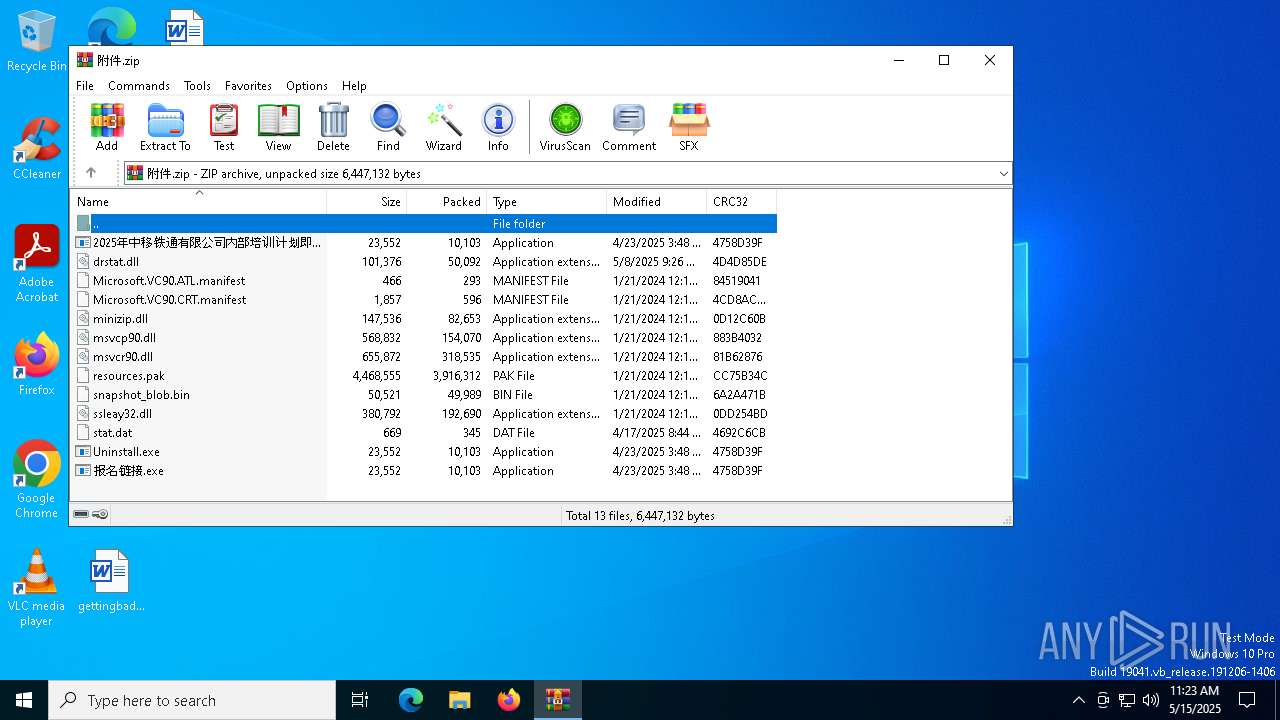
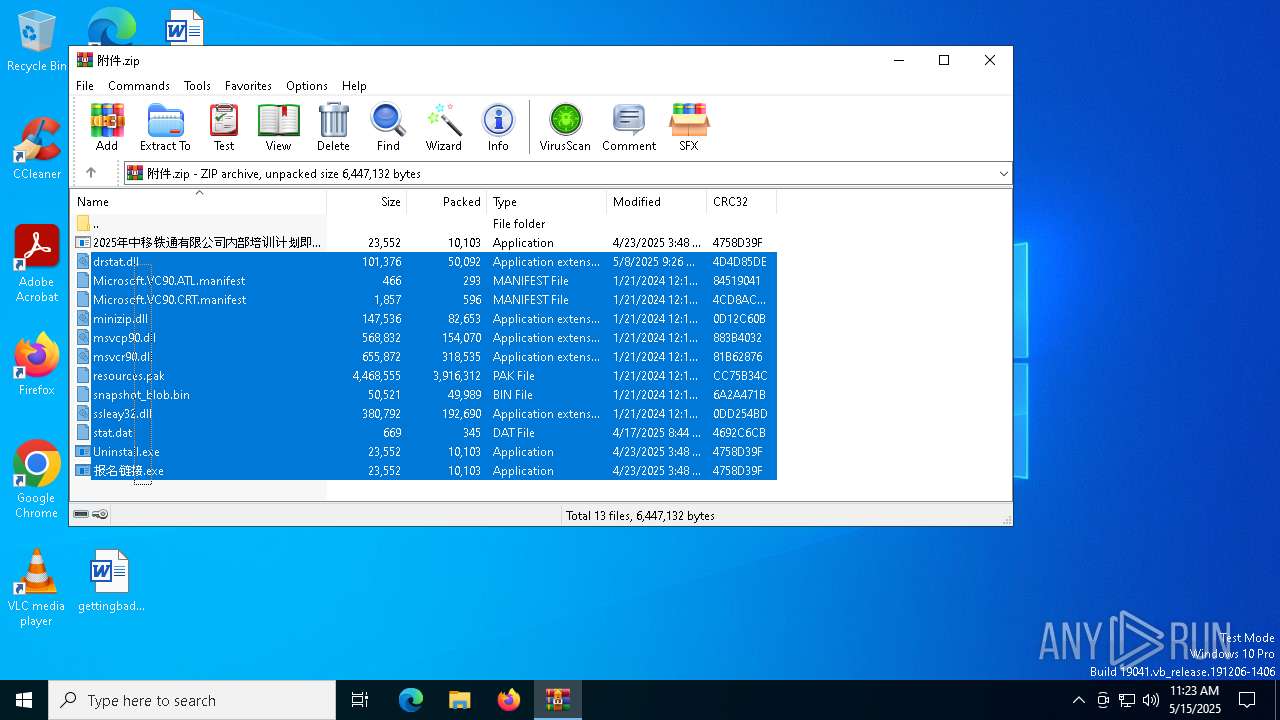
| File name: | 附件.zip |
| Full analysis: | https://app.any.run/tasks/ed8aa77f-8695-4159-8786-99e66c911eeb |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 11:23:11 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | B12D2E01BD88630C9DA08F06DA7DC594 |
| SHA1: | 5B681E3C6F8E488164B0424908BDDB79CC22950C |
| SHA256: | 40450B4212481492D2213D109A0CD0F42DE8E813DE42D53360DA7EFAC7249DF4 |
| SSDEEP: | 98304:pqK+N8nhCDTzC6aOnv2pzD4AliCciPYljRVKv4JctCaOjwtVeQA2o4uJJlAh73Q3:f0txsk9 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 660)
Connects to unusual port
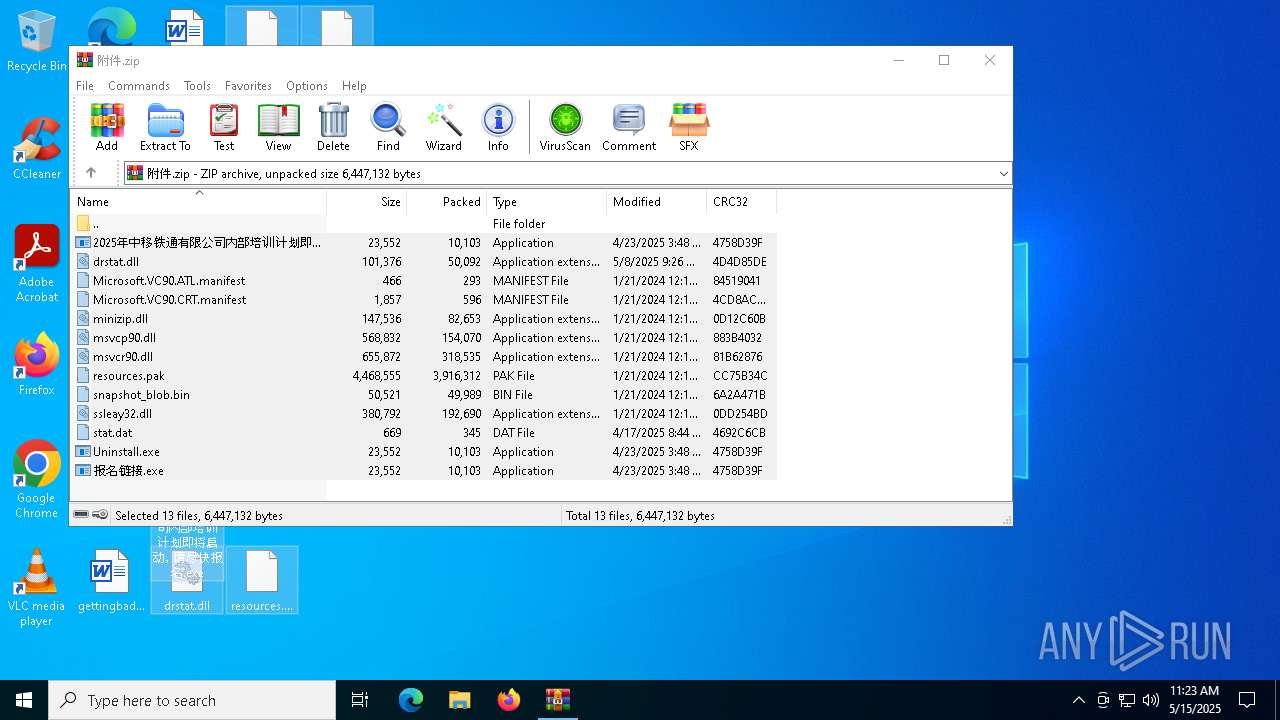
- 2025年中移铁通有限公司内部培训计划即将启动,请尽快报名.exe (PID: 7672)
- Uninstall.exe (PID: 7776)
- 报名链接.exe (PID: 7872)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 660)
The sample compiled with chinese language support
- WinRAR.exe (PID: 660)
Checks supported languages
- 2025年中移铁通有限公司内部培训计划即将启动,请尽快报名.exe (PID: 7672)
- Uninstall.exe (PID: 7776)
- 报名链接.exe (PID: 7872)
Manual execution by a user
- 报名链接.exe (PID: 7872)
- 2025年中移铁通有限公司内部培训计划即将启动,请尽快报名.exe (PID: 7672)
- Uninstall.exe (PID: 7776)
Reads the computer name
- Uninstall.exe (PID: 7776)
- 报名链接.exe (PID: 7872)
- 2025年中移铁通有限公司内部培训计划即将启动,请尽快报名.exe (PID: 7672)
Reads the software policy settings
- slui.exe (PID: 3300)
- slui.exe (PID: 7244)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 660)
Checks proxy server information
- slui.exe (PID: 3300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:23 11:48:48 |
| ZipCRC: | 0x4758d39f |
| ZipCompressedSize: | 10103 |
| ZipUncompressedSize: | 23552 |
| ZipFileName: | 2025????????ͨ????˾?ڲ???ѵ?ƻ????????????뾡?챨??.exe |
Total processes
140
Monitored processes
10
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\附件.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3300 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7212 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7244 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7672 | "C:\Users\admin\Desktop\2025年中移铁通有限公司内部培训计划即将启动,请尽快报名.exe" | C:\Users\admin\Desktop\2025年中移铁通有限公司内部培训计划即将启动,请尽快报名.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7680 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 2025年中移铁通有限公司内部培训计划即将启动,请尽快报名.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7776 | "C:\Users\admin\Desktop\Uninstall.exe" | C:\Users\admin\Desktop\Uninstall.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7784 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Uninstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7872 | "C:\Users\admin\Desktop\报名链接.exe" | C:\Users\admin\Desktop\报名链接.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7880 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 报名链接.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 250
Read events
3 242
Write events
8
Delete events
0
Modification events
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\附件.zip | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
8
Suspicious files
1
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa660.1832\resources.pak | — | |
MD5:— | SHA256:— | |||
| 660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa660.1832\Microsoft.VC90.ATL.manifest | xml | |
MD5:B41644A01C05740576B4E77662C7E86C | SHA256:A9A98FC7062262A47A1C0727339C760D18589B8549E4267762F7F4C88A103632 | |||
| 660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa660.1832\2025年中移铁通有限公司内部培训计划即将启动,请尽快报名.exe | executable | |
MD5:3199796DC2AD51DA41DA51DE58D31012 | SHA256:645F9F81EB83E52BBBD0726E5BF418F8235DD81BA01B6A945F8D6A31BF406992 | |||
| 660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa660.1832\minizip.dll | executable | |
MD5:2823CD80172EF7D8C42FD2EB28B83A15 | SHA256:788467A9C7D8F54AED0630C349EB84329EA2D228CFA110B35C6D86BEB87579BE | |||
| 660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa660.1832\msvcr90.dll | executable | |
MD5:E7D91D008FE76423962B91C43C88E4EB | SHA256:ED0170D3DE86DA33E02BFA1605EEC8FF6010583481B1C530843867C1939D2185 | |||
| 660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa660.1832\msvcp90.dll | executable | |
MD5:6DE5C66E434A9C1729575763D891C6C2 | SHA256:4F7ED27B532888CE72B96E52952073EAB2354160D1156924489054B7FA9B0B1A | |||
| 660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa660.1832\Uninstall.exe | executable | |
MD5:3199796DC2AD51DA41DA51DE58D31012 | SHA256:645F9F81EB83E52BBBD0726E5BF418F8235DD81BA01B6A945F8D6A31BF406992 | |||
| 660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa660.1832\snapshot_blob.bin | binary | |
MD5:C3624C0378FFC720D5F72AF9DECF7E92 | SHA256:FBCCA4C181C06A56EA4DB708FD3EBBEC40CD6769BC754C7FB19F123EADC7CBF6 | |||
| 660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa660.1832\drstat.dll | executable | |
MD5:81F76F83D4C571FE95772F21AFF4D0B9 | SHA256:AC6E0EE1328CFB1B6CA0541E4DFE7BA6398EA79A300C4019253BD908AB6A3DC0 | |||
| 660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa660.1832\Microsoft.VC90.CRT.manifest | xml | |
MD5:4F9ED5EFA4F7B75BCFE0F36C36EE5CB6 | SHA256:FF718390133B400EE679177B2902BBB918DB148BBB4ABABA03D0A1DF325B3303 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
35
DNS requests
18
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8000 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8000 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.113:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.113:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7672 | 2025年中移铁通有限公司内部培训计划即将启动,请尽快报名.exe | Potentially Bad Traffic | PAYLOAD [ANY.RUN] XORed Windows executable has been loaded |
7776 | Uninstall.exe | Potentially Bad Traffic | PAYLOAD [ANY.RUN] XORed Windows executable has been loaded |
7872 | 报名链接.exe | Potentially Bad Traffic | PAYLOAD [ANY.RUN] XORed Windows executable has been loaded |