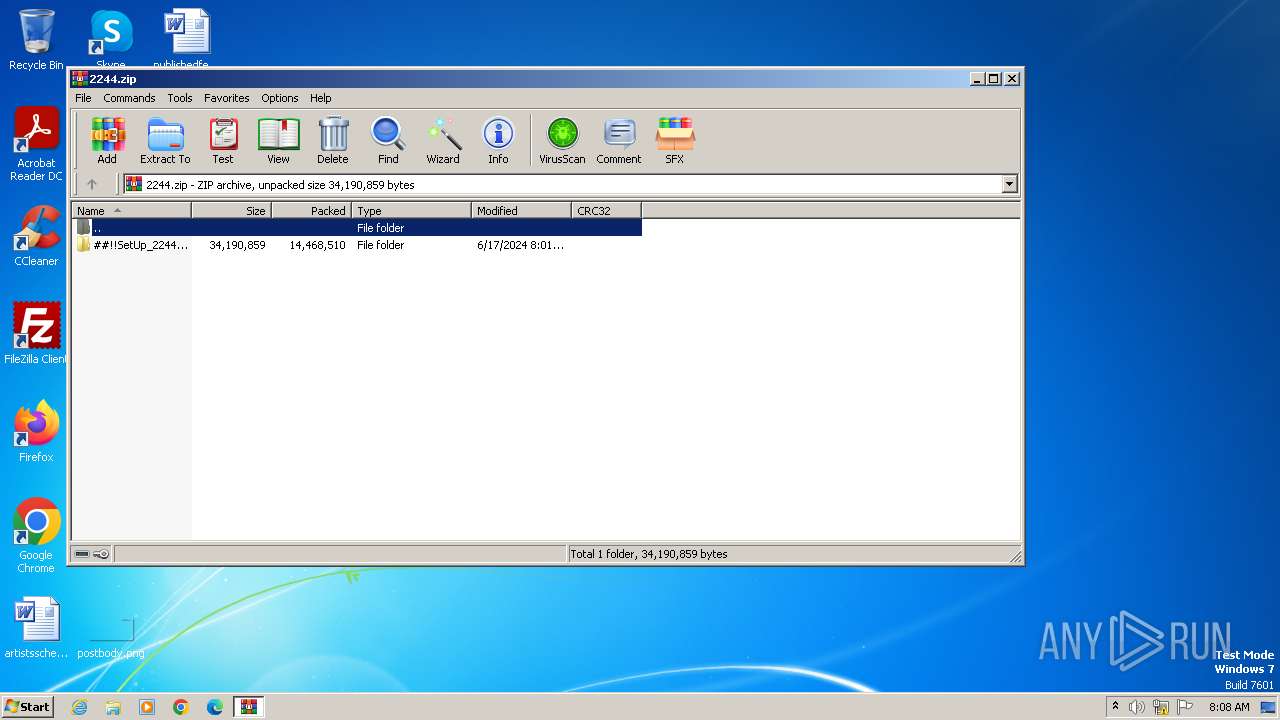
| File name: | 2244.zip |
| Full analysis: | https://app.any.run/tasks/97b4179c-2c05-4b27-8d70-5ba0ea0c2249 |
| Verdict: | Malicious activity |
| Analysis date: | June 17, 2024, 07:08:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 705FAEF7EA7739B6803CF6D86E5456B2 |
| SHA1: | B16DDA656EE23BE405ED8B153E0DC6DCECE6AD97 |
| SHA256: | 40F758387BA5A5D7D79CAE07E15DA4F5C725A5DE08D4E7E63330EF392A5E7D18 |
| SSDEEP: | 98304:zg7surMjdp/6WrBz/IYQqrAxbopw8kkRaeVcjOL5Rt2HTglljVMKyPXzpP6nxgjK:bpNKiF8So6t3aQJUJeVbBh |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3980)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3980)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3980)
Manual execution by a user
- POWERPNT.EXE (PID: 764)
- POWERPNT.EXE (PID: 1136)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:06:17 15:01:32 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
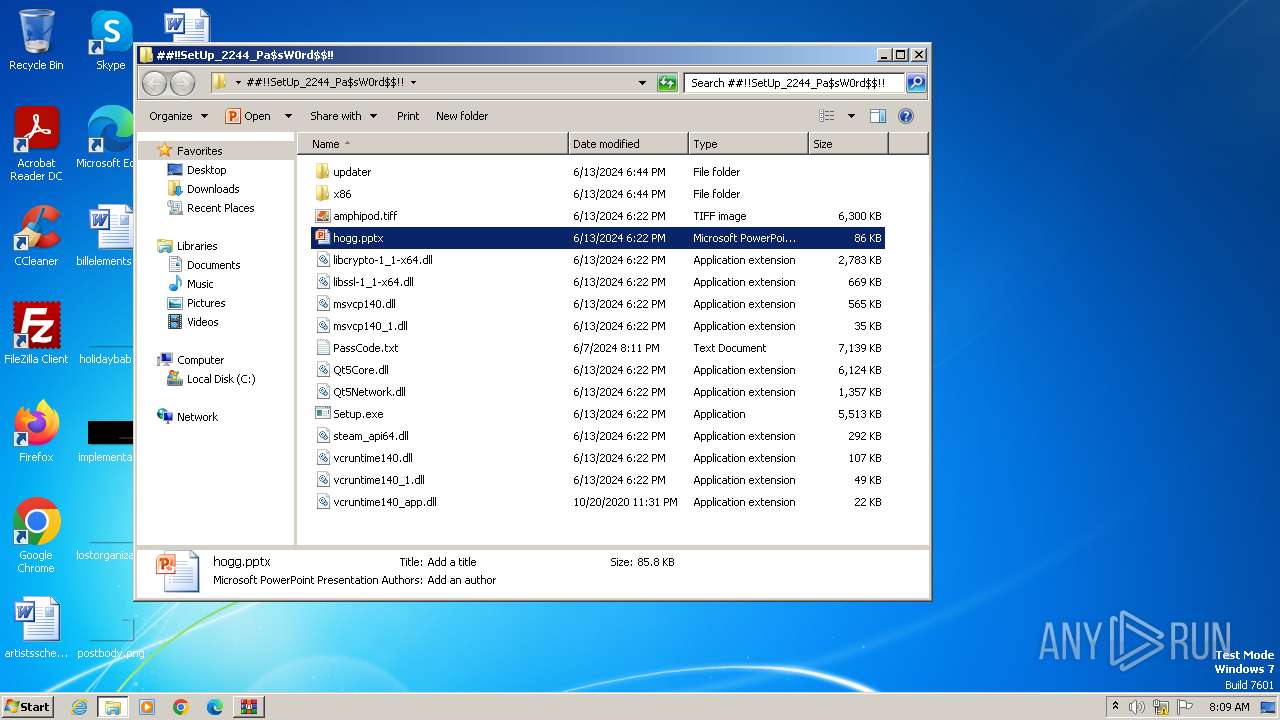
| ZipFileName: | ##!!SetUp_2244_Pa$sW0rd$!!/ |
Total processes
41
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 764 | "C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE" "C:\Users\admin\Desktop\##!!SetUp_2244_Pa$sW0rd$!!\hogg.pptx" | C:\Program Files\microsoft office\Office14\POWERPNT.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft PowerPoint Exit code: 0 Version: 14.0.6009.1000 Modules
| |||||||||||||||
| 1136 | "C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE" "C:\Users\admin\Desktop\##!!SetUp_2244_Pa$sW0rd$!!\hogg.pptx" | C:\Program Files\microsoft office\Office14\POWERPNT.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft PowerPoint Exit code: 0 Version: 14.0.6009.1000 Modules
| |||||||||||||||
| 3980 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\2244.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
8 803
Read events
8 685
Write events
103
Delete events
15
Modification events
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\2244.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
33
Suspicious files
4
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3980 | WinRAR.exe | C:\Users\admin\Desktop\##!!SetUp_2244_Pa$sW0rd$!!\amphipod.tiff | — | |
MD5:— | SHA256:— | |||
| 3980 | WinRAR.exe | C:\Users\admin\Desktop\##!!SetUp_2244_Pa$sW0rd$!!\PassCode.txt | — | |
MD5:— | SHA256:— | |||
| 3980 | WinRAR.exe | C:\Users\admin\Desktop\##!!SetUp_2244_Pa$sW0rd$!!\libssl-1_1-x64.dll | executable | |
MD5:4AD03043A32E9A1EF64115FC1ACE5787 | SHA256:A0E43CBC4A2D8D39F225ABD91980001B7B2B5001E8B2B8292537AE39B17B85D1 | |||
| 3980 | WinRAR.exe | C:\Users\admin\Desktop\##!!SetUp_2244_Pa$sW0rd$!!\libcrypto-1_1-x64.dll | executable | |
MD5:28DEA3E780552EB5C53B3B9B1F556628 | SHA256:52415829D85C06DF8724A3D3D00C98F12BEABF5D6F3CBAD919EC8000841A86E8 | |||
| 3980 | WinRAR.exe | C:\Users\admin\Desktop\##!!SetUp_2244_Pa$sW0rd$!!\msvcp140.dll | executable | |
MD5:1BA6D1CF0508775096F9E121A24E5863 | SHA256:74892D9B4028C05DEBAF0B9B5D9DC6D22F7956FA7D7EEE00C681318C26792823 | |||
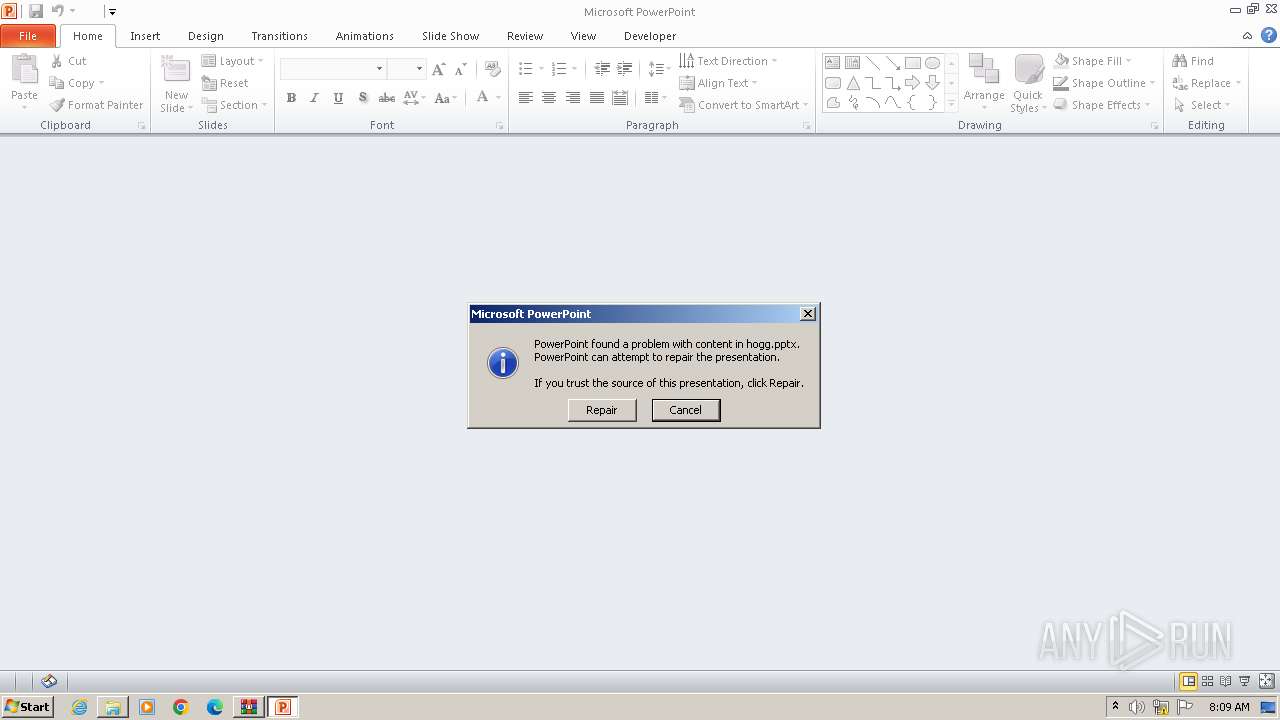
| 3980 | WinRAR.exe | C:\Users\admin\Desktop\##!!SetUp_2244_Pa$sW0rd$!!\hogg.pptx | binary | |
MD5:4A1BB50A70821601F854CB93681F57A1 | SHA256:4DB21E4665018A3E6CD03EC1B65F42A1C6C8F8046B3F451A1E025A2013E8203F | |||
| 3980 | WinRAR.exe | C:\Users\admin\Desktop\##!!SetUp_2244_Pa$sW0rd$!!\vcruntime140_app.dll | executable | |
MD5:C0F29BD3B0EB4D8795D609A0C52E0926 | SHA256:813A447192C4FA7D25D0716B769399546F8BF6B31269DD8AD47F9812008D79E6 | |||
| 3980 | WinRAR.exe | C:\Users\admin\Desktop\##!!SetUp_2244_Pa$sW0rd$!!\x86\api-ms-win-core-string-l1-1-0.dll | executable | |
MD5:2E5C29FC652F432B89A1AFE187736C4D | SHA256:3807DB7ACF1B40C797E4D4C14A12C3806346AE56B25E205E600BE3E635C18D4F | |||
| 3980 | WinRAR.exe | C:\Users\admin\Desktop\##!!SetUp_2244_Pa$sW0rd$!!\x86\api-ms-win-core-synch-l1-1-0.dll | executable | |
MD5:979C67BA244E5328A1A2E588FF748E86 | SHA256:8BB38A7A59FBAA792B3D5F34F94580429588C8C592929CBD307AFD5579762ABC | |||
| 3980 | WinRAR.exe | C:\Users\admin\Desktop\##!!SetUp_2244_Pa$sW0rd$!!\x86\api-ms-win-core-processthreads-l1-1-1.dll | executable | |
MD5:29001F316CCFC800E2246743DF9B15B3 | SHA256:E5EA2C21FB225090F7D0DB6C6990D67B1558D8E834E86513BC8BA7A43C4E7B36 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |