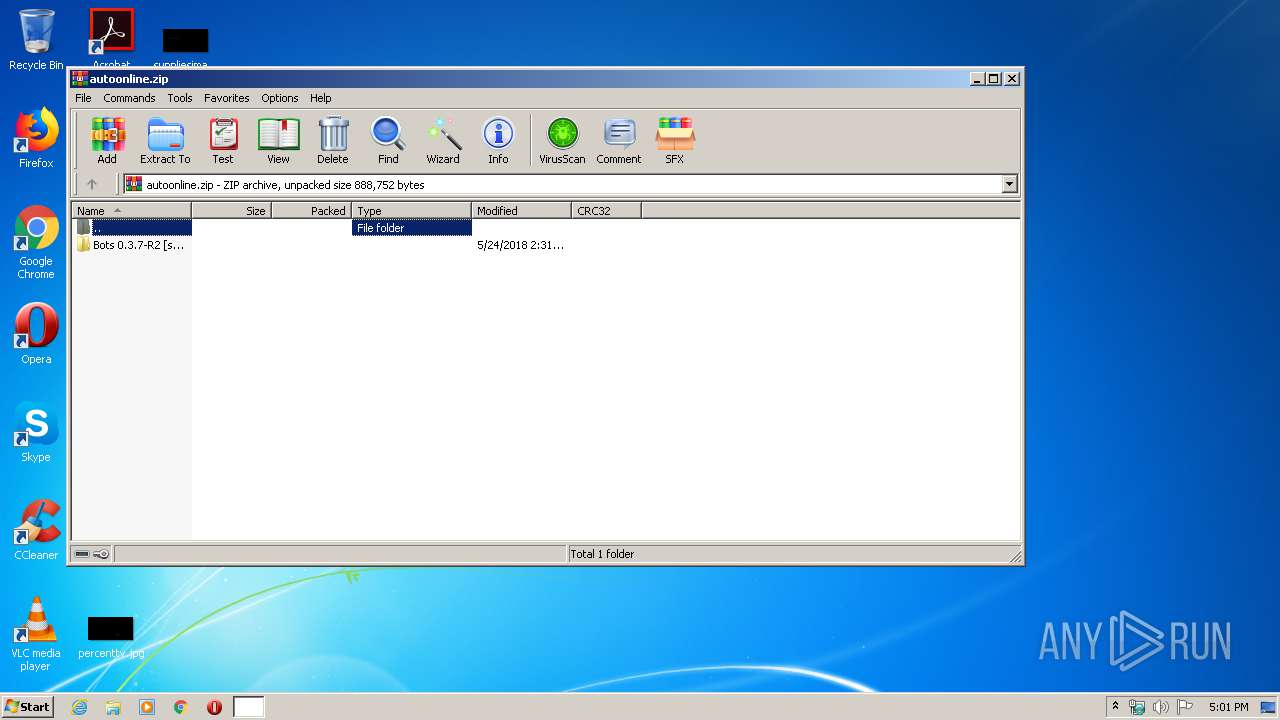
| File name: | autoonline.zip |
| Full analysis: | https://app.any.run/tasks/1a01ca3e-f03d-4c4b-ac44-7363d5d351a5 |
| Verdict: | No threats detected |
| Analysis date: | April 18, 2020, 16:01:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 9705F818E9FCA27029D07F638ECECCDB |
| SHA1: | 6963391C5515B5912DC3A5AAE750845C2594B3C5 |
| SHA256: | 3F6E983D3C8E8B5DB34996FB4A0F8766F92FE7717641C0D20AC0B11A240F1073 |
| SSDEEP: | 6144:dwSevT5WvWMHi8N62By09k0SYZhx80rR2GPyBeFU6mxuvJqLDY1LxS4FkoSktftP:QrMRtk0605s0PyBN6TvJKDY1lFlxtP |
MALICIOUS
No malicious indicators.SUSPICIOUS
Writes to a desktop.ini file (may be used to cloak folders)
- WinRAR.exe (PID: 3148)
Executed via COM
- prevhost.exe (PID: 1392)
INFO
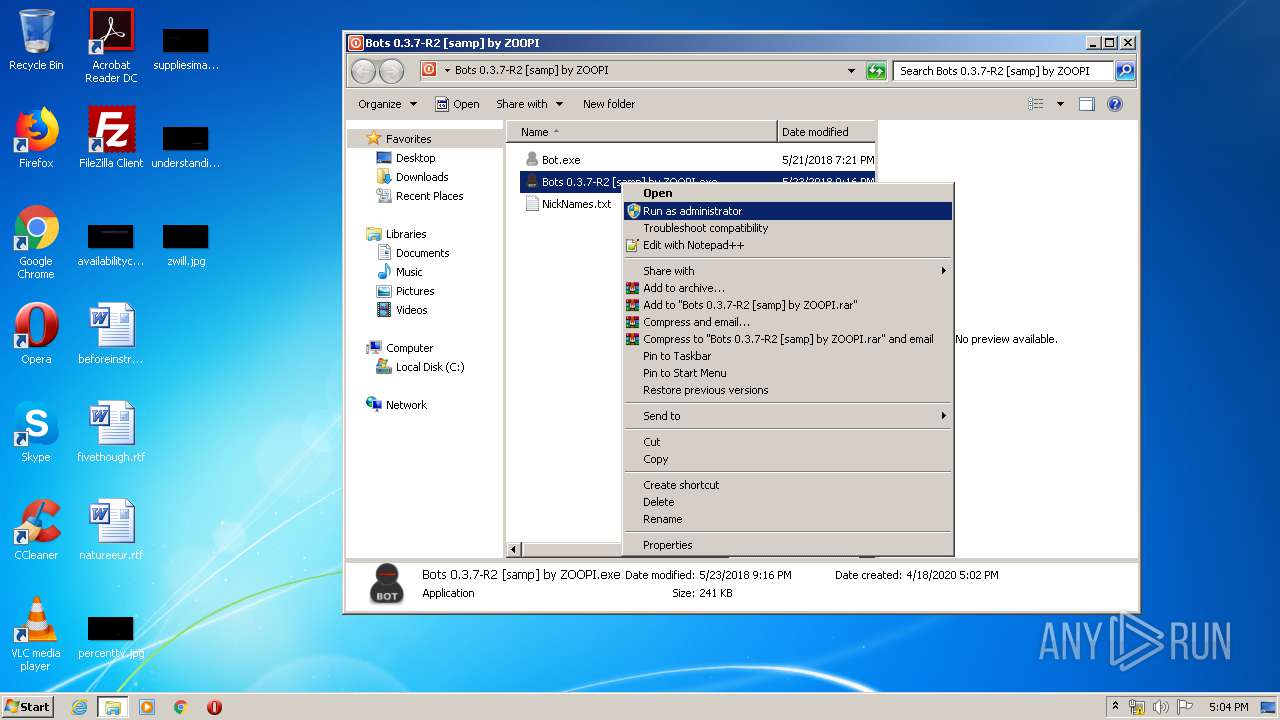
Manual execution by user
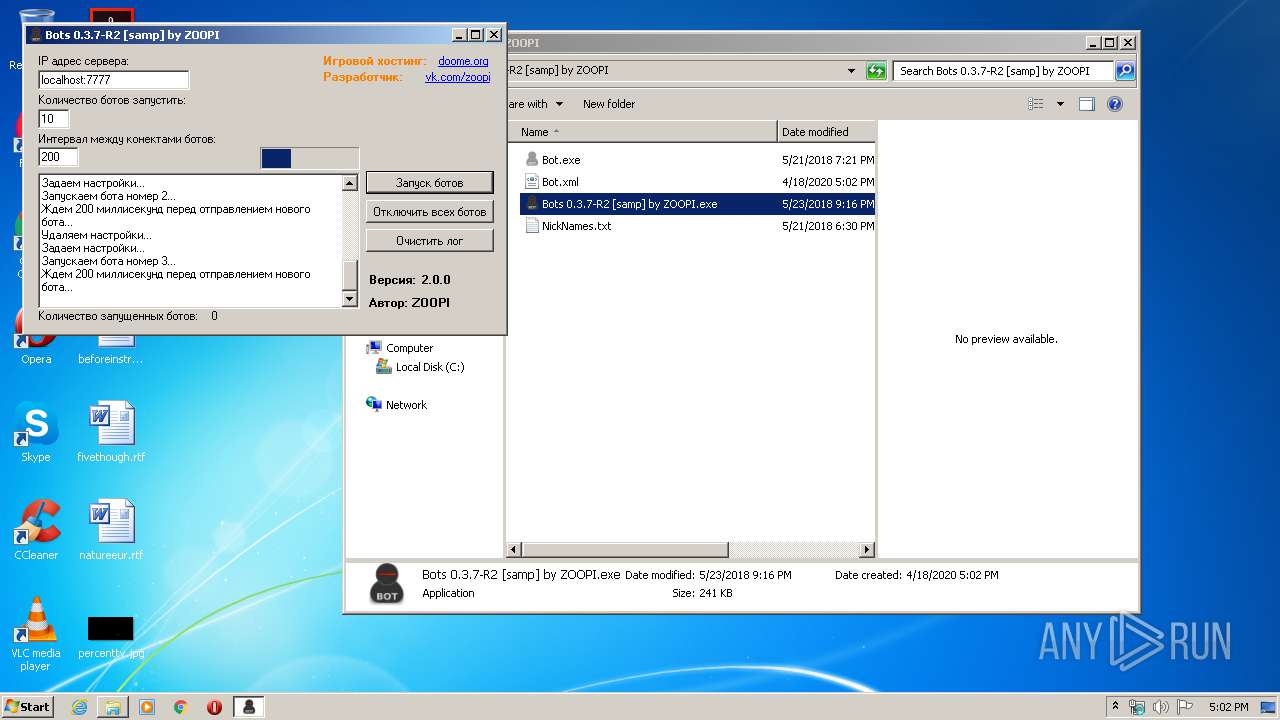
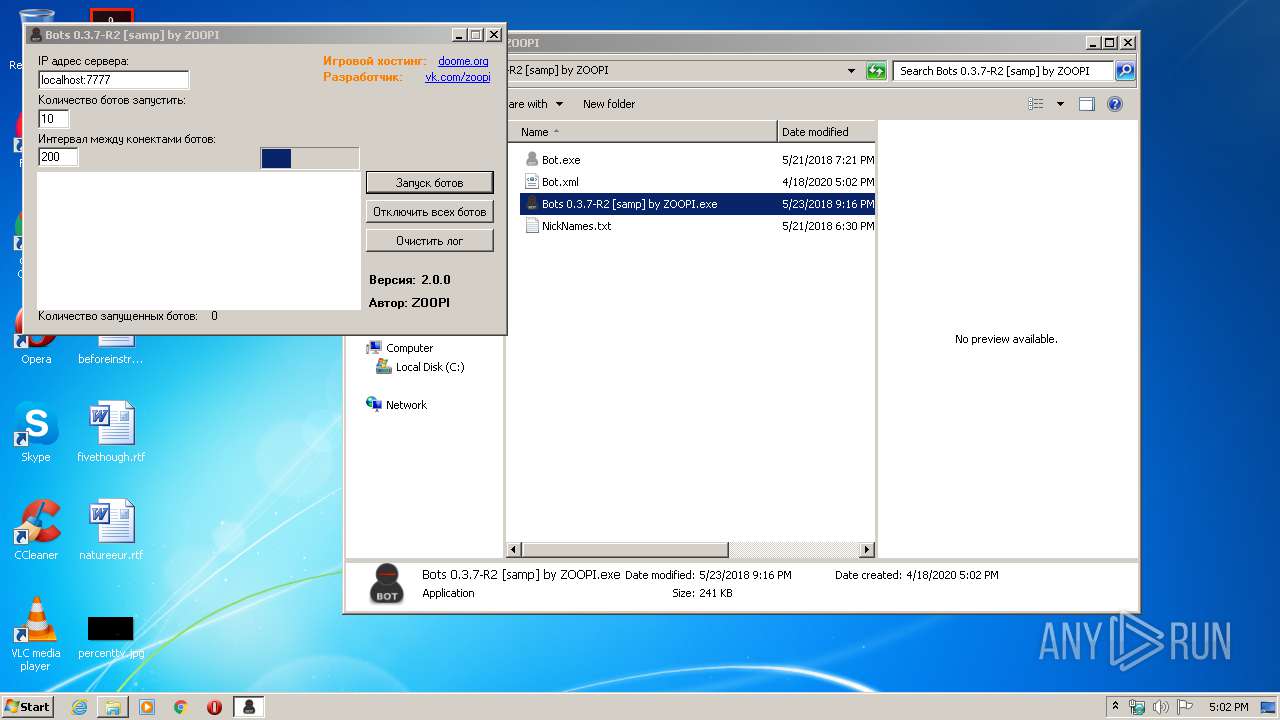
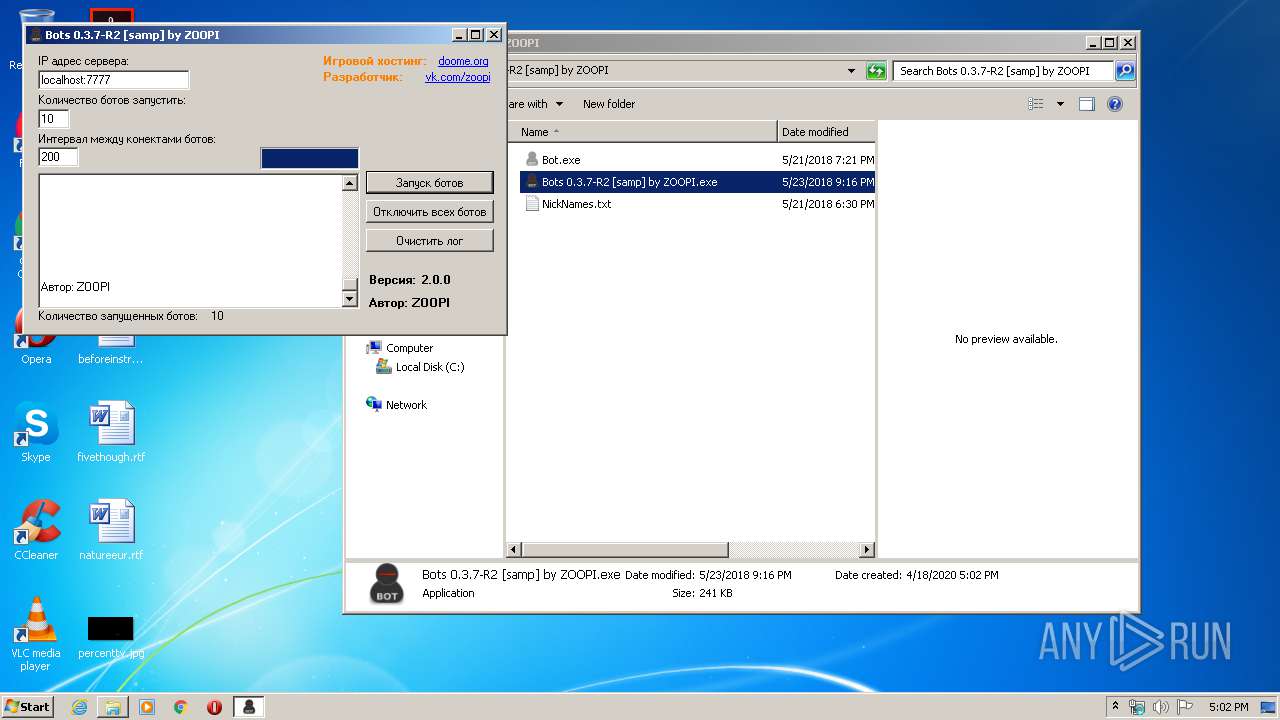
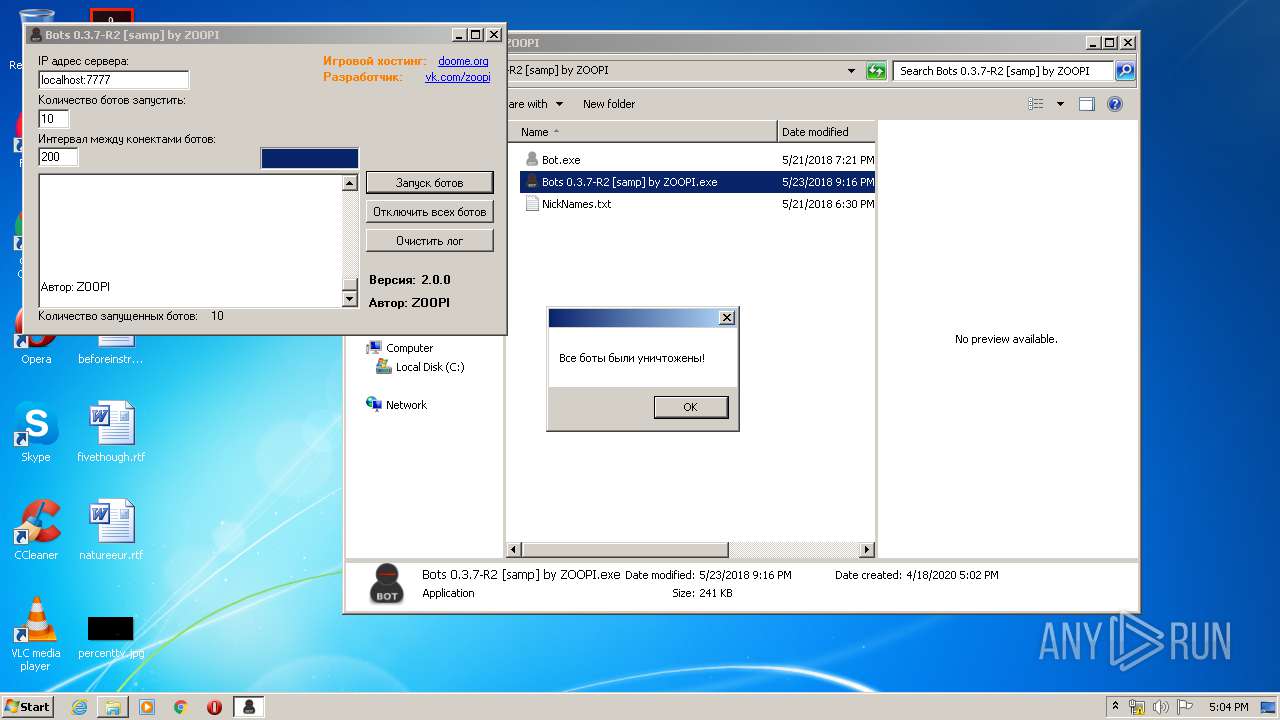
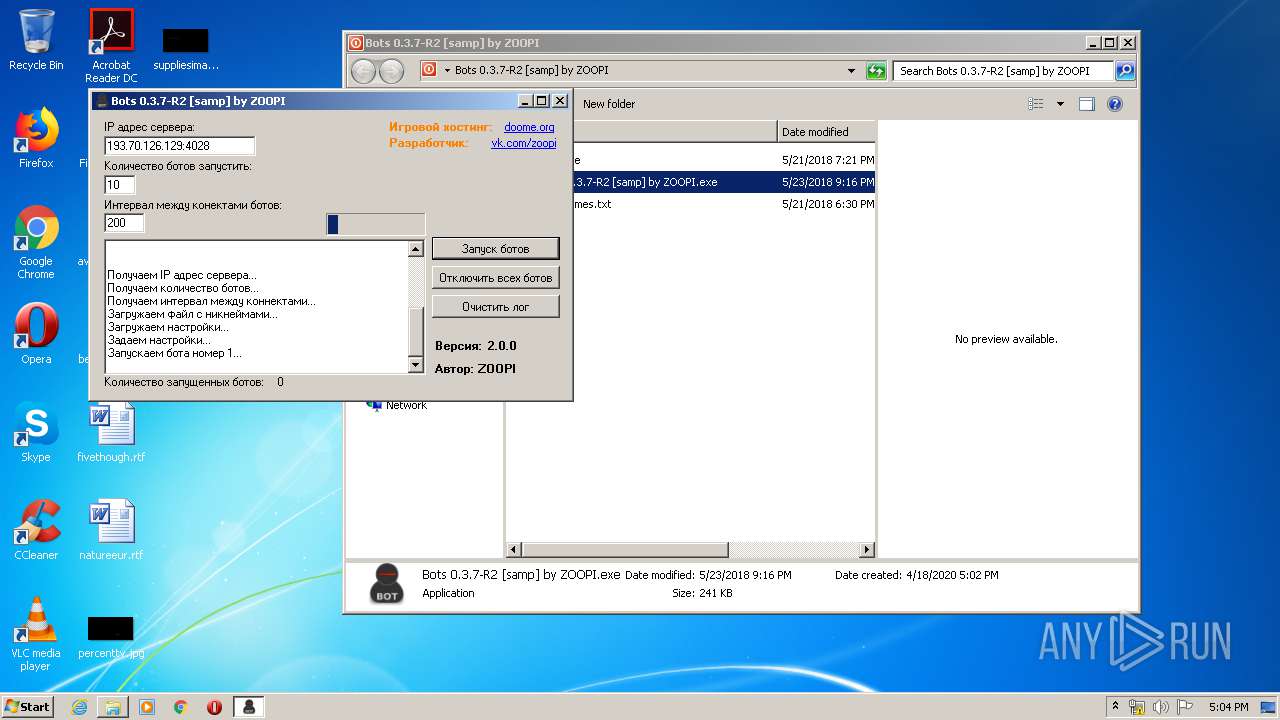
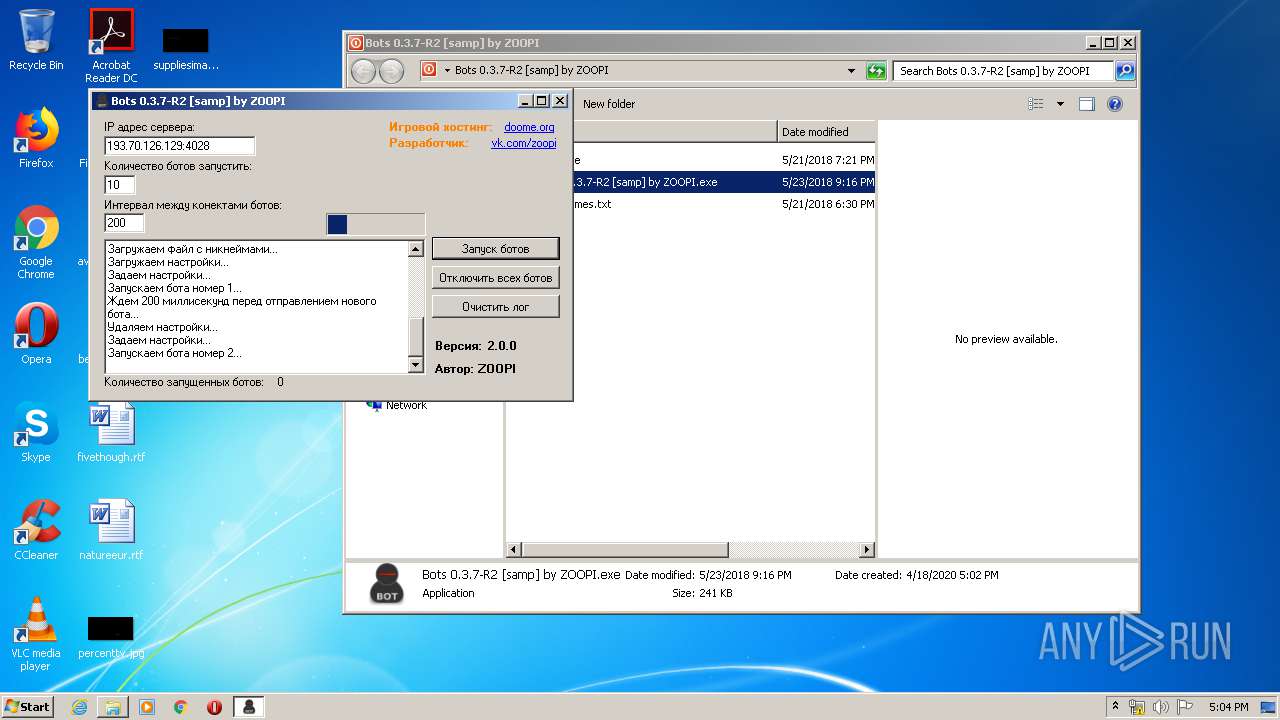
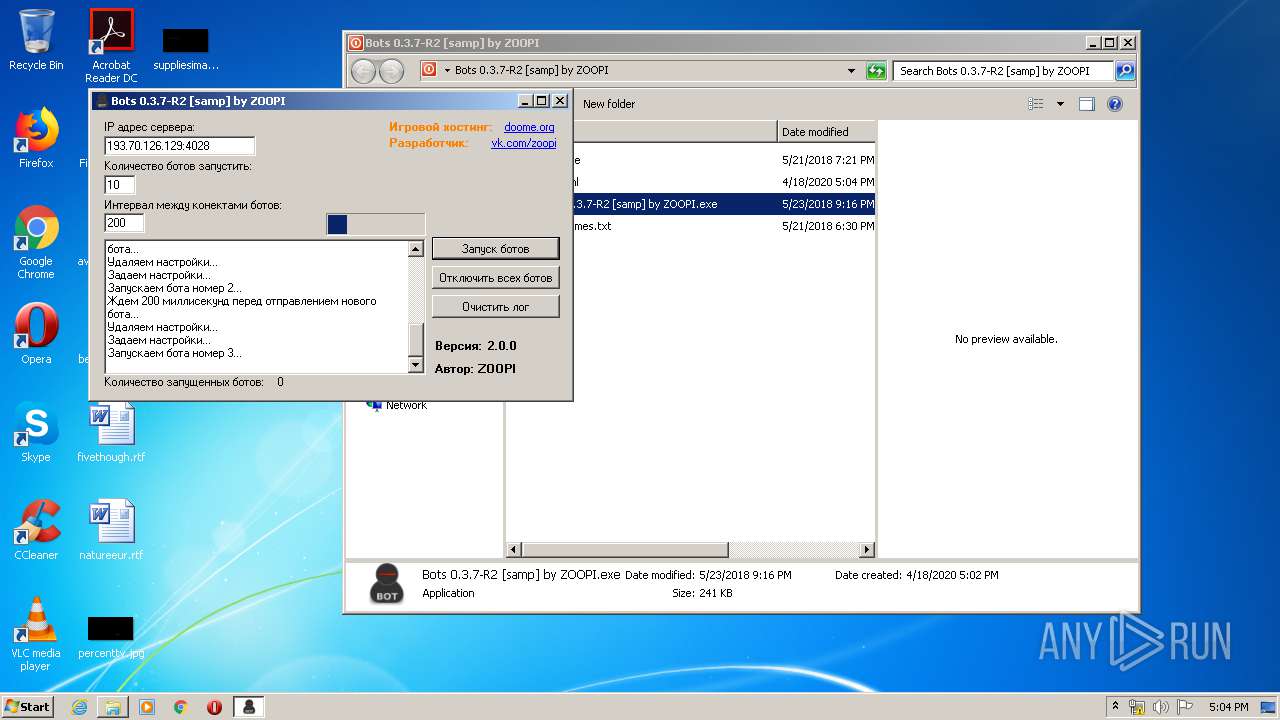
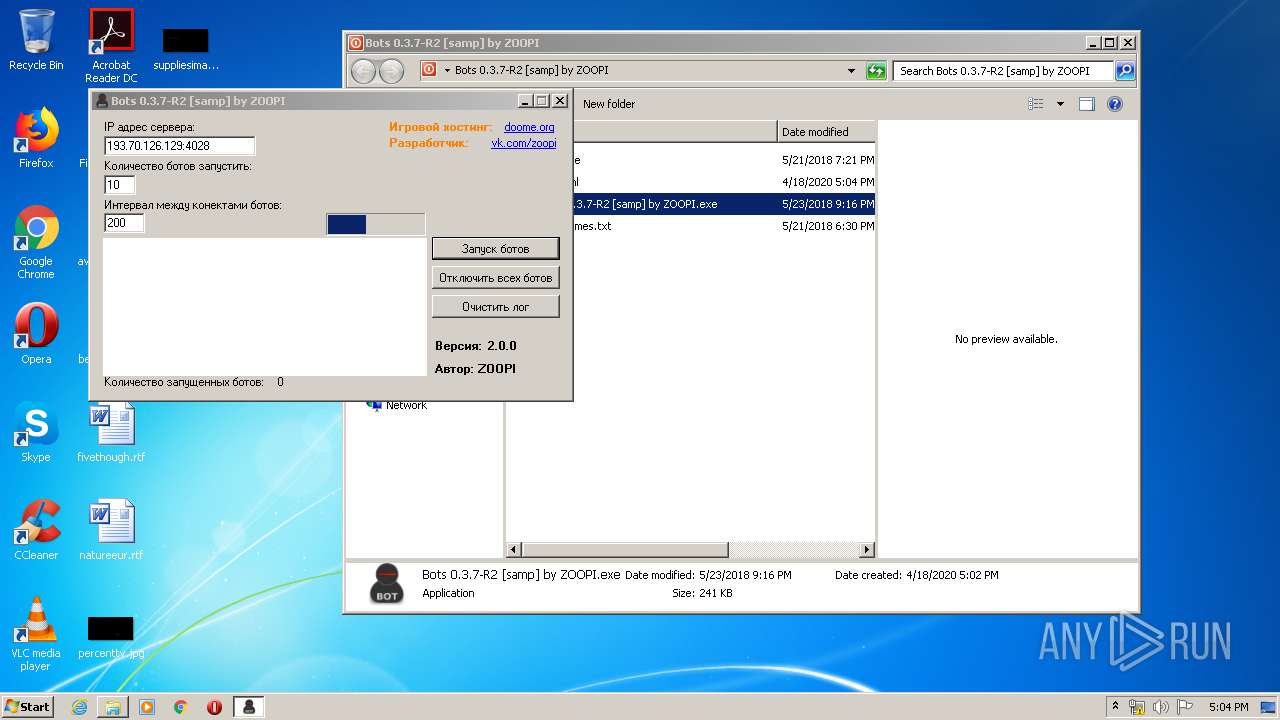
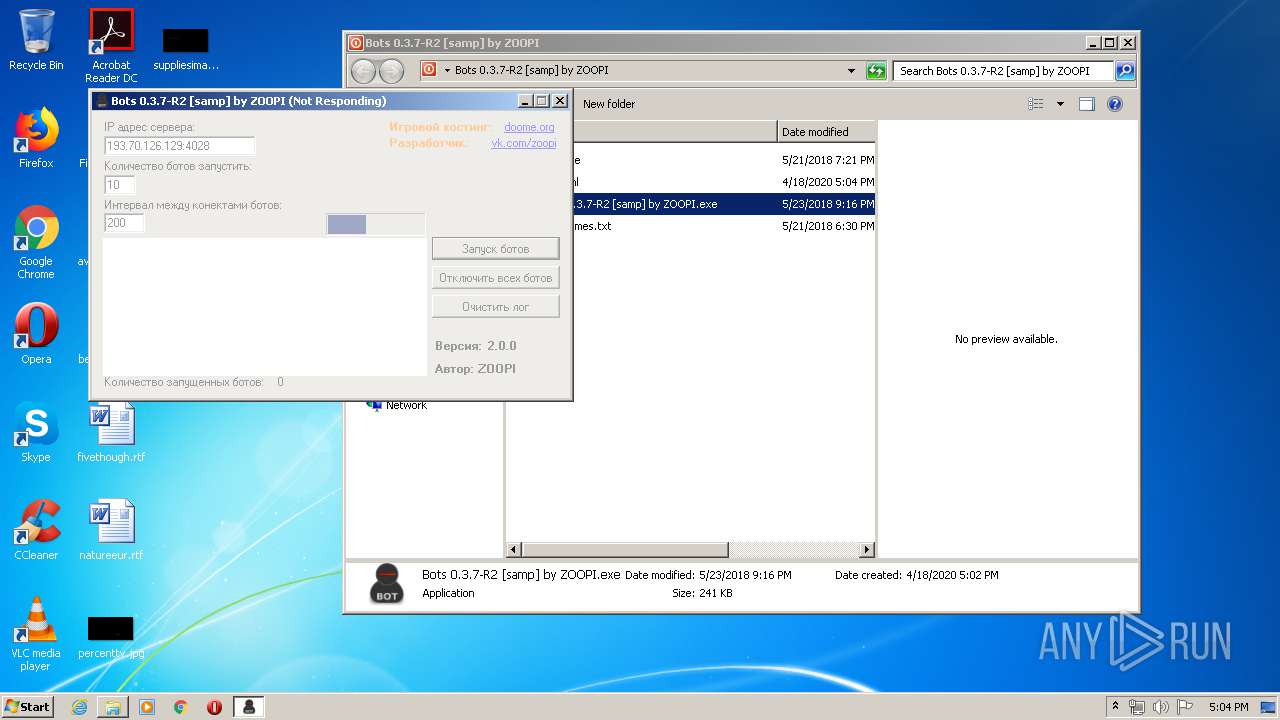
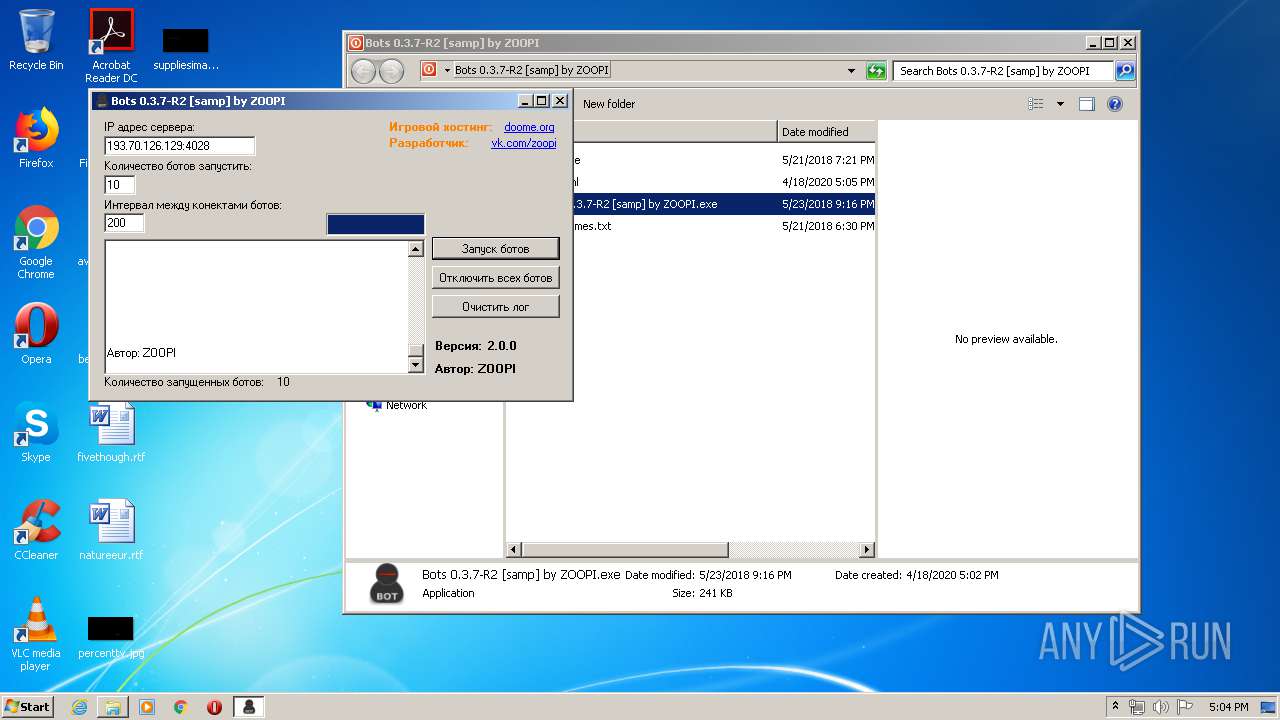
- Bots 0.3.7-R2 [samp] by ZOOPI.exe (PID: 1784)
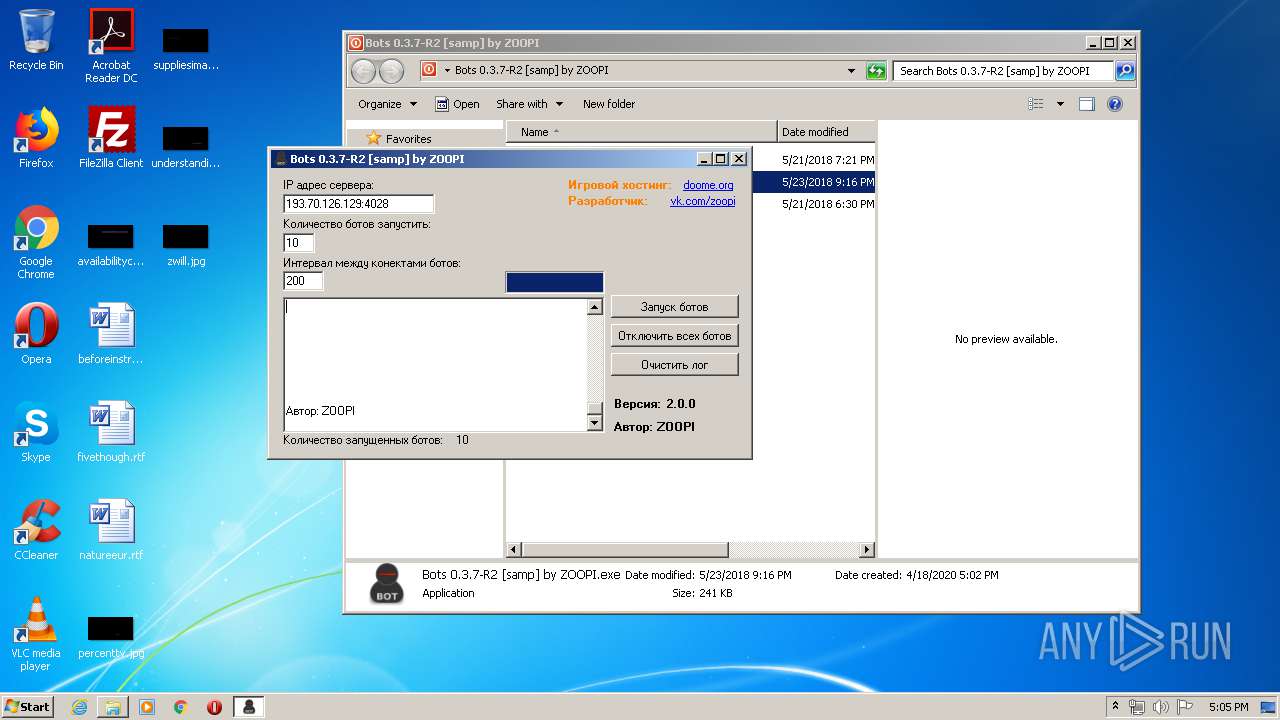
- Bots 0.3.7-R2 [samp] by ZOOPI.exe (PID: 2568)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2018:05:24 16:31:02 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Bots 0.3.7-R2 [samp] by ZOOPI/ |
Total processes
64
Monitored processes
24
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
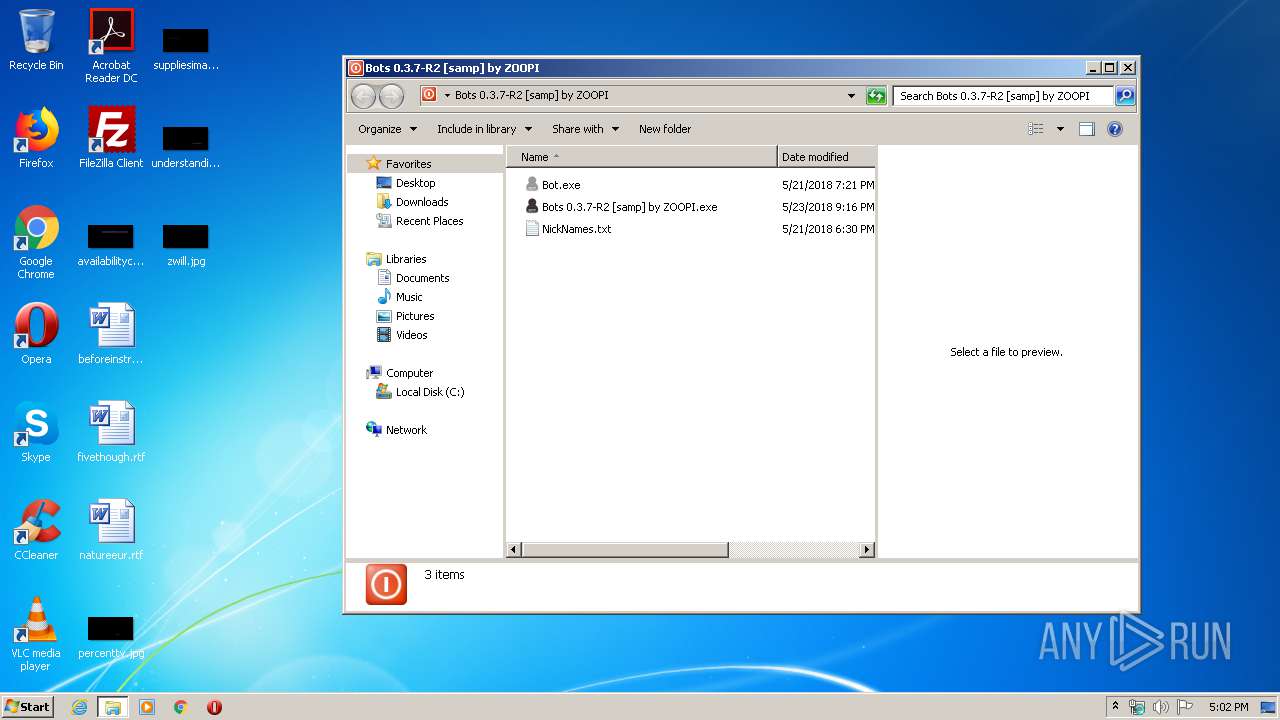
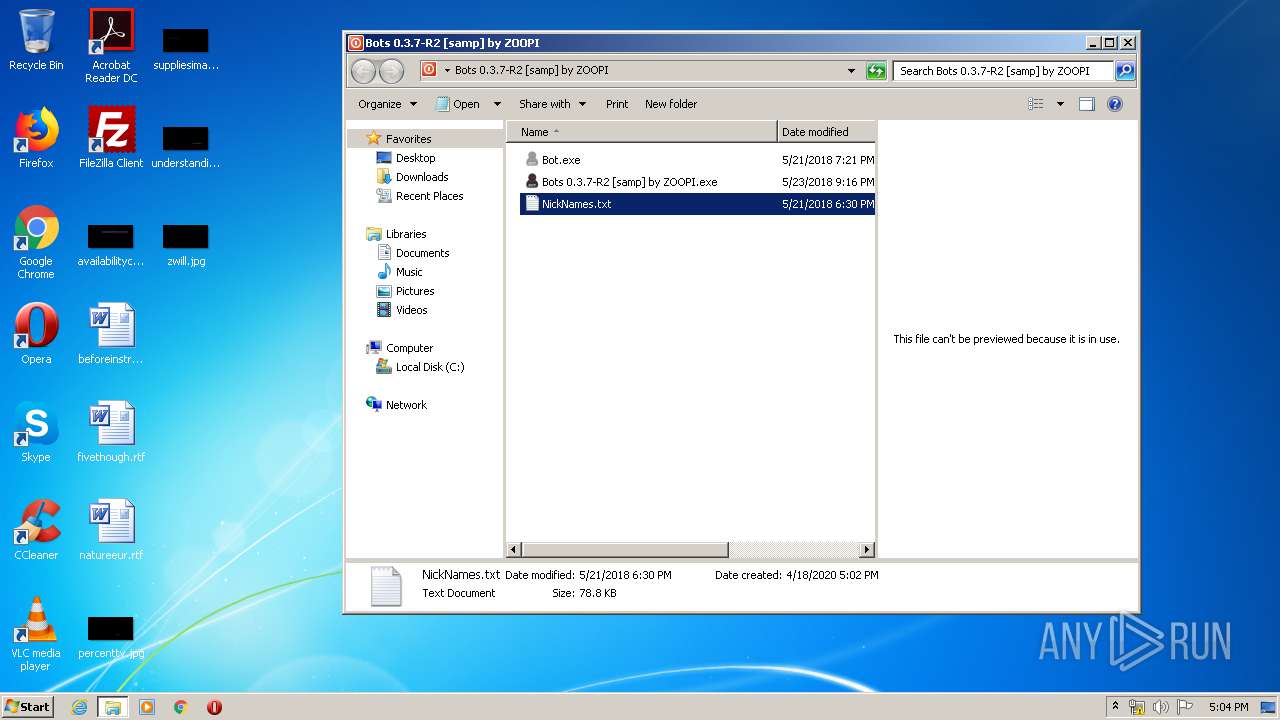
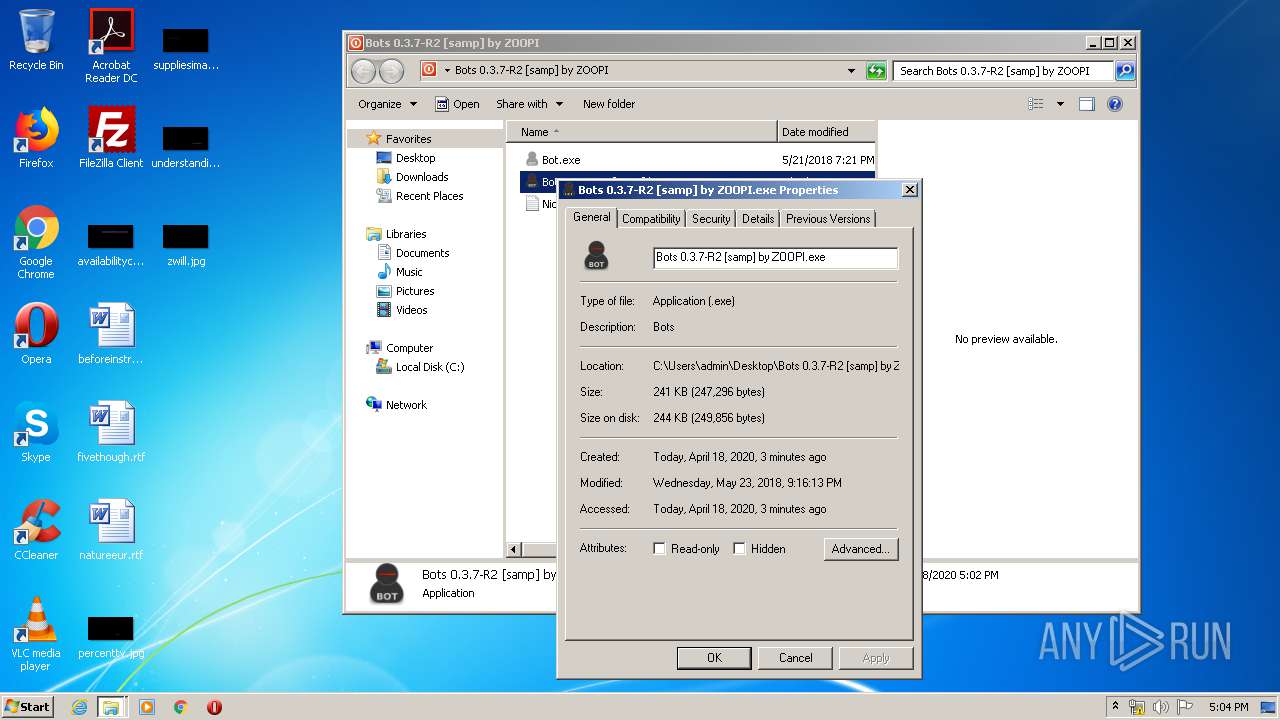
| 988 | "C:\Users\admin\Desktop\Bots 0.3.7-R2 [samp] by ZOOPI\Bot.exe" | C:\Users\admin\Desktop\Bots 0.3.7-R2 [samp] by ZOOPI\Bot.exe | Bots 0.3.7-R2 [samp] by ZOOPI.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 1392 | C:\Windows\system32\prevhost.exe {914FEED8-267A-4BAA-B8AA-21E233792679} -Embedding | C:\Windows\system32\prevhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Preview Handler Surrogate Host Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1524 | "C:\Users\admin\Desktop\Bots 0.3.7-R2 [samp] by ZOOPI\Bot.exe" | C:\Users\admin\Desktop\Bots 0.3.7-R2 [samp] by ZOOPI\Bot.exe | Bots 0.3.7-R2 [samp] by ZOOPI.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
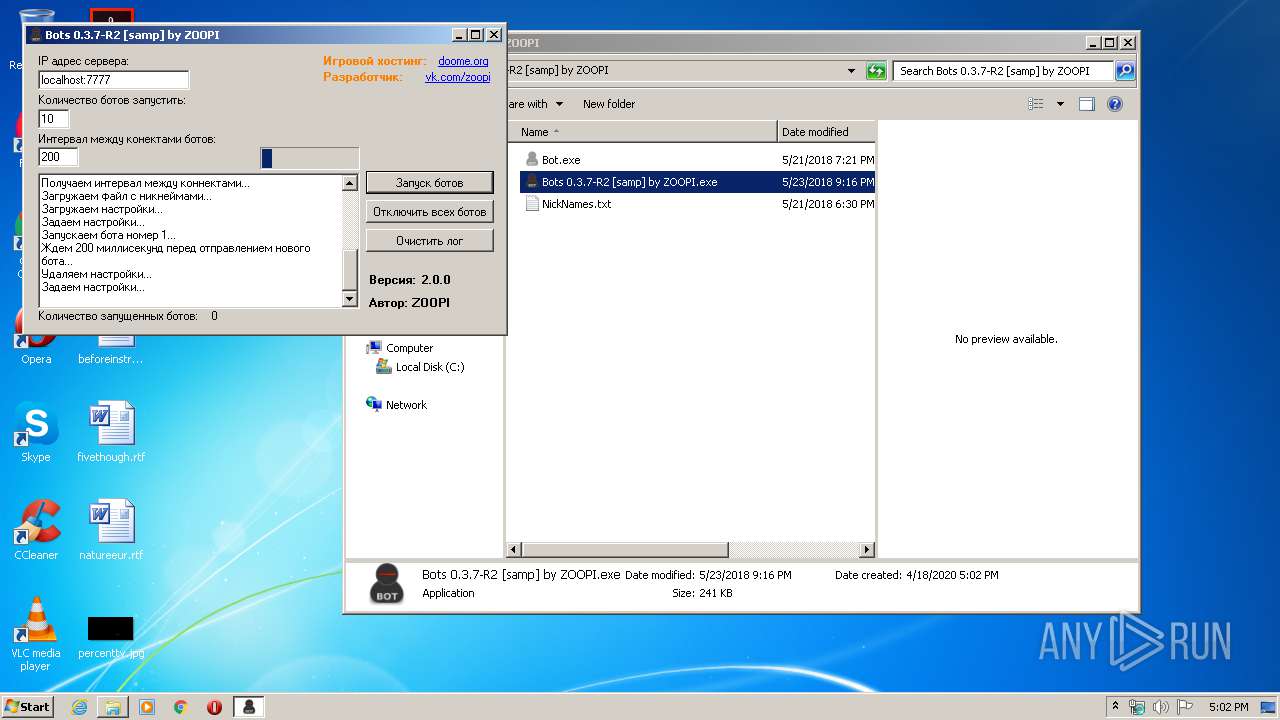
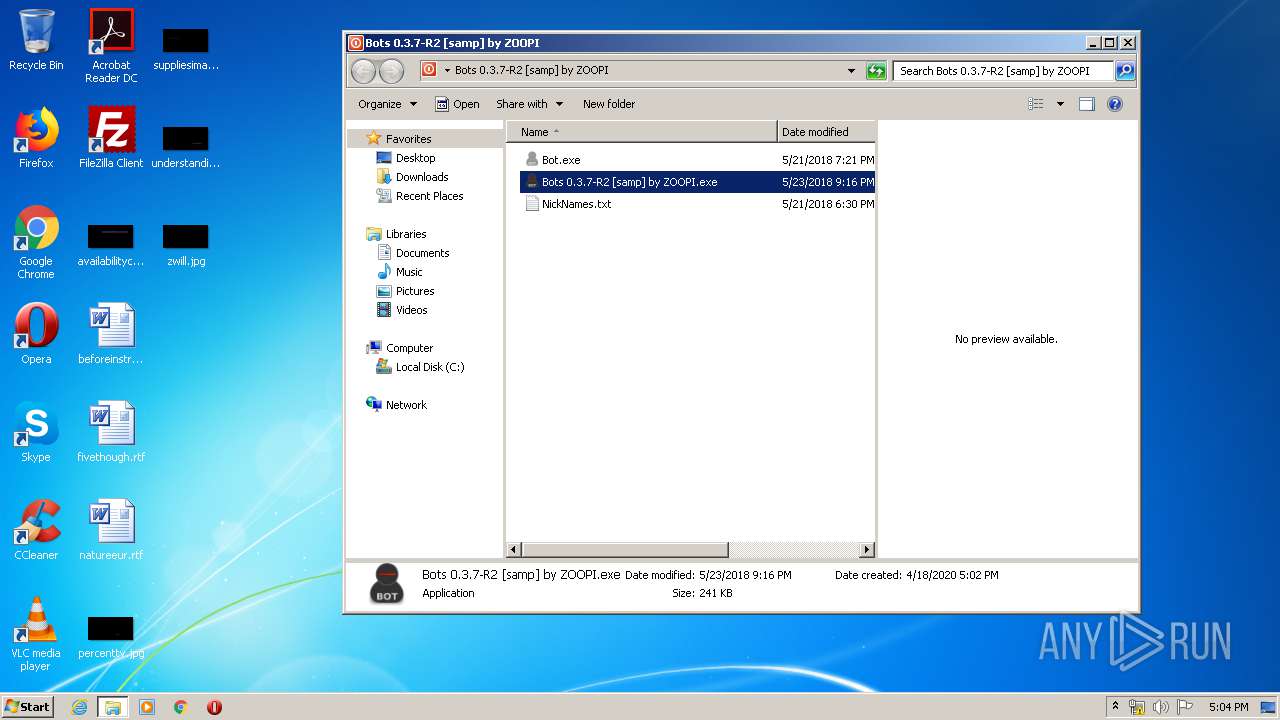
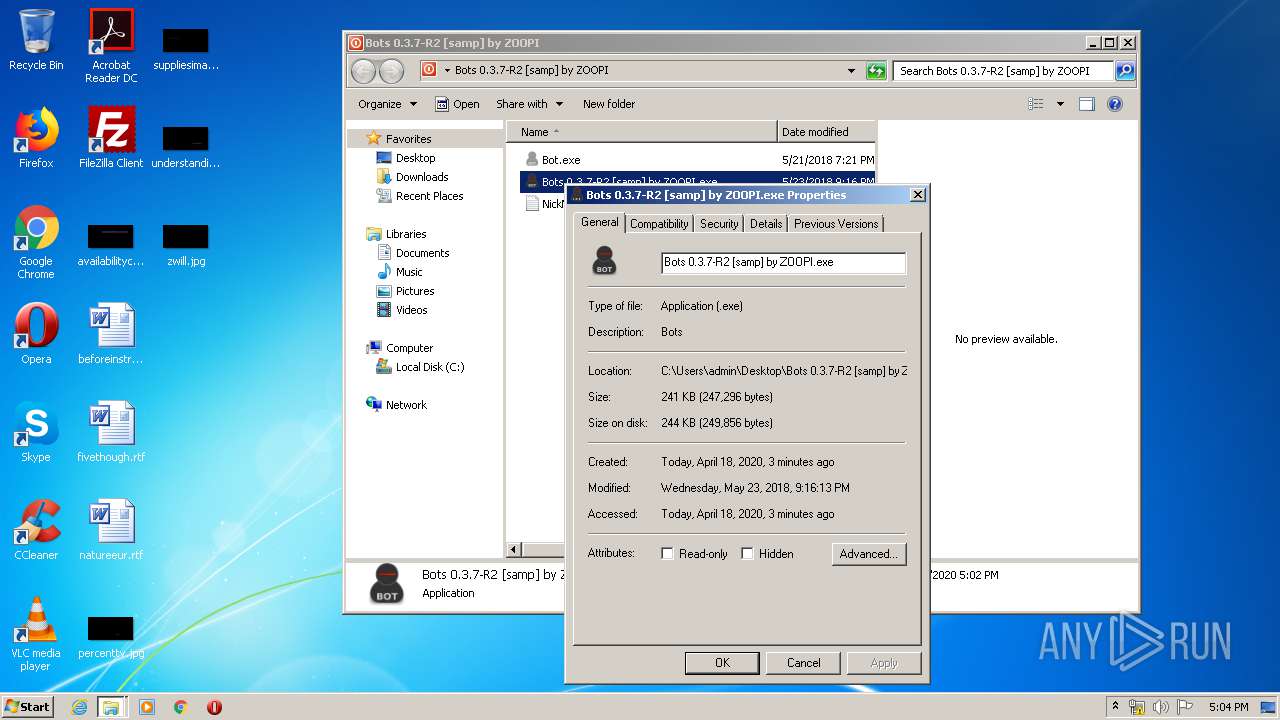
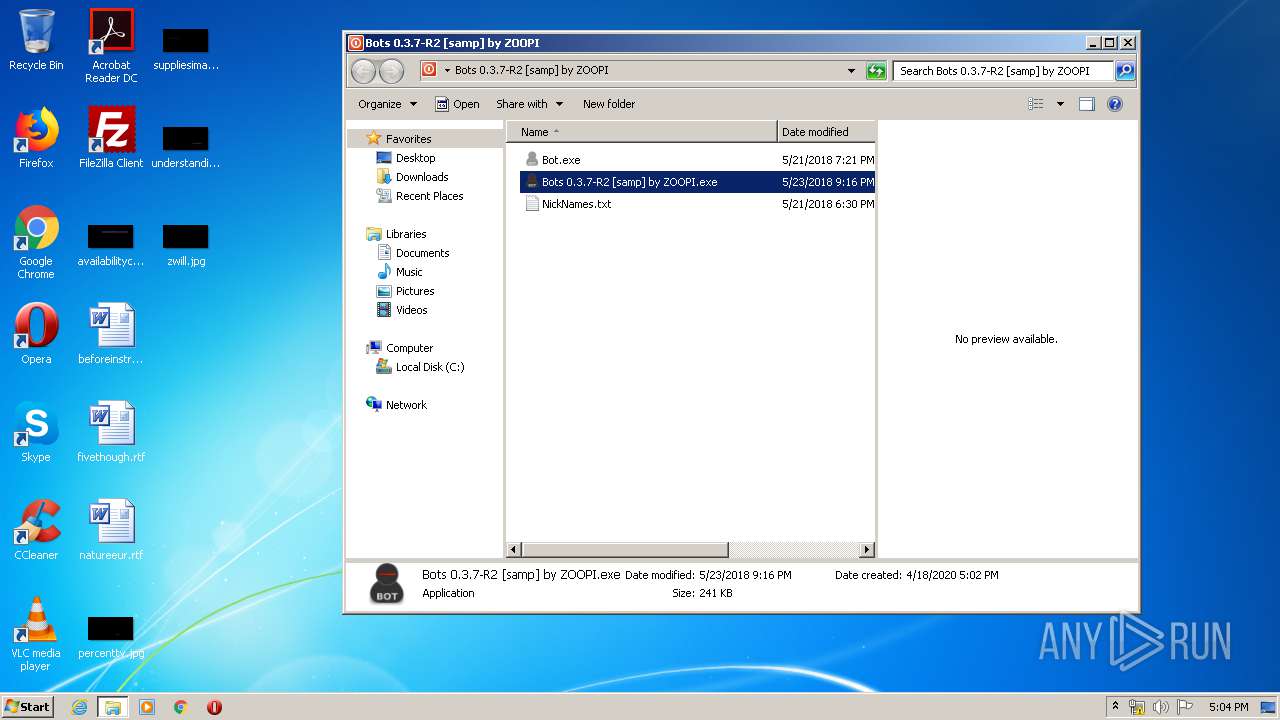
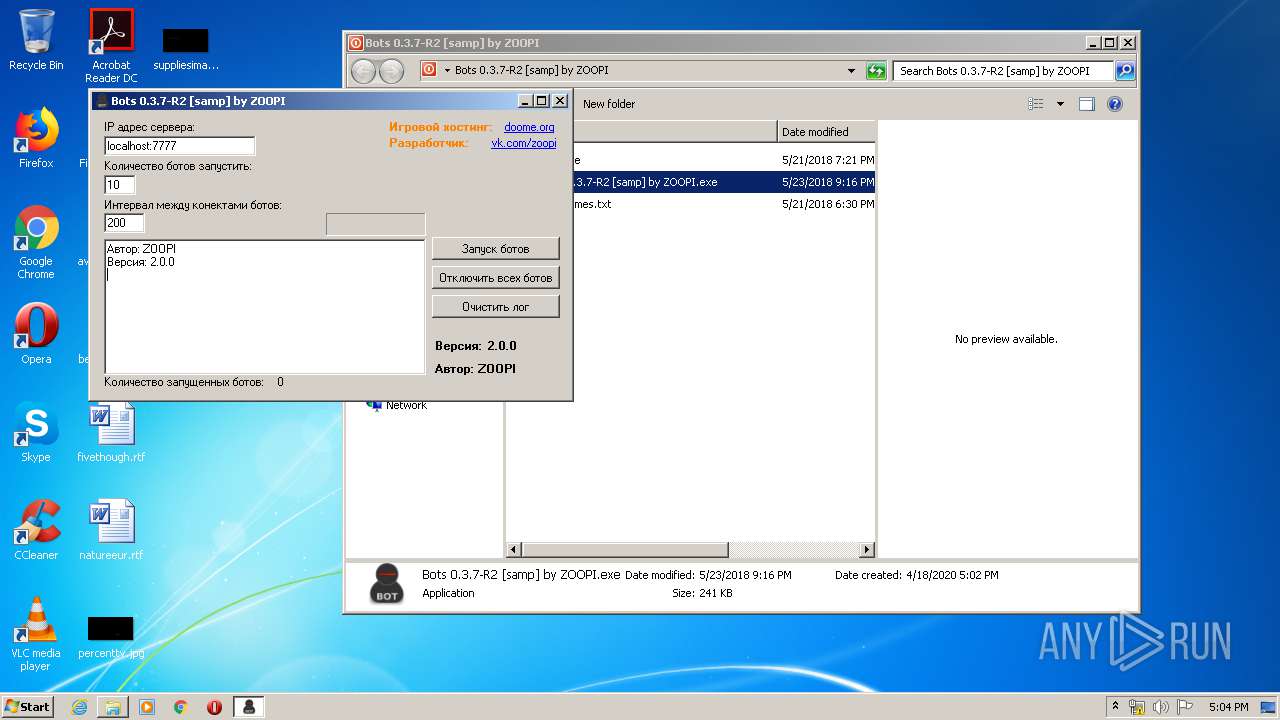
| 1784 | "C:\Users\admin\Desktop\Bots 0.3.7-R2 [samp] by ZOOPI\Bots 0.3.7-R2 [samp] by ZOOPI.exe" | C:\Users\admin\Desktop\Bots 0.3.7-R2 [samp] by ZOOPI\Bots 0.3.7-R2 [samp] by ZOOPI.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Bots Exit code: 0 Version: 2.0.0 Modules
| |||||||||||||||
| 1940 | "C:\Users\admin\Desktop\Bots 0.3.7-R2 [samp] by ZOOPI\Bot.exe" | C:\Users\admin\Desktop\Bots 0.3.7-R2 [samp] by ZOOPI\Bot.exe | Bots 0.3.7-R2 [samp] by ZOOPI.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 2312 | "C:\Users\admin\Desktop\Bots 0.3.7-R2 [samp] by ZOOPI\Bot.exe" | C:\Users\admin\Desktop\Bots 0.3.7-R2 [samp] by ZOOPI\Bot.exe | Bots 0.3.7-R2 [samp] by ZOOPI.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 2356 | "C:\Users\admin\Desktop\Bots 0.3.7-R2 [samp] by ZOOPI\Bot.exe" | C:\Users\admin\Desktop\Bots 0.3.7-R2 [samp] by ZOOPI\Bot.exe | Bots 0.3.7-R2 [samp] by ZOOPI.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 2428 | "C:\Users\admin\Desktop\Bots 0.3.7-R2 [samp] by ZOOPI\Bot.exe" | C:\Users\admin\Desktop\Bots 0.3.7-R2 [samp] by ZOOPI\Bot.exe | Bots 0.3.7-R2 [samp] by ZOOPI.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 2432 | "C:\Users\admin\Desktop\Bots 0.3.7-R2 [samp] by ZOOPI\Bot.exe" | C:\Users\admin\Desktop\Bots 0.3.7-R2 [samp] by ZOOPI\Bot.exe | Bots 0.3.7-R2 [samp] by ZOOPI.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 2568 | "C:\Users\admin\Desktop\Bots 0.3.7-R2 [samp] by ZOOPI\Bots 0.3.7-R2 [samp] by ZOOPI.exe" | C:\Users\admin\Desktop\Bots 0.3.7-R2 [samp] by ZOOPI\Bots 0.3.7-R2 [samp] by ZOOPI.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Bots Exit code: 0 Version: 2.0.0 Modules
| |||||||||||||||
Total events
688
Read events
661
Write events
27
Delete events
0
Modification events
| (PID) Process: | (3148) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3148) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3148) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3148) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\autoonline.zip | |||
| (PID) Process: | (3148) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3148) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3148) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3148) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3148) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3148) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
0
Suspicious files
0
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3148 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3148.4625\Bots 0.3.7-R2 [samp] by ZOOPI\Bot.exe | — | |
MD5:— | SHA256:— | |||
| 3148 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3148.4625\Bots 0.3.7-R2 [samp] by ZOOPI\Bots 0.3.7-R2 [samp] by ZOOPI.exe | — | |
MD5:— | SHA256:— | |||
| 3148 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3148.4625\Bots 0.3.7-R2 [samp] by ZOOPI\desktop.ini | — | |
MD5:— | SHA256:— | |||
| 3148 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3148.4625\Bots 0.3.7-R2 [samp] by ZOOPI\NickNames.txt | — | |
MD5:— | SHA256:— | |||
| 1784 | Bots 0.3.7-R2 [samp] by ZOOPI.exe | C:\Users\admin\Desktop\Bots 0.3.7-R2 [samp] by ZOOPI\Bot.xml | text | |
MD5:— | SHA256:— | |||
| 2568 | Bots 0.3.7-R2 [samp] by ZOOPI.exe | C:\Users\admin\Desktop\Bots 0.3.7-R2 [samp] by ZOOPI\Bot.xml | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
63
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3948 | Bot.exe | 193.70.126.129:4028 | — | OVH SAS | PL | unknown |
2432 | Bot.exe | 193.70.126.129:4028 | — | OVH SAS | PL | unknown |
1524 | Bot.exe | 193.70.126.129:4028 | — | OVH SAS | PL | unknown |
3344 | Bot.exe | 193.70.126.129:4028 | — | OVH SAS | PL | unknown |
3684 | Bot.exe | 193.70.126.129:4028 | — | OVH SAS | PL | unknown |
2884 | Bot.exe | 193.70.126.129:4028 | — | OVH SAS | PL | unknown |
4004 | Bot.exe | 193.70.126.129:4028 | — | OVH SAS | PL | unknown |
2612 | Bot.exe | 193.70.126.129:4028 | — | OVH SAS | PL | unknown |
3284 | Bot.exe | 193.70.126.129:4028 | — | OVH SAS | PL | unknown |
2312 | Bot.exe | 193.70.126.129:4028 | — | OVH SAS | PL | unknown |