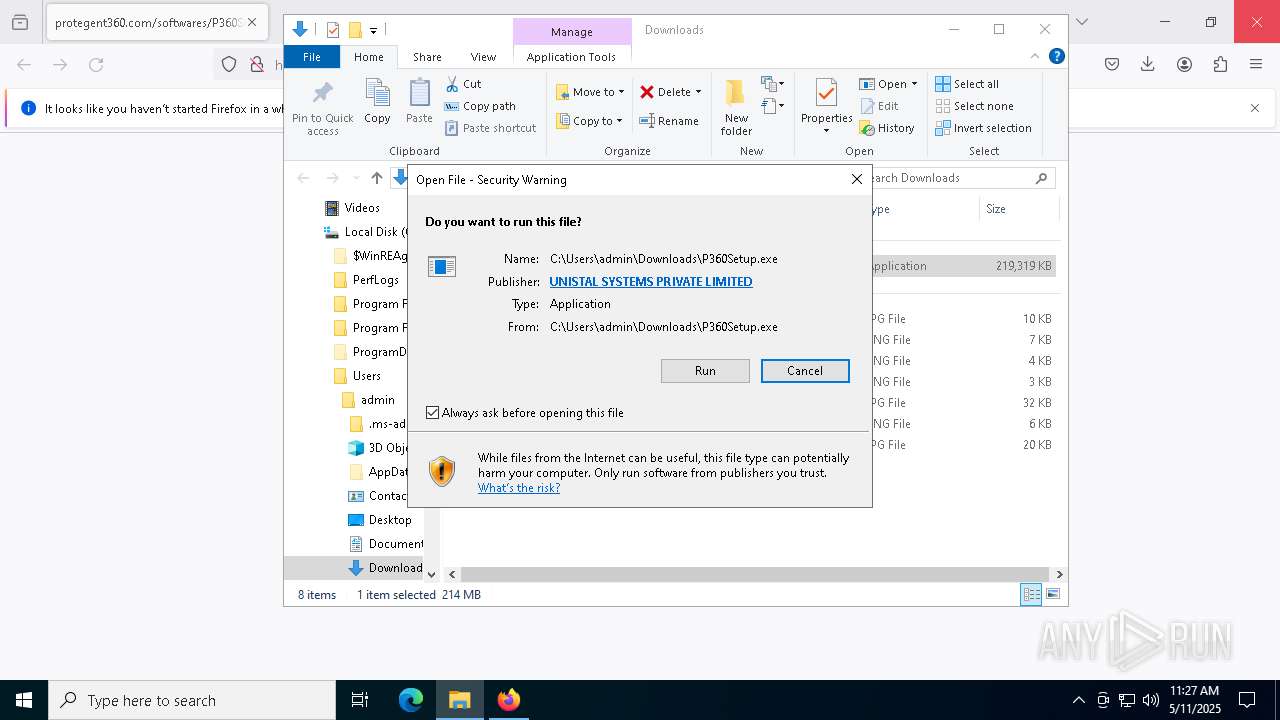
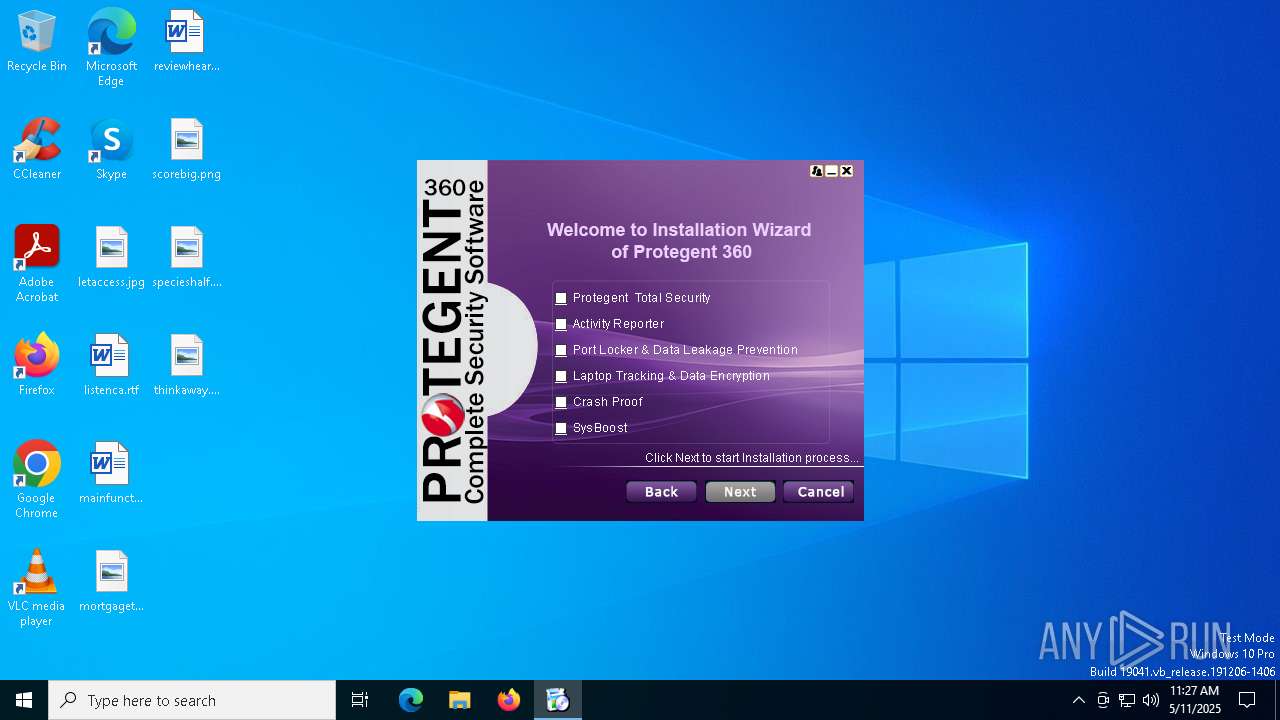
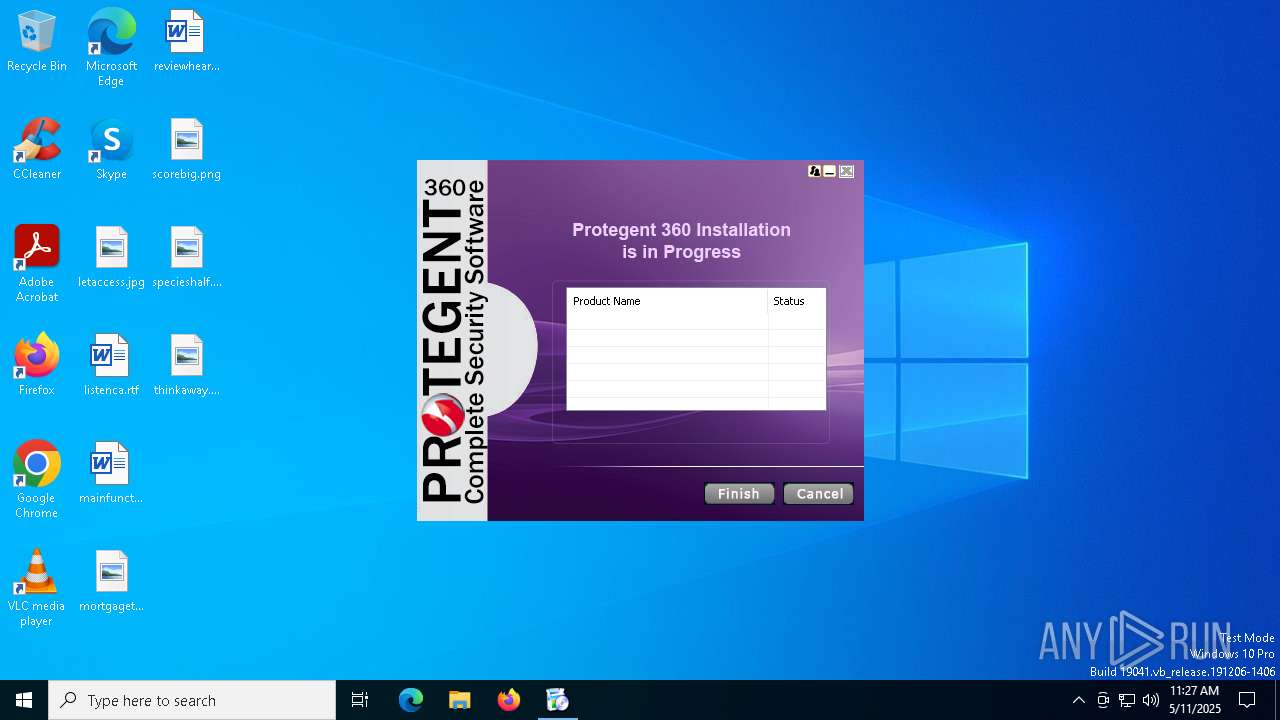
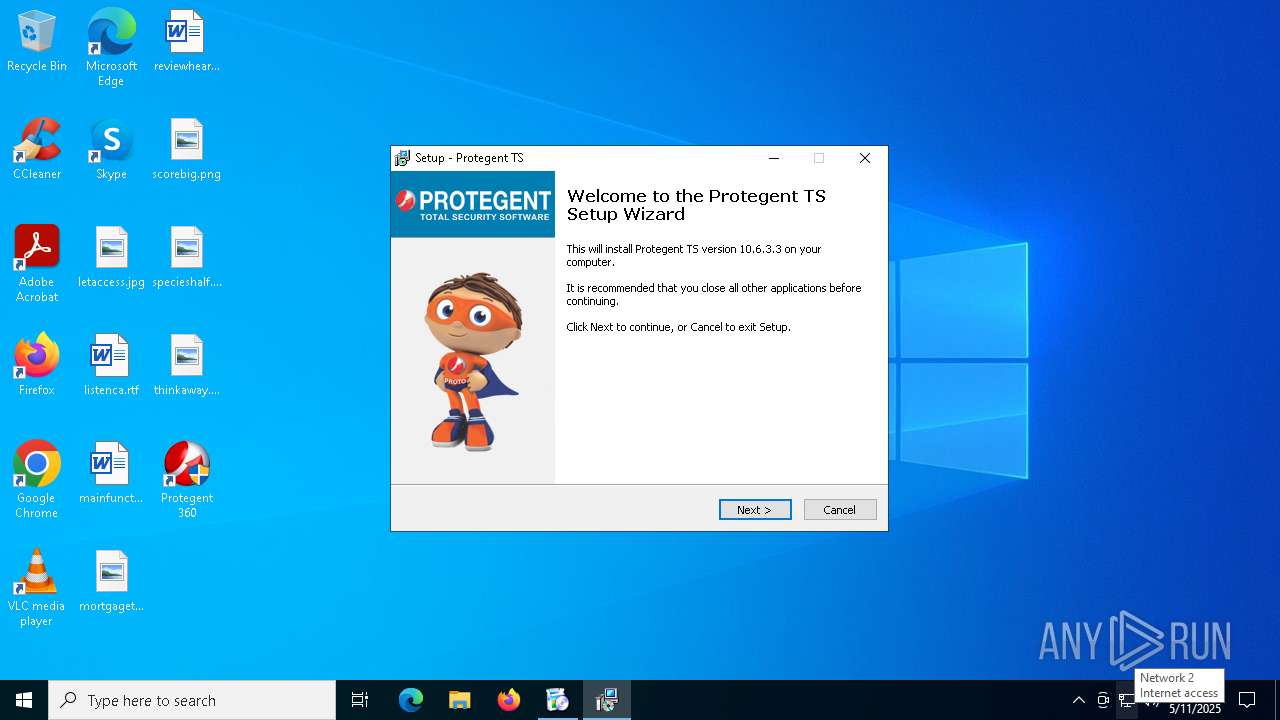
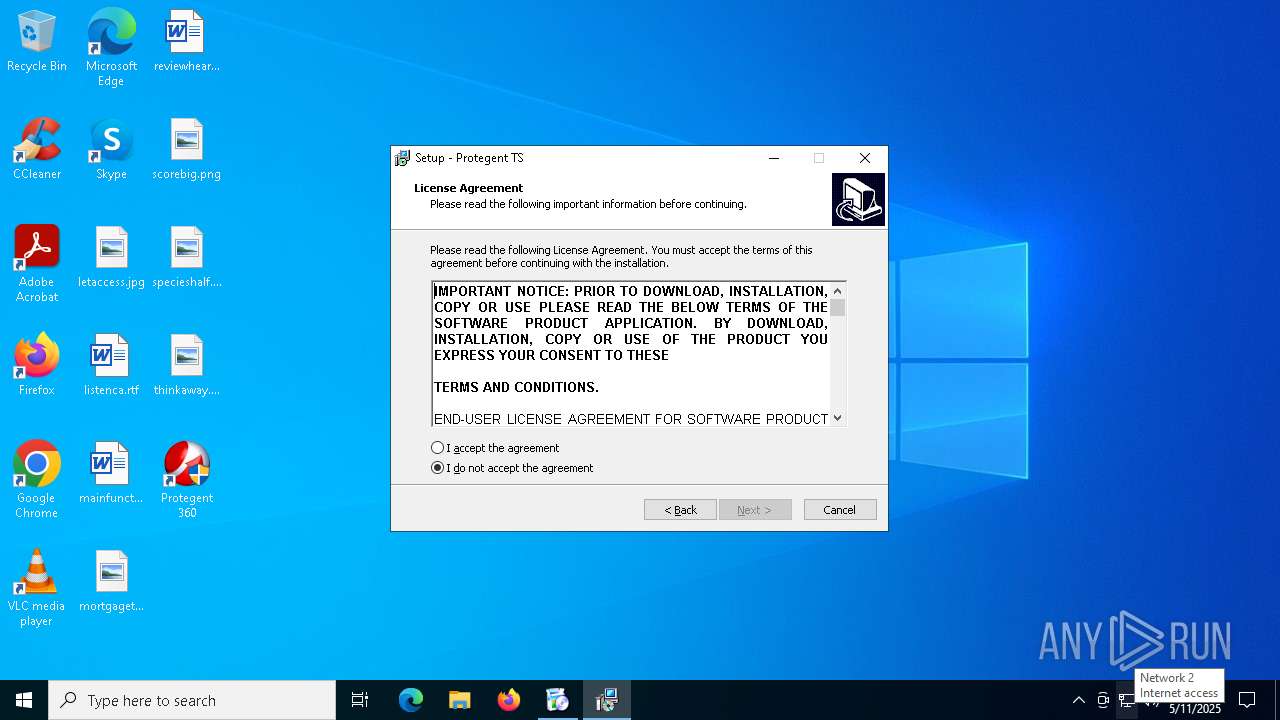
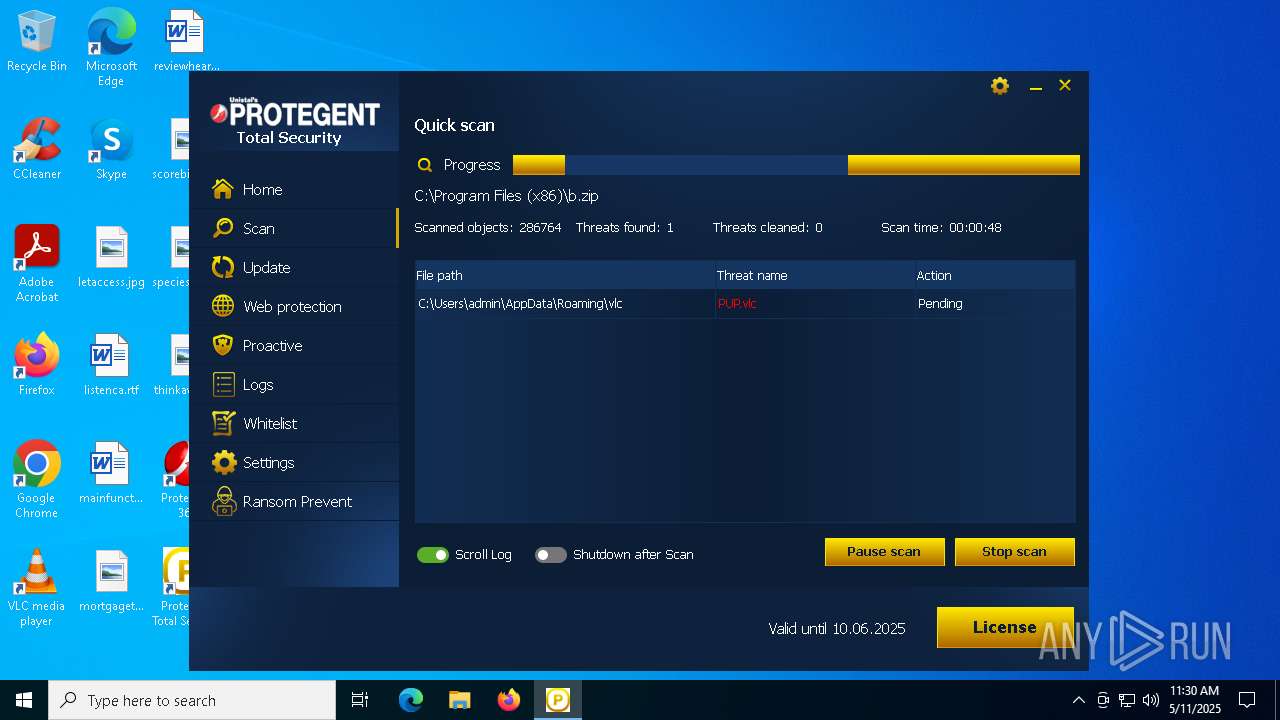
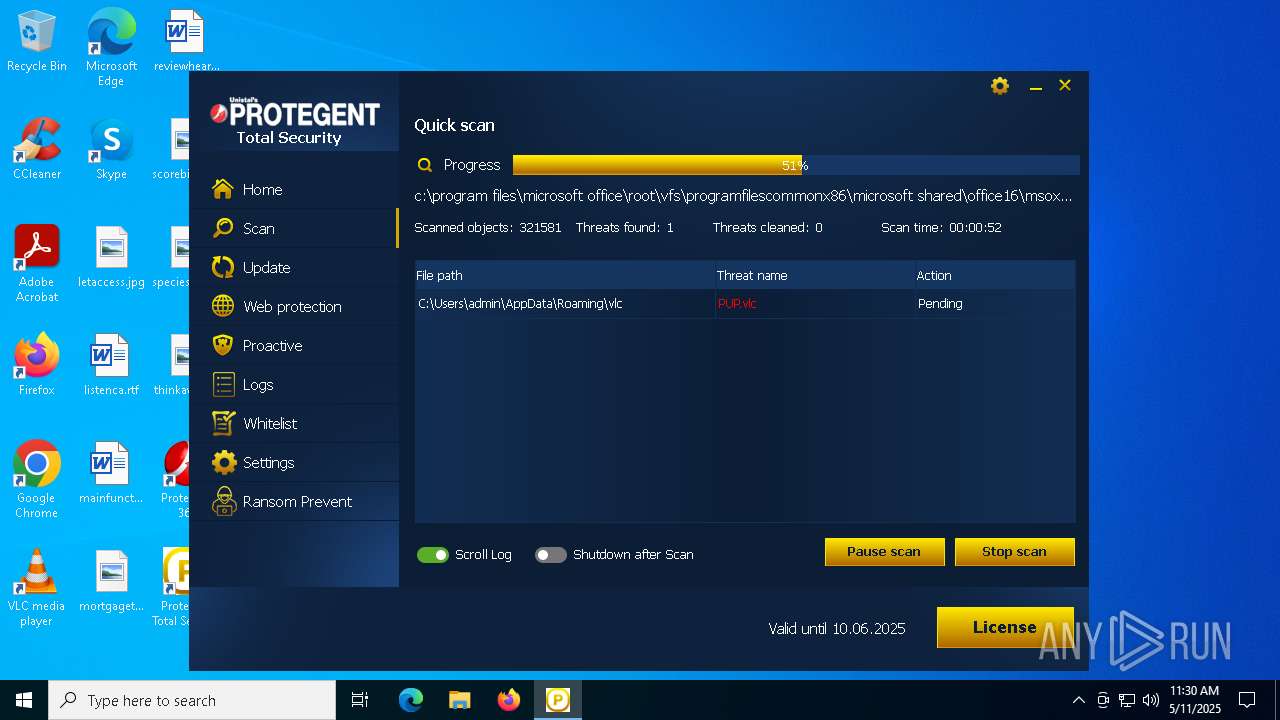
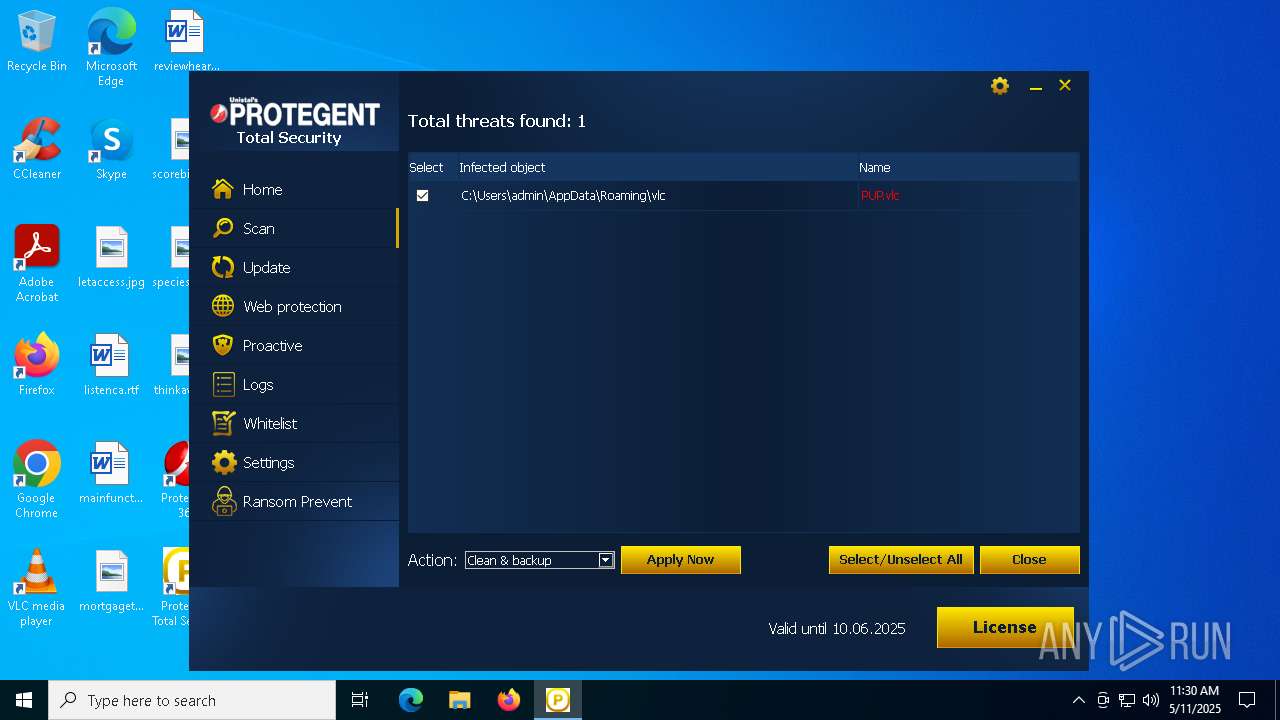
| URL: | https://www.protegent360.com/softwares/P360Setup.exe?_gl=1*1agsl5f*_ga*NTI2NjcyODM2LjE2NzM0OTY3NjY.*_ga_46KWQ06K7F*MTY4MzUzMDE1Ny4xNy4xLjE2ODM1MzAzNDEuMC4wLjA.&_ga=2.118266313.1392168505.1683518672-526672836.1673496766 |
| Full analysis: | https://app.any.run/tasks/46a63edd-72fc-414e-a05d-d006bca2a030 |
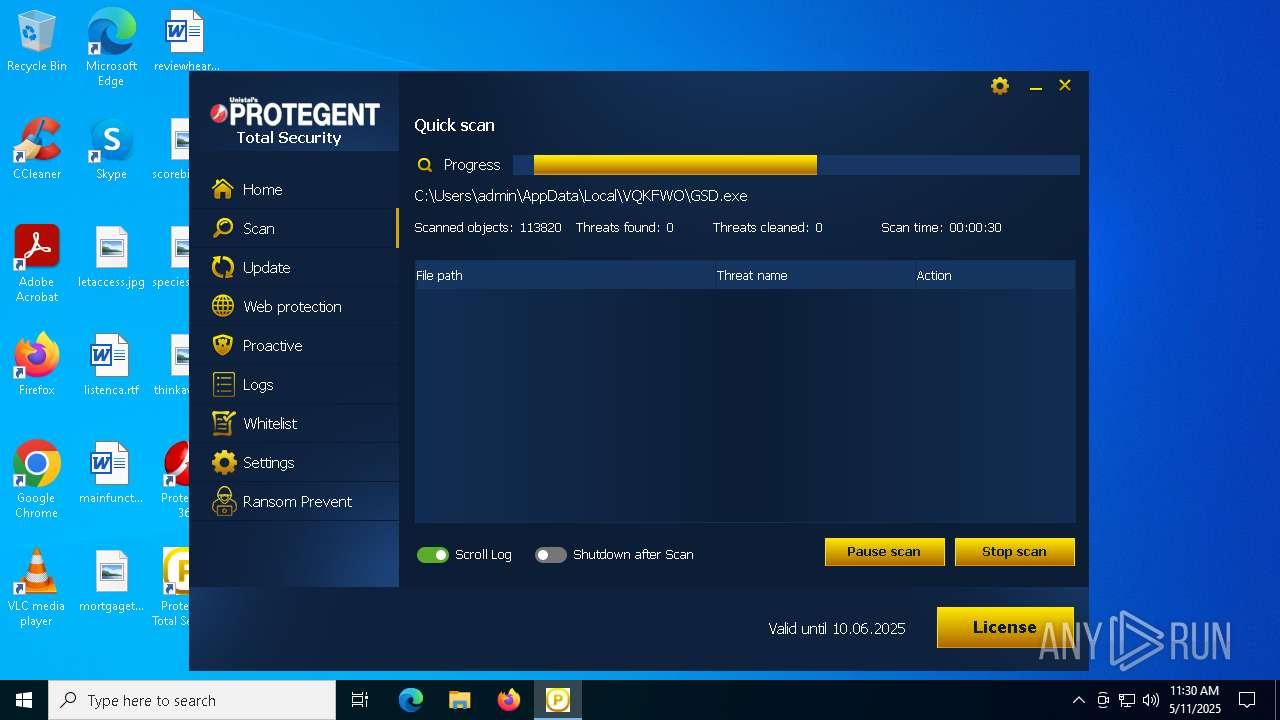
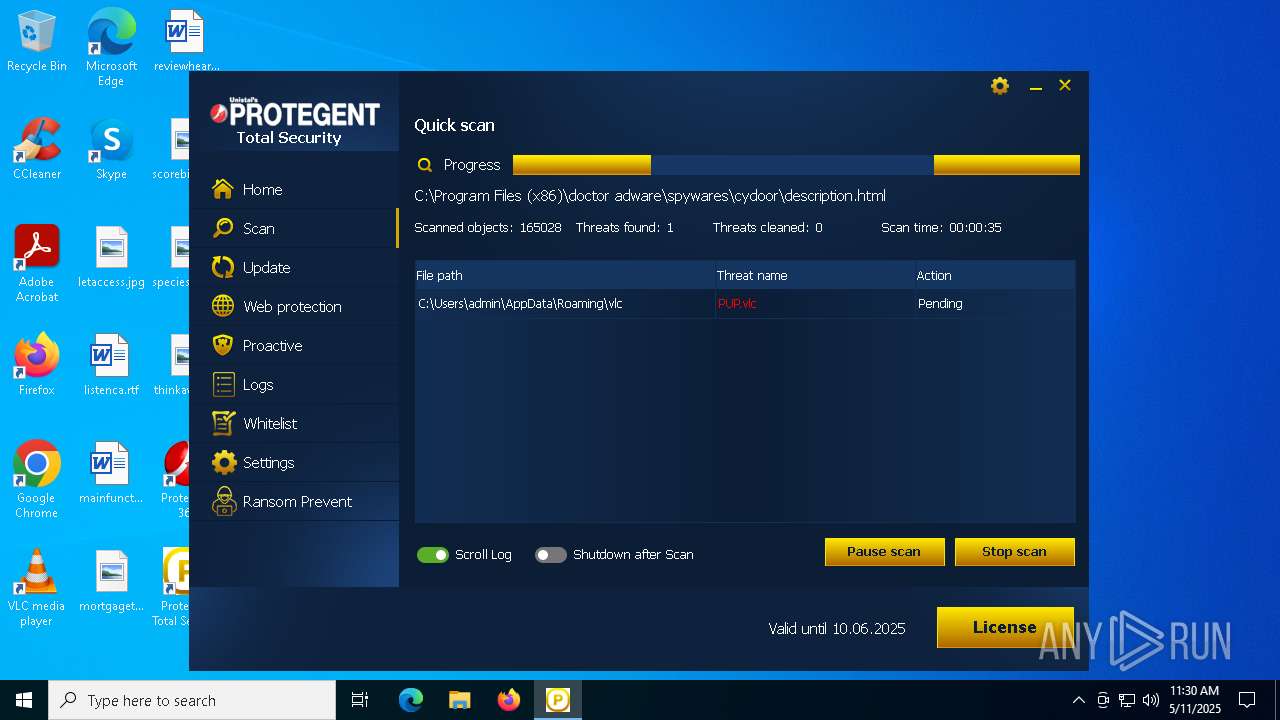
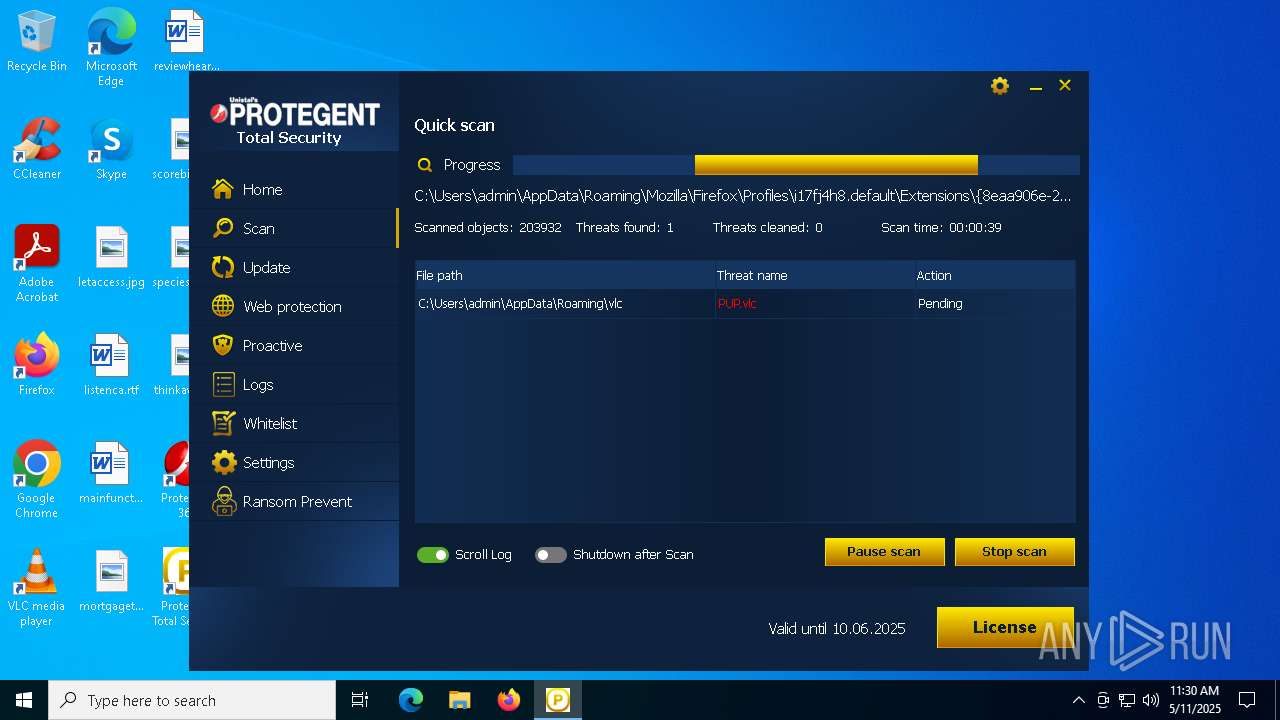
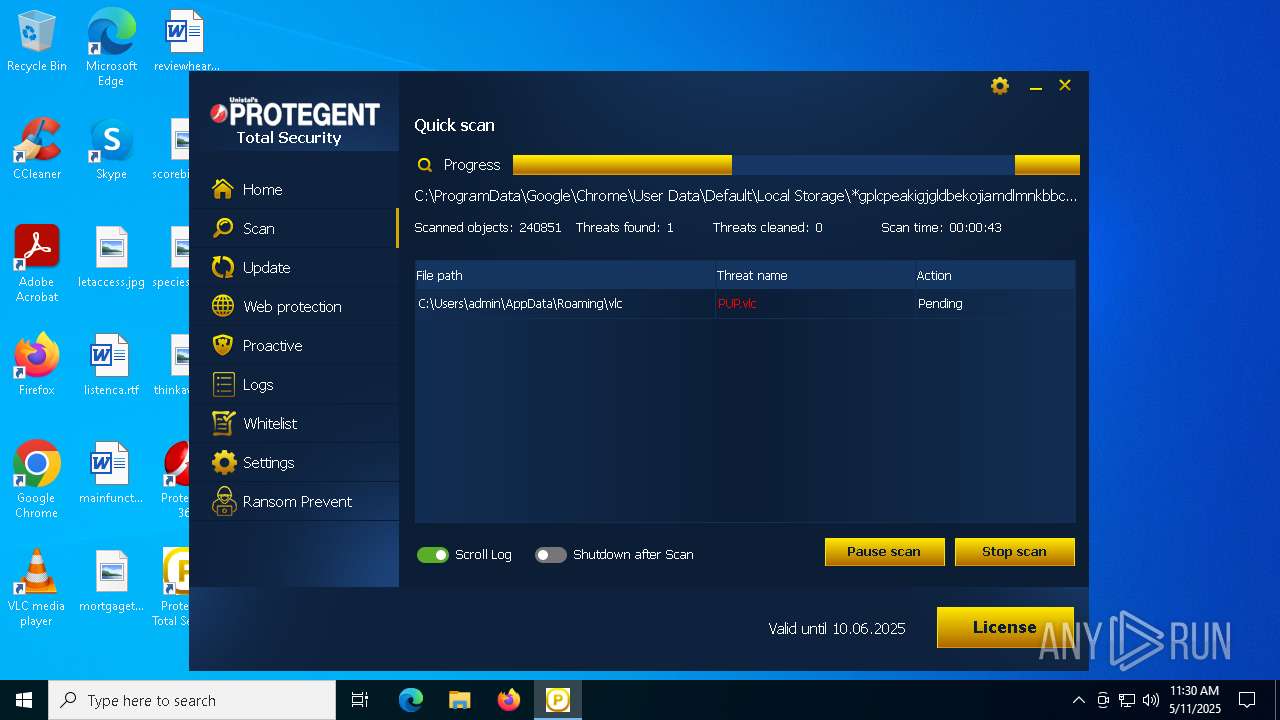
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | May 11, 2025, 11:25:47 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 7CC652697CE776402EC64523D6297E57 |
| SHA1: | E4998C004213AF6F7769EE51EF1668169B2CB5CE |
| SHA256: | 3FE6105E428997CED9F05ED057896FB82B6A850AD23659015A2FFC6D1B0B74D7 |
| SSDEEP: | 6:2OLBCeWZLGGWJ1UcQ/YTr/TS0rHssqjnt74B/U6D8U7XGiTU0rWlRVT:2dMGWu0AsinhkgU7XmWWLVT |
MALICIOUS
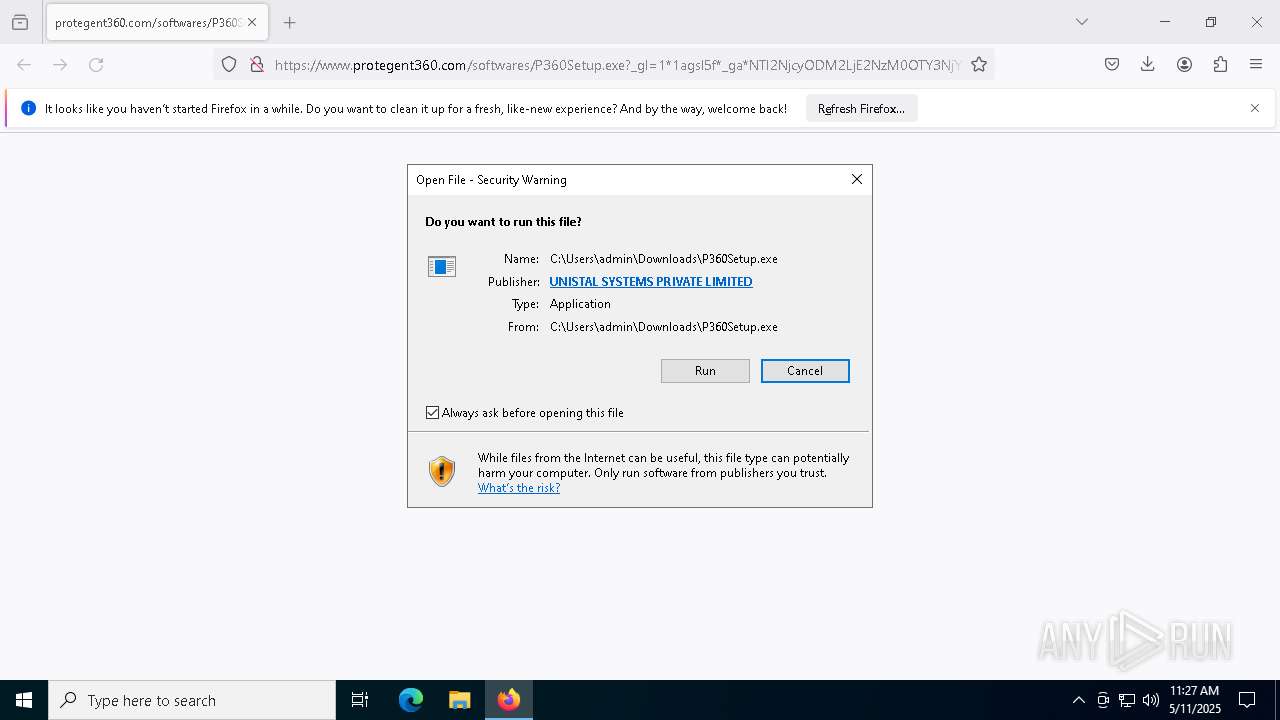
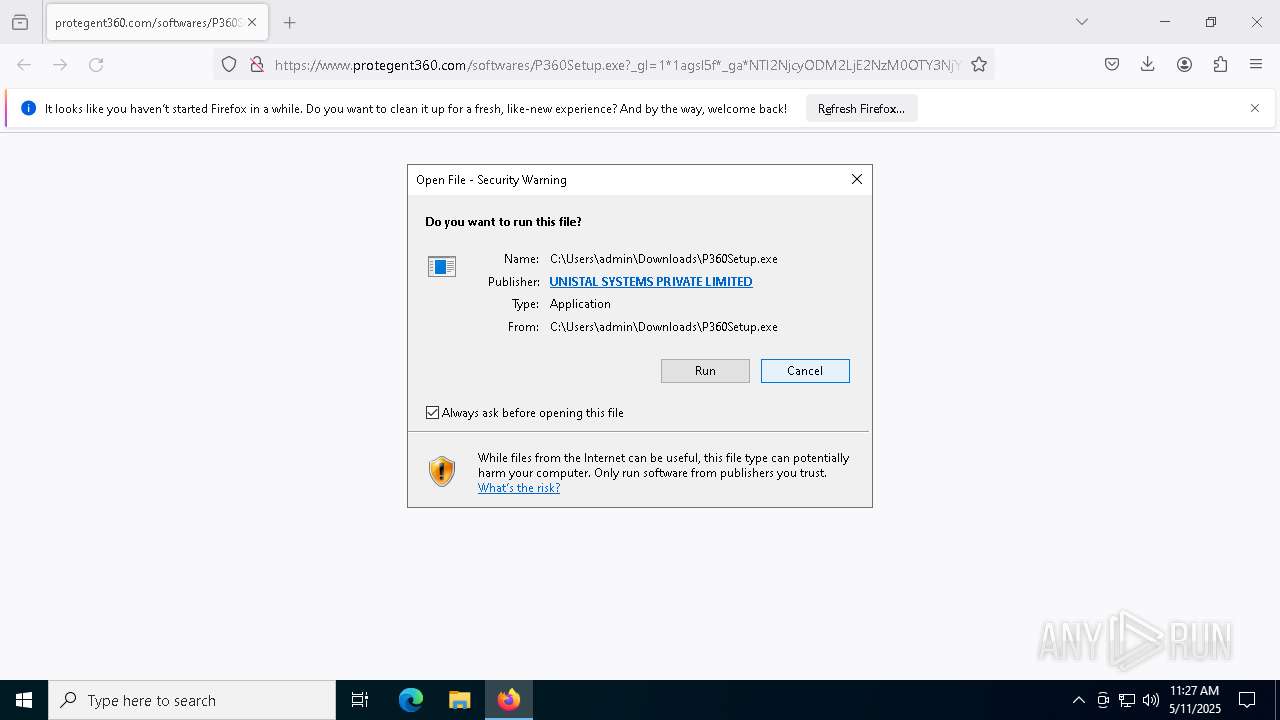
Executing a file with an untrusted certificate
- Setup.exe (PID: 6620)
- Setup.exe (PID: 6660)
- msrp.exe (PID: 7584)
- Proserv.exe (PID: 4736)
- AReporter.exe (PID: 2516)
- USPL-PL-S65.exe (PID: 1132)
- Proserv.exe (PID: 5600)
- LLaptop.exe (PID: 2692)
- USPL-LL-S65.exe (PID: 7688)
- LLActivate.exe (PID: 7368)
- LLaptop.exe (PID: 4152)
- LLaptop.exe (PID: 1348)
- USPL-SBE-S65.exe (PID: 6192)
- Proserv.exe (PID: 3240)
- Proserv.exe (PID: 6136)
- Protegent360.exe (PID: 5260)
- LLActivate.exe (PID: 8084)
- Protegent360.exe (PID: 7876)
- LLStartUp.exe (PID: 7544)
- LLStartUp.exe (PID: 1040)
Changes the autorun value in the registry
- Setup.exe (PID: 6660)
Starts NET.EXE for service management
- ProtegentTS.tmp (PID: 780)
- net.exe (PID: 7620)
Registers / Runs the DLL via REGSVR32.EXE
- ProtegentTS.tmp (PID: 780)
- Setup.exe (PID: 6660)
MASSLOGGER has been detected (YARA)
- pgxsrv.exe (PID: 6072)
XORed URL has been found (YARA)
- pgxsrv.exe (PID: 6072)
ICEDID has been detected (YARA)
- pgxsrv.exe (PID: 6072)
DCRAT has been detected (YARA)
- pgxsrv.exe (PID: 6072)
GROWTOPIA has been detected (YARA)
- pgxsrv.exe (PID: 6072)
SUSPICIOUS
Reads Microsoft Outlook installation path
- P360Setup.exe (PID: 1300)
Reads security settings of Internet Explorer
- P360Setup.exe (PID: 1300)
Executable content was dropped or overwritten
- P360Setup.exe (PID: 1300)
- USPL-P360-S65.exe (PID: 6488)
- ProtegentTS.exe (PID: 924)
- USPL-P360-S65.tmp (PID: 4488)
- ProtegentTS.tmp (PID: 780)
- msrp.exe (PID: 7584)
- USPL-AR-S65.exe (PID: 7376)
- USPL-AR-S65.tmp (PID: 7408)
- USPL-LL-S65.exe (PID: 7688)
- USPL-PL-S65.exe (PID: 1132)
- USPL-PL-S65.tmp (PID: 2136)
- USPL-LL-S65.tmp (PID: 7192)
- LLaptop.exe (PID: 1348)
- USPL-SBE-S65.exe (PID: 6192)
- Setup.exe (PID: 2984)
- USPL-SBE-S65.tmp (PID: 6488)
- Protegent360.exe (PID: 7876)
Process drops legitimate windows executable
- P360Setup.exe (PID: 1300)
- USPL-P360-S65.tmp (PID: 4488)
- USPL-AR-S65.tmp (PID: 7408)
- USPL-PL-S65.tmp (PID: 2136)
- USPL-LL-S65.tmp (PID: 7192)
- USPL-SBE-S65.tmp (PID: 6488)
- LLaptop.exe (PID: 1348)
- Setup.exe (PID: 2984)
Reads Internet Explorer settings
- P360Setup.exe (PID: 1300)
Creates file in the systems drive root
- P360Setup.exe (PID: 1300)
- ProtegentTS.tmp (PID: 780)
- pgxsrv.exe (PID: 6072)
- pgxsrv.exe (PID: 7912)
Reads the Windows owner or organization settings
- USPL-P360-S65.tmp (PID: 4488)
- ProtegentTS.tmp (PID: 780)
Executes as Windows Service
- pgxsrv.exe (PID: 6072)
- LLaptop.exe (PID: 1348)
- Proserv.exe (PID: 6136)
Drops a system driver (possible attempt to evade defenses)
- ProtegentTS.tmp (PID: 780)
- msrp.exe (PID: 7584)
Creates files in the driver directory
- ProtegentTS.tmp (PID: 780)
Application launched itself
- pgxsrv.exe (PID: 6072)
There is functionality for communication dyndns network (YARA)
- pgxsrv.exe (PID: 6072)
Process drops SQLite DLL files
- USPL-AR-S65.tmp (PID: 7408)
The process drops C-runtime libraries
- USPL-AR-S65.tmp (PID: 7408)
- USPL-LL-S65.tmp (PID: 7192)
- LLaptop.exe (PID: 1348)
Possible usage of Discord/Telegram API has been detected (YARA)
- pgxsrv.exe (PID: 6072)
There is functionality for taking screenshot (YARA)
- pgisgui.exe (PID: 5556)
- LLaptop.exe (PID: 1348)
- Proserv.exe (PID: 6136)
INFO
Application launched itself
- firefox.exe (PID: 5008)
- firefox.exe (PID: 4448)
Executable content was dropped or overwritten
- firefox.exe (PID: 4448)
Reads the software policy settings
- slui.exe (PID: 6112)
- slui.exe (PID: 1568)
Manual execution by a user
- P360Setup.exe (PID: 1300)
- Protegent360.exe (PID: 5260)
- Protegent360.exe (PID: 7876)
- pgisgui.exe (PID: 7508)
Checks proxy server information
- P360Setup.exe (PID: 1300)
- slui.exe (PID: 1568)
Checks supported languages
- P360Setup.exe (PID: 1300)
- USPL-P360-S65.tmp (PID: 4488)
- Setup.exe (PID: 6660)
- USPL-P360-S65.exe (PID: 6488)
- ProtegentTS.exe (PID: 924)
- ProtegentTS.tmp (PID: 780)
- pgxsrv.exe (PID: 7912)
- pgxsrv.exe (PID: 6072)
Reads the computer name
- P360Setup.exe (PID: 1300)
- Setup.exe (PID: 6660)
- USPL-P360-S65.tmp (PID: 4488)
- ProtegentTS.tmp (PID: 780)
- pgxsrv.exe (PID: 6072)
- pgxsrv.exe (PID: 7912)
Create files in a temporary directory
- USPL-P360-S65.exe (PID: 6488)
- ProtegentTS.exe (PID: 924)
- USPL-P360-S65.tmp (PID: 4488)
- ProtegentTS.tmp (PID: 780)
The sample compiled with english language support
- P360Setup.exe (PID: 1300)
- USPL-P360-S65.tmp (PID: 4488)
- ProtegentTS.tmp (PID: 780)
- USPL-AR-S65.tmp (PID: 7408)
- USPL-PL-S65.tmp (PID: 2136)
- USPL-LL-S65.tmp (PID: 7192)
- USPL-SBE-S65.tmp (PID: 6488)
- Setup.exe (PID: 2984)
- LLaptop.exe (PID: 1348)
- Protegent360.exe (PID: 7876)
The sample compiled with chinese language support
- P360Setup.exe (PID: 1300)
- USPL-P360-S65.tmp (PID: 4488)
- USPL-PL-S65.tmp (PID: 2136)
- USPL-LL-S65.tmp (PID: 7192)
- LLaptop.exe (PID: 1348)
- USPL-SBE-S65.tmp (PID: 6488)
- Setup.exe (PID: 2984)
Process checks computer location settings
- P360Setup.exe (PID: 1300)
Creates files or folders in the user directory
- USPL-P360-S65.tmp (PID: 4488)
Creates files in the program directory
- USPL-P360-S65.tmp (PID: 4488)
- ProtegentTS.tmp (PID: 780)
- pgxsrv.exe (PID: 7912)
- pgxsrv.exe (PID: 6072)
Creates a software uninstall entry
- USPL-P360-S65.tmp (PID: 4488)
- ProtegentTS.tmp (PID: 780)
Detects InnoSetup installer (YARA)
- ProtegentTS.exe (PID: 924)
- ProtegentTS.tmp (PID: 780)
Compiled with Borland Delphi (YARA)
- ProtegentTS.exe (PID: 924)
- ProtegentTS.tmp (PID: 780)
The sample compiled with russian language support
- ProtegentTS.tmp (PID: 780)
Reads the machine GUID from the registry
- ProtegentTS.tmp (PID: 780)
TSULoader has been detected
- pgxsrv.exe (PID: 6072)
Aspack has been detected
- pgxsrv.exe (PID: 6072)
UPX packer has been detected
- pgxsrv.exe (PID: 6072)
Mpress packer has been detected
- pgxsrv.exe (PID: 6072)
Neolite packer has been detected
- pgxsrv.exe (PID: 6072)
VMProtect protector has been detected
- pgxsrv.exe (PID: 6072)
NsPack has been detected
- pgxsrv.exe (PID: 6072)
Potential remote process memory reading (Base64 Encoded 'ReadProcessMemory')
- pgxsrv.exe (PID: 6072)
Found Base64 encoded access to Marshal class via PowerShell (YARA)
- pgxsrv.exe (PID: 6072)
Themida protector has been detected
- pgxsrv.exe (PID: 6072)
Potential remote process memory interaction (Base64 Encoded 'VirtualAllocEx')
- pgxsrv.exe (PID: 6072)
SQLite executable
- USPL-AR-S65.tmp (PID: 7408)
Found Base64 encoded reflection usage via PowerShell (YARA)
- pgxsrv.exe (PID: 6072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(6072) pgxsrv.exe
Decrypted-URLs (1)http://ghome.mefound.com/j6koq2.txt
Decrypted-URLs (1)http://fewfwe.com/
Decrypted-URLs (2)http://fewfwe.com/
http://ghome.mefound.com/j6koq2.txt
Decrypted-URLs (1)http://172.16.fgg
Decrypted-URLs (1)http://www.58sky.com/index/getcfg?id=
Decrypted-URLs (1)http://www.58sky.com
Decrypted-URLs (1)http://www.ip.cnl
Decrypted-URLs (1)http://pittsburghlive.net/s/?serG
Decrypted-URLs (1)http://www.enigmaprotector.com/
Decrypted-URLs (6)http://172.16.fgg
http://pittsburghlive.net/s/?serG
http://www.58sky.com
http://www.58sky.com/index/getcfg?id=
http://www.enigmaprotector.com/
http://www.ip.cnl
ims-api
(PID) Process(6072) pgxsrv.exe
Discord-Webhook-Tokens (1)616853455805349888/SnD-Y2ReQpDnQqWJWVOQupxayUFrINLJSAU34bCT3lsWuKkzOtf8xMXbiU0plRrb5XYY
Discord-Info-Links
616853455805349888/SnD-Y2ReQpDnQqWJWVOQupxayUFrINLJSAU34bCT3lsWuKkzOtf8xMXbiU0plRrb5XYY
Get Webhook Infohttps://discord.com/api/webhooks/616853455805349888/SnD-Y2ReQpDnQqWJWVOQupxayUFrINLJSAU34bCT3lsWuKkzOtf8xMXbiU0plRrb5XYY
Telegram-Tokens (1)682191468:AAEXDhrDlTGozC8MvnMtAAoGCPymhlkaA4U
Telegram-Info-Links
682191468:AAEXDhrDlTGozC8MvnMtAAoGCPymhlkaA4U
Get info about bothttps://api.telegram.org/bot682191468:AAEXDhrDlTGozC8MvnMtAAoGCPymhlkaA4U/getMe
Get incoming updateshttps://api.telegram.org/bot682191468:AAEXDhrDlTGozC8MvnMtAAoGCPymhlkaA4U/getUpdates
Get webhookhttps://api.telegram.org/bot682191468:AAEXDhrDlTGozC8MvnMtAAoGCPymhlkaA4U/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot682191468:AAEXDhrDlTGozC8MvnMtAAoGCPymhlkaA4U/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot682191468:AAEXDhrDlTGozC8MvnMtAAoGCPymhlkaA4U/deleteWebhook?drop_pending_updates=true
Telegram-Tokens (1)682191468:AAEXDhrDlTGozC8MvnMtAAoGCPymhlkaA4U
Telegram-Info-Links
682191468:AAEXDhrDlTGozC8MvnMtAAoGCPymhlkaA4U
Get info about bothttps://api.telegram.org/bot682191468:AAEXDhrDlTGozC8MvnMtAAoGCPymhlkaA4U/getMe
Get incoming updateshttps://api.telegram.org/bot682191468:AAEXDhrDlTGozC8MvnMtAAoGCPymhlkaA4U/getUpdates
Get webhookhttps://api.telegram.org/bot682191468:AAEXDhrDlTGozC8MvnMtAAoGCPymhlkaA4U/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot682191468:AAEXDhrDlTGozC8MvnMtAAoGCPymhlkaA4U/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot682191468:AAEXDhrDlTGozC8MvnMtAAoGCPymhlkaA4U/deleteWebhook?drop_pending_updates=true
Discord-Webhook-Tokens (1)616853455805349888/SnD-Y2ReQpDnQqWJWVOQupxayUFrINLJSAU34bCT3lsWuKkzOtf8xMXbiU0plRrb5XYY
Discord-Info-Links
616853455805349888/SnD-Y2ReQpDnQqWJWVOQupxayUFrINLJSAU34bCT3lsWuKkzOtf8xMXbiU0plRrb5XYY
Get Webhook Infohttps://discord.com/api/webhooks/616853455805349888/SnD-Y2ReQpDnQqWJWVOQupxayUFrINLJSAU34bCT3lsWuKkzOtf8xMXbiU0plRrb5XYY
Total processes
215
Monitored processes
78
Malicious processes
16
Suspicious processes
13
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 780 | "C:\Users\admin\AppData\Local\Temp\is-37KCD.tmp\ProtegentTS.tmp" /SL5="$4022A,140509665,121344,C:\P360\Unistal\PRO_IS\ProtegentTS.exe" | C:\Users\admin\AppData\Local\Temp\is-37KCD.tmp\ProtegentTS.tmp | ProtegentTS.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 924 | C:\P360\Unistal\PRO_IS\ProtegentTS.exe | C:\P360\Unistal\PRO_IS\ProtegentTS.exe | Setup.exe | ||||||||||||
User: admin Company: Unistal Systems Pvt. Ltd. Integrity Level: HIGH Description: Protegent TS Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 1040 | "C:\Program Files (x86)\Locate Laptop\LLStartUp.exe" RegisterLicense | C:\Program Files (x86)\Locate Laptop\LLStartUp.exe | Setup.exe | ||||||||||||
User: admin Company: Unistal Systems Pvt. Ltd. Integrity Level: HIGH Description: Locate Laptop Application Exit code: 0 Version: 2, 0, 0, 1 Modules
| |||||||||||||||
| 1056 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | C:\P360\Unistal\PRO_PRD\USPL-PL-S65.exe /VERYSILENT /NORESTART | C:\P360\Unistal\PRO_PRD\USPL-PL-S65.exe | Setup.exe | ||||||||||||
User: admin Company: Unistal Systems Pvt. Ltd Integrity Level: HIGH Description: Port Locker & Data Leakage Prevention Setup Exit code: 0 Version: 5.0.01 Modules
| |||||||||||||||
| 1300 | "C:\Users\admin\Downloads\P360Setup.exe" | C:\Users\admin\Downloads\P360Setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1348 | C:\WINDOWS\SysWOW64\pro\LLaptop.exe | C:\Windows\SysWOW64\pro\LLaptop.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Modules
| |||||||||||||||
| 1568 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | "C:\Users\admin\AppData\Local\Temp\is-F4GBN.tmp\USPL-PL-S65.tmp" /SL5="$60354,6674270,152064,C:\P360\Unistal\PRO_PRD\USPL-PL-S65.exe" /VERYSILENT /NORESTART | C:\Users\admin\AppData\Local\Temp\is-F4GBN.tmp\USPL-PL-S65.tmp | USPL-PL-S65.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2140 | "C:\WINDOWS\system32\regsvr32.exe" "C:\Program Files (x86)\Activity Reporter\AROutlook64.dll" -s | C:\Windows\SysWOW64\regsvr32.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 353
Read events
16 702
Write events
413
Delete events
238
Modification events
| (PID) Process: | (4448) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (1300) P360Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1300) P360Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1300) P360Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1300) P360Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (1300) P360Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
| (PID) Process: | (6660) Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\UAAzADYAMAA= |
| Operation: | write | Name: | LLSelect |
Value: 1 | |||
| (PID) Process: | (4488) USPL-P360-S65.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\UAAzADYAMAA= |
| Operation: | write | Name: | FilePath |
Value: C:\Program Files (x86)\Protegent360 | |||
| (PID) Process: | (4488) USPL-P360-S65.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\UAAzADYAMAA= |
| Operation: | write | Name: | DemoInsDate |
Value: | |||
| (PID) Process: | (4488) USPL-P360-S65.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\UAAzADYAMAA= |
| Operation: | write | Name: | DemoInsMonth |
Value: | |||
Executable files
551
Suspicious files
383
Text files
816
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4448 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 4448 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 4448 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4448 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
| 4448 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4448 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 4448 | firefox.exe | C:\Users\admin\Downloads\P360Setup.mVaRgM8L.exe.part | — | |
MD5:— | SHA256:— | |||
| 4448 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 4448 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 4448 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
75
TCP/UDP connections
131
DNS requests
152
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
— | — | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
— | — | POST | 200 | 184.24.77.53:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
— | — | POST | 200 | 184.24.77.53:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
— | — | POST | 200 | 142.250.186.99:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
— | — | POST | 200 | 184.24.77.53:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.190:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.190:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 34.36.137.203:443 | contile.services.mozilla.com | — | — | whitelisted |
— | — | 142.250.184.202:443 | safebrowsing.googleapis.com | — | — | whitelisted |
— | — | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
www.protegent360.com |
| malicious |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |