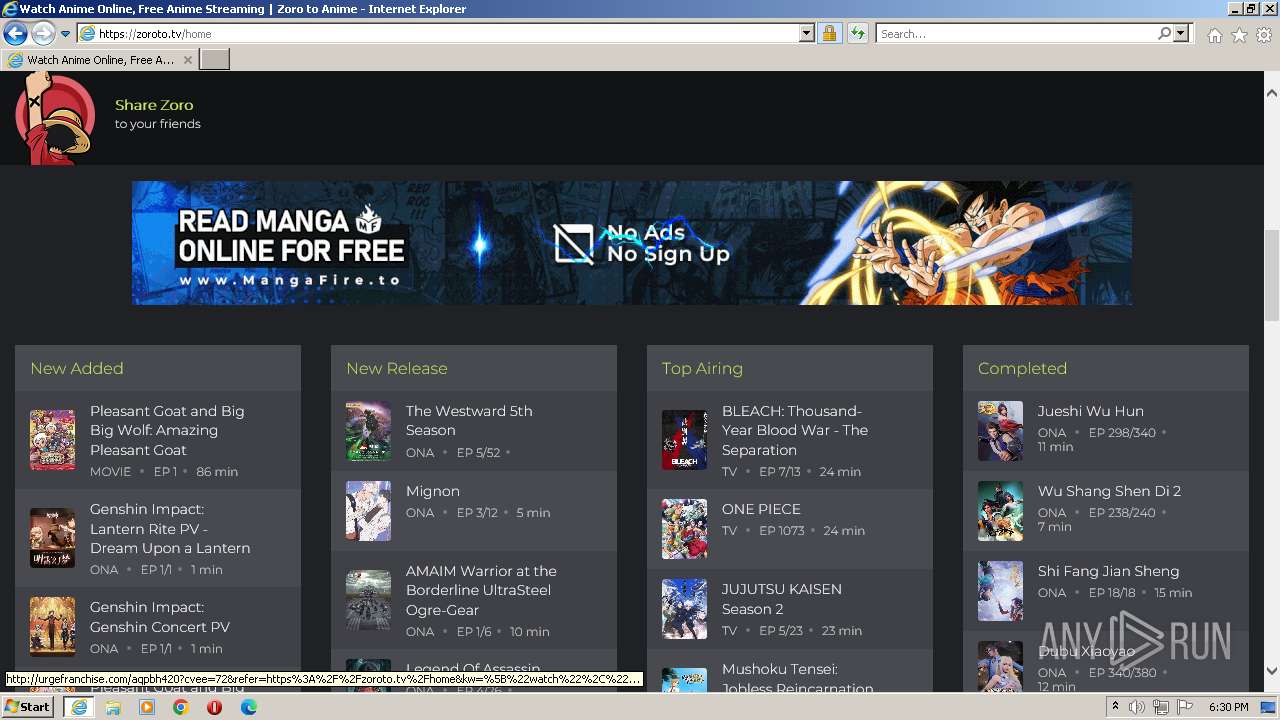
| URL: | https://zoroto.tv/ |
| Full analysis: | https://app.any.run/tasks/a1d2d7f0-70ab-498c-8802-ab9df8e5866c |
| Verdict: | Malicious activity |
| Analysis date: | August 21, 2023, 17:29:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | FDEECF1307598972D6F7DEA35A8D1287 |
| SHA1: | 691C9C3D2E50B64176EB342E83AD9B5B3BFC6943 |
| SHA256: | 3F456748739A45F5A8405A566580AB82CDDC1F44F4B4F2F7E51548D4C7E3CD38 |
| SSDEEP: | 3:N8DQRG:2DQA |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 2968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
38
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2356 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2968 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2968 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://zoroto.tv/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
15 417
Read events
15 353
Write events
64
Delete events
0
Modification events
| (PID) Process: | (2968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
50
Text files
89
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2356 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:CFBC16E33DCBEF6F773F0F79AF528F45 | SHA256:F0937890FB1053069BAAC97B7992C6D22CB74CAE20317FC05D51070D96950FFA | |||
| 2356 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\all[1].js | text | |
MD5:84B839034DBD808D7FC3552367C3228B | SHA256:6121BC3CA548648E8A020E27E524C7CEC9DFFBE985A05D4BF1B0AA7D68E4A00E | |||
| 2356 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 2356 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:AA42CC0C0E30C49FB543088C89828EE3 | SHA256:6267F3A42C54EC9EF4CE63F40B2EA2188138651B2E019AAADF73025AE707255E | |||
| 2356 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\all[1].css | text | |
MD5:256D2026BE886DA931B6E000EA6E1063 | SHA256:9BB09127327CEDD9282C5B7AEED42B6A342925BE32AA5275DE9F9CD1B4168714 | |||
| 2356 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\FCJNW27A.htm | html | |
MD5:22E38D92D021306FC3D93B367B23613B | SHA256:3B7F15A28EDB78F11339C64F5E5AE7210060493886EBCCF41C3958AF64356F50 | |||
| 2356 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\zoro-min[1].png | image | |
MD5:794EB1B676BD536F17B84053A3860E3F | SHA256:68C9A3D128D86590A87F432280CB5560C8DCC14BA1485FF4DDE97F4DDDFCAA17 | |||
| 2356 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\82CB34DD3343FE727DF8890D352E0D8F | binary | |
MD5:716658387DB27B394CD4C4DE15371324 | SHA256:BC60946EBCD78273D54441DE3C6D0F25D1258952D23DCBD1A50D294A0F82F983 | |||
| 2356 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:AEB9C88176EB85A81BE53114EEFE6676 | SHA256:08F0622C3B7EF4379263434B8567B04FEC9A1F4C164FB0C18E81A24E6FF11101 | |||
| 2356 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\logo[1].png | image | |
MD5:4A1EA6D74259DEFA9844A7532B0AF499 | SHA256:E4AE8060A118BAA2EBAF5E698C7226EE6F106FAB592CFF2A01FFF00C456D330B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
148
DNS requests
34
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2356 | iexplore.exe | GET | — | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDGEBdwFpkQsQqVJE7B7pj%2F | US | — | — | whitelisted |
2968 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f268107cd4c44577 | US | — | — | whitelisted |
2356 | iexplore.exe | GET | 200 | 8.253.207.121:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?a705e9c1c7b6a8a0 | US | compressed | 62.3 Kb | whitelisted |
2968 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | US | binary | 471 b | whitelisted |
2356 | iexplore.exe | GET | 200 | 95.101.54.131:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgPVWE%2BnejDRazUtBeMXKjNB3Q%3D%3D | DE | binary | 503 b | shared |
2356 | iexplore.exe | GET | 200 | 23.56.202.135:80 | http://x1.c.lencr.org/ | GB | binary | 717 b | whitelisted |
2356 | iexplore.exe | GET | 200 | 95.101.54.131:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgTd%2Br4%2B06%2B3rxtltgrukKjJHg%3D%3D | DE | binary | 503 b | shared |
2356 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | binary | 1.41 Kb | whitelisted |
2356 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://crl3.digicert.com/Omniroot2025.crl | US | binary | 7.78 Kb | whitelisted |
2356 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCxveB4eLEIHAqwCg22TKZB | US | binary | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2356 | iexplore.exe | 172.67.167.176:443 | zoroto.tv | CLOUDFLARENET | US | suspicious |
2356 | iexplore.exe | 142.250.181.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
2356 | iexplore.exe | 172.64.102.11:443 | use.fontawesome.com | CLOUDFLARENET | US | unknown |
2356 | iexplore.exe | 104.18.11.207:443 | stackpath.bootstrapcdn.com | CLOUDFLARENET | — | suspicious |
2356 | iexplore.exe | 104.17.25.14:443 | cdnjs.cloudflare.com | CLOUDFLARENET | — | suspicious |
2356 | iexplore.exe | 172.64.194.16:443 | s2.bunnycdn.ru | CLOUDFLARENET | US | suspicious |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2968 | iexplore.exe | 2.23.209.140:443 | www.bing.com | Akamai International B.V. | GB | suspicious |
2356 | iexplore.exe | 18.239.94.91:443 | platform-api.sharethis.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
zoroto.tv |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
stackpath.bootstrapcdn.com |
| whitelisted |
use.fontawesome.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
s2.bunnycdn.ru |
| suspicious |
platform-api.sharethis.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |