| File name: | SQLi Dumper.exe |
| Full analysis: | https://app.any.run/tasks/94c92236-c6ad-4901-8f02-b15f6503db1f |
| Verdict: | Malicious activity |
| Analysis date: | August 27, 2024, 11:42:28 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | E5D3F124126A4B1FAA148FC8ECEDF433 |
| SHA1: | 9514608D9A321E61D12D6BE6F14FD667A22CAF2D |
| SHA256: | 3F3ED131FE2A88B0085F5F2E1C5BCDDA32D7C76BCF3F28F82065048966887706 |
| SSDEEP: | 49152:I9E79IPSSf+mJq8bloOAgGMw3eBNXVvv5/x:rCSSfZrbloyGuBFVnh |
MALICIOUS
Scans artifacts that could help determine the target
- dw20.exe (PID: 6332)
SUSPICIOUS
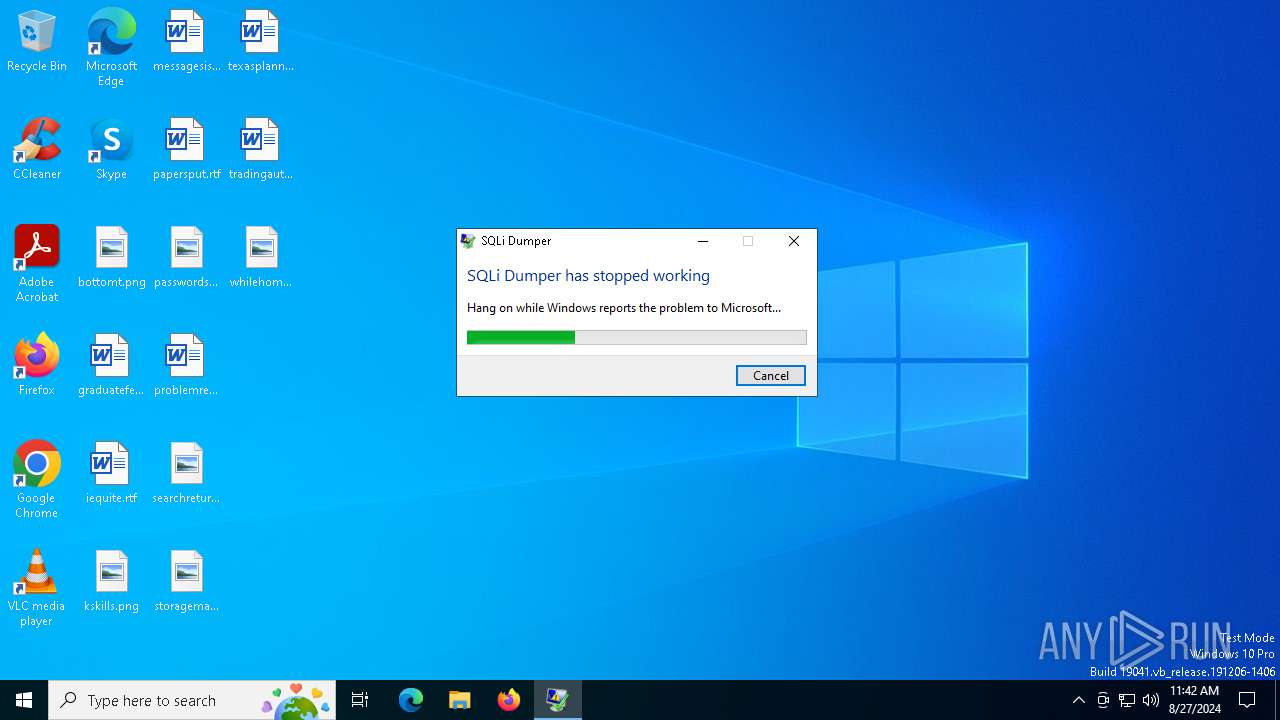
Drops the executable file immediately after the start
- SQLi Dumper.exe (PID: 2068)
Reads the date of Windows installation
- dw20.exe (PID: 6332)
INFO
Checks supported languages
- SQLi Dumper.exe (PID: 2068)
- dw20.exe (PID: 6332)
Reads Environment values
- SQLi Dumper.exe (PID: 2068)
- dw20.exe (PID: 6332)
Reads the machine GUID from the registry
- SQLi Dumper.exe (PID: 2068)
- dw20.exe (PID: 6332)
Reads product name
- dw20.exe (PID: 6332)
Process checks computer location settings
- dw20.exe (PID: 6332)
Reads CPU info
- dw20.exe (PID: 6332)
Checks proxy server information
- dw20.exe (PID: 6332)
Reads the software policy settings
- dw20.exe (PID: 6332)
Reads the computer name
- SQLi Dumper.exe (PID: 2068)
- dw20.exe (PID: 6332)
Creates files in the program directory
- dw20.exe (PID: 6332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:03:02 14:40:05+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 2227712 |
| InitializedDataSize: | 97280 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x221c3e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.3.0.0 |
| ProductVersionNumber: | 8.3.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | I take NO responsibility for what you do with this tool. Use at your OWN risk!! |
| CompanyName: | c4rl0s@jabber.ru |
| FileDescription: | SQLi Dumper |
| FileVersion: | 8.3.0.0 |
| InternalName: | SQLi Dumper.exe |
| LegalCopyright: | c4rl0s.pt@gmail.com |
| LegalTrademarks: | - |
| OriginalFileName: | SQLi Dumper.exe |
| ProductName: | SQLi Dumper |
| ProductVersion: | 8.3.0.0 |
| AssemblyVersion: | 8.3.0.0 |
Total processes
121
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2068 | "C:\Users\admin\Downloads\SQLi Dumper.exe" | C:\Users\admin\Downloads\SQLi Dumper.exe | explorer.exe | ||||||||||||
User: admin Company: c4rl0s@jabber.ru Integrity Level: MEDIUM Description: SQLi Dumper Exit code: 3762507597 Version: 8.3.0.0 Modules
| |||||||||||||||
| 6332 | dw20.exe -x -s 1420 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\dw20.exe | SQLi Dumper.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Error Reporting Shim Exit code: 0 Version: 2.0.50727.9149 (WinRelRS6.050727-9100) Modules
| |||||||||||||||
Total events
4 152
Read events
4 146
Write events
6
Delete events
0
Modification events
| (PID) Process: | (6332) dw20.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\IdentityCRL\ClockData |
| Operation: | write | Name: | ClockTimeSeconds |
Value: BBBBCD6600000000 | |||
| (PID) Process: | (6332) dw20.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\IdentityCRL\ClockData |
| Operation: | write | Name: | TickCount |
Value: 1DDF120000000000 | |||
| (PID) Process: | (6332) dw20.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IdentityCRL\Immersive\production\Property |
| Operation: | write | Name: | 00180010F429971D |
Value: 0100000001000000D08C9DDF0115D1118C7A00C04FC297EB0100000042CB6C300049C042863C8A748EF9A2B2000000000200000000001066000000010000200000001886B8788BC23805C1F4B5C6AE95C1D9875471B270B92112FD2CE747BC5CEC8E000000000E800000000200002000000038E9383F0F1B9A620FEFD9B2FDA0E66B0E2200ABA2295CD8A58DF7CFC639DA44800000008D821B2EA0B2A409276EBCBF60DD38B86D4B371ADD1B05C240228C9446C5A48E35E083726E0A3437FD1DF362967B5FAE6E27869036833E83777346EDC6BCC7996F9FFD5914F136FB3096B0938F28B292D1C8EFE7AFC16911BA15BAB0C7586098A056274414D760695E43940BDDF45D2E50219505EB43CA4773CA3F0895700A734000000003A8752863E3409A6216410951F4B186879933388D60E033940546FF9290490E0033AAA878FF1A2591FD2C0072DE3EE214F815C75FC0CAC8296D3698937871DB | |||
| (PID) Process: | (6332) dw20.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IdentityCRL\Immersive\production\Token\{67082621-8D18-4333-9C64-10DE93676363} |
| Operation: | write | Name: | DeviceTicket |
Value: 0100000001000000D08C9DDF0115D1118C7A00C04FC297EB0100000042CB6C300049C042863C8A748EF9A2B200000000020000000000106600000001000020000000D51FDDF287FC5CE6C3D59621338D4D24A3E4251D4A0CBCBC791975AE26EC90B4000000000E8000000002000020000000A9099B0C10DAA5766B24C8F53734687FCC4D4D62EB922E7766E80E703A728B972008000084478043F4F2186F7967A89D0320A69A27F446FAE313F30C6E5606D734671D7BAFB9754B8674FA7A0BBD8F64A0F7F536598A1C6BAF1FE73BBD631C40BECF749800E8964FA13F5CED3A554D407BCA4C37F3B29B57AA1DAFD0A67E963F2E95B523CC2EE9E9F0A06FFCE55EFCA5DFA55AB5A34C016A46278E84FA59D98DDD65F4BF568385EF32BA2DF786AE5B867B3D25AA89E034559DD02B4E2679ED65B8F3529047FEC91291CDD96583B6EF6D8F9A66B19C21805E1FB8F5B35623A0D42AA0D4DAA0DE6CD57C51B6E998C0CEB80287979055C006FD58C89FA0D8DFA34A1149CD137D55F7897082A920AF7632DDB9FB3AF7553EB8E5DC86E0F370A273B0E22DEB0C3EA0128A2005BCBBA80AAB79A2EDB5F8D68EA788D03C30274E0526F372C8A2080840F196E745F7B20B689CBCCD9C14973E17CCCF0FD39E4E93B637D41731E8126C336BD11AB050B80F2DAFA15AB0F13273C89D6C91A1591EFF6F488A2731931E45F394F426C42F88655914896523396A22F99D0BD5DB9D8D630CE6F0B9A4E41DDB25D0A9E342C295ECC4943B9A9811FE491124FB07A4737DED3B66FF482DA5DD2032E8E5CEFF77175BEE9D09685E02C51369EF091130094B2BA8C704231B04FD05564B7696BBB456B134A1494EB74061410E1FD6D7B7CDE3DDD9A39CA4A01F7AFF3939EFDE67EE1B61E294BF93609F797B6270F3845BBA3CE5B02854DA8FD130544139FEB043FD098ED251F702A397A8EC0448C5AD969212A9A772CDF31052FE80D36E7056ED5DC54F00C363EFCA47C6CCFFE2AD9A93D25048FD0F2A958AFC3885B84D737CE408C8441703363165CA68BE8F02A288A1CED92DB03C89E16A17253E1103A927EB9D75E24DF471C6F935F4F49C5E09E66AC3DBB1959A9D8ABBC3D1A58F6064F2161F3666CE583A9F26269CDFD7C5D2963D0DD55C5C9EE2EB1F6A98BE3BADCF8D4B8F00CB9B8B2D0ADF160B4C76CBF814732CB7EC501881C93FFF1AE4EBA720B5BFFBE54A35B2C503CF916C89DF56D11E6FD94CC98CB7806C0277EB24AE19F18C057C2D98E41336E67FF1F7A9D28158F3D16024A4D5D290D49D3CC3C4F00611745FBCE99741E0E1B258DD4F2D8896727A4594E534D485A8DC78BFFABFD753AF136A1F2A5F1346ADA58514BB15B5D51ED7840BD5A7D98DD31CC712B29E855460804788DBE5B53FD10CBE5136761A1D0A7DC617D83B8044BBCF4C48460D373A32A8CD611B70BF1D17E14E71A2A7171A70842D13C83468E851650EE0D27DA997AC1E77FE7B8EB88976B832A63876E864E7A1448131C3F8892BD27C5E918BB425A3FDB5B7B6F561E6DABA0D60CD644471C1F3C9C0634DF380A609731DA775B3A8521DE479F49D17E9CA05B4C87B2CF5171F84D0593B131B3E623C68766A778CFD0F5C4D9E9D9DF381BC76427C57E0A95526A379176ACFBA88B694DFAF3ABAE097FFA8724170A84447A949B7C26F2956BB599EE52E56E0ADB92DBDB70AFEAB918C07E7DDE03DFE87902604A87423BC7DE3F05666C994057B91311B787F5B06976ECDC78FBCA2926D4E2CC48345C46D97BA76FFA6A116C6DA6D6BAC6584ED8983886339658E9F55F74909CD6324E04F178D0E661ACA566AC7356DFCA397D55785E1895985F286FE28E0DC17081AE61E9AFBE9C9BED51A41859F6459591A8EFCBC8812E02FD307B38AFE6CADFE79994822EEE739439B3BE754B3AAD38B3FB7A35586C4E0A30C96F885DDD2CAF22BD9383FDDA2378AA990C2265ED98A45255B10394CFB9F741AC36100D59DEAC4F4F133EA1F70B06B7935CFCCE2305F89B981A2825EC6BAC0D436E754D098D2D5938070C0A6F96D2E908F6EC5EFE8737DA146349F8600C127668E7295E9491B86CB1E40015DA507C4927F6BCCAA77AFAD8302B238A3A085D37754097A6A93C5626BB5099E648E09E43935ADA2DCD99B8DDEAB79891752B8C508102147283FBAA9E437DAB1808E51EFF9C0ECD5EFC5226DCE3A76CC8A43635D55013F8253BFF1249BD991E5A3D0CD8D4C5EF9D3E3FEE2C6E564FC19E300968C967CF85E8E85ED06A4D7034104AF107B468B564AF2625581C4F918D3BF7D51FE57417B6DB04593890E3D1DFC356F38C2BFCAB8F312997157E230F84510A0490AFA63CEA3BE1BFEE351D5207E2787A2831C14BAE434D449397BED7CC5D48644985C08A2E67EB6CEB33E521F1B73AC39D4122741572628D1A1EACA5ECE87EC599D19EA3D64258FF9A1B3CB31FC4BC2CC1C84D63BA30862E270D601E582796337A0A85051A185D95415E27C2B2016BF556978DADE83787AF642B7A62019872EBEC69F43735DBAD214A15705467546262AA3CA7F3A6169A65571B2858D1AC5F15F1EDB11AA88EF70AF20012A45CB6094723F8E4054C1ABD77B1A6BBD6698D7A13D9C5B5B33C6C99CDC6034D1FD35B77BA3B87D0D40ECC8DDB3CDE1FAFF93F869604BA4E056F3FDC980D4A5A3A641075944C3977BF7007D852F3B0294815E0C8761EF8618C07F874BAEB25B098170D05946B65A7DE076D22E453AA2C17BB1B97EEB817E64D83E22B70618131E1A06979C58161B147F0C32982025DB844208187734D5FF3F3C98A1DB0AFA079CBD36B48B86DEC0EFE0D79F5C7C2599E2840380AEF257A183A0F9AC1A0E1259163F342985A25842C21FE89915CBC07209DA7318357EA1598C23F6CBED2F721BB533E7676271A25820039EE442C15312C5573E9563715F0E9F5A8BEE8CEEA5013611201CAECA4ABC642A92CE3EC0B42AB3371B1420A7682BBEA98DAADCF714A2E8BED42D5954DB9DC58D44436B2EA3D37B0ACF093EE75B358007C562E39F3099C6A7318AC26FC0D6083BD36CDCC866542A65CC263D8CFEC5EA55941BC965C0600AD8935319B8D86BEB8E7C33278E9E1C48B7EC143DC338EBF7788D4229E17611E3DFCE5017B6B191819F86F960FAB9C36340000000969F41541A8F03F202D890C5471837010A4E38559C4DEB30A8E4F35CD19D40A9CF9BD0EF65E382EE30595F3A7FCC6FEA804C1741665B43CE371C084C21F5E4AF | |||
| (PID) Process: | (6332) dw20.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IdentityCRL\Immersive\production\Token\{67082621-8D18-4333-9C64-10DE93676363} |
| Operation: | write | Name: | DeviceId |
Value: 00180010F429971D | |||
| (PID) Process: | (6332) dw20.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IdentityCRL\Immersive\production\Token\{67082621-8D18-4333-9C64-10DE93676363} |
| Operation: | write | Name: | ApplicationFlags |
Value: 1 | |||
Executable files
0
Suspicious files
2
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6332 | dw20.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_sqli dumper.exe_f8d33ce3c2762d643a997f4cf44d21dc8480528b_00000000_bc1537d4-837d-4bfe-82a0-1279af0b17a6\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6332 | dw20.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERDD29.tmp.WERInternalMetadata.xml | xml | |
MD5:06C72260F10332322F488393866F2B7B | SHA256:ED37945E10CA29C4A0437C4759A3EC17DEB86EA45A2F0DA1DCE0F2E6F2E79AE1 | |||
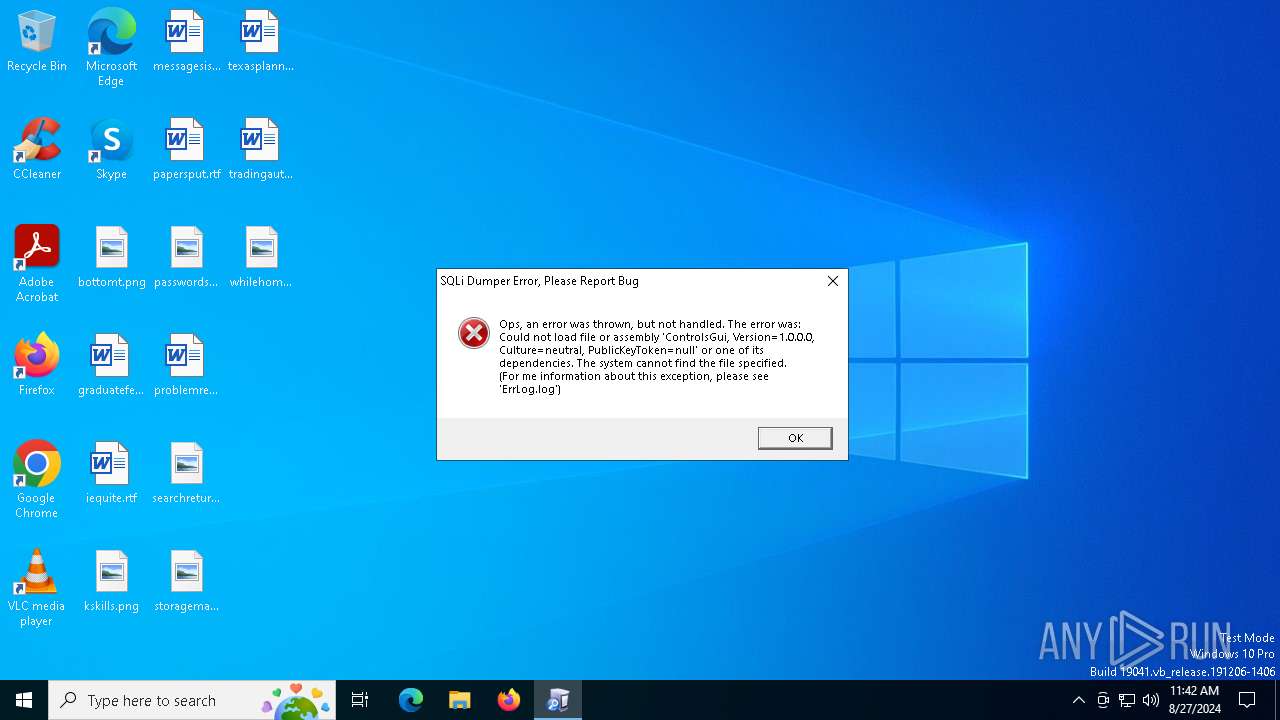
| 2068 | SQLi Dumper.exe | C:\Users\admin\Downloads\ErrLog.log | text | |
MD5:7C6A794E079ED298330AE3AA46622E01 | SHA256:90397A1F7BF0E4477DDBE6FC4DD4ACAC120ECD2EEC0BEFC07F225147245B804F | |||
| 6332 | dw20.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:82C30E45BF5F93A5DB1D5E47F913053B | SHA256:2C6BBFF9207065E8800C4AF0CB2748818ABB3CFFC0D6D518FE17F76A232F8967 | |||
| 6332 | dw20.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:FB64A9EBEDF48D3895381D5B7D80743D | SHA256:EA21D495930AD76F267A33A0F593DBF0C7EA75E457FCAE49A29DAAD8BD920F42 | |||
| 6332 | dw20.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERDD78.tmp.xml | xml | |
MD5:F167B8B640446C850FB2198632D20EFC | SHA256:3488D2E5A3D95327DAE643F138432FEDA1D75AE7E718C4D0598787E059C92691 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
33
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3652 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1184 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1184 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6612 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6264 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3652 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3652 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6612 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6332 | dw20.exe | 20.42.73.29:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |