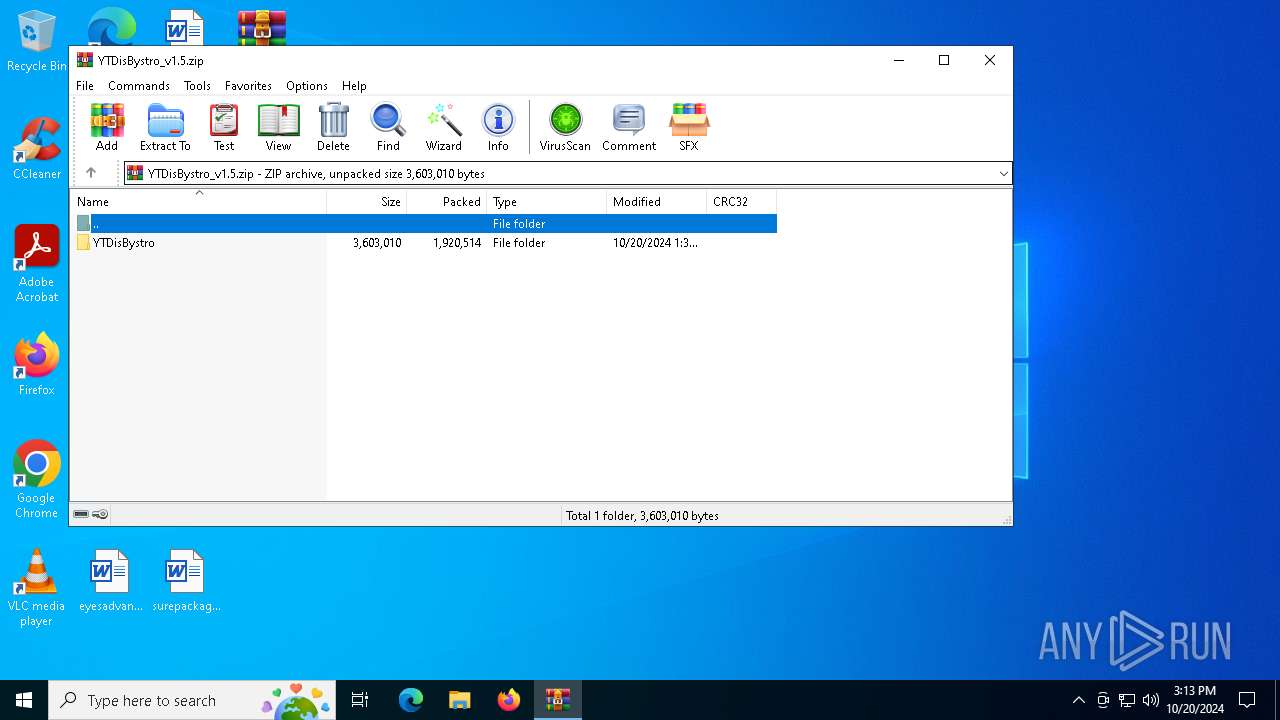
| File name: | YTDisBystro_v1.5.zip |
| Full analysis: | https://app.any.run/tasks/bc543cd2-39fa-42b7-9005-6d1d8d672bc9 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2024, 15:12:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | CF005A3756D858CDB5918068517AA769 |
| SHA1: | 0462F82F2C27218A07A26DB1FDCE7D614E66C8FE |
| SHA256: | 40B19B01E6A1AE4475E50F06ECD21989C9696590A68397D93C1F3F57949F829D |
| SSDEEP: | 98304:OLr7W8jxWdsXYq5CvRR0owqvpAGv+iK3bLyuul5HjZ4Q50OiIby0YdvGgm5QEKjh:+F |
MALICIOUS
Starts NET.EXE for service management
- cmd.exe (PID: 6828)
- net.exe (PID: 3744)
Generic archive extractor
- WinRAR.exe (PID: 1176)
SUSPICIOUS
Starts SC.EXE for service management
- cmd.exe (PID: 6828)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 5612)
Executes as Windows Service
- winws.exe (PID: 6912)
INFO
Manual execution by a user
- cmd.exe (PID: 6828)
- WinRAR.exe (PID: 5612)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:10:20 16:30:06 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | YTDisBystro/ |
Total processes
147
Monitored processes
14
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1176 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\YTDisBystro_v1.5.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1788 | sc delete zapret | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3276 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3568 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3744 | net stop zapret | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3828 | C:\WINDOWS\system32\net1 stop zapret | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3964 | sc description zapret "Zapret DPI bypass software" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5264 | sc start zapret | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5612 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\YTDisBystro_v1.5.zip" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
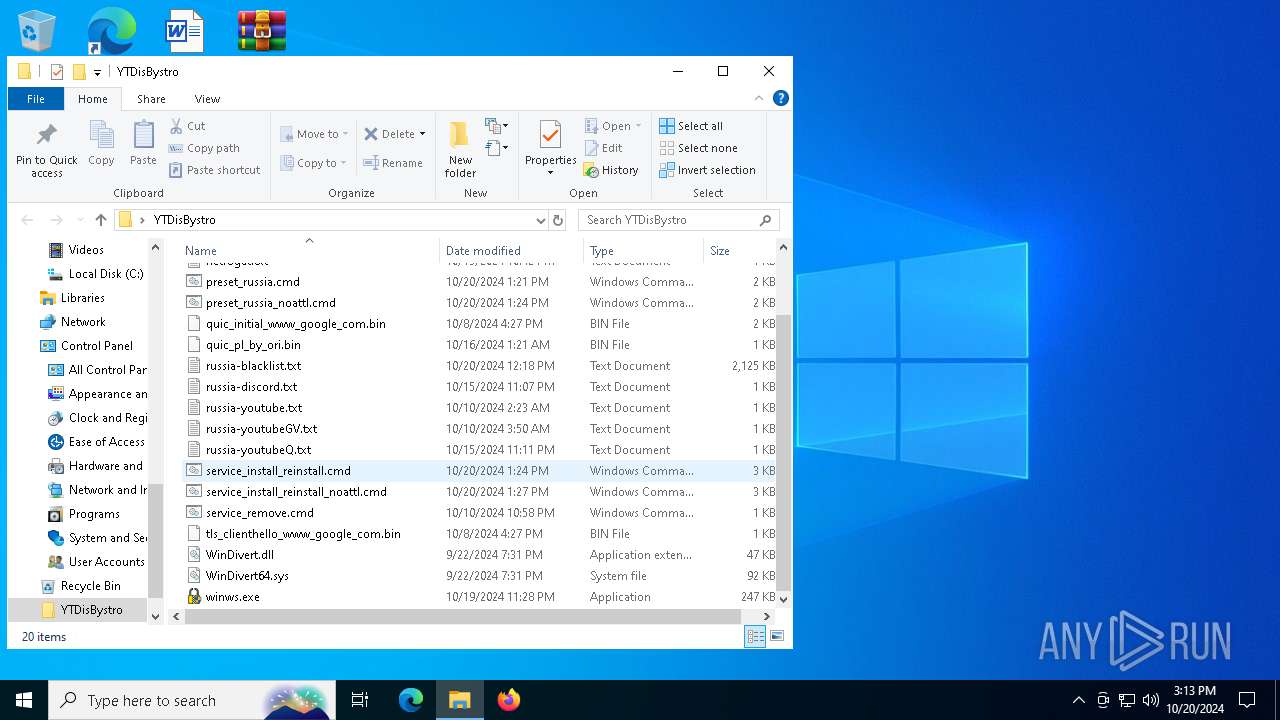
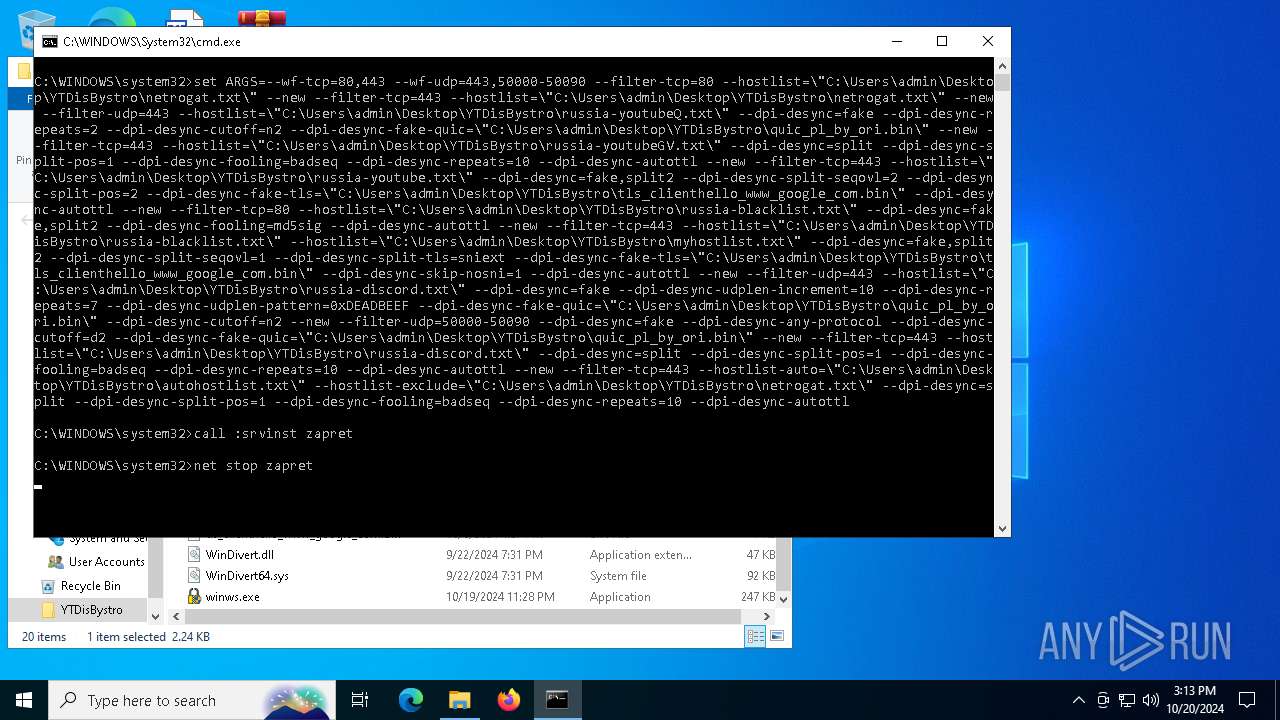
| 5948 | sc create zapret binPath= "\"C:\Users\admin\Desktop\YTDisBystro\winws.exe\" --wf-tcp=80,443 --wf-udp=443,50000-50090 --filter-tcp=80 --hostlist=\"C:\Users\admin\Desktop\YTDisBystro\netrogat.txt\" --new --filter-tcp=443 --hostlist=\"C:\Users\admin\Desktop\YTDisBystro\netrogat.txt\" --new --filter-udp=443 --hostlist=\"C:\Users\admin\Desktop\YTDisBystro\russia-youtubeQ.txt\" --dpi-desync=fake --dpi-desync-repeats=2 --dpi-desync-cutoff=n2 --dpi-desync-fake-quic=\"C:\Users\admin\Desktop\YTDisBystro\quic_pl_by_ori.bin\" --new --filter-tcp=443 --hostlist=\"C:\Users\admin\Desktop\YTDisBystro\russia-youtubeGV.txt\" --dpi-desync=split --dpi-desync-split-pos=1 --dpi-desync-fooling=badseq --dpi-desync-repeats=10 --dpi-desync-autottl --new --filter-tcp=443 --hostlist=\"C:\Users\admin\Desktop\YTDisBystro\russia-youtube.txt\" --dpi-desync=fake,split2 --dpi-desync-split-seqovl=2 --dpi-desync-split-pos=2 --dpi-desync-fake-tls=\"C:\Users\admin\Desktop\YTDisBystro\tls_clienthello_www_google_com.bin\" --dpi-desync-autottl --new --filter-tcp=80 --hostlist=\"C:\Users\admin\Desktop\YTDisBystro\russia-blacklist.txt\" --dpi-desync=fake,split2 --dpi-desync-fooling=md5sig --dpi-desync-autottl --new --filter-tcp=443 --hostlist=\"C:\Users\admin\Desktop\YTDisBystro\russia-blacklist.txt\" --hostlist=\"C:\Users\admin\Desktop\YTDisBystro\myhostlist.txt\" --dpi-desync=fake,split2 --dpi-desync-split-seqovl=1 --dpi-desync-split-tls=sniext --dpi-desync-fake-tls=\"C:\Users\admin\Desktop\YTDisBystro\tls_clienthello_www_google_com.bin\" --dpi-desync-skip-nosni=1 --dpi-desync-autottl --new --filter-udp=443 --hostlist=\"C:\Users\admin\Desktop\YTDisBystro\russia-discord.txt\" --dpi-desync=fake --dpi-desync-udplen-increment=10 --dpi-desync-repeats=7 --dpi-desync-udplen-pattern=0xDEADBEEF --dpi-desync-fake-quic=\"C:\Users\admin\Desktop\YTDisBystro\quic_pl_by_ori.bin\" --dpi-desync-cutoff=n2 --new --filter-udp=50000-50090 --dpi-desync=fake --dpi-desync-any-protocol --dpi-desync-cutoff=d2 --dpi-desync-fake-quic=\"C:\Users\admin\Desktop\YTDisBystro\quic_pl_by_ori.bin\" --new --filter-tcp=443 --hostlist=\"C:\Users\admin\Desktop\YTDisBystro\russia-discord.txt\" --dpi-desync=split --dpi-desync-split-pos=1 --dpi-desync-fooling=badseq --dpi-desync-repeats=10 --dpi-desync-autottl --new --filter-tcp=443 --hostlist-auto=\"C:\Users\admin\Desktop\YTDisBystro\autohostlist.txt\" --hostlist-exclude=\"C:\Users\admin\Desktop\YTDisBystro\netrogat.txt\" --dpi-desync=split --dpi-desync-split-pos=1 --dpi-desync-fooling=badseq --dpi-desync-repeats=10 --dpi-desync-autottl" DisplayName= "Zapret DPI bypass : zapret" start= auto | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 653
Read events
1 630
Write events
23
Delete events
0
Modification events
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\YTDisBystro_v1.5.zip | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
4
Suspicious files
3
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5612 | WinRAR.exe | C:\Users\admin\Desktop\YTDisBystro\russia-discord.txt | text | |
MD5:BB9EFD7C2E78099DDFE6FEE392F8B7CD | SHA256:1879ABCE260C2CE46729511BBCF6D60989FA0BB338D1BA86EF6063F0FFEEBCCC | |||
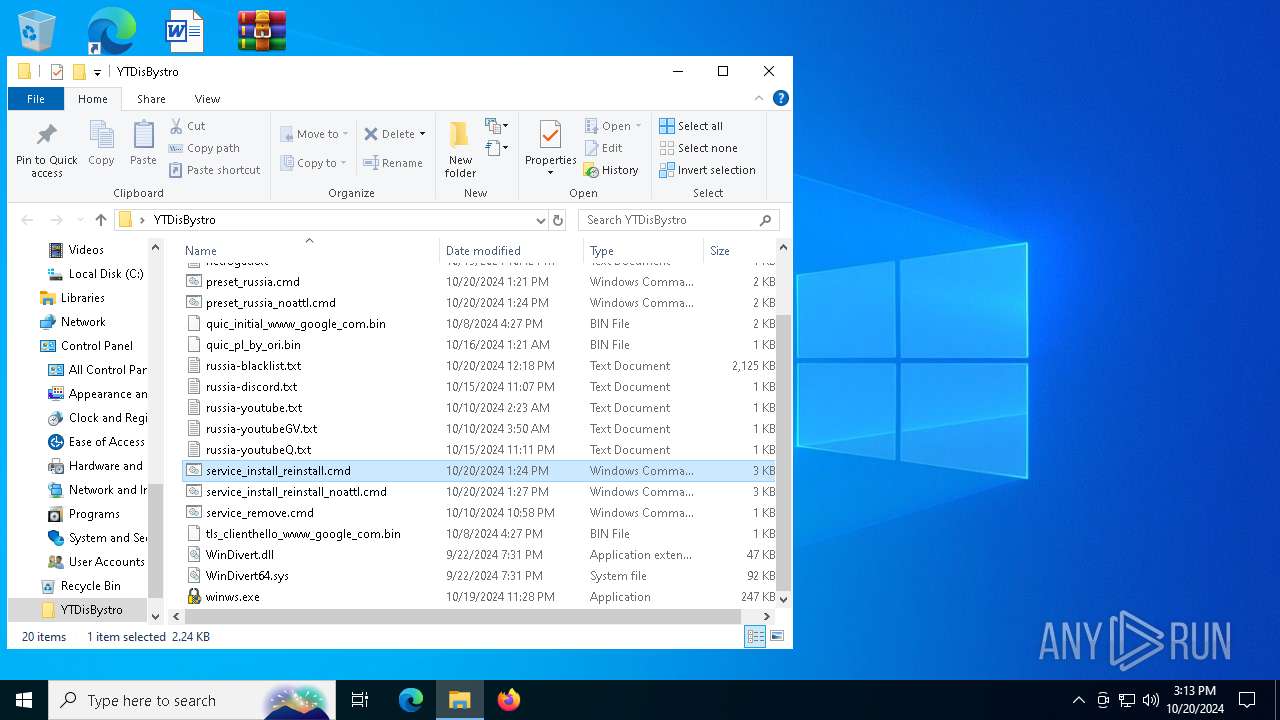
| 5612 | WinRAR.exe | C:\Users\admin\Desktop\YTDisBystro\service_install_reinstall.cmd | text | |
MD5:99E6F55315F2E5FC06D6F47DC6FFF422 | SHA256:3F8227BA6BA1C5E541F63DB37F192ED8CC3B93A464434F4AD57F03C03CA539A8 | |||
| 5612 | WinRAR.exe | C:\Users\admin\Desktop\YTDisBystro\russia-blacklist.txt | text | |
MD5:AAA4A3FA782DF525B220AC750B6D8535 | SHA256:37D88B634CEC8BCE81A41F365A620159D221B7187E73E3EEB9FC749E827F1ED7 | |||
| 5612 | WinRAR.exe | C:\Users\admin\Desktop\YTDisBystro\netrogat.txt | text | |
MD5:5F602B71B755C178CF5841D24B0D0C3C | SHA256:1CDE8AADBFB28444F9AB217BD2269DF2C7BF34976690E0BC38480597204D9374 | |||
| 5612 | WinRAR.exe | C:\Users\admin\Desktop\YTDisBystro\russia-youtubeGV.txt | text | |
MD5:26AE3D472B7EA155B5ED2A283C6F272A | SHA256:B273DA098B1819FE0CD9EEF6C8AA67D649D1DCE0376687B87B1358460A9D6D0E | |||
| 5612 | WinRAR.exe | C:\Users\admin\Desktop\YTDisBystro\preset_russia.cmd | text | |
MD5:0011561220AB0597B50F7C3C8A4852AD | SHA256:4AA03636225DCDF7ABF638FB90F9529993F19CB417B6E79B3390DD6219803851 | |||
| 5612 | WinRAR.exe | C:\Users\admin\Desktop\YTDisBystro\russia-youtubeQ.txt | text | |
MD5:F7C8F11341144C5869DD87EFAF316A54 | SHA256:55394183356C0B5CCABA38EAB1CA4223AAD7FB1B65B0240A2ED15DC989600EDF | |||
| 5612 | WinRAR.exe | C:\Users\admin\Desktop\YTDisBystro\service_remove.cmd | text | |
MD5:410D08325900864D9CF8FD7222B7F8E4 | SHA256:01D9DE489E2F589843ECF639E3B5B6DBBA8218258CBAB4A780B0FE94D5124E98 | |||
| 5612 | WinRAR.exe | C:\Users\admin\Desktop\YTDisBystro\quic_initial_www_google_com.bin | binary | |
MD5:312526D39958D89B1F8AB67789AB985F | SHA256:F4589C57749F956BB30538197A521D7005F8B0A8723B4707E72405E51DDAC50A | |||
| 5612 | WinRAR.exe | C:\Users\admin\Desktop\YTDisBystro\russia-youtube.txt | text | |
MD5:9AD95B8203DBC5DFB25D9829477031EA | SHA256:411C1F2DC67739A36683BD8F5E4485B4E4CCF500F1D89F8BB2E1527B42141CB7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
58
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6564 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3828 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3828 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.48.23.180:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6384 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.16.110.121:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6384 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6384 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4360 | SearchApp.exe | 2.16.110.171:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
780 | svchost.exe | 23.213.166.81:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |