 Mb | unknown |
2672 | powershell.exe | GET | 200 | 178.79.242.181:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/v32.cab | unknown | compressed | 10.8 Kb | unknown |
2972 | powershell.exe | GET | 200 | 178.79.242.181:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20637/i321033.cab | unknown | compressed | 9.84 Kb | unknown |
3112 | powershell.exe | GET | 200 | 41.63.96.130:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/v32.cab | unknown | compressed | 10.8 Kb | unknown |
3284 | powershell.exe | GET | 200 | 41.63.96.130:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20637/i320.cab | unknown | compressed | 23.5 Mb | unknown |
1844 | powershell.exe | GET | 200 | 178.79.242.16:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/v32.cab | unknown | compressed | 10.8 Kb | unknown |
3836 | powershell.exe | GET | 200 | 178.79.242.16:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20637/i320.cab | unknown | compressed | 23.5 Mb | unknown |
2560 | powershell.exe | GET | 200 | 178.79.242.16:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20637/i321033.cab | unknown | compressed | 9.84 Kb | unknown |
2356 | powershell.exe | GET | 200 | 41.63.96.130:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20637/i321033.cab | unknown | compressed | 9.84 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2672 | powershell.exe | 178.79.242.181:80 | officecdn.microsoft.com | LLNW | DE | unknown |
1900 | powershell.exe | 178.79.242.181:80 | officecdn.microsoft.com | LLNW | DE | unknown |
2972 | powershell.exe | 178.79.242.181:80 | officecdn.microsoft.com | LLNW | DE | unknown |
3112 | powershell.exe | 41.63.96.130:80 | officecdn.microsoft.com | LLNW | ZA | unknown |
3284 | powershell.exe | 41.63.96.130:80 | officecdn.microsoft.com | LLNW | ZA | unknown |
2356 | powershell.exe | 41.63.96.130:80 | officecdn.microsoft.com | LLNW | ZA | unknown |
1844 | powershell.exe | 178.79.242.16:80 | officecdn.microsoft.com | LLNW | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officecdn.microsoft.com |
| whitelisted |