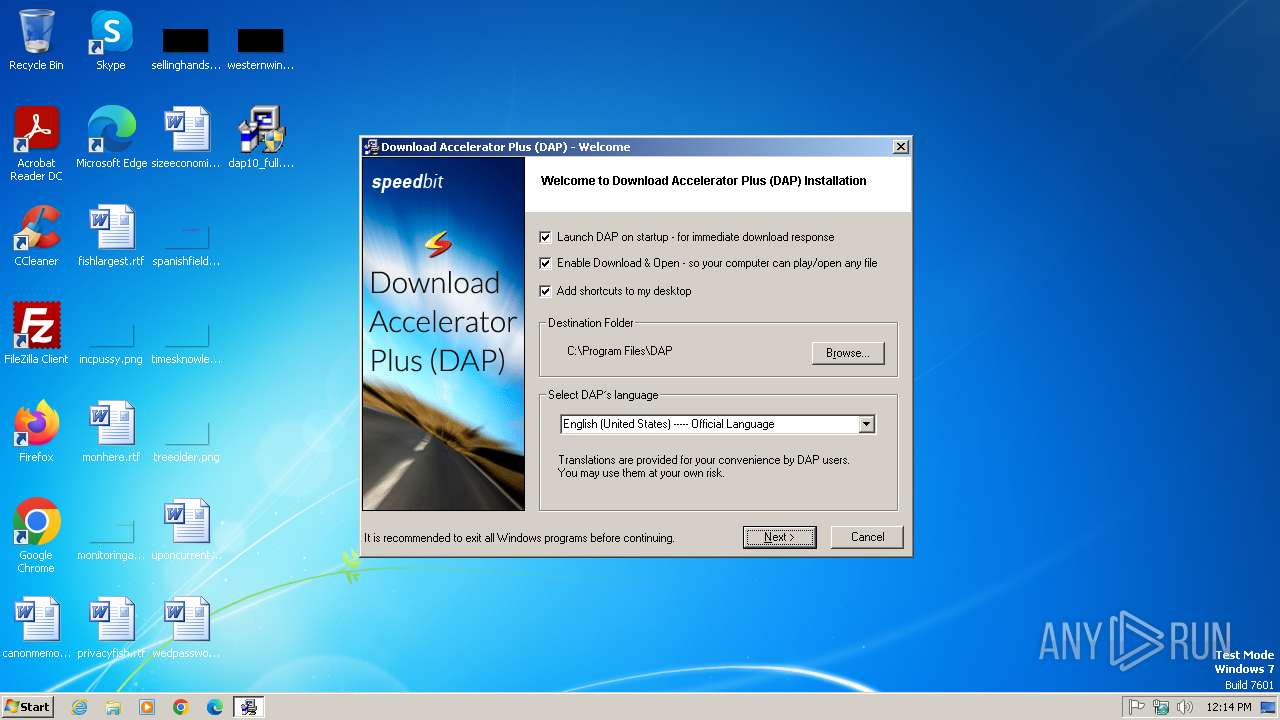
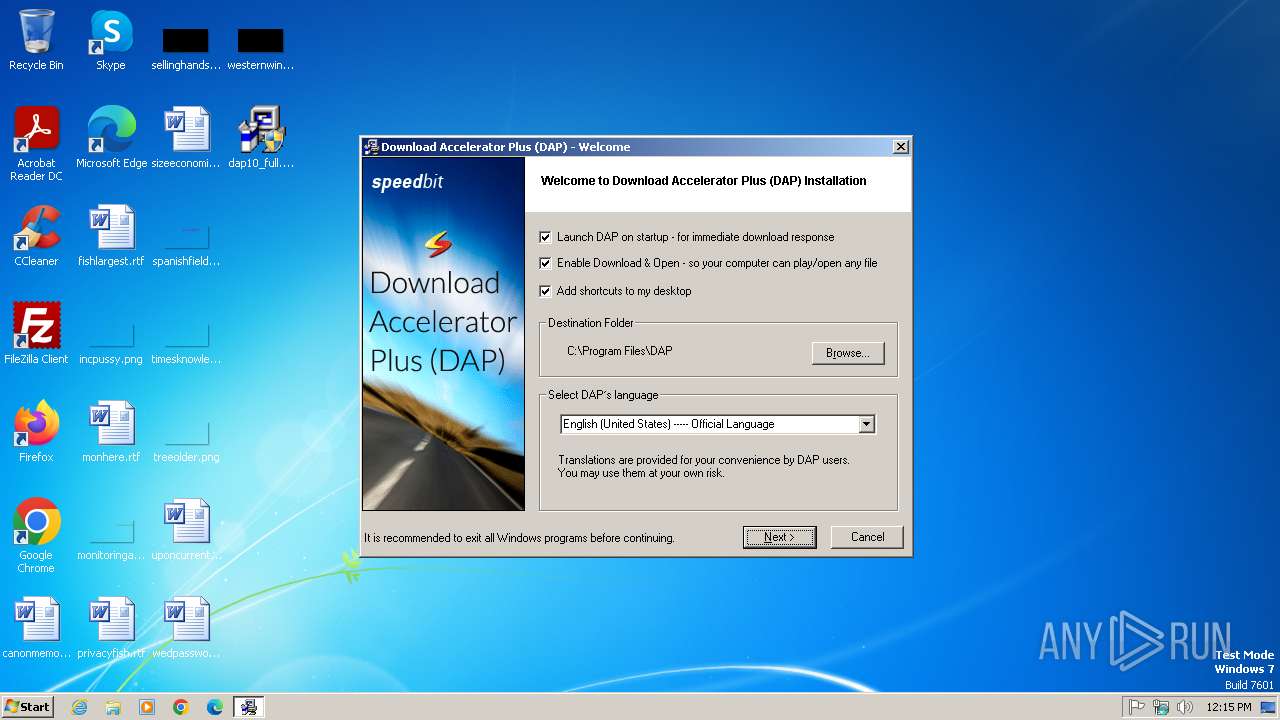
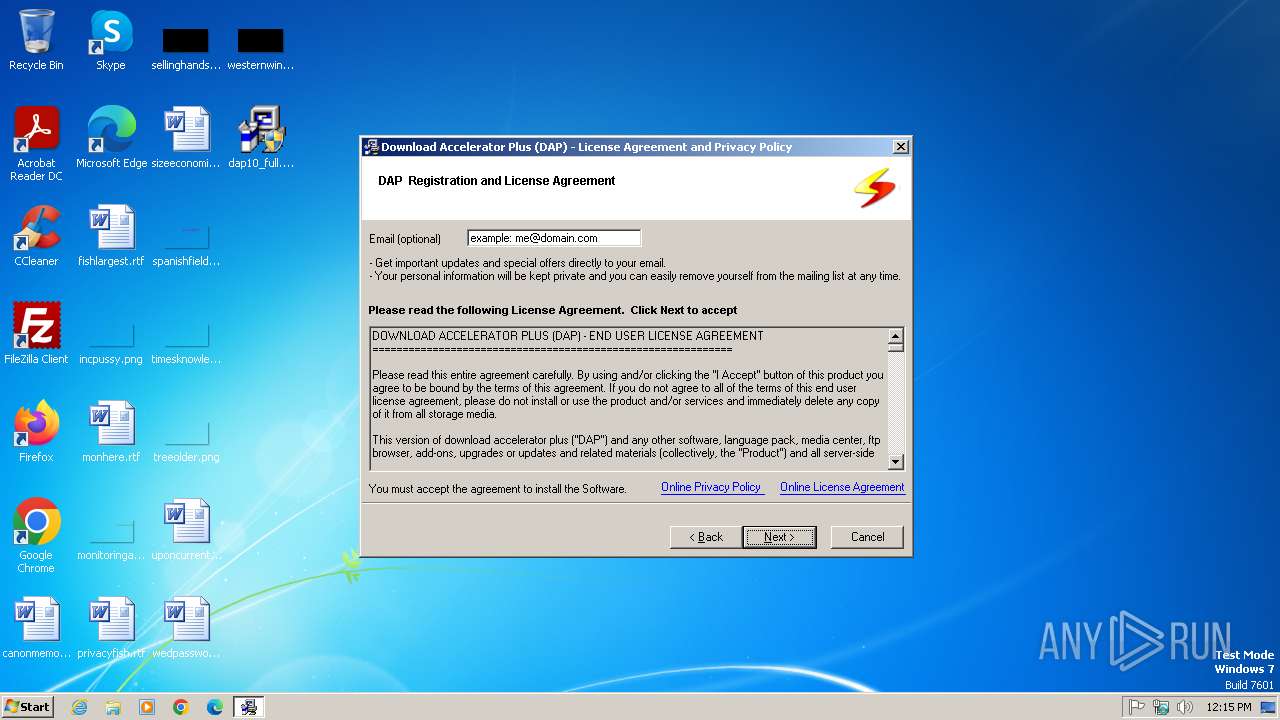
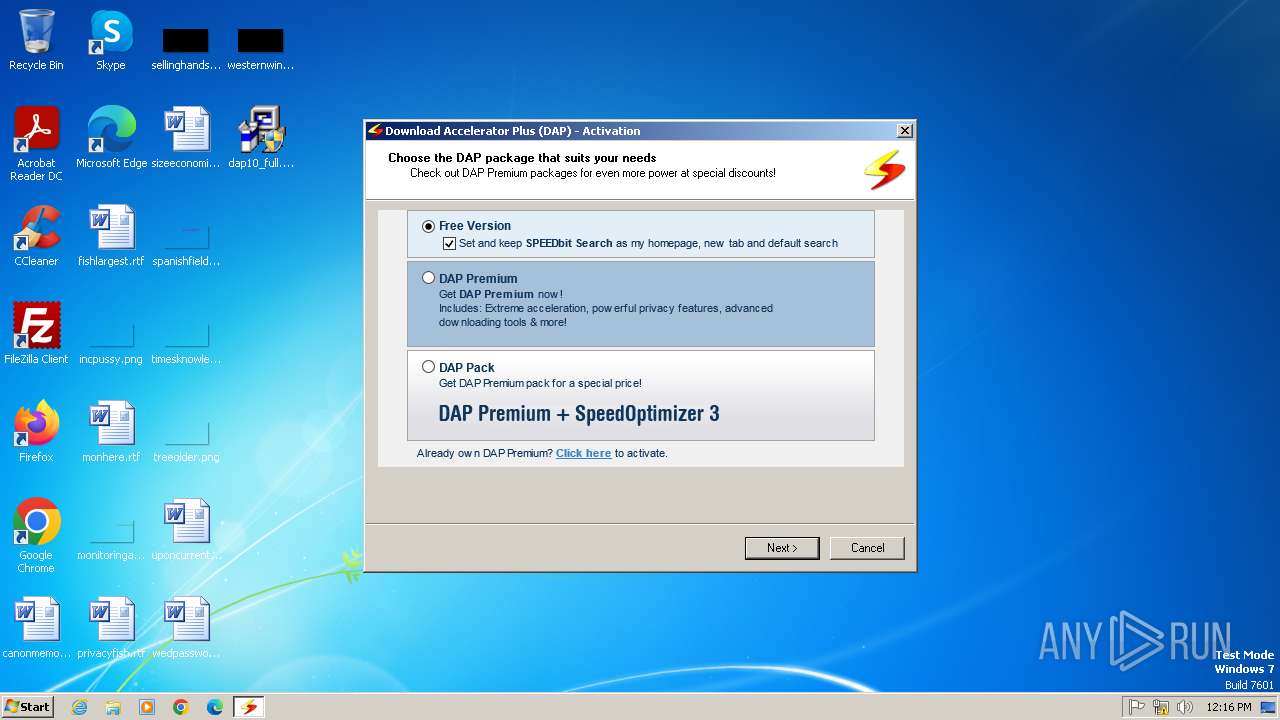
| File name: | dap10_full.exe |
| Full analysis: | https://app.any.run/tasks/b9aaa925-a709-4678-9db0-044068e4b9d1 |
| Verdict: | Malicious activity |
| Analysis date: | May 11, 2025, 11:14:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | BEFFCE53407EC8D165693BB13C006285 |
| SHA1: | F746A2BCAA846DE4494742F6CB39F78E15169FFF |
| SHA256: | 40B63673A293023AE00AB3FBAACD3B906E2F06DC4B09F110B1E002D16AE07B45 |
| SSDEEP: | 98304:sIJtekPclVVrzMQLGjTpD92oDJEHxQD5Rp2FnyOT3IlIFhcZ63owLgdDmmC40nOl:6ApfECCulzhwpesJaOOZYb2e79Y |
MALICIOUS
Executing a file with an untrusted certificate
- dap10_full.exe (PID: 576)
- dap10_full.exe (PID: 2060)
- vcredist_x86.exe (PID: 892)
- install.exe (PID: 2740)
- DAP.exe (PID: 3688)
Changes the autorun value in the registry
- DAP.exe (PID: 3688)
SUSPICIOUS
Executable content was dropped or overwritten
- dap10_full.exe (PID: 576)
- GLB2073.tmp (PID: 1748)
- vcredist_x86.exe (PID: 892)
- DAP.exe (PID: 3688)
Starts application with an unusual extension
- dap10_full.exe (PID: 576)
- GLB2073.tmp (PID: 1748)
Process drops legitimate windows executable
- GLB2073.tmp (PID: 1748)
- vcredist_x86.exe (PID: 892)
- msiexec.exe (PID: 328)
Reads the Internet Settings
- GLB2073.tmp (PID: 1748)
- DAP.exe (PID: 3688)
There is functionality for taking screenshot (YARA)
- dap10_full.exe (PID: 576)
- GLB2073.tmp (PID: 1748)
- DAP.exe (PID: 3688)
Starts a Microsoft application from unusual location
- vcredist_x86.exe (PID: 892)
Reads security settings of Internet Explorer
- GLB2073.tmp (PID: 1748)
- DAP.exe (PID: 3688)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 328)
Creates file in the systems drive root
- msiexec.exe (PID: 328)
The process drops C-runtime libraries
- msiexec.exe (PID: 328)
Creates a software uninstall entry
- GLB2073.tmp (PID: 1748)
Searches for installed software
- GLB2073.tmp (PID: 1748)
Changes Internet Explorer settings (feature browser emulation)
- GLB2073.tmp (PID: 1748)
Creates/Modifies COM task schedule object
- GLB2073.tmp (PID: 1748)
- GLJ20D2.tmp (PID: 3824)
- GLJ20D2.tmp (PID: 3224)
- DAP.exe (PID: 3688)
- GLJ20D2.tmp (PID: 3344)
Reads the BIOS version
- DAP.exe (PID: 3688)
Reads Microsoft Outlook installation path
- DAP.exe (PID: 3688)
Reads Internet Explorer settings
- DAP.exe (PID: 3688)
Detected use of alternative data streams (AltDS)
- DAP.exe (PID: 3688)
INFO
Checks supported languages
- dap10_full.exe (PID: 576)
- GLB2073.tmp (PID: 1748)
- vcredist_x86.exe (PID: 892)
- msiexec.exe (PID: 328)
- install.exe (PID: 2740)
- GLJ20D2.tmp (PID: 3344)
- GLJ20D2.tmp (PID: 3824)
- GLJ20D2.tmp (PID: 3224)
- DAP.exe (PID: 3688)
The sample compiled with english language support
- dap10_full.exe (PID: 576)
- GLB2073.tmp (PID: 1748)
- vcredist_x86.exe (PID: 892)
- msiexec.exe (PID: 328)
- DAP.exe (PID: 3688)
Create files in a temporary directory
- dap10_full.exe (PID: 576)
- GLB2073.tmp (PID: 1748)
- install.exe (PID: 2740)
- msiexec.exe (PID: 328)
- DAP.exe (PID: 3688)
Reads the computer name
- GLB2073.tmp (PID: 1748)
- vcredist_x86.exe (PID: 892)
- install.exe (PID: 2740)
- msiexec.exe (PID: 328)
- DAP.exe (PID: 3688)
Checks proxy server information
- GLB2073.tmp (PID: 1748)
- DAP.exe (PID: 3688)
Reads the machine GUID from the registry
- GLB2073.tmp (PID: 1748)
- vcredist_x86.exe (PID: 892)
- msiexec.exe (PID: 328)
- install.exe (PID: 2740)
- DAP.exe (PID: 3688)
Reads Environment values
- vcredist_x86.exe (PID: 892)
The sample compiled with spanish language support
- vcredist_x86.exe (PID: 892)
- msiexec.exe (PID: 328)
The sample compiled with Italian language support
- vcredist_x86.exe (PID: 892)
- msiexec.exe (PID: 328)
The sample compiled with korean language support
- vcredist_x86.exe (PID: 892)
- msiexec.exe (PID: 328)
The sample compiled with japanese language support
- vcredist_x86.exe (PID: 892)
- msiexec.exe (PID: 328)
The sample compiled with french language support
- vcredist_x86.exe (PID: 892)
- msiexec.exe (PID: 328)
The sample compiled with german language support
- vcredist_x86.exe (PID: 892)
- msiexec.exe (PID: 328)
The sample compiled with chinese language support
- vcredist_x86.exe (PID: 892)
- msiexec.exe (PID: 328)
Reads the software policy settings
- msiexec.exe (PID: 328)
Executable content was dropped or overwritten
- msiexec.exe (PID: 328)
Creates a software uninstall entry
- msiexec.exe (PID: 328)
Creates files in the program directory
- GLB2073.tmp (PID: 1748)
- DAP.exe (PID: 3688)
Creates files or folders in the user directory
- DAP.exe (PID: 3688)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Wise Installer executable (91.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (5.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.2) |
| .exe | | | Win32 Executable (generic) (0.8) |
| .exe | | | Generic Win/DOS Executable (0.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1999:04:08 20:24:47+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 512 |
| InitializedDataSize: | 10810368 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 10060.4455.0.0 |
| ProductVersionNumber: | 10060.4455.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | SpeedBit Ltd. |
| FileDescription: | DAP 10 |
| FileVersion: | 10060 (Build 259 |
| LegalCopyright: | speedbit |
| XXXXXXXXXXXXXXXXXXXXXXXXXXXX: | - |
Total processes
55
Monitored processes
10
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 576 | "C:\Users\admin\Desktop\dap10_full.exe" | C:\Users\admin\Desktop\dap10_full.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 892 | "C:\Users\admin\AppData\Local\Temp\VCREDI~1.EXE" /s /v/qn | C:\Users\admin\AppData\Local\Temp\vcredist_x86.exe | GLB2073.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2008 Redistributable Setup Exit code: 0 Version: 9.0.21022.08 Modules
| |||||||||||||||
| 1748 | C:\Users\admin\AppData\Local\Temp\GLB2073.tmp 4736 C:\Users\admin\Desktop\DAP10_~1.EXE | C:\Users\admin\AppData\Local\Temp\GLB2073.tmp | dap10_full.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2060 | "C:\Users\admin\Desktop\dap10_full.exe" | C:\Users\admin\Desktop\dap10_full.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2740 | c:\220258150006dd11f8ec16\.\install.exe /s /v/qn | C:\220258150006dd11f8ec16\install.exe | — | vcredist_x86.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: External Installer Exit code: 0 Version: 9.0.21022.8 built by: RTM Modules
| |||||||||||||||
| 3224 | "C:\Users\admin\AppData\Local\Temp\GLJ20D2.tmp" C:\Windows\System32\AniGIF.ocx | C:\Users\admin\AppData\Local\Temp\GLJ20D2.tmp | — | GLB2073.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3344 | "C:\Users\admin\AppData\Local\Temp\GLJ20D2.tmp" C:\Program Files\DAP\dexthlp.dll | C:\Users\admin\AppData\Local\Temp\GLJ20D2.tmp | — | GLB2073.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3688 | "C:\PROGRA~1\DAP\DAP.exe" /BUNDLE | C:\Program Files\DAP\DAP.exe | GLB2073.tmp | ||||||||||||
User: admin Company: Speedbit Ltd. Integrity Level: HIGH Description: Download Accelerator Plus (DAP) Version: 10.0.6.0 Modules
| |||||||||||||||
| 3824 | "C:\Users\admin\AppData\Local\Temp\GLJ20D2.tmp" C:\Program Files\DAP\LinkVerifier.dll | C:\Users\admin\AppData\Local\Temp\GLJ20D2.tmp | — | GLB2073.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
8 328
Read events
7 762
Write events
519
Delete events
47
Modification events
| (PID) Process: | (1748) GLB2073.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | DAP10 |
Value: | |||
| (PID) Process: | (1748) GLB2073.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\{D936E36D-C7AC-4F09-852F-5563AC3C1B9D} |
| Operation: | write | Name: | WpadDecisionReason |
Value: 1 | |||
| (PID) Process: | (1748) GLB2073.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\{D936E36D-C7AC-4F09-852F-5563AC3C1B9D} |
| Operation: | write | Name: | WpadDecisionTime |
Value: 0A7AAFDF65C2DB01 | |||
| (PID) Process: | (1748) GLB2073.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\{D936E36D-C7AC-4F09-852F-5563AC3C1B9D} |
| Operation: | write | Name: | WpadDecision |
Value: 0 | |||
| (PID) Process: | (1748) GLB2073.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\{D936E36D-C7AC-4F09-852F-5563AC3C1B9D} |
| Operation: | write | Name: | WpadNetworkName |
Value: Network 5 | |||
| (PID) Process: | (1748) GLB2073.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\{D936E36D-C7AC-4F09-852F-5563AC3C1B9D} |
| Operation: | delete value | Name: | WpadDetectedUrl |
Value: | |||
| (PID) Process: | (1748) GLB2073.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\d4-da-6d-3f-88-67 |
| Operation: | write | Name: | WpadDecisionReason |
Value: 1 | |||
| (PID) Process: | (1748) GLB2073.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\d4-da-6d-3f-88-67 |
| Operation: | write | Name: | WpadDecisionTime |
Value: 0A7AAFDF65C2DB01 | |||
| (PID) Process: | (1748) GLB2073.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\d4-da-6d-3f-88-67 |
| Operation: | write | Name: | WpadDecision |
Value: 0 | |||
| (PID) Process: | (1748) GLB2073.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\d4-da-6d-3f-88-67 |
| Operation: | delete value | Name: | WpadDetectedUrl |
Value: | |||
Executable files
160
Suspicious files
113
Text files
368
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1748 | GLB2073.tmp | C:\Users\admin\AppData\Local\Temp\DAPINST\~GLH0005.TMP | — | |
MD5:— | SHA256:— | |||
| 1748 | GLB2073.tmp | C:\Users\admin\AppData\Local\Temp\DAPINST\DapLang.cab | — | |
MD5:— | SHA256:— | |||
| 1748 | GLB2073.tmp | C:\Users\admin\AppData\Local\Temp\GLJ20D2.tmp | executable | |
MD5:6F608D264503796BEBD7CD66B687BE92 | SHA256:49833D2820AFB1D7409DFBD916480F2CDF5787D2E2D94166725BEB9064922D5D | |||
| 1748 | GLB2073.tmp | C:\Users\admin\AppData\Local\Temp\GLM24DB.tmp | executable | |
MD5:484CB68472473A1A84FF07996BB8C1F6 | SHA256:15BB390AF019D92E1D02771B02335FA360DB1BB34BCF4F0C72705027428F4FF1 | |||
| 1748 | GLB2073.tmp | C:\Users\admin\AppData\Local\Temp\SetupUtils6.dll | executable | |
MD5:70F40994C03E7F2431630276ECA81670 | SHA256:1F54ED892297B217A88FC03F120752474AAB83FED3F41A090937C2C094856257 | |||
| 1748 | GLB2073.tmp | C:\Users\admin\AppData\Local\Temp\~GLH0003.TMP | executable | |
MD5:70F40994C03E7F2431630276ECA81670 | SHA256:1F54ED892297B217A88FC03F120752474AAB83FED3F41A090937C2C094856257 | |||
| 1748 | GLB2073.tmp | C:\Users\admin\AppData\Local\Temp\~GLH0001.TMP | html | |
MD5:6A87B7A399327F4BCFF0572C96213C41 | SHA256:7DB7B0B22A32D8A6EAF04970C8D1E5F2A9CBF9FEDAFE2C5CB00D09B79BCCA9B8 | |||
| 1748 | GLB2073.tmp | C:\Users\admin\AppData\Local\Temp\dapextie.htm | html | |
MD5:6A87B7A399327F4BCFF0572C96213C41 | SHA256:7DB7B0B22A32D8A6EAF04970C8D1E5F2A9CBF9FEDAFE2C5CB00D09B79BCCA9B8 | |||
| 1748 | GLB2073.tmp | C:\Users\admin\AppData\Local\Temp\~GLH0000.TMP | executable | |
MD5:3B2E23D259394C701050486E642D14FA | SHA256:166D7156142F3EE09FA69EB617DD22E4FD248AA80A1AC08767DB6AD99A2705C1 | |||
| 1748 | GLB2073.tmp | C:\Users\admin\AppData\Local\Temp\GLF28D6.tmp | executable | |
MD5:3B2E23D259394C701050486E642D14FA | SHA256:166D7156142F3EE09FA69EB617DD22E4FD248AA80A1AC08767DB6AD99A2705C1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
12
DNS requests
5
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1748 | GLB2073.tmp | 173.239.4.35:80 | stub.speedbit.com | WEBAIR-INTERNET | US | whitelisted |
3688 | DAP.exe | 173.239.4.82:80 | client.speedbit.com | WEBAIR-INTERNET | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
stub.speedbit.com |
| whitelisted |
client.speedbit.com |
| whitelisted |
pix.speedbit.com |
| whitelisted |
Threats
Process | Message |
|---|---|
DAP.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
DAP.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
DAP.exe | [SbTracer::ReadConfiguration] ___Warning - No Trace Destination
|
DAP.exe | [SbTracer::ReadConfiguration] ___Warning - No Trace Backup
|
DAP.exe | [SbTracer::ReadConfiguration] ___Warning - No Trace Time Limit
|
DAP.exe | [SbTracer::ReadConfiguration] ___Warning - No Trace Time Stamp
|
DAP.exe | [SbTracer::ReadConfiguration] Trace Max Size: 3
|
DAP.exe | [SbTracer::ReadConfiguration] Done
|
DAP.exe | [SbTracer::RecursiveCreateDirectory] Directory: C:\ProgramData\SpeedBit\DAP\Log\
|
DAP.exe | [SbTracer::FormatFilePath] Log Path: C:\ProgramData\SpeedBit\DAP\Log\DAP_BETA.LOG
|