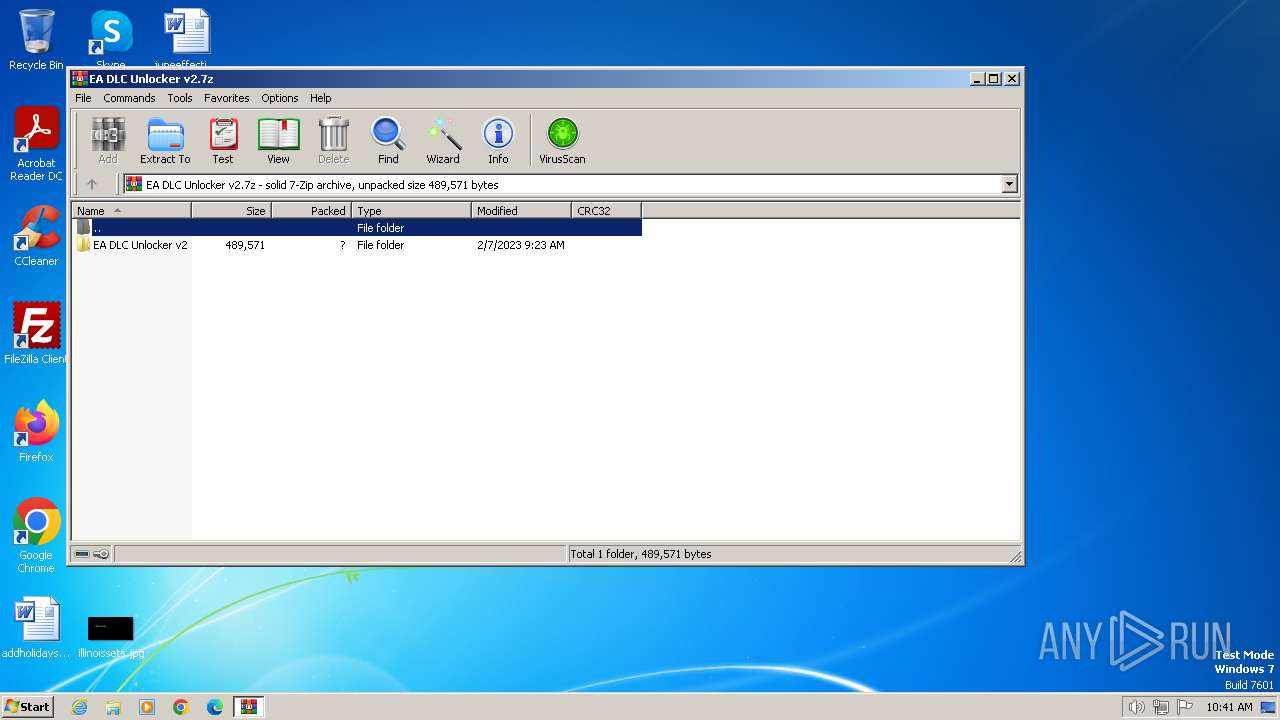
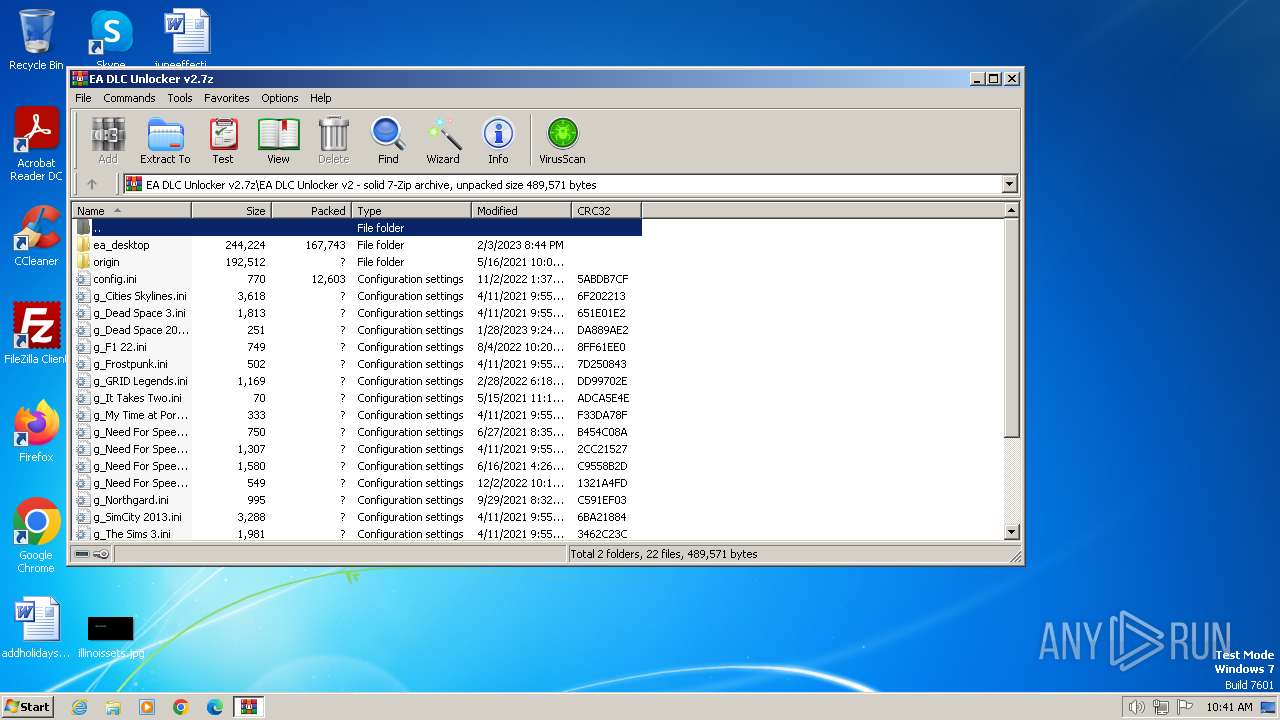
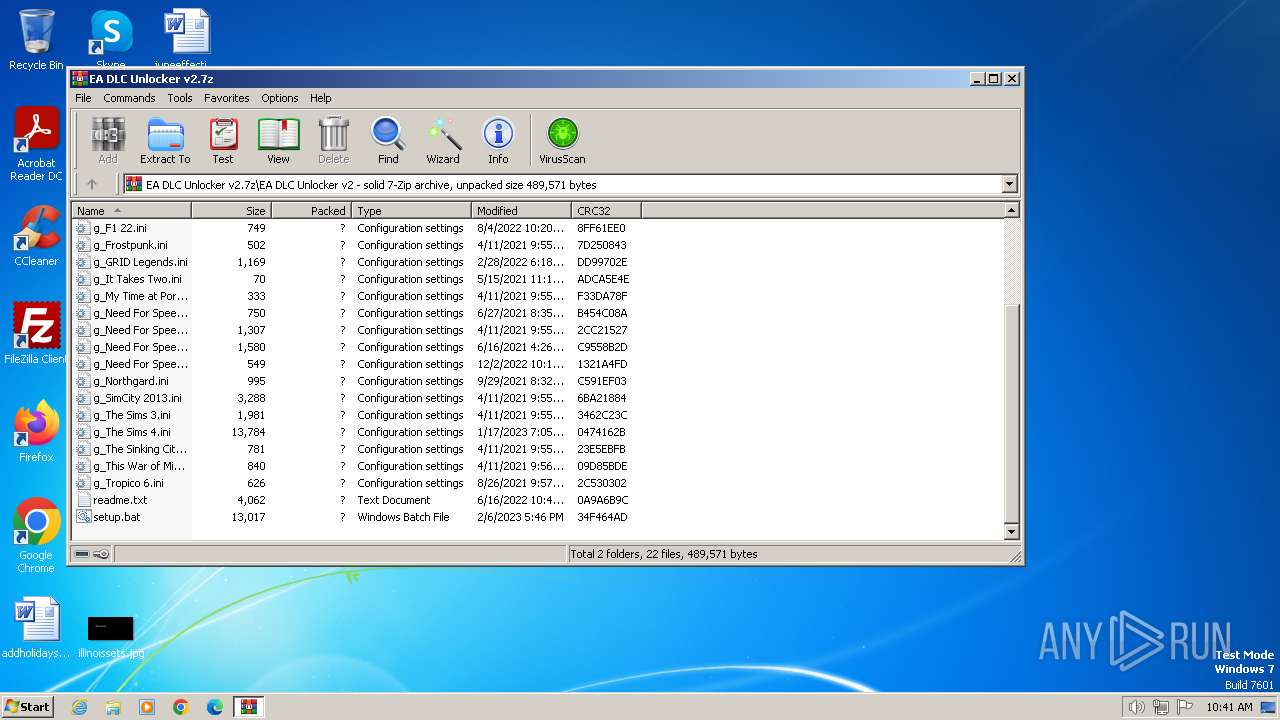
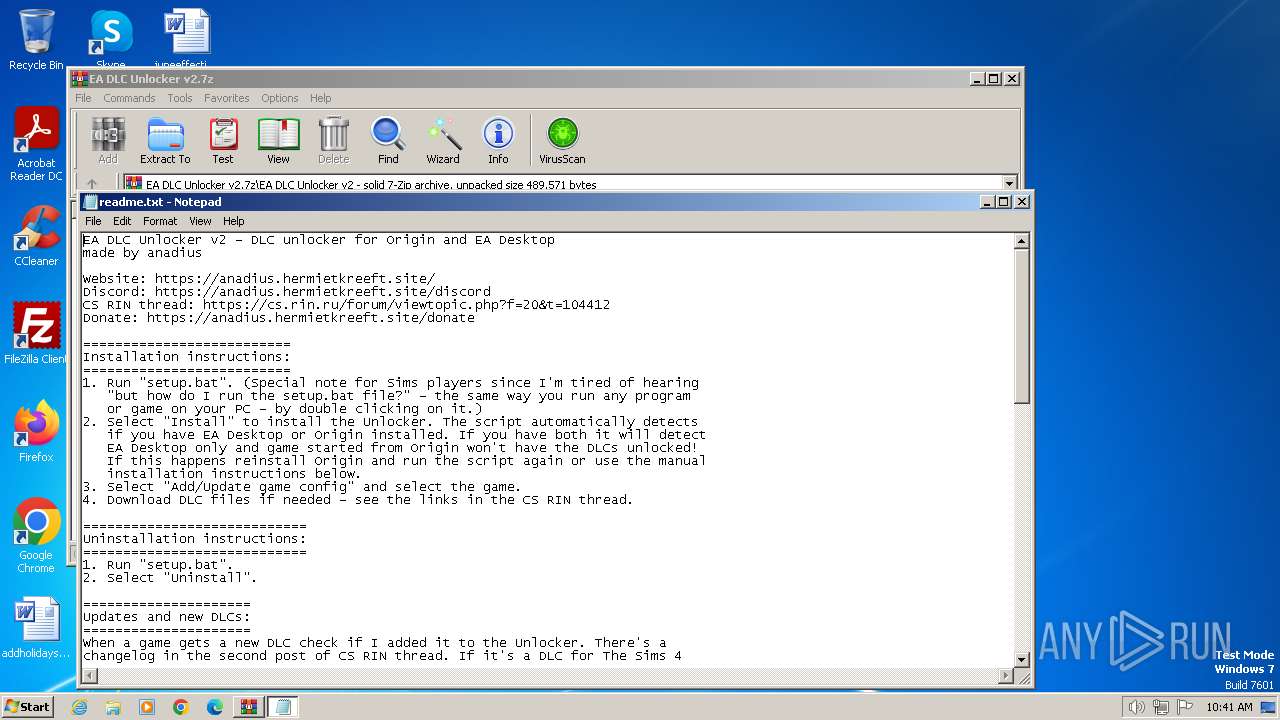
| File name: | EA DLC Unlocker v2.7z |
| Full analysis: | https://app.any.run/tasks/373de52b-61f9-4d62-bf25-b473e7d8880f |
| Verdict: | Malicious activity |
| Analysis date: | March 13, 2024, 10:40:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 9261761138CE9E19EC9CBF11B5EC9A71 |
| SHA1: | 492D3F8429D56B22785540485EC8D4069546514D |
| SHA256: | 3F8034B5146391C534CD739B40A9A5ABC08351C3782538F3E9F3946A70EDC997 |
| SSDEEP: | 6144:3UHSRfbF7PCvlwLp5VIboCdX7i2+mVVE9t6eGloa:EH4fBPSlwfqbr9hVq0floa |
MALICIOUS
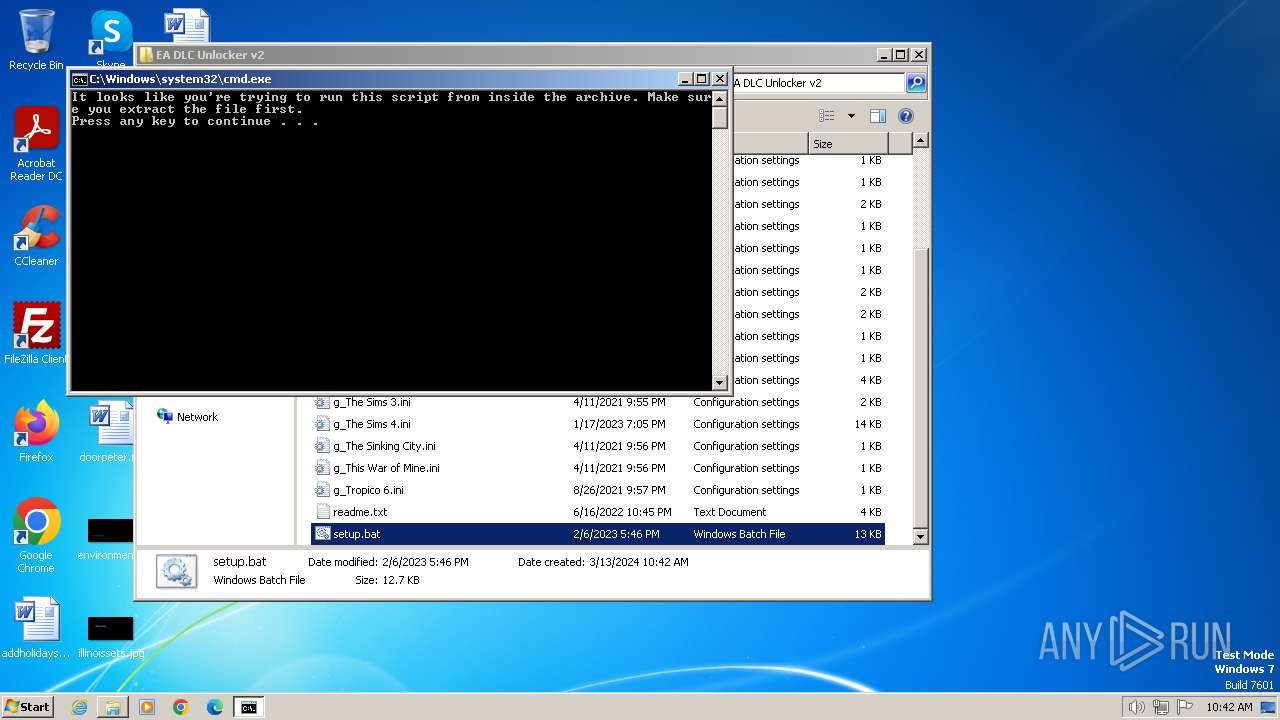
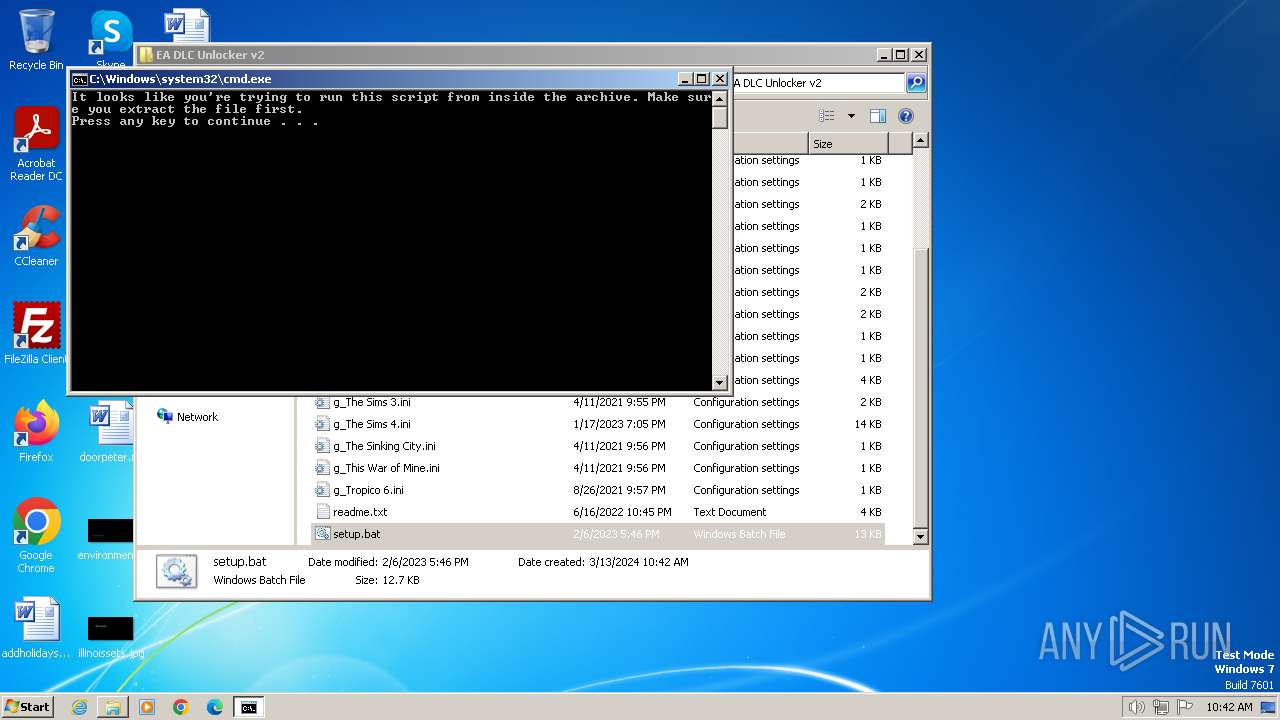
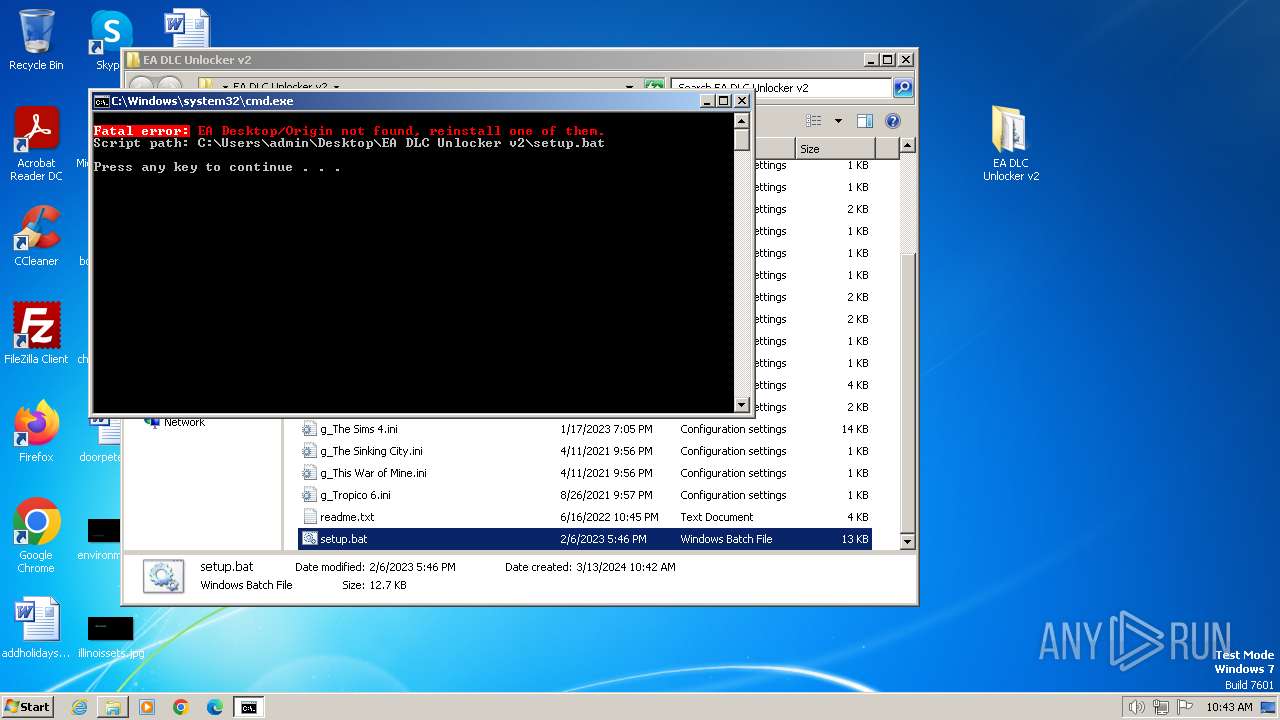
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3668)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3668)
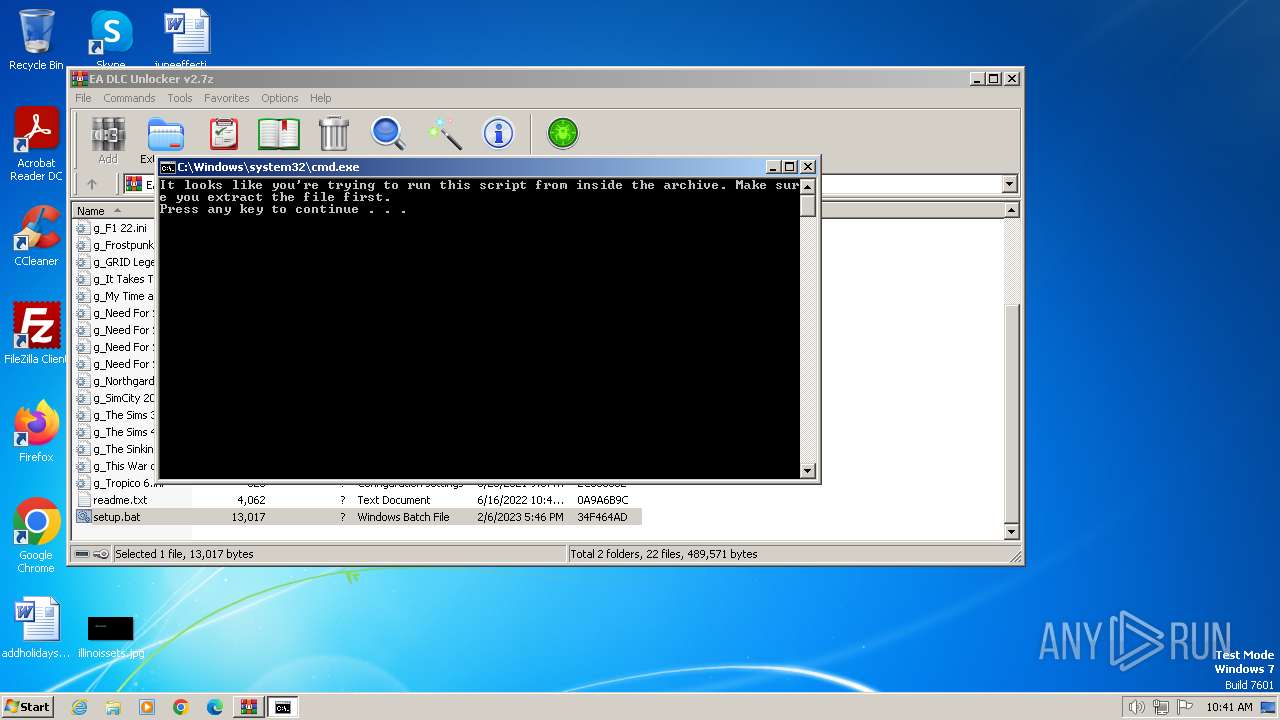
Executing commands from a ".bat" file
- WinRAR.exe (PID: 3668)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3664)
- WinRAR.exe (PID: 3668)
- cmd.exe (PID: 3664)
- cmd.exe (PID: 3068)
Application launched itself
- cmd.exe (PID: 3664)
- cmd.exe (PID: 3664)
- cmd.exe (PID: 3068)
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 3668)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3664)
- cmd.exe (PID: 3664)
- cmd.exe (PID: 3068)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 3068)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 3068)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3068)
INFO
Manual execution by a user
- explorer.exe (PID: 2328)
- WinRAR.exe (PID: 4012)
- explorer.exe (PID: 680)
- cmd.exe (PID: 3664)
- cmd.exe (PID: 3068)
- wmpnscfg.exe (PID: 712)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4012)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4012)
Checks supported languages
- wmpnscfg.exe (PID: 712)
Reads the computer name
- wmpnscfg.exe (PID: 712)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
73
Monitored processes
28
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 680 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 712 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1040 | C:\Windows\system32\cmd.exe /S /D /c" echo "C:\Users\admin\AppData\Local\Temp\EA DLC Unlocker v2\EA DLC Unlocker v2\" " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1236 | findstr /C:"polo" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1340 | powershell -noprofile "$_PSCommandPath = [Environment]::GetEnvironmentVariable('script_path', 'Process'); iex ((Get-Content -LiteralPath $_PSCommandPath) | out-string)" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1844 | C:\Windows\system32\cmd.exe /S /D /c" echo "C:\Users\admin\Desktop\EA DLC Unlocker v2\" " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2160 | findstr /V /C:"polo" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2240 | findstr /V /C:"polo" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2260 | findstr /V /C:"C:\Users\admin\AppData\Local\Temp" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2328 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
9 637
Read events
9 596
Write events
41
Delete events
0
Modification events
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\EA DLC Unlocker v2.7z | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
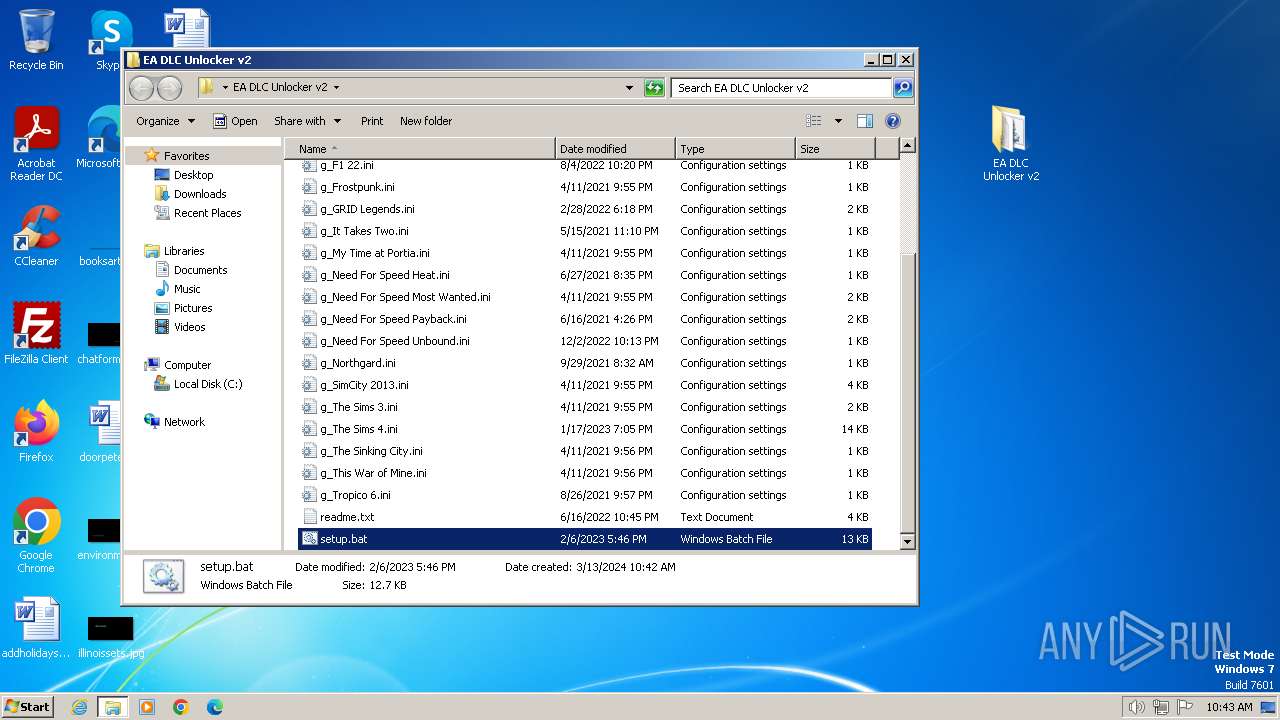
Executable files
2
Suspicious files
2
Text files
24
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4012 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EA DLC Unlocker v2\EA DLC Unlocker v2\g_Dead Space 2023.ini | text | |
MD5:FC3F0C4D744A4310C775B2879399C468 | SHA256:934211FE00D6151381796B7001D7AEF5BC883DAA9F1B1F68AF60A7AF93EB1835 | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3668.45386\readme.txt | text | |
MD5:40777E23043D467158E03BFDDF4FCD3E | SHA256:CEC5779E88C60EA8682029B47B3C992E9C4824653D53115BE09044F9BC7684CC | |||
| 4012 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EA DLC Unlocker v2\EA DLC Unlocker v2\config.ini | ini | |
MD5:14CF4A3CE6A5F39790B2678EE0B0CFA0 | SHA256:94699C9C6106C6C737820472E102B6D762A0268801DADB9C0E0272DB7D5ED3BF | |||
| 4012 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EA DLC Unlocker v2\EA DLC Unlocker v2\g_Dead Space 3.ini | text | |
MD5:19F5DEDA4368C463D16687109ABF543D | SHA256:8996053E41CE56F0822A2A3E9449F3960FF1D395C6587ACDDB608AB306A3E6EE | |||
| 4012 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EA DLC Unlocker v2\EA DLC Unlocker v2\g_Frostpunk.ini | text | |
MD5:FB2516CAACEBCDB02E9F2194BA72DE12 | SHA256:8A28296795FC669C047ED3AFBEB82791C4C86D3160B5A6843A144D814AE578C2 | |||
| 4012 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EA DLC Unlocker v2\EA DLC Unlocker v2\g_F1 22.ini | text | |
MD5:FECE8042278EFC32B3F32A4109ADB50C | SHA256:F0435DC6ECF94DFCFE718EAC51293924617B7377C11DF5A9747EF60E83791F1D | |||
| 4012 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EA DLC Unlocker v2\EA DLC Unlocker v2\g_Need For Speed Most Wanted.ini | text | |
MD5:53020D0FF8E79EE8305061D5D3964927 | SHA256:070AC609263921F4C91061F8C8DDD78A3305038EC3F13F4FE265AE715F2C0B89 | |||
| 4012 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EA DLC Unlocker v2\EA DLC Unlocker v2\g_It Takes Two.ini | text | |
MD5:31561ACF01F495280B2E03EC26B7812F | SHA256:3435BE593EE7214A75789417B0B6E90FB7939B26DC43A8CCA197620E72EC48AF | |||
| 4012 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EA DLC Unlocker v2\EA DLC Unlocker v2\g_Need For Speed Payback.ini | text | |
MD5:C49B925D0158A9C34E976D436C8AC2A0 | SHA256:C58E8C92876A1656D417FDA84F43093C0BD4C52DDE42CD9ADDCD001E9A38879E | |||
| 4012 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EA DLC Unlocker v2\EA DLC Unlocker v2\g_My Time at Portia.ini | text | |
MD5:EDE7B7058E8C95575EF5517D36784FE2 | SHA256:D7812CD7633CBC13521C9D7A862541EB13A93A8F42D1E56137D4BE8D7225F90A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |