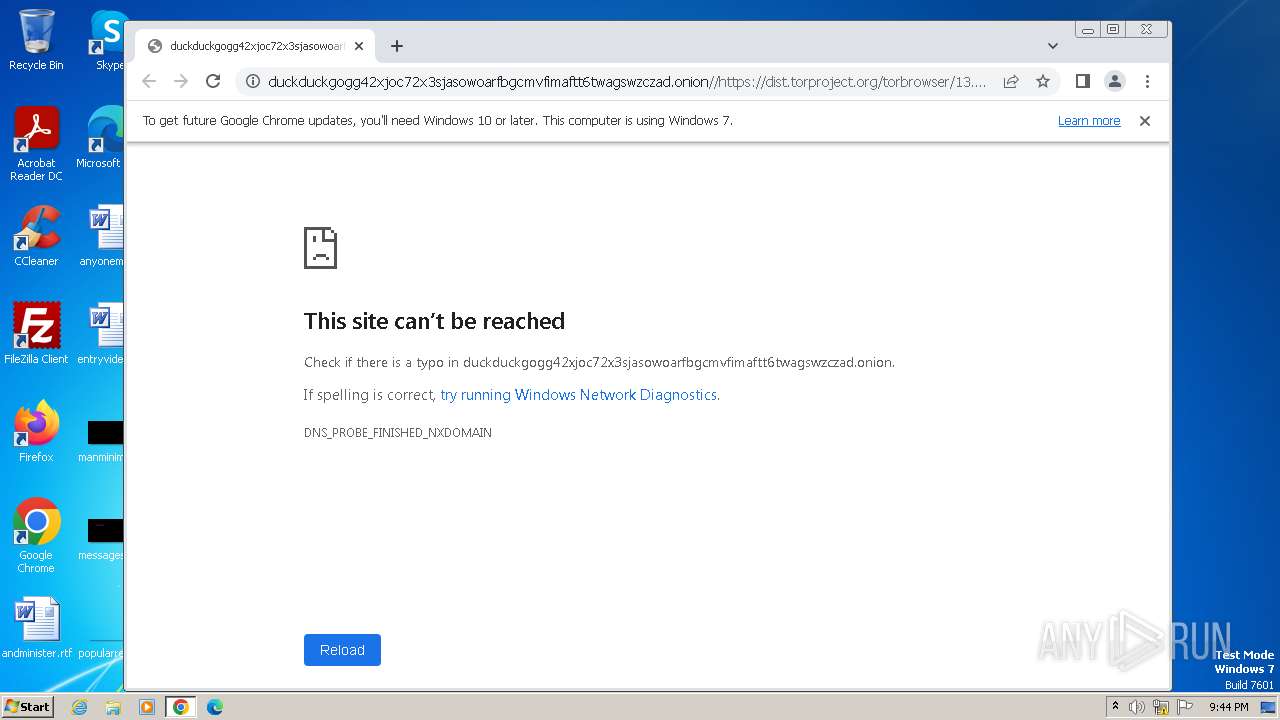
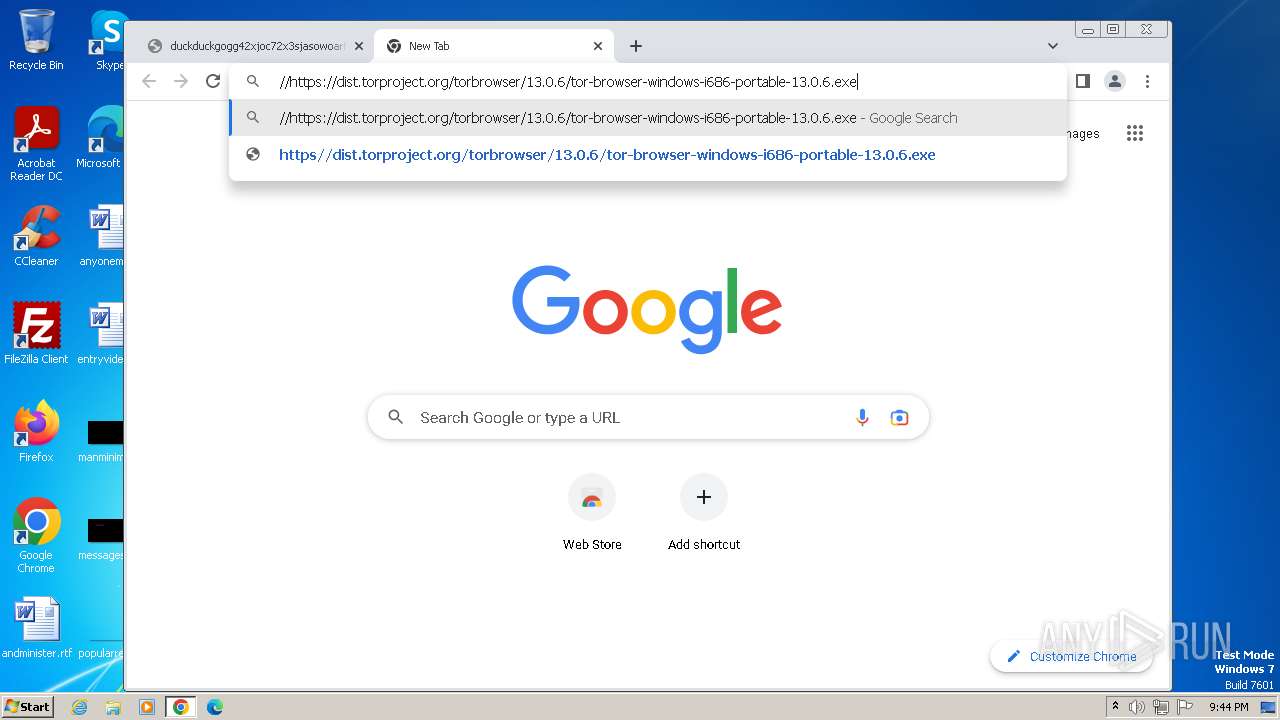
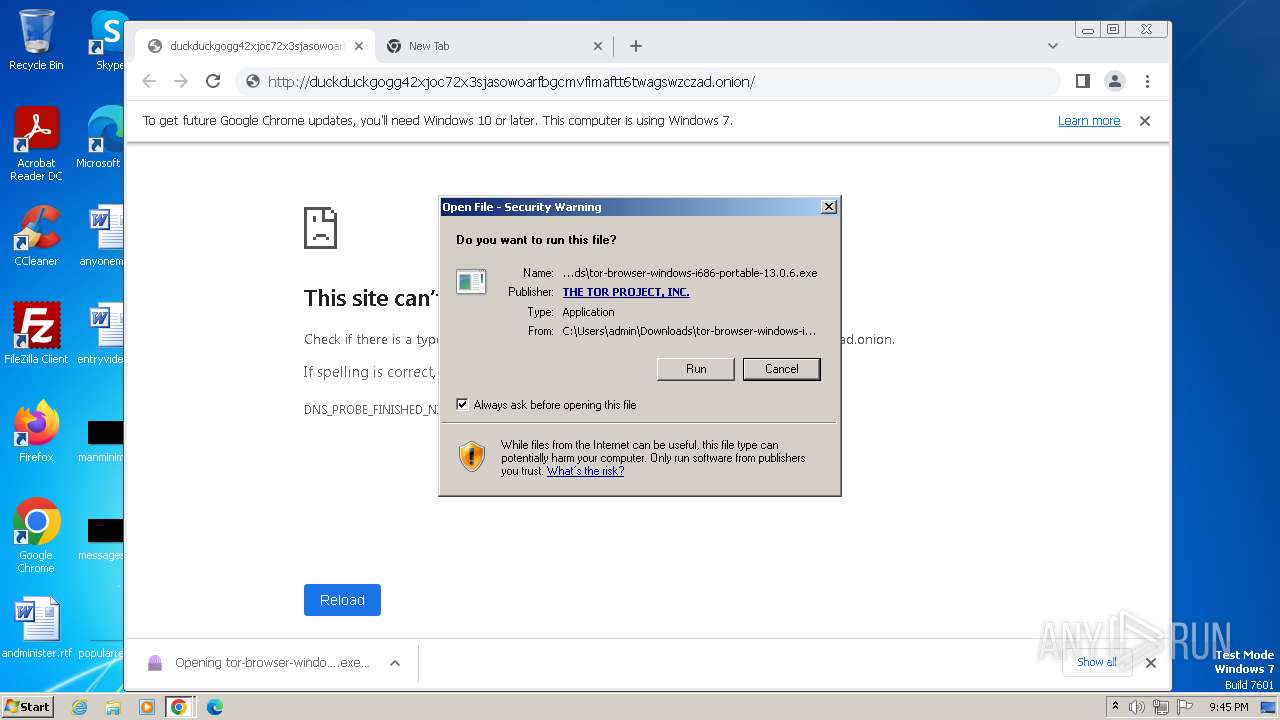
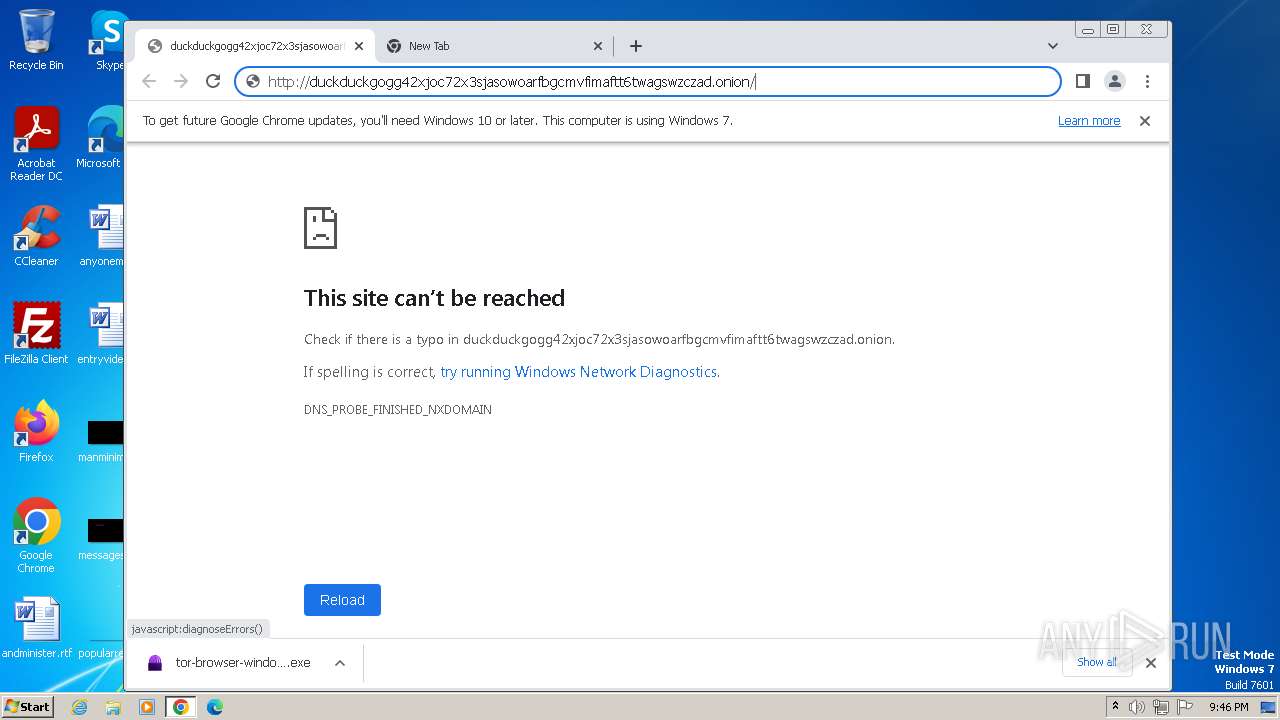
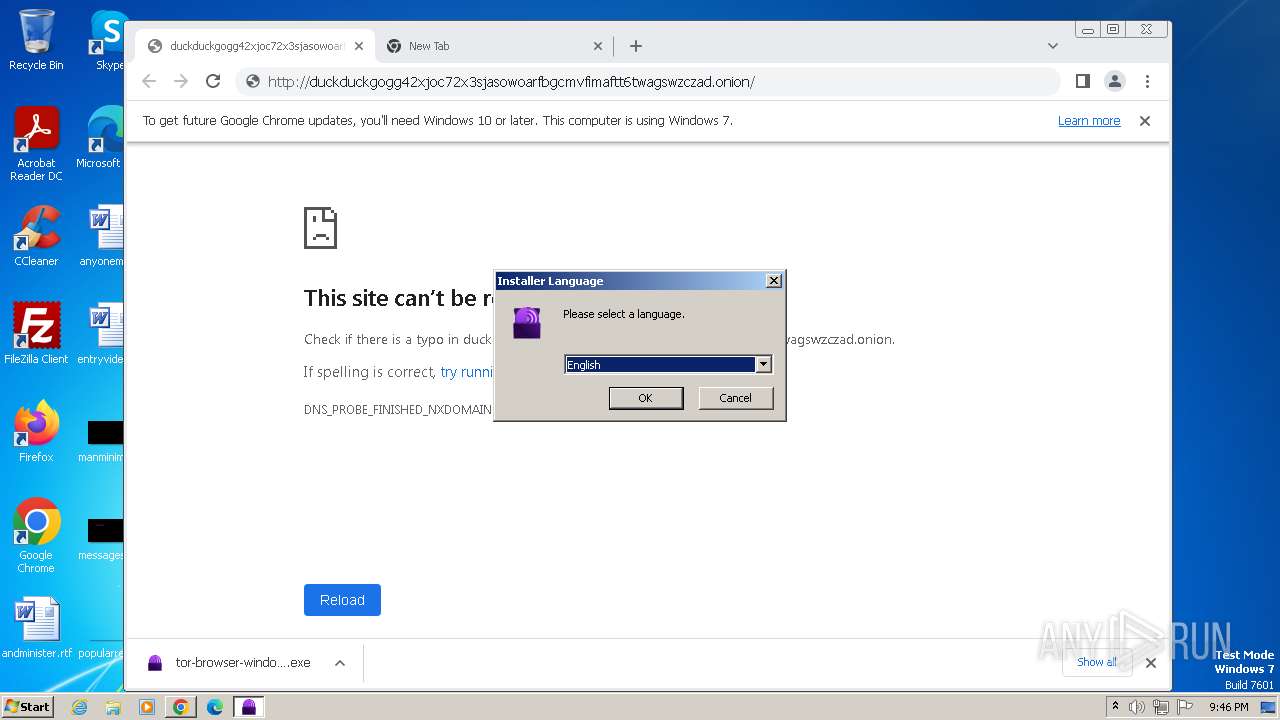
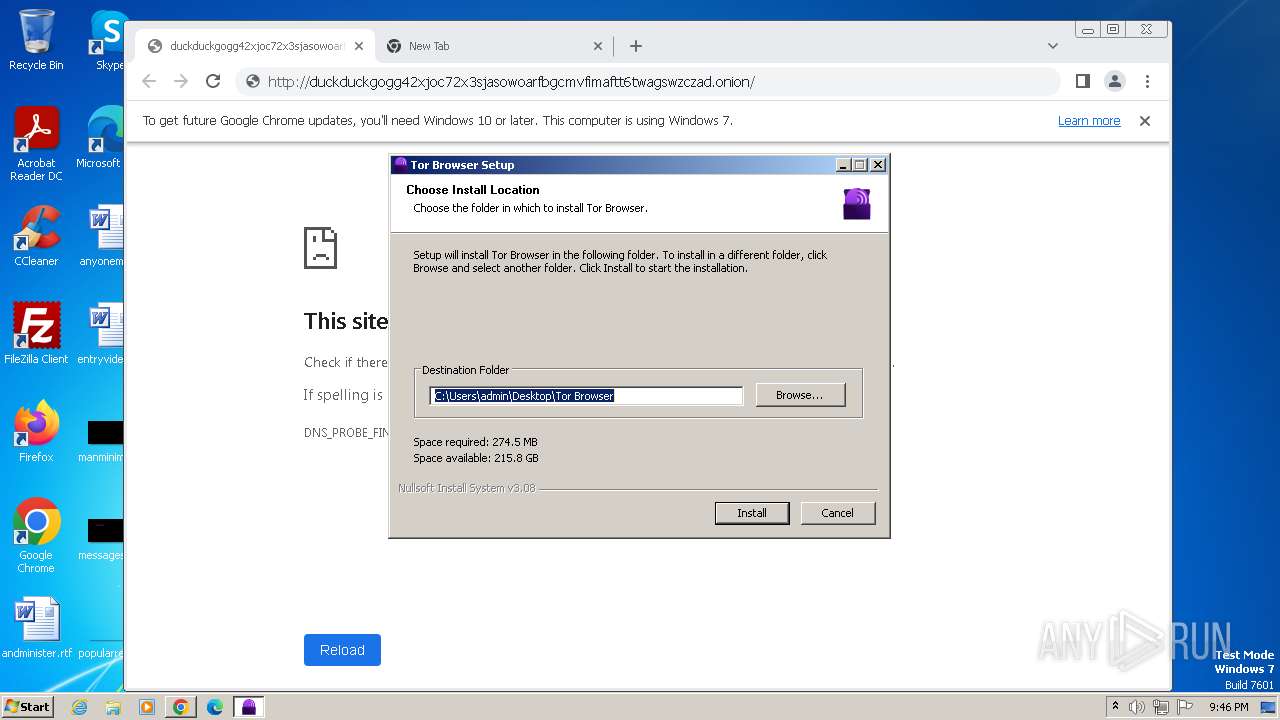
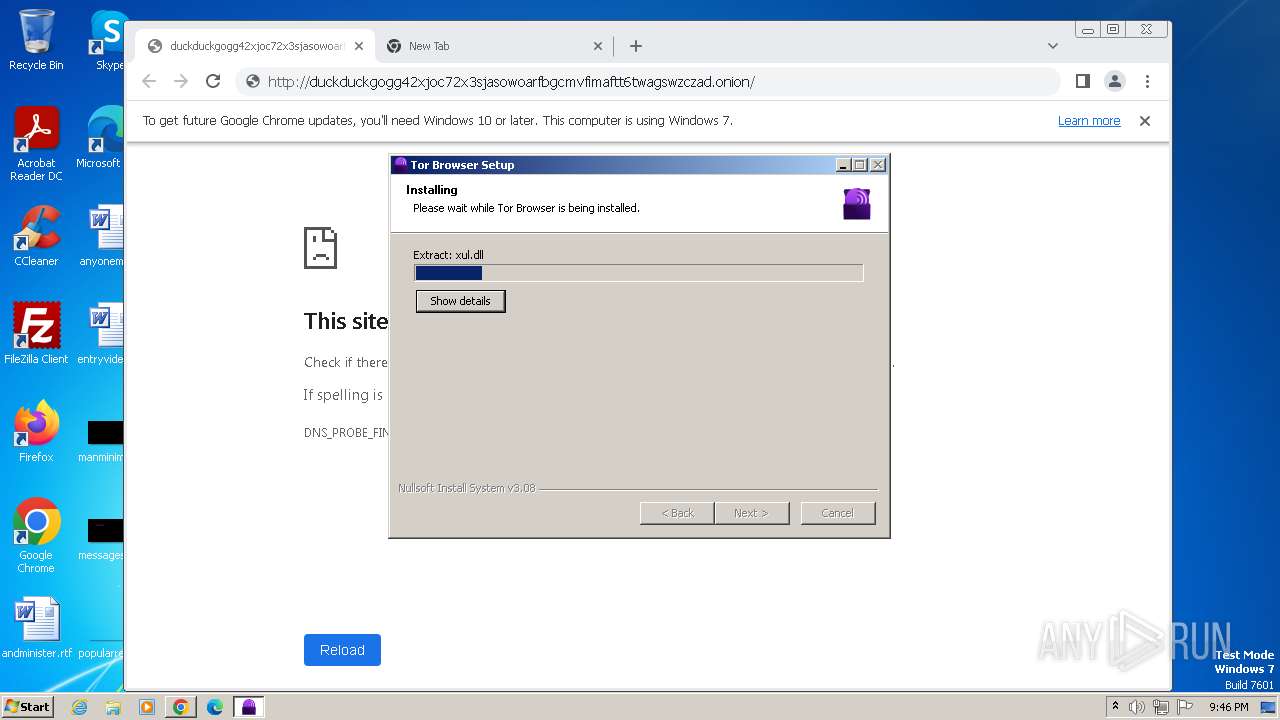
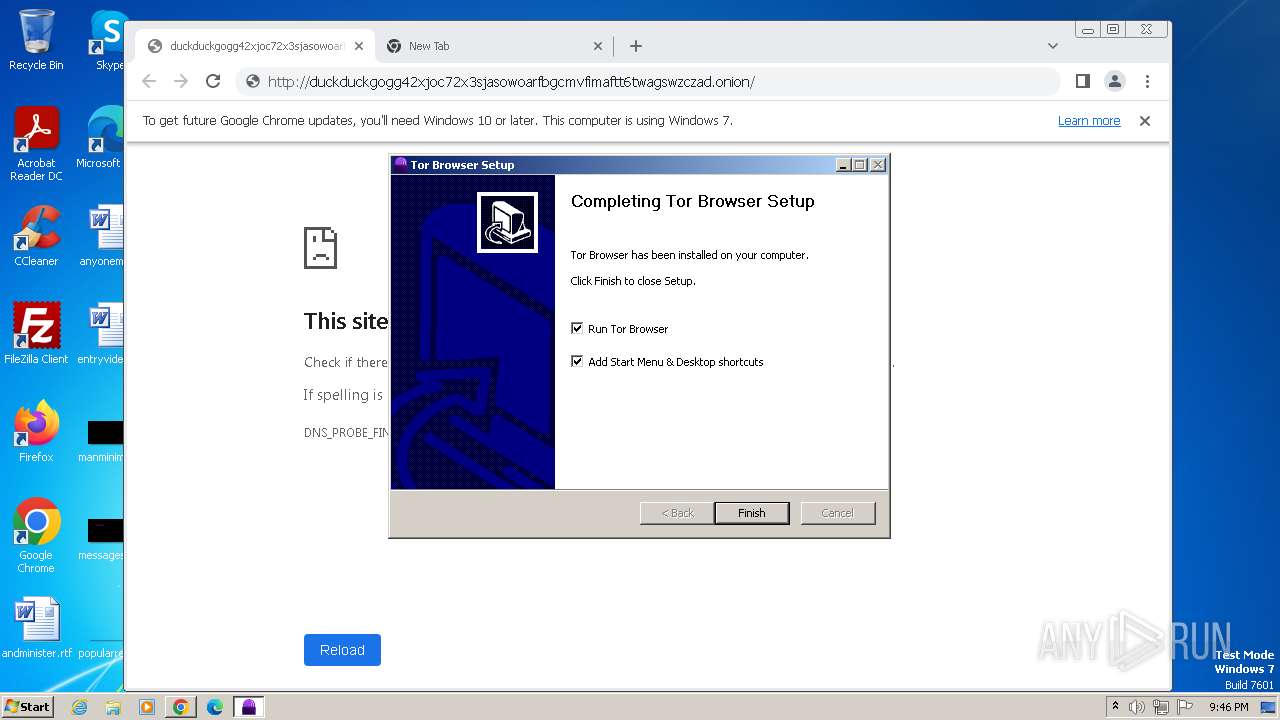
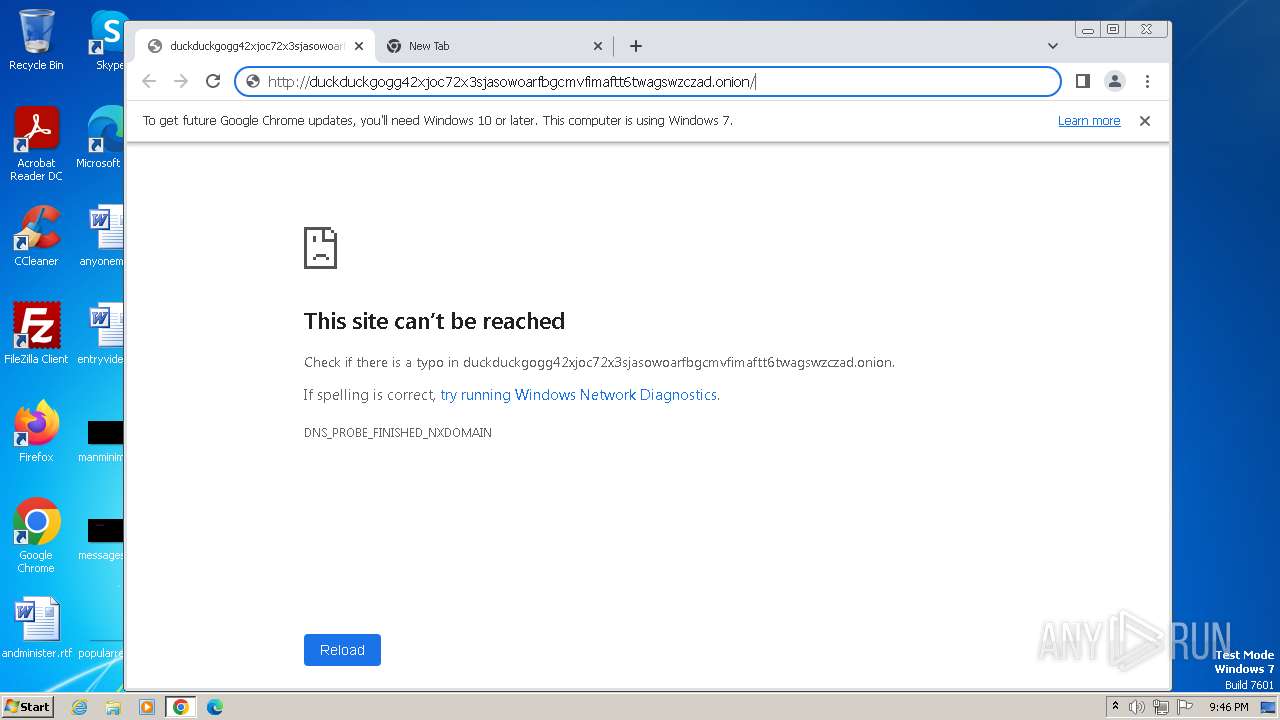
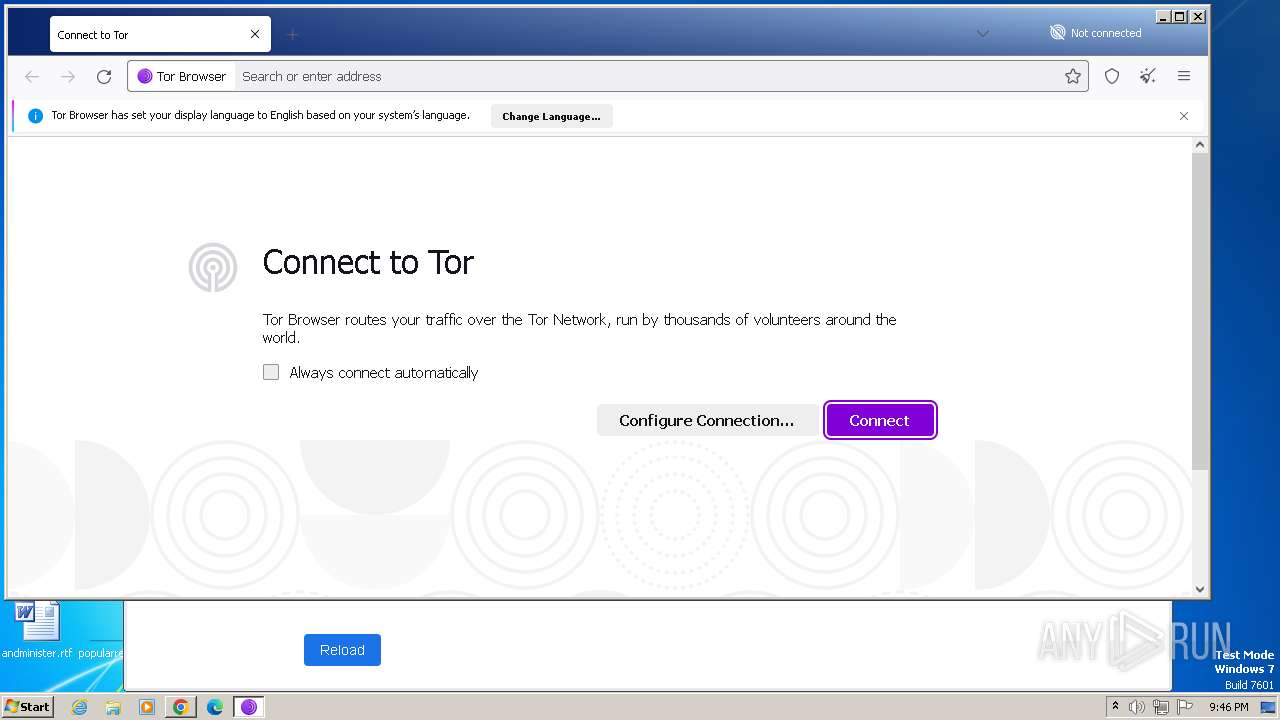
| URL: | duckduckgogg42xjoc72x3sjasowoarfbgcmvfimaftt6twagswzczad.onion//https://dist.torproject.org/torbrowser/13.0.6/tor-browser-windows-i686-portable-13.0.6.exe |
| Full analysis: | https://app.any.run/tasks/c0d120cb-4b22-4559-83ce-c72f16ced519 |
| Verdict: | Malicious activity |
| Analysis date: | December 09, 2023, 21:43:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 7F7CE7282D3C433545138F9617473513 |
| SHA1: | E0A9B6BD5F9AD50A54E4B9EA977EEBD16C8EF639 |
| SHA256: | 3F37C71DCE442C8590482C454A72DAFD62A447DE9A563BBADEFC2CED5F9C2B4A |
| SSDEEP: | 3:ImZC+SNWWP/t2GITDMIqR/fWZfSWfMMRKDG+X03KSWyaTRrlAXSBKSkIVRZLT0dA:7WWWH3MMIqpfASYMQqGUSIRrlAiBKSNX |
MALICIOUS
Drops the executable file immediately after the start
- tor-browser-windows-i686-portable-13.0.6.exe (PID: 3460)
SUSPICIOUS
Reads the Internet Settings
- tor-browser-windows-i686-portable-13.0.6.exe (PID: 3460)
- lyrebird.exe (PID: 2308)
Process drops legitimate windows executable
- chrome.exe (PID: 1996)
- tor-browser-windows-i686-portable-13.0.6.exe (PID: 3460)
The process creates files with name similar to system file names
- tor-browser-windows-i686-portable-13.0.6.exe (PID: 3460)
Malware-specific behavior (creating "System.dll" in Temp)
- tor-browser-windows-i686-portable-13.0.6.exe (PID: 3460)
Application launched itself
- firefox.exe (PID: 1832)
- firefox.exe (PID: 1584)
Reads settings of System Certificates
- lyrebird.exe (PID: 2308)
Adds/modifies Windows certificates
- lyrebird.exe (PID: 2308)
INFO
The process uses the downloaded file
- chrome.exe (PID: 904)
- chrome.exe (PID: 3596)
- chrome.exe (PID: 1064)
- chrome.exe (PID: 4044)
- chrome.exe (PID: 1996)
Manual execution by a user
- wmpnscfg.exe (PID: 4068)
Checks supported languages
- wmpnscfg.exe (PID: 4068)
- firefox.exe (PID: 1832)
- firefox.exe (PID: 3520)
- tor-browser-windows-i686-portable-13.0.6.exe (PID: 3460)
- firefox.exe (PID: 1584)
- firefox.exe (PID: 3836)
- firefox.exe (PID: 1844)
- firefox.exe (PID: 2416)
- firefox.exe (PID: 4088)
- tor.exe (PID: 3380)
- firefox.exe (PID: 3808)
- firefox.exe (PID: 2236)
- firefox.exe (PID: 2520)
- lyrebird.exe (PID: 2308)
- firefox.exe (PID: 3124)
- firefox.exe (PID: 3956)
Dropped object may contain TOR URL's
- tor-browser-windows-i686-portable-13.0.6.exe (PID: 3460)
- firefox.exe (PID: 1832)
Reads the machine GUID from the registry
- tor-browser-windows-i686-portable-13.0.6.exe (PID: 3460)
- firefox.exe (PID: 1832)
- tor.exe (PID: 3380)
- lyrebird.exe (PID: 2308)
Reads the computer name
- wmpnscfg.exe (PID: 4068)
- tor-browser-windows-i686-portable-13.0.6.exe (PID: 3460)
- firefox.exe (PID: 1832)
- firefox.exe (PID: 2416)
- firefox.exe (PID: 1844)
- firefox.exe (PID: 3520)
- firefox.exe (PID: 3808)
- firefox.exe (PID: 2236)
- firefox.exe (PID: 2520)
- firefox.exe (PID: 3836)
- tor.exe (PID: 3380)
- firefox.exe (PID: 3124)
- firefox.exe (PID: 3956)
- firefox.exe (PID: 4088)
- lyrebird.exe (PID: 2308)
Drops the executable file immediately after the start
- chrome.exe (PID: 1996)
- chrome.exe (PID: 3788)
Create files in a temporary directory
- tor-browser-windows-i686-portable-13.0.6.exe (PID: 3460)
- firefox.exe (PID: 1832)
- lyrebird.exe (PID: 2308)
The dropped object may contain a URL to Tor Browser
- tor-browser-windows-i686-portable-13.0.6.exe (PID: 3460)
Application launched itself
- chrome.exe (PID: 1996)
Creates files in the program directory
- firefox.exe (PID: 1832)
Creates files or folders in the user directory
- tor-browser-windows-i686-portable-13.0.6.exe (PID: 3460)
Reads CPU info
- firefox.exe (PID: 1832)
Process checks computer location settings
- firefox.exe (PID: 1832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
103
Monitored processes
62
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --mojo-platform-channel-handle=3548 --field-trial-handle=808,i,16613811320951606024,14007003494206106314,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 528 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3404 --field-trial-handle=808,i,16613811320951606024,14007003494206106314,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 552 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=24 --mojo-platform-channel-handle=4020 --field-trial-handle=808,i,16613811320951606024,14007003494206106314,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 824 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1012 --field-trial-handle=808,i,16613811320951606024,14007003494206106314,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 904 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=4000 --field-trial-handle=808,i,16613811320951606024,14007003494206106314,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 984 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=4312 --field-trial-handle=808,i,16613811320951606024,14007003494206106314,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1064 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3900 --field-trial-handle=808,i,16613811320951606024,14007003494206106314,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1072 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --mojo-platform-channel-handle=3988 --field-trial-handle=808,i,16613811320951606024,14007003494206106314,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1328 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1080 --field-trial-handle=808,i,16613811320951606024,14007003494206106314,131072 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1404 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --mojo-platform-channel-handle=3000 --field-trial-handle=808,i,16613811320951606024,14007003494206106314,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
23 893
Read events
23 492
Write events
397
Delete events
4
Modification events
| (PID) Process: | (1996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (1996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1996) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (1996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
| (PID) Process: | (1996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_enableddate |
Value: 0 | |||
Executable files
38
Suspicious files
580
Text files
117
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF20fb1d.TMP | — | |
MD5:— | SHA256:— | |||
| 1996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF20fb1d.TMP | text | |
MD5:513218482935B0D388C0A990D868387A | SHA256:8E39CBAAF4AACC3A01AFA74EA8C30FB24FE69A22B8B30728AFB1614FD68809D9 | |||
| 1996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:8175FB7046E977DAAD01289080C116EF | SHA256:19E403B4BEF7D83DD425AB6A54DE943D244A16E5EA121DEC91C417608AEAACB7 | |||
| 1996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Platform Notifications\LOG.old | text | |
MD5:05387A3C4FCF1F3B992FF9FBF045AA1A | SHA256:B01E9451B8F6ABF03C9CD2E158C02D0A6BFDF771944F5D0B96DAD2DA6A7E3C8F | |||
| 1996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Extension State\LOG.old | text | |
MD5:4F91C1E6BB20F7FF680A09754DC1139D | SHA256:48F675EFB86CCE216ED6DC02D7A05D91BFD3ACB402DF3617DF2E779D02264215 | |||
| 1996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF20fdbd.TMP | — | |
MD5:— | SHA256:— | |||
| 1996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 1996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\optimization_guide_hint_cache_store\LOG.old~RF2109c3.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
47
TCP/UDP connections
30
DNS requests
38
Threats
26
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 5.54 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 8.42 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 11.5 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 11.7 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 8.54 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 52.5 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 218 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 107 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 421 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1996 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2108 | chrome.exe | 64.233.166.84:443 | accounts.google.com | GOOGLE | US | unknown |
1996 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
2108 | chrome.exe | 142.250.185.196:443 | www.google.com | GOOGLE | US | whitelisted |
2108 | chrome.exe | 142.250.186.170:443 | optimizationguide-pa.googleapis.com | GOOGLE | US | whitelisted |
2108 | chrome.exe | 216.58.212.131:443 | www.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
duckduckgogg42xjoc72x3sjasowoarfbgcmvfimaftt6twagswzczad.onion |
| unknown |
accounts.google.com |
| shared |
google.com |
| whitelisted |
www.google.com |
| whitelisted |
optimizationguide-pa.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
www.googleapis.com |
| whitelisted |
dist.torproject.org |
| whitelisted |
update.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2108 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
2108 | chrome.exe | Potential Corporate Privacy Violation | AV POLICY DNS Query for .onion Domain Via TOR - Not Google |
2108 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
2108 | chrome.exe | Potential Corporate Privacy Violation | AV POLICY DNS Query for .onion Domain Via TOR - Not Google |
1080 | svchost.exe | Potential Corporate Privacy Violation | AV POLICY DNS Query for .onion Domain Via TOR - Not Google |
1080 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
2108 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
2108 | chrome.exe | Potential Corporate Privacy Violation | AV POLICY DNS Query for .onion Domain Via TOR - Not Google |
2108 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
2108 | chrome.exe | Potential Corporate Privacy Violation | AV POLICY DNS Query for .onion Domain Via TOR - Not Google |