| File name: | 9R1B.exe |
| Full analysis: | https://app.any.run/tasks/60c31665-44b8-41e2-98f9-592e7c8b778e |
| Verdict: | Malicious activity |
| Analysis date: | March 13, 2018, 06:47:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 1501EB7322E4839A66FEFD60D6C6A91C |
| SHA1: | 211C558BD7BAC8FAE038AD4489733B92DA998261 |
| SHA256: | 40784B2C14F7726B2B6227D8CC5C935D8FE4057D3A2D70DD5F224E619296651B |
| SSDEEP: | 393216:mVDj9QDcHESlos2UW9qiGoTQXSHNDfQ+8HwBn3Htzxx5pvVhcU:a5QDCEkoJPs7SH8qn3d5psU |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the Windows directory
- 9R1B.exe (PID: 3524)
Creates or modifies windows services
- 9R1B.exe (PID: 3524)
Modifies files in the system directory
- 9R1B.exe (PID: 3524)
Creates files in the driver directory
- 9R1B.exe (PID: 3524)
Removes files from Windows directory
- 9R1B.exe (PID: 3524)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| PEType: | PE32 |
| LinkerVersion: | - |
| CodeSize: | - |
| InitializedDataSize: | - |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2858f8b |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
36
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3340 | "C:\Users\admin\AppData\Local\Temp\9R1B.exe" | C:\Users\admin\AppData\Local\Temp\9R1B.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 | |||||||||||||||
| 3524 | "C:\Users\admin\AppData\Local\Temp\9R1B.exe" | C:\Users\admin\AppData\Local\Temp\9R1B.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
12
Read events
10
Write events
2
Delete events
0
Modification events
| (PID) Process: | (3524) 9R1B.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\Tcpip\Parameters |
| Operation: | write | Name: | DataBasePath |
Value: %SystemRoot%\System32\drivers\ | |||
Executable files
0
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3524 | 9R1B.exe | C:\Windows\System32\drivers\etc\hosts | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
20
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 92.222.82.85:80 | http://auth.memoryhackers.net/LeftSpaceV3/hDelirkudur.php | FR | binary | 2.55 Kb | unknown |
— | — | GET | 200 | 92.222.82.85:80 | http://auth.memoryhackers.net/LeftSpaceV3/Loader.php | FR | binary | 192 b | unknown |
— | — | GET | 200 | 92.222.82.85:80 | http://auth.memoryhackers.net/LeftSpaceV3/root_delir.php | FR | binary | 800 b | unknown |
— | — | POST | 200 | 92.222.82.85:80 | http://auth.memoryhackers.net/index.php | FR | — | — | unknown |
— | — | GET | 200 | 92.222.82.85:80 | http://auth.memoryhackers.net/LeftSpaceV3/lists-update.php | FR | binary | 5.13 Kb | unknown |
— | — | POST | 200 | 92.222.82.85:80 | http://auth.memoryhackers.net/KeyGen.php | FR | text | 20 b | unknown |
— | — | GET | 200 | 92.222.82.85:80 | http://auth.memoryhackers.net/LeftSpaceV3/images/ros.png | FR | image | 3.02 Kb | unknown |
— | — | GET | 200 | 92.222.82.85:80 | http://auth.memoryhackers.net/LeftSpaceV3/images/wolfteam.png | FR | image | 1.91 Kb | unknown |
— | — | GET | 200 | 92.222.82.85:80 | http://auth.memoryhackers.net/LeftSpaceV3/images/wolfteam.png | FR | image | 1.91 Kb | unknown |
— | — | GET | 200 | 92.222.82.85:80 | http://auth.memoryhackers.net/getNicknamebyads.php | FR | text | 9 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 92.222.82.85:80 | auth.memoryhackers.net | OVH SAS | FR | unknown |
— | — | 92.222.82.85:4000 | auth.memoryhackers.net | OVH SAS | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
auth.memoryhackers.net |
| unknown |
teredo.ipv6.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
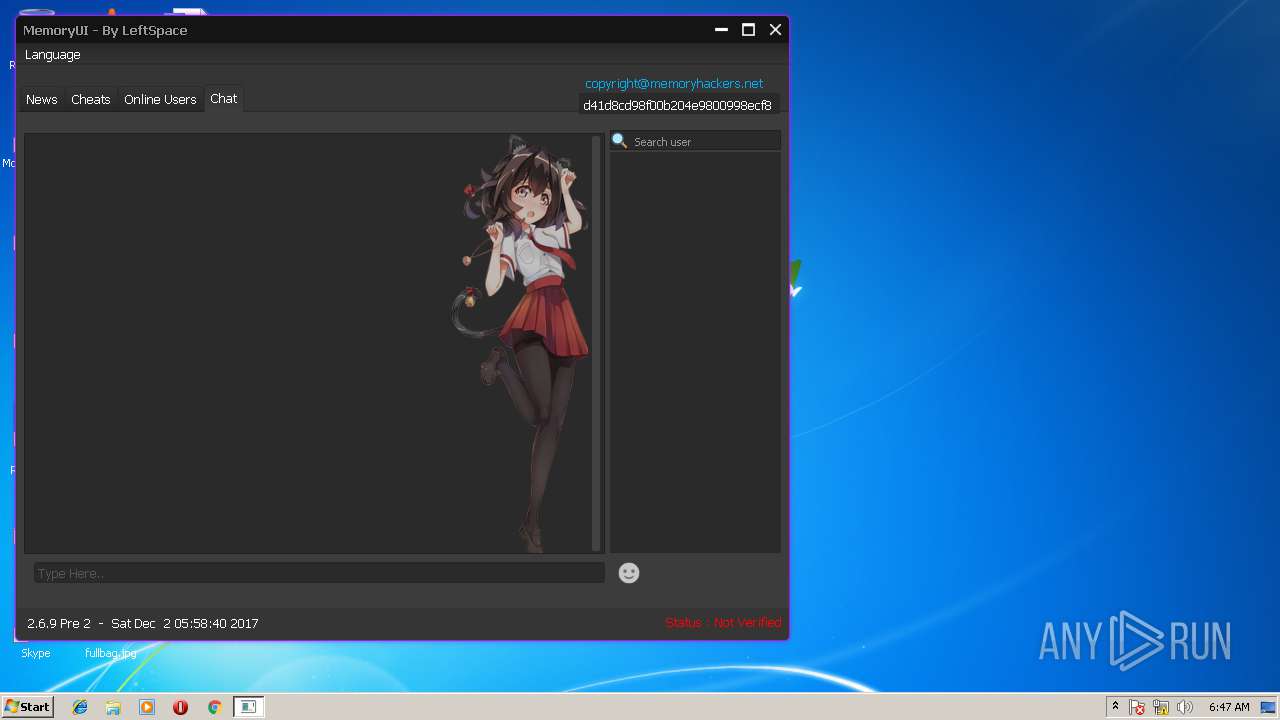
9R1B.exe | WARNING: QApplication was not created in the main() thread.
|
9R1B.exe | QWidget: Incompatible window flags: the window can't be on top and on bottom at the same time
|
9R1B.exe | QMetaObject::connectSlotsByName: No matching signal for on_keySequenceEdit_keySequenceChanged(QKeySequence)
|
9R1B.exe | QMetaObject::connectSlotsByName: No matching signal for on_pushButton_clicked()
|
9R1B.exe | libpng warning: iCCP: known incorrect sRGB profile
|