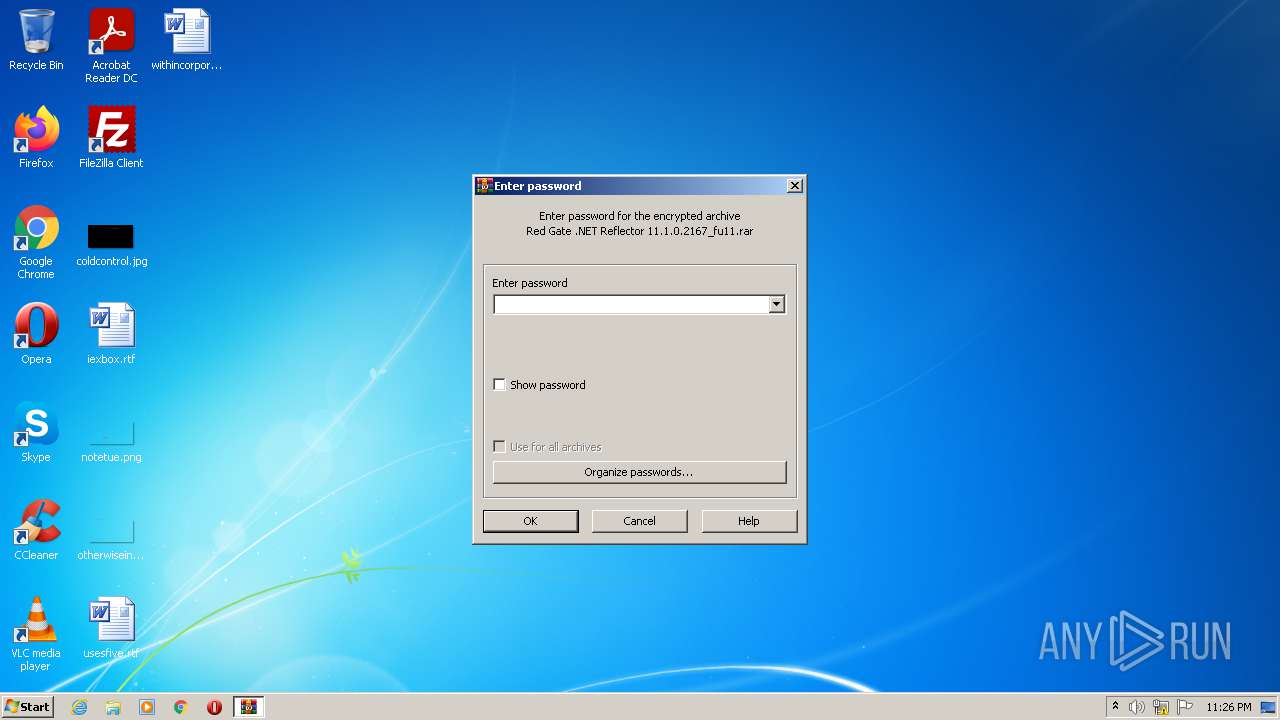
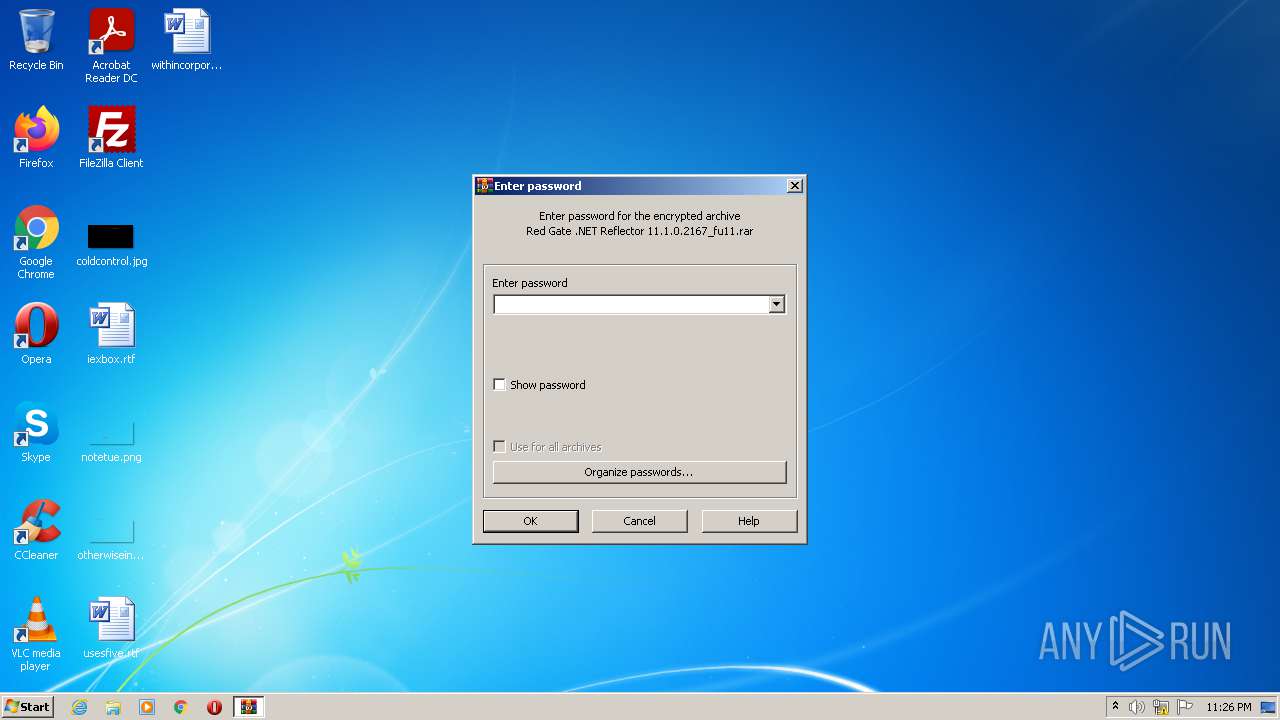
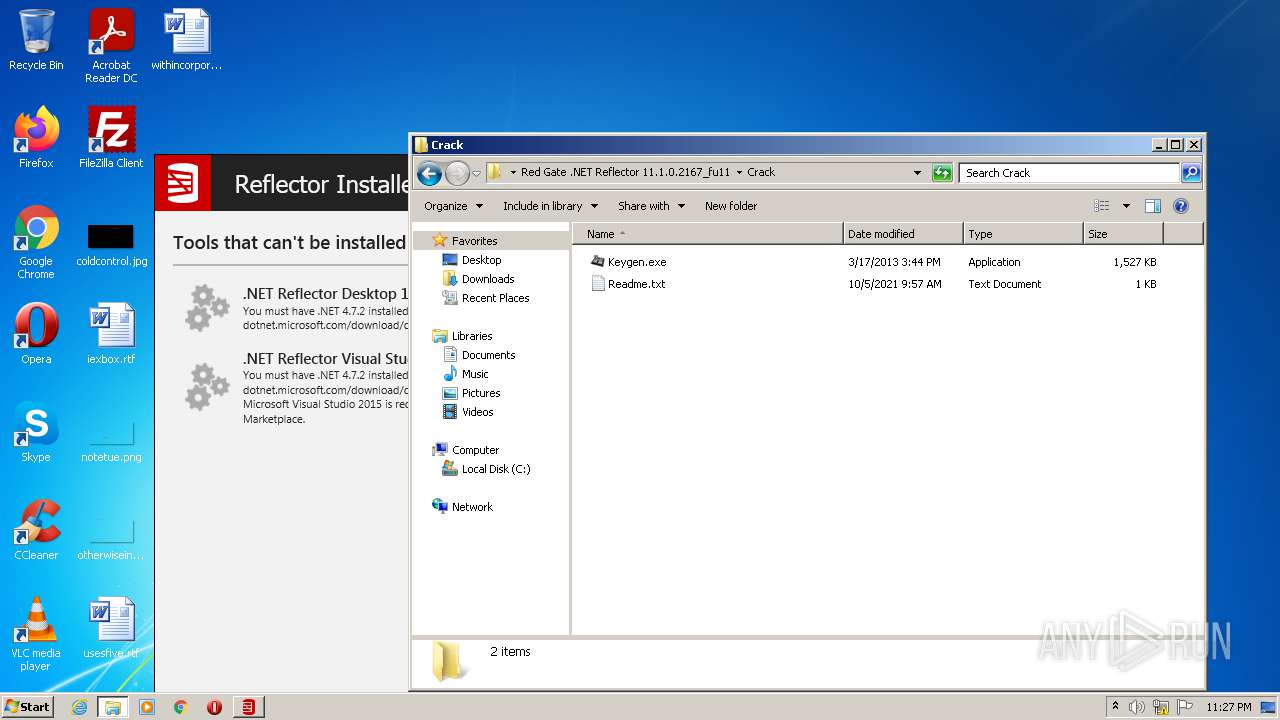
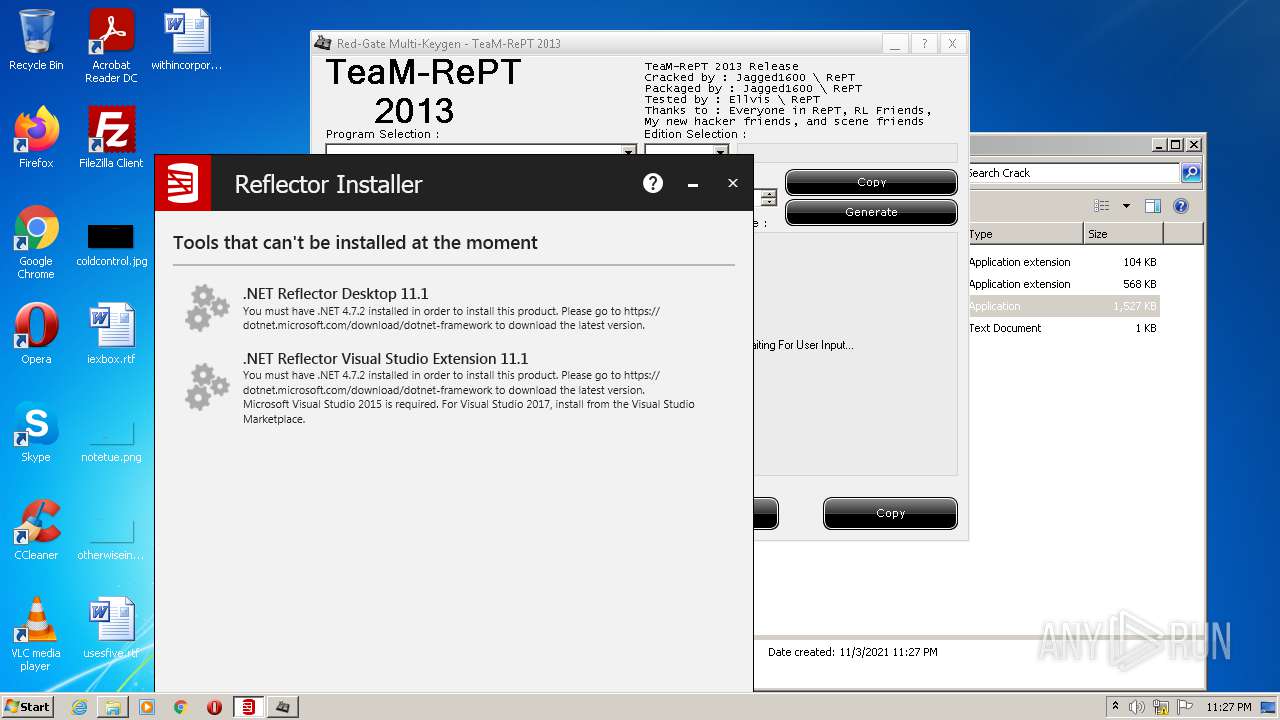
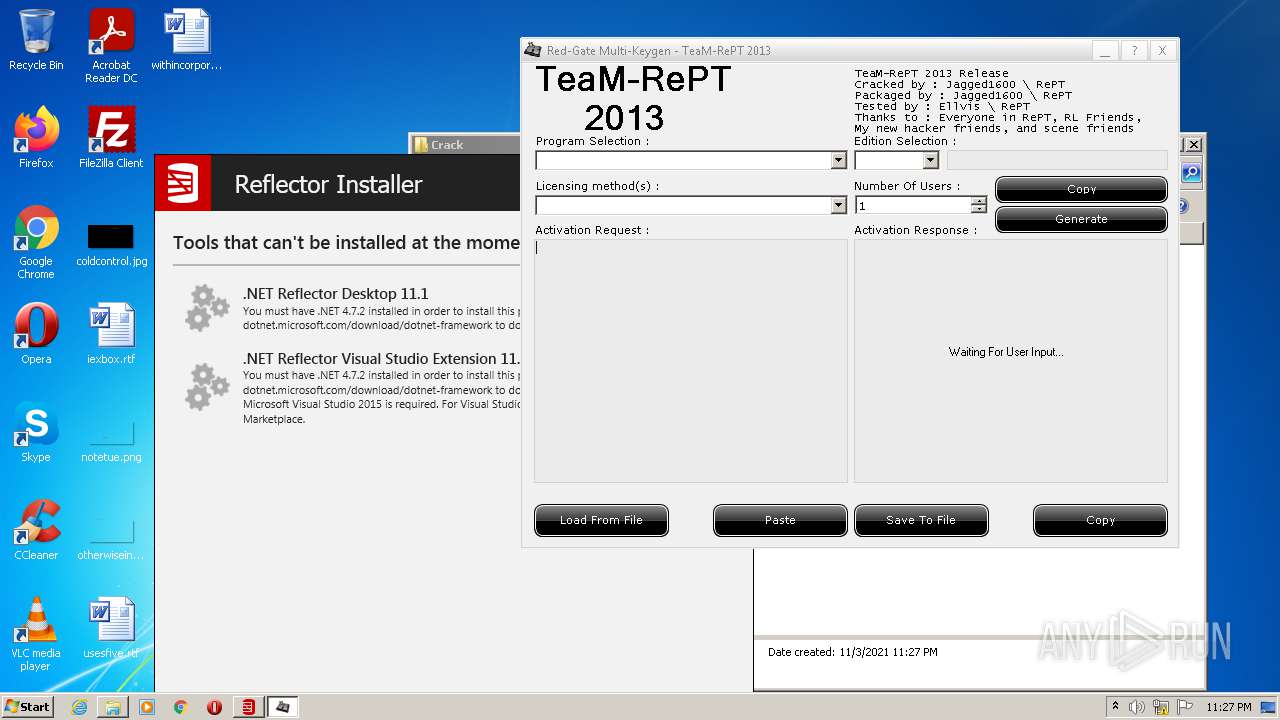
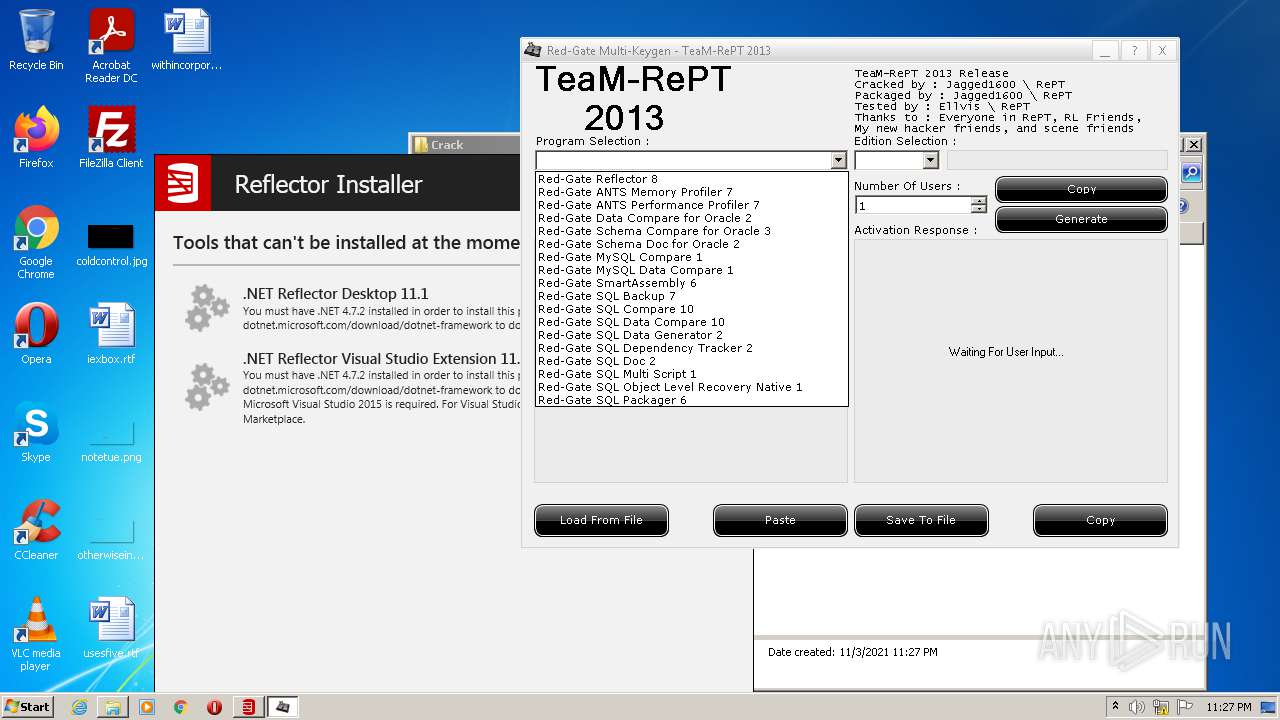
| File name: | Red Gate .NET Reflector 11.1.0.2167_fu11.rar |
| Full analysis: | https://app.any.run/tasks/7349bcf8-6c56-4a2c-975b-3948d13a1415 |
| Verdict: | Malicious activity |
| Analysis date: | November 03, 2021, 23:26:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | F231F116F36DEB5E1F9FBD80598F117D |
| SHA1: | 5E7AEFA342EE26C35B02AEE5E910609435968811 |
| SHA256: | 407B1B30EABE875C14EBE0841E993D20B533CC55019AF8C0209000A583C2B732 |
| SSDEEP: | 196608:iJj/xE5WjsfcYUYTuUlPQx1UoOvRrE6snKFZVQOcVQd8U/4MX6JElq:ip/y5WjsASGXdqmKN4Lwq |
MALICIOUS
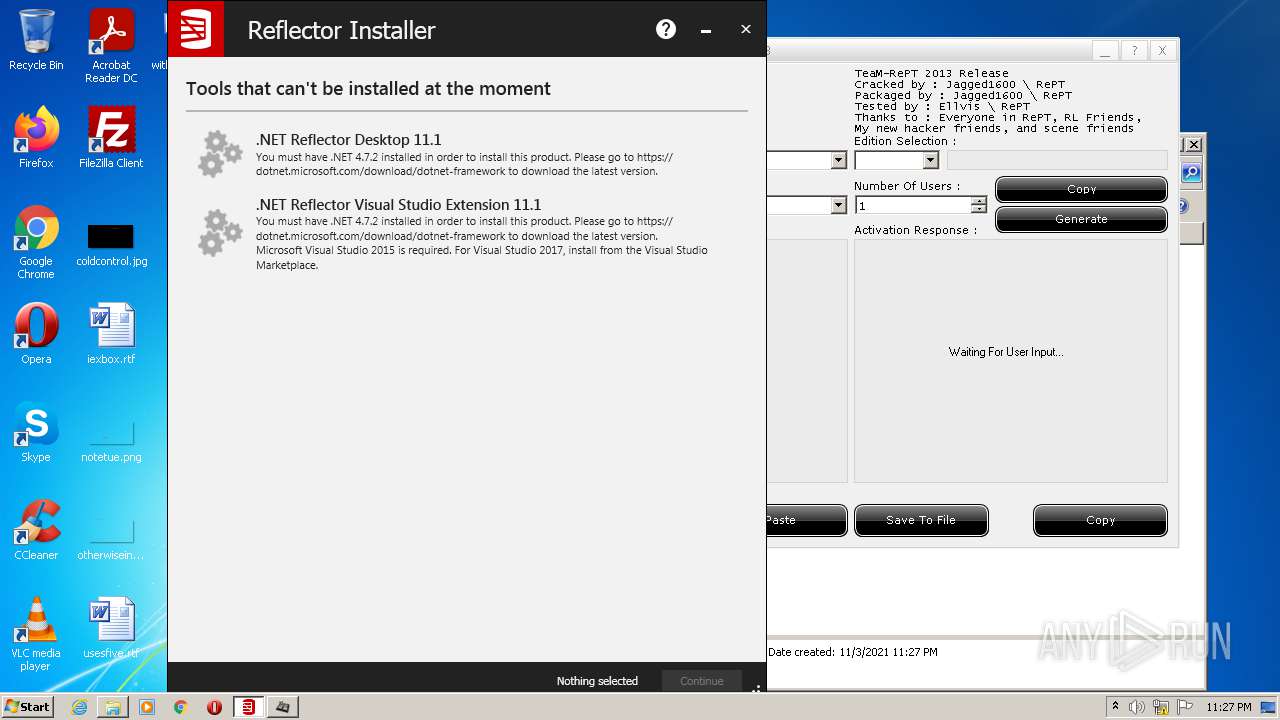
Application was dropped or rewritten from another process
- ReflectorInstaller_softoroom.net.exe (PID: 2092)
- ReflectorInstaller_softoroom.net.exe (PID: 1240)
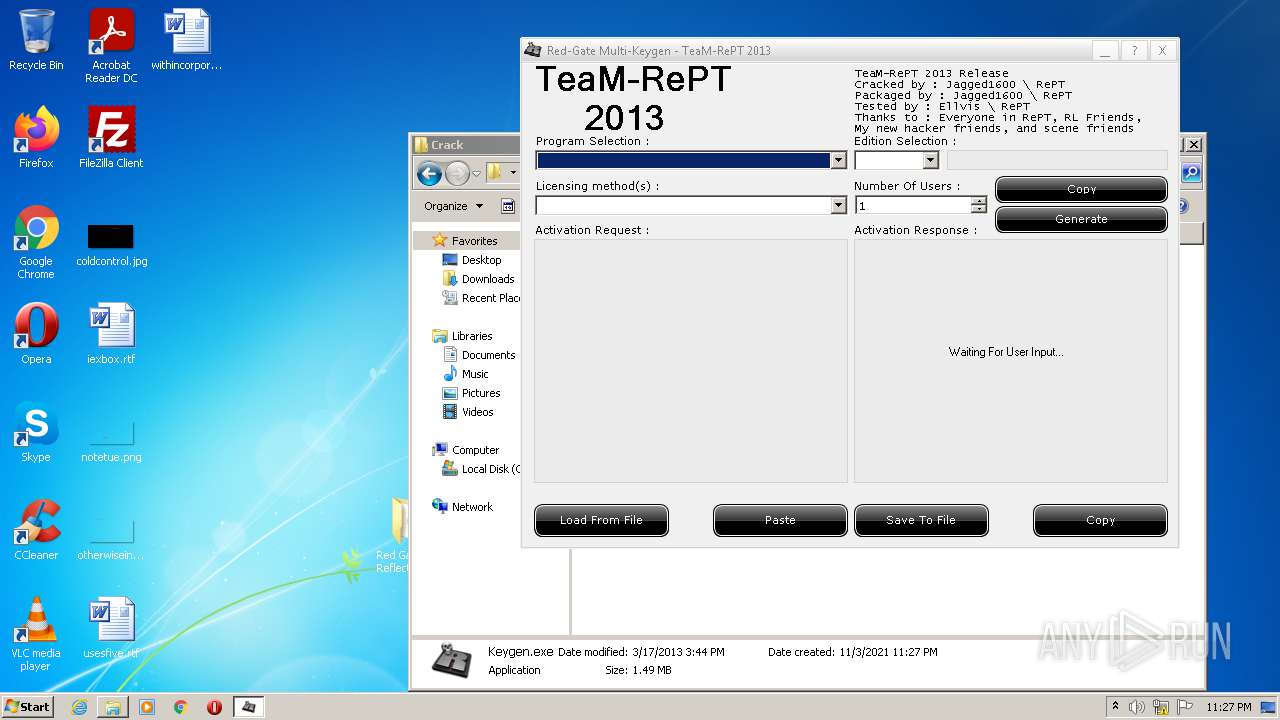
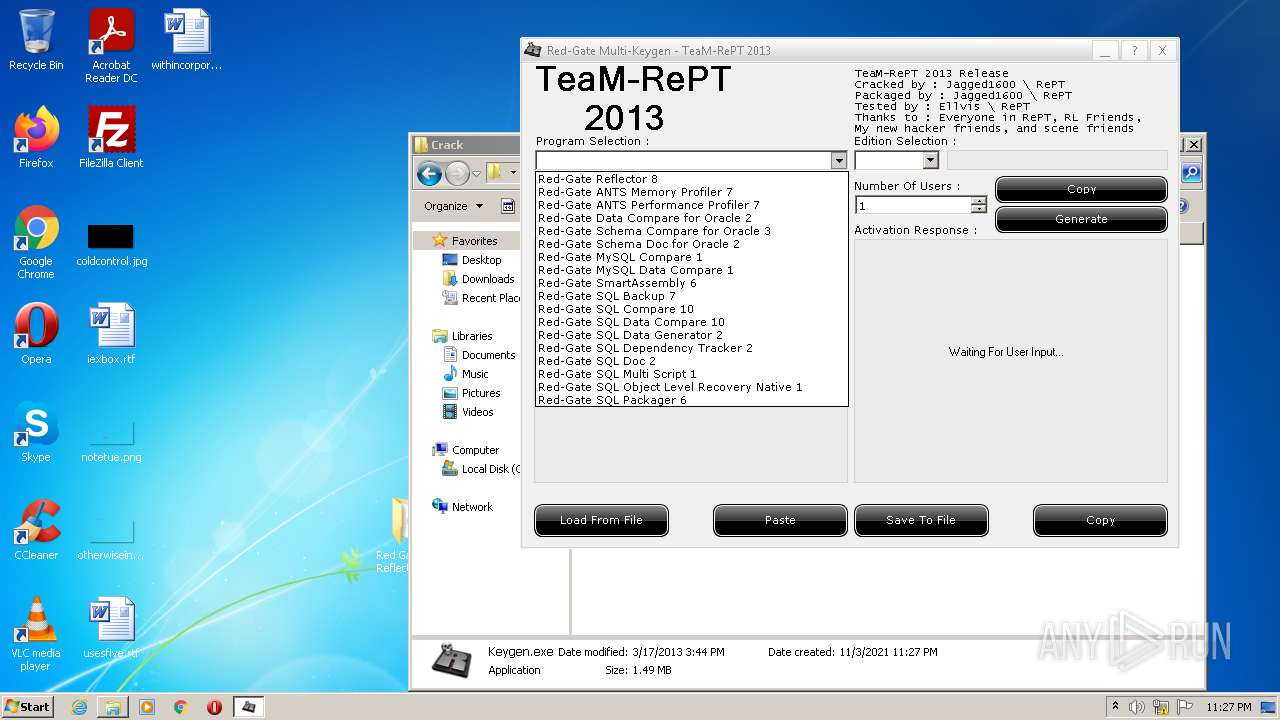
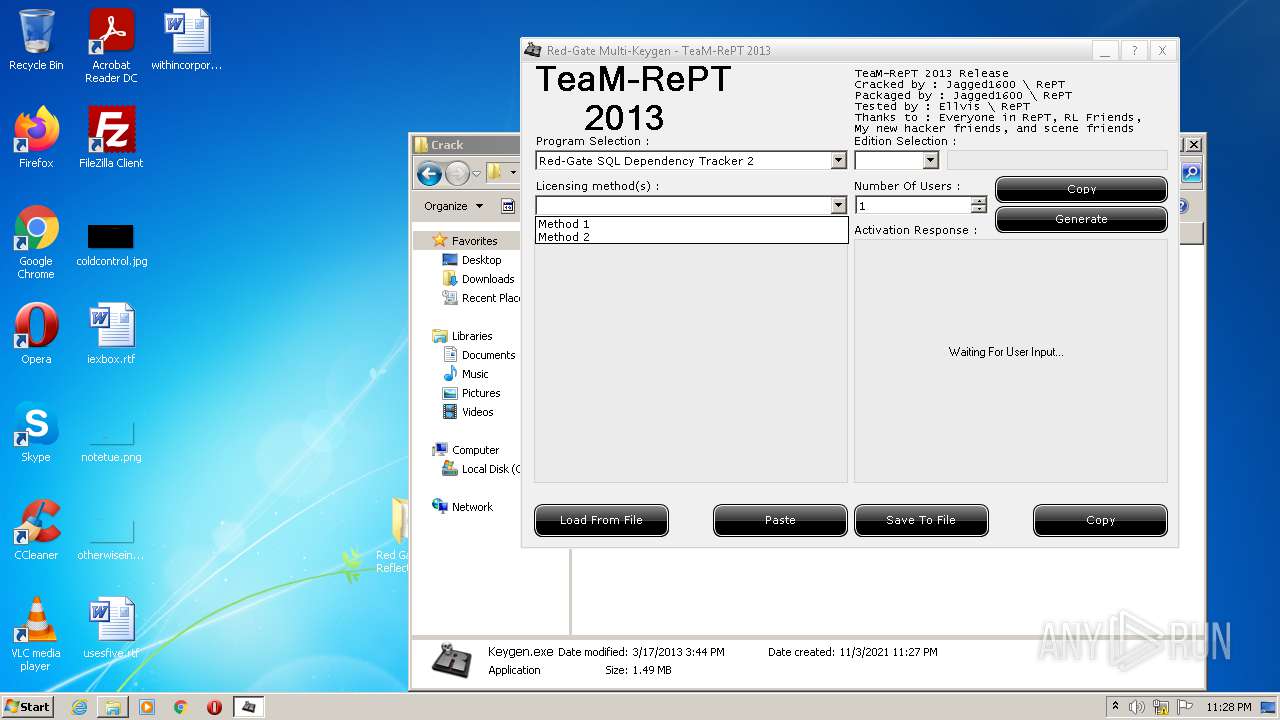
- Keygen.exe (PID: 1344)
- RedGate.Installer.UI.App.exe (PID: 3844)
Changes settings of System certificates
- ReflectorInstaller_softoroom.net.exe (PID: 1240)
Drops executable file immediately after starts
- Keygen.exe (PID: 1344)
Loads dropped or rewritten executable
- RedGate.Installer.UI.App.exe (PID: 3844)
- Keygen.exe (PID: 1344)
- SearchProtocolHost.exe (PID: 592)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 3304)
- ReflectorInstaller_softoroom.net.exe (PID: 1240)
- RedGate.Installer.UI.App.exe (PID: 3844)
- Keygen.exe (PID: 1344)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3304)
- ReflectorInstaller_softoroom.net.exe (PID: 1240)
- RedGate.Installer.UI.App.exe (PID: 3844)
Checks supported languages
- WinRAR.exe (PID: 3304)
- ReflectorInstaller_softoroom.net.exe (PID: 1240)
- RedGate.Installer.UI.App.exe (PID: 3844)
- Keygen.exe (PID: 1344)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3304)
- ReflectorInstaller_softoroom.net.exe (PID: 1240)
- RedGate.Installer.UI.App.exe (PID: 3844)
- Keygen.exe (PID: 1344)
Adds / modifies Windows certificates
- ReflectorInstaller_softoroom.net.exe (PID: 1240)
Drops a file with too old compile date
- ReflectorInstaller_softoroom.net.exe (PID: 1240)
- RedGate.Installer.UI.App.exe (PID: 3844)
Searches for installed software
- RedGate.Installer.UI.App.exe (PID: 3844)
Reads Environment values
- RedGate.Installer.UI.App.exe (PID: 3844)
Executed as Windows Service
- msiexec.exe (PID: 472)
Reads Windows owner or organization settings
- RedGate.Installer.UI.App.exe (PID: 3844)
Reads the Windows organization settings
- RedGate.Installer.UI.App.exe (PID: 3844)
INFO
Manual execution by user
- ReflectorInstaller_softoroom.net.exe (PID: 2092)
- ReflectorInstaller_softoroom.net.exe (PID: 1240)
- Keygen.exe (PID: 1344)
- chrome.exe (PID: 3460)
Reads settings of System Certificates
- ReflectorInstaller_softoroom.net.exe (PID: 1240)
- RedGate.Installer.UI.App.exe (PID: 3844)
- chrome.exe (PID: 3924)
Checks supported languages
- SearchProtocolHost.exe (PID: 592)
- msiexec.exe (PID: 472)
- WISPTIS.EXE (PID: 1132)
- chrome.exe (PID: 3460)
- chrome.exe (PID: 2404)
- chrome.exe (PID: 880)
- chrome.exe (PID: 3924)
- chrome.exe (PID: 2596)
- chrome.exe (PID: 972)
- chrome.exe (PID: 3456)
- chrome.exe (PID: 3500)
- chrome.exe (PID: 1092)
- chrome.exe (PID: 2252)
- chrome.exe (PID: 3764)
- chrome.exe (PID: 736)
- chrome.exe (PID: 3232)
- chrome.exe (PID: 1560)
- chrome.exe (PID: 2228)
- chrome.exe (PID: 3132)
- chrome.exe (PID: 2972)
- chrome.exe (PID: 756)
- chrome.exe (PID: 2572)
- chrome.exe (PID: 3308)
- chrome.exe (PID: 2080)
- chrome.exe (PID: 320)
- chrome.exe (PID: 2152)
- chrome.exe (PID: 3180)
Reads the computer name
- SearchProtocolHost.exe (PID: 592)
- msiexec.exe (PID: 472)
- WISPTIS.EXE (PID: 1132)
- chrome.exe (PID: 3460)
- chrome.exe (PID: 3924)
- chrome.exe (PID: 2404)
- chrome.exe (PID: 3456)
- chrome.exe (PID: 320)
- chrome.exe (PID: 2152)
Checks Windows Trust Settings
- ReflectorInstaller_softoroom.net.exe (PID: 1240)
- RedGate.Installer.UI.App.exe (PID: 3844)
Application launched itself
- chrome.exe (PID: 3460)
Reads the hosts file
- chrome.exe (PID: 3460)
- chrome.exe (PID: 3924)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
73
Monitored processes
33
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1056,15998019794377077577,2382750080396375653,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2732 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 472 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 592 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 736 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1056,15998019794377077577,2382750080396375653,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3600 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 756 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1056,15998019794377077577,2382750080396375653,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3572 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 880 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6dc7d988,0x6dc7d998,0x6dc7d9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 972 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,15998019794377077577,2382750080396375653,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2284 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1092 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1056,15998019794377077577,2382750080396375653,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2840 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1132 | "C:\Windows\SYSTEM32\WISPTIS.EXE" /ManualLaunch; | C:\Windows\SYSTEM32\WISPTIS.EXE | — | RedGate.Installer.UI.App.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Pen and Touch Input Component Exit code: 24 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1240 | "C:\Users\admin\Desktop\Red Gate .NET Reflector 11.1.0.2167_fu11\ReflectorInstaller_softoroom.net.exe" | C:\Users\admin\Desktop\Red Gate .NET Reflector 11.1.0.2167_fu11\ReflectorInstaller_softoroom.net.exe | Explorer.EXE | ||||||||||||
User: admin Company: Red Gate Software Ltd Integrity Level: HIGH Description: Redgate Installer Exit code: 0 Version: 3.2.4.2829 Modules
| |||||||||||||||
Total events
22 011
Read events
21 824
Write events
187
Delete events
0
Modification events
| (PID) Process: | (3304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3304) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (3304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Red Gate .NET Reflector 11.1.0.2167_fu11.rar | |||
| (PID) Process: | (3304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3304) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
71
Suspicious files
38
Text files
95
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
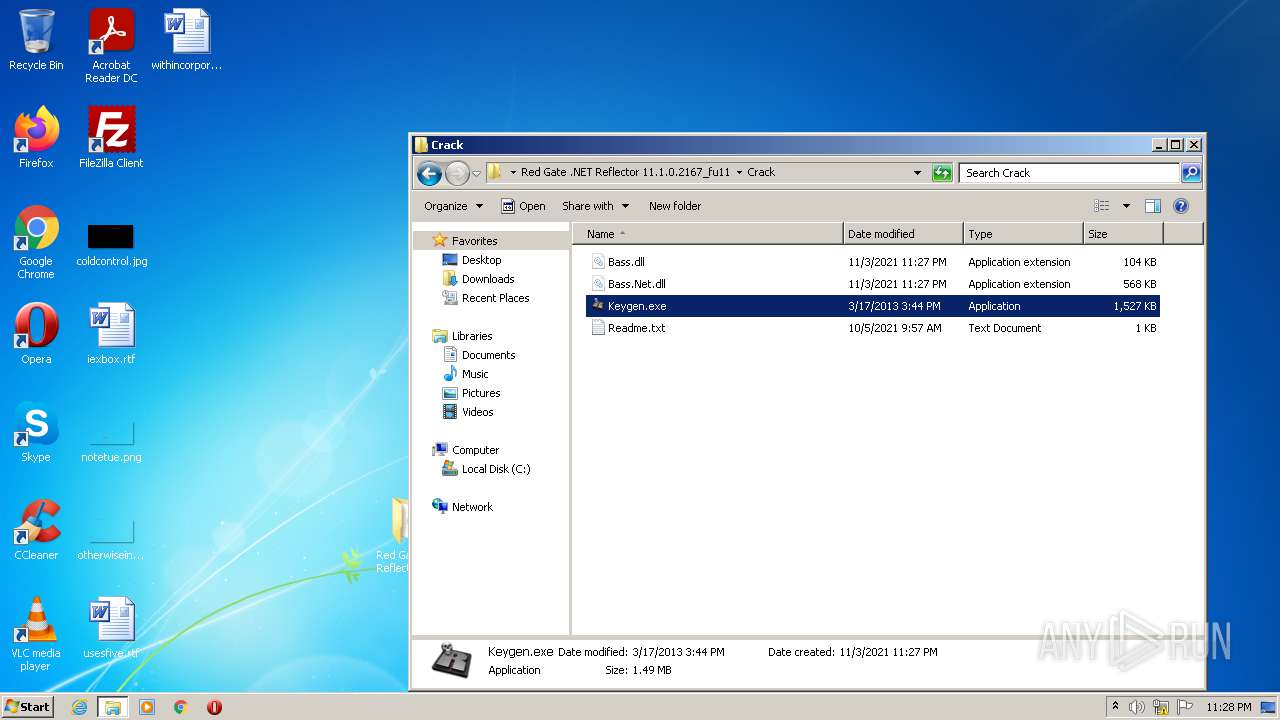
| 3304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3304.19409\Red Gate .NET Reflector 11.1.0.2167_fu11\Crack\Readme.txt | text | |
MD5:— | SHA256:— | |||
| 1240 | ReflectorInstaller_softoroom.net.exe | C:\Users\admin\AppData\Local\Temp\{D4257D52-B9B1-48D8-9CF5-3E91920C19B1}\RedGate.Installer.LongFileName.dll | executable | |
MD5:66248496A67973639D12FD6194354C30 | SHA256:B6244C62195385D31AB104BD768A6F19F87D7DDDEFD11300F7030FCCCB6DB994 | |||
| 1240 | ReflectorInstaller_softoroom.net.exe | C:\Users\admin\AppData\Local\Temp\{D4257D52-B9B1-48D8-9CF5-3E91920C19B1}\INTERNAL_.NET Reflector Visual Studio Extension_11.1.0.2167_x86.msi | executable | |
MD5:197140F00092D29299B9C72FF6A8EAC1 | SHA256:08C9EF763957EF36EB1646D644099C59A65F9378C485655F99C15A4119ACA5B4 | |||
| 1240 | ReflectorInstaller_softoroom.net.exe | C:\Users\admin\AppData\Local\Temp\{D4257D52-B9B1-48D8-9CF5-3E91920C19B1}\SQLToolBeltInstaller.project | pi2 | |
MD5:5C81E1E2241A662C2D11945C4D470640 | SHA256:CDE11EF571E5A9377A51498ABB9EF7AA5C73D12448615E6C514886FF9DF75A75 | |||
| 1240 | ReflectorInstaller_softoroom.net.exe | C:\Users\admin\AppData\Local\Temp\{D4257D52-B9B1-48D8-9CF5-3E91920C19B1}\RedGate.InstallerEngine.Interfaces.dll | executable | |
MD5:C70A4D6F6983E4382CB754D2C3CE68D6 | SHA256:35932E0F8848BD07B673158805AA9075539C2283CD2F424297D17F142DB7B726 | |||
| 3304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3304.19409\Red Gate .NET Reflector 11.1.0.2167_fu11\ReflectorInstaller_softoroom.net.exe | executable | |
MD5:893C74F0DE8BEE456F692976F86AA873 | SHA256:562D649DC21FD1E7F8A17575BC15137EFA6B7BCE7757DD70D9689CB64AC5066C | |||
| 3304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3304.19409\Red Gate .NET Reflector 11.1.0.2167_fu11\Crack\Keygen.exe | executable | |
MD5:31A96483E4CE9E1376EB6A0E6DF5BD08 | SHA256:D3E9558E433828F64C899E51D8CD457F899F6A65CDD0577BD0D760E54CE038C4 | |||
| 1240 | ReflectorInstaller_softoroom.net.exe | C:\Users\admin\AppData\Local\Temp\{D4257D52-B9B1-48D8-9CF5-3E91920C19B1}\ProjectItems.xml | xml | |
MD5:6C2BBD8A39DD397D53491AFA51142D10 | SHA256:5D2220E738965D9BF09C8059317F481962619CB10D5AE9D3536C2978ED730549 | |||
| 1240 | ReflectorInstaller_softoroom.net.exe | C:\Users\admin\AppData\Local\Temp\{D4257D52-B9B1-48D8-9CF5-3E91920C19B1}\RedGate.Installer.ProductParsing.dll | executable | |
MD5:50699D3B8EE7FD679F8250B200ACFEE8 | SHA256:E137C5A53C2FECA697D7FB952A5E7DFA24DF6B16E15069A3819F0FCC9442FFD0 | |||
| 1240 | ReflectorInstaller_softoroom.net.exe | C:\Users\admin\AppData\Local\Temp\{D4257D52-B9B1-48D8-9CF5-3E91920C19B1}\RedGate.Licensing.Client.dll | executable | |
MD5:49CDA4A92EDEA36C67022A8CF71983DC | SHA256:7048454BAE0C12DB8BE32F703DF2B863AC04DC8A348BB31D39110E661FA720D3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
23
DNS requests
14
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3924 | chrome.exe | 142.250.74.206:443 | clients2.google.com | Google Inc. | US | whitelisted |
3924 | chrome.exe | 142.250.184.196:443 | www.google.com | Google Inc. | US | whitelisted |
3924 | chrome.exe | 142.250.185.67:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3924 | chrome.exe | 142.250.185.161:443 | lh5.googleusercontent.com | Google Inc. | US | whitelisted |
3924 | chrome.exe | 142.250.184.206:443 | apis.google.com | Google Inc. | US | whitelisted |
— | — | 142.250.186.78:443 | encrypted-tbn0.gstatic.com | Google Inc. | US | whitelisted |
3924 | chrome.exe | 142.250.186.99:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3924 | chrome.exe | 142.250.186.74:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3924 | chrome.exe | 142.250.186.78:443 | encrypted-tbn0.gstatic.com | Google Inc. | US | whitelisted |
3924 | chrome.exe | 142.250.186.163:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
productusage.red-gate.com |
| malicious |
featureusage.red-gate.com |
| malicious |
clientservices.googleapis.com |
| whitelisted |
www.google.com |
| malicious |
clients2.google.com |
| whitelisted |
accounts.google.com |
| shared |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3924 | chrome.exe | Generic Protocol Command Decode | SURICATA STREAM CLOSEWAIT FIN out of window |