| File name: | 1 (325) |
| Full analysis: | https://app.any.run/tasks/91d70e28-55c3-490a-a188-2f6b408de492 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 21:07:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 6EC3670524D99CECD05F314BB9DC8000 |
| SHA1: | A09AF51D2C58F957EB65A120E5DC611AD9BAEDD3 |
| SHA256: | 40833A25C278F835625A763FA5890F7E464115E1E828BB2D19F5FB4C326FE139 |
| SSDEEP: | 24576:YWo/GQUCC1Qrk/LICnLlgu0yBszURztR4:YWo/GQUCCark/LICnLlgu0yBsARztR4 |
MALICIOUS
PYKSPA mutex has been found
- hajwhnbjdnd.exe (PID: 6620)
- hajwhnbjdnd.exe (PID: 6424)
- hajwhnbjdnd.exe (PID: 6524)
- zbmqv.exe (PID: 6596)
- zbmqv.exe (PID: 6588)
- zbmqv.exe (PID: 7352)
- zbmqv.exe (PID: 7388)
Changes appearance of the Explorer extensions
- hajwhnbjdnd.exe (PID: 6620)
- zbmqv.exe (PID: 7352)
- zbmqv.exe (PID: 7388)
- hajwhnbjdnd.exe (PID: 6424)
- zbmqv.exe (PID: 6588)
- zbmqv.exe (PID: 6596)
Changes the autorun value in the registry
- zbmqv.exe (PID: 7352)
- zbmqv.exe (PID: 7388)
- hajwhnbjdnd.exe (PID: 6620)
- hajwhnbjdnd.exe (PID: 6424)
- zbmqv.exe (PID: 6596)
- zbmqv.exe (PID: 6588)
UAC/LUA settings modification
- zbmqv.exe (PID: 7352)
- zbmqv.exe (PID: 7388)
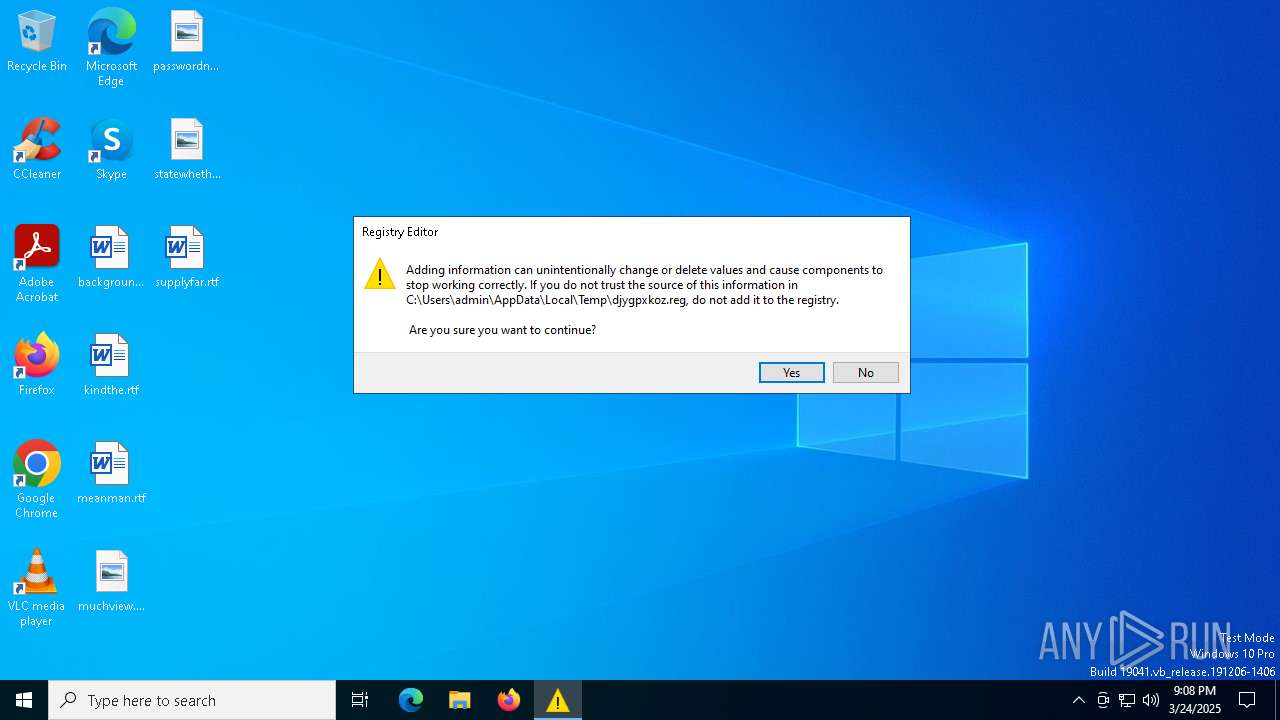
- regedit.exe (PID: 7632)
- hajwhnbjdnd.exe (PID: 6424)
- zbmqv.exe (PID: 6596)
- zbmqv.exe (PID: 6588)
- hajwhnbjdnd.exe (PID: 6620)
Modify registry editing tools (regedit)
- zbmqv.exe (PID: 6588)
- zbmqv.exe (PID: 6596)
PYKSPA has been detected (SURICATA)
- zbmqv.exe (PID: 6596)
SUSPICIOUS
Executable content was dropped or overwritten
- 1 (325).exe (PID: 5508)
- hajwhnbjdnd.exe (PID: 6620)
- hajwhnbjdnd.exe (PID: 6424)
- zbmqv.exe (PID: 6596)
Reads security settings of Internet Explorer
- 1 (325).exe (PID: 5508)
- zbmqv.exe (PID: 7352)
- ShellExperienceHost.exe (PID: 7740)
- droevlgslqpexoaui.exe (PID: 6376)
- hajwhnbjdnd.exe (PID: 6424)
- zbmqv.exe (PID: 6596)
- hajwhnbjdnd.exe (PID: 6620)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 2260)
Potential Corporate Privacy Violation
- zbmqv.exe (PID: 6596)
Checks for external IP
- zbmqv.exe (PID: 6596)
- svchost.exe (PID: 2180)
Creates file in the systems drive root
- zbmqv.exe (PID: 6596)
Connects to unusual port
- zbmqv.exe (PID: 6596)
Suspicious files were dropped or overwritten
- zbmqv.exe (PID: 6596)
INFO
Checks supported languages
- 1 (325).exe (PID: 5508)
- zbmqv.exe (PID: 7388)
- hajwhnbjdnd.exe (PID: 6620)
- ShellExperienceHost.exe (PID: 7740)
- droevlgslqpexoaui.exe (PID: 6376)
- OfficeClickToRun.exe (PID: 2952)
- hajwhnbjdnd.exe (PID: 6524)
- zbmqv.exe (PID: 6588)
- wjfukztewaymeufy.exe (PID: 6456)
- zbmqv.exe (PID: 6596)
- zbmqv.exe (PID: 7352)
Reads the computer name
- 1 (325).exe (PID: 5508)
- hajwhnbjdnd.exe (PID: 6620)
- zbmqv.exe (PID: 7352)
- zbmqv.exe (PID: 7388)
- ShellExperienceHost.exe (PID: 7740)
- PLUGScheduler.exe (PID: 2260)
- droevlgslqpexoaui.exe (PID: 6376)
- zbmqv.exe (PID: 6596)
- hajwhnbjdnd.exe (PID: 6524)
- zbmqv.exe (PID: 6588)
Create files in a temporary directory
- 1 (325).exe (PID: 5508)
- hajwhnbjdnd.exe (PID: 6620)
- zbmqv.exe (PID: 7352)
- zbmqv.exe (PID: 6596)
Process checks computer location settings
- 1 (325).exe (PID: 5508)
- zbmqv.exe (PID: 7352)
- droevlgslqpexoaui.exe (PID: 6376)
- wjfukztewaymeufy.exe (PID: 6456)
- hajwhnbjdnd.exe (PID: 6620)
Process checks whether UAC notifications are on
- hajwhnbjdnd.exe (PID: 6620)
- zbmqv.exe (PID: 7388)
- zbmqv.exe (PID: 7352)
- hajwhnbjdnd.exe (PID: 6424)
- zbmqv.exe (PID: 6596)
Creates files or folders in the user directory
- zbmqv.exe (PID: 7352)
- zbmqv.exe (PID: 6596)
Creates files in the program directory
- PLUGScheduler.exe (PID: 2260)
- zbmqv.exe (PID: 6596)
Manual execution by a user
- wjfukztewaymeufy.exe (PID: 6456)
- droevlgslqpexoaui.exe (PID: 6376)
Reads Microsoft Office registry keys
- OfficeClickToRun.exe (PID: 2952)
Checks proxy server information
- zbmqv.exe (PID: 6596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2008:12:30 15:40:22+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 7.1 |
| CodeSize: | 28672 |
| InitializedDataSize: | 1007616 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x41d2 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
275
Monitored processes
18
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2180 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2260 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2600 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2952 | "C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeClickToRun.exe" /service | C:\Program Files\Common Files\microsoft shared\ClickToRun\OfficeClickToRun.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Office Click-to-Run (SxS) Version: 16.0.16026.20140 Modules
| |||||||||||||||
| 5508 | "C:\Users\admin\AppData\Local\Temp\1 (325).exe" | C:\Users\admin\AppData\Local\Temp\1 (325).exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6376 | "C:\Users\admin\AppData\Local\Temp\droevlgslqpexoaui.exe" | C:\Users\admin\AppData\Local\Temp\droevlgslqpexoaui.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6424 | "C:\Users\admin\AppData\Local\Temp\hajwhnbjdnd.exe" "c:\users\admin\appdata\local\temp\droevlgslqpexoaui.exe*" | C:\Users\admin\AppData\Local\Temp\hajwhnbjdnd.exe | droevlgslqpexoaui.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 6456 | "C:\Users\admin\AppData\Local\Temp\wjfukztewaymeufy.exe" . | C:\Users\admin\AppData\Local\Temp\wjfukztewaymeufy.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 6524 | "C:\Users\admin\AppData\Local\Temp\hajwhnbjdnd.exe" "c:\users\admin\appdata\local\temp\wjfukztewaymeufy.exe*." | C:\Users\admin\AppData\Local\Temp\hajwhnbjdnd.exe | wjfukztewaymeufy.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 6588 | "C:\Users\admin\AppData\Local\Temp\zbmqv.exe" "-C:\Users\admin\AppData\Local\Temp\wjfukztewaymeufy.exe" | C:\Users\admin\AppData\Local\Temp\zbmqv.exe | hajwhnbjdnd.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
6 399
Read events
5 994
Write events
385
Delete events
20
Modification events
| (PID) Process: | (6620) hajwhnbjdnd.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (6620) hajwhnbjdnd.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | oxpamxnuiicm |
Value: mbzqizviciiyskxshi.exe | |||
| (PID) Process: | (6620) hajwhnbjdnd.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | nxqcpbsapqlwl |
Value: wjfukztewaymeufy.exe . | |||
| (PID) Process: | (6620) hajwhnbjdnd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | rdymbpisjmjwncm |
Value: kbbuohfuqyasoixulohg.exe | |||
| (PID) Process: | (6620) hajwhnbjdnd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | wjfukztewaymeufy |
Value: mbzqizviciiyskxshi.exe . | |||
| (PID) Process: | (6620) hajwhnbjdnd.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | mbzqizviciiyskxshi |
Value: C:\Users\admin\AppData\Local\Temp\mbzqizviciiyskxshi.exe | |||
| (PID) Process: | (6620) hajwhnbjdnd.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | droevlgslqpexoaui |
Value: C:\Users\admin\AppData\Local\Temp\mbzqizviciiyskxshi.exe . | |||
| (PID) Process: | (6620) hajwhnbjdnd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | oxpamxnuiicm |
Value: C:\Users\admin\AppData\Local\Temp\kbbuohfuqyasoixulohg.exe | |||
| (PID) Process: | (6620) hajwhnbjdnd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | nxqcpbsapqlwl |
Value: C:\Users\admin\AppData\Local\Temp\zrsmhbaqnwzspkayquooa.exe . | |||
| (PID) Process: | (6620) hajwhnbjdnd.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableRegistryTools |
Value: 1 | |||
Executable files
35
Suspicious files
60
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6620 | hajwhnbjdnd.exe | C:\Users\admin\AppData\Local\Temp\droevlgslqpexoaui.exe | executable | |
MD5:6EC3670524D99CECD05F314BB9DC8000 | SHA256:40833A25C278F835625A763FA5890F7E464115E1E828BB2D19F5FB4C326FE139 | |||
| 6620 | hajwhnbjdnd.exe | C:\Users\admin\AppData\Local\Temp\zrsmhbaqnwzspkayquooa.exe | executable | |
MD5:6EC3670524D99CECD05F314BB9DC8000 | SHA256:40833A25C278F835625A763FA5890F7E464115E1E828BB2D19F5FB4C326FE139 | |||
| 6620 | hajwhnbjdnd.exe | C:\Users\admin\AppData\Local\Temp\wjfukztewaymeufy.exe | executable | |
MD5:6EC3670524D99CECD05F314BB9DC8000 | SHA256:40833A25C278F835625A763FA5890F7E464115E1E828BB2D19F5FB4C326FE139 | |||
| 6620 | hajwhnbjdnd.exe | C:\Users\admin\AppData\Local\Temp\zbmqv.exe | executable | |
MD5:0D0B492C46796161F526352F3E890E47 | SHA256:4FFC04061A7B338BB0291DA7A1B8637FBCCBB17C00C5FAFC3CB0F4952A21A494 | |||
| 2260 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.049.etl | etl | |
MD5:5EA68411BF8E9EAF4621BAF73F61449E | SHA256:9D4CA5A1D871F819C139A498BB910A63576C2FE6367853544F8D172D8B6EBFF7 | |||
| 7352 | zbmqv.exe | C:\Users\admin\AppData\Local\VirtualStore\Windows\edlmopvswmwwaczedopwpzno.zhi | binary | |
MD5:812B0DCEE6999DAF3CD44FCF0DEBA072 | SHA256:F0DA7793F2C696780FE8BD76C39E3F4B38B0CC72C7939E20CB476B6ABB427DC4 | |||
| 7352 | zbmqv.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files (x86)\edlmopvswmwwaczedopwpzno.zhi | binary | |
MD5:812B0DCEE6999DAF3CD44FCF0DEBA072 | SHA256:F0DA7793F2C696780FE8BD76C39E3F4B38B0CC72C7939E20CB476B6ABB427DC4 | |||
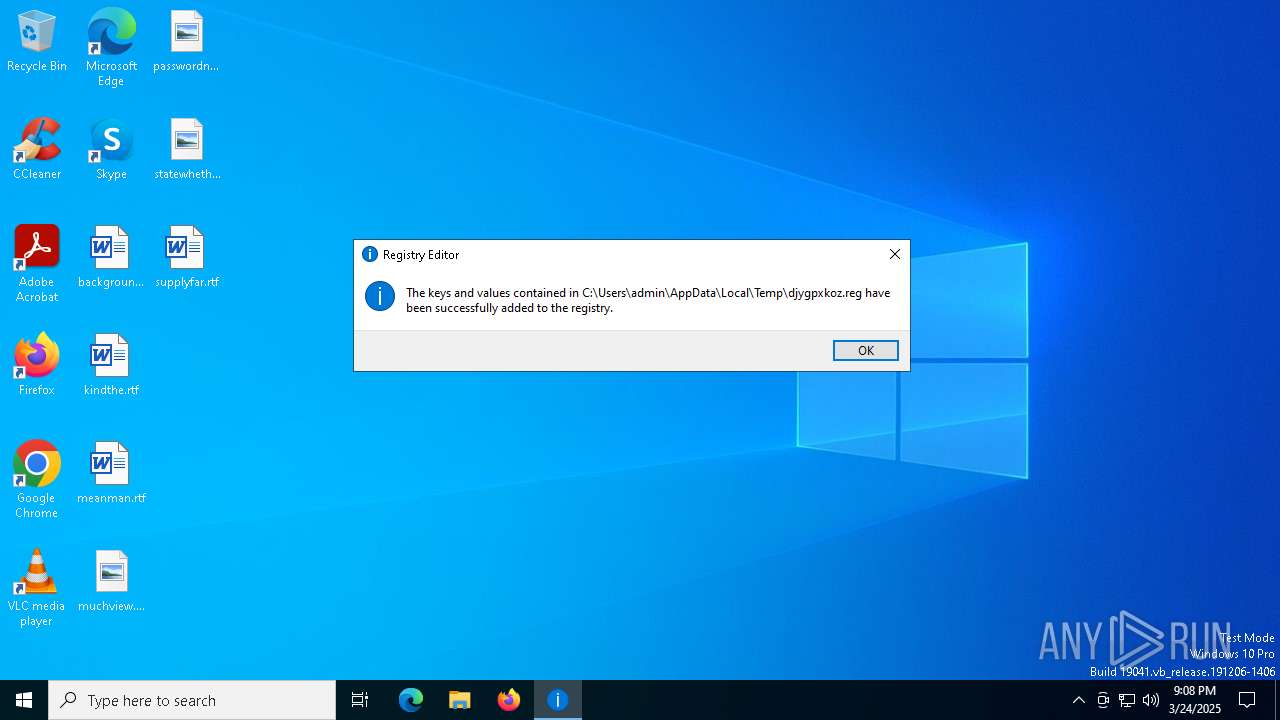
| 7352 | zbmqv.exe | C:\Users\admin\AppData\Local\Temp\djygpxkoz.reg | text | |
MD5:A8702BDFF482E47B2E74B115FFAAF779 | SHA256:15BD561433C476CB5E4AD5EB3AFE7ECA32841149FFDC21E1D33181532669EE6B | |||
| 7352 | zbmqv.exe | C:\Users\admin\AppData\Local\Temp\edlmopvswmwwaczedopwpzno.zhi | binary | |
MD5:812B0DCEE6999DAF3CD44FCF0DEBA072 | SHA256:F0DA7793F2C696780FE8BD76C39E3F4B38B0CC72C7939E20CB476B6ABB427DC4 | |||
| 2260 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.050.etl | binary | |
MD5:C8834D365FAE073DEDE1F1620454CE71 | SHA256:C6DD793EEE1D5551CA507A3C5BFFECA82DD3E29C63C2C6DD218A7D4BFB37046B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
70
DNS requests
356
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.24.77.23:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6596 | zbmqv.exe | GET | — | 104.19.222.79:80 | http://whatismyipaddress.com/ | unknown | — | — | whitelisted |
6596 | zbmqv.exe | GET | 301 | 188.114.97.3:80 | http://www.showmyipaddress.com/ | unknown | — | — | malicious |
5312 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6596 | zbmqv.exe | GET | 301 | 188.114.97.3:80 | http://www.showmyipaddress.com/ | unknown | — | — | malicious |
6596 | zbmqv.exe | GET | 403 | 104.19.222.79:80 | http://whatismyipaddress.com/ | unknown | — | — | whitelisted |
6828 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6828 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6596 | zbmqv.exe | GET | 301 | 188.114.97.3:80 | http://www.showmyipaddress.com/ | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 184.24.77.23:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 20.198.162.78:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
6544 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6596 | zbmqv.exe | Potential Corporate Privacy Violation | ET INFO IP Check Domain (showmyipaddress .com in HTTP Host) |
6596 | zbmqv.exe | A Network Trojan was detected | ET MALWARE Win32/Pykspa.C Public IP Check |
6596 | zbmqv.exe | Potential Corporate Privacy Violation | ET INFO IP Check Domain (showmyipaddress .com in HTTP Host) |
6596 | zbmqv.exe | A Network Trojan was detected | ET MALWARE Win32/Pykspa.C Public IP Check |
2180 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (whatismyipaddress .com) |
6596 | zbmqv.exe | A Network Trojan was detected | ET MALWARE Win32/Pykspa.C Public IP Check |
6596 | zbmqv.exe | A Network Trojan was detected | ET MALWARE Win32/Pykspa.C Public IP Check |
6596 | zbmqv.exe | Potential Corporate Privacy Violation | ET INFO IP Check Domain (showmyipaddress .com in HTTP Host) |
6596 | zbmqv.exe | A Network Trojan was detected | ET MALWARE Win32/Pykspa.C Public IP Check |
6596 | zbmqv.exe | Potential Corporate Privacy Violation | ET INFO IP Check Domain (showmyipaddress .com in HTTP Host) |