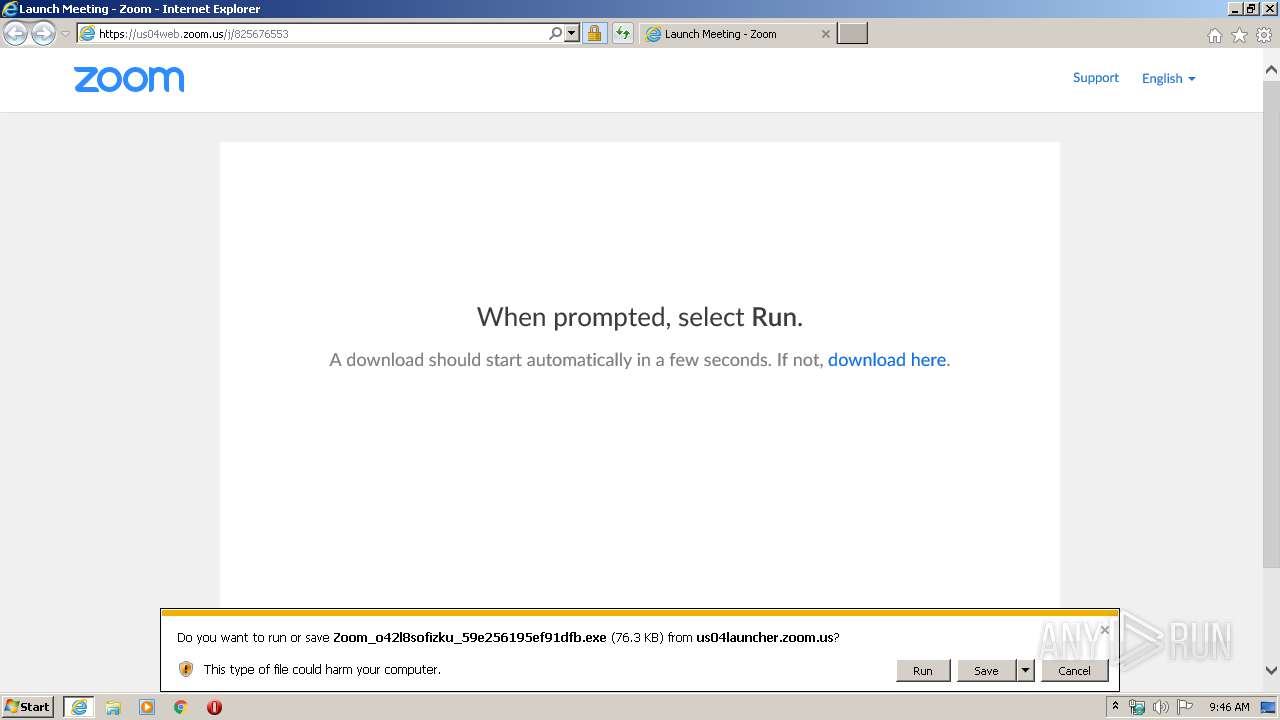
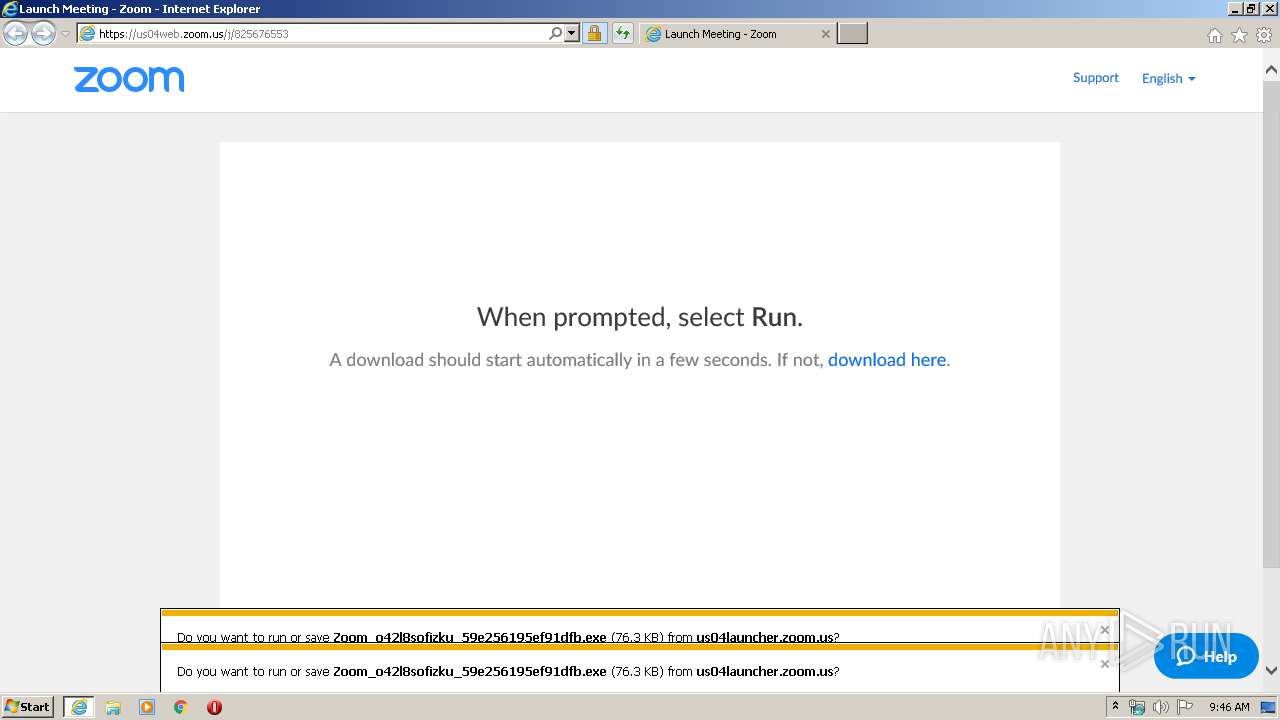
| URL: | https://us04web.zoom.us/j/825676553 |
| Full analysis: | https://app.any.run/tasks/9bf098db-6f6a-4be8-8274-37c3aa9e295a |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2020, 08:45:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 77672C80F5BE3AA0D44F6721B50FC5FC |
| SHA1: | 0B810051294F2BEC8C412BF89EF9A3FDCD7B92DB |
| SHA256: | 3F6CB59CF5EC92E03E41703320FC281ED35EF53031964D0CD49D27947F306055 |
| SSDEEP: | 3:N8VeKILQN4G6Wn:2j94G9 |
MALICIOUS
Application was dropped or rewritten from another process
- Zoom_o42l8sofizku_59e256195ef91dfb.exe (PID: 2492)
- Installer.exe (PID: 680)
- Installer.exe (PID: 1684)
- zm5BD1.tmp (PID: 1684)
- Zoom.exe (PID: 2608)
- Zoom.exe (PID: 3548)
- Zoom.exe (PID: 2816)
- Zoom.exe (PID: 572)
Loads dropped or rewritten executable
- Installer.exe (PID: 680)
- Zoom.exe (PID: 2608)
- Zoom.exe (PID: 2816)
- Zoom.exe (PID: 3548)
- Zoom.exe (PID: 572)
Changes settings of System certificates
- Zoom_o42l8sofizku_59e256195ef91dfb.exe (PID: 2492)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 3616)
- iexplore.exe (PID: 1720)
- Zoom_o42l8sofizku_59e256195ef91dfb.exe (PID: 2492)
- Installer.exe (PID: 680)
Reads Internet Cache Settings
- Zoom_o42l8sofizku_59e256195ef91dfb.exe (PID: 2492)
Creates files in the user directory
- Zoom_o42l8sofizku_59e256195ef91dfb.exe (PID: 2492)
- Zoom.exe (PID: 2608)
- Installer.exe (PID: 680)
- Zoom.exe (PID: 3548)
- Zoom.exe (PID: 2816)
- Zoom.exe (PID: 572)
Application launched itself
- Installer.exe (PID: 680)
- Zoom.exe (PID: 2608)
Creates a software uninstall entry
- Installer.exe (PID: 680)
Changes IE settings (feature browser emulation)
- Installer.exe (PID: 680)
Starts application with an unusual extension
- Zoom_o42l8sofizku_59e256195ef91dfb.exe (PID: 2492)
Modifies the open verb of a shell class
- Installer.exe (PID: 680)
Starts itself from another location
- Zoom_o42l8sofizku_59e256195ef91dfb.exe (PID: 2492)
Adds / modifies Windows certificates
- Zoom_o42l8sofizku_59e256195ef91dfb.exe (PID: 2492)
INFO
Creates files in the user directory
- iexplore.exe (PID: 3616)
- iexplore.exe (PID: 1720)
Reads Internet Cache Settings
- iexplore.exe (PID: 1720)
- iexplore.exe (PID: 3616)
Changes internet zones settings
- iexplore.exe (PID: 1720)
Reads internet explorer settings
- iexplore.exe (PID: 3616)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1720)
Reads settings of System Certificates
- iexplore.exe (PID: 1720)
- Installer.exe (PID: 680)
- Zoom.exe (PID: 572)
- Zoom_o42l8sofizku_59e256195ef91dfb.exe (PID: 2492)
Dropped object may contain Bitcoin addresses
- Installer.exe (PID: 680)
Changes settings of System certificates
- iexplore.exe (PID: 1720)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1720)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
48
Monitored processes
10
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 572 | Zoom.exe --action=uploadFeedback | C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe | — | Zoom.exe | |||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Exit code: 0 Version: 4,6,19178,0323 Modules
| |||||||||||||||
| 680 | "C:\Users\admin\AppData\Roaming\Zoom\ZoomDownload\Installer.exe" ZInstaller --conf.mode=silent --ipc_wnd=262536 | C:\Users\admin\AppData\Roaming\Zoom\ZoomDownload\Installer.exe | Zoom_o42l8sofizku_59e256195ef91dfb.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Installer Exit code: 0 Version: 4,6,19178,0323 Modules
| |||||||||||||||
| 1684 | "C:\Users\admin\AppData\Local\Temp\zm5BD1.tmp" -DAF8C715436E44649F1312698287E6A5=C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\Zoom_o42l8sofizku_59e256195ef91dfb.exe | C:\Users\admin\AppData\Local\Temp\zm5BD1.tmp | — | Zoom_o42l8sofizku_59e256195ef91dfb.exe | |||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Opener Exit code: 0 Version: 4,6,19178,0323 Modules
| |||||||||||||||
| 1684 | "C:\Users\admin\AppData\Roaming\Zoom\ZoomDownload\Installer.exe" /addfwexception --bin_home="C:\Users\admin\AppData\Roaming\Zoom\bin" | C:\Users\admin\AppData\Roaming\Zoom\ZoomDownload\Installer.exe | Installer.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: HIGH Description: Zoom Installer Exit code: 0 Version: 4,6,19178,0323 Modules
| |||||||||||||||
| 1720 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://us04web.zoom.us/j/825676553" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2492 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\Zoom_o42l8sofizku_59e256195ef91dfb.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\Zoom_o42l8sofizku_59e256195ef91dfb.exe | iexplore.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Opener Exit code: 0 Version: 4,6,19178,0323 Modules
| |||||||||||||||
| 2608 | "C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe" "--url=zoommtg://win.launch?action=join&browser=msie&confid=dXNzPTU2NWNlNWI3LnhXUUdIRjV6NnlzaGFPdmdLVGlPRTZsZkdjcWNsWkJPcXlnOGNCUHRiRmYwbnVMd3RJTjBKb2REWDlmNDdBazZSdkwxWkpzRHZYUmxFczEyUUg1S0ZBJTNEJTNEJnRpZD03NmVmNDFhNDM2YzI0MDgwOGRjZmJiODhjZWJmYjExZg%3D%3D&confno=825676553&mcv=0.92.11227.0929&zc=0" | C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe | Zoom_o42l8sofizku_59e256195ef91dfb.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Exit code: 0 Version: 4,6,19178,0323 Modules
| |||||||||||||||
| 2816 | Zoom.exe --action=uploadFeedback | C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe | — | Zoom.exe | |||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Exit code: 0 Version: 4,6,19178,0323 Modules
| |||||||||||||||
| 3548 | C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe --action=join --runaszvideo=TRUE | C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe | Zoom.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Exit code: 0 Version: 4,6,19178,0323 Modules
| |||||||||||||||
| 3616 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1720 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
11 263
Read events
2 364
Write events
5 990
Delete events
2 909
Modification events
| (PID) Process: | (1720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 3775593672 | |||
| (PID) Process: | (1720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30803768 | |||
| (PID) Process: | (1720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
91
Suspicious files
76
Text files
69
Unknown types
39
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1720 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3616 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab965C.tmp | — | |
MD5:— | SHA256:— | |||
| 3616 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar965D.tmp | — | |
MD5:— | SHA256:— | |||
| 3616 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\I62BBKP0.txt | — | |
MD5:— | SHA256:— | |||
| 3616 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\4IT734EV.txt | — | |
MD5:— | SHA256:— | |||
| 3616 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\137XNXRM.txt | — | |
MD5:— | SHA256:— | |||
| 3616 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\PEY6WIWY.txt | — | |
MD5:— | SHA256:— | |||
| 3616 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C5FD5BF0CE6372B1CAFE381FD0BC969C | der | |
MD5:— | SHA256:— | |||
| 3616 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | binary | |
MD5:— | SHA256:— | |||
| 3616 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
77
DNS requests
39
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3616 | iexplore.exe | GET | 200 | 192.124.249.41:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
3616 | iexplore.exe | GET | 200 | 52.222.149.213:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
3616 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEBPqKHBb9OztDDZjCYBhQzY%3D | US | der | 471 b | whitelisted |
3616 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
3616 | iexplore.exe | GET | 200 | 172.217.23.131:80 | http://ocsp.pki.goog/gts1o1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEFeh1L3VO0beCAAAAAAyCgc%3D | US | der | 471 b | whitelisted |
3616 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQC5UUQDFilM79r2jgo50n2A | US | der | 472 b | whitelisted |
3616 | iexplore.exe | GET | 200 | 192.124.249.41:80 | http://crl.godaddy.com/gdroot.crl | US | der | 429 b | whitelisted |
3616 | iexplore.exe | GET | 200 | 52.222.149.182:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
3616 | iexplore.exe | GET | 200 | 172.217.23.131:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
3616 | iexplore.exe | GET | 200 | 52.222.149.182:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3616 | iexplore.exe | 3.235.82.211:443 | us04web.zoom.us | — | US | unknown |
1720 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3616 | iexplore.exe | 192.124.249.41:80 | ocsp.godaddy.com | Sucuri | US | suspicious |
3616 | iexplore.exe | 52.222.158.54:443 | us04st1.zoom.us | Amazon.com, Inc. | US | malicious |
3616 | iexplore.exe | 104.18.72.113:443 | static.zdassets.com | Cloudflare Inc | US | shared |
3616 | iexplore.exe | 52.222.158.77:443 | us04st1.zoom.us | Amazon.com, Inc. | US | whitelisted |
3616 | iexplore.exe | 52.222.149.182:80 | o.ss2.us | Amazon.com, Inc. | US | whitelisted |
3616 | iexplore.exe | 151.139.128.14:80 | ocsp.usertrust.com | Highwinds Network Group, Inc. | US | suspicious |
3616 | iexplore.exe | 216.58.210.14:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
3616 | iexplore.exe | 52.222.149.213:80 | ocsp.rootg2.amazontrust.com | Amazon.com, Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
us04web.zoom.us |
| whitelisted |
ocsp.godaddy.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.godaddy.com |
| whitelisted |
us04st1.zoom.us |
| whitelisted |
us04st2.zoom.us |
| whitelisted |
us04st3.zoom.us |
| whitelisted |
static.ada.support |
| whitelisted |
static.zdassets.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Installer.exe | C:\Users\admin\AppData\Roaming\Zoom\zoom_install_src |
Installer.exe | |
Installer.exe | C:\Users\admin\AppData\Roaming\Zoom\zoom_install_src |
Installer.exe | [ProductPathHelper::RecursiveRemoveDirA] Path is: |
Installer.exe | C:\Users\admin\AppData\Roaming\Zoom\uninstall |
Installer.exe | |
Installer.exe | [ProductPathHelper::RecursiveRemoveDirA] Path is: |
Installer.exe | C:\Users\admin\AppData\Roaming\Zoom\bin |
Installer.exe | |
Installer.exe | C:\Users\admin\AppData\Roaming\Zoom\zoom_install_src\ |