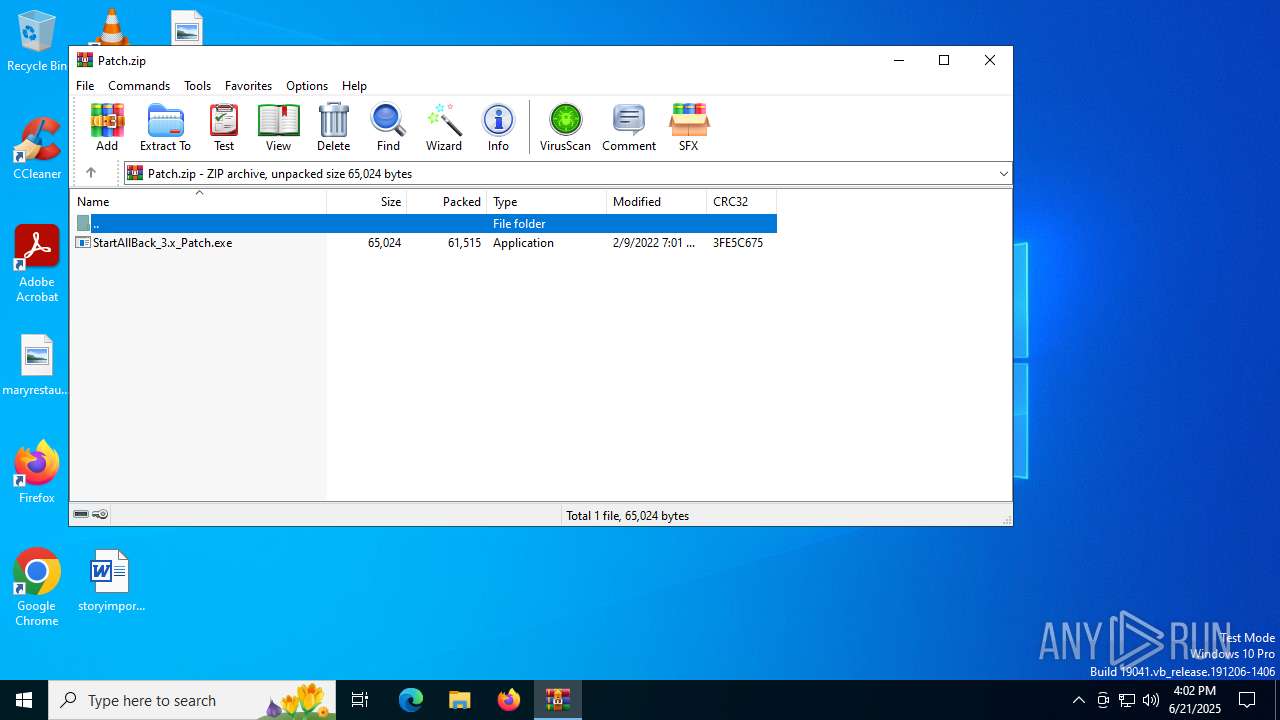
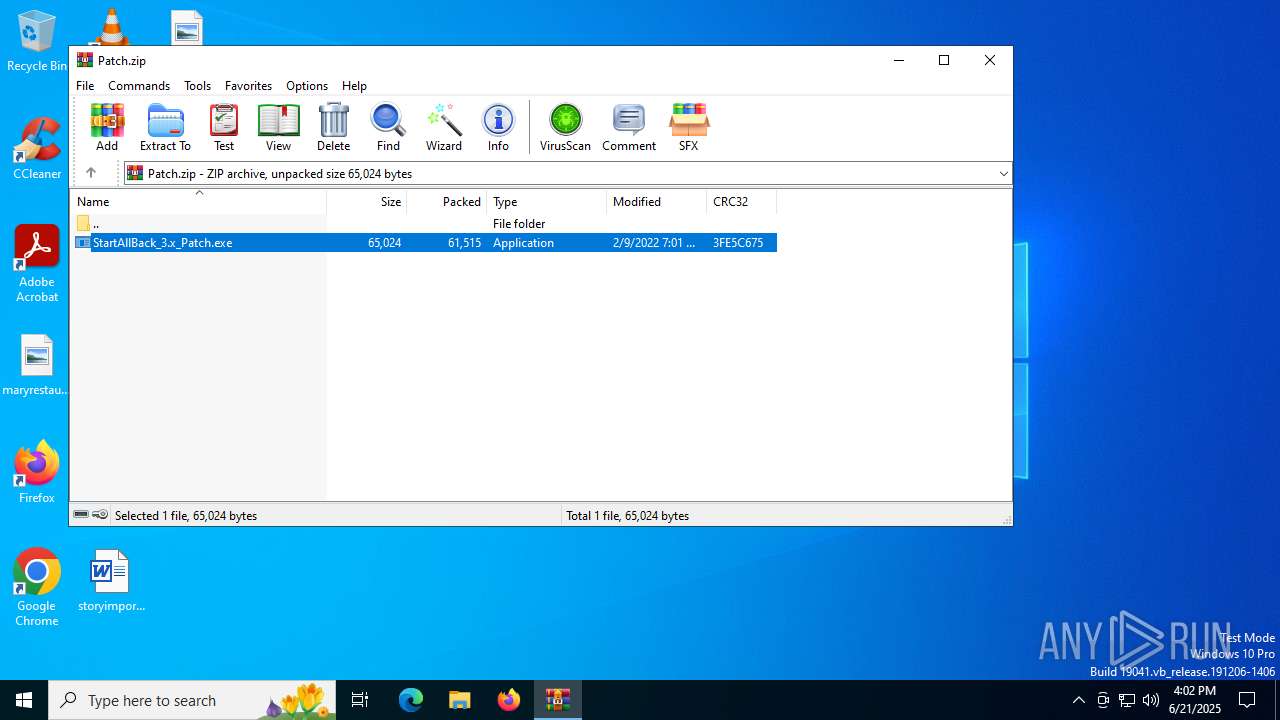
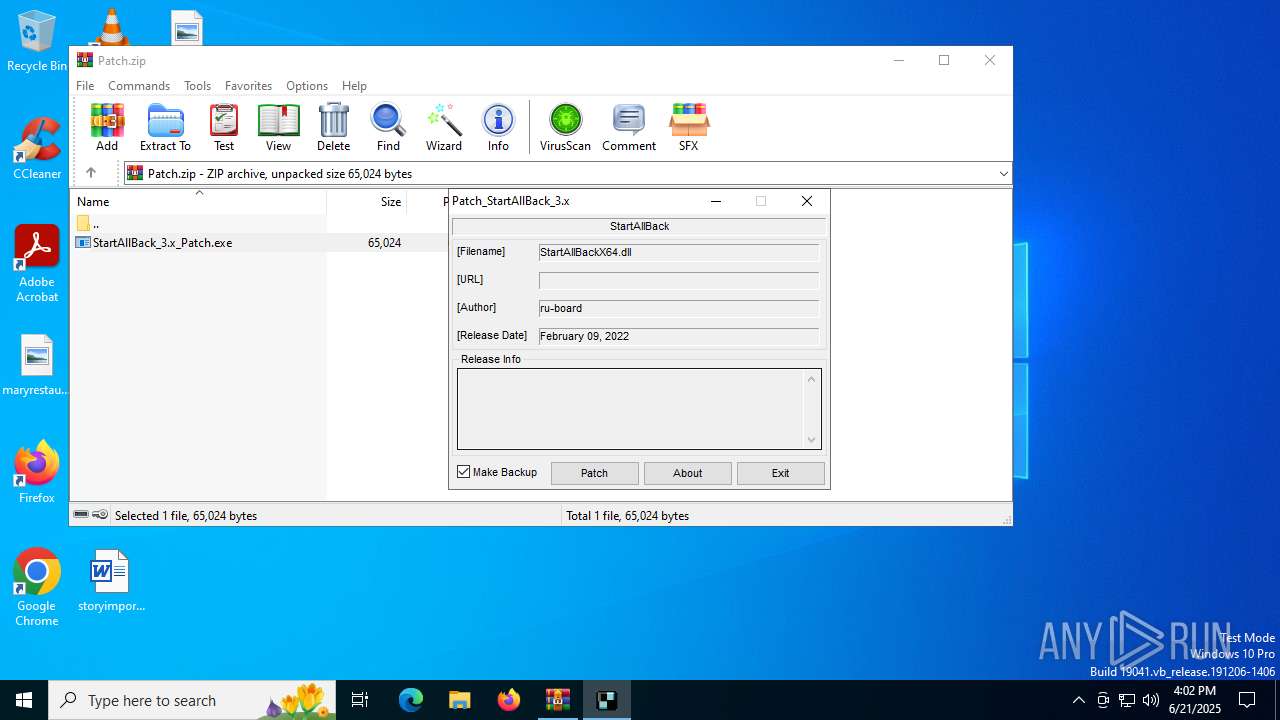
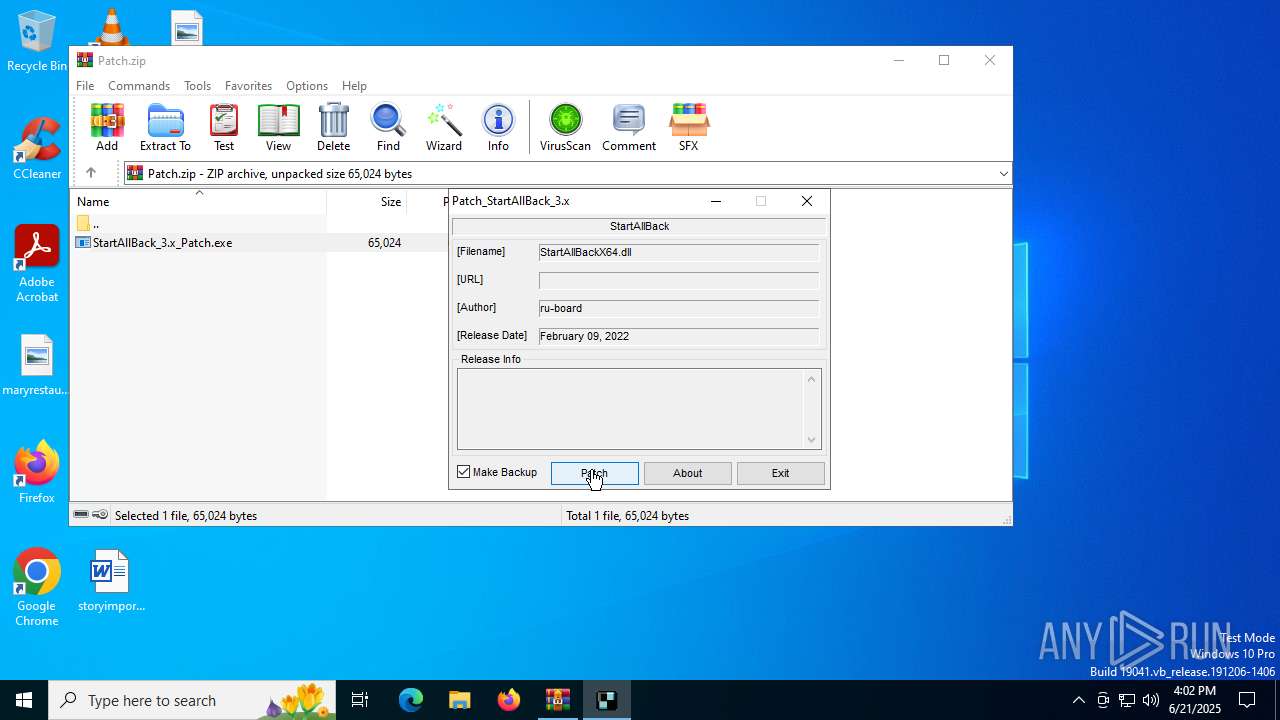
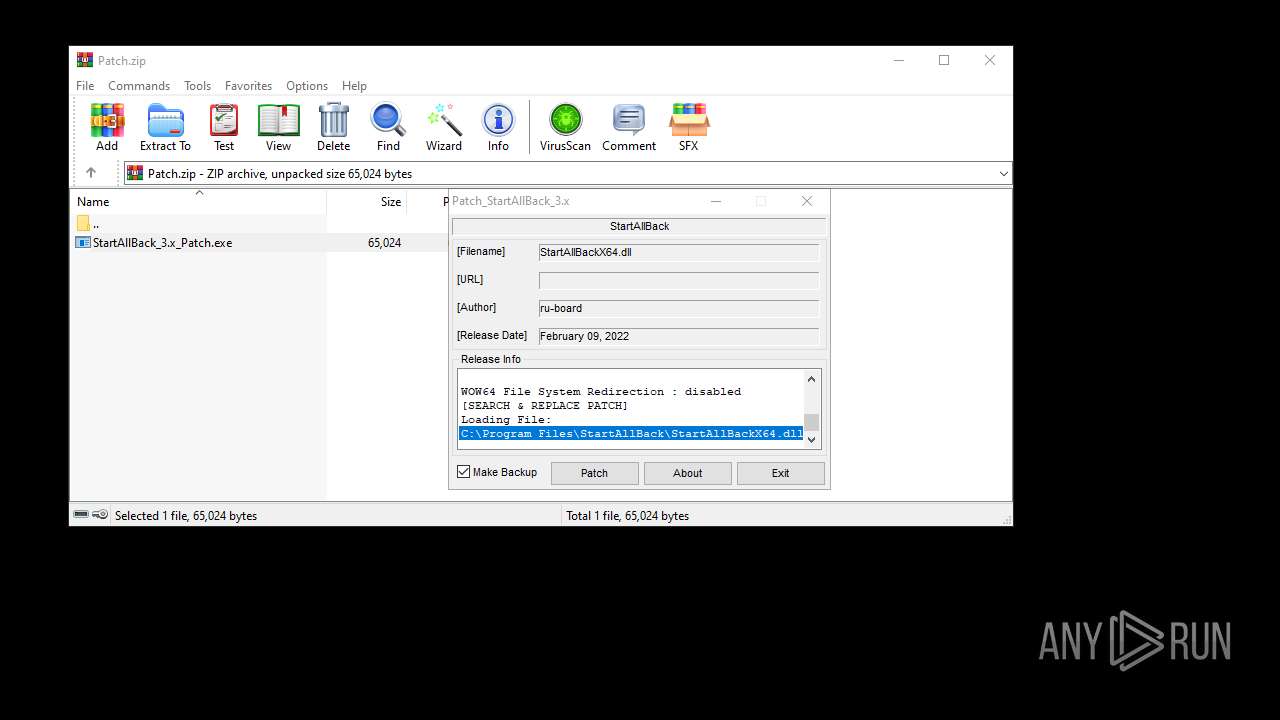
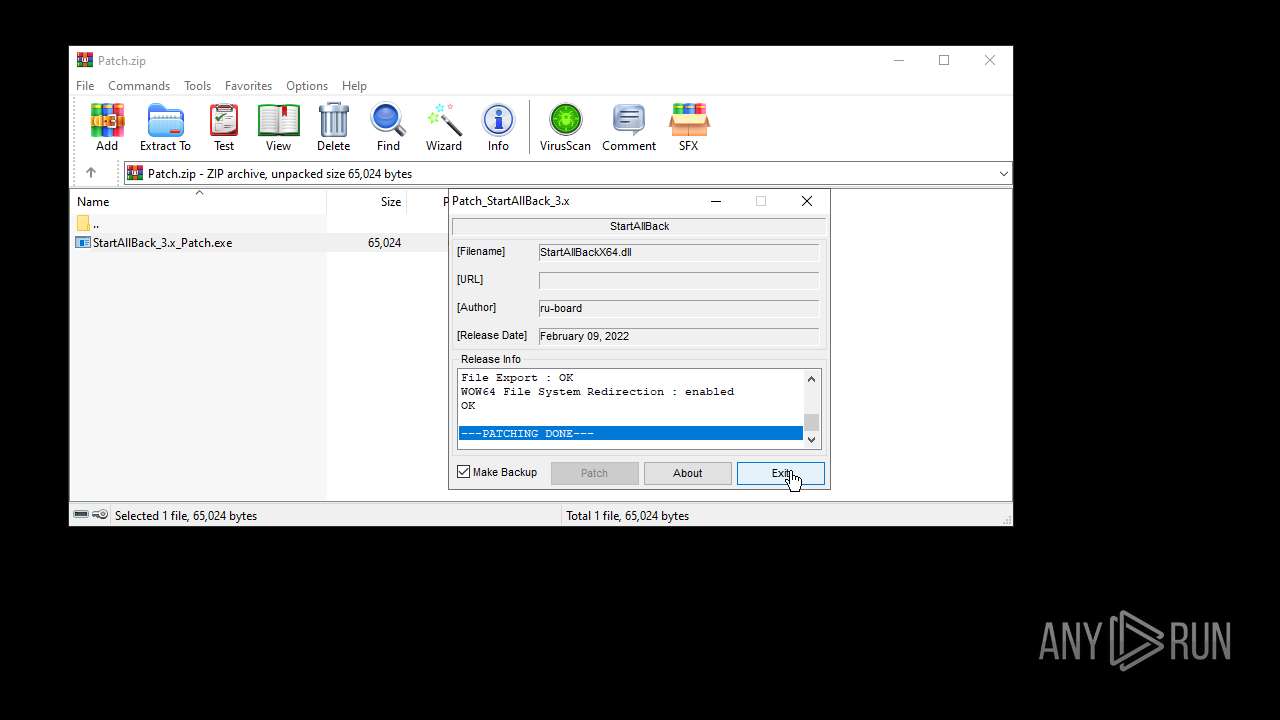
| File name: | Patch.zip |
| Full analysis: | https://app.any.run/tasks/f9712d93-1ef5-40ba-9de0-e17f8bc334c8 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 16:02:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 44416C453E3A38ABAF11A5D2F5DF2466 |
| SHA1: | 928872F6BA4FB6E4151591078D0C03F64D7B512D |
| SHA256: | 3FD8B29CD45ABCF30449F94423AE3FA6E38778C195C5160D5863E59259F71CE7 |
| SSDEEP: | 1536:F26Fincmz/mwNe2v14aSRaNLyXNcxI5BePSG7:wncmSwNe2v14aSRALymW/ex7 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 3888)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- StartAllBack_3.x_Patch.exe (PID: 6428)
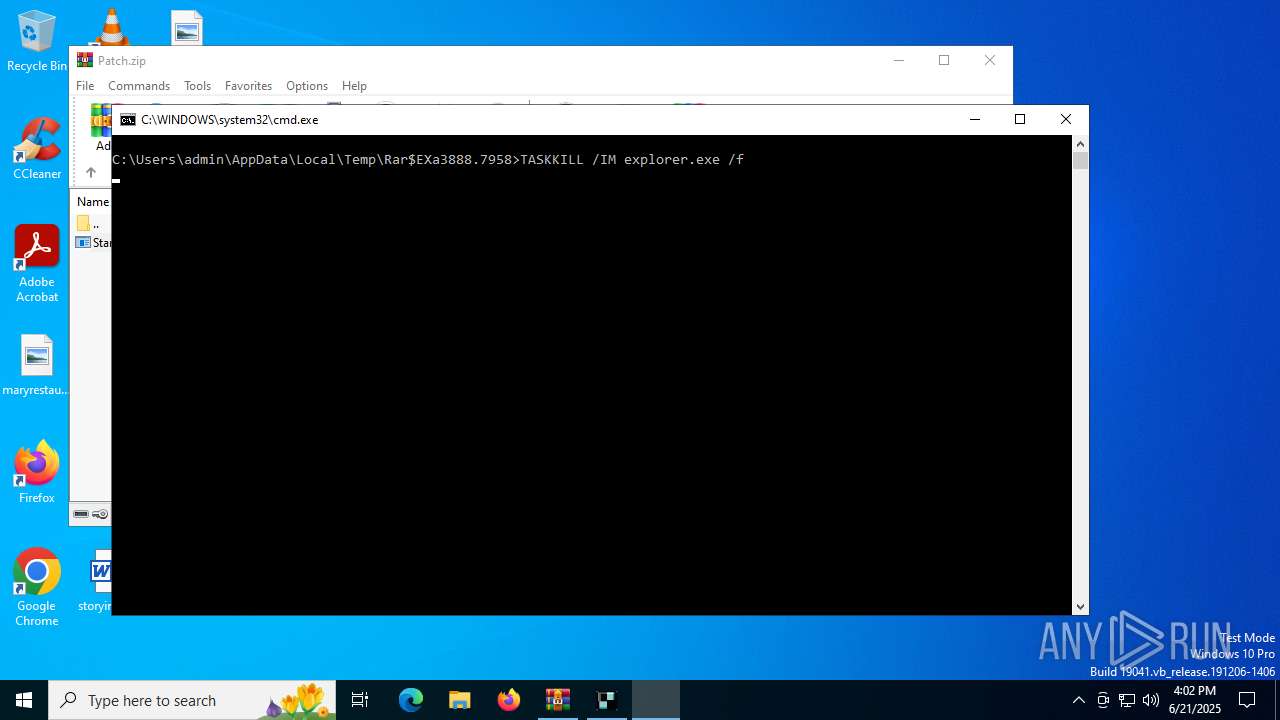
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 760)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3888)
- StartAllBack_3.x_Patch.exe (PID: 6428)
- StartMenuExperienceHost.exe (PID: 5744)
Executable content was dropped or overwritten
- StartAllBack_3.x_Patch.exe (PID: 6428)
Executing commands from ".cmd" file
- StartAllBack_3.x_Patch.exe (PID: 6428)
Starts CMD.EXE for commands execution
- StartAllBack_3.x_Patch.exe (PID: 6428)
The process executes via Task Scheduler
- explorer.exe (PID: 1644)
Reads the date of Windows installation
- SearchApp.exe (PID: 5964)
- StartMenuExperienceHost.exe (PID: 5744)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3888)
Checks supported languages
- StartAllBack_3.x_Patch.exe (PID: 6428)
- StartMenuExperienceHost.exe (PID: 5744)
- SearchApp.exe (PID: 5964)
Create files in a temporary directory
- StartAllBack_3.x_Patch.exe (PID: 6428)
Reads the computer name
- StartAllBack_3.x_Patch.exe (PID: 6428)
- StartMenuExperienceHost.exe (PID: 5744)
- SearchApp.exe (PID: 5964)
Reads security settings of Internet Explorer
- explorer.exe (PID: 1644)
Process checks computer location settings
- StartMenuExperienceHost.exe (PID: 5744)
- SearchApp.exe (PID: 5964)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5964)
Checks proxy server information
- SearchApp.exe (PID: 5964)
- explorer.exe (PID: 1644)
Reads the software policy settings
- SearchApp.exe (PID: 5964)
Reads Environment values
- SearchApp.exe (PID: 5964)
Creates files or folders in the user directory
- explorer.exe (PID: 1644)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2022:02:09 19:01:40 |
| ZipCRC: | 0x3fe5c675 |
| ZipCompressedSize: | 61515 |
| ZipUncompressedSize: | 65024 |
| ZipFileName: | StartAllBack_3.x_Patch.exe |
Total processes
155
Monitored processes
15
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 620 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 760 | C:\WINDOWS\system32\cmd.exe /c "C:\Users\admin\AppData\Local\Temp\Rar$EXa3888.7958\kill.cmd" | C:\Windows\System32\cmd.exe | — | StartAllBack_3.x_Patch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | C:\WINDOWS\System32\mobsync.exe -Embedding | C:\Windows\System32\mobsync.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Sync Center Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1468 | TASKKILL /IM explorer.exe /f | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1644 | "C:\WINDOWS\explorer.exe" /NoUACCheck | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3888 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Patch.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4036 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4456 | explorer.exe | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 2 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4648 | C:\WINDOWS\system32\cmd.exe /c "C:\Users\admin\AppData\Local\Temp\Rar$EXa3888.7958\start.cmd" | C:\Windows\System32\cmd.exe | — | StartAllBack_3.x_Patch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4960 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
28 017
Read events
27 744
Write events
252
Delete events
21
Modification events
| (PID) Process: | (3888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Patch.zip | |||
| (PID) Process: | (3888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6428) StartAllBack_3.x_Patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (6428) StartAllBack_3.x_Patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 040000000000000003000000110000000E000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
Executable files
4
Suspicious files
45
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6428 | StartAllBack_3.x_Patch.exe | C:\Users\admin\AppData\Local\Temp\dup2patcher.dll | executable | |
MD5:2FCAC0A53E9AAFFA146E751F8A1E1AE4 | SHA256:62DCA27BFCF3CFAB9FE834CA78278BE7A53D8C1B485C0FA5051A86703FE79059 | |||
| 6428 | StartAllBack_3.x_Patch.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3888.7958\start.cmd | text | |
MD5:911E338D3E70218DE331BF02C38B4DAC | SHA256:CA3E34E1ECC3DF0A2EB47429C1252C24A0FE16CB6805A4EAA698379E0896D999 | |||
| 5964 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:5A996F0A3D2526E619BEE7BB4381A488 | SHA256:CF97DDB8D8FD7789294FE7BA26B9BC7D542E62F4D5B86BC75BA79C6D0787B063 | |||
| 3888 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3888.7958\StartAllBack_3.x_Patch.exe | executable | |
MD5:07CA9EF8CA62BDFDCB8BD9B966D60BF2 | SHA256:124A96831880A7F4EC1C70705466B9A48723CA387F7ABC12F0D28D28A18EDF20 | |||
| 6428 | StartAllBack_3.x_Patch.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3888.7958\kill.cmd | text | |
MD5:B8332745BD37B45E7EC3FC8CC04EC422 | SHA256:F56D48597370F2B4417CAB335F95485F065315375F41931FFF5D782F3AC103D9 | |||
| 5964 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\Internet Explorer\DOMStore\ZWUI0EBX\www.bing[1].xml | text | |
MD5:B0A9A11AC525CE02839225DE1754AA52 | SHA256:A9F5DA370F8E07472A7D1B708E790C1D3B8C96C5E0B260777BD07F452AABD0E1 | |||
| 5964 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\INetCache\Q84V0JUH\6hU_LneafI_NFLeDvM367ebFaKQ[1].js | binary | |
MD5:C6C21B7634D82C53FB86080014D86E66 | SHA256:D39E9BA92B07F4D50B11A49965E9B162452D7B9C9F26D9DCB07825727E31057E | |||
| 5964 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\tUCiVcVWZ-go7BLlq95YW6bKHZE[1].css | text | |
MD5:445D78544E0CFC11EFC1E172DA3ECBBC | SHA256:76EFEBABB82AE8342985C99A498137C04B3E46BC59D78191F0DA44C660B980F5 | |||
| 5964 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\NajusmjIqB4kdLn9FmVxeS4xi2o[1].css | text | |
MD5:73D1CEBD8E3B6C7246F422D624EDF803 | SHA256:0674786CF9978A1F9065F57D98E986070C7CBB5177F154F40E8A924C0E0C13F2 | |||
| 5964 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\3-X3h7uDMtfcne46mFDSZyqDAWs.br[1].js | binary | |
MD5:E766B650487DC4BC853C0DF56D828A34 | SHA256:5294321F5371681E306FE4FB2D8FD9E6E4829BB27FB6338C6F3FABF19DF2FCBA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
34
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7164 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1508 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5964 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1508 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5012 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7164 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7164 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |