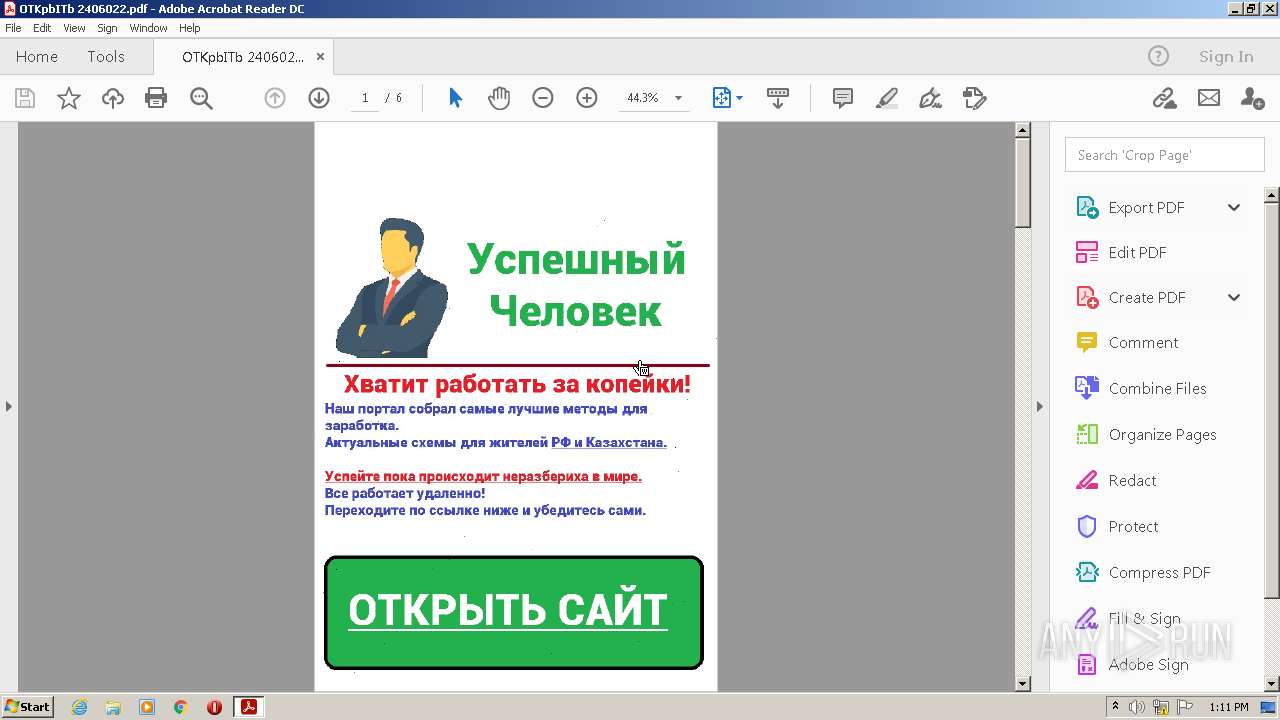
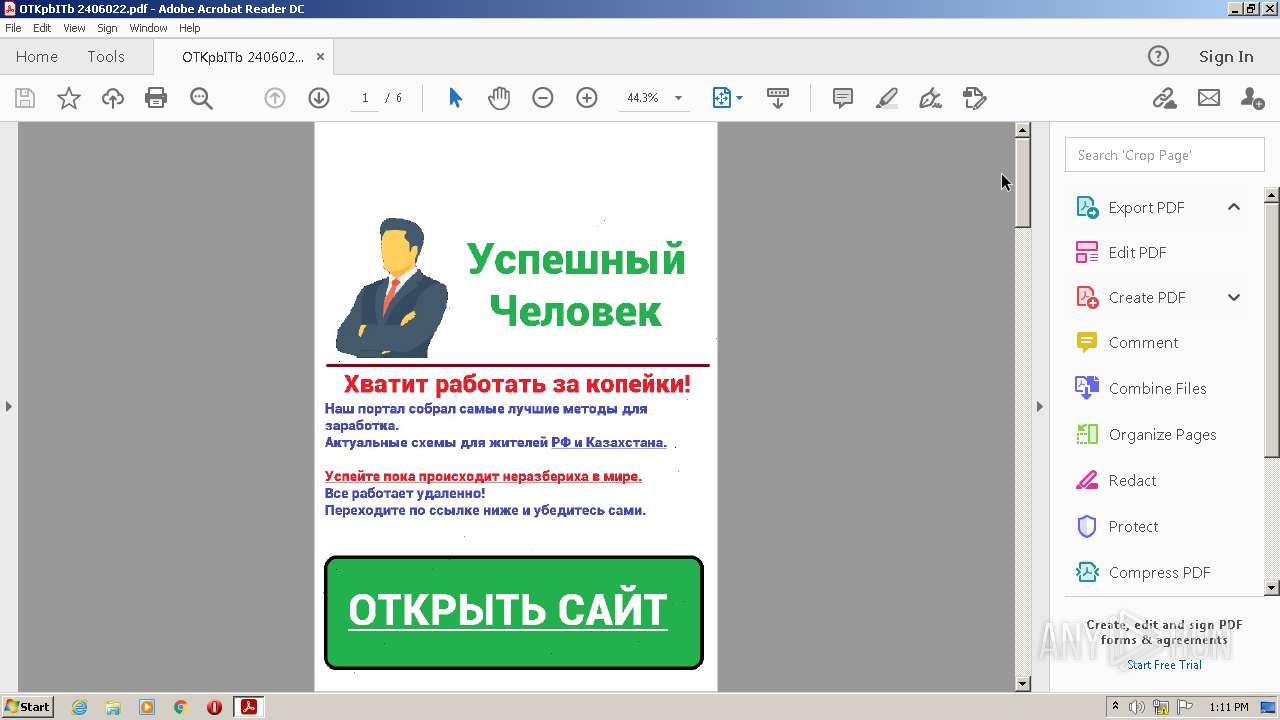
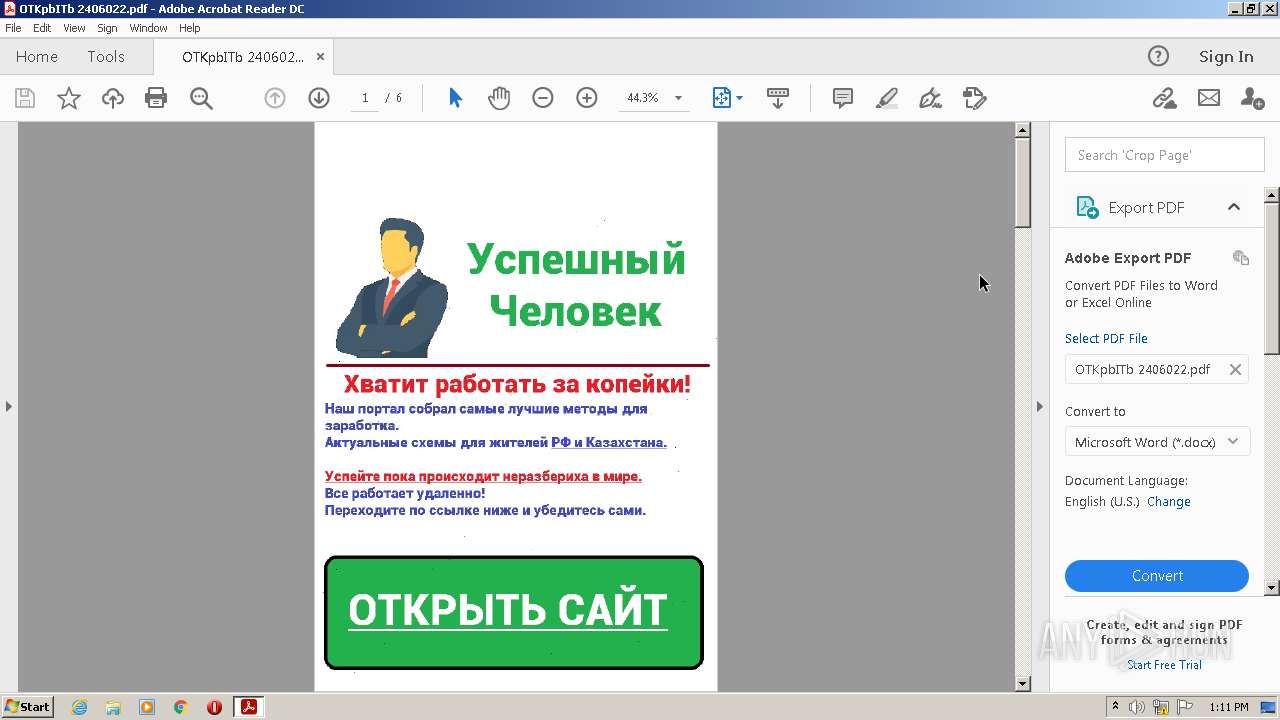
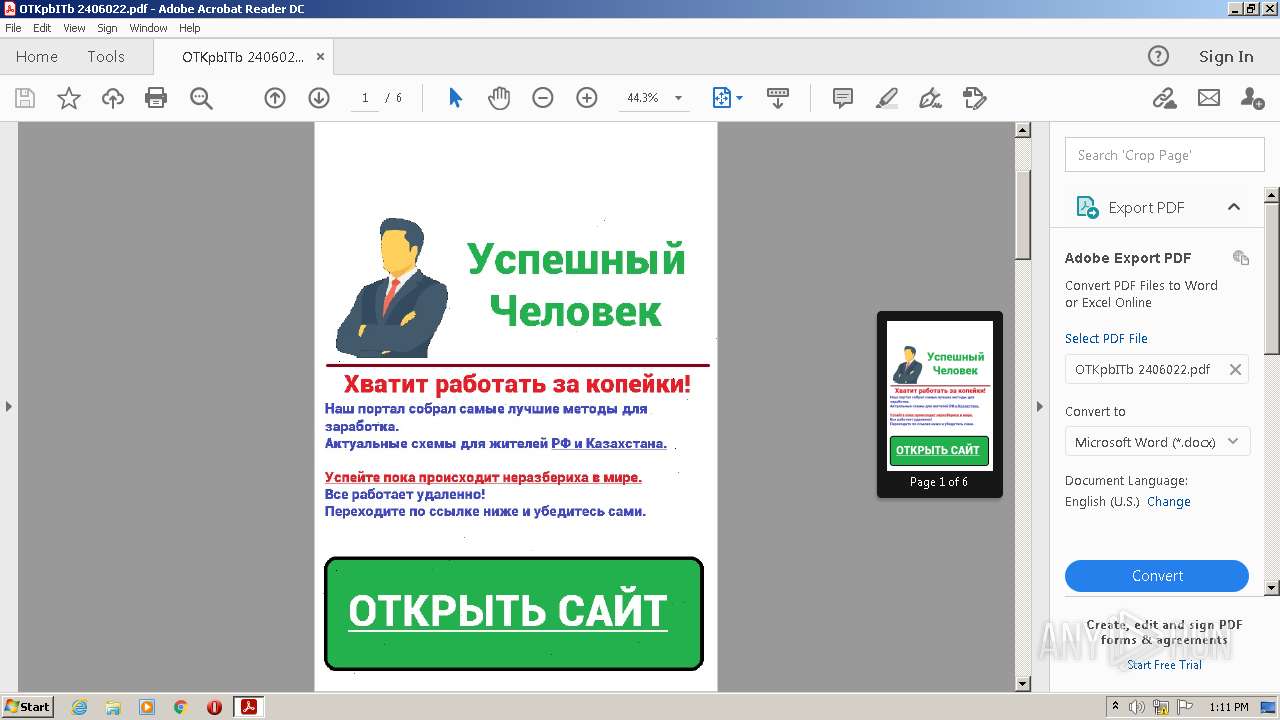
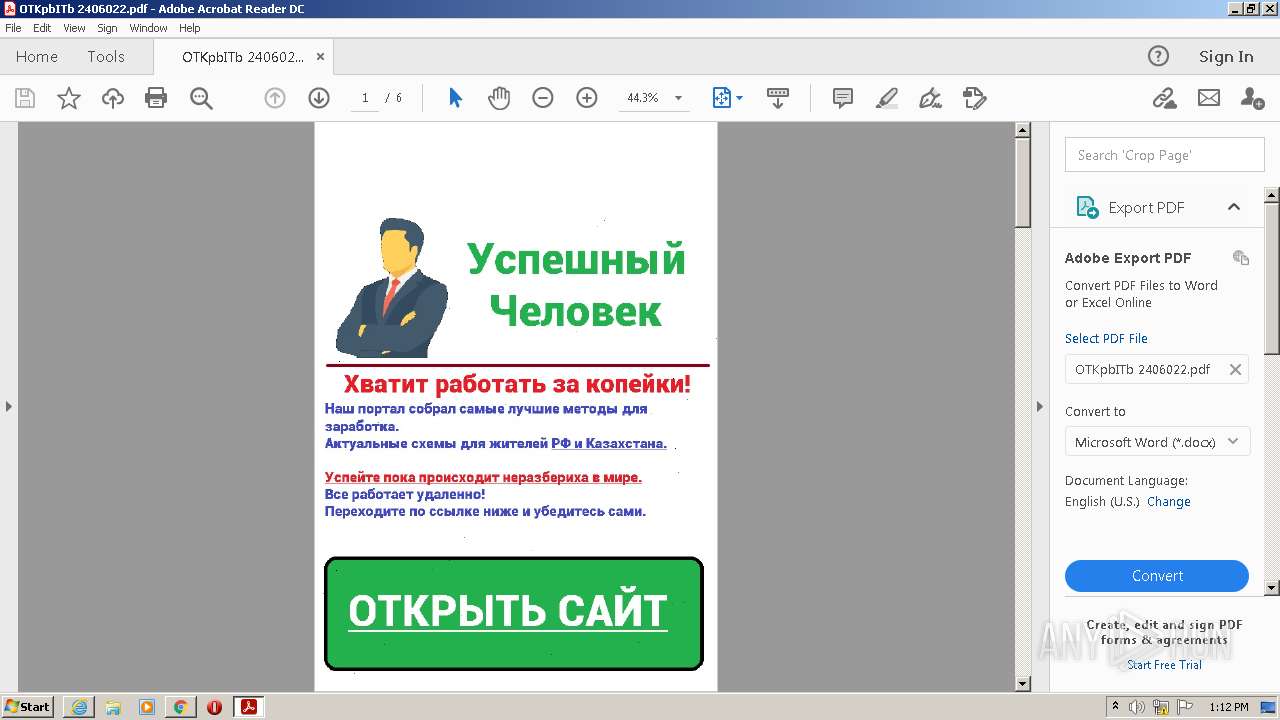
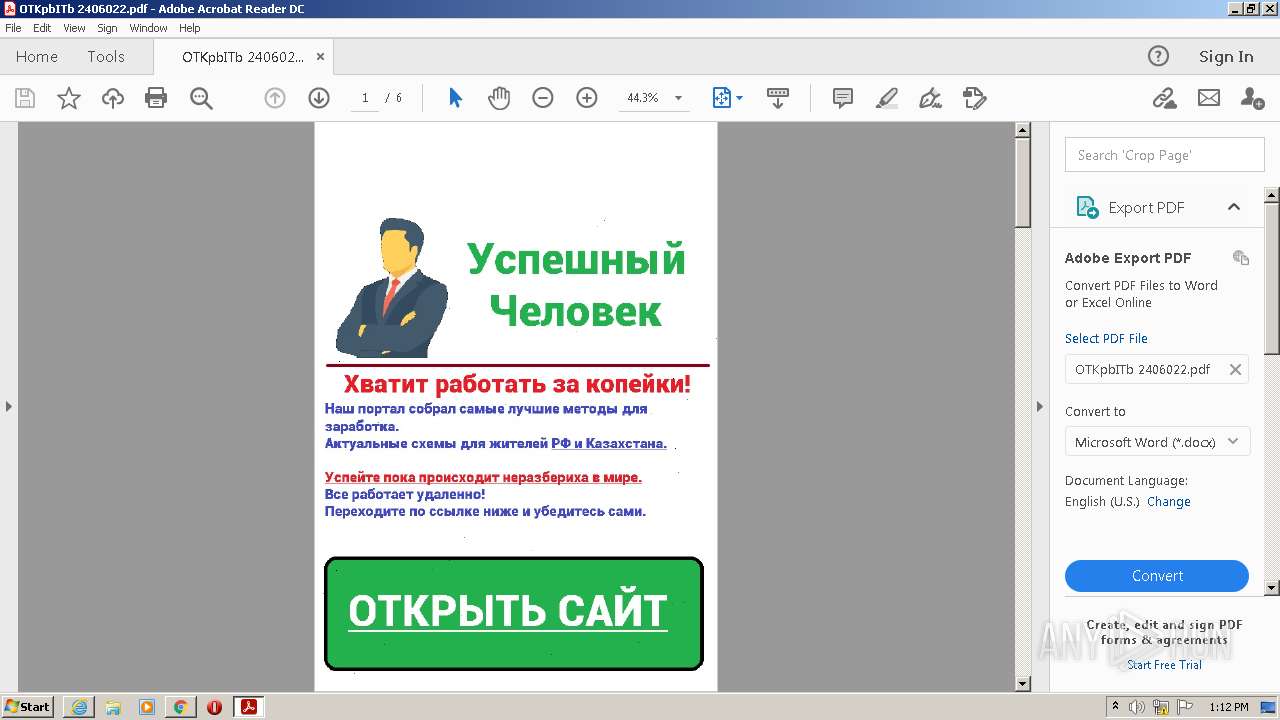
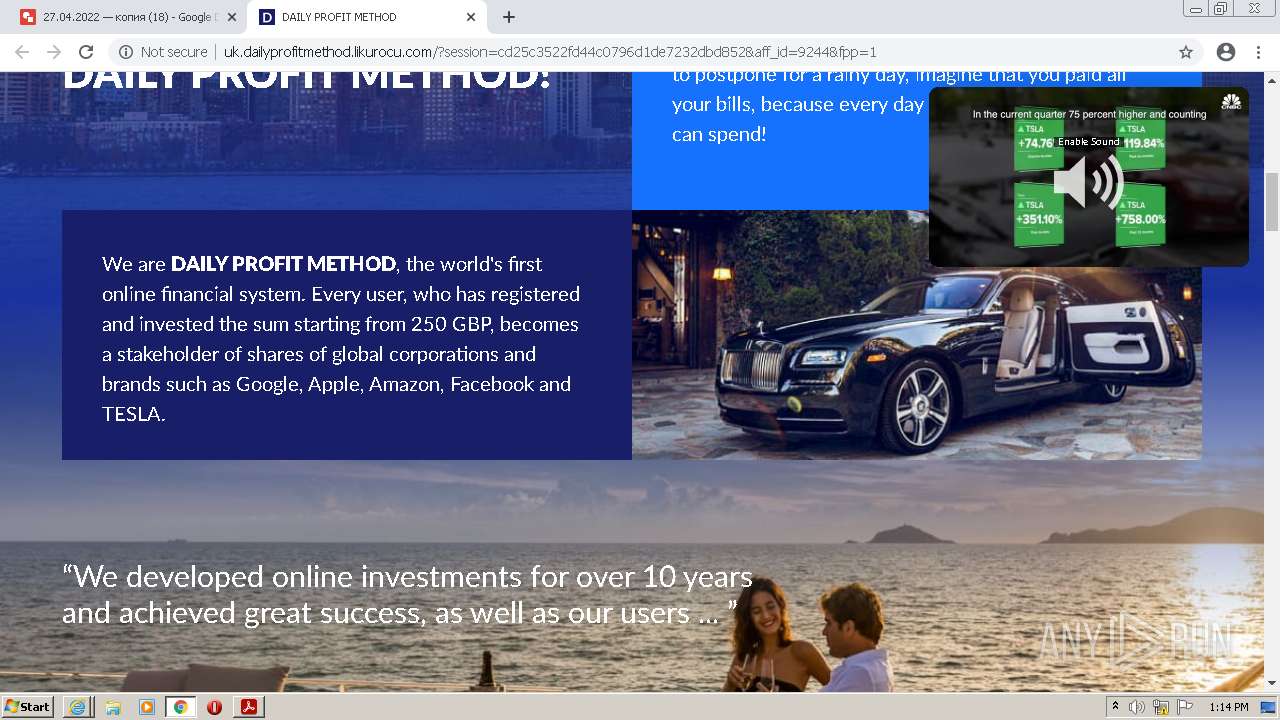
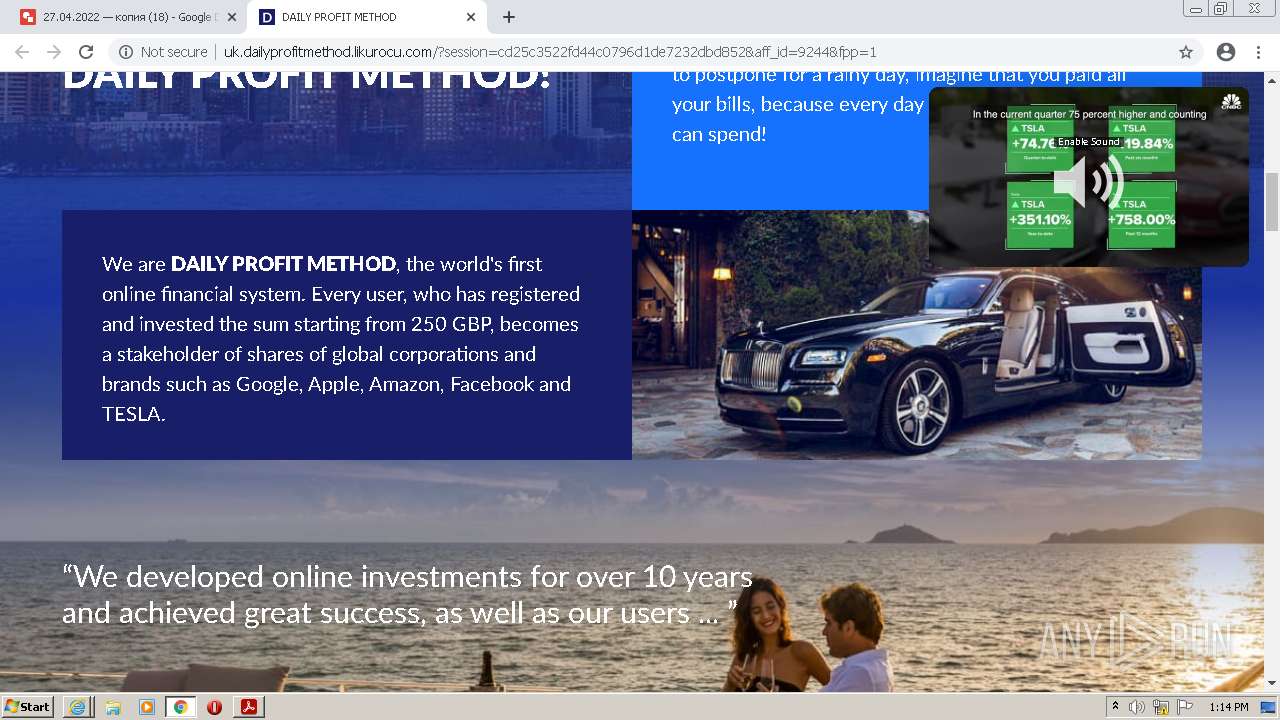
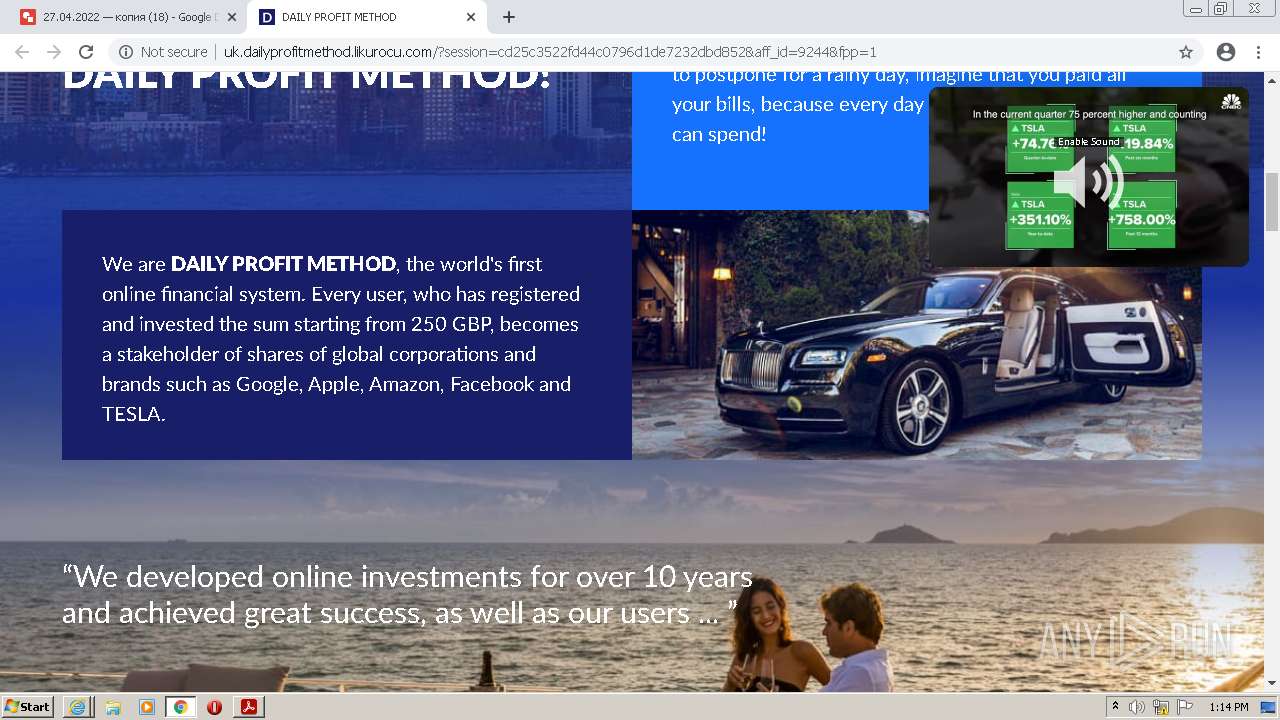
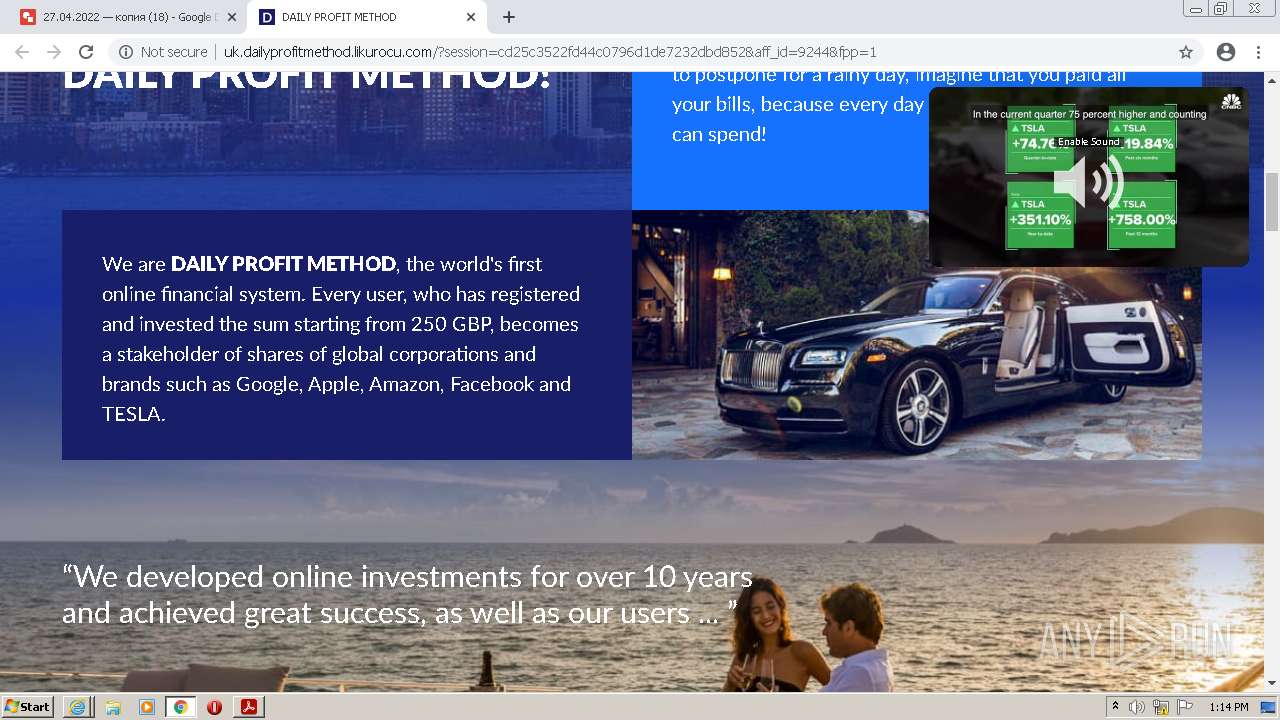
| File name: | OTKpbITb 2406022.pdf |
| Full analysis: | https://app.any.run/tasks/760ea75a-04ff-40e6-b525-5ceb3ef79d31 |
| Verdict: | Malicious activity |
| Analysis date: | April 27, 2022, 12:11:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.3 |
| MD5: | 8E615798F8780C60A8F53D9851E018AA |
| SHA1: | 1D057987AF89D80B05609A28011517F24F76C05B |
| SHA256: | 3FCD58CD55C13272586E09A7D603B91803000DDFE7A402A405885BCCB7250D1D |
| SSDEEP: | 6144:XTfaYpc5+U44F9vs2IxBRtpAOpZ1uxgQspmg98SWsZ5q9kjB1hUooMW:DCYS7vKPAOpZOB5SWsrqqjB1ti |
MALICIOUS
Drops executable file immediately after starts
- chrome.exe (PID: 2884)
- chrome.exe (PID: 2268)
SUSPICIOUS
Starts Internet Explorer
- AcroRd32.exe (PID: 2952)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2640)
- iexplore.exe (PID: 2520)
Reads the computer name
- AdobeARM.exe (PID: 3320)
Checks supported languages
- AdobeARM.exe (PID: 3320)
- Reader_sl.exe (PID: 1260)
Creates files in the program directory
- AdobeARM.exe (PID: 3320)
Executable content was dropped or overwritten
- AdobeARM.exe (PID: 3320)
- chrome.exe (PID: 2268)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2888)
Drops a file with a compile date too recent
- chrome.exe (PID: 2884)
- chrome.exe (PID: 2268)
INFO
Checks supported languages
- AcroRd32.exe (PID: 2952)
- RdrCEF.exe (PID: 3732)
- AcroRd32.exe (PID: 3028)
- RdrCEF.exe (PID: 2360)
- RdrCEF.exe (PID: 2460)
- RdrCEF.exe (PID: 3508)
- RdrCEF.exe (PID: 3416)
- RdrCEF.exe (PID: 2936)
- RdrCEF.exe (PID: 312)
- RdrCEF.exe (PID: 3176)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 2640)
- chrome.exe (PID: 2888)
- chrome.exe (PID: 2884)
- chrome.exe (PID: 3844)
- chrome.exe (PID: 392)
- chrome.exe (PID: 2820)
- chrome.exe (PID: 2308)
- chrome.exe (PID: 2816)
- chrome.exe (PID: 2512)
- chrome.exe (PID: 2180)
- chrome.exe (PID: 1008)
- chrome.exe (PID: 3412)
- chrome.exe (PID: 3672)
- chrome.exe (PID: 3968)
- chrome.exe (PID: 1460)
- chrome.exe (PID: 3080)
- iexplore.exe (PID: 2520)
- chrome.exe (PID: 3748)
- chrome.exe (PID: 2304)
- chrome.exe (PID: 456)
- chrome.exe (PID: 3540)
- chrome.exe (PID: 4044)
- chrome.exe (PID: 2244)
- chrome.exe (PID: 2268)
- chrome.exe (PID: 2948)
- chrome.exe (PID: 3952)
- chrome.exe (PID: 1996)
- chrome.exe (PID: 3776)
- chrome.exe (PID: 3872)
Reads the computer name
- AcroRd32.exe (PID: 2952)
- AcroRd32.exe (PID: 3028)
- RdrCEF.exe (PID: 3732)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 2640)
- chrome.exe (PID: 2888)
- chrome.exe (PID: 392)
- chrome.exe (PID: 2884)
- chrome.exe (PID: 2180)
- iexplore.exe (PID: 2520)
- chrome.exe (PID: 3672)
- chrome.exe (PID: 3776)
- chrome.exe (PID: 2304)
- chrome.exe (PID: 4044)
- chrome.exe (PID: 3412)
Application launched itself
- AcroRd32.exe (PID: 2952)
- RdrCEF.exe (PID: 3732)
- iexplore.exe (PID: 3040)
- chrome.exe (PID: 2888)
Searches for installed software
- AcroRd32.exe (PID: 2952)
- AcroRd32.exe (PID: 3028)
Reads CPU info
- AcroRd32.exe (PID: 3028)
Reads the hosts file
- RdrCEF.exe (PID: 3732)
- chrome.exe (PID: 2888)
- chrome.exe (PID: 2884)
Checks Windows Trust Settings
- AcroRd32.exe (PID: 2952)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 2640)
- AdobeARM.exe (PID: 3320)
- iexplore.exe (PID: 2520)
Reads settings of System Certificates
- AcroRd32.exe (PID: 2952)
- RdrCEF.exe (PID: 3732)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 2640)
- AdobeARM.exe (PID: 3320)
- chrome.exe (PID: 2884)
- iexplore.exe (PID: 2520)
Changes internet zones settings
- iexplore.exe (PID: 3040)
Reads internet explorer settings
- iexplore.exe (PID: 2640)
- iexplore.exe (PID: 2520)
Creates files in the user directory
- iexplore.exe (PID: 2640)
- iexplore.exe (PID: 3040)
Changes settings of System certificates
- iexplore.exe (PID: 3040)
Manual execution by user
- chrome.exe (PID: 2888)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3040)
Reads the date of Windows installation
- chrome.exe (PID: 3776)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| ModifyDate: | 2022:04:27 13:33:57Z |
|---|---|
| Title: | Tycu Xeju Pido Roxynudi Firsi Sulureku Cewpy Vuqiby Dyninyry17360461136 |
| Subject: | dslkjgjvpylGARHPVAGYLCWTBWQTYOU |
| Keywords: | ag |
| Creator: | Noqufiru Vuryhope Zihu Vevuvi Buhki Becte Lesyvucy Solono Bidosyw Bozezuvi Wopje Lyjysyje Kijokiz Suwineb Gihliccywhbjilnwqro |
| CreateDate: | 2022:04:27 13:33:57Z |
| Author: | 5837350 |
| Producer: | Synopse PDF engine 1.18.6228 |
| PageCount: | 6 |
| PageLayout: | SinglePage |
| Linearized: | No |
| PDFVersion: | 1.3 |
Total processes
83
Monitored processes
42
Malicious processes
0
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 312 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1180,15304818258047361420,301068094136172566,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3386606312761745455 --renderer-client-id=7 --mojo-platform-channel-handle=1484 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1044,15264133679065764560,7555215307238881150,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1068 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 456 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,15264133679065764560,7555215307238881150,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=20 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2784 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1044,15264133679065764560,7555215307238881150,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2816 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1260 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe | — | AdobeARM.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat SpeedLauncher Exit code: 0 Version: 20.12.20041.394260 Modules
| |||||||||||||||
| 1460 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1044,15264133679065764560,7555215307238881150,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3552 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1996 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,15264133679065764560,7555215307238881150,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1568 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2180 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1044,15264133679065764560,7555215307238881150,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=1144 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2244 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1044,15264133679065764560,7555215307238881150,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3156 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1044,15264133679065764560,7555215307238881150,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1040 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
74 180
Read events
73 784
Write events
380
Delete events
16
Modification events
| (PID) Process: | (3028) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (3028) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | iNumReaderLaunches |
Value: 2 | |||
| (PID) Process: | (3028) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\FTEDialog |
| Operation: | write | Name: | bShowUpdateFTE |
Value: 1 | |||
| (PID) Process: | (3028) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\HomeWelcome |
| Operation: | write | Name: | bIsAcrobatUpdated |
Value: 1 | |||
| (PID) Process: | (3028) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\HomeWelcomeFirstMileReader |
| Operation: | write | Name: | iCardCountShown |
Value: 2 | |||
| (PID) Process: | (3028) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\FTEDialog |
| Operation: | delete value | Name: | iLastCardShown |
Value: 0 | |||
| (PID) Process: | (2952) AcroRd32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3028) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\SessionManagement |
| Operation: | write | Name: | bNormalExit |
Value: 0 | |||
| (PID) Process: | (3028) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\SessionManagement\cWindowsCurrent\cWin0 |
| Operation: | write | Name: | iTabCount |
Value: 0 | |||
| (PID) Process: | (3028) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\SessionManagement\cWindowsCurrent |
| Operation: | write | Name: | iWinCount |
Value: 1 | |||
Executable files
3
Suspicious files
359
Text files
176
Unknown types
35
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3732 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\4a0e94571d979b3c_0 | binary | |
MD5:— | SHA256:— | |||
| 3732 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\aba6710fde0876af_0 | binary | |
MD5:— | SHA256:— | |||
| 3732 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\bba29d2e6197e2f4_0 | binary | |
MD5:— | SHA256:— | |||
| 3732 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\92c56fa2a6c4d5ba_0 | binary | |
MD5:— | SHA256:— | |||
| 3732 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\8c84d92a9dbce3e0_0 | binary | |
MD5:— | SHA256:— | |||
| 3732 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\fd17b2d8331c91e8_0 | binary | |
MD5:— | SHA256:— | |||
| 3732 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\8e417e79df3bf0e9_0 | binary | |
MD5:— | SHA256:— | |||
| 3732 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\8c159cc5880890bc_0 | binary | |
MD5:— | SHA256:— | |||
| 3732 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\0786087c3c360803_0 | binary | |
MD5:— | SHA256:— | |||
| 3732 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\72d9f526d2e2e7c8_0 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
120
TCP/UDP connections
126
DNS requests
78
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
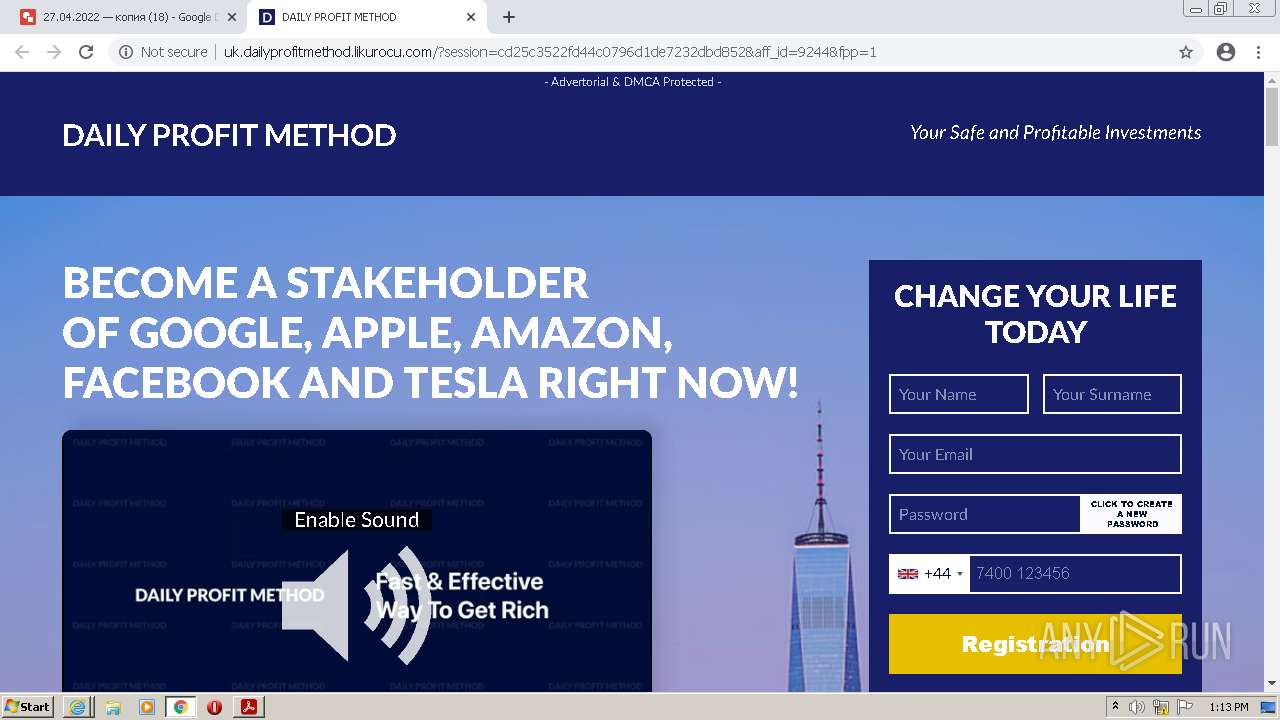
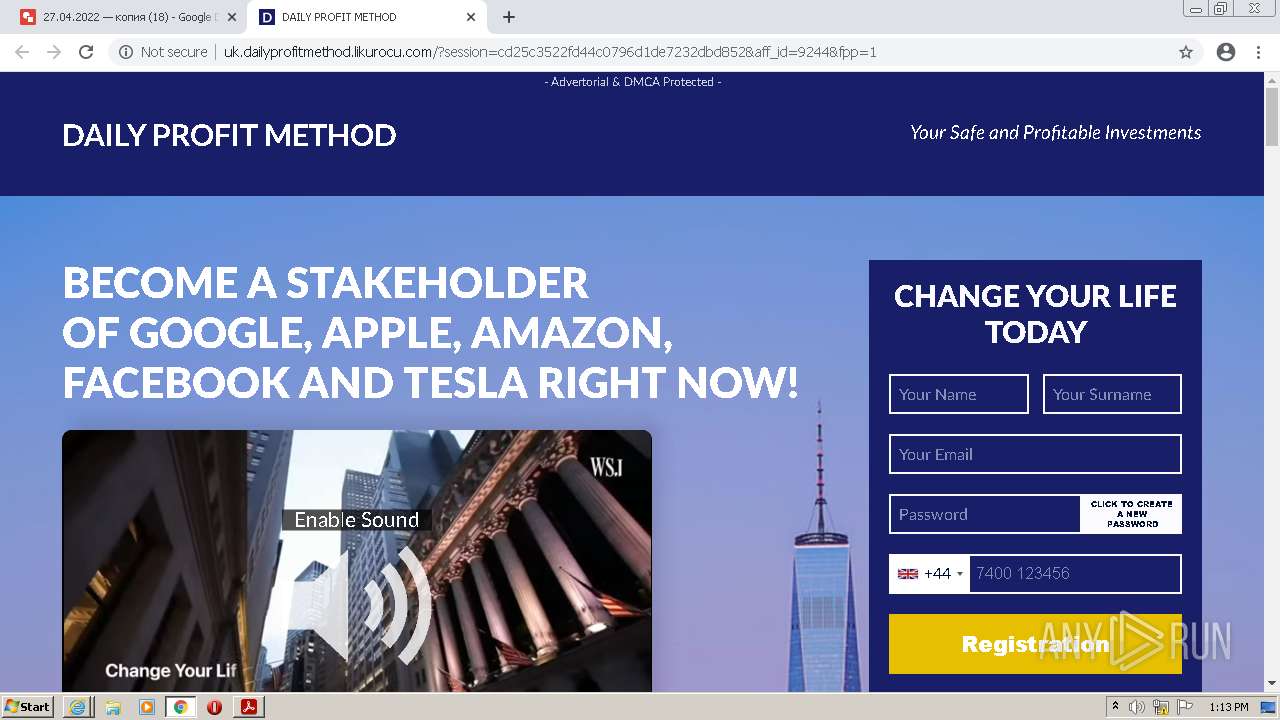
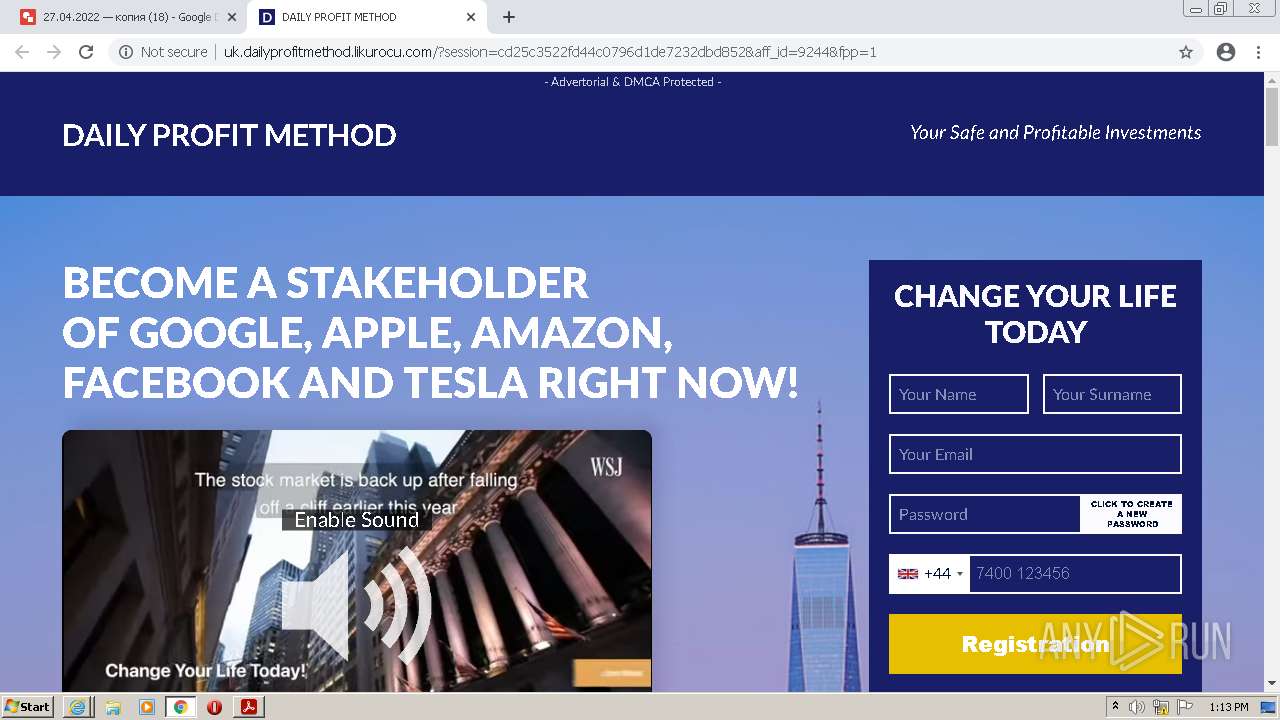
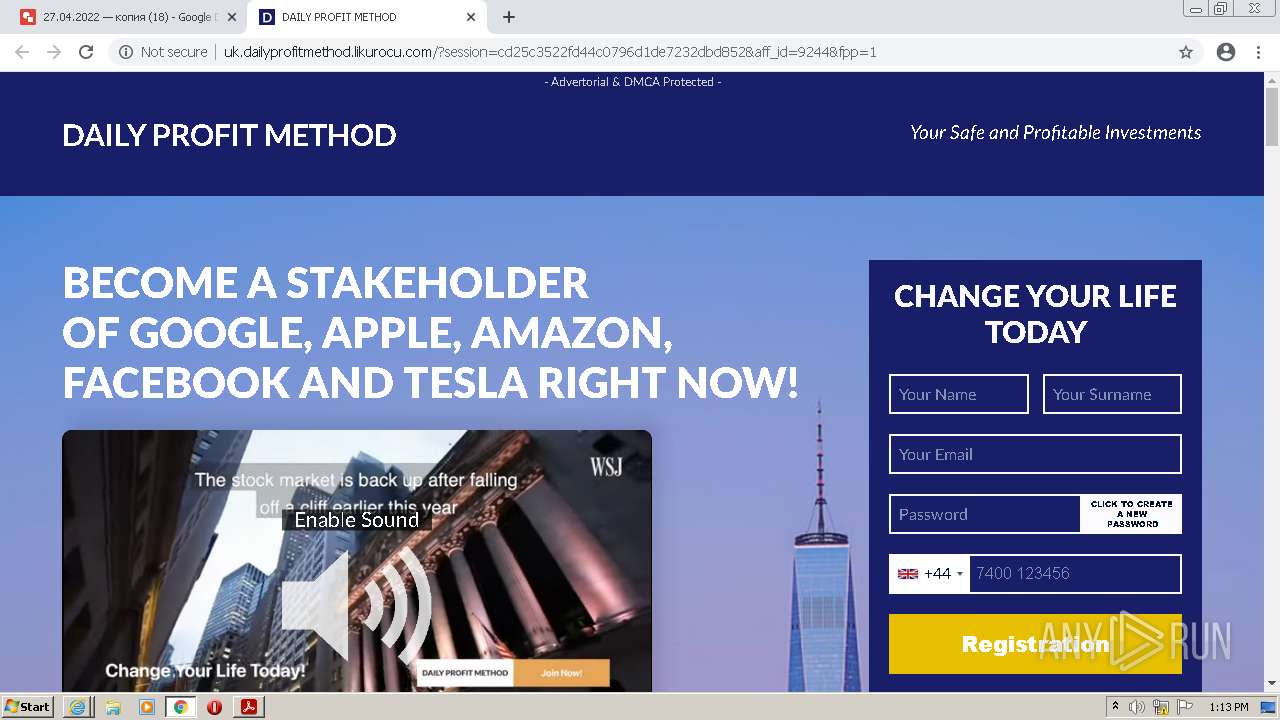
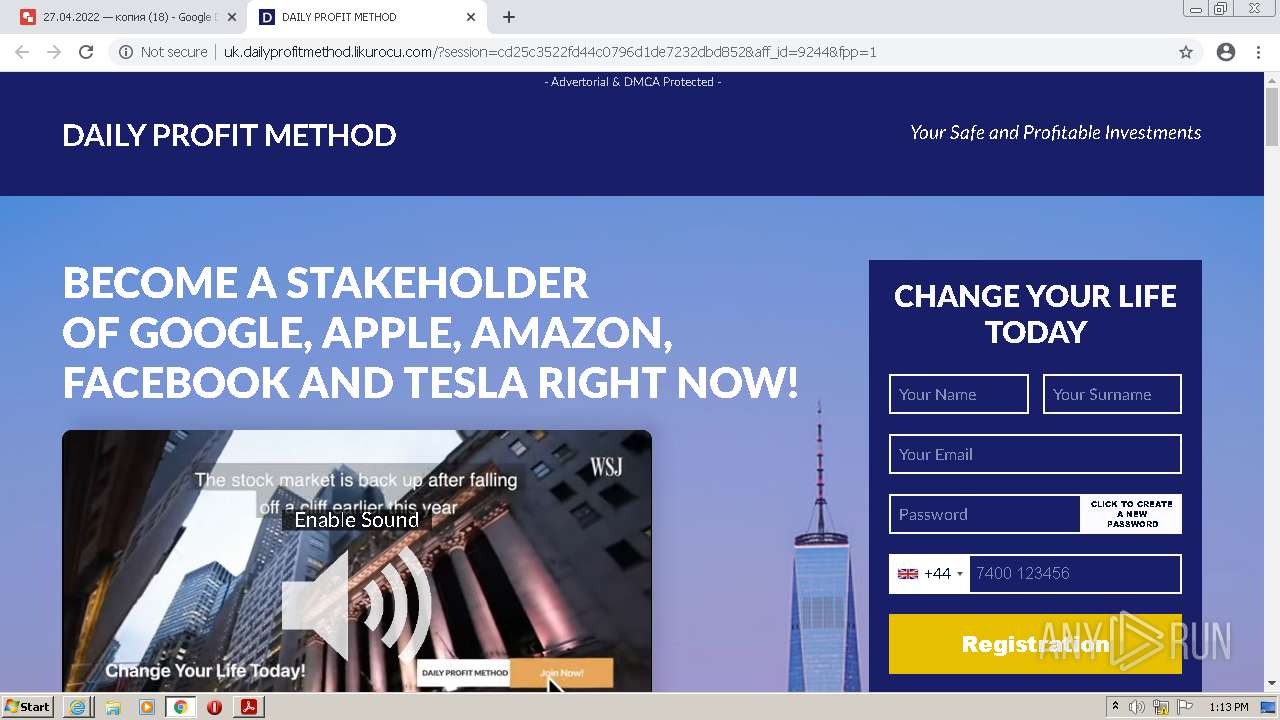
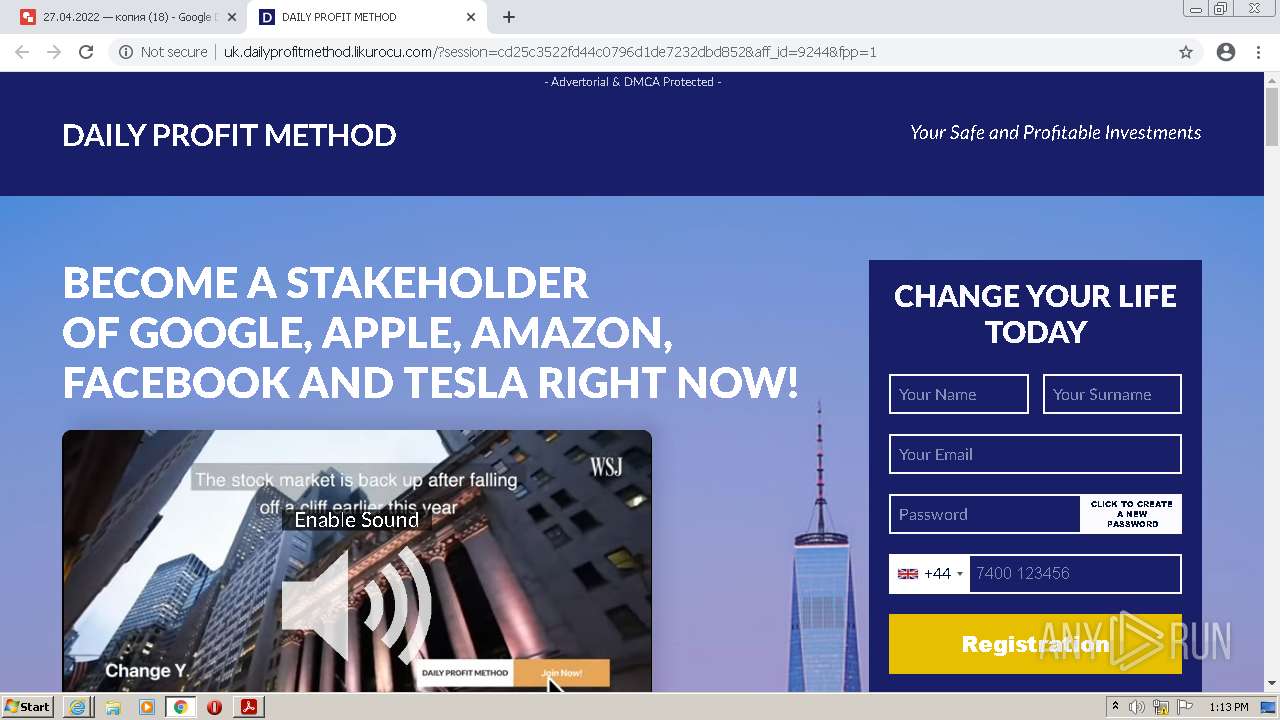
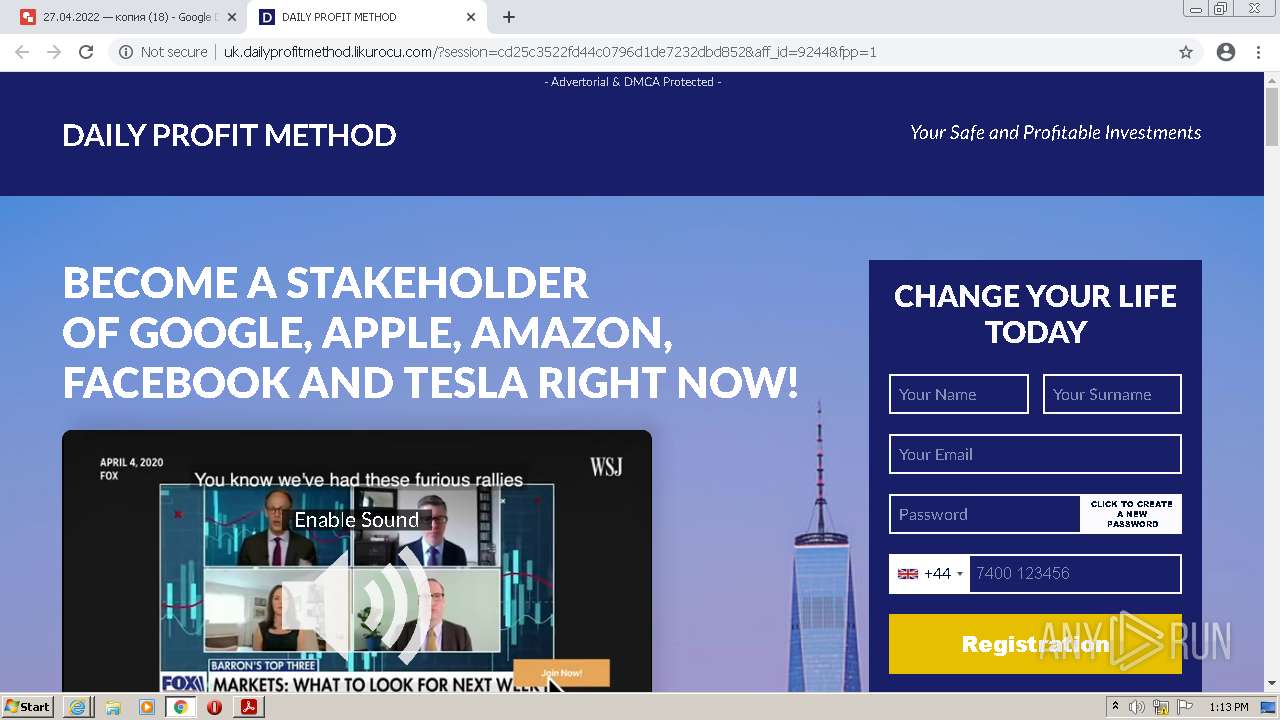
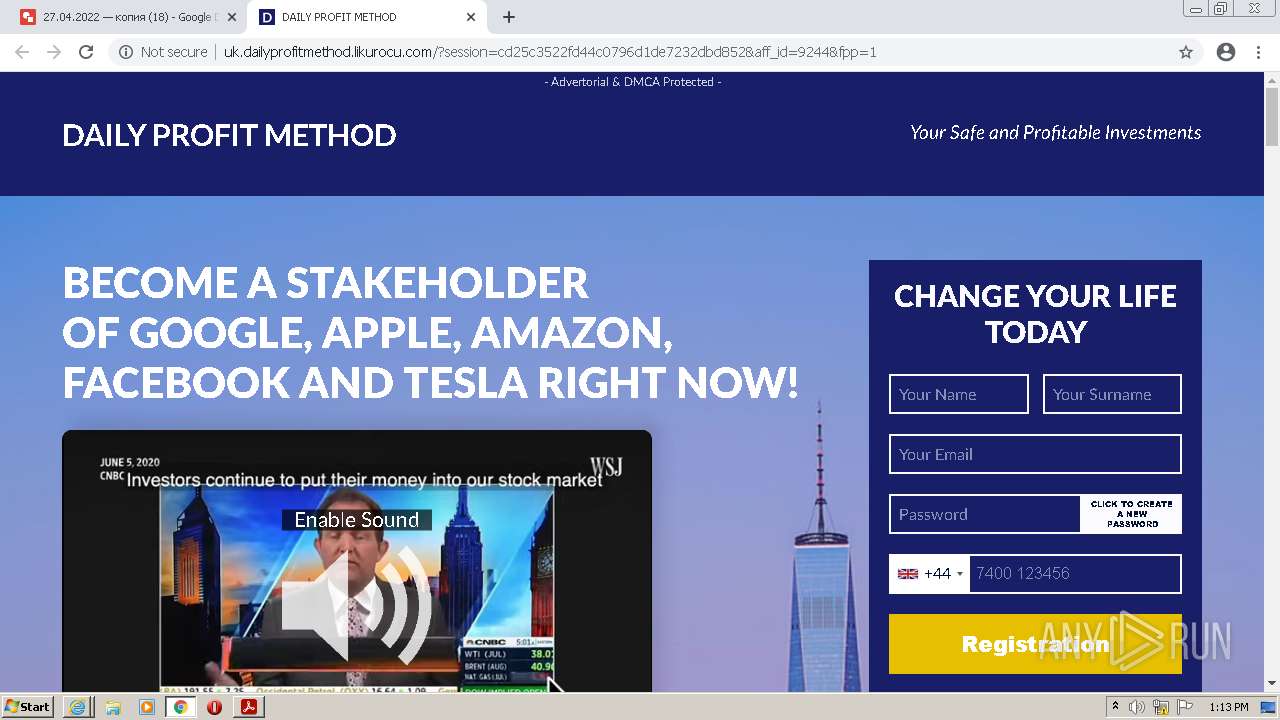
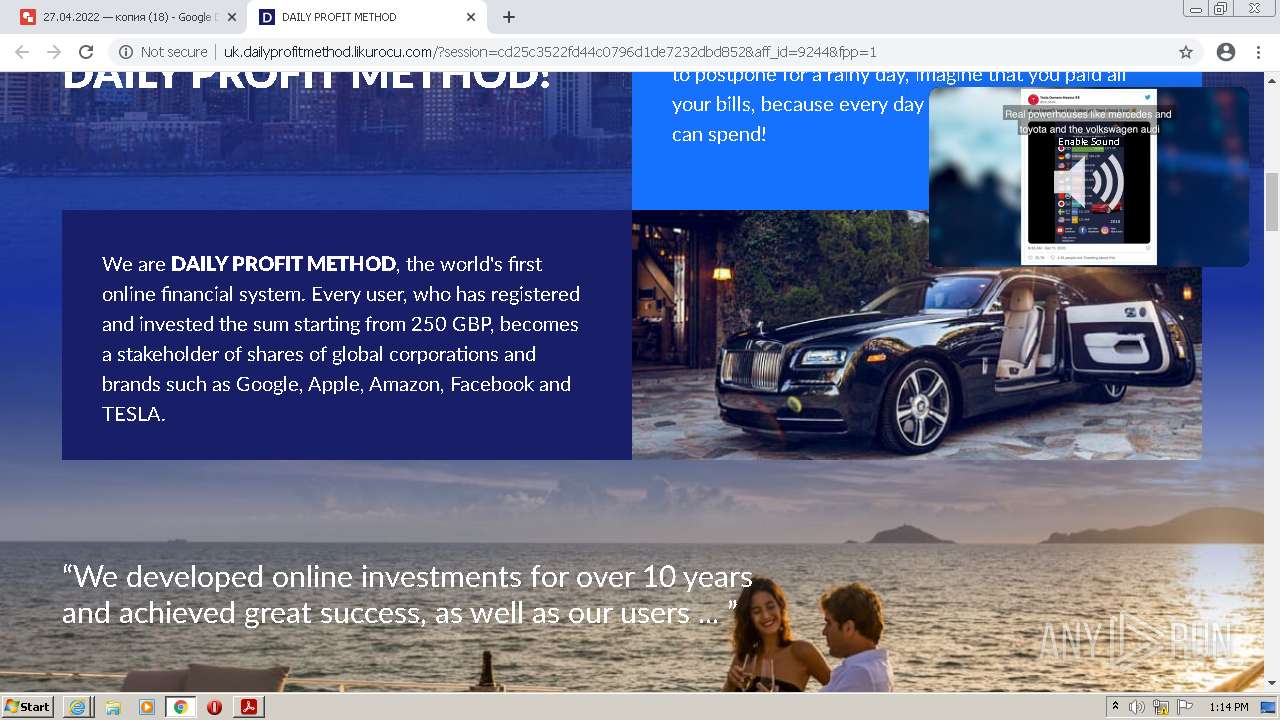
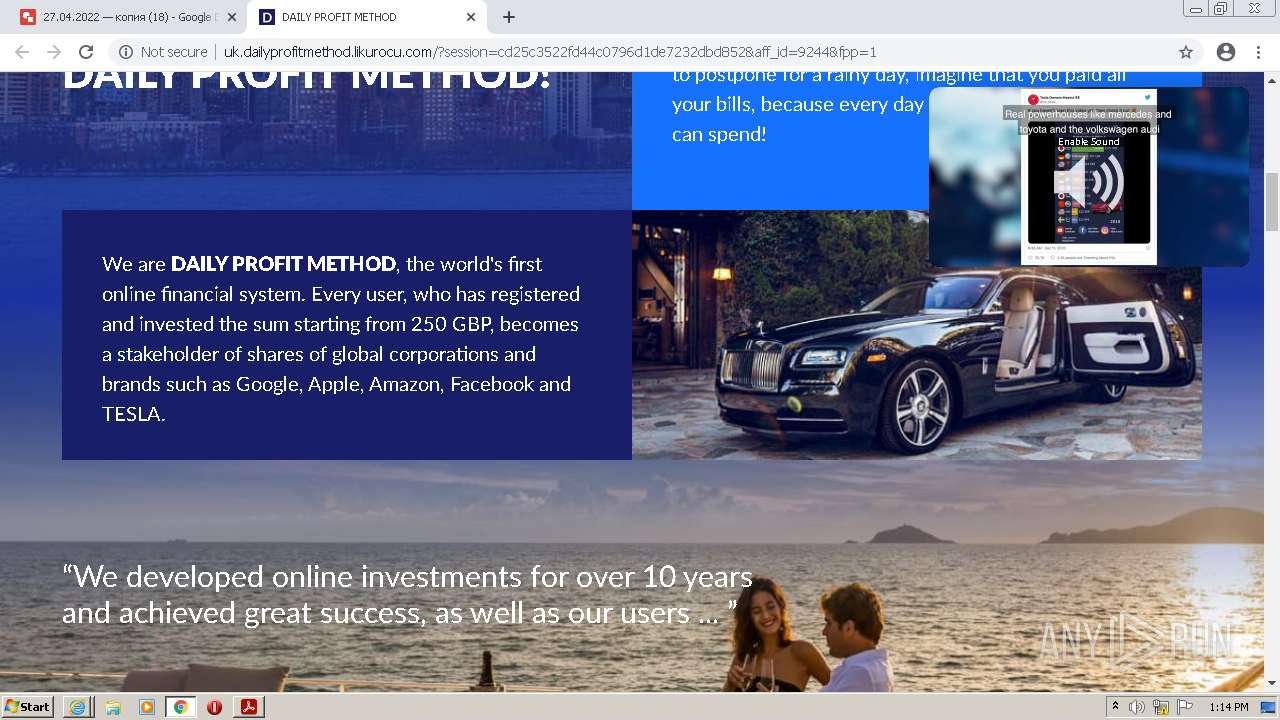
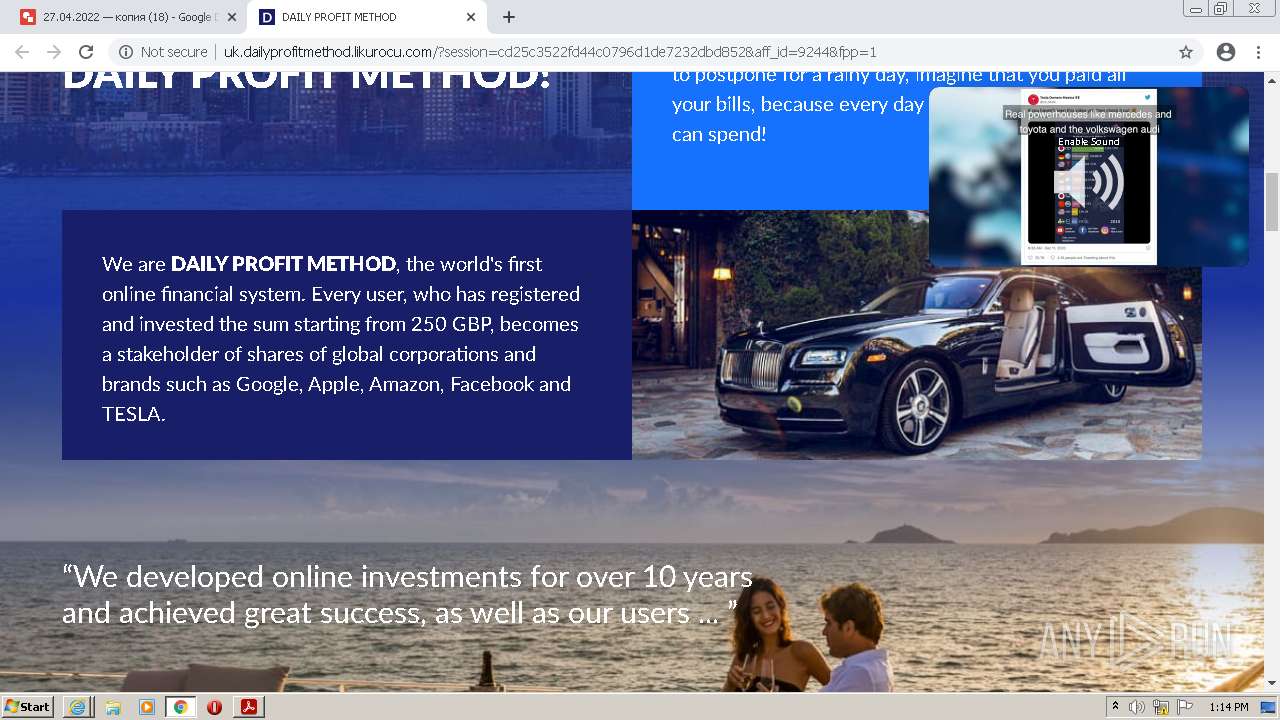
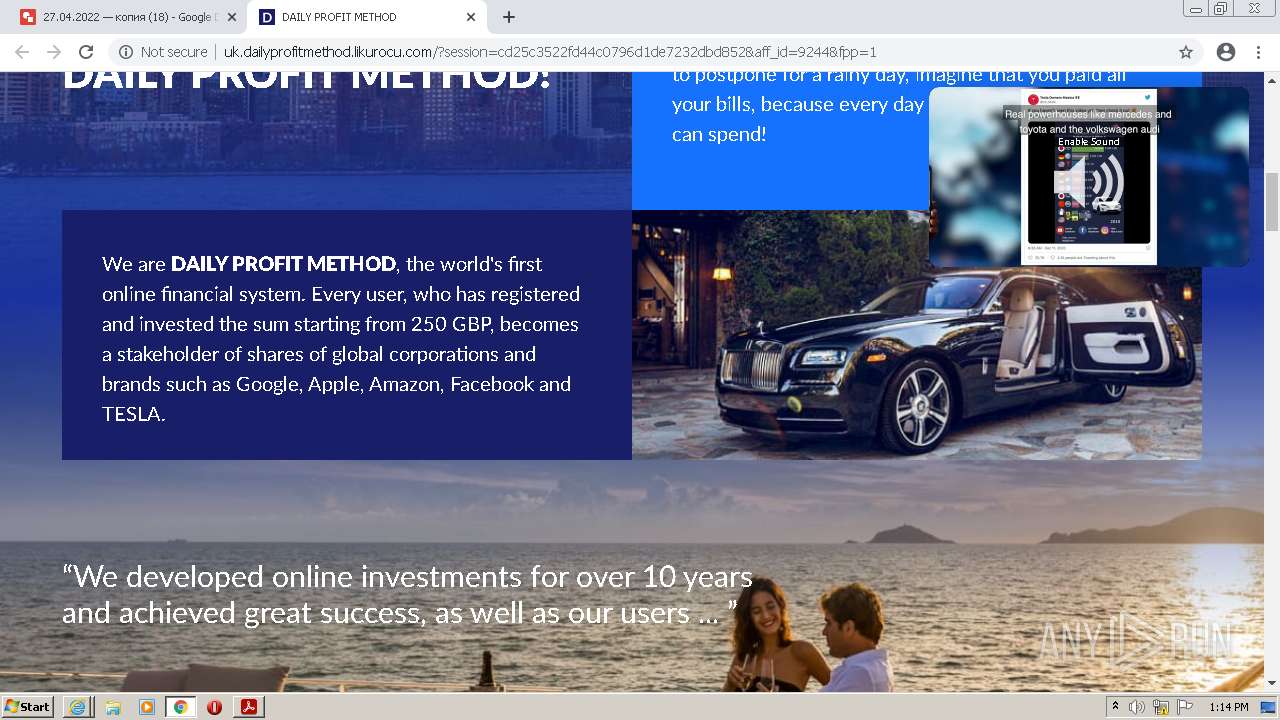
2884 | chrome.exe | GET | 302 | 104.21.48.131:80 | http://go.likurocu.com/0gbh?aff_sub=6269335421fa120001340be2 | US | — | — | suspicious |
872 | svchost.exe | HEAD | 302 | 142.250.185.206:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/adktovjj3t3n7jwiiegl5h6y3v5q_1.3.36.121/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.121_win_bxugoraqoudfswxg22hsatfdbi.crx3 | US | — | — | whitelisted |
2884 | chrome.exe | GET | 302 | 188.114.97.7:80 | http://go.helloclick6.online/sl?id=5f5b69631a6e4b18792251ff&pid=123 | US | — | — | malicious |
2640 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
2640 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
2640 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDZVQ0c3n%2F16xKL4oJJTrDj | US | der | 472 b | whitelisted |
3040 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2640 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCdmHyZTVWPdwrUMsTDPsDC | US | der | 472 b | whitelisted |
2952 | AcroRd32.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
2640 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCCPD%2BmI1IjpApTbalFlJFC | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3732 | RdrCEF.exe | 104.102.28.179:443 | geo2.adobe.com | Akamai Technologies, Inc. | US | unknown |
3732 | RdrCEF.exe | 54.227.187.23:443 | p13n.adobe.io | Amazon.com, Inc. | US | suspicious |
2952 | AcroRd32.exe | 92.123.225.66:443 | acroipm2.adobe.com | Akamai International B.V. | — | suspicious |
2952 | AcroRd32.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3040 | iexplore.exe | 13.107.21.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
872 | svchost.exe | 184.30.20.134:443 | armmf.adobe.com | GTT Communications Inc. | US | suspicious |
3040 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
872 | svchost.exe | 92.123.225.67:443 | acroipm2.adobe.com | Akamai International B.V. | — | malicious |
2640 | iexplore.exe | 142.250.186.67:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3320 | AdobeARM.exe | 92.123.225.67:443 | acroipm2.adobe.com | Akamai International B.V. | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
armmf.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
docs.google.com |
| shared |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
872 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |