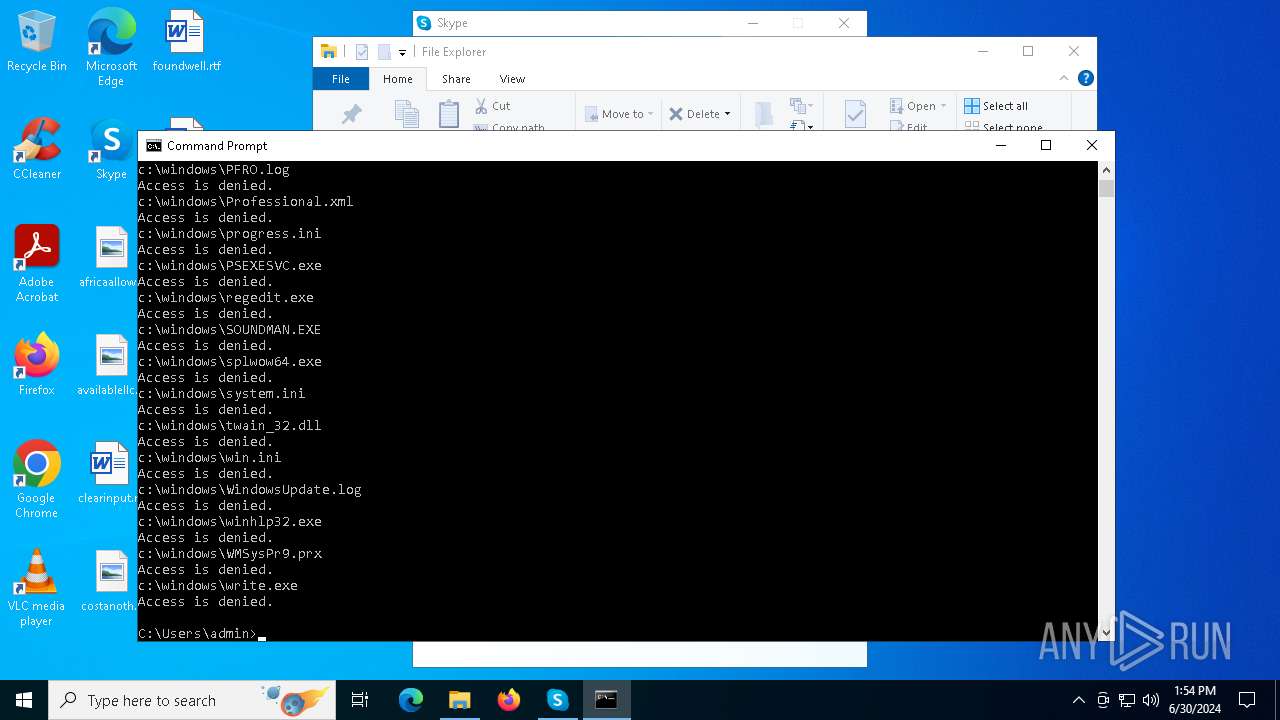
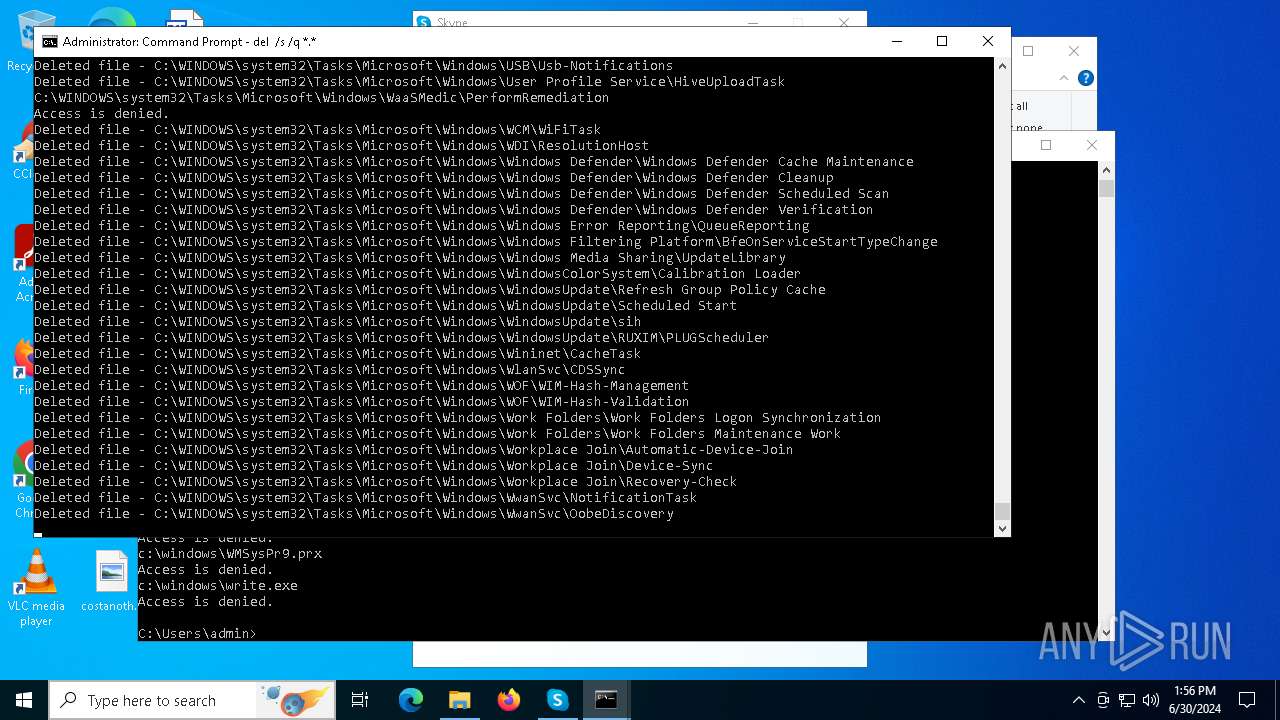
| File name: | BIOSRenamer.exe |
| Full analysis: | https://app.any.run/tasks/27999ab2-5991-453a-a742-bf21f0c9edd3 |
| Verdict: | Malicious activity |
| Analysis date: | June 30, 2024, 13:53:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | F54768924322CC9B6BAC3C19CE03D8EA |
| SHA1: | 384385A1B3707557191D8183AE5DB78071559BCD |
| SHA256: | 412449D304C606DC57AA902FDF9BD040B756732B34307D2C274EBE9E06BF8732 |
| SSDEEP: | 3072:YU+AoZLR/u0jA13fk/Ua+cE9Z4Wqnp6a7fREoXSlWig9hJbAy366:YUiRRGj3fkbpq41623fJbD366 |
MALICIOUS
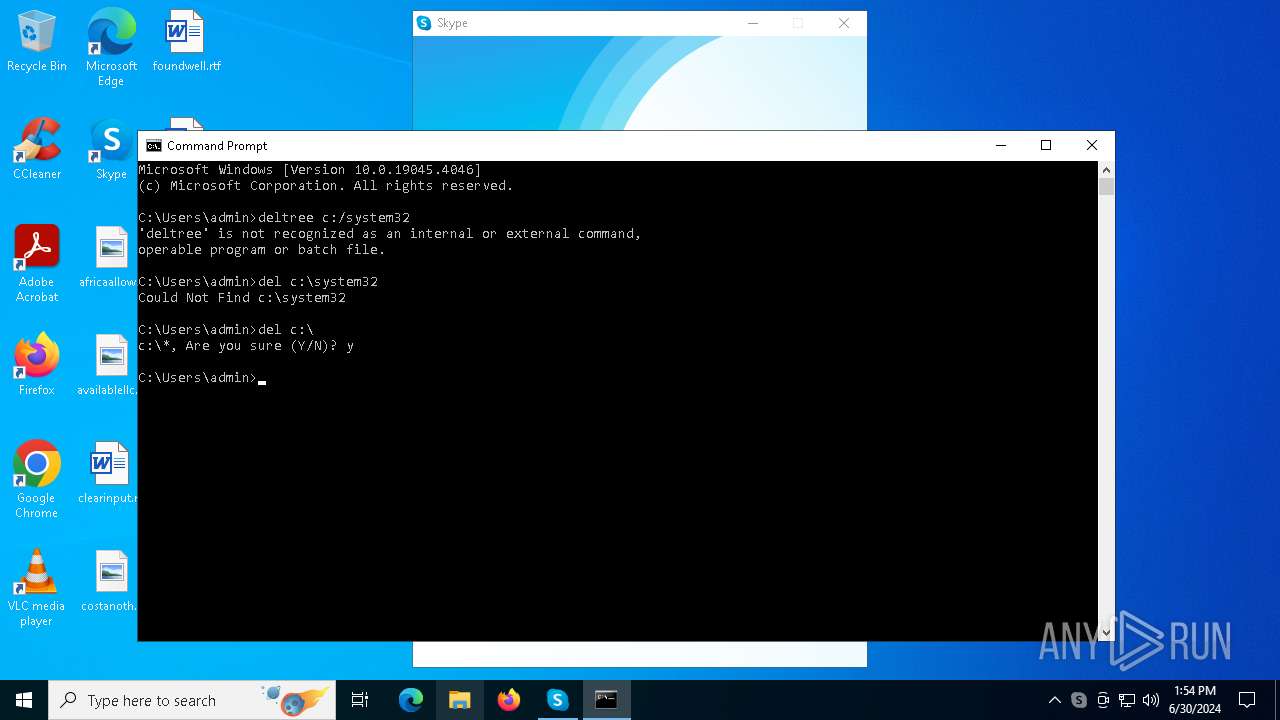
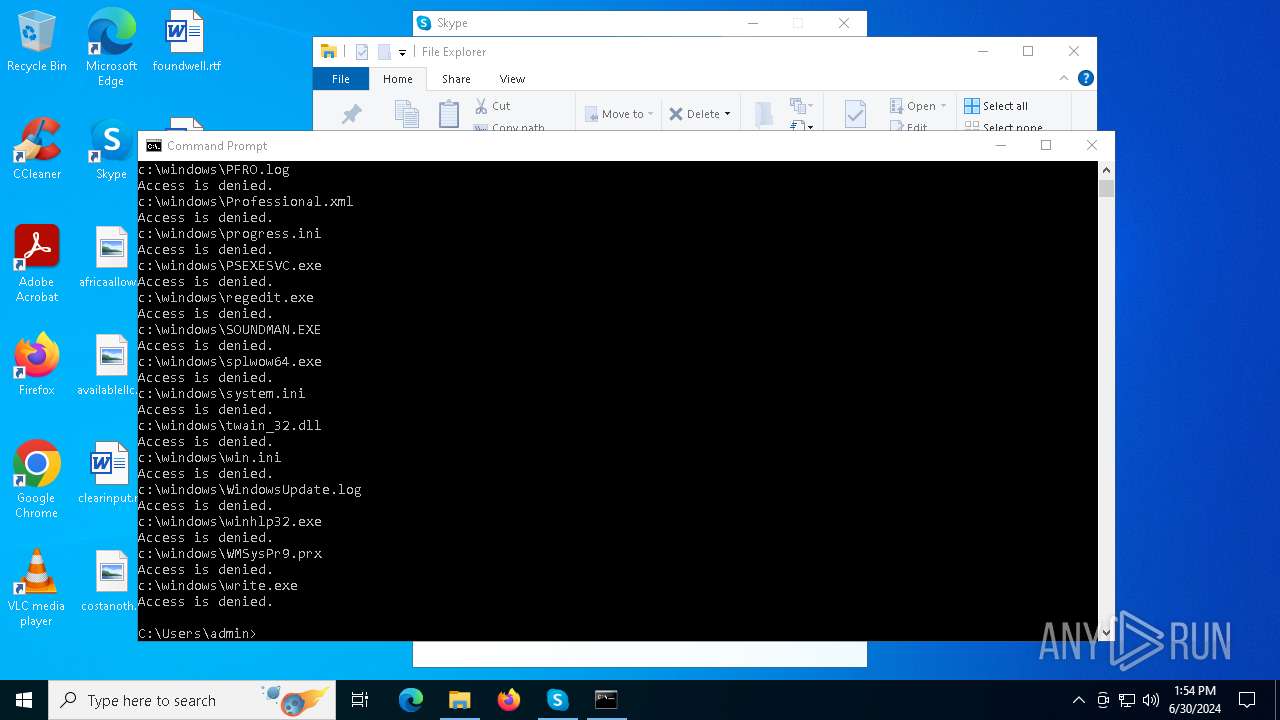
Drops the executable file immediately after the start
- BIOSRenamer.exe (PID: 2472)
- CCleaner64.exe (PID: 7048)
- CCleaner64.exe (PID: 5764)
Changes the autorun value in the registry
- reg.exe (PID: 6548)
- CCleaner64.exe (PID: 5764)
Actions looks like stealing of personal data
- CCleaner64.exe (PID: 6300)
- CCleaner64.exe (PID: 7048)
- CCleaner64.exe (PID: 5764)
Steals credentials from Web Browsers
- CCleaner64.exe (PID: 7048)
- CCleaner64.exe (PID: 5764)
- cmd.exe (PID: 8024)
SUSPICIOUS
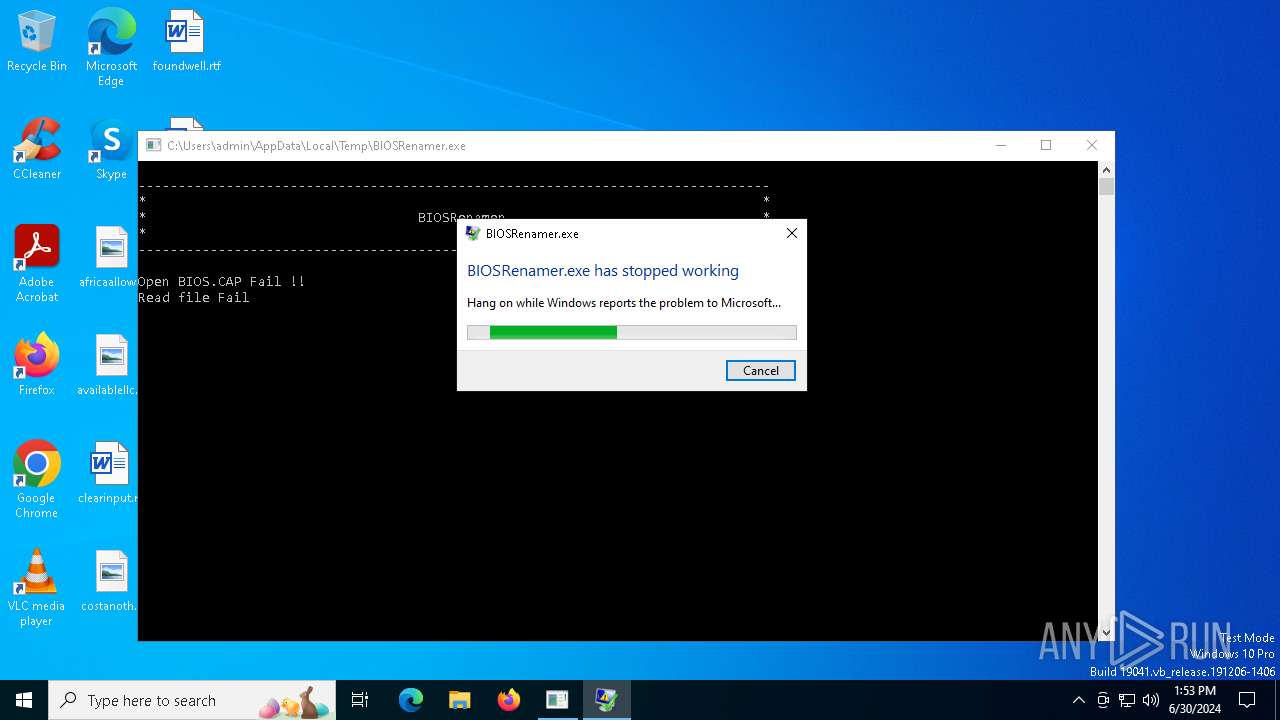
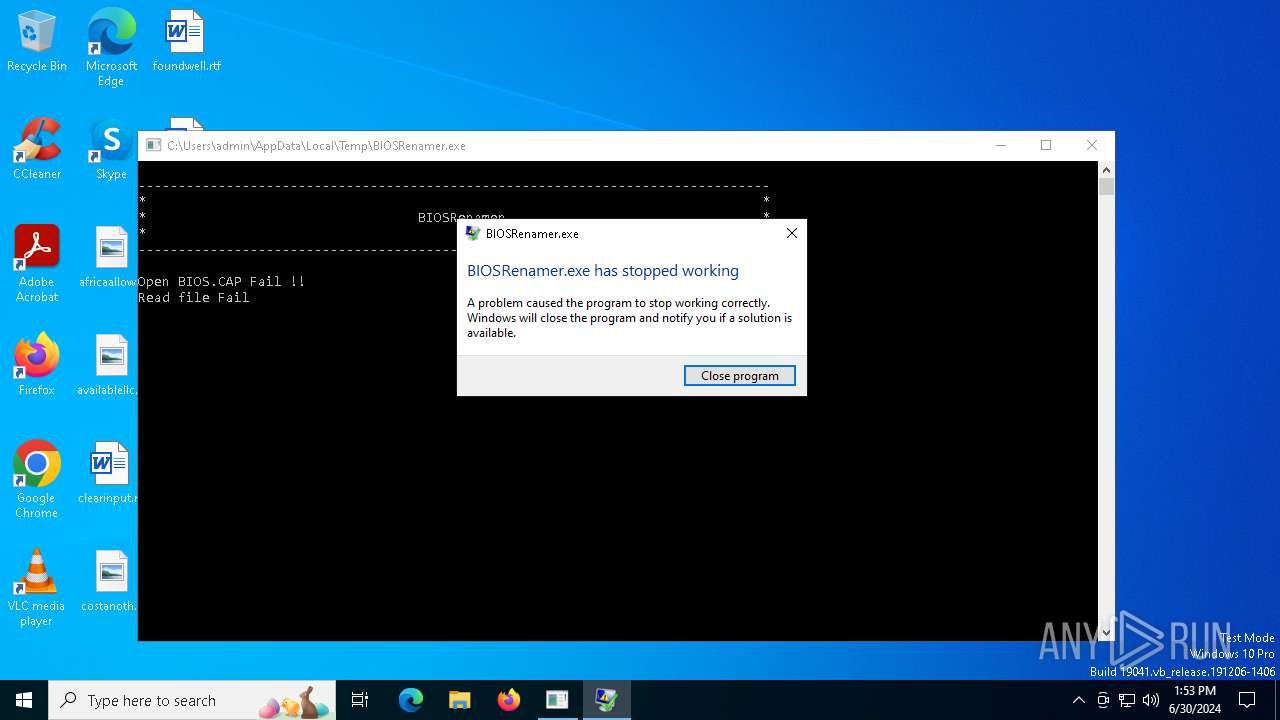
Executes application which crashes
- BIOSRenamer.exe (PID: 2472)
Application launched itself
- Skype.exe (PID: 5504)
- CCleaner64.exe (PID: 6300)
- CCleaner64.exe (PID: 7048)
Reads the date of Windows installation
- CCleaner64.exe (PID: 6300)
- CCleaner64.exe (PID: 7048)
Uses REG/REGEDIT.EXE to modify registry
- Skype.exe (PID: 5504)
Reads security settings of Internet Explorer
- CCleaner64.exe (PID: 6300)
- CCleaner64.exe (PID: 7048)
- CCleaner64.exe (PID: 5764)
- Skype.exe (PID: 5504)
- ShellExperienceHost.exe (PID: 7784)
Searches for installed software
- CCleaner64.exe (PID: 7048)
- CCleaner64.exe (PID: 5764)
Reads Internet Explorer settings
- CCleaner64.exe (PID: 7048)
- CCleaner64.exe (PID: 5764)
Executable content was dropped or overwritten
- CCleaner64.exe (PID: 7048)
- CCleaner64.exe (PID: 5764)
Checks Windows Trust Settings
- CCleaner64.exe (PID: 7048)
- CCleaner64.exe (PID: 5764)
Detected use of alternative data streams (AltDS)
- Skype.exe (PID: 5504)
Checks for external IP
- CCleaner64.exe (PID: 7048)
The process verifies whether the antivirus software is installed
- CCleaner64.exe (PID: 5764)
INFO
Reads the software policy settings
- WerFault.exe (PID: 5868)
- CCleaner64.exe (PID: 7048)
- CCleaner64.exe (PID: 5764)
- Skype.exe (PID: 5504)
Checks proxy server information
- WerFault.exe (PID: 5868)
- Skype.exe (PID: 5504)
- CCleaner64.exe (PID: 7048)
Creates files or folders in the user directory
- WerFault.exe (PID: 5868)
- Skype.exe (PID: 5504)
- Skype.exe (PID: 6680)
- CCleaner64.exe (PID: 7048)
- Skype.exe (PID: 6536)
Checks supported languages
- BIOSRenamer.exe (PID: 2472)
- Skype.exe (PID: 5504)
- Skype.exe (PID: 6376)
- Skype.exe (PID: 6516)
- Skype.exe (PID: 6536)
- Skype.exe (PID: 6680)
- CCleaner64.exe (PID: 6300)
- CCleaner64.exe (PID: 7048)
- CCleaner64.exe (PID: 5764)
- Skype.exe (PID: 4424)
- TextInputHost.exe (PID: 5784)
- ShellExperienceHost.exe (PID: 7784)
- Skype.exe (PID: 7052)
Manual execution by a user
- WINWORD.EXE (PID: 2196)
- Skype.exe (PID: 5504)
- CCleaner64.exe (PID: 6300)
- mspaint.exe (PID: 2660)
- cmd.exe (PID: 4180)
- cmd.exe (PID: 8024)
Reads Environment values
- Skype.exe (PID: 5504)
- CCleaner64.exe (PID: 6300)
- Skype.exe (PID: 6680)
- CCleaner64.exe (PID: 7048)
- CCleaner64.exe (PID: 5764)
Reads CPU info
- Skype.exe (PID: 5504)
- CCleaner64.exe (PID: 7048)
- CCleaner64.exe (PID: 5764)
Reads the computer name
- Skype.exe (PID: 5504)
- Skype.exe (PID: 6516)
- Skype.exe (PID: 6536)
- CCleaner64.exe (PID: 6300)
- Skype.exe (PID: 6680)
- CCleaner64.exe (PID: 7048)
- CCleaner64.exe (PID: 5764)
- TextInputHost.exe (PID: 5784)
- ShellExperienceHost.exe (PID: 7784)
- Skype.exe (PID: 7052)
Process checks computer location settings
- Skype.exe (PID: 6680)
- Skype.exe (PID: 5504)
- CCleaner64.exe (PID: 6300)
- CCleaner64.exe (PID: 7048)
- Skype.exe (PID: 4424)
Create files in a temporary directory
- Skype.exe (PID: 5504)
Reads the machine GUID from the registry
- CCleaner64.exe (PID: 7048)
- CCleaner64.exe (PID: 5764)
- Skype.exe (PID: 5504)
- Skype.exe (PID: 7052)
Reads product name
- CCleaner64.exe (PID: 7048)
- CCleaner64.exe (PID: 5764)
Creates files in the program directory
- CCleaner64.exe (PID: 7048)
- CCleaner64.exe (PID: 5764)
Reads Microsoft Office registry keys
- CCleaner64.exe (PID: 7048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:11:22 07:49:09+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.15 |
| CodeSize: | 83968 |
| InitializedDataSize: | 37888 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x16e1 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
187
Monitored processes
37
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | C:\WINDOWS\system32\reg.exe QUERY HKCU\Software\Microsoft\Windows\Shell\Associations\UrlAssociations\http\UserChoice /v ProgId | C:\Windows\SysWOW64\reg.exe | — | Skype.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\foundwell.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 2220 | C:\WINDOWS\system32\reg.exe QUERY HKCU\Software\Microsoft\Edge\BLBeacon /v version | C:\Windows\SysWOW64\reg.exe | — | Skype.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2472 | "C:\Users\admin\AppData\Local\Temp\BIOSRenamer.exe" | C:\Users\admin\AppData\Local\Temp\BIOSRenamer.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 2660 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\wasteloss.jpg" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3220 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4180 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4424 | "C:\Program Files (x86)\Microsoft\Skype for Desktop\Skype.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop" --app-user-model-id=Microsoft.Skype.SkypeDesktop --app-path="C:\Program Files (x86)\Microsoft\Skype for Desktop\resources\app.asar" --no-sandbox --no-zygote --enable-blink-features --disable-blink-features --autoplay-policy=no-user-gesture-required --disable-background-timer-throttling --ms-disable-indexeddb-transaction-timeout --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=4024 --field-trial-handle=2228,i,10214553553838524539,13504286432761273882,131072 --enable-features=WinUseBrowserSpellChecker,WinUseHybridSpellChecker,WinrtGeolocationImplementation --disable-features=SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:1 | C:\Program Files (x86)\Microsoft\Skype for Desktop\Skype.exe | — | Skype.exe | |||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Version: 8.104.0.207 Modules
| |||||||||||||||
| 4564 | C:\WINDOWS\system32\reg.exe QUERY "HKLM\Software\Microsoft\Windows\CurrentVersion\App Paths\msedge.exe" /ve | C:\Windows\SysWOW64\reg.exe | — | Skype.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4784 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | BIOSRenamer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
56 301
Read events
55 797
Write events
402
Delete events
102
Modification events
| (PID) Process: | (2660) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | WindowPlacement |
Value: 2C00000000000000010000000000000000000000FFFFFFFFFFFFFFFF7F000000470000007F04000087020000 | |||
| (PID) Process: | (2660) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ShowThumbnail |
Value: 0 | |||
| (PID) Process: | (2660) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | BMPWidth |
Value: 0 | |||
| (PID) Process: | (2660) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | BMPHeight |
Value: 0 | |||
| (PID) Process: | (2660) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ThumbXPos |
Value: 0 | |||
| (PID) Process: | (2660) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ThumbYPos |
Value: 0 | |||
| (PID) Process: | (2660) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ThumbWidth |
Value: 0 | |||
| (PID) Process: | (2660) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ThumbHeight |
Value: 0 | |||
| (PID) Process: | (2660) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | UnitSetting |
Value: 0 | |||
| (PID) Process: | (2660) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ShowRulers |
Value: 0 | |||
Executable files
8
Suspicious files
99
Text files
18
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5868 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_BIOSRenamer.exe_7e6bfaeca10c4c95a17bef62faf5969db352e_d3ade3c2_b5538495-e317-437c-98f9-63e73b4be708\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5868 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:13DA38D4F03D2B513664ECB11AF27B76 | SHA256:E8470A0B1403036D8CEC7B12929D0CD3E2E905BC9A95C32D8D518EB492FA93E8 | |||
| 5868 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERE273.tmp.WERInternalMetadata.xml | xml | |
MD5:CF4EB65FBD3C10D04B3979B56A5EA2F4 | SHA256:A5F2681AA3E037070871584F0375F5859EB81F1297A4E02AD02FD5AB9DF51119 | |||
| 5868 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERE2C2.tmp.xml | xml | |
MD5:B54718AE0F39B432C0D6D2B365188126 | SHA256:428E94121B2A1ACAE5B611B8732BF36FFB93DC7ED8030502AEB5CC21EB3EF024 | |||
| 5868 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERE1F5.tmp.dmp | dmp | |
MD5:AB2F69469961D53FD7F1FB1883C458CC | SHA256:D05A91C260794997C4FC5C82A773E2BCB90C2F68E306C64064C0CE659B574E13 | |||
| 2196 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:8CD27348A814BBF5EB02E34141C34439 | SHA256:46E0FBB351CEC306C1B5792EC6AAC39CDBBBDEECD806EDB6CE56801C55ECD416 | |||
| 5504 | Skype.exe | C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Local Storage\leveldb\LOG.old | text | |
MD5:46EED8B7CAAD25F7F453617DA0FB0857 | SHA256:5BC1DE0E32F2969386351B2BE088F13B6CC3DF7693EE9E92FEEF59DB6AF1FB92 | |||
| 5504 | Skype.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\0EG2PNX98V8318D5KYUQ.temp | binary | |
MD5:6DB0378151D369950A13558D0EE753C1 | SHA256:3143D184AFC86FD3B674815F4E52C4F14A2CAEC200C8E3BAB2C70B436CCBC166 | |||
| 2196 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | der | |
MD5:9C7E8856A3F456A9F535125A7F3A8020 | SHA256:DB21529CEF9E84CDA7F7A1B144F36AFDA687388C204ECD501BAB1479C90ECE63 | |||
| 2196 | WINWORD.EXE | C:\Users\admin\Desktop\~$undwell.rtf | binary | |
MD5:BDFD6F890197A9944E98F37F382BE584 | SHA256:15EB2D905D27FF0691C3D432AB43FA0A578F945BCDC2B9B0C1A641F805945D53 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
130
DNS requests
66
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5868 | WerFault.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5868 | WerFault.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
2504 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
2504 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
5732 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
5248 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
5732 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4656 | SearchApp.exe | 104.126.37.155:443 | r.bing.com | Akamai International B.V. | DE | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2444 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5868 | WerFault.exe | 20.189.173.21:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
5868 | WerFault.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
5868 | WerFault.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
2504 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3508 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2504 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
watson.events.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2168 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
7048 | CCleaner64.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
Process | Message |
|---|---|
CCleaner64.exe | [2024-06-30 13:53:42.875] [error ] [settings ] [ 7048: 7052] [000000: 0] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner64.exe | [2024-06-30 13:53:42.875] [error ] [ini_access ] [ 7048: 7052] [000000: 0] Incorrect ini_accessor configuration! Fixing relative input path to avoid recursion. Input was: Setup
|
CCleaner64.exe | Failed to open log file 'C:\Program Files\CCleaner' |
CCleaner64.exe | OnLanguage - en
|
CCleaner64.exe | [2024-06-30 13:53:44.048] [error ] [settings ] [ 7048: 6248] [D2EC45: 356] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner64.exe | [2024-06-30 13:53:44.077] [error ] [Burger ] [ 7048: 6248] [904E07: 253] [23.2.1118.0] [BurgerReporter.cpp] [253] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner64.exe | [2024-06-30 13:53:44.077] [error ] [Burger ] [ 7048: 6248] [904E07: 253] [23.2.1118.0] [BurgerReporter.cpp] [253] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner64.exe | file:///tis/optimizer.tis(1131) : warning :'await' should be used only inside 'async' or 'event'
|
CCleaner64.exe | file:///tis/optimizer.tis(1288) : warning :'async' does not contain any 'await'
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|