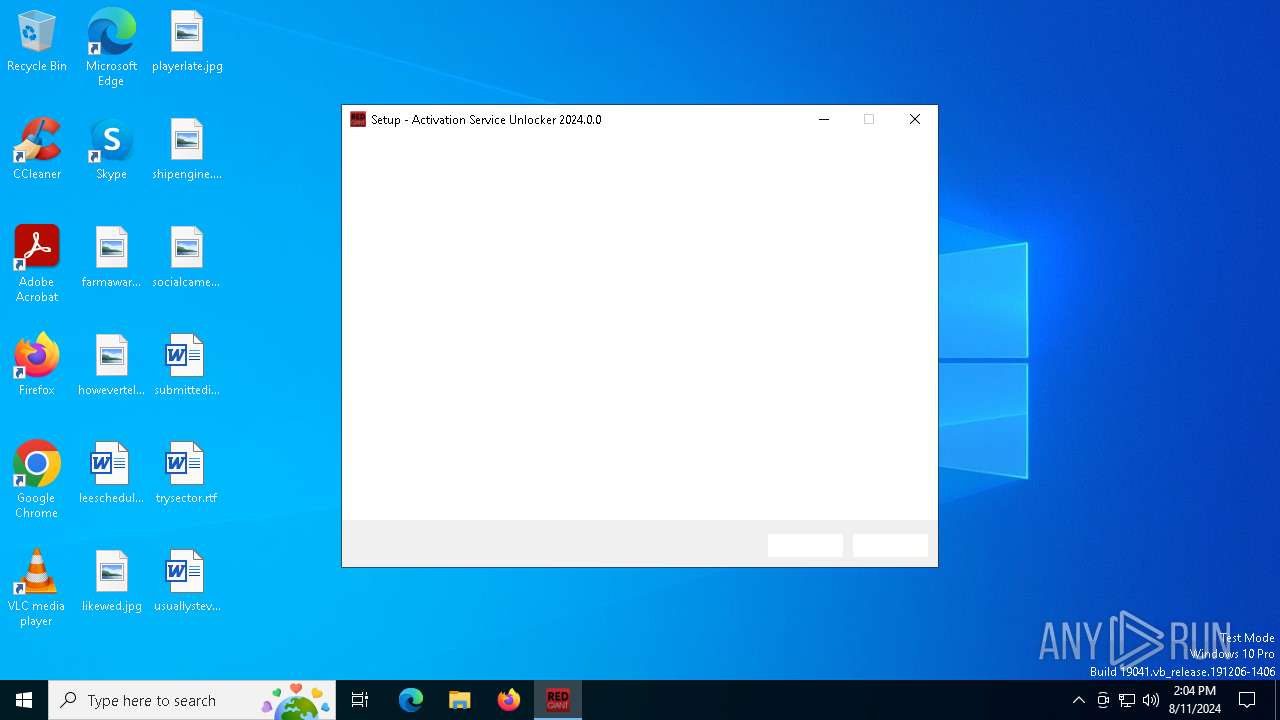
| File name: | RedGiant Activation Service Unlocker 2024.0.0.exe |
| Full analysis: | https://app.any.run/tasks/c45679dc-1d4a-4da2-af25-4589ec0f12a5 |
| Verdict: | Malicious activity |
| Analysis date: | August 11, 2024, 14:03:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 345C16A685EC82E33FA63E558CD8D464 |
| SHA1: | 81B37D064D87D50952D7F0012884D8639E9306FA |
| SHA256: | 40F0FDCAA1FB8D69A968737AF9EA161D719E67BC1B6CE0B7AF2963682E00B8FB |
| SSDEEP: | 98304:r+cD4dnI0HTE5E44SKlBi6/+1aveY8RPwd63BhXxW1FBBd1L9U7qMX1rKc2aEfXE:+ROgI0T4qSsKD |
MALICIOUS
Starts NET.EXE for service management
- net.exe (PID: 6696)
- RedGiant Activation Service Unlocker 2024.0.0.tmp (PID: 6656)
- net.exe (PID: 6856)
- net.exe (PID: 640)
SUSPICIOUS
Drops the executable file immediately after the start
- RedGiant Activation Service Unlocker 2024.0.0.exe (PID: 6632)
- RedGiant Activation Service Unlocker 2024.0.0.tmp (PID: 6656)
- deep.exe (PID: 7164)
- deep.tmp (PID: 6340)
Executable content was dropped or overwritten
- RedGiant Activation Service Unlocker 2024.0.0.exe (PID: 6632)
- RedGiant Activation Service Unlocker 2024.0.0.tmp (PID: 6656)
- deep.exe (PID: 7164)
- deep.tmp (PID: 6340)
Reads the Windows owner or organization settings
- RedGiant Activation Service Unlocker 2024.0.0.tmp (PID: 6656)
- deep.tmp (PID: 6340)
Uses TIMEOUT.EXE to delay execution
- RedGiant Activation Service Unlocker 2024.0.0.tmp (PID: 6656)
Uses TASKKILL.EXE to kill process
- RedGiant Activation Service Unlocker 2024.0.0.tmp (PID: 6656)
- deep.tmp (PID: 6340)
INFO
Checks supported languages
- RedGiant Activation Service Unlocker 2024.0.0.tmp (PID: 6656)
- deep.exe (PID: 7164)
- RedGiant Activation Service Unlocker 2024.0.0.exe (PID: 6632)
- deep.tmp (PID: 6340)
- TextInputHost.exe (PID: 6792)
Reads the computer name
- RedGiant Activation Service Unlocker 2024.0.0.tmp (PID: 6656)
- deep.tmp (PID: 6340)
- TextInputHost.exe (PID: 6792)
Create files in a temporary directory
- RedGiant Activation Service Unlocker 2024.0.0.tmp (PID: 6656)
- deep.exe (PID: 7164)
- RedGiant Activation Service Unlocker 2024.0.0.exe (PID: 6632)
- deep.tmp (PID: 6340)
Creates files in the program directory
- RedGiant Activation Service Unlocker 2024.0.0.tmp (PID: 6656)
- deep.tmp (PID: 6340)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (51.8) |
|---|---|---|
| .exe | | | InstallShield setup (20.3) |
| .exe | | | Win32 EXE PECompact compressed (generic) (19.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.1) |
| .exe | | | Win32 Executable (generic) (2.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 57344 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2024.0.0.0 |
| ProductVersionNumber: | 2024.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Red Giant, LLC |
| FileDescription: | Activation Service Unlocker Setup |
| FileVersion: | 2024.0.0 |
| LegalCopyright: | © Red Giant LLC |
| OriginalFileName: | |
| ProductName: | Activation Service Unlocker |
| ProductVersion: | 2024.0.0 |
Total processes
161
Monitored processes
23
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 640 | "C:\WINDOWS\system32\net.exe" start "Red Giant Service" | C:\Windows\System32\net.exe | — | RedGiant Activation Service Unlocker 2024.0.0.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4104 | C:\WINDOWS\system32\net1 start "Red Giant Service" | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6340 | "C:\Users\admin\AppData\Local\Temp\is-2BOS2.tmp\deep.tmp" /SL5="$902D2,4084182,800256,C:\Users\admin\AppData\Local\Temp\is-ABU86.tmp\deep.exe" /verysilent | C:\Users\admin\AppData\Local\Temp\is-2BOS2.tmp\deep.tmp | deep.exe | ||||||||||||
User: admin Company: Red Giant, LLC Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6372 | "C:\WINDOWS\system32\taskkill.exe" /f /im maxon.exe | C:\Windows\System32\taskkill.exe | — | deep.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6380 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6400 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6544 | "C:\Users\admin\AppData\Local\Temp\RedGiant Activation Service Unlocker 2024.0.0.exe" | C:\Users\admin\AppData\Local\Temp\RedGiant Activation Service Unlocker 2024.0.0.exe | — | explorer.exe | |||||||||||
User: admin Company: Red Giant, LLC Integrity Level: MEDIUM Description: Activation Service Unlocker Setup Exit code: 3221226540 Version: 2024.0.0 Modules
| |||||||||||||||
| 6632 | "C:\Users\admin\AppData\Local\Temp\RedGiant Activation Service Unlocker 2024.0.0.exe" | C:\Users\admin\AppData\Local\Temp\RedGiant Activation Service Unlocker 2024.0.0.exe | explorer.exe | ||||||||||||
User: admin Company: Red Giant, LLC Integrity Level: HIGH Description: Activation Service Unlocker Setup Exit code: 0 Version: 2024.0.0 Modules
| |||||||||||||||
| 6656 | "C:\Users\admin\AppData\Local\Temp\is-LIE7D.tmp\RedGiant Activation Service Unlocker 2024.0.0.tmp" /SL5="$402B2,5241603,800256,C:\Users\admin\AppData\Local\Temp\RedGiant Activation Service Unlocker 2024.0.0.exe" | C:\Users\admin\AppData\Local\Temp\is-LIE7D.tmp\RedGiant Activation Service Unlocker 2024.0.0.tmp | RedGiant Activation Service Unlocker 2024.0.0.exe | ||||||||||||
User: admin Company: Red Giant, LLC Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6696 | "C:\WINDOWS\system32\net.exe" stop "Red Giant Service" | C:\Windows\System32\net.exe | — | RedGiant Activation Service Unlocker 2024.0.0.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 514
Read events
3 490
Write events
12
Delete events
12
Modification events
| (PID) Process: | (6656) RedGiant Activation Service Unlocker 2024.0.0.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 001A0000FDE80353F7EBDA01 | |||
| (PID) Process: | (6656) RedGiant Activation Service Unlocker 2024.0.0.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 824FFD72332889C21CD4932B04E68C1F199DA6952E2937CCA1BEABE04AF44C55 | |||
| (PID) Process: | (6656) RedGiant Activation Service Unlocker 2024.0.0.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6656) RedGiant Activation Service Unlocker 2024.0.0.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Users\admin\AppData\Local\Temp\is-ABU86.tmp\deep.exe | |||
| (PID) Process: | (6656) RedGiant Activation Service Unlocker 2024.0.0.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 7EAFD2E4545638C75F80F9D32CD4B62A19D354A17D4ABD3422067FA983766249 | |||
| (PID) Process: | (6340) deep.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | Owner |
Value: C4180000A15D9B55F7EBDA01 | |||
| (PID) Process: | (6340) deep.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | SessionHash |
Value: C8DEADBD265DC4991EBE12197B0FA503B084FA50F67FAF7F5707790CE82A91A7 | |||
| (PID) Process: | (6340) deep.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6340) deep.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\Red Giant\Services\Red Giant Service.exe | |||
| (PID) Process: | (6340) deep.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | RegFilesHash |
Value: 8E90B7A48DE59DC014864D0F0B45667C9BCBDCE42B0DA4B32E4978EC5BADA0D8 | |||
Executable files
10
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6656 | RedGiant Activation Service Unlocker 2024.0.0.tmp | C:\Users\admin\AppData\Local\Temp\is-ABU86.tmp\deep.exe | executable | |
MD5:876B237BF252BB46E32819B922DE24A6 | SHA256:5FF1D21792FFE57480A86281AFBE821A8001A665CF553EF804A709C5F5063385 | |||
| 6656 | RedGiant Activation Service Unlocker 2024.0.0.tmp | C:\ProgramData\Maxon\RLM\is-0TLHR.tmp | text | |
MD5:0F859D7B2D90DA5CD66AB4ABAED90E6E | SHA256:42C788E02A05E7718B81FB6F88E543E6A54753FA28F7FBD52555F0DE1687925F | |||
| 6340 | deep.tmp | C:\Users\admin\AppData\Local\Temp\is-M0450.tmp\_isetup\_iscrypt.dll | executable | |
MD5:A69559718AB506675E907FE49DEB71E9 | SHA256:2F6294F9AA09F59A574B5DCD33BE54E16B39377984F3D5658CDA44950FA0F8FC | |||
| 6656 | RedGiant Activation Service Unlocker 2024.0.0.tmp | C:\Users\admin\AppData\Local\Temp\is-ABU86.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 6632 | RedGiant Activation Service Unlocker 2024.0.0.exe | C:\Users\admin\AppData\Local\Temp\is-LIE7D.tmp\RedGiant Activation Service Unlocker 2024.0.0.tmp | executable | |
MD5:26506307EAE459A235710FB1117D11FC | SHA256:3105A5F6787096B4F7C4C5CE91948242EE615363BBD7A0A68D076C18EB26A4FD | |||
| 6656 | RedGiant Activation Service Unlocker 2024.0.0.tmp | C:\Users\admin\AppData\Local\Temp\is-ABU86.tmp\is-U77ED.tmp | executable | |
MD5:876B237BF252BB46E32819B922DE24A6 | SHA256:5FF1D21792FFE57480A86281AFBE821A8001A665CF553EF804A709C5F5063385 | |||
| 6340 | deep.tmp | C:\Users\admin\AppData\Local\Temp\is-M0450.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 7164 | deep.exe | C:\Users\admin\AppData\Local\Temp\is-2BOS2.tmp\deep.tmp | executable | |
MD5:26506307EAE459A235710FB1117D11FC | SHA256:3105A5F6787096B4F7C4C5CE91948242EE615363BBD7A0A68D076C18EB26A4FD | |||
| 6340 | deep.tmp | C:\Program Files\Red Giant\Services\is-QVPDV.tmp | executable | |
MD5:7876D882E7D1B0405E93C074850C8148 | SHA256:E4FCE708890F4FA470488EDC89D0453C38C381D3A00DCD6F382FE2115523B872 | |||
| 6340 | deep.tmp | C:\Program Files\Red Giant\Services\Red Giant Service.exe | executable | |
MD5:7876D882E7D1B0405E93C074850C8148 | SHA256:E4FCE708890F4FA470488EDC89D0453C38C381D3A00DCD6F382FE2115523B872 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
61
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5092 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5092 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6552 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
6184 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4056 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2472 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4056 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5336 | SearchApp.exe | 95.100.146.25:443 | www.bing.com | Akamai International B.V. | CZ | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5092 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |