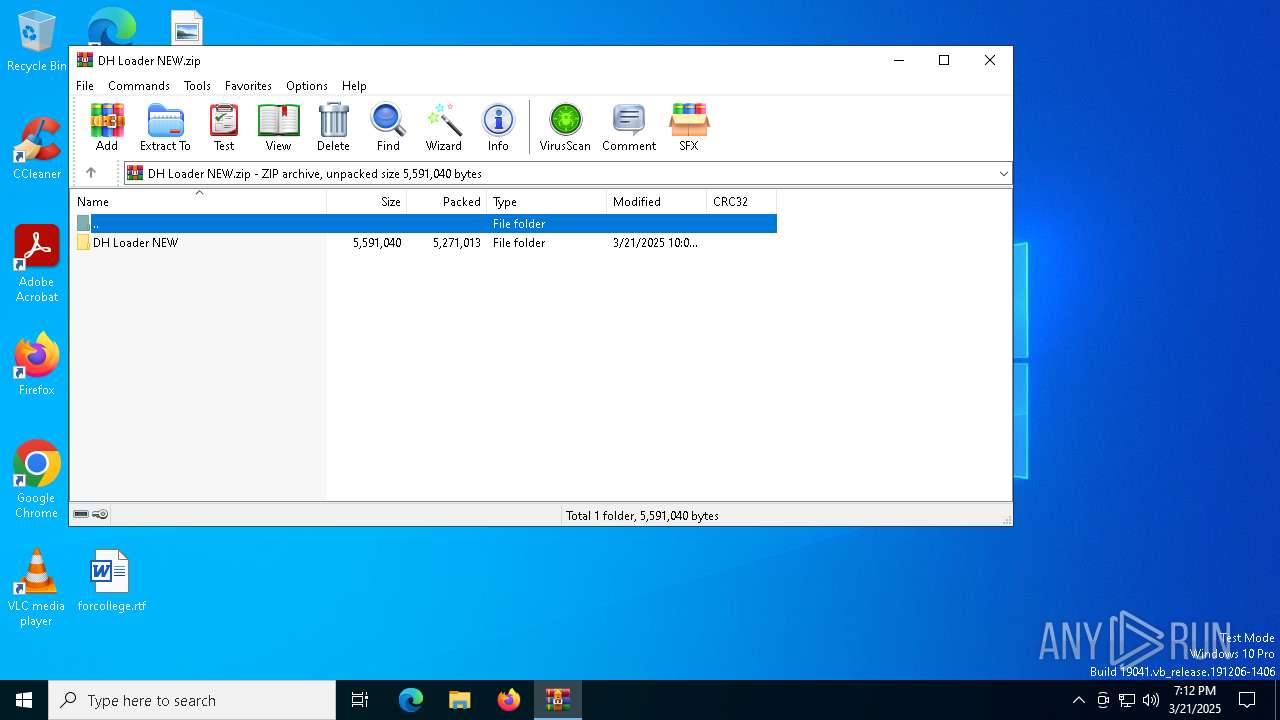
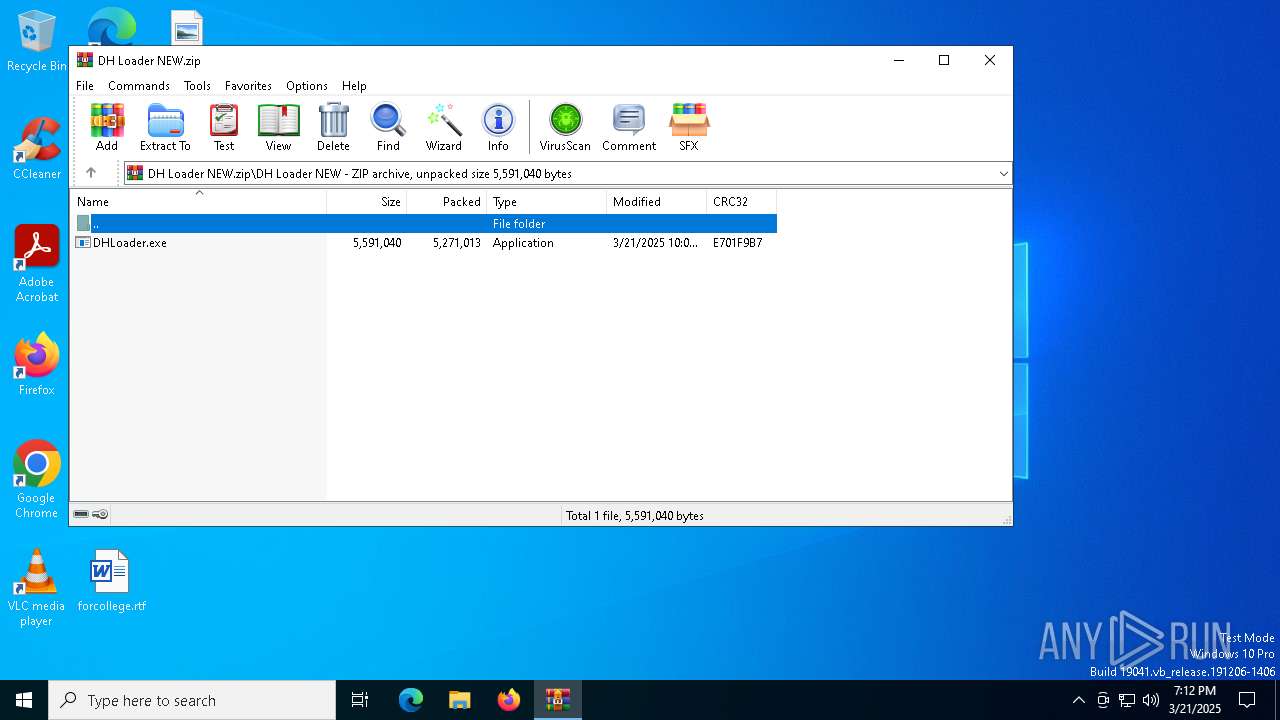
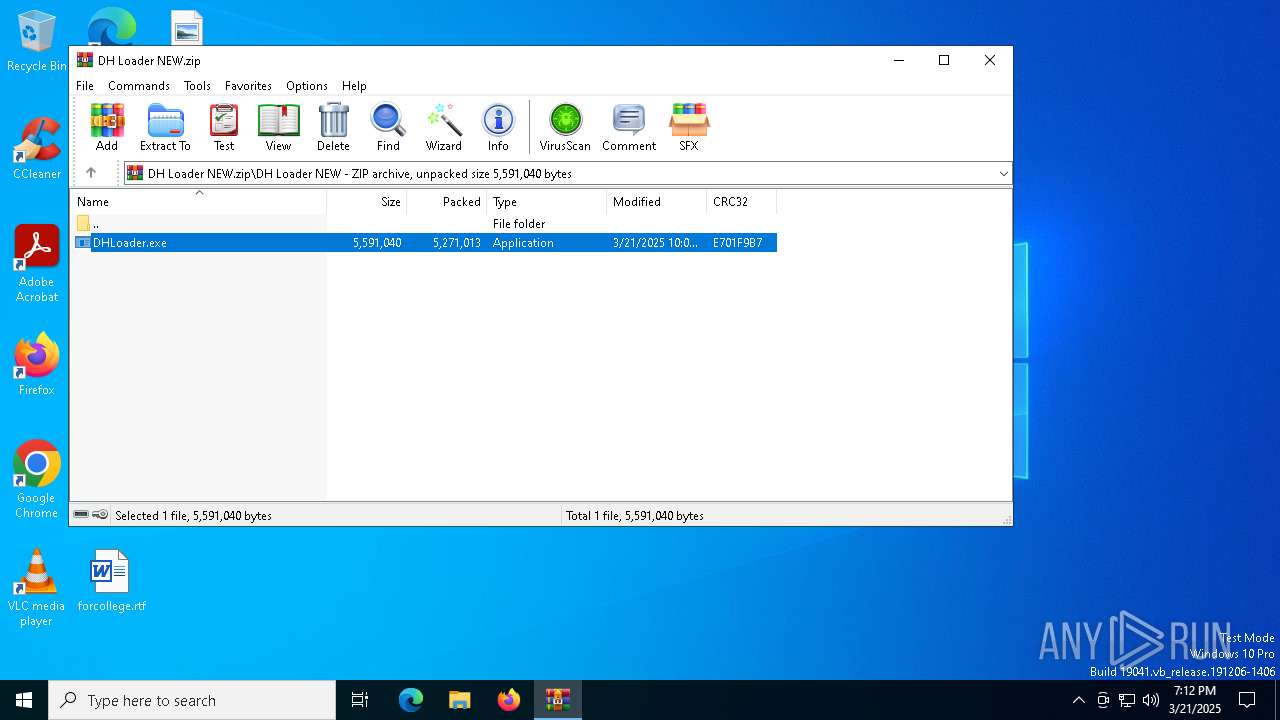
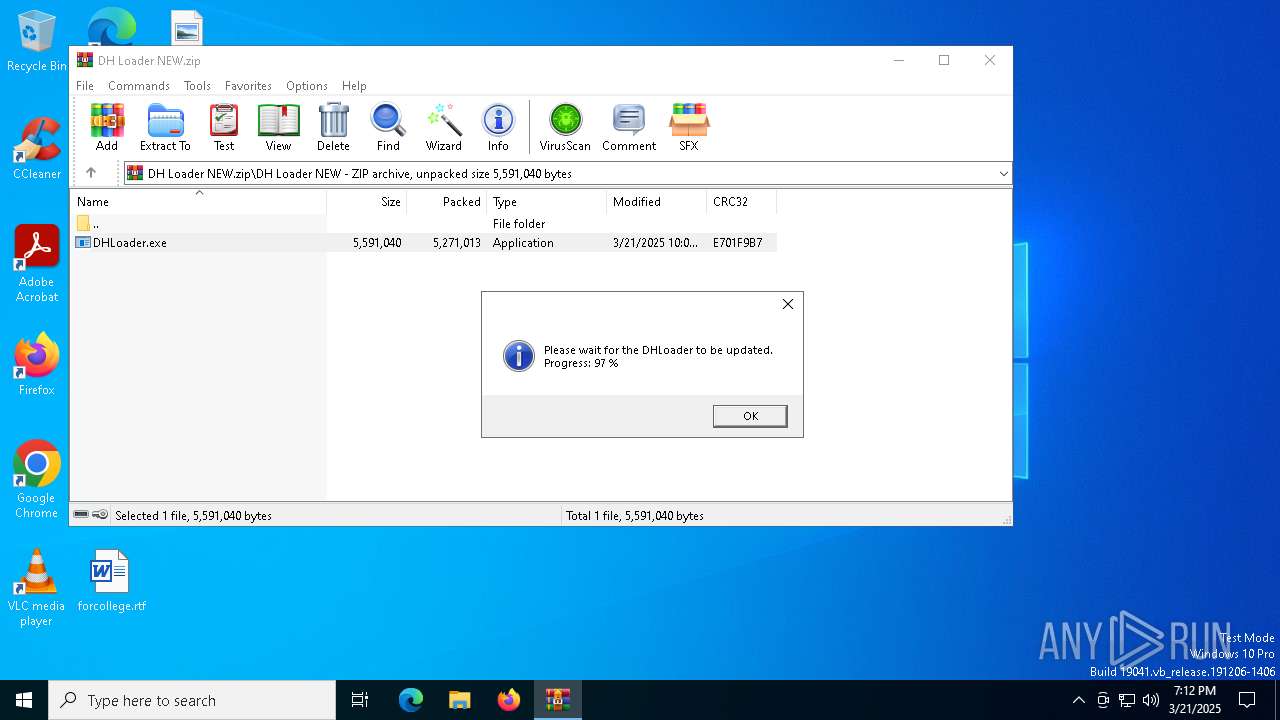
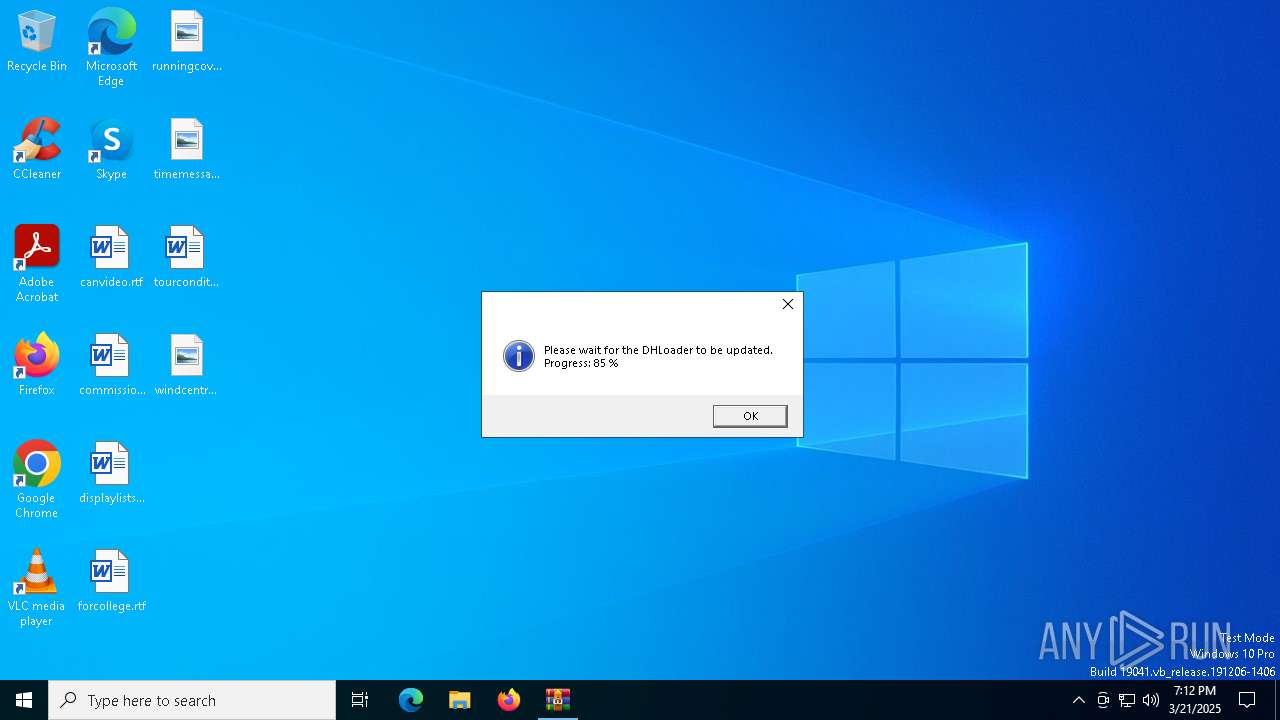
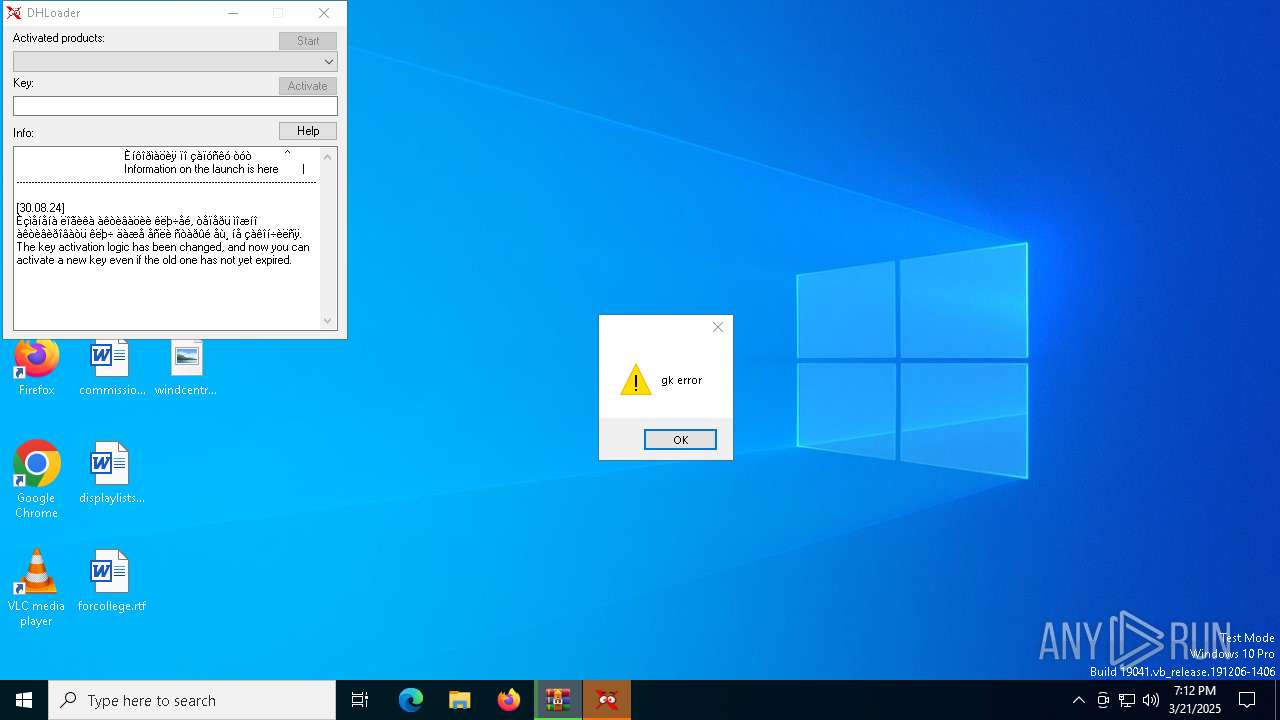
| File name: | DH Loader NEW.zip |
| Full analysis: | https://app.any.run/tasks/f9404dfd-553a-412f-89c5-4f567ca80fe7 |
| Verdict: | Malicious activity |
| Analysis date: | March 21, 2025, 19:12:06 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 1356A2EB545903855B867D900A909FEE |
| SHA1: | 39B567A20EC00FFA422A62C385B8133FA20840D4 |
| SHA256: | 3F6B4B9B46862865DC13E494687F61FBB870AE5ADE2BD99EB5E69FDF635C265E |
| SSDEEP: | 98304:i9dtRBGpF2+w9hxRY7h50NagknbBOz64XLC1IZADRuzJ1bJX1ku5k7DZhMXfW4br:vL4T7JT |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6044)
SUSPICIOUS
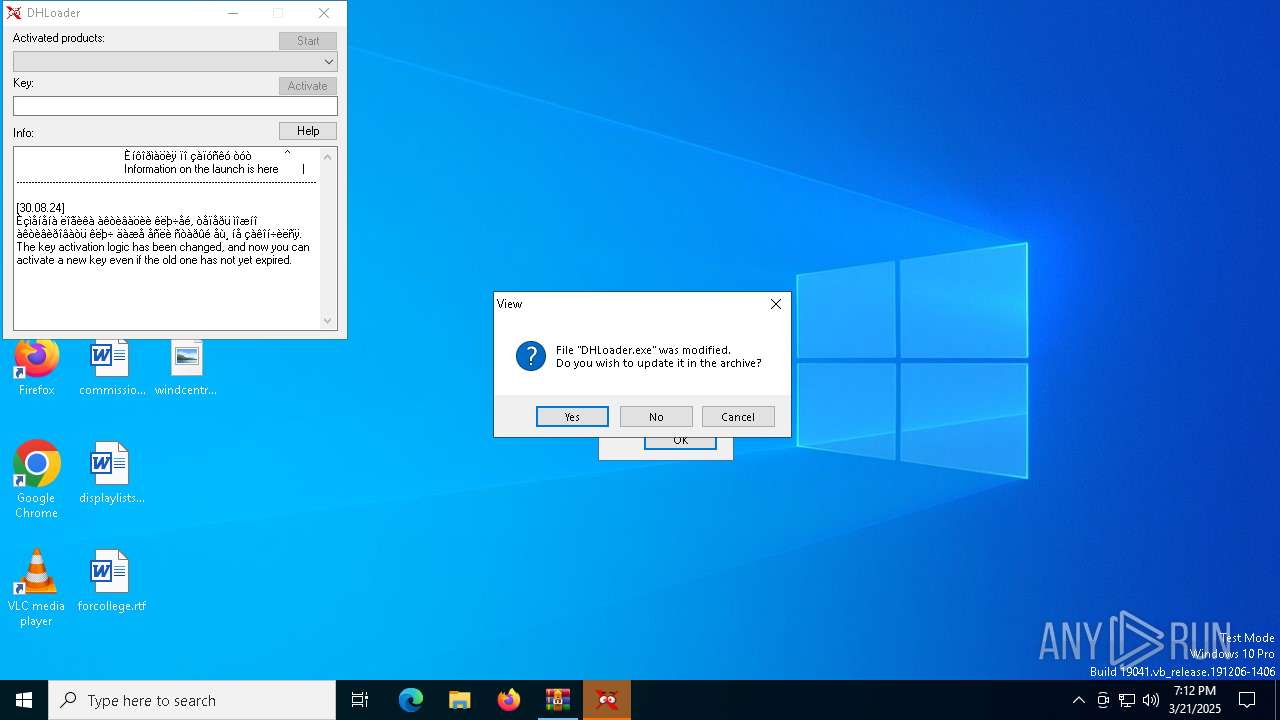
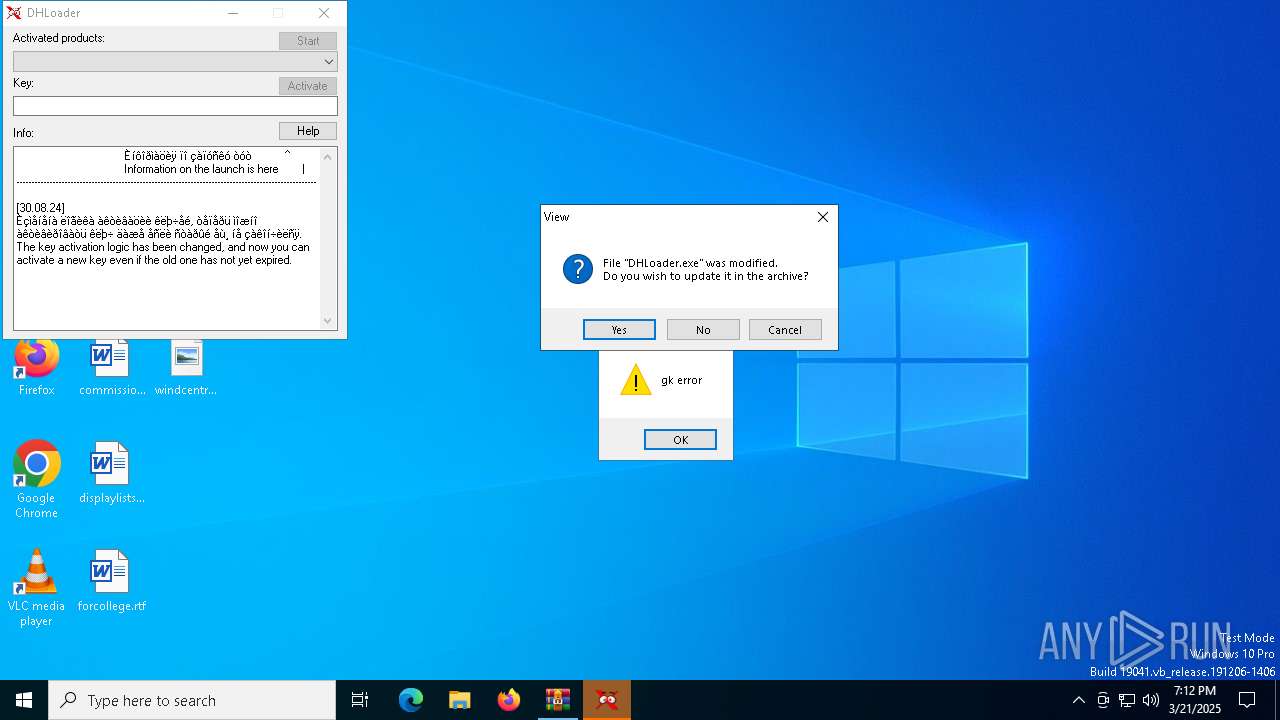
Executable content was dropped or overwritten
- DHLoader.exe (PID: 6876)
Connects to unusual port
- DHLoader.exe (PID: 6876)
- DHLoader.exe (PID: 7396)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6044)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6044)
Checks supported languages
- DHLoader.exe (PID: 7396)
- DHLoader.exe (PID: 6876)
Reads the computer name
- DHLoader.exe (PID: 6876)
- DHLoader.exe (PID: 7396)
Create files in a temporary directory
- DHLoader.exe (PID: 6876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:03:21 22:09:14 |
| ZipCRC: | 0xe701f9b7 |
| ZipCompressedSize: | 5271013 |
| ZipUncompressedSize: | 5591040 |
| ZipFileName: | DH Loader NEW/DHLoader.exe |
Total processes
136
Monitored processes
6
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2656 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6044 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\DH Loader NEW.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6808 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6876 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6044.14709\DH Loader NEW\DHLoader.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6044.14709\DH Loader NEW\DHLoader.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7396 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6044.14709\DH Loader NEW\DHLoader.exe" "C:\Users\admin\AppData\Local\Temp\Rar$EXa6044.14709\DH Loader NEW\DHLoader.tmp" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6044.14709\DH Loader NEW\DHLoader.exe | DHLoader.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
3 083
Read events
3 068
Write events
15
Delete events
0
Modification events
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\DH Loader NEW.zip | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
3
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6876 | DHLoader.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6044.14709\DH Loader NEW\DHLoader.tmp | executable | |
MD5:5B51C39031153A67715BEFAB4EC6AC40 | SHA256:94386FE3BE5412D46A72D64B1A42130626540C818DB429A3D63A1B19D05F6132 | |||
| 6044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\__rzi_6044.16706 | compressed | |
MD5:26A4A1723DEABC316AE23CFBCB4E57C6 | SHA256:F6E3DD45C0B14CAF8481D5BB8578582B0899F3059A546BE700754541FE07F469 | |||
| 6044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6044.14709\DH Loader NEW\DHLoader.exe | executable | |
MD5:5B51C39031153A67715BEFAB4EC6AC40 | SHA256:94386FE3BE5412D46A72D64B1A42130626540C818DB429A3D63A1B19D05F6132 | |||
| 6876 | DHLoader.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6044.14709\DH Loader NEW\DHLoader.exe | executable | |
MD5:AAB85DC73386CC3169D6AE7193CCF428 | SHA256:26DC38AB5B3DA1BA611F331540B2D2C98F393DE1BF88F9D1379FCBD0A5FC1136 | |||
| 6044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\DH Loader NEW.zip | compressed | |
MD5:26A4A1723DEABC316AE23CFBCB4E57C6 | SHA256:F6E3DD45C0B14CAF8481D5BB8578582B0899F3059A546BE700754541FE07F469 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
26
DNS requests
14
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.168.200:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7864 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7864 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1228 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.16.168.200:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6876 | DHLoader.exe | 213.242.56.89:48711 | crvsx.zapto.org | Rostelecom | RU | suspicious |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1228 | backgroundTaskHost.exe | 20.223.36.55:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
crvsx.zapto.org |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DNS Query to DynDNS Domain *.zapto .org |