| File name: | LRE mdb.pptx |
| Full analysis: | https://app.any.run/tasks/2d564c69-319e-46cc-9432-ed215e44bba3 |
| Verdict: | Malicious activity |
| Analysis date: | January 31, 2024, 22:20:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.presentationml.presentation |
| File info: | Microsoft PowerPoint 2007+ |
| MD5: | 778D951BE5DDF38187D9019C0117D968 |
| SHA1: | 403EF615F919CF229EBC5961E76C0AA9E60E6423 |
| SHA256: | 4133D26877B3DEA09D790902A3974CB30EE417F78321BFC7D01D159C364A1DC3 |
| SSDEEP: | 49152:9hors6aqetYNFYjXRgRCCVPClk3YDE8B9wQ7EvK6NACG/f7+onIZcepxn0OAZXcR:9horsXDmNFiyXVC3E8B9w3KwZWFICepn |
MALICIOUS
Unusual execution from MS Office
- POWERPNT.EXE (PID: 268)
SUSPICIOUS
Searches for installed software
- MSACCESS.EXE (PID: 3084)
INFO
The process uses the downloaded file
- POWERPNT.EXE (PID: 268)
- WinRAR.exe (PID: 2628)
Checks supported languages
- MSACCESS.EXE (PID: 3084)
Reads the computer name
- MSACCESS.EXE (PID: 3084)
Reads Microsoft Office registry keys
- MSACCESS.EXE (PID: 3084)
Manual execution by a user
- MSACCESS.EXE (PID: 3084)
Creates files or folders in the user directory
- MSACCESS.EXE (PID: 3084)
Reads the machine GUID from the registry
- MSACCESS.EXE (PID: 3084)
Reads Environment values
- MSACCESS.EXE (PID: 3084)
Create files in a temporary directory
- MSACCESS.EXE (PID: 3084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .pptx | | | PowerPoint Microsoft Office Open XML Format document (87) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (10.5) |
| .zip | | | ZIP compressed archive (2.4) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x5f7e075a |
| ZipCompressedSize: | 457 |
| ZipUncompressedSize: | 3290 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | Output log |
|---|---|
| Creator: | Savo Regulic |
XML
| LastModifiedBy: | Savo Regulic |
|---|---|
| RevisionNumber: | 1 |
| CreateDate: | 2024:01:31 06:44:33Z |
| ModifyDate: | 2024:01:31 06:45:06Z |
| TotalEditTime: | - |
| Words: | 2 |
| Application: | Microsoft Office PowerPoint |
| PresentationFormat: | Widescreen |
| Paragraphs: | 1 |
| Slides: | 1 |
| Notes: | - |
| HiddenSlides: | - |
| MMClips: | - |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: |
|
| Company: | - |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
Total processes
40
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | "C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE" "C:\Users\admin\Desktop\LRE mdb.pptx" | C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft PowerPoint Exit code: 0 Version: 14.0.6009.1000 Modules
| |||||||||||||||
| 2628 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\output.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | POWERPNT.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3084 | "C:\Program Files\Microsoft Office\Office14\MSACCESS.EXE" /NOSTARTUP "C:\Users\admin\Desktop\output.mdb" | C:\Program Files\Microsoft Office\Office14\MSACCESS.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Access Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
3 689
Read events
3 585
Write events
83
Delete events
21
Modification events
| (PID) Process: | (268) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (268) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (268) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (268) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (268) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (268) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (268) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (268) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (268) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (268) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
1
Suspicious files
9
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 268 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\CVR332A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
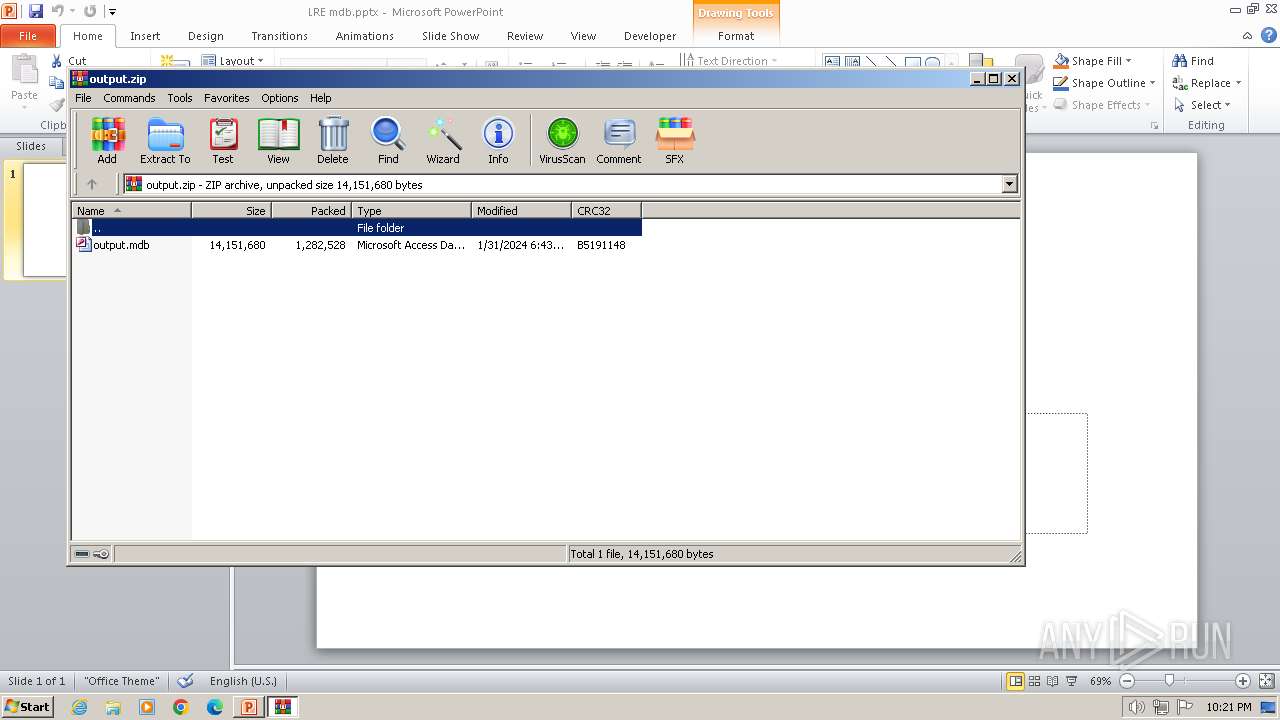
| 2628 | WinRAR.exe | C:\Users\admin\Desktop\output.mdb | — | |
MD5:— | SHA256:— | |||
| 3084 | MSACCESS.EXE | C:\Users\admin\AppData\Local\Temp\CVRF83F.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 268 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\msoE053.tmp | binary | |
MD5:4836655D0F09355FDB2275075A9829F0 | SHA256:419C36F50225B7DC5AEA6E83DD700A06432E4B9F40E253E25FEF9A9F6B98C5EC | |||
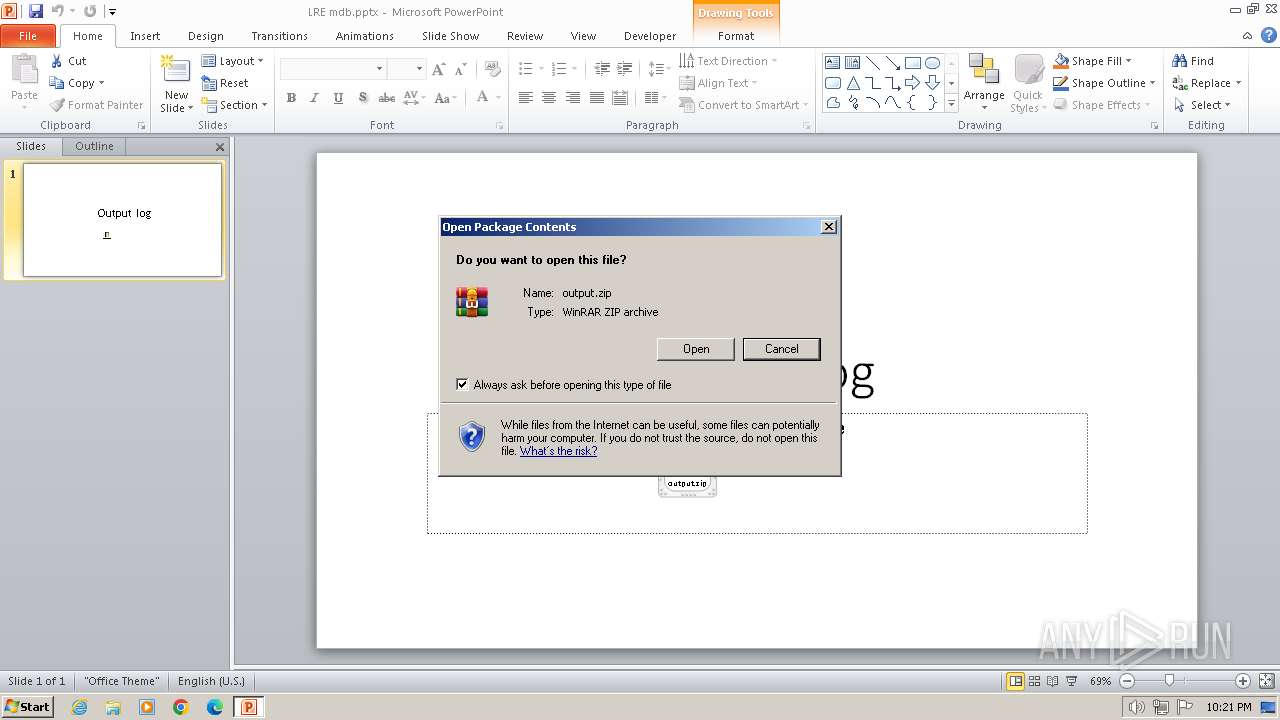
| 268 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\output.zip | compressed | |
MD5:0C7620B14AEA57A7BC216B8913E61EA0 | SHA256:446873C2A2CBB7796CE3E078F9532A5AC38B468E3DEB5C1E7A18D63087FAA0B0 | |||
| 268 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\2B025B43.wmz | binary | |
MD5:4836655D0F09355FDB2275075A9829F0 | SHA256:419C36F50225B7DC5AEA6E83DD700A06432E4B9F40E253E25FEF9A9F6B98C5EC | |||
| 268 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\output.zip:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 268 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\~DF05CD06C084080175.TMP | binary | |
MD5:29C8DFDECE6538974E4D8770F66F81C3 | SHA256:0272EB6073C30D563F90075A854CD0F43FE6A6C4BDD2078E6A5782C1D4B2E90A | |||
| 268 | POWERPNT.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:C9BD49D86CE76FC3BB6EC314AE244686 | SHA256:ADACC686B074728FD4BED423717DF054FE2D1154897DB39C1EEC11E6AC094F2F | |||
| 268 | POWERPNT.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\LRE mdb.pptx.LNK | binary | |
MD5:9A503E2AE890F74B54C39E8AA3A6CFF4 | SHA256:A679B56D80F0C38DF1FF8D1860C3B382D43102445421D9F4B41AF0257C843420 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Threats
Process | Message |
|---|---|
MSACCESS.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Access\System.mdw |