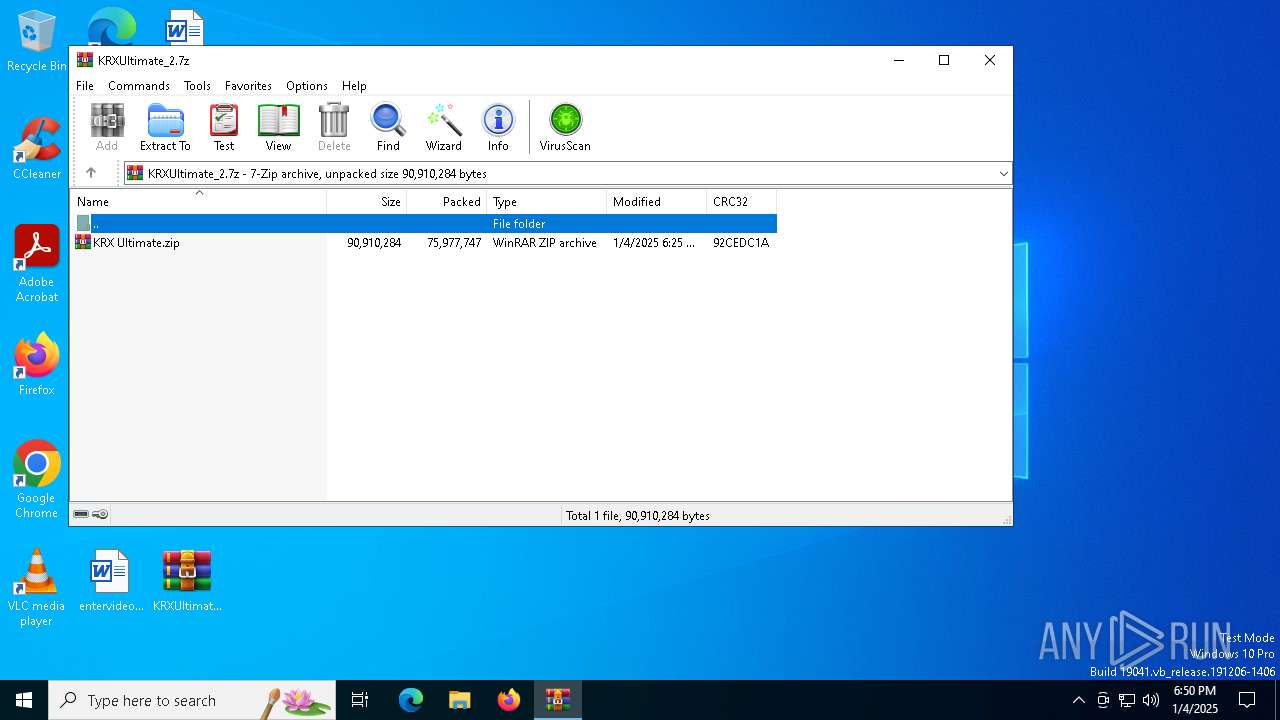
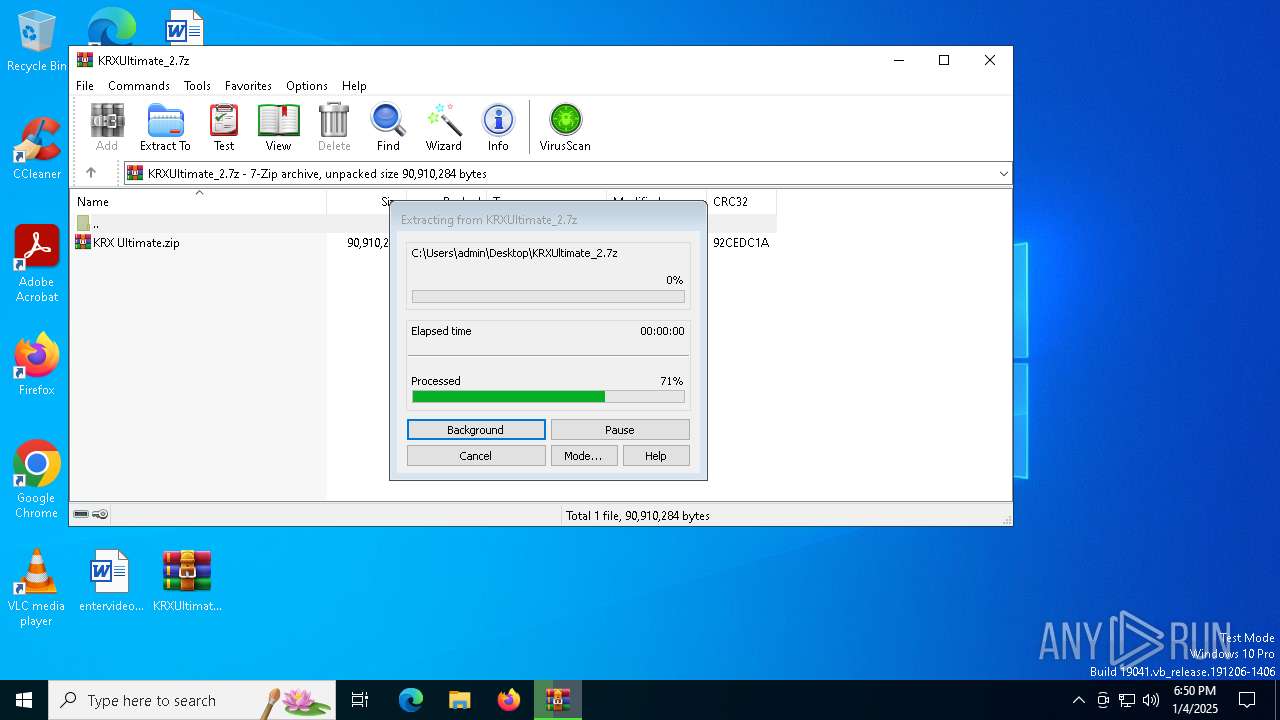
| File name: | KRXUltimate_2.7z |
| Full analysis: | https://app.any.run/tasks/bc6a27b2-d6dc-4abc-89bd-814ad68b4bb4 |
| Verdict: | Malicious activity |
| Analysis date: | January 04, 2025, 18:49:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | A564F4F040CA2F4C882B7C257A9C9F82 |
| SHA1: | 94E3DF16530D8897A1F24DE2B5F2B1C16EDE85FE |
| SHA256: | 3F9295785791D57B9BAD730D40B97598A4AAA3A89379F65BEF514D13F83F38FE |
| SSDEEP: | 393216:4fywLp1WFrnjwmfMQQFYSPhww3hdLDo9zjpvgN5DYaOrf/kLy1Oyku3aLU/bp:49pow9YS8NlobI/kL8OHghl |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5320)
SUSPICIOUS
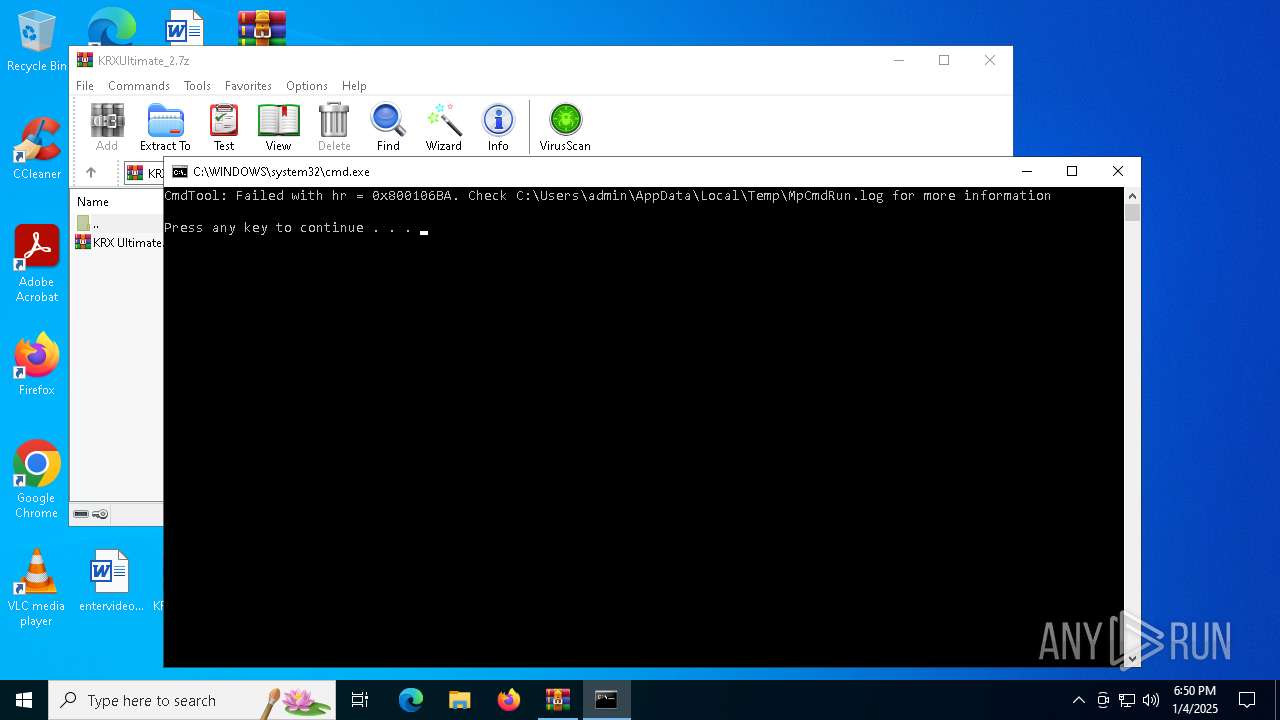
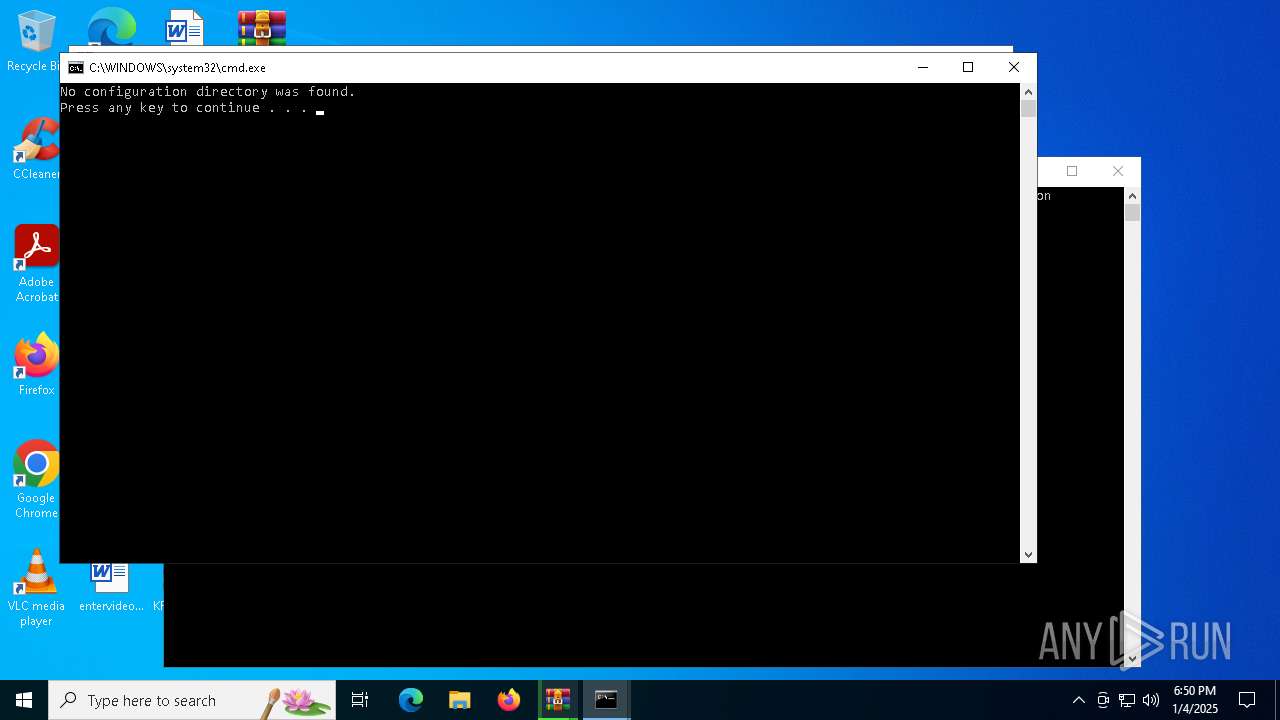
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 5320)
- WinRAR.exe (PID: 5684)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5320)
- WinRAR.exe (PID: 5684)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 5320)
- WinRAR.exe (PID: 5684)
Process drops legitimate windows executable
- WinRAR.exe (PID: 5684)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 5320)
- WinRAR.exe (PID: 5684)
Checks supported languages
- MpCmdRun.exe (PID: 3732)
- MpCmdRun.exe (PID: 4648)
Create files in a temporary directory
- MpCmdRun.exe (PID: 3732)
Reads the computer name
- MpCmdRun.exe (PID: 3732)
- MpCmdRun.exe (PID: 4648)
Manual execution by a user
- WinRAR.exe (PID: 5684)
- cmd.exe (PID: 6084)
- notepad.exe (PID: 3296)
- OpenWith.exe (PID: 5392)
- OpenWith.exe (PID: 768)
- rundll32.exe (PID: 1536)
- OpenWith.exe (PID: 2280)
- OpenWith.exe (PID: 2728)
- notepad.exe (PID: 4188)
- OpenWith.exe (PID: 2072)
- OpenWith.exe (PID: 3836)
The sample compiled with english language support
- WinRAR.exe (PID: 5684)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 3836)
- OpenWith.exe (PID: 5392)
- OpenWith.exe (PID: 2728)
- OpenWith.exe (PID: 768)
- OpenWith.exe (PID: 2280)
- OpenWith.exe (PID: 2072)
- rundll32.exe (PID: 1536)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5684)
Reads security settings of Internet Explorer
- notepad.exe (PID: 3296)
- notepad.exe (PID: 4188)
- rundll32.exe (PID: 1536)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2025:01:04 18:25:25+00:00 |
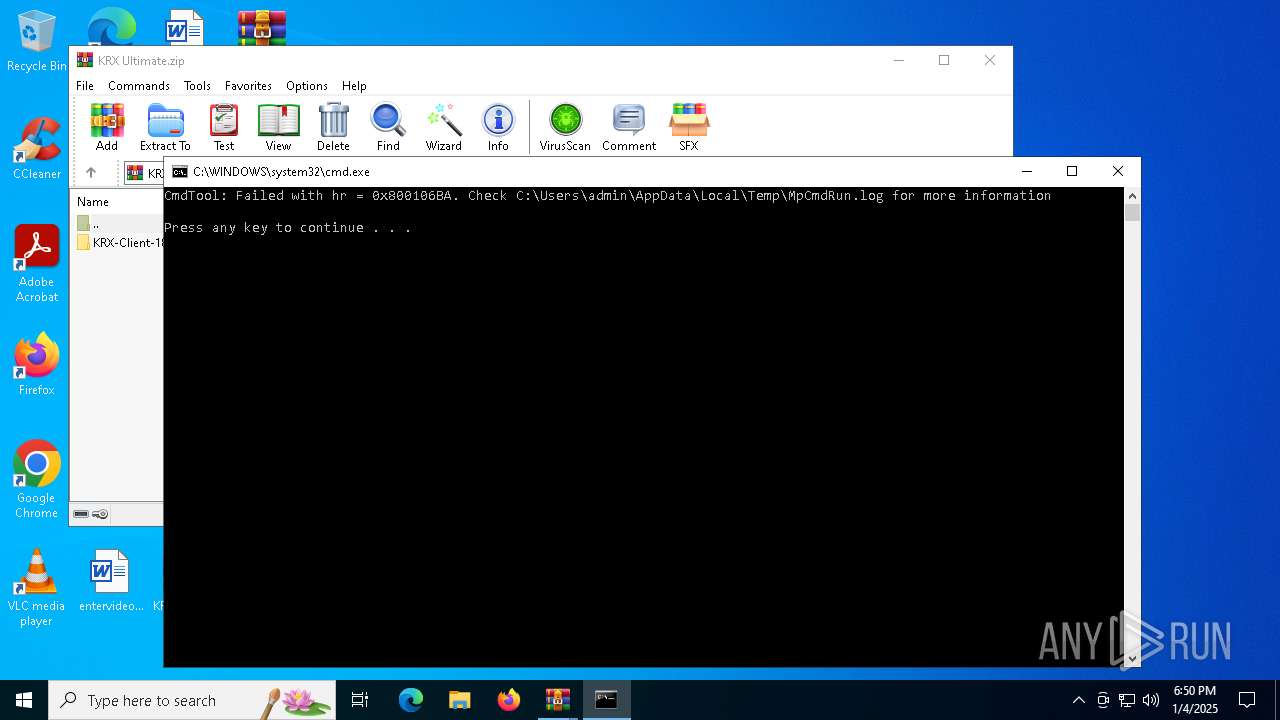
| ArchivedFileName: | KRX Ultimate.zip |
Total processes
128
Monitored processes
19
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
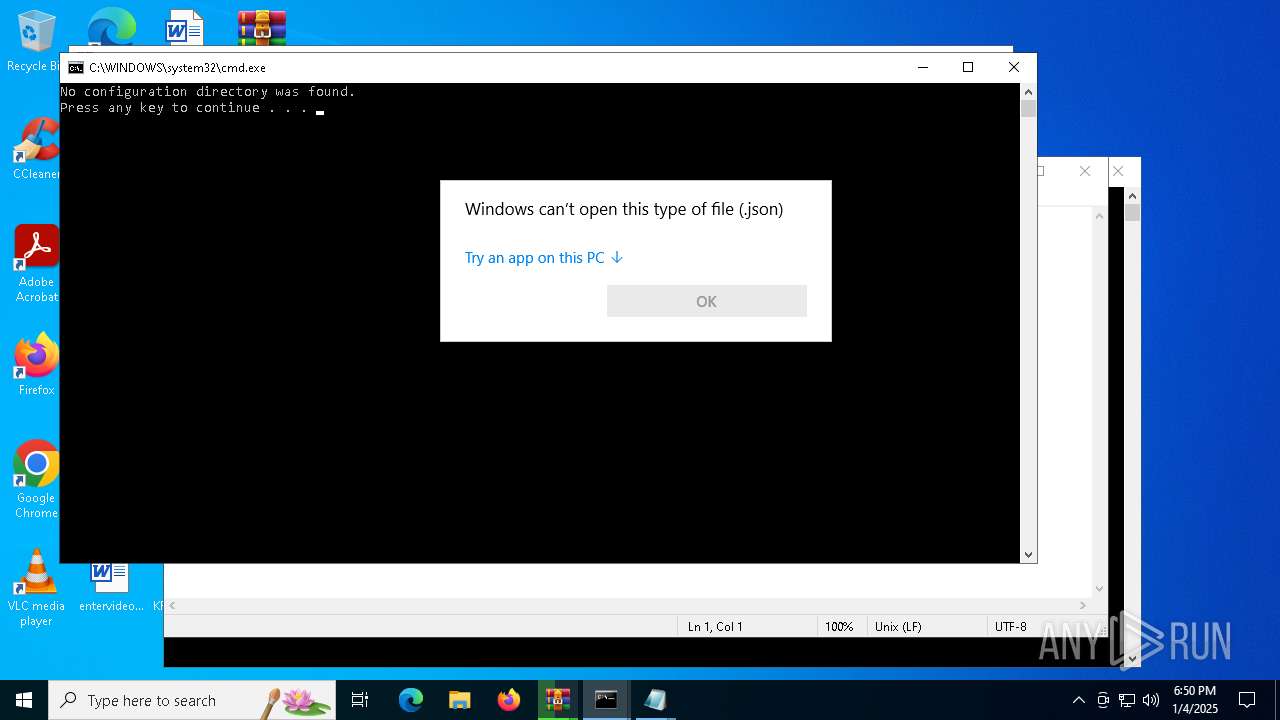
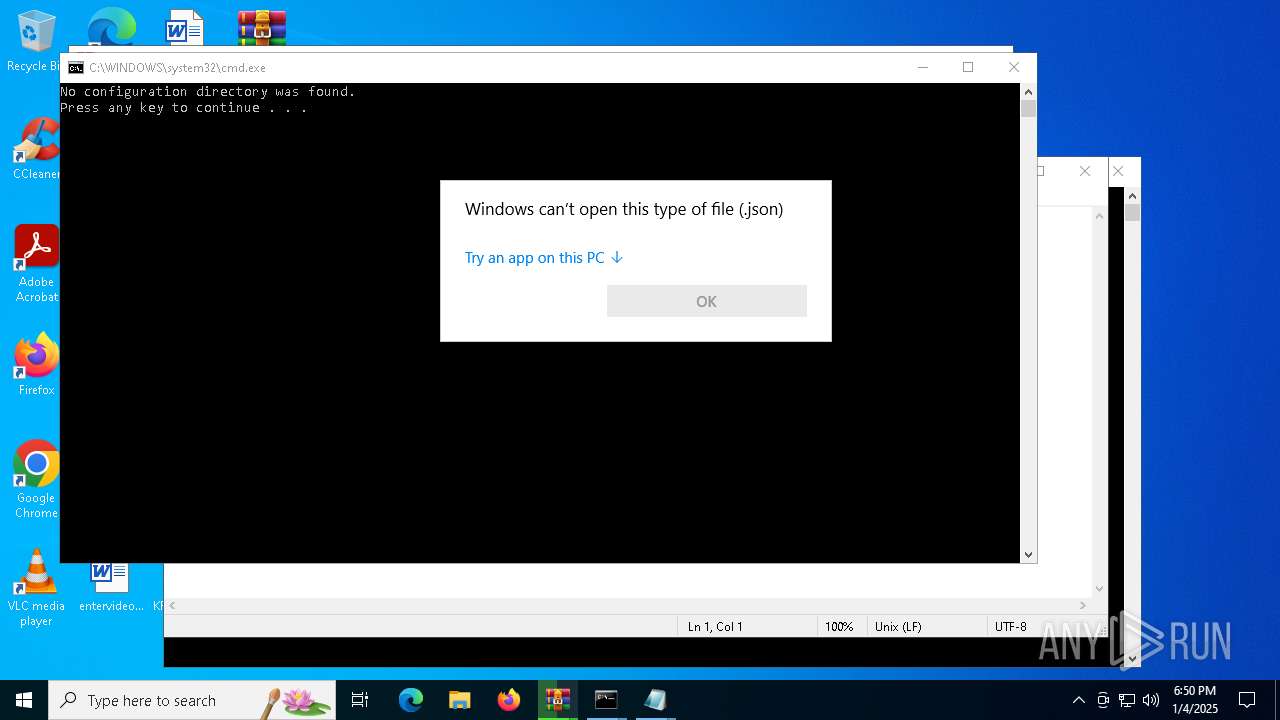
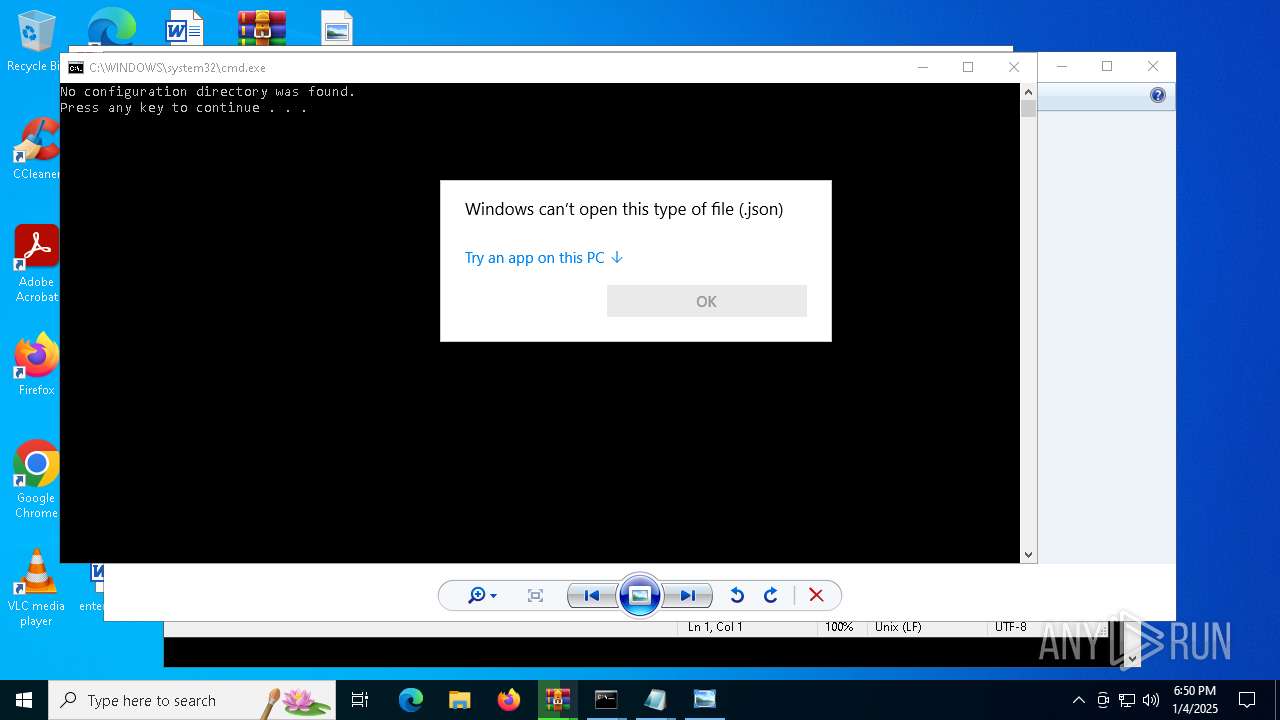
| 768 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\cammo.json | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
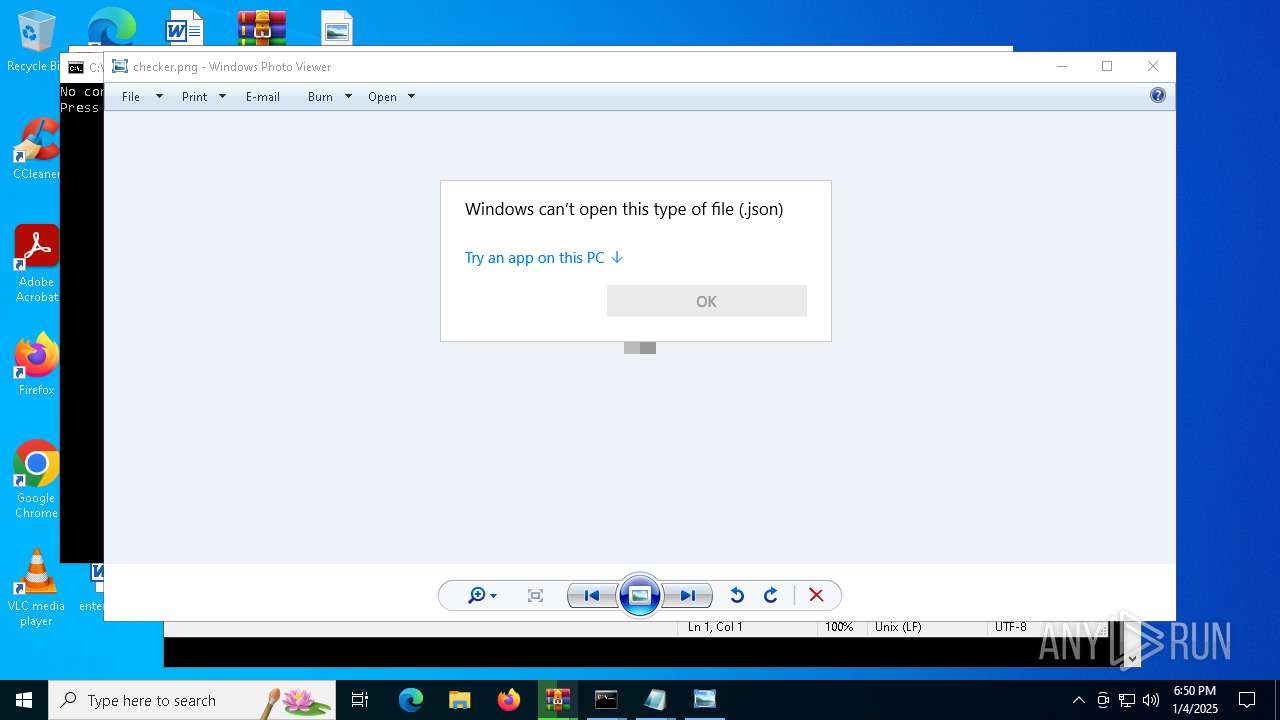
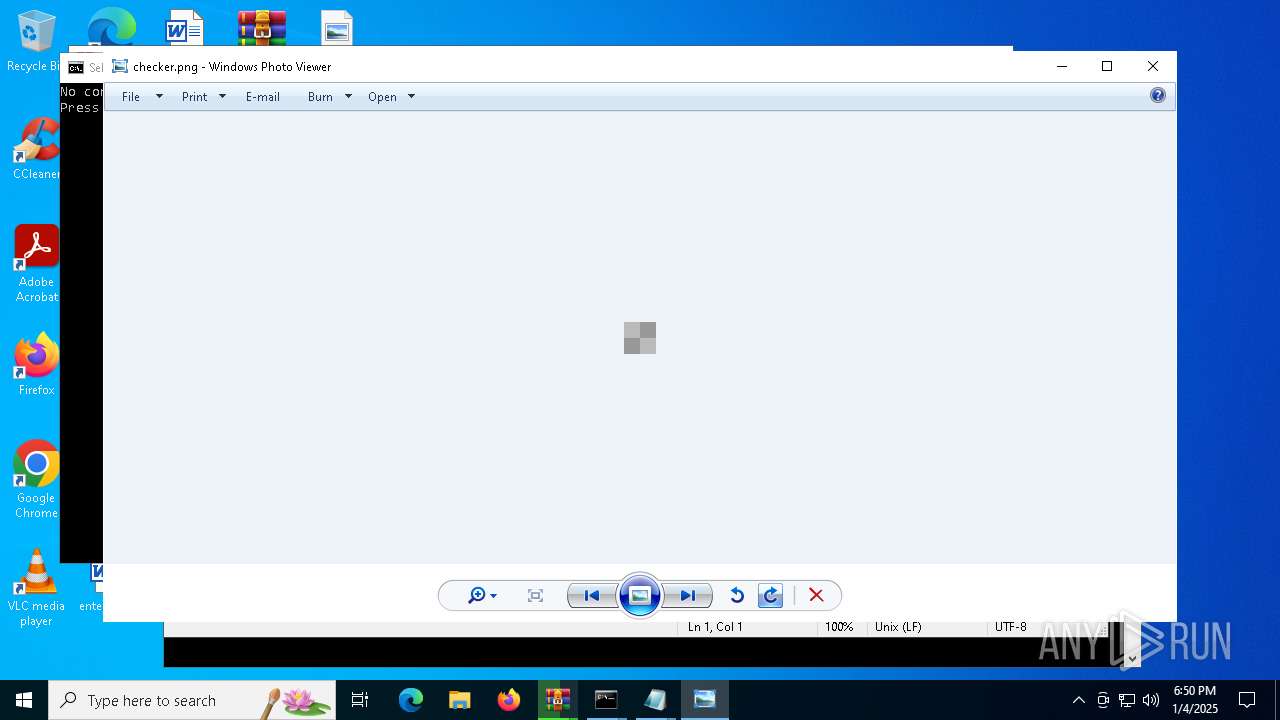
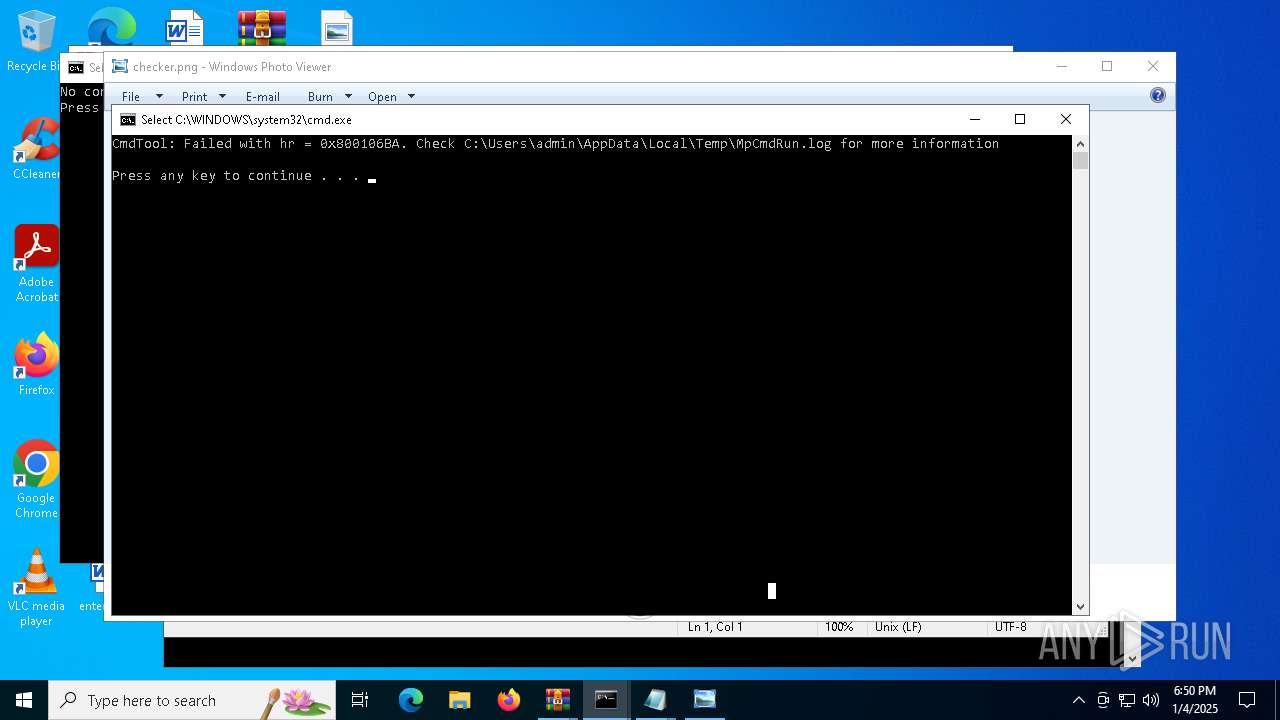
| 1536 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\checker.png | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1760 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR5320.41962\Rar$Scan10119.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2072 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\warmouse.json | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2280 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\bluestripe.json | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2356 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2728 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\greensward.json | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2744 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3296 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\license.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 006
Read events
14 961
Write events
45
Delete events
0
Modification events
| (PID) Process: | (5320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\KRXUltimate_2.7z | |||
| (PID) Process: | (5320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
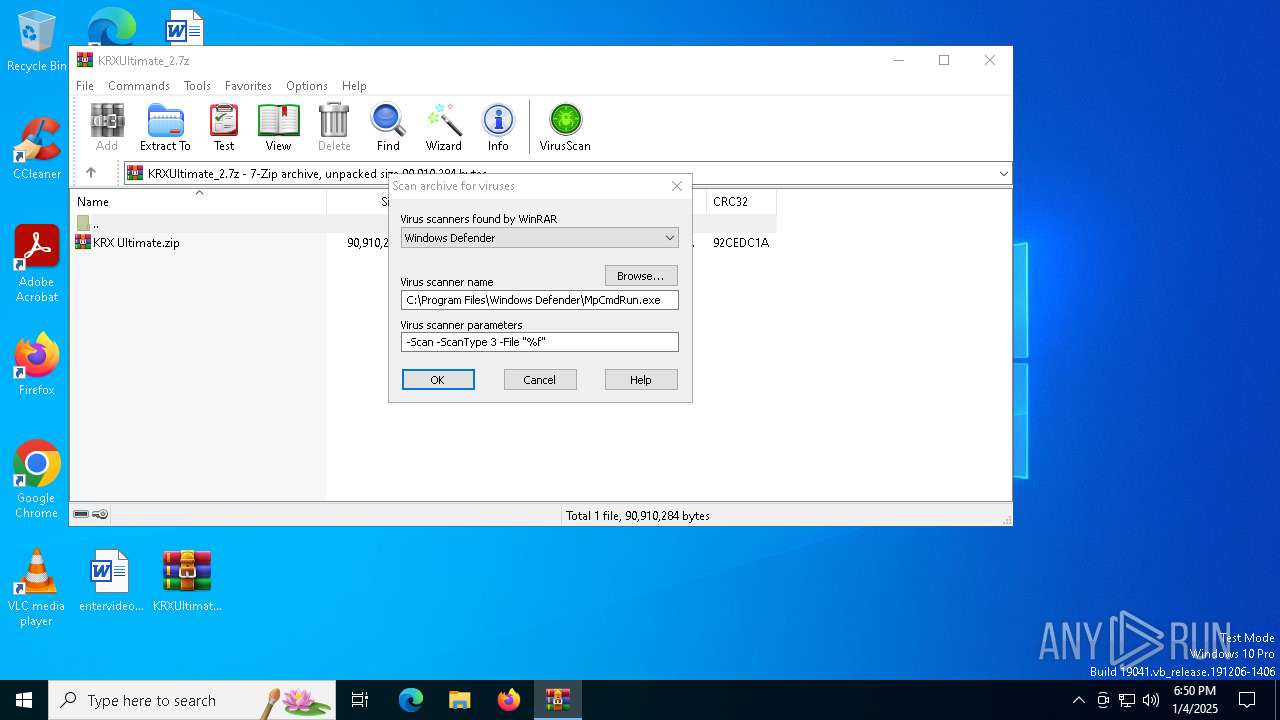
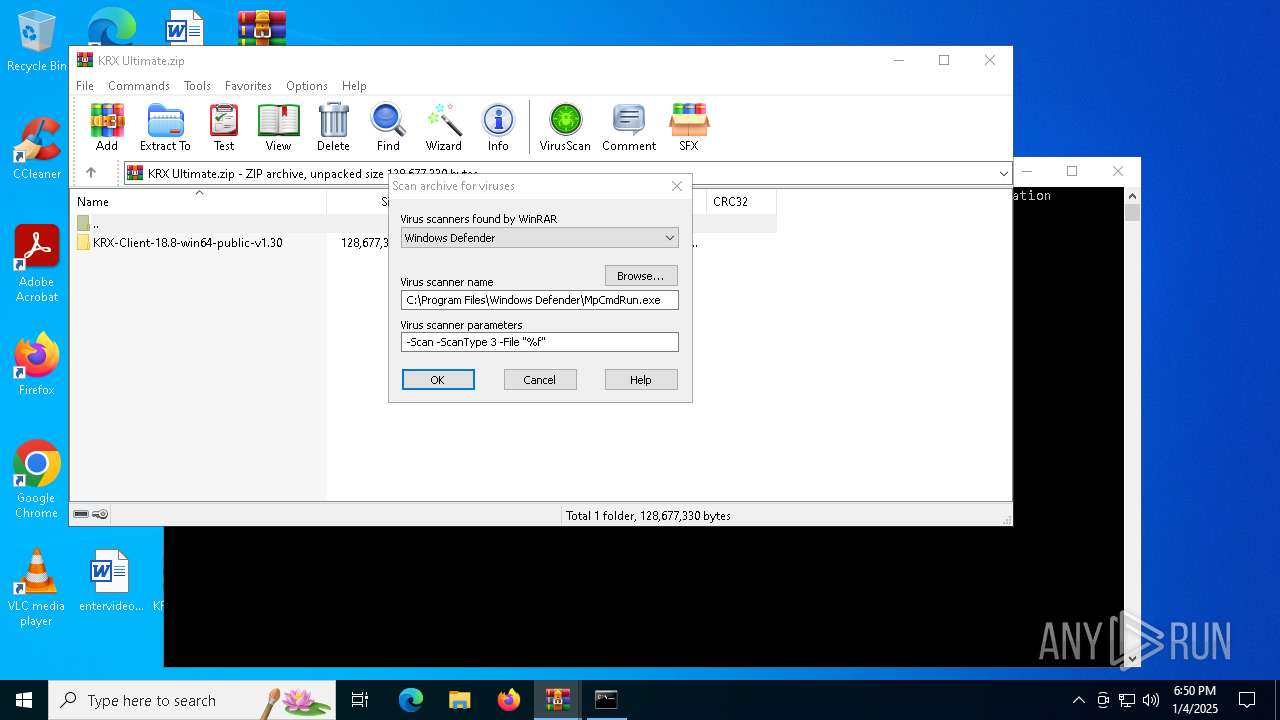
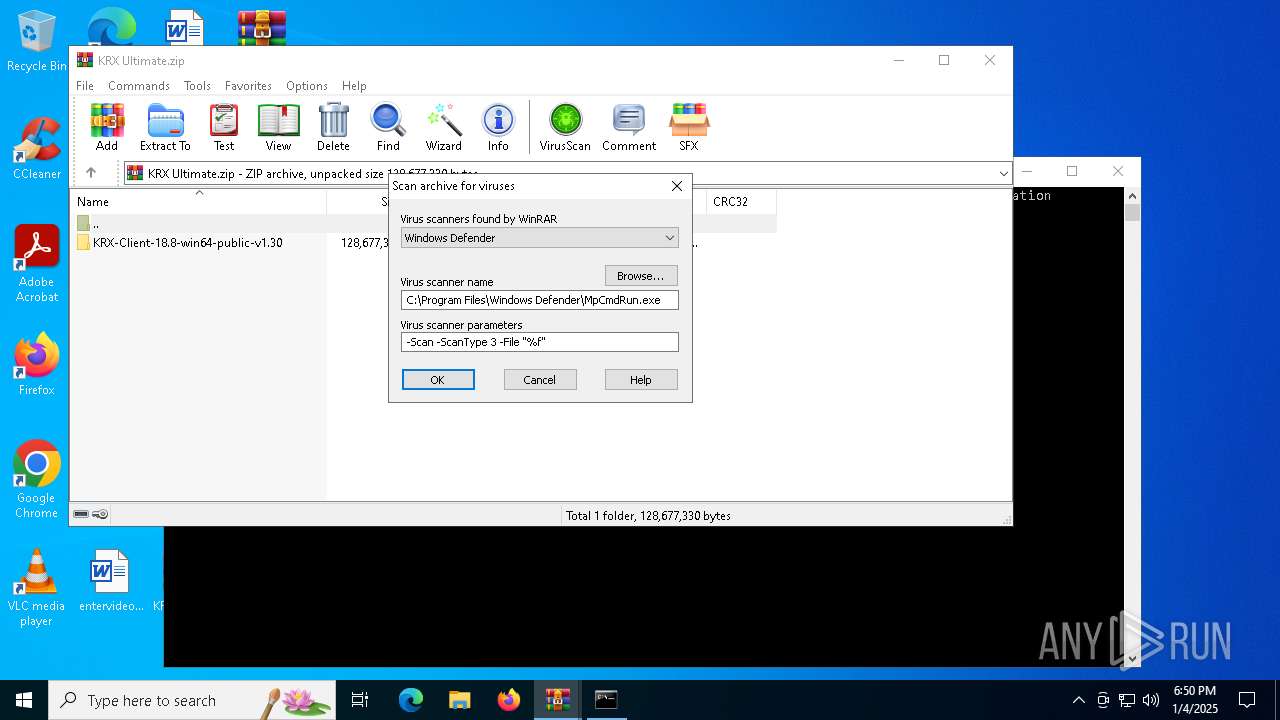
| (PID) Process: | (5320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
| (PID) Process: | (5684) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
Executable files
38
Suspicious files
240
Text files
653
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5320.41962\KRXUltimate_2.7z\KRX Ultimate.zip | — | |
MD5:— | SHA256:— | |||
| 5684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5684.43096\KRX Ultimate.zip\KRX-Client-18.8-win64-public-v1.30\avformat-61.dll | executable | |
MD5:179F9AE9EB9E05411966A0D943E75360 | SHA256:B72292ED8140957752E45880B597B6E1A673FB66E740379D29614DEE1454D3A2 | |||
| 5684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5684.43096\KRX Ultimate.zip\KRX-Client-18.8-win64-public-v1.30\data\assets\entities\comfort\ddnet.png | image | |
MD5:7973124505C42958FB0DE3287E13E53D | SHA256:4CBF66DF078A56FFAF245B658638A54F50B5DAB5681E6BD6D7272DFF42688E50 | |||
| 3732 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | text | |
MD5:3044842E4569205DECE68D35B464F7D3 | SHA256:991187D5992DB23F9037EEDCDB588C1F074FCB611C016C06778B6869206175DA | |||
| 5320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5320.41962\Rar$Scan10119.bat | text | |
MD5:22C228B6E1A537F7BB5185ED2FD3D61D | SHA256:4ED2CD14566C4A701717833B3716DD0EC561B7A1772138767AAD0BD6159F3121 | |||
| 5684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5684.43096\KRX Ultimate.zip\KRX-Client-18.8-win64-public-v1.30\config_retrieve.exe | executable | |
MD5:F7555D80FF6E60A59365F01414501479 | SHA256:278AA12AFD5178F7FE61B41C0F639BB38449D7D76E20E87948A56C8BFB16273B | |||
| 5684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5684.43096\KRX Ultimate.zip\KRX-Client-18.8-win64-public-v1.30\avcodec-61.dll | executable | |
MD5:AE6632DB7DE61EF9A0E1045B829502DC | SHA256:58C71BAA592DA746C9C5E30FDD41814A2736454B2B7168DA4AB88585758D4786 | |||
| 5684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5684.43096\KRX Ultimate.zip\KRX-Client-18.8-win64-public-v1.30\config_directory.bat | text | |
MD5:6191EC1743F8B924E43EBC2AB61ED4FC | SHA256:1FBAD52532E2685345CC3E5366E88D965F107E6C6013002E0BD6AD5DA0377AD7 | |||
| 5684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5684.43096\KRX Ultimate.zip\KRX-Client-18.8-win64-public-v1.30\avutil-59.dll | executable | |
MD5:9F4E1D61CF779052FED243C2142495B2 | SHA256:CD256113D455D362D769A859D2214B9F672BE8D2692EEBD7539675D31620CA6B | |||
| 5684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5684.43096\KRX Ultimate.zip\KRX-Client-18.8-win64-public-v1.30\config_store.exe | executable | |
MD5:44B8F89981FE8CEE058B46E645BB07F9 | SHA256:3E3E64438CCC8F4DBD185AE727946F8AAFEEF7261414C8F529599CD17E83F4E1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
19
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5564 | svchost.exe | GET | 200 | 2.16.164.129:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.129:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.129:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5564 | svchost.exe | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
5564 | svchost.exe | 2.16.164.129:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.129:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.16.164.129:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5564 | svchost.exe | 184.30.230.103:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.230.103:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
— | — | 184.30.230.103:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |