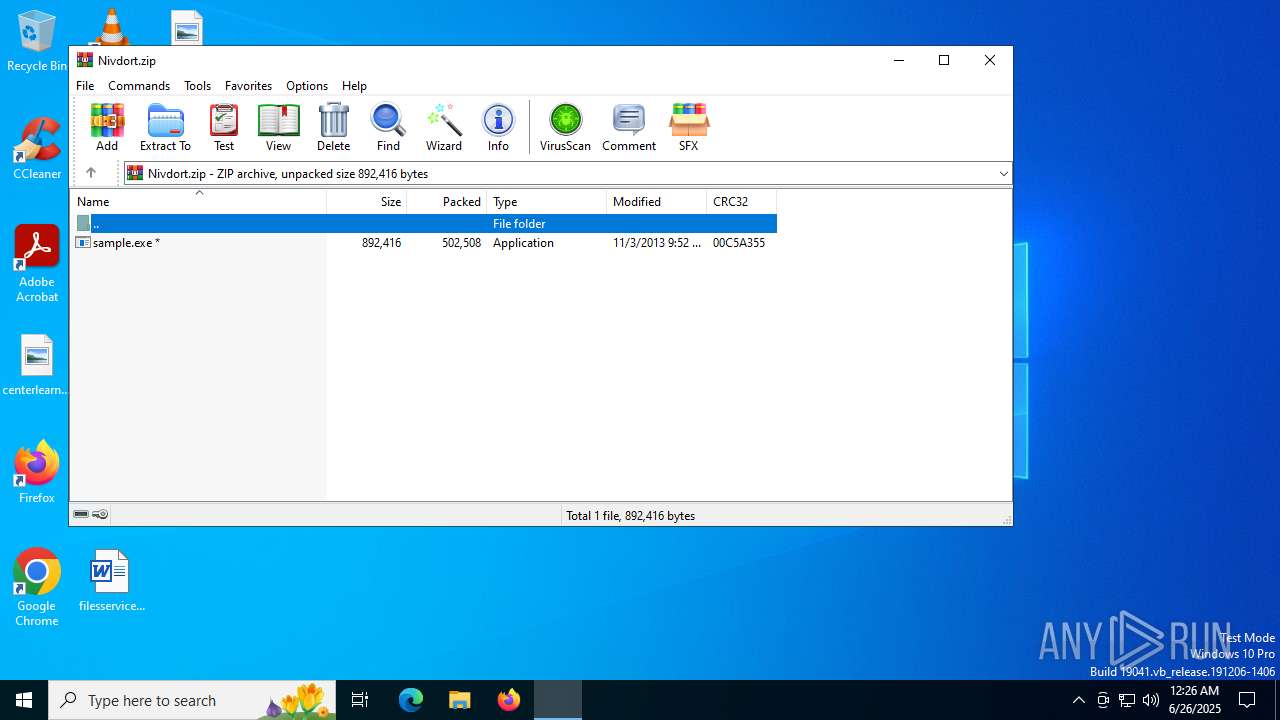
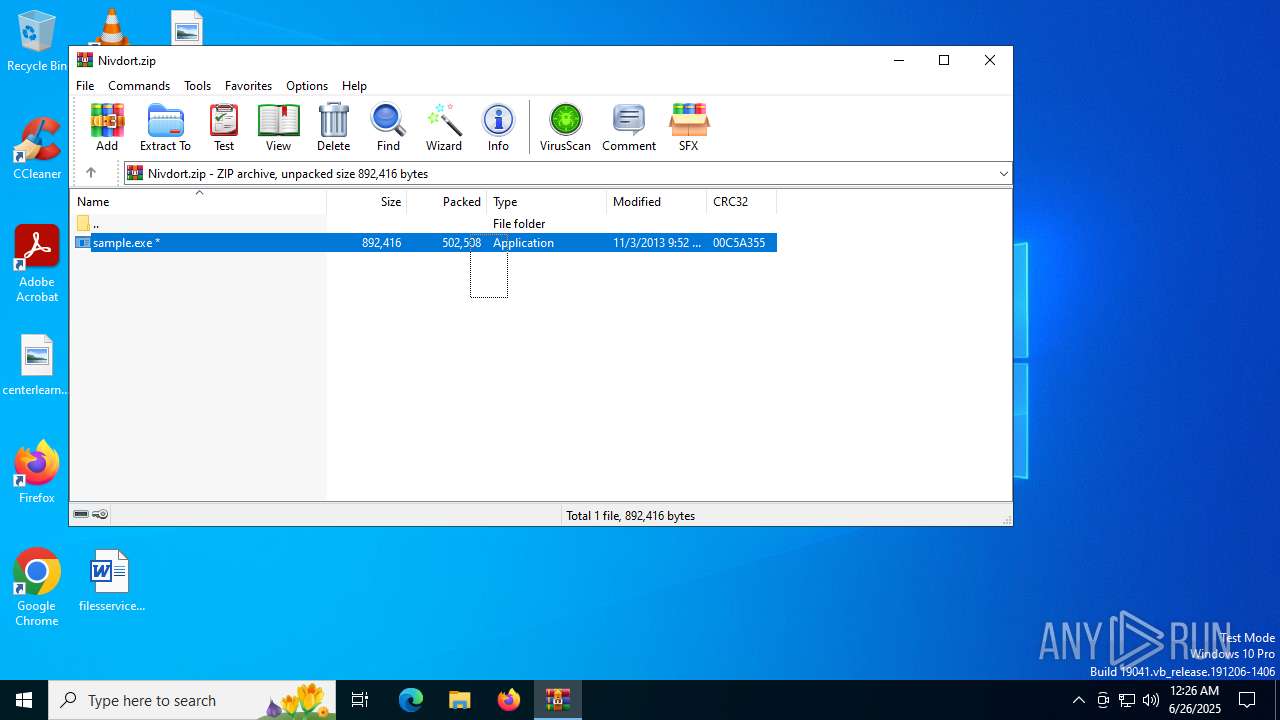
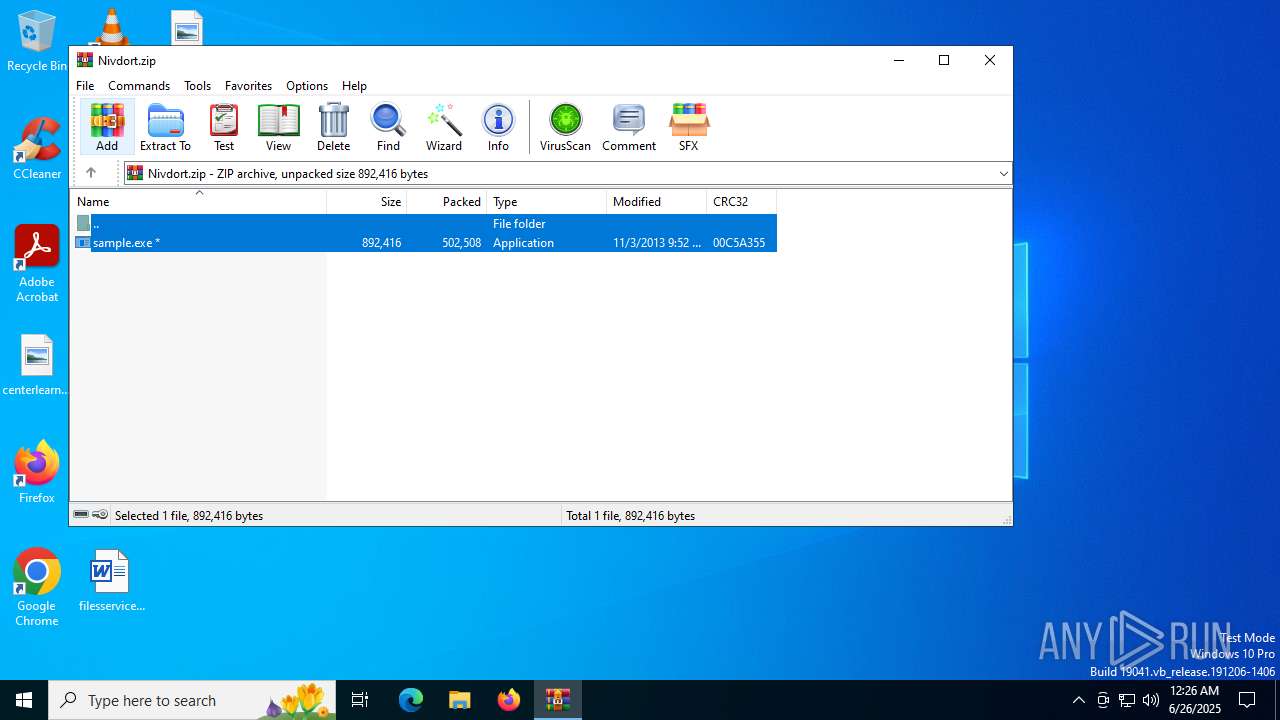
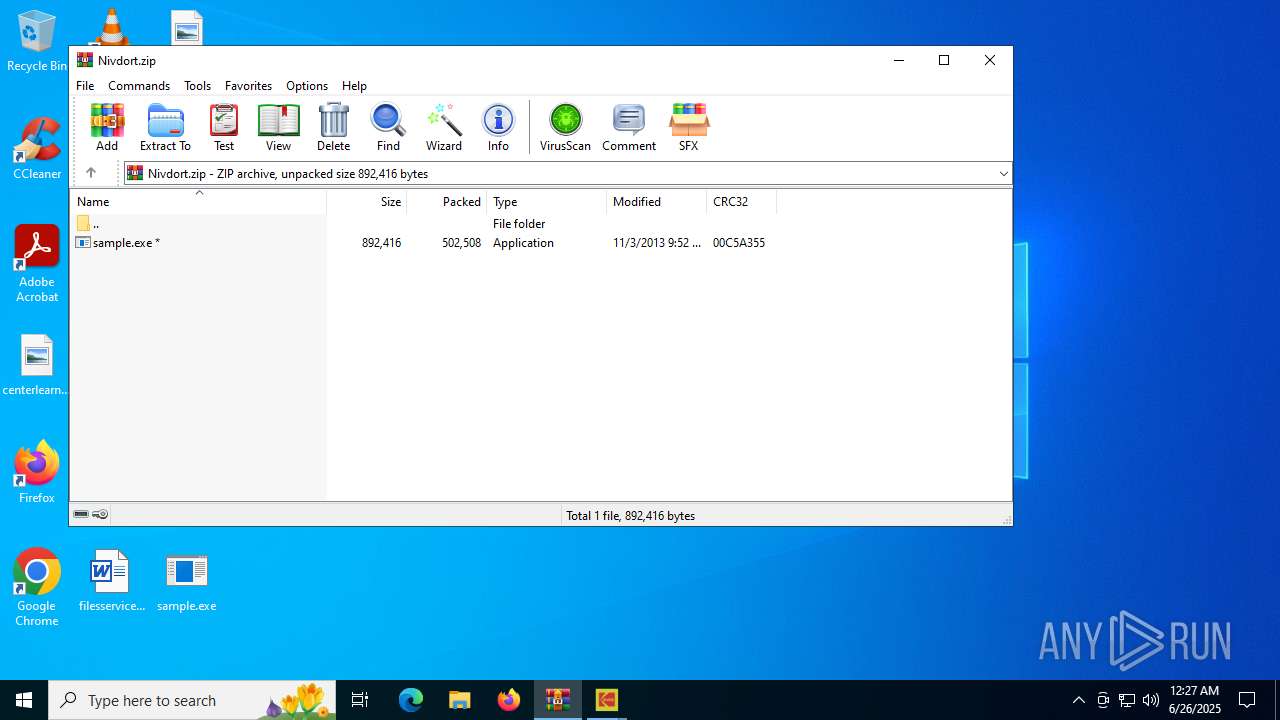
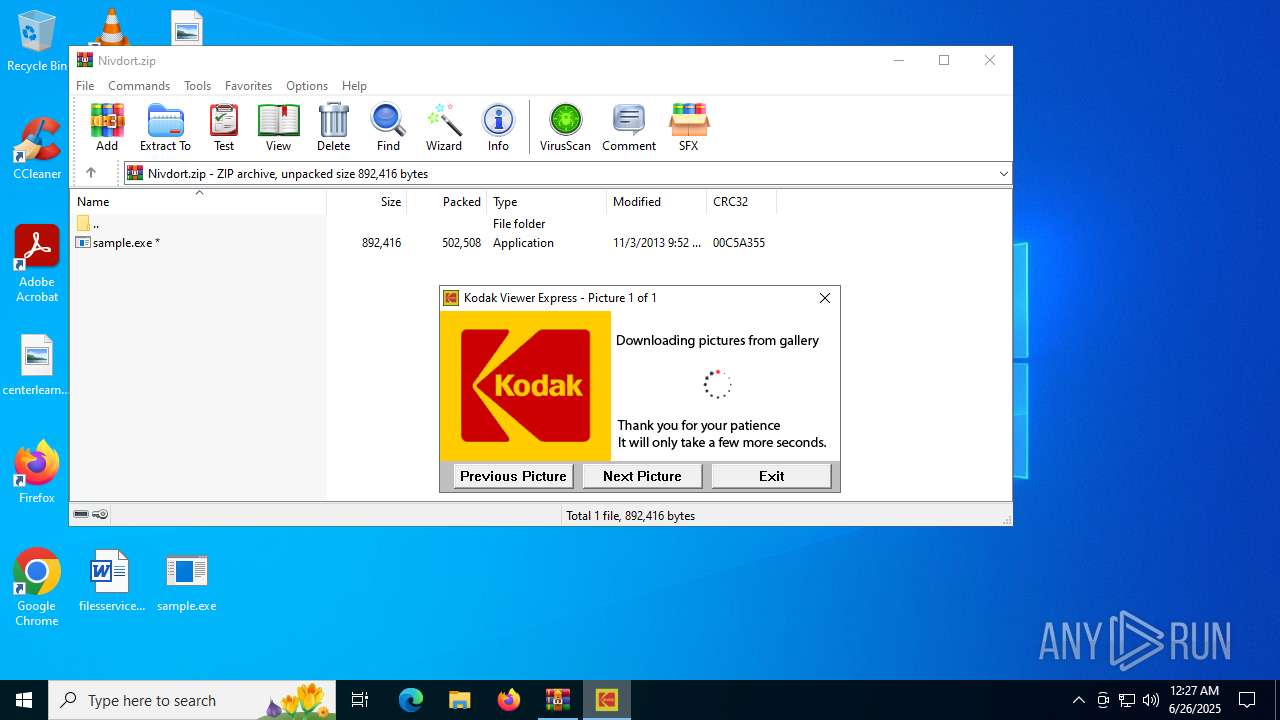
| File name: | Nivdort.zip |
| Full analysis: | https://app.any.run/tasks/733b9022-5576-4d47-9020-e585030f91d0 |
| Verdict: | Malicious activity |
| Analysis date: | June 26, 2025, 00:26:47 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 2CF9704B9AD48C05501F372A26D14636 |
| SHA1: | 1E3900F7603A549D034923290AF27E63E8E26F2A |
| SHA256: | 3FBDEDE25A0EB245357501033B64ADCD9380E592F386EF05748CA3D9B42910AF |
| SSDEEP: | 12288:0dMUnJ5CSMFUB9OvWVLn+majhquqCkVY63Vd5z3K4RqZuRhzM:7UnvnL+malqseYYVDFAuR6 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4788)
Changes the autorun value in the registry
- lowcvzx3tdygxruduobu.exe (PID: 7448)
- lowcvzx43sygxruduobu.exe (PID: 9828)
Create files in the Startup directory
- lowcvzx3tdygxruduobu.exe (PID: 7448)
SUSPICIOUS
The process checks if it is being run in the virtual environment
- WinRAR.exe (PID: 4788)
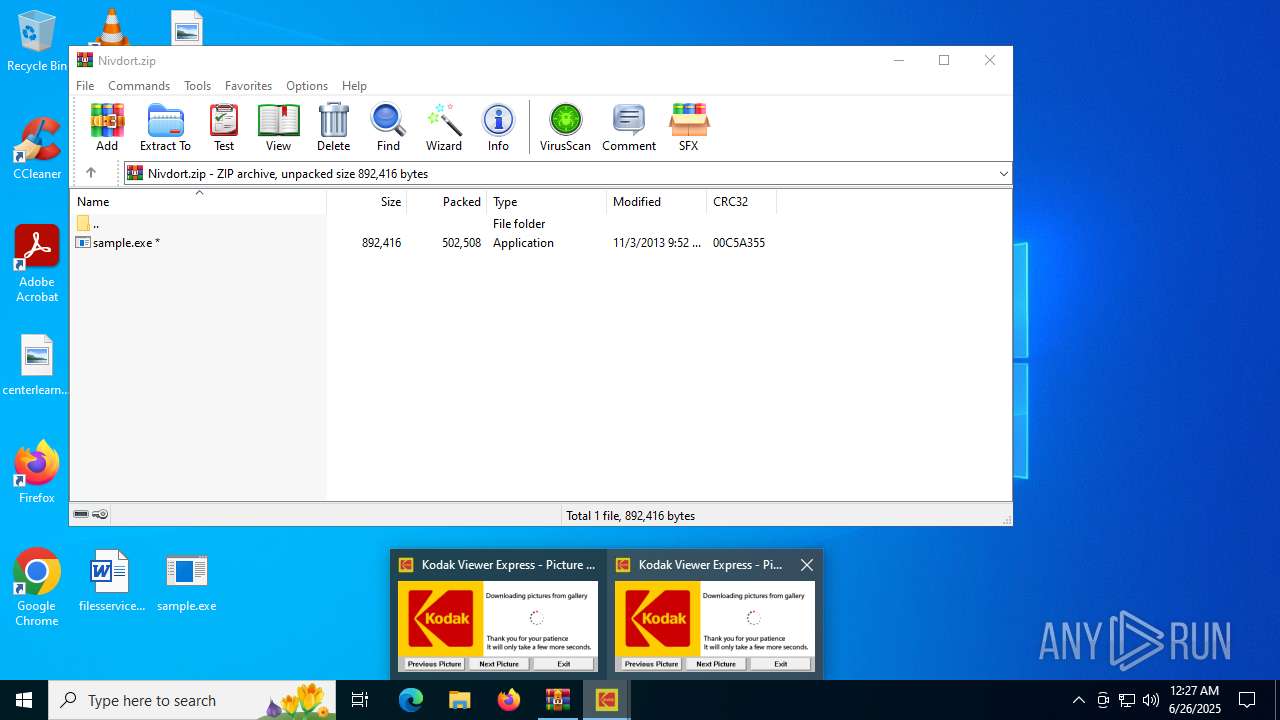
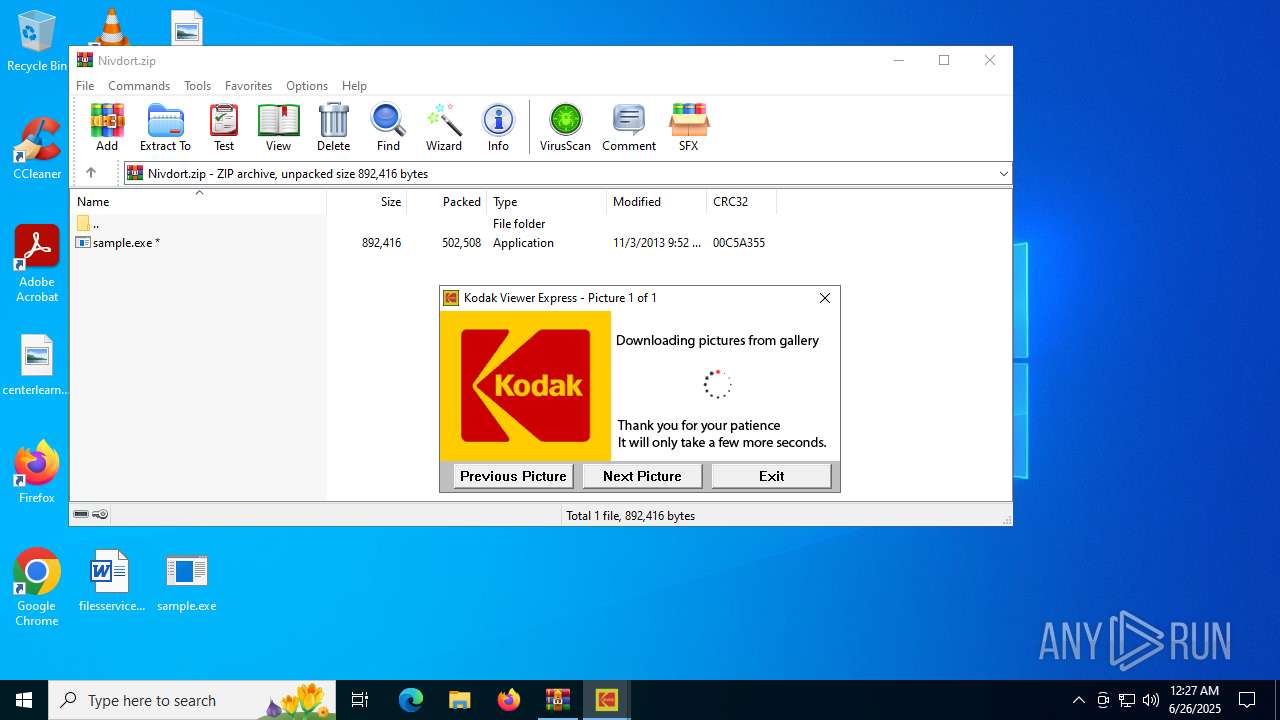
Executable content was dropped or overwritten
- sample.exe (PID: 6004)
- sample.exe (PID: 8652)
- lowcvzx3tdygxruduobu.exe (PID: 7448)
- tdtxjtat.exe (PID: 11172)
Starts itself from another location
- sample.exe (PID: 6004)
- sample.exe (PID: 8652)
- tdtxjtat.exe (PID: 11172)
- lowcvzx3tdygxruduobu.exe (PID: 7448)
- lowcvzx43sygxruduobu.exe (PID: 9828)
Reads security settings of Internet Explorer
- lowcvzx3tdygxruduobu.exe (PID: 7448)
- lowcvzx43sygxruduobu.exe (PID: 9828)
There is functionality for taking screenshot (YARA)
- sample.exe (PID: 6004)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4788)
Checks supported languages
- sample.exe (PID: 6004)
- lowcvzx3tdygxruduobu.exe (PID: 7448)
- sample.exe (PID: 8652)
- lowcvzx43sygxruduobu.exe (PID: 9828)
- tdtxjtat.exe (PID: 11172)
- ylxgpkkuiif.exe (PID: 12172)
- tdtxjtat.exe (PID: 8540)
Manual execution by a user
- sample.exe (PID: 6004)
- sample.exe (PID: 8652)
Create files in a temporary directory
- sample.exe (PID: 6004)
- sample.exe (PID: 8652)
Creates files or folders in the user directory
- sample.exe (PID: 6004)
- lowcvzx3tdygxruduobu.exe (PID: 7448)
- tdtxjtat.exe (PID: 11172)
Reads the computer name
- lowcvzx3tdygxruduobu.exe (PID: 7448)
- lowcvzx43sygxruduobu.exe (PID: 9828)
- sample.exe (PID: 6004)
- sample.exe (PID: 8652)
- tdtxjtat.exe (PID: 11172)
Checks proxy server information
- lowcvzx3tdygxruduobu.exe (PID: 7448)
- lowcvzx43sygxruduobu.exe (PID: 9828)
- slui.exe (PID: 10148)
Launching a file from a Registry key
- lowcvzx3tdygxruduobu.exe (PID: 7448)
- lowcvzx43sygxruduobu.exe (PID: 9828)
Reads the machine GUID from the registry
- sample.exe (PID: 6004)
- tdtxjtat.exe (PID: 11172)
- sample.exe (PID: 8652)
Launching a file from the Startup directory
- lowcvzx3tdygxruduobu.exe (PID: 7448)
Reads the software policy settings
- slui.exe (PID: 10148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2013:11:03 12:52:22 |
| ZipCRC: | 0x00c5a355 |
| ZipCompressedSize: | 502508 |
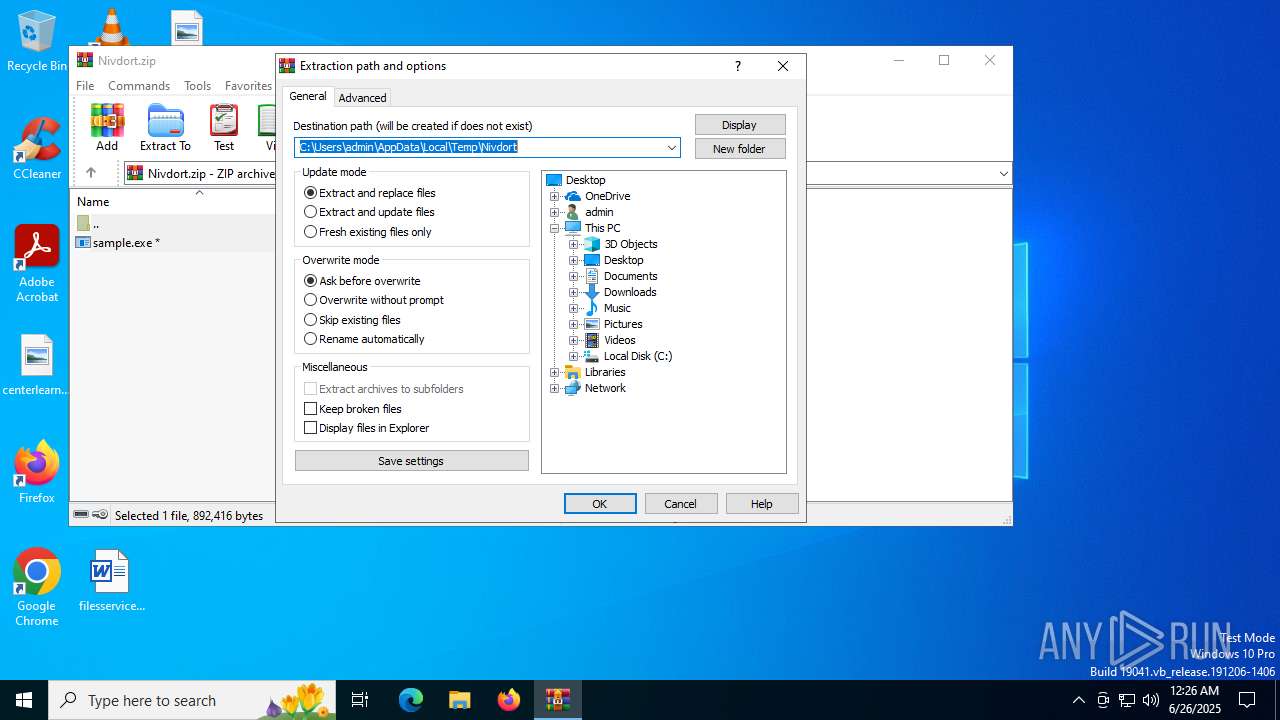
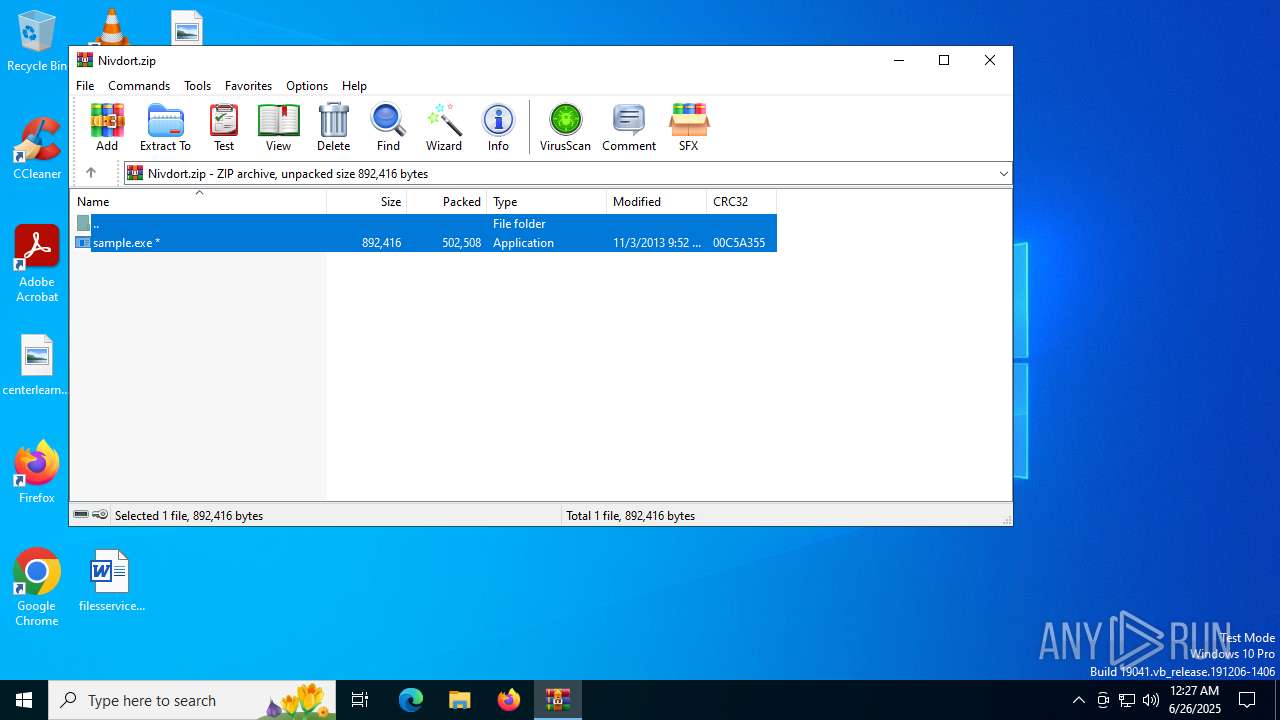
| ZipUncompressedSize: | 892416 |
| ZipFileName: | sample.exe |
Total processes
145
Monitored processes
10
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4788 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Nivdort.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6004 | "C:\Users\admin\Desktop\sample.exe" | C:\Users\admin\Desktop\sample.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7448 | "C:\Users\admin\AppData\Local\Temp\lowcvzx3tdygxruduobu.exe" | C:\Users\admin\AppData\Local\Temp\lowcvzx3tdygxruduobu.exe | sample.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 8540 | "C:\Users\admin\AppData\Local\tdtxjtat.exe" | C:\Users\admin\AppData\Local\tdtxjtat.exe | — | lowcvzx43sygxruduobu.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 8652 | "C:\Users\admin\Desktop\sample.exe" | C:\Users\admin\Desktop\sample.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 9828 | "C:\Users\admin\AppData\Local\Temp\lowcvzx43sygxruduobu.exe" | C:\Users\admin\AppData\Local\Temp\lowcvzx43sygxruduobu.exe | sample.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 10148 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 11172 | "C:\Users\admin\AppData\Local\tdtxjtat.exe" | C:\Users\admin\AppData\Local\tdtxjtat.exe | lowcvzx3tdygxruduobu.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 12172 | WATCHDOGPROC "c:\users\admin\appdata\local\tdtxjtat.exe" | C:\Users\admin\AppData\Local\ylxgpkkuiif.exe | — | tdtxjtat.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
4 143
Read events
4 116
Write events
14
Delete events
13
Modification events
| (PID) Process: | (4788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Nivdort.zip | |||
| (PID) Process: | (4788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (4788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
6
Suspicious files
3
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4788 | WinRAR.exe | C:\Users\admin\Desktop\sample.exe | executable | |
MD5:ED2CD14A28FF2D00A5CEFCF6A074AF8D | SHA256:EEA059174127860154F4DCE1A7D8995A9A5056FEBF73819D63DDADB522ED6C8F | |||
| 7448 | lowcvzx3tdygxruduobu.exe | C:\Users\admin\AppData\Local\tdtxjtat.exe | executable | |
MD5:ED2CD14A28FF2D00A5CEFCF6A074AF8D | SHA256:EEA059174127860154F4DCE1A7D8995A9A5056FEBF73819D63DDADB522ED6C8F | |||
| 7448 | lowcvzx3tdygxruduobu.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\i17fj4h8.default\user.js | text | |
MD5:8D45C1975634AC94EB3DAF829837C607 | SHA256:307BC658D9AA32983B5E988277EE5895E3006384080CCCABB47EF52CB30CE326 | |||
| 11172 | tdtxjtat.exe | C:\Users\admin\AppData\Local\ylxgpkkuiif.exe | executable | |
MD5:ED2CD14A28FF2D00A5CEFCF6A074AF8D | SHA256:EEA059174127860154F4DCE1A7D8995A9A5056FEBF73819D63DDADB522ED6C8F | |||
| 7448 | lowcvzx3tdygxruduobu.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\tdtxjtat.exe | executable | |
MD5:ED2CD14A28FF2D00A5CEFCF6A074AF8D | SHA256:EEA059174127860154F4DCE1A7D8995A9A5056FEBF73819D63DDADB522ED6C8F | |||
| 11172 | tdtxjtat.exe | C:\Users\admin\AppData\Local\mfyexntuvqd\rng | binary | |
MD5:2A92885230E214350B4FA1241229A026 | SHA256:5CDEC5D34B5E22AAA37BB0D30BE4BEA3333F71739F6517E070C46552789F6774 | |||
| 11172 | tdtxjtat.exe | C:\Users\admin\AppData\Local\mfyexntuvqd\run | text | |
MD5:F88AFA0FA241403DFD98C4A821363068 | SHA256:3EC913F1DE6E549C24261B68F8623FCD609AFCC301985D231414CBAA09E2B55E | |||
| 11172 | tdtxjtat.exe | C:\Users\admin\AppData\Local\mfyexntuvqd\cfg | binary | |
MD5:24F78552E61BD14FE3DC14B95C46E15C | SHA256:16D34B557EBC7E1B924E814C5E51A721CBF68AB360F22D94E68FCE6EE1DF2274 | |||
| 6004 | sample.exe | C:\Users\admin\AppData\Local\mfyexntuvqd\tst | text | |
MD5:D9E0D258DF86C6859951B803FA0E539C | SHA256:E71EB9E1B484BED5DC20E32ACF079F979AEC46863078331771912423E08B564E | |||
| 6004 | sample.exe | C:\Users\admin\AppData\Local\Temp\lowcvzx3tdygxruduobu.exe | executable | |
MD5:ED2CD14A28FF2D00A5CEFCF6A074AF8D | SHA256:EEA059174127860154F4DCE1A7D8995A9A5056FEBF73819D63DDADB522ED6C8F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
32
DNS requests
119
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5444 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6004 | sample.exe | GET | 403 | 75.2.18.233:80 | http://offercross.net/forum/search.php?method=validate&mode=my&email=davis447@comcast.net&lici=auto_000860&ver=013 | unknown | — | — | unknown |
6004 | sample.exe | GET | 200 | 34.229.166.50:80 | http://hangshade.net/forum/search.php?method=validate&mode=my&email=davis447@comcast.net&lici=auto_000860&ver=013 | unknown | — | — | unknown |
8652 | sample.exe | GET | 403 | 75.2.18.233:80 | http://offercross.net/forum/search.php?method=validate&mode=my&email=davis447@comcast.net&lici=auto_000860&ver=013 | unknown | — | — | unknown |
8652 | sample.exe | GET | 200 | 34.229.166.50:80 | http://hangshade.net/forum/search.php?method=validate&mode=my&email=davis447@comcast.net&lici=auto_000860&ver=013 | unknown | — | — | unknown |
8652 | sample.exe | GET | 200 | 52.27.79.221:80 | http://wishthrew.net/forum/search.php?method=validate&mode=my&email=davis447@comcast.net&lici=auto_000860&ver=013 | unknown | — | — | unknown |
6004 | sample.exe | GET | 200 | 52.27.79.221:80 | http://wishthrew.net/forum/search.php?method=validate&mode=my&email=davis447@comcast.net&lici=auto_000860&ver=013 | unknown | — | — | unknown |
9960 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6788 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5444 | svchost.exe | 40.126.31.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5444 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
elementarimagine.com |
| unknown |
mojoguia.com |
| unknown |
pengthecon.com |
| unknown |
themorrefk.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |