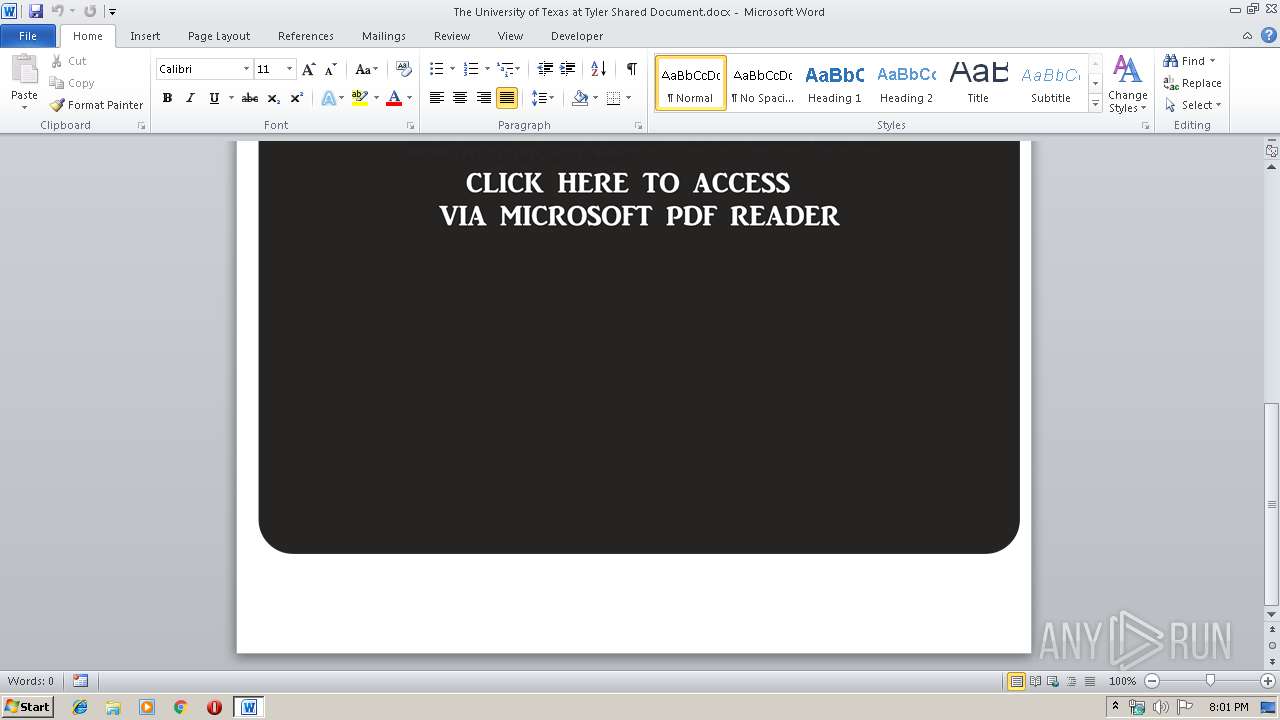
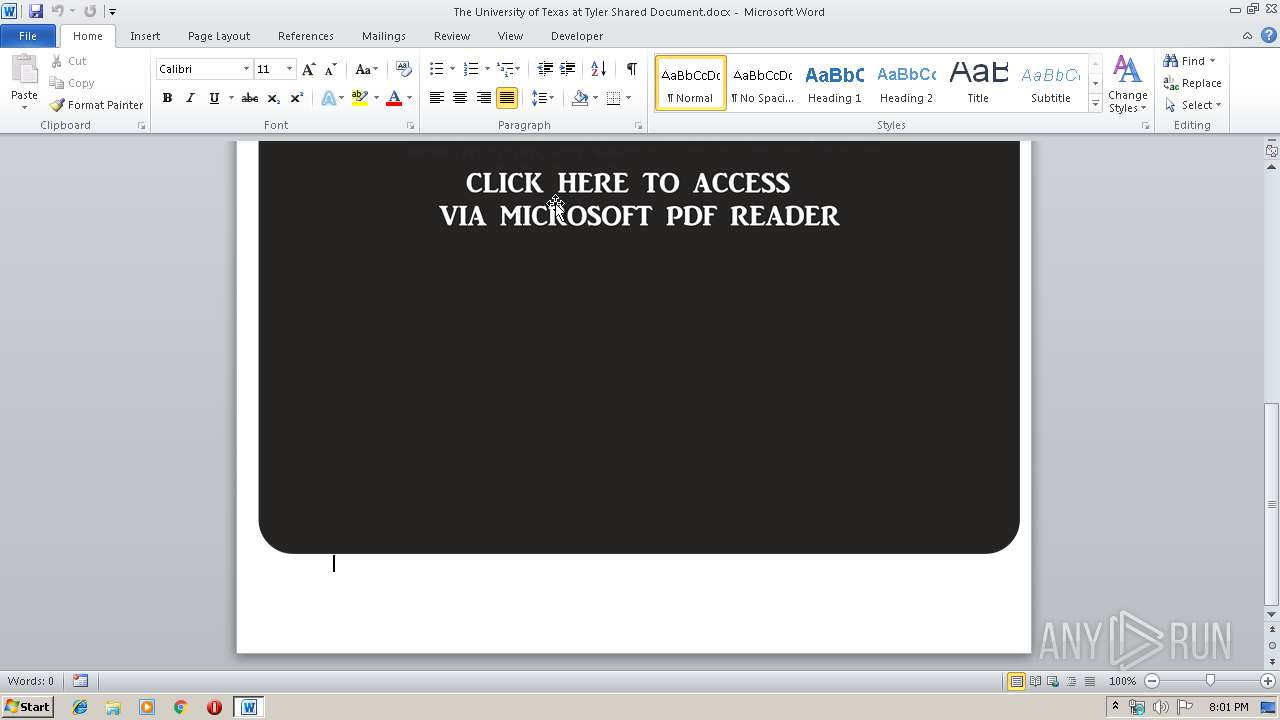
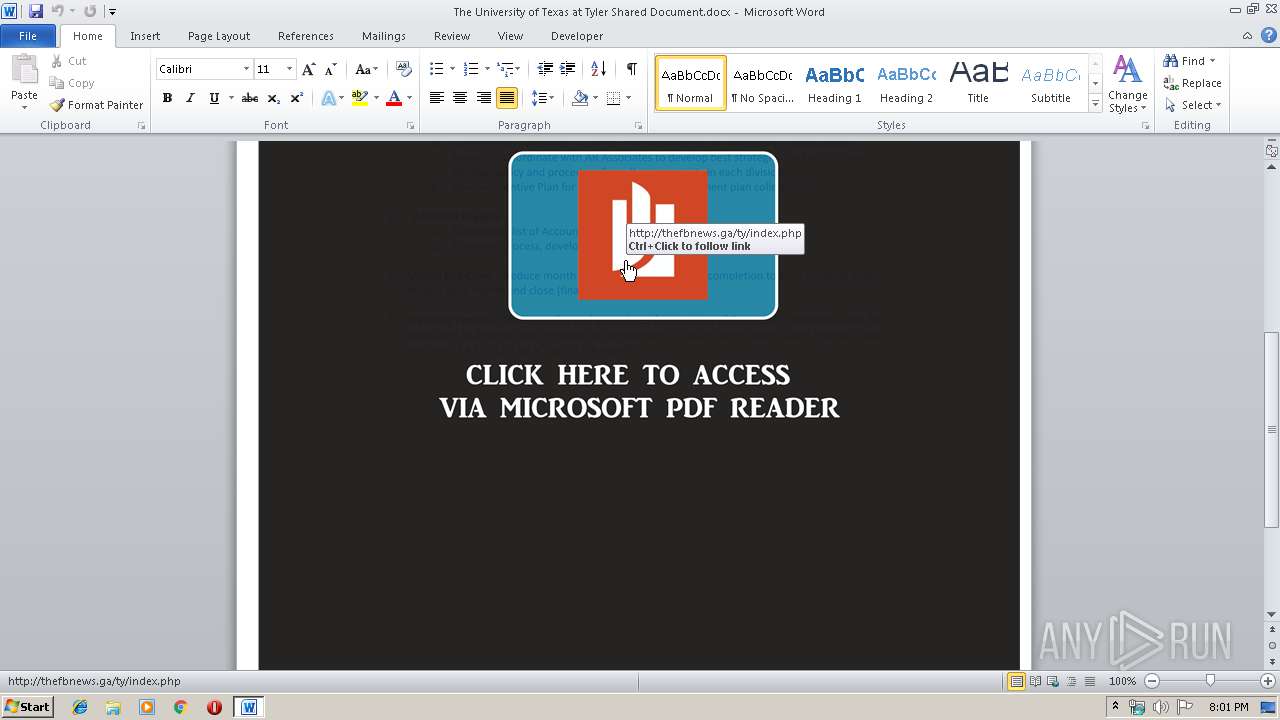
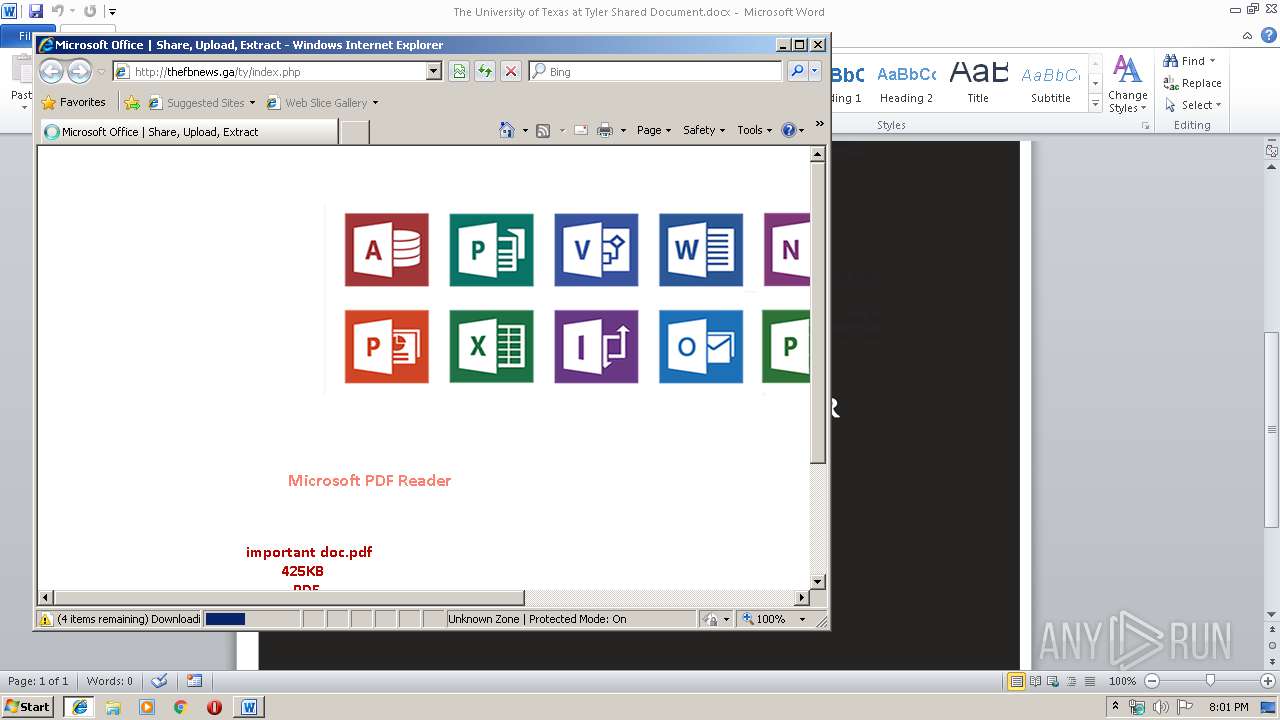
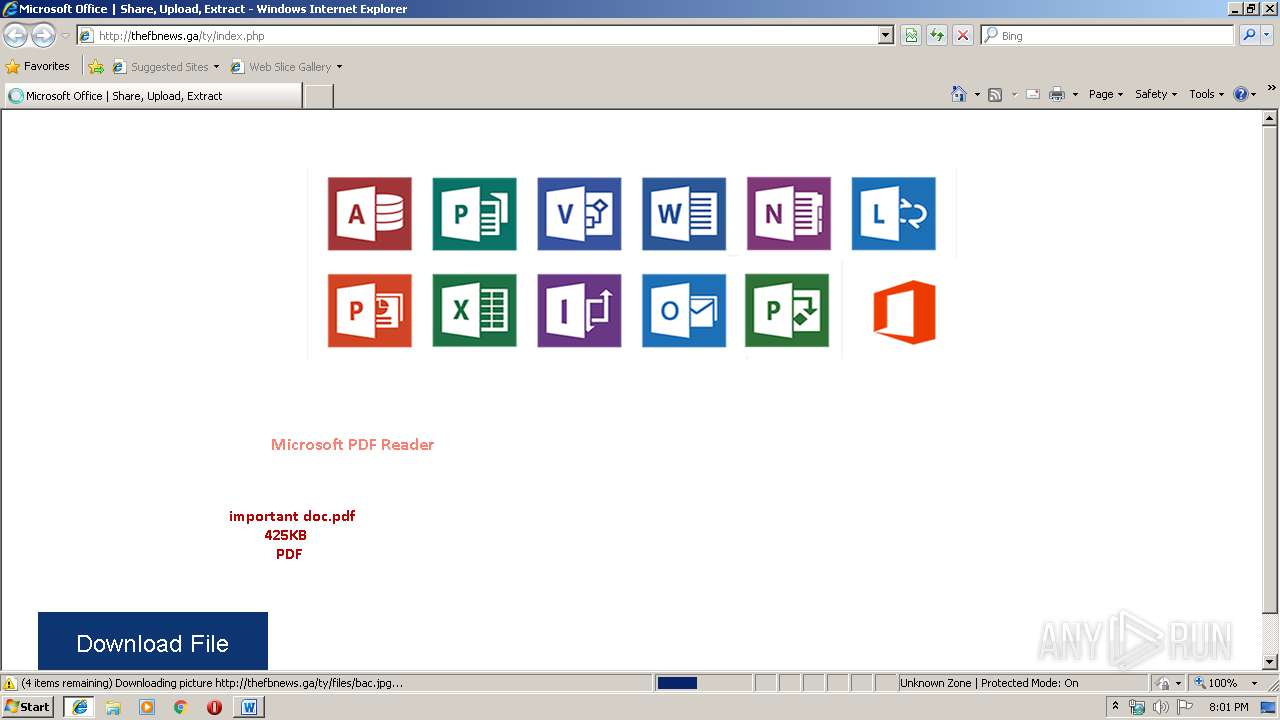
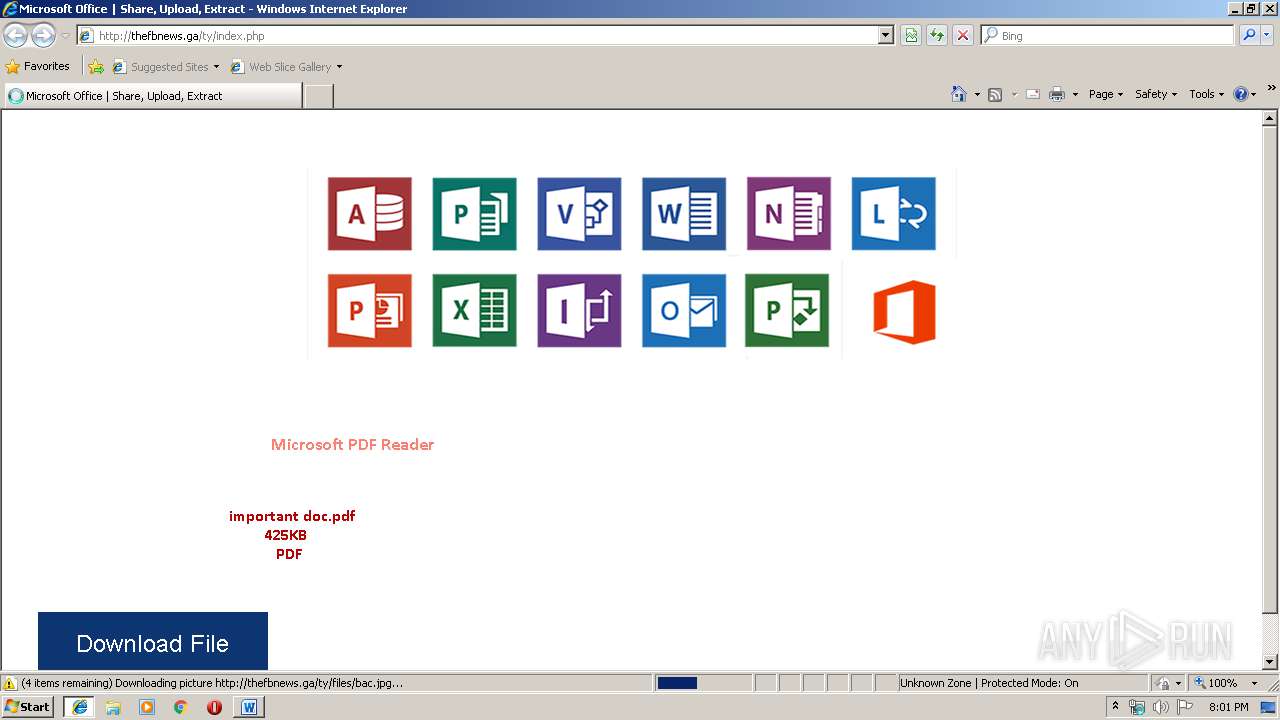
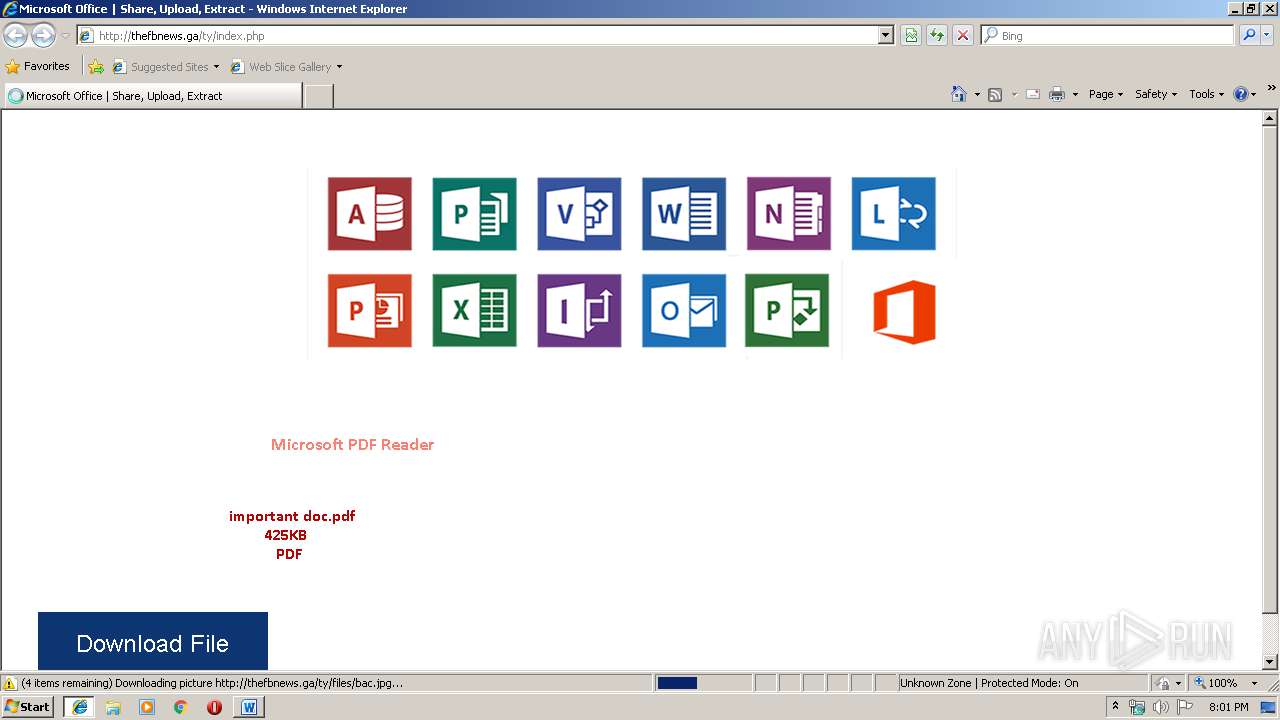
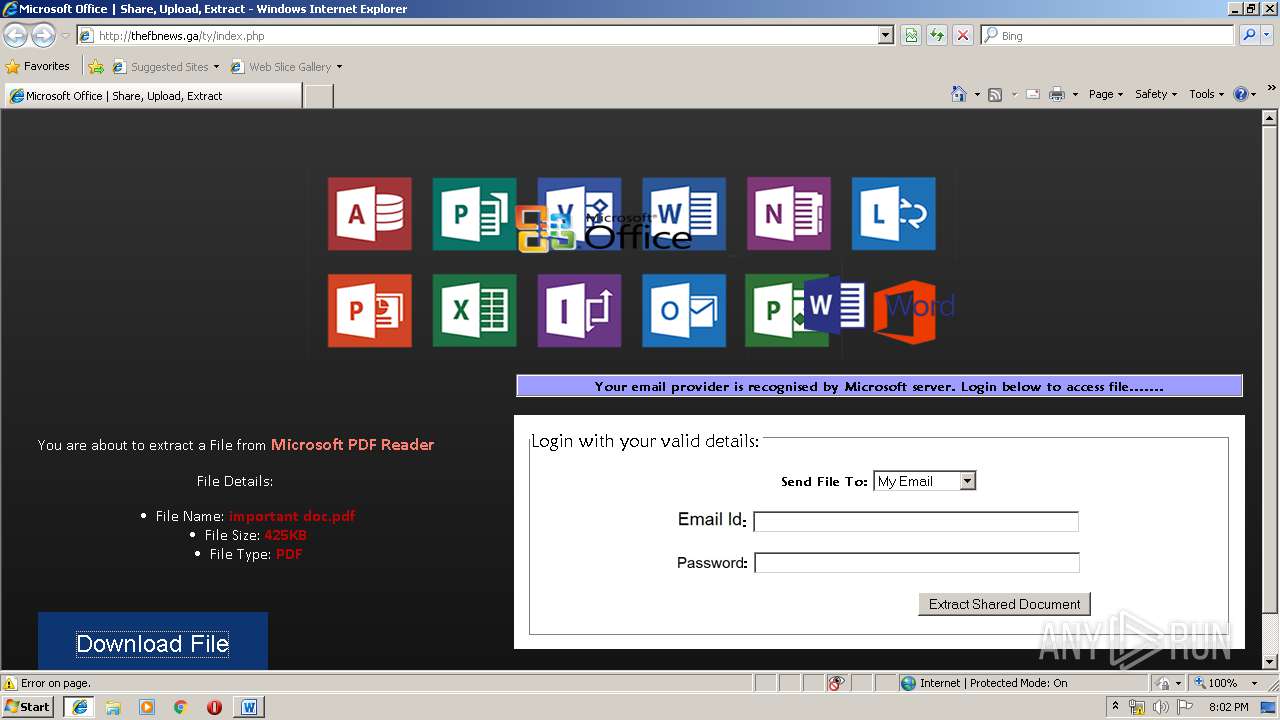
| File name: | The University of Texas at Tyler Shared Document.docx |
| Full analysis: | https://app.any.run/tasks/68c11d0e-fe61-4a8c-a49f-0bfa7bfe019d |
| Verdict: | Malicious activity |
| Analysis date: | March 21, 2019, 20:01:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 39E6B238E3ABDD48507337C0C2344A84 |
| SHA1: | 8C48B8A67C43169E06C86B121A40007A32FD47A2 |
| SHA256: | 406CB9DB6069F65BB8011AFE747ED6F8F6C04A9BFD48C588044AC4056FA87F71 |
| SSDEEP: | 6144:SpCX2M3UQ0KRgZupngVOsVPTlA1qmgIDOBGefB:c0EJkgomrV7uxfeZ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads internet explorer settings
- WINWORD.EXE (PID: 3480)
Unusual connect from Microsoft Office
- WINWORD.EXE (PID: 3480)
Creates files in the program directory
- AdobeARM.exe (PID: 3564)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3480)
Application launched itself
- AcroRd32.exe (PID: 3276)
- iexplore.exe (PID: 3720)
- RdrCEF.exe (PID: 2320)
Creates files in the user directory
- WINWORD.EXE (PID: 3480)
- iexplore.exe (PID: 3716)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3716)
Reads internet explorer settings
- iexplore.exe (PID: 3716)
Changes internet zones settings
- iexplore.exe (PID: 3720)
Reads Internet Cache Settings
- iexplore.exe (PID: 3716)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x1dbbefa3 |
| ZipCompressedSize: | 357 |
| ZipUncompressedSize: | 1362 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | - |
|---|---|
| Creator: | JUSTIN MONTAGE |
XML
| LastModifiedBy: | laurie victoria |
|---|---|
| RevisionNumber: | 2 |
| LastPrinted: | 2018:04:09 16:12:00Z |
| CreateDate: | 2019:03:20 17:57:00Z |
| ModifyDate: | 2019:03:20 17:57:00Z |
| Template: | Normal.dotm |
| TotalEditTime: | - |
| Pages: | 1 |
| Words: | - |
| Characters: | 1 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| Company: | Hewlett-Packard |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 1 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
Total processes
44
Monitored processes
12
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2320 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2376 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer /o /eo /l /b /id 3716 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 3104 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe | — | AdobeARM.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat SpeedLauncher Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 3124 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" /o /eo /l /b /id 3716 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | iexplore.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 3256 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="2320.2.1684406801\154422440" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 3276 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" /o /eo /l /b /id 3716 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | iexplore.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 3480 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\The University of Texas at Tyler Shared Document.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3564 | "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Reader /VERSION:15.0 /MODE:3 | C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.824.27.2646 Modules
| |||||||||||||||
| 3716 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3720 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3720 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 040
Read events
1 331
Write events
703
Delete events
6
Modification events
| (PID) Process: | (3480) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 6#= |
Value: 36233D00980D0000010000000000000000000000 | |||
| (PID) Process: | (3480) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3480) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3480) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1316290590 | |||
| (PID) Process: | (3480) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1316290704 | |||
| (PID) Process: | (3480) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1316290705 | |||
| (PID) Process: | (3480) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 980D0000F6F75CD820E0D40100000000 | |||
| (PID) Process: | (3480) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | o$= |
Value: 6F243D00980D000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3480) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | o$= |
Value: 6F243D00980D000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3480) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
3
Text files
46
Unknown types
24
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3480 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR716.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3720 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3720 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3480 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF5468EF0A3EA62FA1.TMP | — | |
MD5:— | SHA256:— | |||
| 3480 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3480 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$e University of Texas at Tyler Shared Document.docx | pgc | |
MD5:— | SHA256:— | |||
| 3480 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\index[1].htm | html | |
MD5:— | SHA256:— | |||
| 3716 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
| 3716 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\TJUQFCCI\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
| 3716 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\NCAGDB46\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
32
DNS requests
10
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
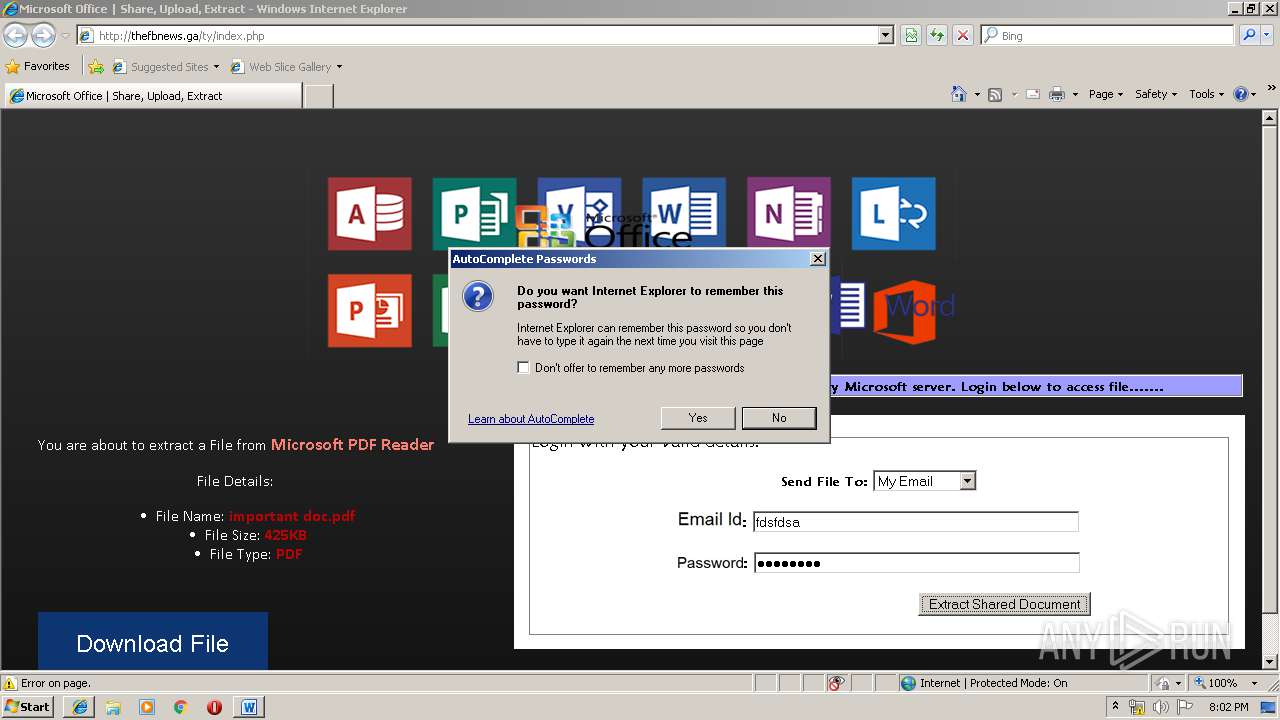
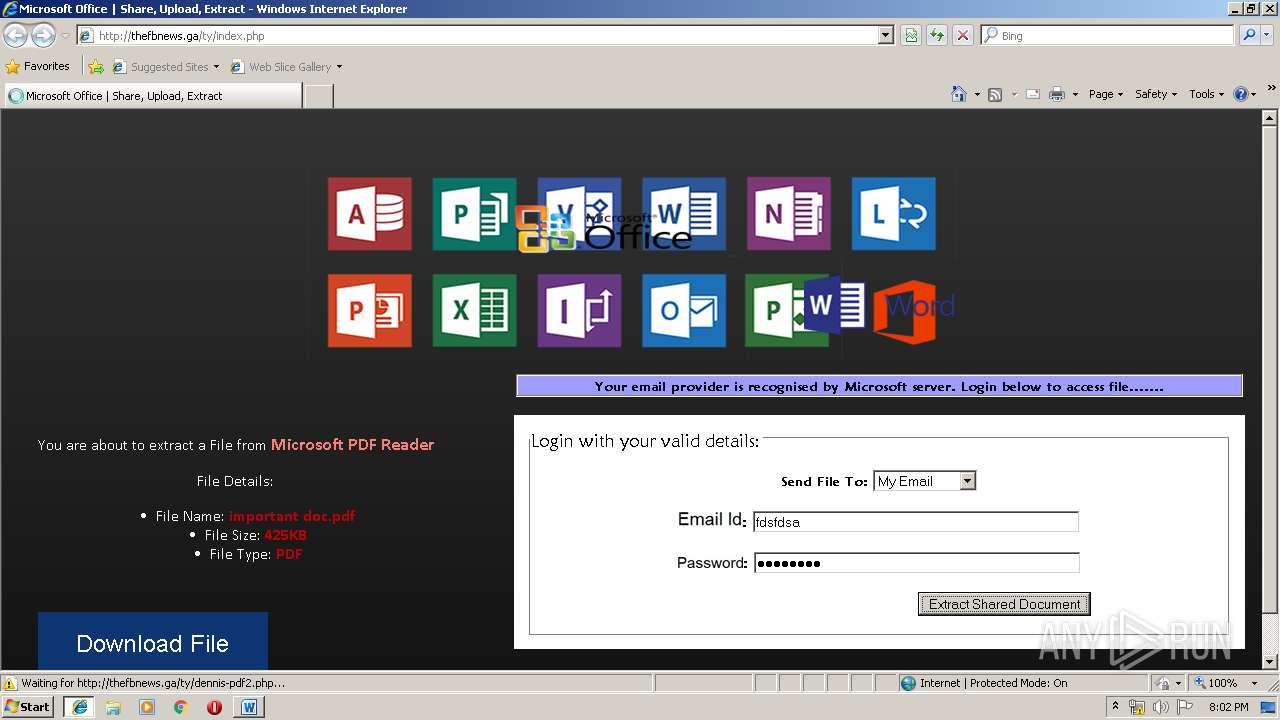
3716 | iexplore.exe | GET | 200 | 204.152.207.69:80 | http://thefbnews.ga/ty/files/lnkr5.js | US | text | 5.55 Kb | suspicious |
3716 | iexplore.exe | GET | 404 | 204.152.207.69:80 | http://thefbnews.ga/ty/mm.jpg | US | html | 326 b | suspicious |
3716 | iexplore.exe | GET | 200 | 204.152.207.69:80 | http://thefbnews.ga/ty/index.php | US | html | 5.29 Kb | suspicious |
3716 | iexplore.exe | GET | 200 | 204.152.207.69:80 | http://thefbnews.ga/ty/files/oflog.png | US | image | 63.4 Kb | suspicious |
3716 | iexplore.exe | GET | 200 | 204.152.207.69:80 | http://thefbnews.ga/ty/files/wrdd.png | US | image | 6.37 Kb | suspicious |
3716 | iexplore.exe | GET | 404 | 204.152.207.69:80 | http://thefbnews.ga/ty/files/whoami | US | html | 332 b | suspicious |
3480 | WINWORD.EXE | GET | 200 | 204.152.207.69:80 | http://thefbnews.ga/ty/index.php | US | html | 5.29 Kb | suspicious |
3716 | iexplore.exe | GET | 200 | 138.201.253.3:80 | http://urlvalidation.com/whoami?jsonp=func10098 | DE | text | 57 b | malicious |
3716 | iexplore.exe | GET | 200 | 204.152.207.69:80 | http://thefbnews.ga/ty/files/email-validation.js | US | html | 97 b | suspicious |
3716 | iexplore.exe | GET | 200 | 204.152.207.69:80 | http://thefbnews.ga/ty/files/p.jpg | US | image | 3.51 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3480 | WINWORD.EXE | 204.152.207.69:80 | thefbnews.ga | QuadraNet, Inc | US | suspicious |
3720 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3716 | iexplore.exe | 204.152.207.69:80 | thefbnews.ga | QuadraNet, Inc | US | suspicious |
3716 | iexplore.exe | 138.201.253.3:80 | urlvalidation.com | Hetzner Online GmbH | DE | suspicious |
3720 | iexplore.exe | 204.152.207.69:80 | thefbnews.ga | QuadraNet, Inc | US | suspicious |
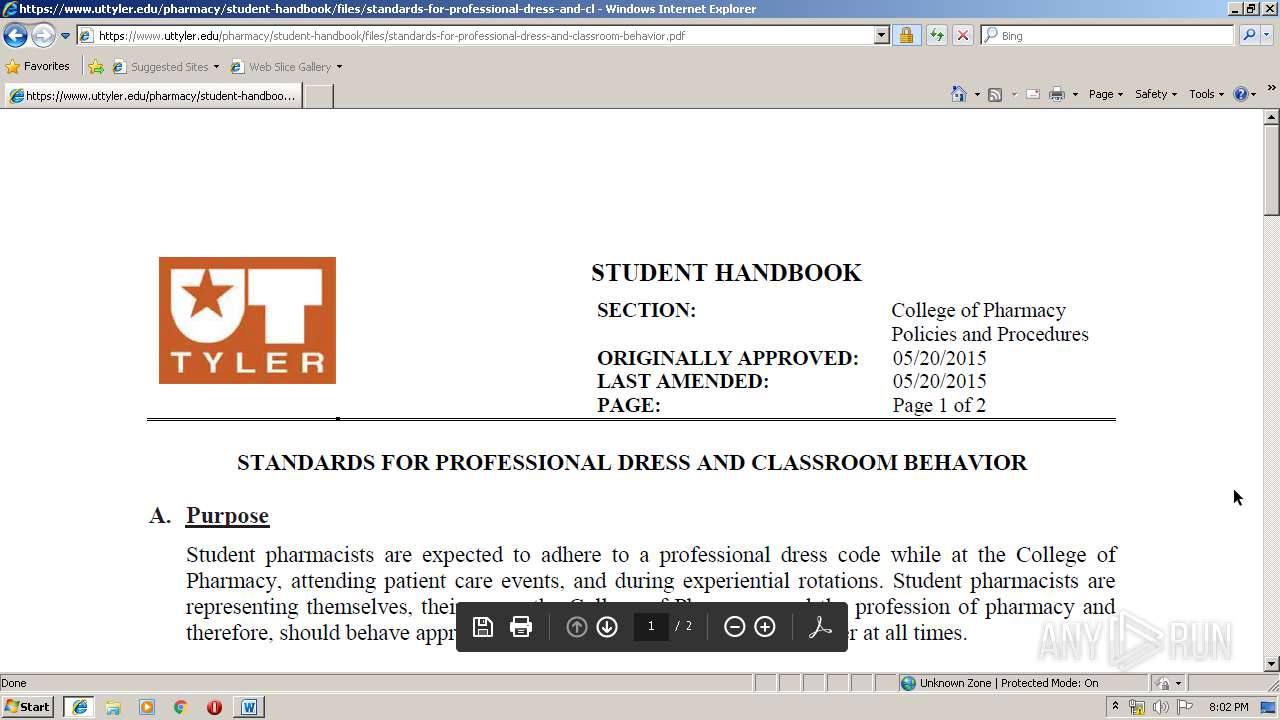
3716 | iexplore.exe | 104.214.68.202:443 | www.uttyler.edu | Microsoft Corporation | US | unknown |
3716 | iexplore.exe | 91.199.212.52:80 | crt.usertrust.com | Comodo CA Ltd | GB | suspicious |
3276 | AcroRd32.exe | 2.16.186.32:80 | acroipm2.adobe.com | Akamai International B.V. | — | whitelisted |
— | — | 2.18.68.206:443 | ardownload2.adobe.com | Akamai International B.V. | — | whitelisted |
3276 | AcroRd32.exe | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
thefbnews.ga |
| suspicious |
www.bing.com |
| whitelisted |
lancheck.net |
| malicious |
urlvalidation.com |
| malicious |
www.uttyler.edu |
| unknown |
crt.usertrust.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
ardownload2.adobe.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .ga Domain |
3716 | iexplore.exe | A Network Trojan was detected | SUSPICIOUS [PTsecurity] Successful PDF Online Phishing |
3716 | iexplore.exe | Potentially Bad Traffic | ET INFO HTTP POST Request to Suspicious *.ga Domain |
3 ETPRO signatures available at the full report