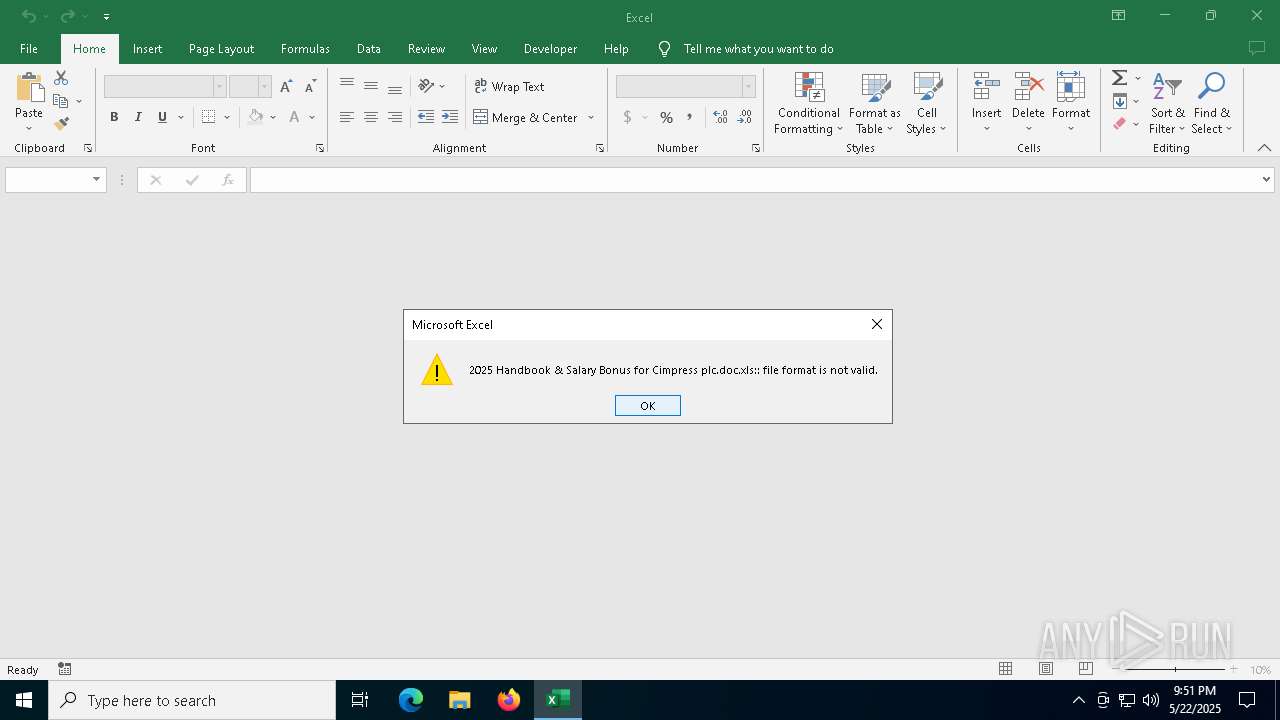
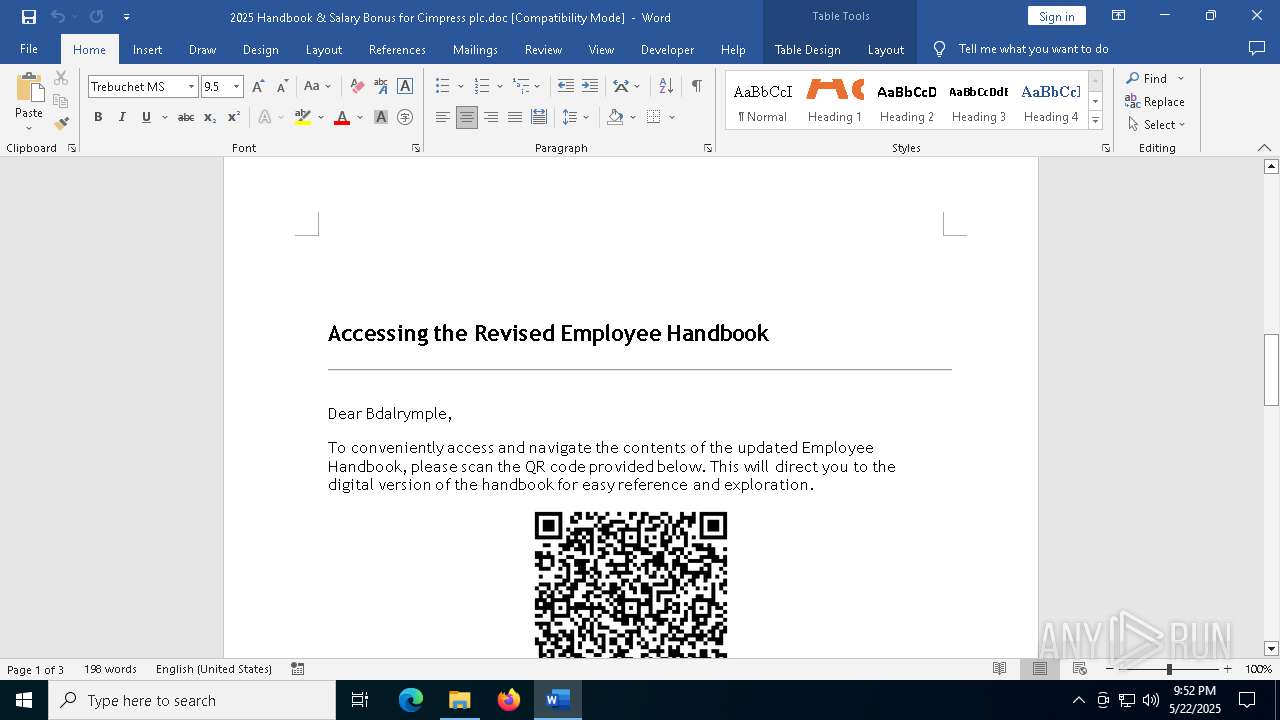
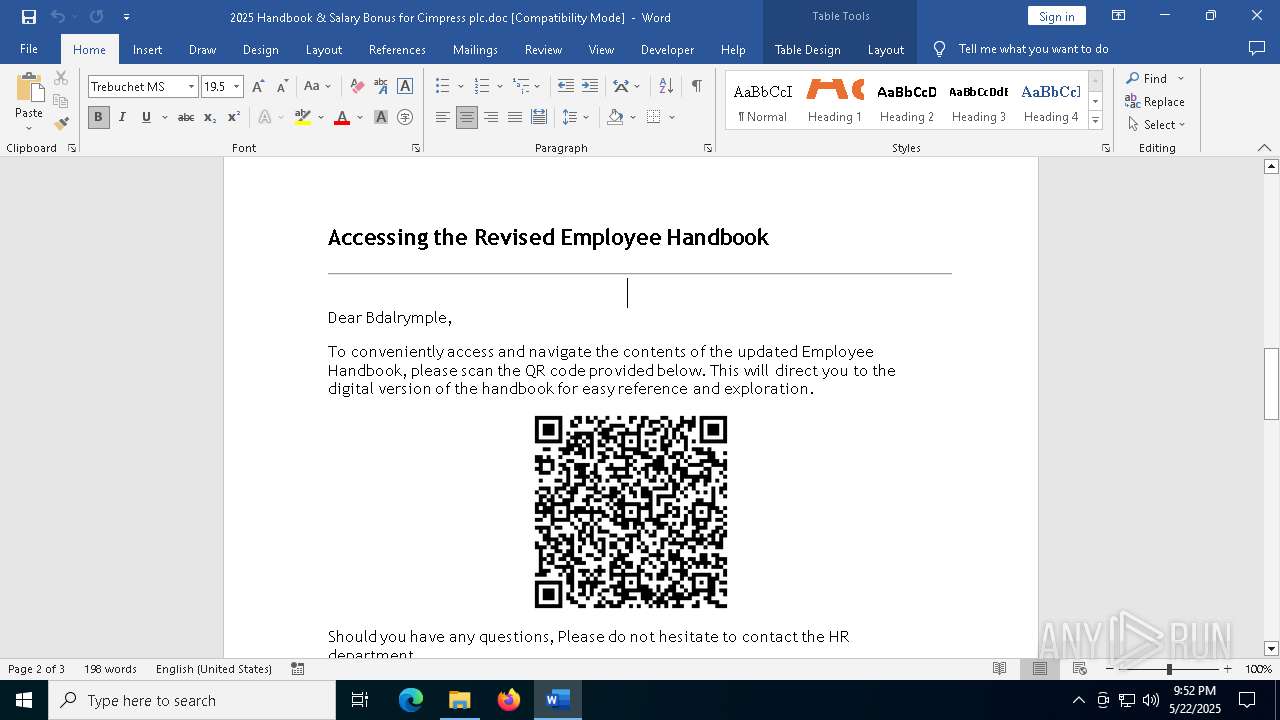
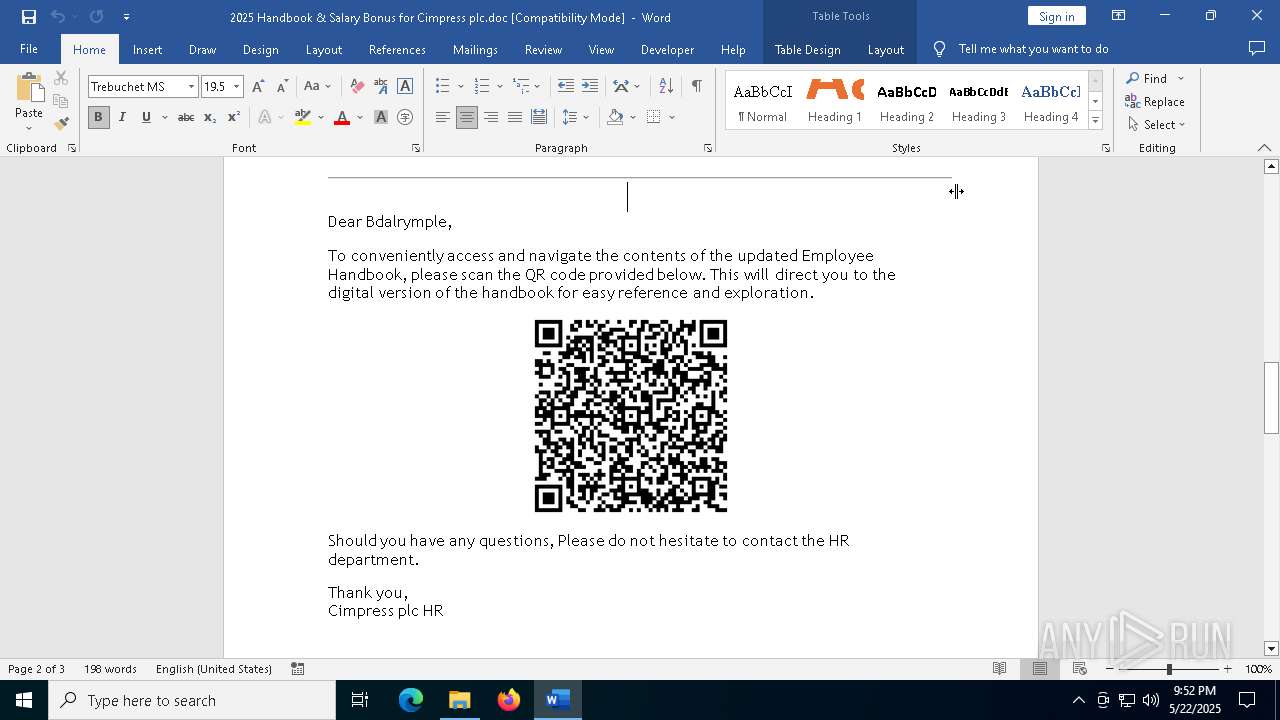
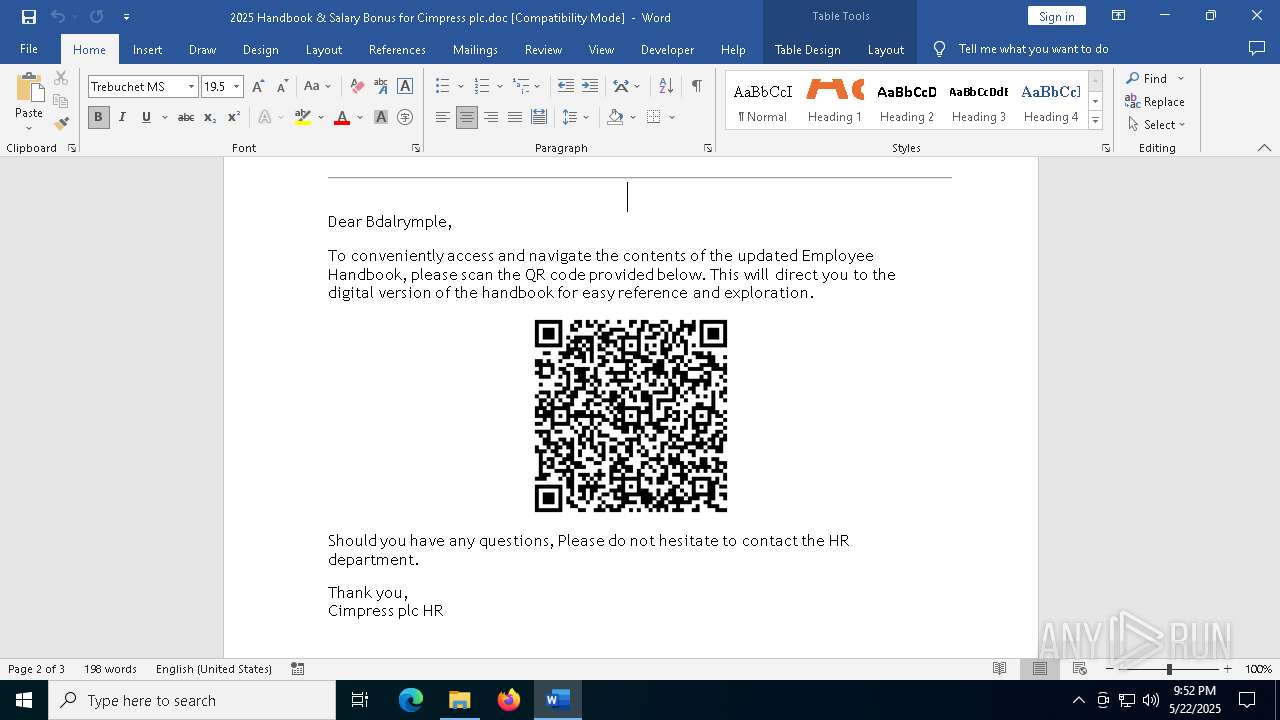
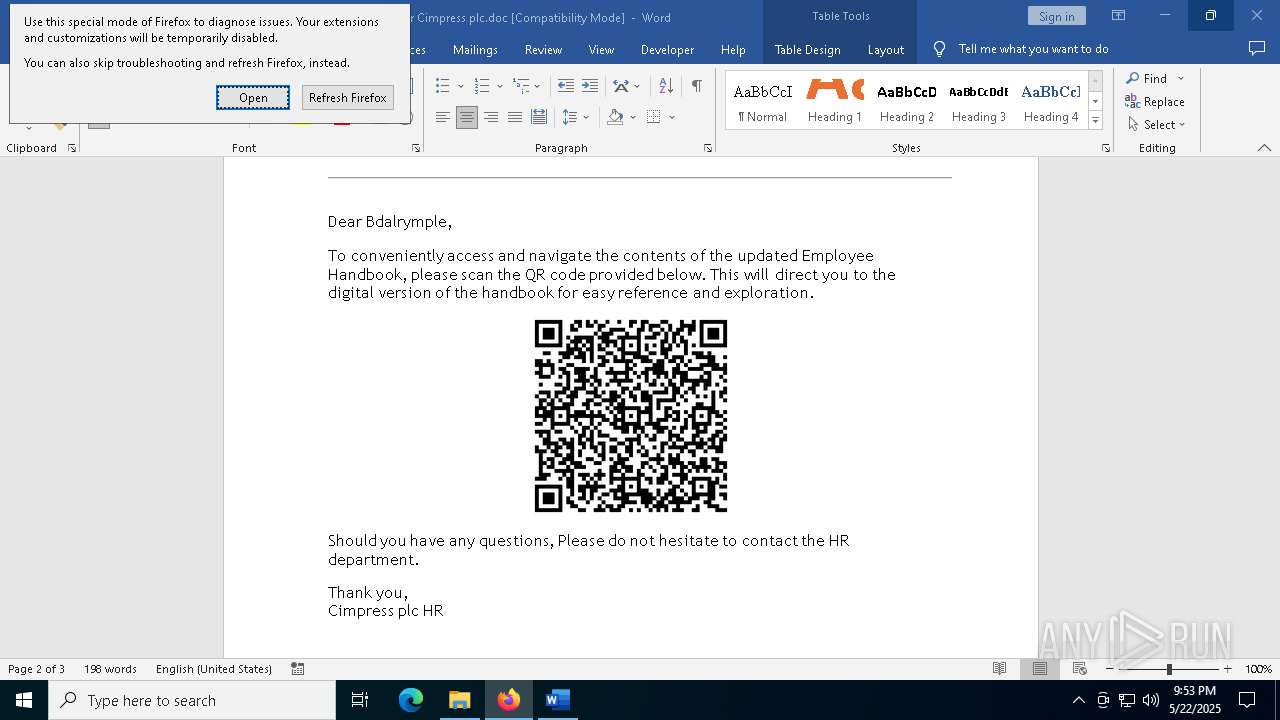
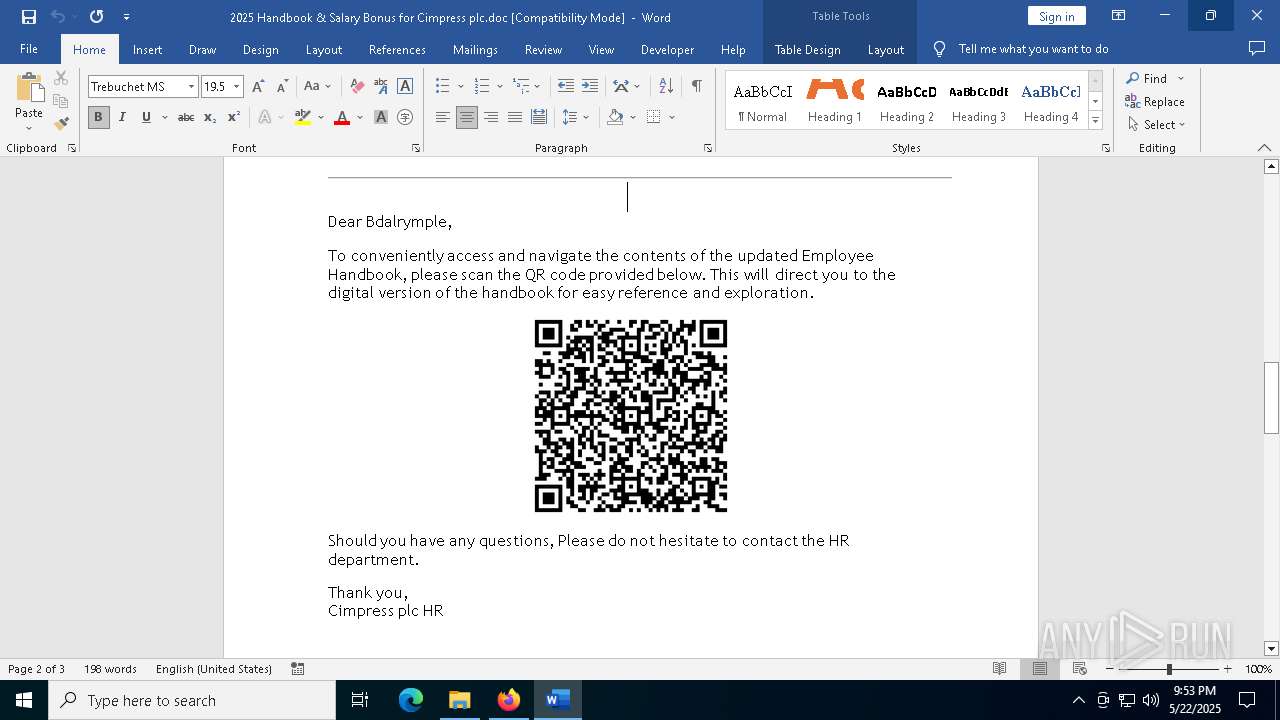
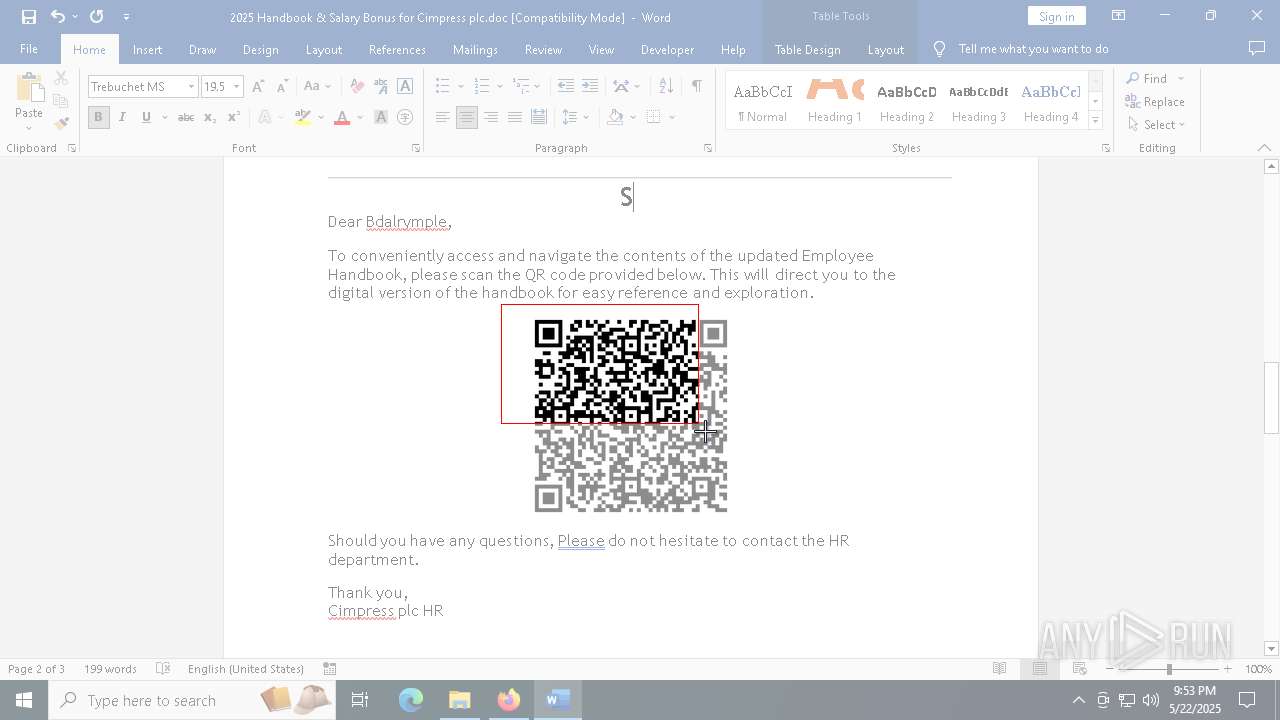
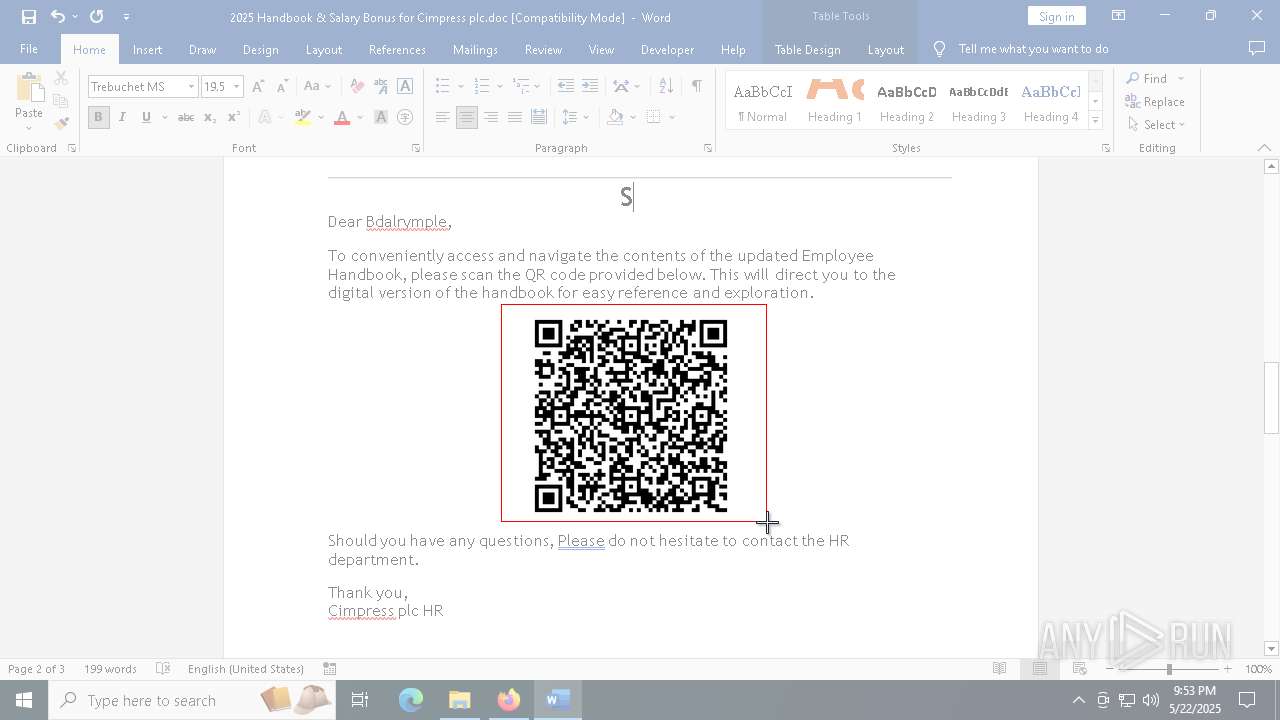
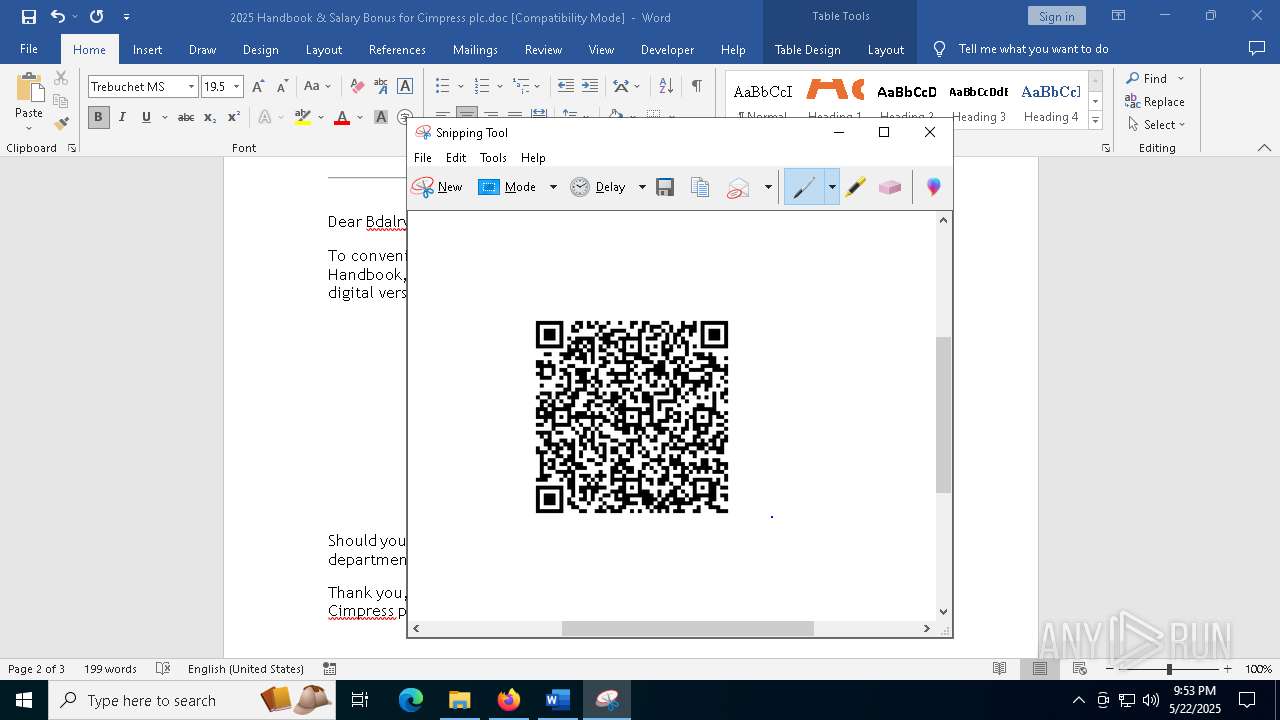
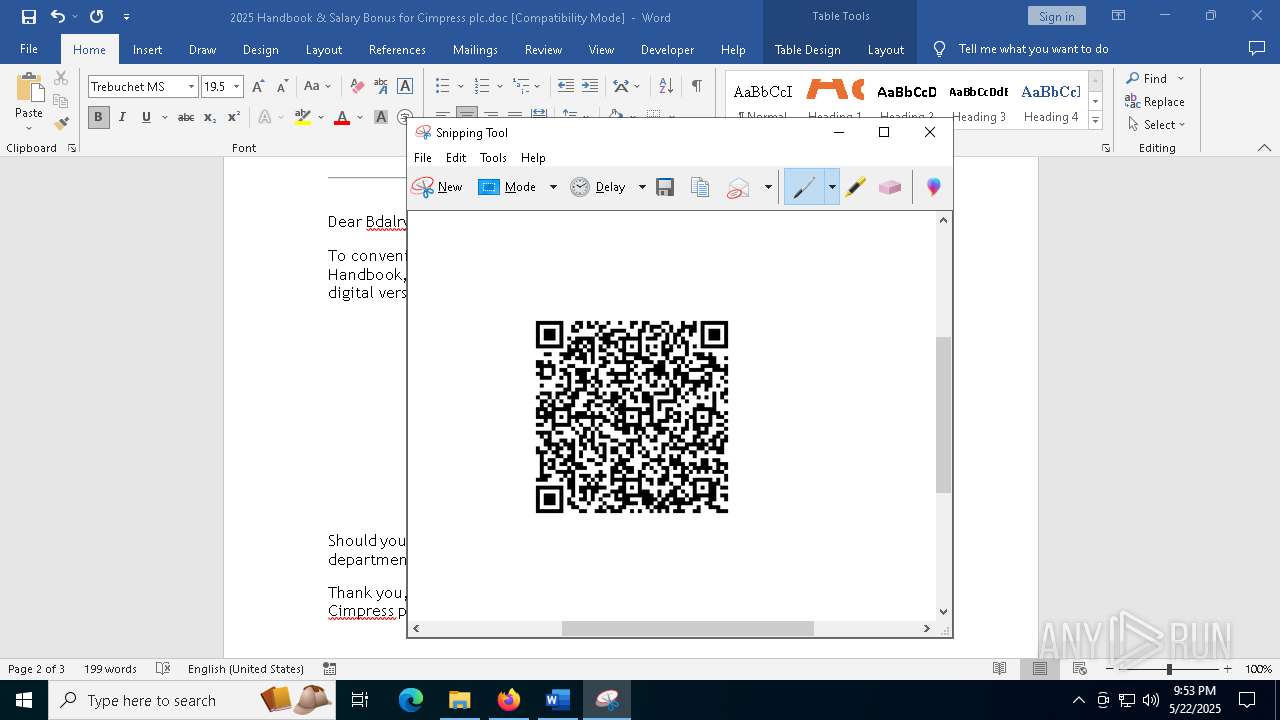
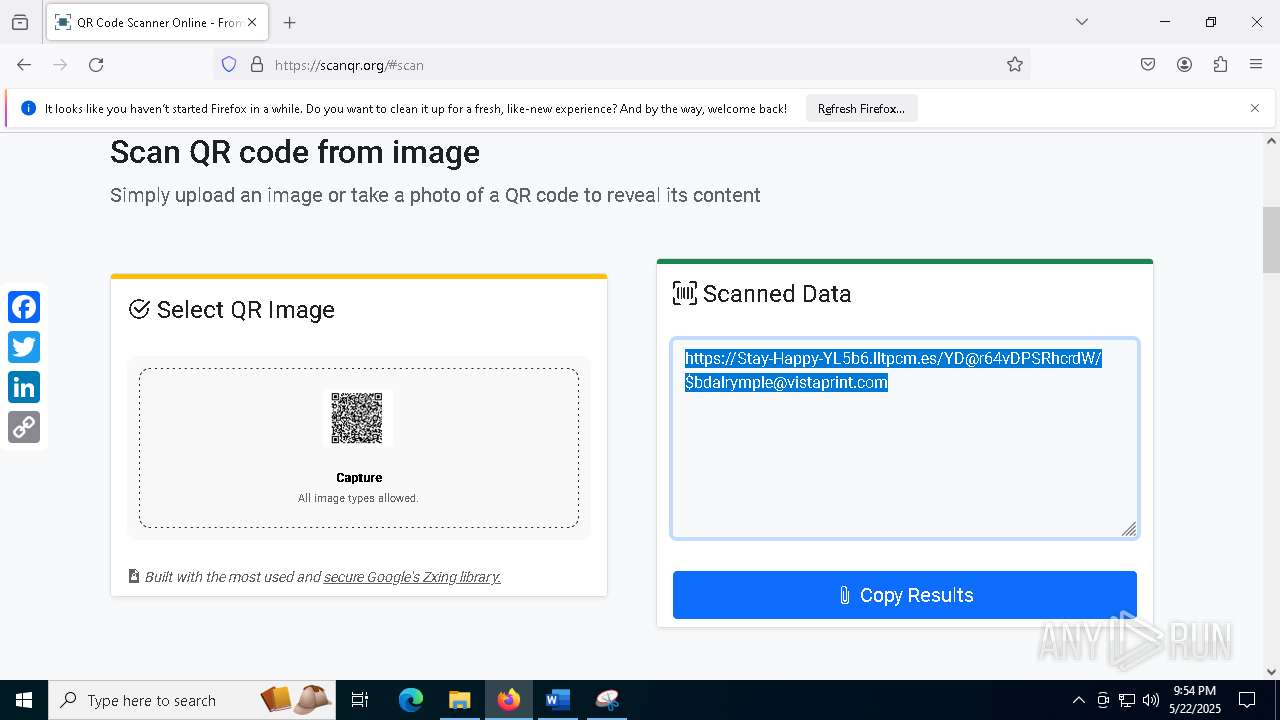
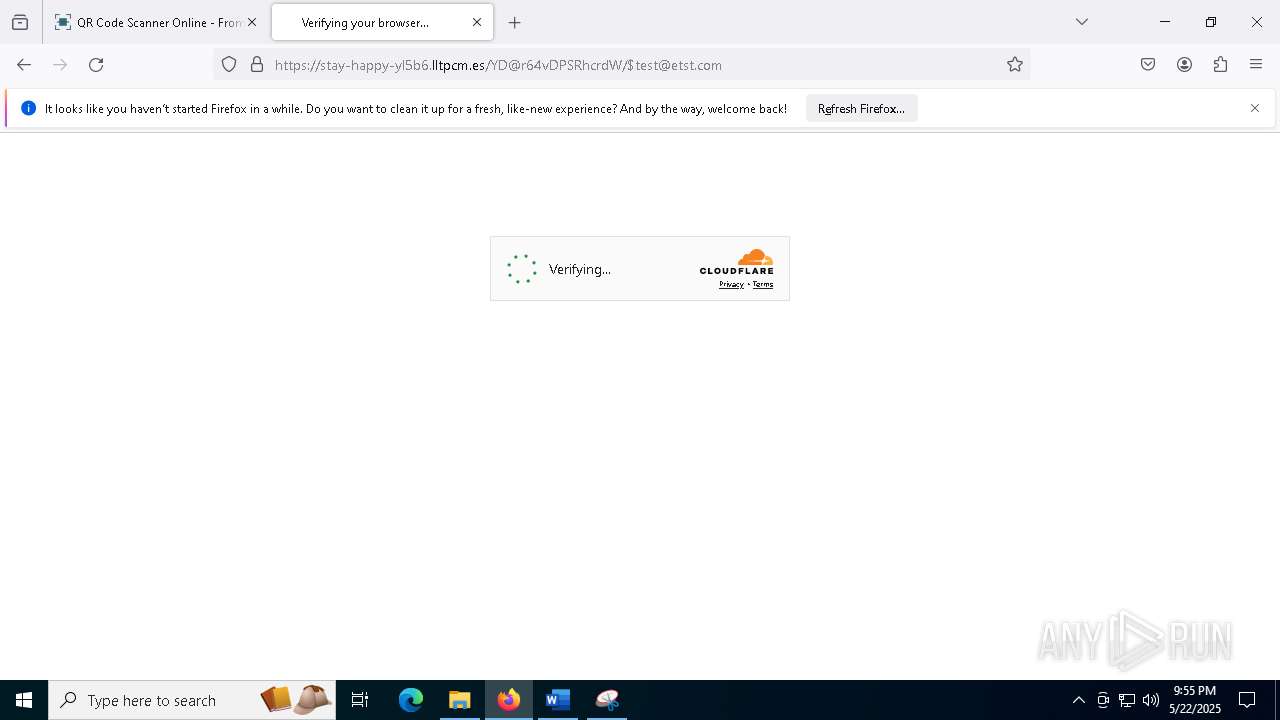
| File name: | 2025 Handbook & Salary Bonus for Cimpress plc.doc |
| Full analysis: | https://app.any.run/tasks/8376ea4f-389b-4ae0-97e4-505185434923 |
| Verdict: | Malicious activity |
| Analysis date: | May 22, 2025, 21:51:22 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 5.1, Code page: 1200, Number of Characters: 0, Revision Number: 0, Security: 0, Number of Words: 0 |
| MD5: | F61D8C05E69BFB65A92BAE8BE7E14DF8 |
| SHA1: | E96DCBFACBC854770086393D66B54C0A949F00EB |
| SHA256: | 4091D0FDEB40147CEB971C07E28B73C8D9A301892FE69A883546C488B1CD4795 |
| SSDEEP: | 1536:vXj6urc0oHspwhr6LD5E+u8Eo0UzGScrC3goRn0UR4bjbbwgJ4Rg:vPrHoHsUGL9BZEo0u0C3goRn0UR4bjb1 |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- firefox.exe (PID: 5968)
- firefox.exe (PID: 2416)
Manual execution by a user
- WINWORD.EXE (PID: 132)
- firefox.exe (PID: 5968)
- WINWORD.EXE (PID: 5544)
- SnippingTool.exe (PID: 4728)
Reads the software policy settings
- slui.exe (PID: 6436)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (78.9) |
|---|
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Author: | - |
| CreateDate: | - |
| Keywords: | - |
| LastModifiedBy: | - |
| ModifyDate: | - |
| Security: | None |
| Subject: | - |
| Title: | - |
| CodePage: | Unicode UTF-16, little endian |
| ScaleCrop: | No |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | - |
| TotalEditTime: | - |
| Words: | - |
| Characters: | - |
| Pages: | 1 |
| Paragraphs: | - |
| Lines: | 1 |
Total processes
169
Monitored processes
30
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | "C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 496 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" "C:\Users\admin\AppData\Local\Temp\2025 Handbook & Salary Bonus for Cimpress plc.doc.xls" | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 672 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4120 -childID 1 -isForBrowser -prefsHandle 4112 -prefMapHandle 4108 -prefsLen 31361 -prefMapSize 244583 -safeMode -parentBuildID 20240213221259 -appDir "C:\Program Files\Mozilla Firefox\browser" - {d651fde4-8458-43f6-8975-097c9253b37a} 2416 "\\.\pipe\gecko-crash-server-pipe.2416" 1c33573d4d0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 720 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1996 -parentBuildID 20240213221259 -prefsHandle 1936 -prefMapHandle 1904 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {1a4be383-fb4d-46c4-97b4-44e5190c4501} 2416 "\\.\pipe\gecko-crash-server-pipe.2416" 1c32e42d810 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 924 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=8756 -childID 10 -isForBrowser -prefsHandle 4820 -prefMapHandle 8704 -prefsLen 31277 -prefMapSize 244583 -safeMode -parentBuildID 20240213221259 -appDir "C:\Program Files\Mozilla Firefox\browser" - {380f8529-5791-4d95-97d2-b9e2b80b2e3e} 2416 "\\.\pipe\gecko-crash-server-pipe.2416" 1c3335b5bd0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2416 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2984 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3268 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3676 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "91D0588C-42F9-40F0-AE96-FFB8629381B9" "2128F954-DDC1-4933-9633-89FCEAF5FE10" "5544" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 4000 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2380 -parentBuildID 20240213221259 -prefsHandle 2372 -prefMapHandle 2360 -prefsLen 31067 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {f94574b2-9e2e-402f-bcab-7c857c66a113} 2416 "\\.\pipe\gecko-crash-server-pipe.2416" 1c320784910 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
Total events
52 950
Read events
52 019
Write events
860
Delete events
71
Modification events
| (PID) Process: | (496) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | q( |
Value: 71282000F00100000100000000000000A04F40B063CBDB0100000000 | |||
| (PID) Process: | (496) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Excel |
| Operation: | write | Name: | ImmersiveWorkbookDirtySentinel |
Value: 0 | |||
| (PID) Process: | (496) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Excel |
| Operation: | write | Name: | ExcelPreviousSessionId |
Value: {C6FA29D6-3826-4C56-8962-814BD6D43713} | |||
| (PID) Process: | (496) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (496) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\EXCEL\496 |
| Operation: | write | Name: | 0 |
Value: 0B0E10D629FAC62638564C8962814BD6D43713230046A6C6E481BBECF2ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511F003D2120965007800630065006C002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (496) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (496) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (496) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (496) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (496) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
Executable files
33
Suspicious files
279
Text files
56
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 496 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\Diagnostics\EXCEL\App1747950695751043700_C6FA29D6-3826-4C56-8962-814BD6D43713.log | — | |
MD5:— | SHA256:— | |||
| 496 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF9F9C95E4F0578725.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 496 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:11C75E5BF30B9F08513709990C1A7094 | SHA256:C6CFE773E01616ECAFFA52F63B034031D389ADD299A212471B4900E83D8D0976 | |||
| 496 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:EFE306A476DA27BCD3B203A60CEBB4E0 | SHA256:BC246245AF79B1D8FC564F31515705793905F9AD5EE99968AF6961A9344506F2 | |||
| 496 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\excel.exe_Rules.xml | xml | |
MD5:13AF026BB17E87B1A24C00E8295447B0 | SHA256:4695B860F6568E9EDDC220E4C80C848D5B6BE780C9A4A31FAD4D878E098FF8DB | |||
| 496 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:E69068A6DF5CC5EF491D4EE089C269A8 | SHA256:0FA29FC4B9C8A40792F59F67AA0892E0AC8E528ECCF770AF397C8886EB7E5514 | |||
| 496 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\52A2B4F8-647C-4A34-B420-C72683489363 | xml | |
MD5:A91EA79C728F704D8C3521A3799F5FFB | SHA256:01692972380D8B7C93CBACE0E4549BEC5D5D259A6C95CE40223F846BD6A49BFD | |||
| 496 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:4381675AA6BD21C24E6148103C06794D | SHA256:FC13EEB3B4D675D472CF959A1F0DCC5814904DC0413BCC70D5DFFF918CA22727 | |||
| 496 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Floodgate\Excel.SurveyHistoryStats.json | binary | |
MD5:6CA4960355E4951C72AA5F6364E459D5 | SHA256:88301F0B7E96132A2699A8BCE47D120855C7F0A37054540019E3204D6BCBABA3 | |||
| 496 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json | binary | |
MD5:923880A09F6286F30863FBFAB37CB6FC | SHA256:4373AA01ED903B73C3D1DAC0F5F990693C7604BBED88E4F3DC9692557673D220 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
60
TCP/UDP connections
185
DNS requests
215
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
496 | EXCEL.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1388 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
496 | EXCEL.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
1388 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5544 | WINWORD.EXE | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
5544 | WINWORD.EXE | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
5544 | WINWORD.EXE | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
496 | EXCEL.EXE | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |