| File name: | docx.rtf |
| Full analysis: | https://app.any.run/tasks/61b8f30d-645c-4d86-b524-039f7a942587 |
| Verdict: | Malicious activity |
| Analysis date: | January 09, 2024, 17:00:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/rtf |
| File info: | Rich Text Format data, version 1, ANSI, code page 936, default middle east language ID 1025 |
| MD5: | 7525AEB5667F0FEC28C64476AA134FEB |
| SHA1: | 7BE64405DEC5BCE177D2D11C32170F48E172CCCF |
| SHA256: | 40EA7507A340AC7F84AA1968D7C9EC863BCAC28414CAA447E7855CA9D1493BC9 |
| SSDEEP: | 12288:3eE/Q+qD4g10hZhUWOfinoeHJK5g9rScukPQcP7S92L3vc4UEWCZM:3eE/Q+Gb1IIinos8Pcu5cP77L3yHCq |
MALICIOUS
Unusual execution from MS Office
- WINWORD.EXE (PID: 2160)
SUSPICIOUS
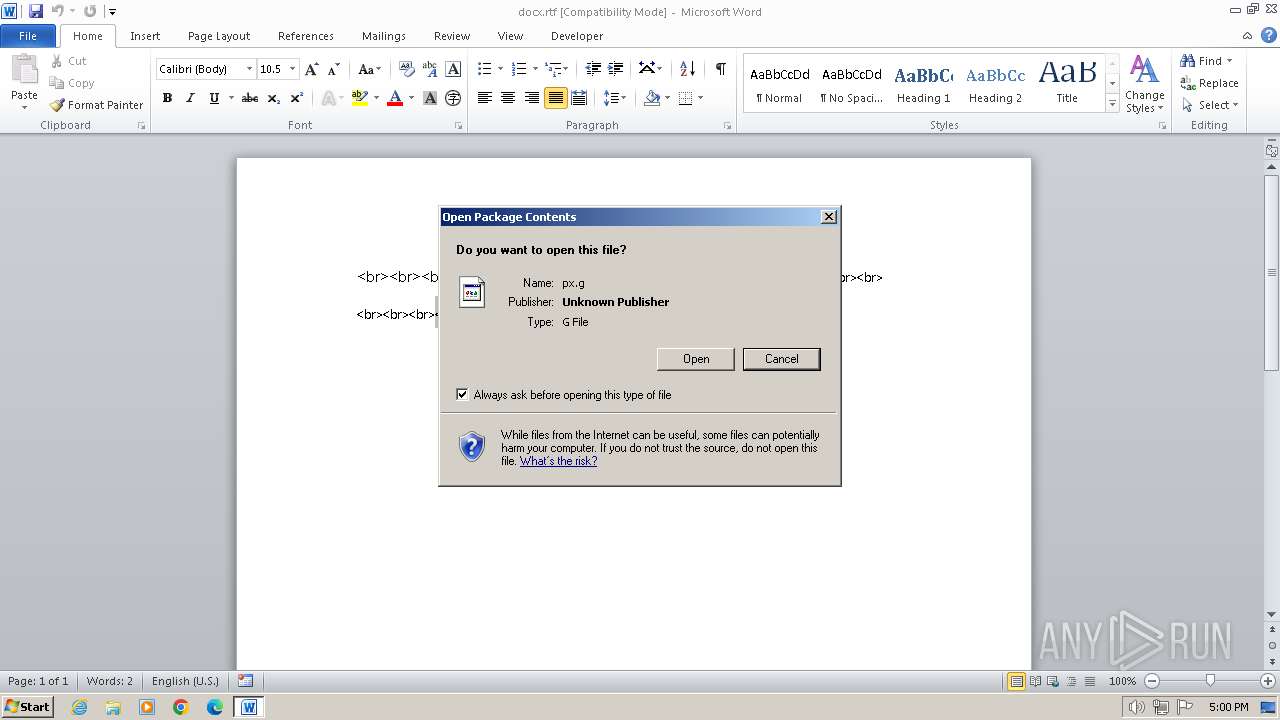
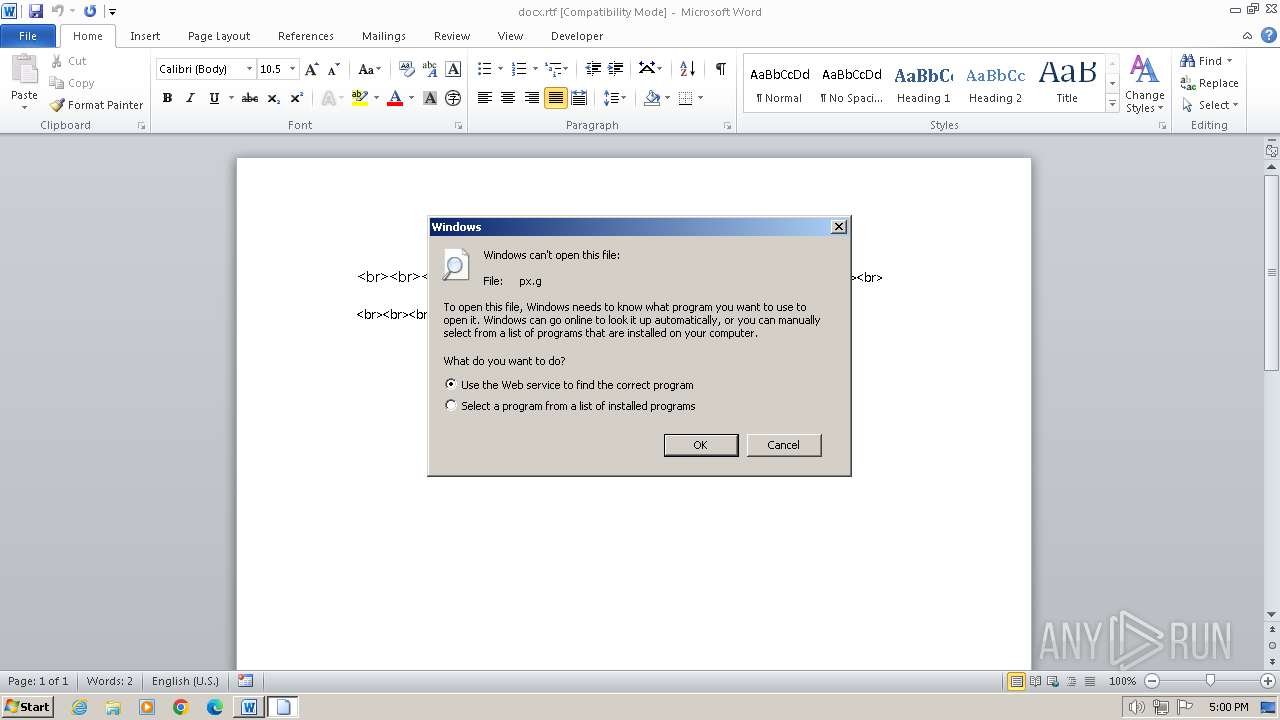
Uses RUNDLL32.EXE to load library
- WINWORD.EXE (PID: 2160)
INFO
Checks supported languages
- EQNEDT32.EXE (PID: 1308)
Reads the computer name
- EQNEDT32.EXE (PID: 1308)
Reads the machine GUID from the registry
- EQNEDT32.EXE (PID: 1308)
The process uses the downloaded file
- WINWORD.EXE (PID: 2160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rtf | | | Rich Text Format (100) |
|---|
EXIF
RTF
| Author: | CRAZY |
|---|---|
| LastModifiedBy: | CRAZY |
| CreateDate: | 2023:11:20 12:00:00 |
| ModifyDate: | 2023:11:20 12:01:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | 1 minute |
| Pages: | 1 |
| Words: | 1 |
| Characters: | 7 |
| CharactersWithSpaces: | 7 |
| InternalVersionNumber: | 85 |
Total processes
38
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
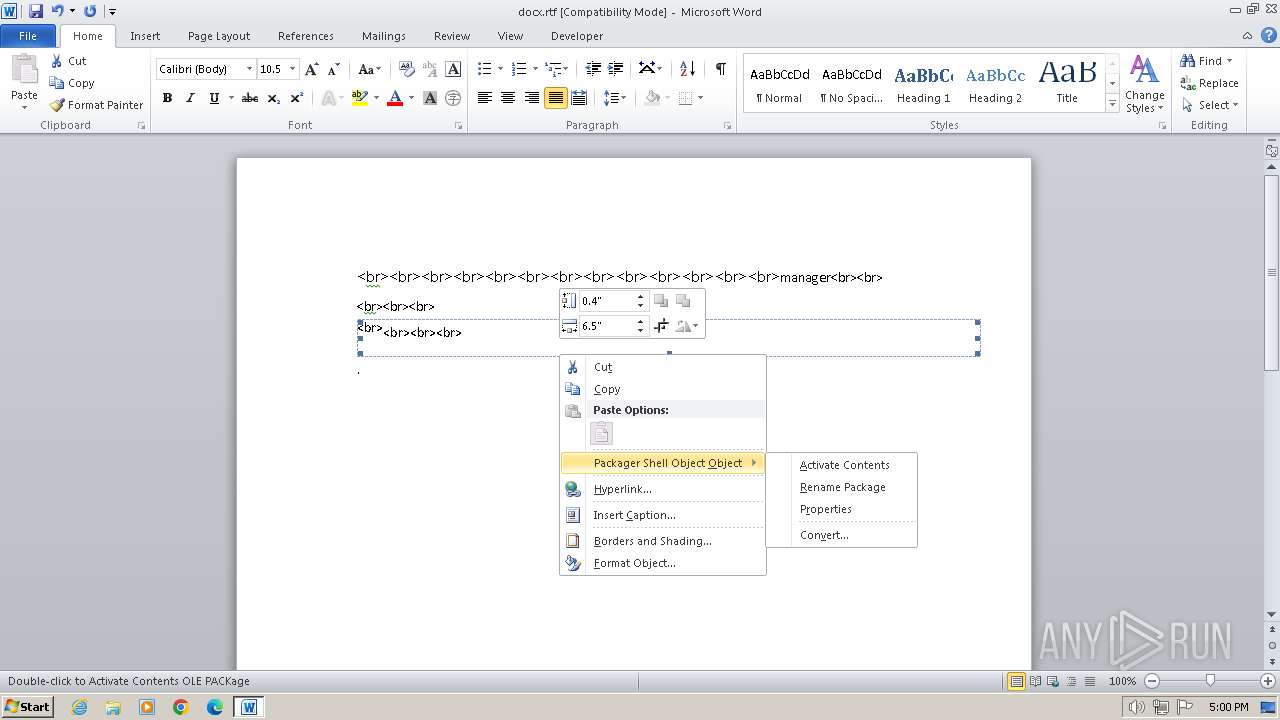
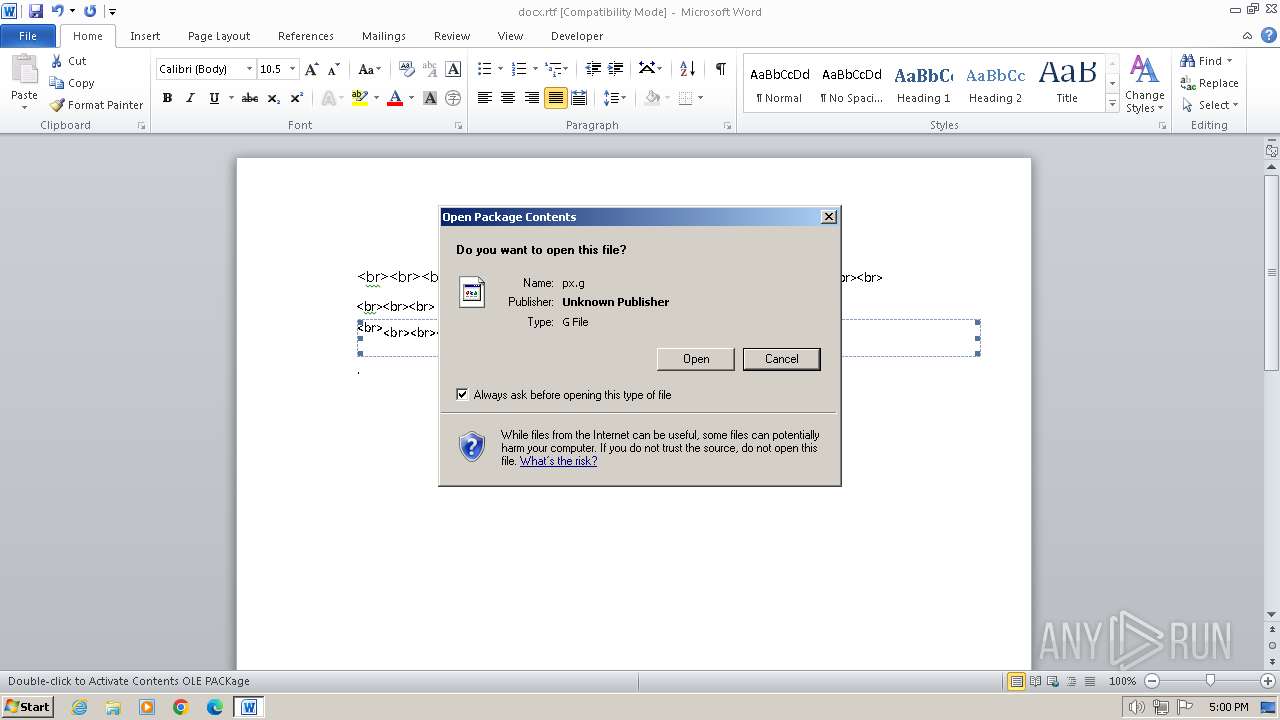
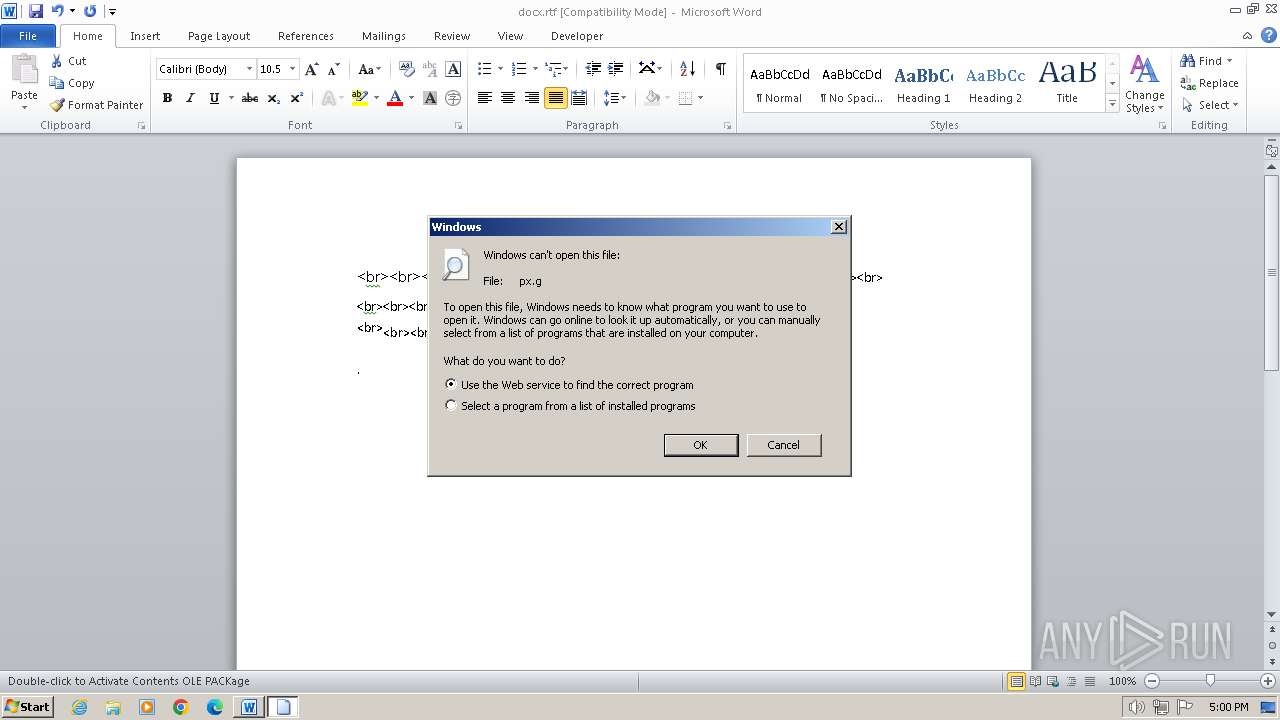
| 1040 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\px.g | C:\Windows\System32\rundll32.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1308 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | — | svchost.exe | |||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
| 1588 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\px.g | C:\Windows\System32\rundll32.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2160 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\docx.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
3 571
Read events
3 349
Write events
82
Delete events
140
Modification events
| (PID) Process: | (2160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (2160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (2160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (2160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (2160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (2160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (2160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (2160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (2160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
0
Suspicious files
6
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2160 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRF29E.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2160 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\UProof\ExcludeDictionaryEN0409.lex | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 2160 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$docx.rtf | binary | |
MD5:E5B32FCEE8322650BA12E7651E3E6C84 | SHA256:D4AE2C31ED300D8CF7F6503511AF697932D7DD34CACB3E196BD92FB5FE275192 | |||
| 2160 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\px.g | binary | |
MD5:519AA1FE07D6FFAD853D11DF9DBEC5B2 | SHA256:44E3BE69FEB0BF4FD3781484409988DB845AB92FDCF38E9E43181022471A676A | |||
| 2160 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{0E57F726-E4F8-412F-B948-D8A8A6E36EA8}.tmp | binary | |
MD5:40EF16A41601D36EC2F82B6E72C329FD | SHA256:6BBC6F29BC0D6D9B60D9336A89B7073117E5F1B74DC31157B8BE4960B027A568 | |||
| 2160 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{C2FD0AED-64A8-405B-A4A5-A8C6A8313ADC}.tmp | binary | |
MD5:42E450CB13D7FD96A1C4295C67FAA904 | SHA256:587B31A07CFA21D9214248EABDA454E968B418166EC67F1221403184484C5A04 | |||
| 2160 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\px.g:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 2160 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{3C82A351-8C8F-49A2-9F31-A83A1C612708}.tmp | binary | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
| 2160 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:061961556F0A3726D85224FB48AAFB20 | SHA256:8878D86122AE19A5D7D696CFA6A3C0DADE730379E744D6EEA757D79AB7AE5F89 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report