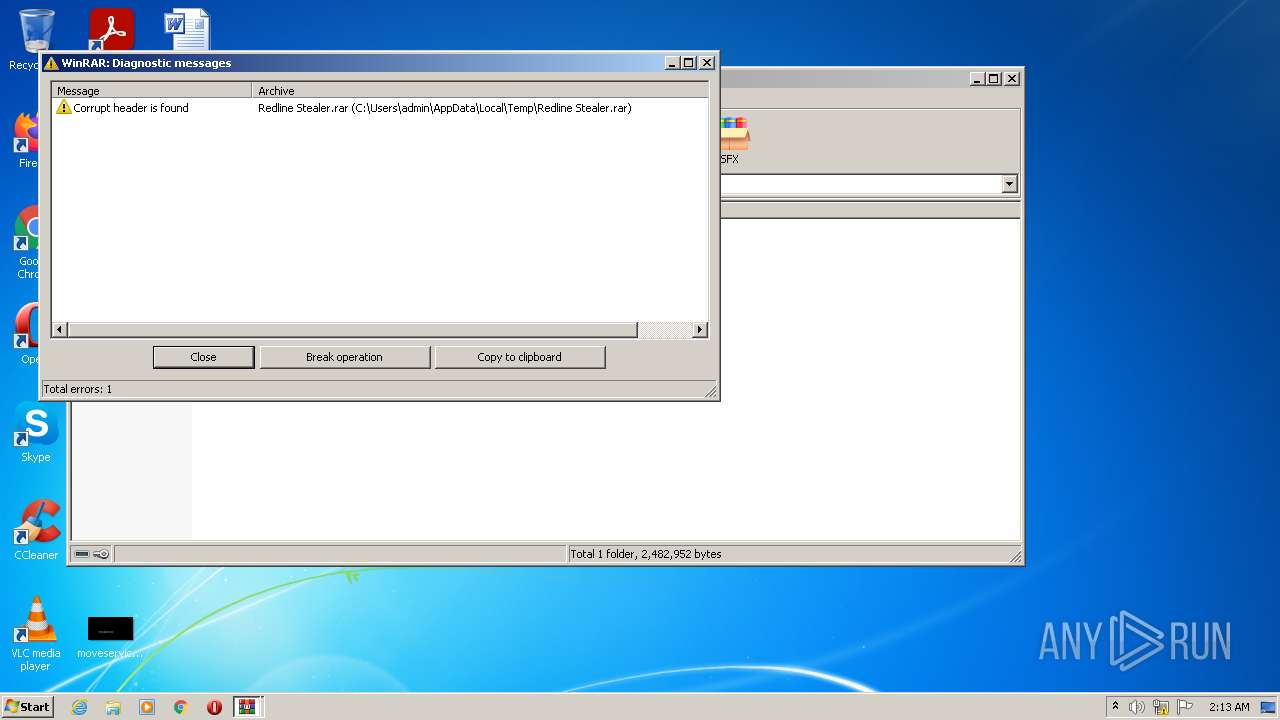
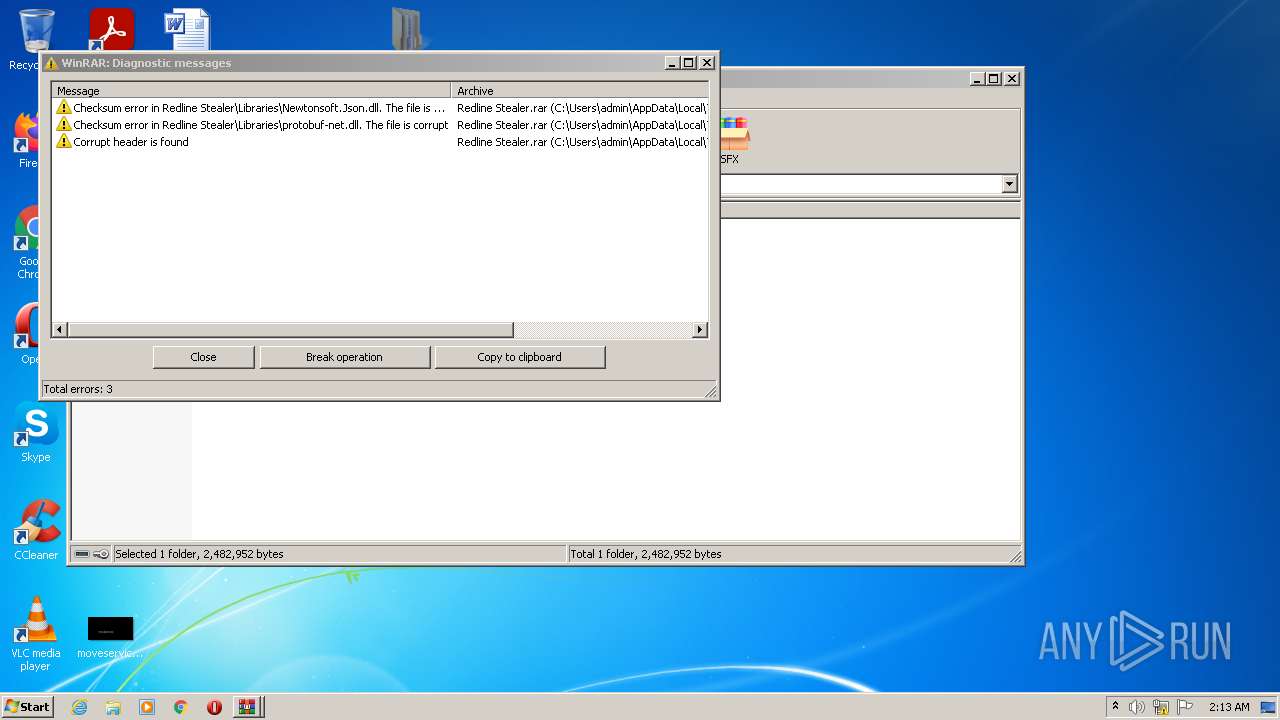
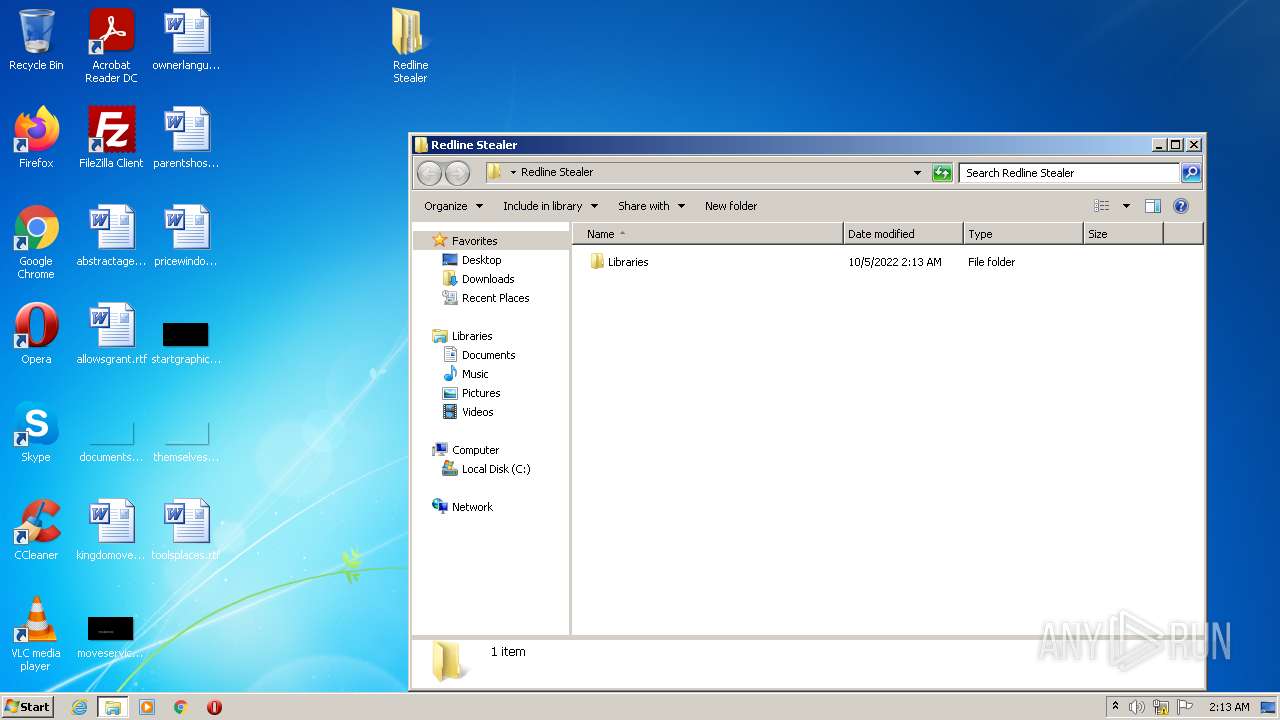
| File name: | Redline Stealer.rar |
| Full analysis: | https://app.any.run/tasks/298d534d-77c9-41fa-a68c-5a5cd68898f9 |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2022, 01:13:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 4B76841752D06F1B75311A83DCEDF8CF |
| SHA1: | 81DA0FB3790FBBF91F1A8C31F2D9AE4B02731713 |
| SHA256: | 414029596093D762DCE3F3FDF32E666E5A663447AFA11ACB7B3683F5AACE1CD9 |
| SSDEEP: | 24576:0Tr4jmzrCmbfYOM4+v/GT+Q75cCJLXR3U7jQ0/PMx2xDex7Ou2l3pXw42:03PZM4+v/onGCRh3un7ehyl3tR2 |
MALICIOUS
Drops executable file immediately after starts
- WinRAR.exe (PID: 3164)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 528)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3164)
Checks supported languages
- WinRAR.exe (PID: 3164)
Reads the computer name
- WinRAR.exe (PID: 3164)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3164)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
34
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 528 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 3164 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Redline Stealer.rar" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
1 762
Read events
1 741
Write events
21
Delete events
0
Modification events
| (PID) Process: | (3164) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3164) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3164) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3164) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3164) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3164) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Redline Stealer.rar | |||
| (PID) Process: | (3164) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3164) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3164) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3164) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
8
Suspicious files
4
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3164.8352\Redline Stealer\Libraries\Mono.Cecil.Mdb.pdb | binary | |
MD5:0BA762B6B5FBDA000E51D66722A3BB2C | SHA256:D18EB89421D50F079291B78783408CEE4BAB6810E4C5A4B191849265BDD5BA7C | |||
| 3164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3164.8352\Redline Stealer\Libraries\GuiLib.dll | executable | |
MD5:EAF9C55793CD26F133708714ED3A5397 | SHA256:87CFC70BEC2D2A37BCD5D46F9E6F0051F82E015FF96E8F2BC2D81B85F2632F15 | |||
| 3164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3164.8352\Redline Stealer\Libraries\Mono.Cecil.dll | executable | |
MD5:7546ACEBC5A5213DEE2A5ED18D7EBC6C | SHA256:7744C9C84C28033BC3606F4DFCE2ADCD6F632E2BE7827893C3E2257100F1CF9E | |||
| 3164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3164.8352\Redline Stealer\Libraries\Mono.Cecil.Rocks.dll | executable | |
MD5:C8F36848CE8F13084B355C934FC91746 | SHA256:A08C040912DF2A3C823ADE85D62239D56ABAA8F788A2684FB9D33961922687C7 | |||
| 3164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3164.8352\Redline Stealer\Libraries\Mono.Cecil.Rocks.pdb | binary | |
MD5:17E3CCB3A96BE6D93CA3C286CA3B93DC | SHA256:CA54D2395697EFC3163016BBC2BB1E91B13D454B9A5A3EE9A4304012F012E5EB | |||
| 3164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3164.8352\Redline Stealer\Libraries\builder.exe | executable | |
MD5:DE6F68CDF350FCE9BE13803D84BE98C4 | SHA256:51BBC69942823B84C2A1F0EFDB9D63FB04612B223E86AF8A83B4B307DD15CD24 | |||
| 3164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3164.8352\Redline Stealer\Libraries\Mono.Cecil.Pdb.dll | executable | |
MD5:6CD3ED3DB95D4671B866411DB4950853 | SHA256:D67EBD49241041E6B6191703A90D89E68D4465ADCE02C595218B867DF34581A3 | |||
| 3164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3164.8352\Redline Stealer\Libraries\Bunifu_UI_v1.52.dll | executable | |
MD5:5ECA94D909F1BA4C5F3E35AC65A49076 | SHA256:DE0E530D46C803D85B8AEB6D18816F1B09CB3DAFEFB5E19FDFA15C9F41E0F474 | |||
| 3164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3164.8352\Redline Stealer\Libraries\Newtonsoft.Json.dll | executable | |
MD5:— | SHA256:— | |||
| 3164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3164.8352\Redline Stealer\Libraries\builder.pdb | pdb | |
MD5:418DC008EF956465E179EC29D3C3C245 | SHA256:8C7E21B37540211D56C5FDBB7E731655A96945AA83F2988E33D5ADB8AA7C8DF1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report