| File name: | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee |
| Full analysis: | https://app.any.run/tasks/ccd99019-fced-421a-8997-c41855539536 |
| Verdict: | Malicious activity |
| Analysis date: | May 22, 2025, 00:30:28 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 17CF50251C8B8BECA41A42E18C57C168 |
| SHA1: | 80DC23E899978FAD88DC43F33591C9CCBCD56B5B |
| SHA256: | 3FEF649CF29BC6BF16B960E14532BFCB0F8BDD1BE13E4983E9026E16CF4759A6 |
| SSDEEP: | 98304:RSyydgpXBA5x+ozs7TbighABgE5GIR6RZdIVEwDidHtB0XUle3yF45vfc0oGN7ex:snBs7Ws0/COi |
MALICIOUS
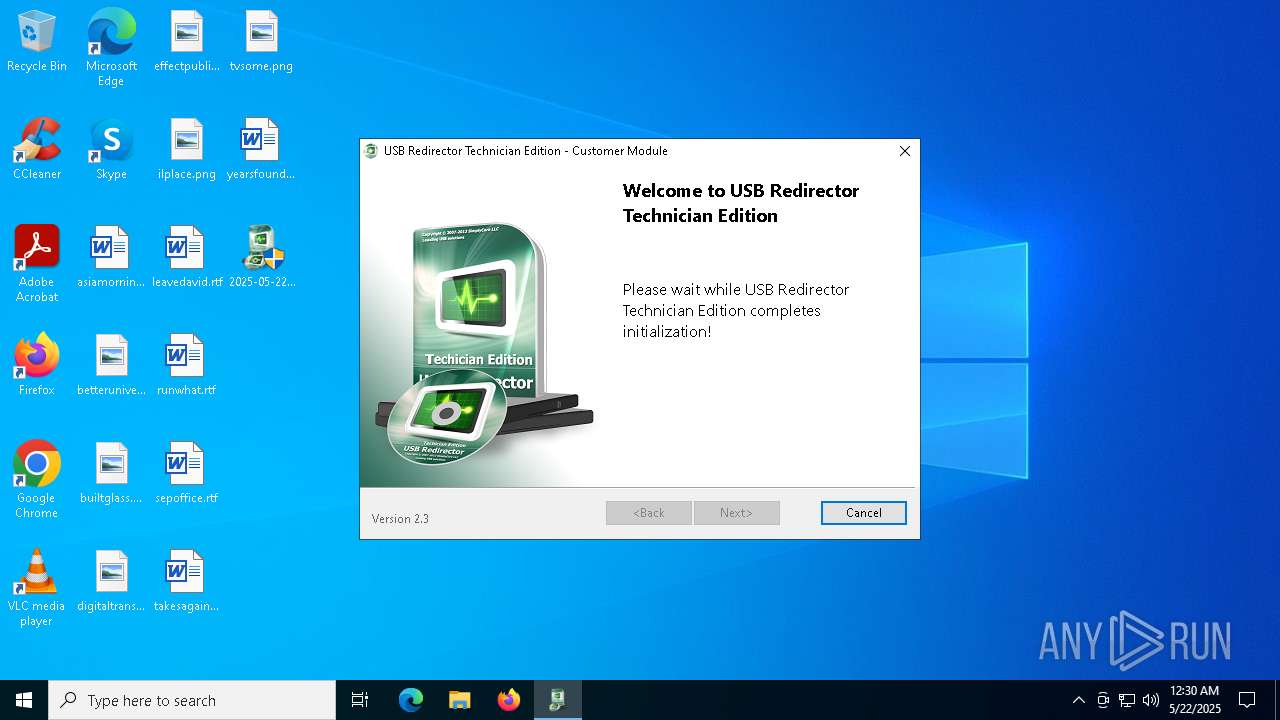
Executing a file with an untrusted certificate
- 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe (PID: 7564)
Connects to the CnC server
- 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe (PID: 7564)
SUSPICIOUS
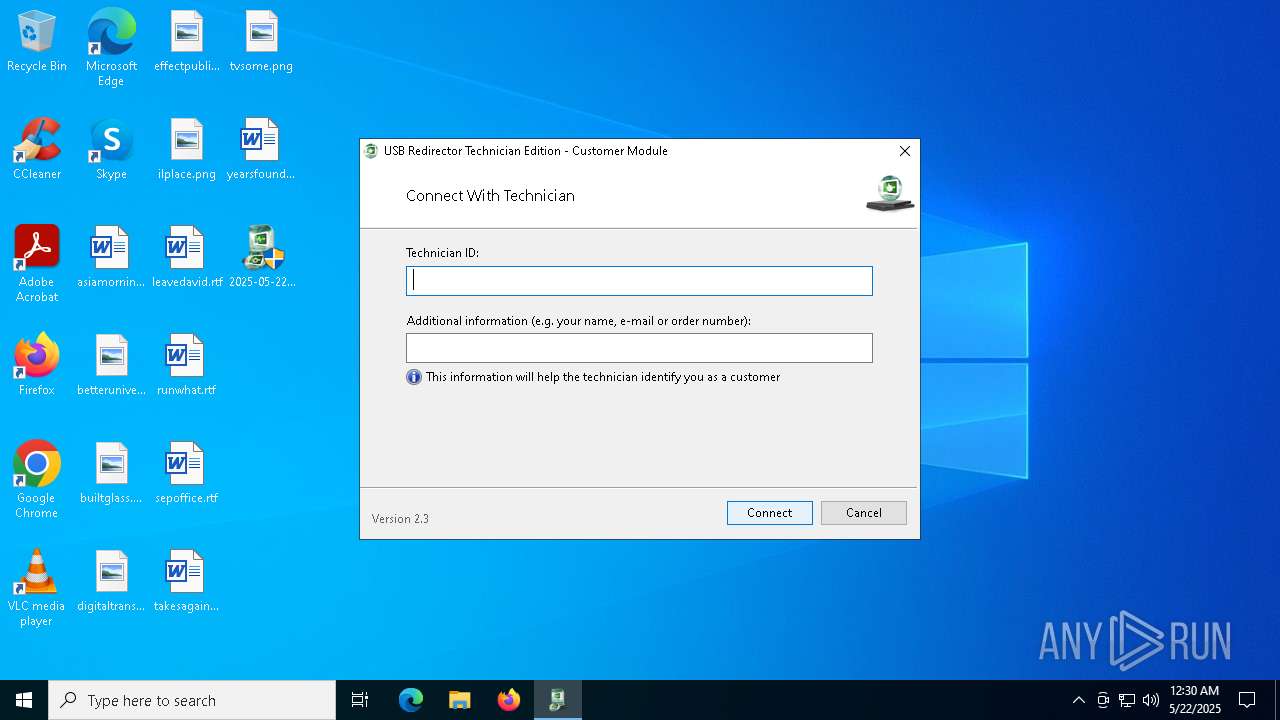
Drops a system driver (possible attempt to evade defenses)
- 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe (PID: 7564)
- usb-redirector-customer-module-gui.exe (PID: 7596)
- drvinst.exe (PID: 7720)
Process drops legitimate windows executable
- 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe (PID: 7564)
Executable content was dropped or overwritten
- 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe (PID: 7564)
- usb-redirector-customer-module-gui.exe (PID: 7596)
- drvinst.exe (PID: 7720)
Reads security settings of Internet Explorer
- 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe (PID: 7564)
Creates files in the driver directory
- drvinst.exe (PID: 7720)
Executes as Windows Service
- usbredirectortechcsrv.exe (PID: 7772)
Contacting a server suspected of hosting an CnC
- 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe (PID: 7564)
Connects to unusual port
- usbredirectortechcsrv.exe (PID: 7772)
INFO
Checks supported languages
- 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe (PID: 7564)
- usb-redirector-customer-module-gui.exe (PID: 7596)
- drvinst.exe (PID: 7720)
- usbredirectortechcsrv.exe (PID: 7772)
Creates files in the program directory
- 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe (PID: 7564)
The sample compiled with english language support
- 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe (PID: 7564)
- usb-redirector-customer-module-gui.exe (PID: 7596)
- drvinst.exe (PID: 7720)
Reads the computer name
- 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe (PID: 7564)
- usb-redirector-customer-module-gui.exe (PID: 7596)
- drvinst.exe (PID: 7720)
- usbredirectortechcsrv.exe (PID: 7772)
Create files in a temporary directory
- 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe (PID: 7564)
- usb-redirector-customer-module-gui.exe (PID: 7596)
Checks proxy server information
- 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe (PID: 7564)
- slui.exe (PID: 8036)
Reads the machine GUID from the registry
- drvinst.exe (PID: 7720)
Reads the software policy settings
- drvinst.exe (PID: 7720)
- slui.exe (PID: 8036)
Creates files or folders in the user directory
- 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe (PID: 7564)
UPX packer has been detected
- 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe (PID: 7564)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:07:06 14:10:30+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 98816 |
| InitializedDataSize: | 192512 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xf97b |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.3.0.3330 |
| ProductVersionNumber: | 2.3.0.3330 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Private build, Special build |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | USB Redirector Technician Edition Customer Module |
| CompanyName: | SimplyCore LLC |
| FileDescription: | USB Redirector Technician Edition Customer Module |
| FileVersion: | 2,3,0,3330 |
| InternalName: | usbredirector-customer-module.exe |
| LegalCopyright: | Copyright (c) 2007 - 2022 SimplyCore LLC. All rights reserved. |
| LegalTrademarks: | Copyright (c) 2007 - 2022 SimplyCore LLC. All rights reserved. |
| OriginalFileName: | usbredirector-customer-module.exe |
| PrivateBuild: | 2,3,0,3330 |
| ProductName: | USB Redirector Technician Edition Customer Module |
| ProductVersion: | 2,3,0,3330 |
| SpecialBuild: | 2,3,0,3330 |
Total processes
128
Monitored processes
6
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7468 | "C:\Users\admin\Desktop\2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe" | C:\Users\admin\Desktop\2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | — | explorer.exe | |||||||||||
User: admin Company: SimplyCore LLC Integrity Level: MEDIUM Description: USB Redirector Technician Edition Customer Module Exit code: 3221226540 Version: 2,3,0,3330 Modules
| |||||||||||||||
| 7564 | "C:\Users\admin\Desktop\2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe" | C:\Users\admin\Desktop\2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | explorer.exe | ||||||||||||
User: admin Company: SimplyCore LLC Integrity Level: HIGH Description: USB Redirector Technician Edition Customer Module Version: 2,3,0,3330 Modules
| |||||||||||||||
| 7596 | "C:\Users\admin\AppData\Local\Temp\c43fec151911db41276f5161738d627b\usb-redirector-customer-module-gui.exe" | C:\Users\admin\AppData\Local\Temp\c43fec151911db41276f5161738d627b\usb-redirector-customer-module-gui.exe | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | ||||||||||||
User: admin Company: SimplyCore LLC Integrity Level: HIGH Description: USB Redirector Technician Edition Customer Module Setup Wizard Version: 2,3,0,3330 Modules
| |||||||||||||||
| 7720 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{bf66a835-939c-2c4b-8be0-1ad6d28a519a}\ttechusbd.inf" "9" "47f7e4ccf" "0000000000000174" "WinSta0\Default" "00000000000001D4" "208" "C:\Users\admin\AppData\Local\Temp\c43fec151911db41276f5161738d627b" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7772 | C:\Users\admin\AppData\Local\Temp\c43fec151911db41276f5161738d627b\usbredirectortechcsrv.exe | C:\Users\admin\AppData\Local\Temp\c43fec151911db41276f5161738d627b\usbredirectortechcsrv.exe | services.exe | ||||||||||||
User: SYSTEM Company: SimplyCore LLC Integrity Level: SYSTEM Description: USB Redirector Technician Edition Customer Module service Version: 2,3,0,3330 Modules
| |||||||||||||||
| 8036 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 382
Read events
7 378
Write events
4
Delete events
0
Modification events
| (PID) Process: | (7596) usb-redirector-customer-module-gui.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\SetupapiLogStatus |
| Operation: | write | Name: | setupapi.dev.log |
Value: 4096 | |||
| (PID) Process: | (7564) 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7564) 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7564) 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
16
Suspicious files
12
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | C:\Users\admin\AppData\Local\Temp\__try__temporary__file__1097593 | binary | |
MD5:B4DB5AA9D9FA3D55EF0B17EE92F7D7A9 | SHA256:302F538E67F23AF1FD81144C8F087D506890B5FE1F7735D84AD6E0346353A9EB | |||
| 7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | C:\Users\admin\AppData\Local\Temp\c43fec151911db41276f5161738d627b\ttechusbd.cat | binary | |
MD5:E6756A675A4D1367EF9463736E948FEF | SHA256:586C551BBF12221C693DB578F959BF6C3A4816B645C86EDF089CCB83EC15E2B0 | |||
| 7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | C:\Users\admin\AppData\Local\Temp\c43fec151911db41276f5161738d627b\usb-redirector-customer-module-gui.exe | executable | |
MD5:31901C8409E9F2271D278EE04465E5BF | SHA256:55D9A1E4003A7BDAC5A879375EECEA470D26C0454CE08AAE3065AED4B73B1C80 | |||
| 7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | C:\Users\admin\AppData\Local\Temp\c43fec151911db41276f5161738d627b\ttechusbd.inf | binary | |
MD5:3E0BF576033C3D90CE0EE543940DEA64 | SHA256:852BCA64B94A158D23FFCFA1CD5EA2FE87F5ED51FD3EBC39021430A0058DEDFA | |||
| 7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | C:\Users\admin\AppData\Local\Temp\c43fec151911db41276f5161738d627b\amd64\ttechusbd.sys | executable | |
MD5:3CF990F46D8772F4E731CEB526AADC48 | SHA256:ED34E9AD250A49E1B93164784EAD56A284A89ABAF1CDDF3213D61C02A73A3469 | |||
| 7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | C:\Users\admin\AppData\Local\Temp\c43fec151911db41276f5161738d627b\amd64\ttechpnptls.sys | executable | |
MD5:7BF22BCBA2C05A9BBD1E29470B37A151 | SHA256:63ACB06D0CE41B01724644388720DD28C2B671F24E25D36B6EB783E6237FB6D0 | |||
| 7596 | usb-redirector-customer-module-gui.exe | C:\Users\admin\AppData\Local\Temp\{bf66a835-939c-2c4b-8be0-1ad6d28a519a}\SETCA48.tmp | binary | |
MD5:3E0BF576033C3D90CE0EE543940DEA64 | SHA256:852BCA64B94A158D23FFCFA1CD5EA2FE87F5ED51FD3EBC39021430A0058DEDFA | |||
| 7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | C:\Users\admin\AppData\Local\Temp\c43fec151911db41276f5161738d627b\openssl-license.txt | text | |
MD5:D343E62FC9C833710BBBED25F27364C8 | SHA256:C32913B33252E71190AF2066F08115C69BC9FDDADF3BF29296E20C835389841C | |||
| 7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | C:\Users\admin\AppData\Local\Temp\c43fec151911db41276f5161738d627b\libssl-1_1-x64.dll | executable | |
MD5:601282ECB3914720C2E299BEB7C6F5D2 | SHA256:38F5FDCF3EC06F7AEE140D20D57271337E2EB1A97816CECF6AE5222FC4FD7960 | |||
| 7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | C:\Users\admin\AppData\Local\Temp\c43fec151911db41276f5161738d627b\libcrypto-1_1-x64.dll | executable | |
MD5:D4BF5E133CD530F86934AB0A54BE6BFC | SHA256:5AD98C8E5E913566055C6DDF2DDABC14FF7F61488CE179AA9DC01C940EB20196 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
30
DNS requests
10
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | GET | 200 | 13.248.169.48:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | GET | 200 | 13.248.169.48:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | GET | 200 | 13.248.169.48:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | GET | 200 | 13.248.169.48:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | GET | 200 | 13.248.169.48:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | GET | 200 | 13.248.169.48:80 | http://www.aieov.com/so.gif | unknown | — | — | malicious |
7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | GET | 200 | 13.248.169.48:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | 13.248.169.48:80 | www.aieov.com | AMAZON-02 | US | malicious |
7772 | usbredirectortechcsrv.exe | 185.161.211.222:47912 | cloud.incentivespro.com | Zemlyaniy Dmitro Leonidovich | NL | unknown |
5072 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
8036 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
5isohu.com |
| whitelisted |
www.aieov.com |
| malicious |
cloud.incentivespro.com |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | Malware Command and Control Activity Detected | MALWARE [ANY.RUN] Possible Floxif CnC Communication |
7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | Malware Command and Control Activity Detected | MALWARE [ANY.RUN] Possible Floxif CnC Communication |
7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | Malware Command and Control Activity Detected | MALWARE [ANY.RUN] Possible Floxif CnC Communication |
7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | Malware Command and Control Activity Detected | MALWARE [ANY.RUN] Possible Floxif CnC Communication |
7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | Malware Command and Control Activity Detected | MALWARE [ANY.RUN] Possible Floxif CnC Communication |
7564 | 2025-05-22_17cf50251c8b8beca41a42e18c57c168_elex_floxif_hijackloader_rhadamanthys_stop_tofsee.exe | Malware Command and Control Activity Detected | MALWARE [ANY.RUN] Possible Floxif CnC Communication |