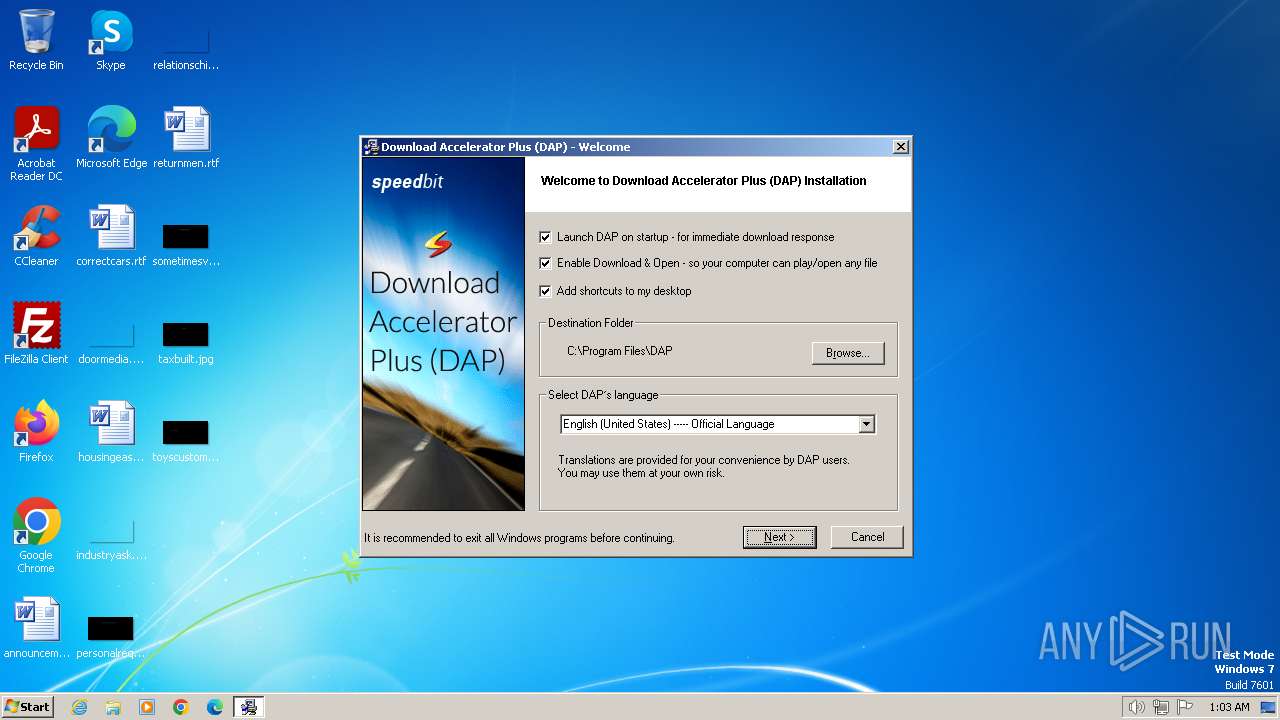
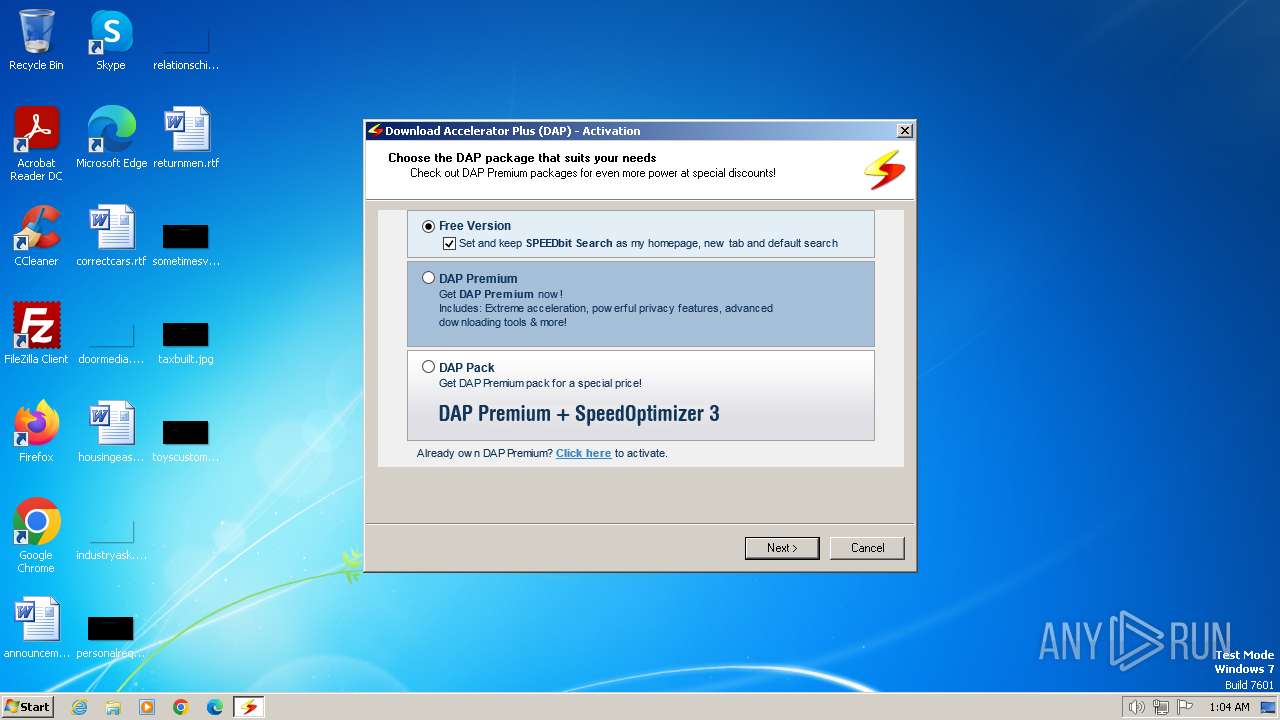
| File name: | dap10_full.exe |
| Full analysis: | https://app.any.run/tasks/ac422891-3031-459c-b263-5cfc5595fd80 |
| Verdict: | Malicious activity |
| Analysis date: | February 13, 2024, 01:03:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | BEFFCE53407EC8D165693BB13C006285 |
| SHA1: | F746A2BCAA846DE4494742F6CB39F78E15169FFF |
| SHA256: | 40B63673A293023AE00AB3FBAACD3B906E2F06DC4B09F110B1E002D16AE07B45 |
| SSDEEP: | 98304:sIJtekPclVVrzMQLGjTpD92oDJEHxQD5Rp2FnyOT3IlIFhcZ63owLgdDmmC40nOl:6ApfECCulzhwpesJaOOZYb2e79Y |
MALICIOUS
Creates a writable file in the system directory
- GLBF702.tmp (PID: 1776)
Drops the executable file immediately after the start
- GLBF702.tmp (PID: 1776)
- vcredist_x86.exe (PID: 1696)
- DAP.exe (PID: 3684)
- dap10_full.exe (PID: 2844)
- csc.exe (PID: 2780)
- csc.exe (PID: 2756)
- csc.exe (PID: 3920)
- csc.exe (PID: 1824)
- csc.exe (PID: 1596)
- csc.exe (PID: 3696)
- csc.exe (PID: 128)
- csc.exe (PID: 332)
- csc.exe (PID: 2832)
- csc.exe (PID: 1768)
- csc.exe (PID: 2152)
- csc.exe (PID: 2108)
- csc.exe (PID: 3956)
- csc.exe (PID: 1696)
- csc.exe (PID: 1956)
- csc.exe (PID: 3396)
- csc.exe (PID: 2860)
- csc.exe (PID: 2244)
- csc.exe (PID: 1900)
- csc.exe (PID: 3344)
- csc.exe (PID: 3284)
- csc.exe (PID: 1544)
- csc.exe (PID: 3612)
- csc.exe (PID: 3460)
- csc.exe (PID: 3888)
- csc.exe (PID: 3828)
- csc.exe (PID: 3116)
- csc.exe (PID: 2388)
- csc.exe (PID: 2624)
- csc.exe (PID: 3696)
- csc.exe (PID: 332)
- csc.exe (PID: 2192)
- csc.exe (PID: 2268)
Changes the autorun value in the registry
- DAP.exe (PID: 3684)
- GLBF702.tmp (PID: 1776)
- DAP.exe (PID: 3232)
Actions looks like stealing of personal data
- DAP.exe (PID: 3684)
- DAP.exe (PID: 3232)
Steals credentials from Web Browsers
- DAP.exe (PID: 3684)
Modifies files in the Chrome extension folder
- DAP.exe (PID: 3684)
Starts Visual C# compiler
- DAP.exe (PID: 3232)
SUSPICIOUS
Executable content was dropped or overwritten
- dap10_full.exe (PID: 2844)
- GLBF702.tmp (PID: 1776)
- vcredist_x86.exe (PID: 1696)
- DAP.exe (PID: 3684)
- csc.exe (PID: 2780)
- csc.exe (PID: 2756)
- csc.exe (PID: 3920)
- csc.exe (PID: 1824)
- csc.exe (PID: 1596)
- csc.exe (PID: 3696)
- csc.exe (PID: 128)
- csc.exe (PID: 2832)
- csc.exe (PID: 1768)
- csc.exe (PID: 332)
- csc.exe (PID: 2152)
- csc.exe (PID: 2108)
- csc.exe (PID: 1956)
- csc.exe (PID: 3956)
- csc.exe (PID: 1696)
- csc.exe (PID: 3396)
- csc.exe (PID: 2244)
- csc.exe (PID: 2860)
- csc.exe (PID: 1900)
- csc.exe (PID: 3612)
- csc.exe (PID: 3344)
- csc.exe (PID: 3284)
- csc.exe (PID: 1544)
- csc.exe (PID: 3460)
- csc.exe (PID: 3888)
- csc.exe (PID: 3828)
- csc.exe (PID: 3116)
- csc.exe (PID: 2388)
- csc.exe (PID: 2624)
- csc.exe (PID: 3696)
- csc.exe (PID: 332)
- csc.exe (PID: 2192)
- csc.exe (PID: 2268)
Starts application with an unusual extension
- dap10_full.exe (PID: 2844)
- GLBF702.tmp (PID: 1776)
Process drops legitimate windows executable
- GLBF702.tmp (PID: 1776)
- vcredist_x86.exe (PID: 1696)
Starts a Microsoft application from unusual location
- vcredist_x86.exe (PID: 1696)
Reads the Internet Settings
- GLBF702.tmp (PID: 1776)
- DAP.exe (PID: 3684)
- DAP.exe (PID: 3232)
Reads security settings of Internet Explorer
- GLBF702.tmp (PID: 1776)
- DAP.exe (PID: 3684)
- DAP.exe (PID: 3232)
Searches for installed software
- GLBF702.tmp (PID: 1776)
Creates/Modifies COM task schedule object
- GLJF742.tmp (PID: 2960)
- GLBF702.tmp (PID: 1776)
- GLJF742.tmp (PID: 2440)
- GLJF742.tmp (PID: 796)
- DAP.exe (PID: 3684)
Changes Internet Explorer settings (feature browser emulation)
- GLBF702.tmp (PID: 1776)
Creates a software uninstall entry
- GLBF702.tmp (PID: 1776)
Reads the BIOS version
- DAP.exe (PID: 3684)
- DAP.exe (PID: 3232)
- DAP.exe (PID: 1604)
- DAP.exe (PID: 2656)
- DAP.exe (PID: 4044)
- DAP.exe (PID: 2572)
- DAP.exe (PID: 1288)
- DAP.exe (PID: 560)
- DAP.exe (PID: 2780)
Detected use of alternative data streams (AltDS)
- DAP.exe (PID: 3684)
- DAP.exe (PID: 3232)
- DAP.exe (PID: 1604)
- DAP.exe (PID: 2656)
- DAP.exe (PID: 4044)
- DAP.exe (PID: 2572)
- DAP.exe (PID: 1288)
- DAP.exe (PID: 560)
- DAP.exe (PID: 2780)
Reads Internet Explorer settings
- DAP.exe (PID: 3684)
- DAP.exe (PID: 3232)
Reads Microsoft Outlook installation path
- DAP.exe (PID: 3684)
- DAP.exe (PID: 3232)
Changes the Home page of Internet Explorer
- DAP.exe (PID: 3684)
Changes the title of the Internet Explorer window
- DAP.exe (PID: 3684)
Reads Mozilla Firefox installation path
- DAP.exe (PID: 3684)
- DAP.exe (PID: 3232)
The process executes via Task Scheduler
- DAP.exe (PID: 3232)
Checks Windows Trust Settings
- DAP.exe (PID: 3232)
Reads settings of System Certificates
- DAP.exe (PID: 3232)
Uses .NET C# to load dll
- DAP.exe (PID: 3232)
INFO
Checks supported languages
- dap10_full.exe (PID: 2844)
- GLBF702.tmp (PID: 1776)
- vcredist_x86.exe (PID: 1696)
- GLJF742.tmp (PID: 2960)
- install.exe (PID: 2860)
- GLJF742.tmp (PID: 2440)
- DAP.exe (PID: 3684)
- GLJF742.tmp (PID: 796)
- unelevate.EXE (PID: 2808)
- DAP.exe (PID: 3232)
- csc.exe (PID: 2780)
- cvtres.exe (PID: 1848)
- csc.exe (PID: 2756)
- cvtres.exe (PID: 1888)
- csc.exe (PID: 3920)
- cvtres.exe (PID: 3932)
- csc.exe (PID: 1824)
- cvtres.exe (PID: 3704)
- csc.exe (PID: 1596)
- cvtres.exe (PID: 3820)
- csc.exe (PID: 3696)
- csc.exe (PID: 128)
- cvtres.exe (PID: 2020)
- csc.exe (PID: 332)
- cvtres.exe (PID: 1572)
- cvtres.exe (PID: 1428)
- csc.exe (PID: 2832)
- cvtres.exe (PID: 2564)
- csc.exe (PID: 1768)
- cvtres.exe (PID: 2488)
- csc.exe (PID: 2108)
- DAP.exe (PID: 1604)
- csc.exe (PID: 2152)
- cvtres.exe (PID: 1124)
- csc.exe (PID: 1956)
- cvtres.exe (PID: 1820)
- DAP.exe (PID: 2656)
- cvtres.exe (PID: 1020)
- csc.exe (PID: 3956)
- cvtres.exe (PID: 2808)
- csc.exe (PID: 1696)
- cvtres.exe (PID: 1072)
- csc.exe (PID: 3396)
- DAP.exe (PID: 4044)
- cvtres.exe (PID: 3700)
- csc.exe (PID: 2860)
- cvtres.exe (PID: 2788)
- csc.exe (PID: 2244)
- csc.exe (PID: 3344)
- cvtres.exe (PID: 3000)
- cvtres.exe (PID: 2040)
- csc.exe (PID: 1900)
- cvtres.exe (PID: 2756)
- cvtres.exe (PID: 1220)
- csc.exe (PID: 3612)
- cvtres.exe (PID: 2724)
- csc.exe (PID: 1544)
- cvtres.exe (PID: 2304)
- csc.exe (PID: 3460)
- csc.exe (PID: 3284)
- cvtres.exe (PID: 2996)
- csc.exe (PID: 3888)
- cvtres.exe (PID: 560)
- csc.exe (PID: 3828)
- cvtres.exe (PID: 3928)
- csc.exe (PID: 3116)
- cvtres.exe (PID: 2184)
- csc.exe (PID: 3696)
- cvtres.exe (PID: 2332)
- cvtres.exe (PID: 2128)
- csc.exe (PID: 2624)
- cvtres.exe (PID: 2988)
- csc.exe (PID: 2388)
- cvtres.exe (PID: 664)
- csc.exe (PID: 2192)
- cvtres.exe (PID: 2024)
- csc.exe (PID: 2268)
- csc.exe (PID: 332)
- cvtres.exe (PID: 1820)
- DAP.exe (PID: 2572)
- DAP.exe (PID: 2780)
- DAP.exe (PID: 1288)
- DAP.exe (PID: 560)
Create files in a temporary directory
- dap10_full.exe (PID: 2844)
- GLBF702.tmp (PID: 1776)
- install.exe (PID: 2860)
- DAP.exe (PID: 3684)
- DAP.exe (PID: 3232)
- cvtres.exe (PID: 1848)
- cvtres.exe (PID: 1888)
- cvtres.exe (PID: 3932)
- cvtres.exe (PID: 3704)
- cvtres.exe (PID: 3820)
- cvtres.exe (PID: 2020)
- cvtres.exe (PID: 1572)
- cvtres.exe (PID: 1428)
- cvtres.exe (PID: 2488)
- cvtres.exe (PID: 1124)
- cvtres.exe (PID: 1020)
- cvtres.exe (PID: 1820)
- cvtres.exe (PID: 2808)
- cvtres.exe (PID: 1072)
- cvtres.exe (PID: 2788)
- cvtres.exe (PID: 3700)
- cvtres.exe (PID: 3000)
- cvtres.exe (PID: 2040)
- cvtres.exe (PID: 2564)
- cvtres.exe (PID: 2756)
- cvtres.exe (PID: 1220)
- cvtres.exe (PID: 2724)
- cvtres.exe (PID: 2304)
- cvtres.exe (PID: 2996)
- cvtres.exe (PID: 560)
- cvtres.exe (PID: 3928)
- cvtres.exe (PID: 2184)
- cvtres.exe (PID: 2332)
- cvtres.exe (PID: 2128)
- cvtres.exe (PID: 2988)
- cvtres.exe (PID: 664)
- cvtres.exe (PID: 2024)
- cvtres.exe (PID: 1820)
Checks proxy server information
- GLBF702.tmp (PID: 1776)
- DAP.exe (PID: 3684)
- DAP.exe (PID: 3232)
Reads the computer name
- GLBF702.tmp (PID: 1776)
- vcredist_x86.exe (PID: 1696)
- install.exe (PID: 2860)
- DAP.exe (PID: 3684)
- unelevate.EXE (PID: 2808)
- DAP.exe (PID: 3232)
- DAP.exe (PID: 1604)
- DAP.exe (PID: 2656)
- DAP.exe (PID: 4044)
- DAP.exe (PID: 2572)
- DAP.exe (PID: 2780)
- DAP.exe (PID: 1288)
- DAP.exe (PID: 560)
Reads Environment values
- vcredist_x86.exe (PID: 1696)
- DAP.exe (PID: 3232)
Reads the machine GUID from the registry
- GLBF702.tmp (PID: 1776)
- vcredist_x86.exe (PID: 1696)
- install.exe (PID: 2860)
- DAP.exe (PID: 3684)
- DAP.exe (PID: 3232)
- csc.exe (PID: 2780)
- cvtres.exe (PID: 1848)
- csc.exe (PID: 2756)
- cvtres.exe (PID: 1888)
- csc.exe (PID: 3920)
- cvtres.exe (PID: 3932)
- csc.exe (PID: 1824)
- cvtres.exe (PID: 3704)
- csc.exe (PID: 1596)
- cvtres.exe (PID: 3820)
- csc.exe (PID: 3696)
- csc.exe (PID: 128)
- cvtres.exe (PID: 2020)
- csc.exe (PID: 332)
- cvtres.exe (PID: 1572)
- cvtres.exe (PID: 1428)
- csc.exe (PID: 2832)
- csc.exe (PID: 1768)
- cvtres.exe (PID: 2488)
- cvtres.exe (PID: 2564)
- cvtres.exe (PID: 1124)
- csc.exe (PID: 2108)
- DAP.exe (PID: 1604)
- csc.exe (PID: 2152)
- csc.exe (PID: 1956)
- cvtres.exe (PID: 1820)
- DAP.exe (PID: 2656)
- cvtres.exe (PID: 1020)
- csc.exe (PID: 3956)
- cvtres.exe (PID: 2808)
- csc.exe (PID: 1696)
- cvtres.exe (PID: 1072)
- csc.exe (PID: 3396)
- cvtres.exe (PID: 3700)
- DAP.exe (PID: 4044)
- csc.exe (PID: 2860)
- cvtres.exe (PID: 2788)
- csc.exe (PID: 2244)
- cvtres.exe (PID: 3000)
- csc.exe (PID: 3344)
- cvtres.exe (PID: 2040)
- csc.exe (PID: 1900)
- cvtres.exe (PID: 2756)
- csc.exe (PID: 3612)
- cvtres.exe (PID: 1220)
- csc.exe (PID: 3284)
- cvtres.exe (PID: 2724)
- cvtres.exe (PID: 2304)
- csc.exe (PID: 1544)
- csc.exe (PID: 3460)
- cvtres.exe (PID: 2996)
- csc.exe (PID: 3888)
- cvtres.exe (PID: 560)
- csc.exe (PID: 3828)
- cvtres.exe (PID: 3928)
- csc.exe (PID: 3116)
- cvtres.exe (PID: 2184)
- csc.exe (PID: 3696)
- cvtres.exe (PID: 2332)
- csc.exe (PID: 2388)
- csc.exe (PID: 2624)
- cvtres.exe (PID: 2128)
- cvtres.exe (PID: 2988)
- cvtres.exe (PID: 664)
- csc.exe (PID: 2192)
- cvtres.exe (PID: 2024)
- csc.exe (PID: 332)
- cvtres.exe (PID: 1820)
- DAP.exe (PID: 2572)
- DAP.exe (PID: 2780)
- csc.exe (PID: 2268)
- DAP.exe (PID: 1288)
- DAP.exe (PID: 560)
Creates files in the program directory
- GLBF702.tmp (PID: 1776)
- DAP.exe (PID: 3684)
- DAP.exe (PID: 3232)
- csc.exe (PID: 2756)
- csc.exe (PID: 3920)
- csc.exe (PID: 1824)
- csc.exe (PID: 1596)
- csc.exe (PID: 3696)
- csc.exe (PID: 2780)
- csc.exe (PID: 128)
- csc.exe (PID: 332)
- csc.exe (PID: 2832)
- csc.exe (PID: 1768)
- csc.exe (PID: 2152)
- csc.exe (PID: 2108)
- csc.exe (PID: 1956)
- csc.exe (PID: 3956)
- csc.exe (PID: 1696)
- csc.exe (PID: 3396)
- csc.exe (PID: 2244)
- csc.exe (PID: 3344)
- csc.exe (PID: 1900)
- csc.exe (PID: 3612)
- csc.exe (PID: 3284)
- csc.exe (PID: 1544)
- csc.exe (PID: 3888)
- csc.exe (PID: 3828)
- csc.exe (PID: 3460)
- csc.exe (PID: 3116)
- csc.exe (PID: 3696)
- csc.exe (PID: 2388)
- csc.exe (PID: 2624)
- csc.exe (PID: 2192)
- csc.exe (PID: 2860)
- csc.exe (PID: 332)
- csc.exe (PID: 2268)
Creates files or folders in the user directory
- DAP.exe (PID: 3684)
- DAP.exe (PID: 3232)
Application launched itself
- msedge.exe (PID: 3504)
- msedge.exe (PID: 3808)
Manual execution by a user
- msedge.exe (PID: 3808)
- DAP.exe (PID: 1604)
- DAP.exe (PID: 2656)
- DAP.exe (PID: 4044)
- DAP.exe (PID: 2572)
- DAP.exe (PID: 2780)
- DAP.exe (PID: 560)
- DAP.exe (PID: 1288)
Reads the software policy settings
- DAP.exe (PID: 3232)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Wise Installer executable (91.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (5.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.2) |
| .exe | | | Win32 Executable (generic) (0.8) |
| .exe | | | Generic Win/DOS Executable (0.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1999:04:08 20:24:47+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 512 |
| InitializedDataSize: | 10810368 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 10060.4455.0.0 |
| ProductVersionNumber: | 10060.4455.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | SpeedBit Ltd. |
| FileDescription: | DAP 10 |
| FileVersion: | 10060 (Build 259 |
| LegalCopyright: | speedbit |
| XXXXXXXXXXXXXXXXXXXXXXXXXXXX: | - |
Total processes
196
Monitored processes
109
Malicious processes
12
Suspicious processes
33
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Windows\Microsoft.NET\Framework\v3.5\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\su7rdhf2.cmdline" | C:\Windows\Microsoft.NET\Framework\v3.5\csc.exe | DAP.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 3.5.30729.5420 built by: Win7SP1 Modules
| |||||||||||||||
| 332 | "C:\Windows\Microsoft.NET\Framework\v3.5\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\duw-964t.cmdline" | C:\Windows\Microsoft.NET\Framework\v3.5\csc.exe | DAP.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 3.5.30729.5420 built by: Win7SP1 Modules
| |||||||||||||||
| 332 | "C:\Windows\Microsoft.NET\Framework\v3.5\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\9tuuh7on.cmdline" | C:\Windows\Microsoft.NET\Framework\v3.5\csc.exe | DAP.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 3.5.30729.5420 built by: Win7SP1 Modules
| |||||||||||||||
| 560 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESE631.tmp" "c:\ProgramData\SpeedBit\DAP\Plugins\189AE673-13C1-4133-A470-8C4DDD1ACB8C\1.0.1.3_0\CSCE5F1.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.5003 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 560 | "C:\Program Files\DAP\DAP.exe" | C:\Program Files\DAP\DAP.exe | explorer.exe | ||||||||||||
User: admin Company: Speedbit Ltd. Integrity Level: MEDIUM Description: Download Accelerator Plus (DAP) Exit code: 1 Version: 10.0.6.0 Modules
| |||||||||||||||
| 664 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESF256.tmp" "c:\ProgramData\SpeedBit\DAP\Plugins\189AE673-13C1-4133-A470-8C4DDD1ACB8C\1.0.1.3_0\CSCF217.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.5003 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 796 | "C:\Users\admin\AppData\Local\Temp\GLJF742.tmp" C:\Windows\System32\AniGIF.ocx | C:\Users\admin\AppData\Local\Temp\GLJF742.tmp | — | GLBF702.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1020 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESCC7F.tmp" "c:\ProgramData\SpeedBit\DAP\Plugins\189AE673-13C1-4133-A470-8C4DDD1ACB8C\1.0.1.3_0\CSCCC10.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.5003 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 1072 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESD180.tmp" "c:\ProgramData\SpeedBit\DAP\Plugins\189AE673-13C1-4133-A470-8C4DDD1ACB8C\1.0.1.3_0\CSCD111.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.5003 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 1124 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESCA5C.tmp" "c:\ProgramData\SpeedBit\DAP\Plugins\189AE673-13C1-4133-A470-8C4DDD1ACB8C\1.0.1.3_0\CSCC6D0.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.5003 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
Total events
34 123
Read events
31 896
Write events
2 143
Delete events
84
Modification events
| (PID) Process: | (1776) GLBF702.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | DAP10 |
Value: | |||
| (PID) Process: | (1776) GLBF702.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1776) GLBF702.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (1776) GLBF702.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (1776) GLBF702.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (1776) GLBF702.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
| (PID) Process: | (1776) GLBF702.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005C010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1776) GLBF702.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1776) GLBF702.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1776) GLBF702.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
159
Suspicious files
195
Text files
525
Unknown types
85
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1776 | GLBF702.tmp | C:\Users\admin\AppData\Local\Temp\DAPINST\~GLH0005.TMP | — | |
MD5:— | SHA256:— | |||
| 1776 | GLBF702.tmp | C:\Users\admin\AppData\Local\Temp\DAPINST\DapLang.cab | — | |
MD5:— | SHA256:— | |||
| 1776 | GLBF702.tmp | C:\Users\admin\AppData\Local\Temp\GLJF742.tmp | executable | |
MD5:6F608D264503796BEBD7CD66B687BE92 | SHA256:49833D2820AFB1D7409DFBD916480F2CDF5787D2E2D94166725BEB9064922D5D | |||
| 1776 | GLBF702.tmp | C:\Users\admin\AppData\Local\Temp\GLKF946.tmp | executable | |
MD5:9839938C16AF50B43B78B073F447A1D6 | SHA256:5A0BEBB30C025B020C0FECB56B6D5C298235DFED1BD887E64237BD0CFCC3DC8B | |||
| 1776 | GLBF702.tmp | C:\Users\admin\AppData\Local\Temp\GLFFF45.tmp | executable | |
MD5:3B2E23D259394C701050486E642D14FA | SHA256:166D7156142F3EE09FA69EB617DD22E4FD248AA80A1AC08767DB6AD99A2705C1 | |||
| 1776 | GLBF702.tmp | C:\Users\admin\AppData\Local\Temp\cabex.dll | executable | |
MD5:0A70935AC8BD68BB40D649849CE0EBEF | SHA256:BCC5DB00EA6FD4E83D04D7A26D77EC85D084BE3F80697FA1DA8CF0776F194A29 | |||
| 1776 | GLBF702.tmp | C:\Users\admin\AppData\Local\Temp\DAPINST\DapRemove.exe | executable | |
MD5:8BF069204E5C44215B5F41D43EC8B349 | SHA256:25A3DA198CA0A069518A5D3B7F6235F1CEE76E484F854A61C9136B3C940E0BD9 | |||
| 1776 | GLBF702.tmp | C:\Users\admin\AppData\Local\Temp\SetupUtils6.dll | executable | |
MD5:70F40994C03E7F2431630276ECA81670 | SHA256:1F54ED892297B217A88FC03F120752474AAB83FED3F41A090937C2C094856257 | |||
| 1776 | GLBF702.tmp | C:\Users\admin\AppData\Local\Temp\GLMFB4B.tmp | executable | |
MD5:484CB68472473A1A84FF07996BB8C1F6 | SHA256:15BB390AF019D92E1D02771B02335FA360DB1BB34BCF4F0C72705027428F4FF1 | |||
| 1776 | GLBF702.tmp | C:\Users\admin\AppData\Local\Temp\~GLH0001.TMP | html | |
MD5:6A87B7A399327F4BCFF0572C96213C41 | SHA256:7DB7B0B22A32D8A6EAF04970C8D1E5F2A9CBF9FEDAFE2C5CB00D09B79BCCA9B8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
40
DNS requests
26
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1776 | GLBF702.tmp | GET | 200 | 173.239.4.35:80 | http://stub.speedbit.com/p.aspx?e=/9ZmISdorEtde4FcBjAa0KamUw0o8OGNLUMNINn3bfXtNQqpF/SBTguiJVZAAvOypqUgV2pBp/DubYXFLcRRvxnzKW1HDIvRTPnfxsC1sLOOPx8smASgOBInS1jzS5Zd | unknown | — | — | unknown |
3232 | DAP.exe | GET | 301 | 142.250.187.110:80 | http://www.youtube.com/favicon.ico | unknown | html | 232 b | unknown |
3232 | DAP.exe | GET | 404 | 208.91.196.152:80 | http://shareflare.net/favicon.ico | unknown | text | 10 b | unknown |
1776 | GLBF702.tmp | GET | 200 | 173.239.4.35:80 | http://stub.speedbit.com/p.aspx?e=N6dOqWm8Q95QKVDNhYrVZ55IqVYgXfBJ4XLIs55rVmXw5kzsCdcwEil0KR7+wQEAXw4PLh17YOgFj1J4iNn3pf/xnj2M+81rebpSlsRkhCxMB7SVxwb0S45MWp8MfmX99JgsGI2WhWE= | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1776 | GLBF702.tmp | 173.239.4.35:80 | stub.speedbit.com | WEBAIR-INTERNET | US | unknown |
3684 | DAP.exe | 173.239.4.82:80 | client.speedbit.com | WEBAIR-INTERNET | US | unknown |
3684 | DAP.exe | 173.239.4.63:80 | www.speedbit.com | WEBAIR-INTERNET | US | unknown |
3808 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
3432 | msedge.exe | 173.239.4.63:80 | www.speedbit.com | WEBAIR-INTERNET | US | unknown |
3432 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3432 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
stub.speedbit.com |
| unknown |
client.speedbit.com |
| unknown |
dns.msftncsi.com |
| shared |
pix.speedbit.com |
| unknown |
update.speedbit.com |
| unknown |
www.speedbit.com |
| malicious |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
newuser.speedbit.com |
| unknown |
online.speedbit.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1776 | GLBF702.tmp | Misc activity | ET POLICY Wise Solutions Install Reporting via HTTP - User Agent (Wise) |
1776 | GLBF702.tmp | Misc activity | ET POLICY Wise Solutions Install Reporting via HTTP - User Agent (Wise) |
Process | Message |
|---|---|
DAP.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
DAP.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
DAP.exe | [SbTracer::UpdateAllParameters]
|
DAP.exe | [SbTracer::ReadConfiguration] Trace Level: 3
|
DAP.exe | [SbTracer::ReadConfiguration] ___Warning - No Trace Destination
|
DAP.exe | [SbTracer::ReadConfiguration] ___Warning - No Trace Backup
|
DAP.exe | [SbTracer::ReadConfiguration] ___Warning - No Trace Time Limit
|
DAP.exe | [SbTracer::ReadConfiguration] ___Warning - No Trace Time Stamp
|
DAP.exe | [SbTracer::ReadConfiguration] Trace Max Size: 3
|
DAP.exe | [SbTracer::ReadConfiguration] Done
|