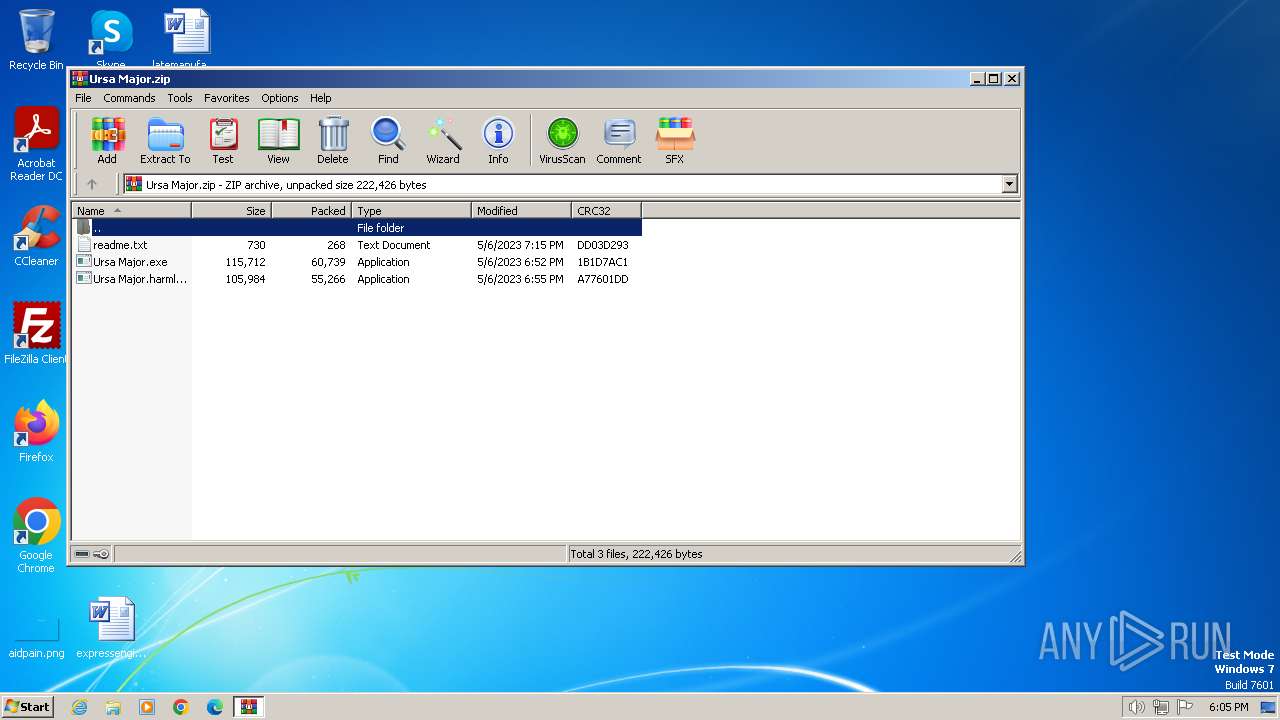
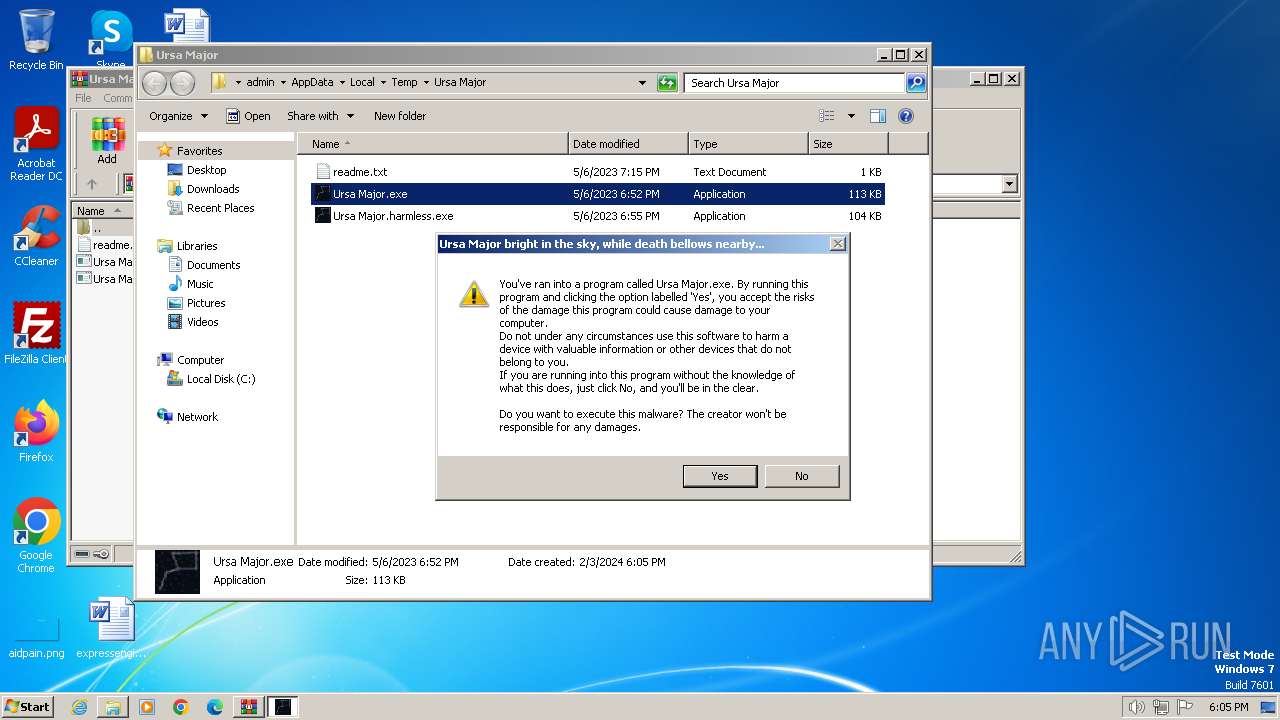
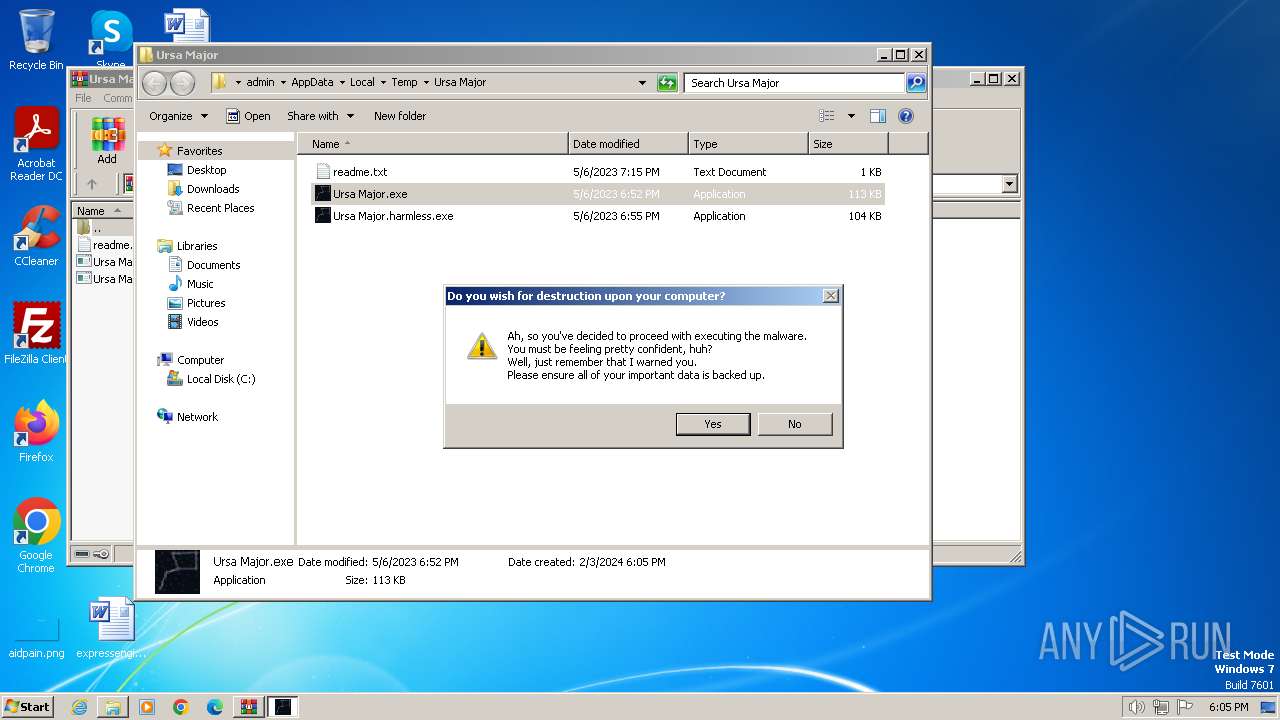
| File name: | Ursa Major.zip |
| Full analysis: | https://app.any.run/tasks/6bf2424c-e0b0-4bed-8abc-5c0afbd0477c |
| Verdict: | Malicious activity |
| Analysis date: | February 03, 2024, 18:05:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 29871EE46BA50FAAAF7E7609C8329DAA |
| SHA1: | AAD44E6D6BEAF82DABB8FC3D503F6FB1A0773C8E |
| SHA256: | 3FCDFDC0493E7673BA2489CE260355E6C96EA039A6D7A13170CAEF8188B1FAEB |
| SSDEEP: | 3072:0yE61zaTwb9tdo9OA6tUxf8Njfu6iCStGkibRS7CU6Qboe0:HHzaa9tdAzxkfhiCjD0GU70 |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 752)
Create files in the Startup directory
- regsvr32.exe (PID: 2092)
Actions looks like stealing of personal data
- setup.exe (PID: 2448)
- setup.exe (PID: 2692)
- setup.exe (PID: 2408)
Antivirus name has been found in the command line (generic signature)
- unregmp2.exe (PID: 2040)
SUSPICIOUS
The process executes via Task Scheduler
- ctfmon.exe (PID: 1668)
- sipnotify.exe (PID: 1496)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3808)
- cmd.exe (PID: 3364)
Changes internet zones settings
- ie4uinit.exe (PID: 1956)
Starts CMD.EXE for commands execution
- Ursa Major.exe (PID: 4092)
Write to the desktop.ini file (may be used to cloak folders)
- ie4uinit.exe (PID: 1956)
- WinMail.exe (PID: 1900)
- regsvr32.exe (PID: 2092)
Application launched itself
- ie4uinit.exe (PID: 1956)
- rundll32.exe (PID: 1424)
- setup.exe (PID: 2408)
- setup.exe (PID: 2692)
Uses RUNDLL32.EXE to load library
- rundll32.exe (PID: 1424)
- ie4uinit.exe (PID: 1956)
Reads the Internet Settings
- ie4uinit.exe (PID: 2032)
- ie4uinit.exe (PID: 2080)
- rundll32.exe (PID: 2208)
- ie4uinit.exe (PID: 1956)
Reads Microsoft Outlook installation path
- ie4uinit.exe (PID: 1956)
Changes the title of the Internet Explorer window
- iexplore.exe (PID: 3152)
INFO
Manual execution by a user
- Ursa Major.exe (PID: 4092)
- regsvr32.exe (PID: 340)
- ie4uinit.exe (PID: 1956)
- WinMail.exe (PID: 1900)
- ie4uinit.exe (PID: 2032)
- ie4uinit.exe (PID: 2080)
- unregmp2.exe (PID: 2040)
- regsvr32.exe (PID: 2092)
- rundll32.exe (PID: 2208)
- chrmstp.exe (PID: 2220)
- setup.exe (PID: 2408)
- IMEKLMG.EXE (PID: 2528)
- IMEKLMG.EXE (PID: 2548)
- wmpnscfg.exe (PID: 3040)
- explorer.exe (PID: 2792)
- wmpnscfg.exe (PID: 3056)
- wmpnscfg.exe (PID: 2448)
- iexplore.exe (PID: 3152)
Checks supported languages
- Ursa Major.exe (PID: 4092)
- WinMail.exe (PID: 1900)
- setup.exe (PID: 2416)
- setup.exe (PID: 2408)
- IMEKLMG.EXE (PID: 2528)
- IMEKLMG.EXE (PID: 2548)
- IMJPPDMG.EXE (PID: 2708)
- IMKRMIG.EXE (PID: 2560)
- wmpnscfg.exe (PID: 3040)
- wmpnscfg.exe (PID: 3056)
- wmpnscfg.exe (PID: 2448)
- setup.exe (PID: 2752)
- setup.exe (PID: 2692)
- setup.exe (PID: 2448)
Reads the computer name
- Ursa Major.exe (PID: 4092)
- WinMail.exe (PID: 1900)
- setup.exe (PID: 2448)
- IMEKLMG.EXE (PID: 2528)
- IMJPPDMG.EXE (PID: 2708)
- IMEKLMG.EXE (PID: 2548)
- wmpnscfg.exe (PID: 3040)
- wmpnscfg.exe (PID: 3056)
- wmpnscfg.exe (PID: 2448)
- setup.exe (PID: 2752)
- setup.exe (PID: 2416)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 752)
Reads the machine GUID from the registry
- WinMail.exe (PID: 1900)
Creates files or folders in the user directory
- WinMail.exe (PID: 1900)
- unregmp2.exe (PID: 2040)
- regsvr32.exe (PID: 2092)
Application launched itself
- chrmstp.exe (PID: 2220)
- chrmstp.exe (PID: 2268)
- iexplore.exe (PID: 3152)
- msedge.exe (PID: 3360)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2528)
- IMEKLMG.EXE (PID: 2548)
- IMJPPDMG.EXE (PID: 2708)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:05:06 18:52:22 |
| ZipCRC: | 0x1b1d7ac1 |
| ZipCompressedSize: | 60739 |
| ZipUncompressedSize: | 115712 |
| ZipFileName: | Ursa Major.exe |
Total processes
155
Monitored processes
59
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | REG DELETE HKEY_users /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 340 | "C:\Windows\System32\regsvr32.exe" /s /n /i:/UserInstall C:\Windows\system32\themeui.dll | C:\Windows\System32\regsvr32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 752 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Ursa Major.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1088 | C:\Windows\System32\rundll32 advpack.dll,LaunchINFSectionEx C:\Windows\system32\ieuinit.inf,Install,,36 | C:\Windows\System32\rundll32.exe | — | ie4uinit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1424 | C:\Windows\System32\rundll32 C:\Windows\system32\migration\WininetPlugin.dll,MigrateCacheForUser /m | C:\Windows\System32\rundll32.exe | — | ie4uinit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1496 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1632 | C:\Windows\system32\RunDll32.exe C:\Windows\system32\migration\WininetPlugin.dll,MigrateCacheForUser /m /0 | C:\Windows\System32\rundll32.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1668 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1900 | "C:\Program Files\Windows Mail\WinMail.exe" OCInstallUserConfigOE | C:\Program Files\Windows Mail\WinMail.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Mail Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1956 | "C:\Windows\System32\ie4uinit.exe" -UserConfig | C:\Windows\System32\ie4uinit.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IE Per-User Initialization Utility Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
38 612
Read events
25 894
Write events
397
Delete events
12 321
Modification events
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (292) reg.exe | Key: | HKEY_CURRENT_USER\AppEvents\EventLabels\.Default |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
8
Suspicious files
160
Text files
133
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1956 | ie4uinit.exe | C:\Windows\TEMP\RGI250F.tmp | text | |
MD5:31CB7778F65DF8D02353E6C7B2B2CFFC | SHA256:647A8C7F316EF325F73C2037E8883854F9287584904C977C81D1662DB6471A58 | |||
| 752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Ursa Major\Ursa Major.harmless.exe | executable | |
MD5:4F6EB1A44BCC7A46F325B787225C22F0 | SHA256:455812C6A35A99AC4CB753B48AA032C56E494420DF71126C0AB25D5BFD831414 | |||
| 1956 | ie4uinit.exe | C:\Users\admin\Favorites\Links\Web Slice Gallery.url | text | |
MD5:1E7E5E93C2A5AADAF932F93D25C57F3E | SHA256:8B94D04FECE582E4182E8E73F46FB86EB8E965C69C526C42805ABB9E43641E35 | |||
| 1956 | ie4uinit.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\brndlog.bak | text | |
MD5:E9E473C9777B0C24D50EE8C972A78FE2 | SHA256:90BE32975E76E679B01FF719148DF508CBBE2D7F2C47D93201F33A31994B4174 | |||
| 1956 | ie4uinit.exe | C:\Windows\TEMP\RGI256E.tmp | text | |
MD5:87BA1D52A05A8D4343356EB0C6279DE2 | SHA256:564A351DB0AB9249751ECF3F5D03049A43BEB0F8F3B95A5B8AAE9A9F7D0C17FB | |||
| 1956 | ie4uinit.exe | C:\Windows\TEMP\www26F5.tmp | binary | |
MD5:873C8643CBBFB8FF63731BC25AC9B18C | SHA256:C4AD21379C11DA7943C605EADB22F6FC6F54B49783466F8C1F3AD371EB167466 | |||
| 1900 | WinMail.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Mail\edb.log | binary | |
MD5:09F9EC30C43F61C1B4E3CF574CEF1740 | SHA256:3A2C8485989DE3437B107D5459308E6984CC2D0F029B25CA74DFA0BC4B754054 | |||
| 1956 | ie4uinit.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Tiles\pin9728060290\msapplication.xml | xml | |
MD5:4057DC3819C2F00164C416BA0C19FD6D | SHA256:E7892793F676B3C21071529D5967FB75C4746BCD8A595EB464BAE3C5BB8411D2 | |||
| 1956 | ie4uinit.exe | C:\Windows\TEMP\www26F6.tmp | binary | |
MD5:C2858B664C882DCCE6042C40041F6108 | SHA256:B4A6FB97B5E3F87BCD9FAE49A9174E3F5B230A37767D7A70BF33D151702EFF91 | |||
| 752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Ursa Major\Ursa Major.exe | executable | |
MD5:A5DD8BABDEE5E2C377E848E128C4A131 | SHA256:8BC5B7E08C1ECCE47BC450E6E3523B4C20FF3A50C22812BDF1C9B7CA5CF52269 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
32
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3248 | iexplore.exe | GET | 200 | 184.24.77.207:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a055bf949f709bf8 | unknown | compressed | 4.66 Kb | unknown |
3152 | iexplore.exe | GET | 200 | 184.24.77.207:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f5058ef4554a5e5c | unknown | compressed | 4.66 Kb | unknown |
3248 | iexplore.exe | GET | 200 | 184.24.77.207:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8f2c92b493bcf6fb | unknown | compressed | 4.66 Kb | unknown |
3152 | iexplore.exe | GET | 200 | 184.24.77.207:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6abadbe2aa656a5c | unknown | compressed | 4.66 Kb | unknown |
3152 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
3248 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
3248 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | binary | 471 b | unknown |
3152 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEA6Nvl6mEObLtWnHNvbXAEs%3D | unknown | binary | 312 b | unknown |
3152 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1096 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3152 | iexplore.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
3248 | iexplore.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
3152 | iexplore.exe | 184.24.77.207:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3248 | iexplore.exe | 184.24.77.207:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3248 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3152 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
query.prod.cms.rt.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
www.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |