| URL: | https://github.com/yuankong666/Ultimate-RAT-Collection/tree/main/XWorm/XWorm%20V3.1 |
| Full analysis: | https://app.any.run/tasks/2e2ce7ad-35fd-44cc-9030-290c1b8d5d4a |
| Verdict: | Malicious activity |
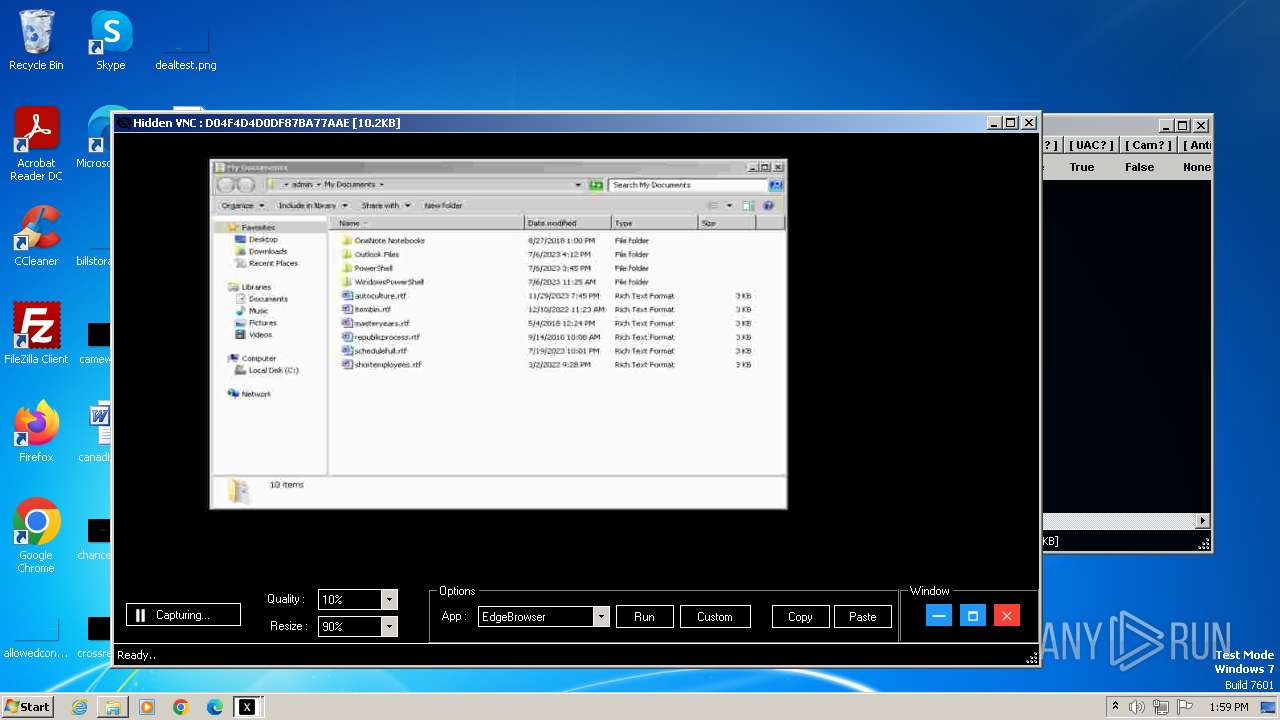
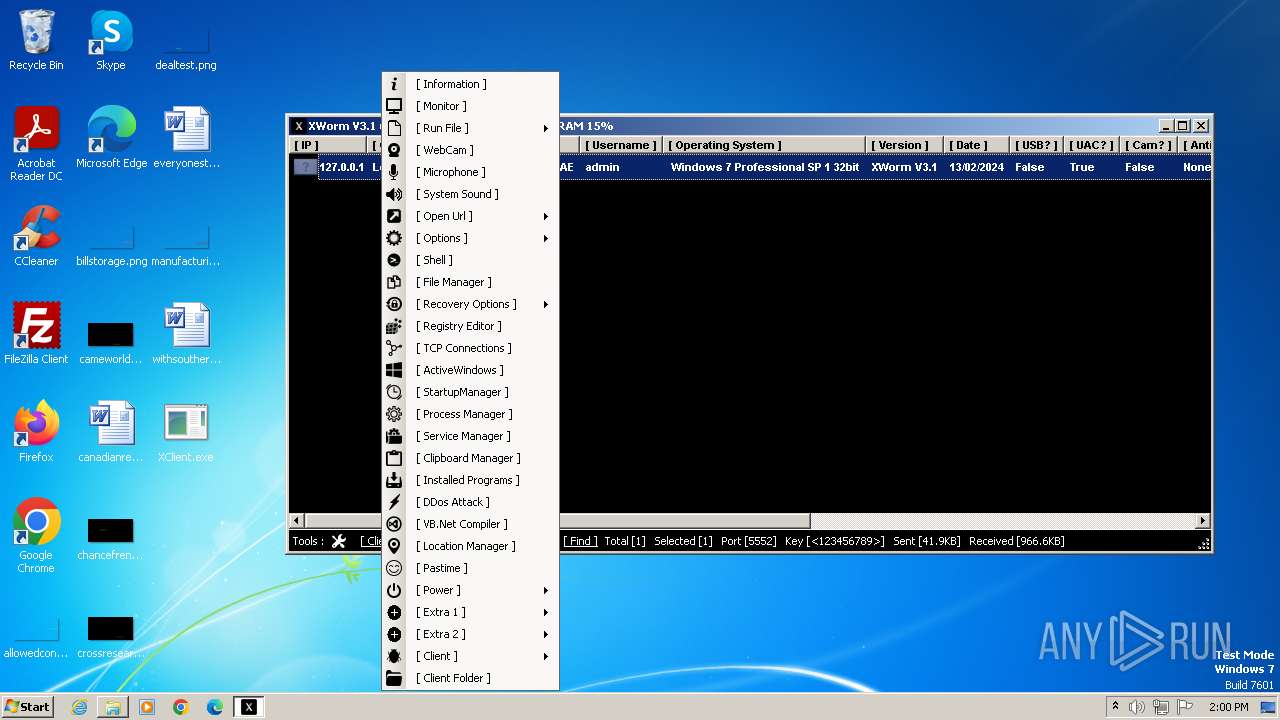
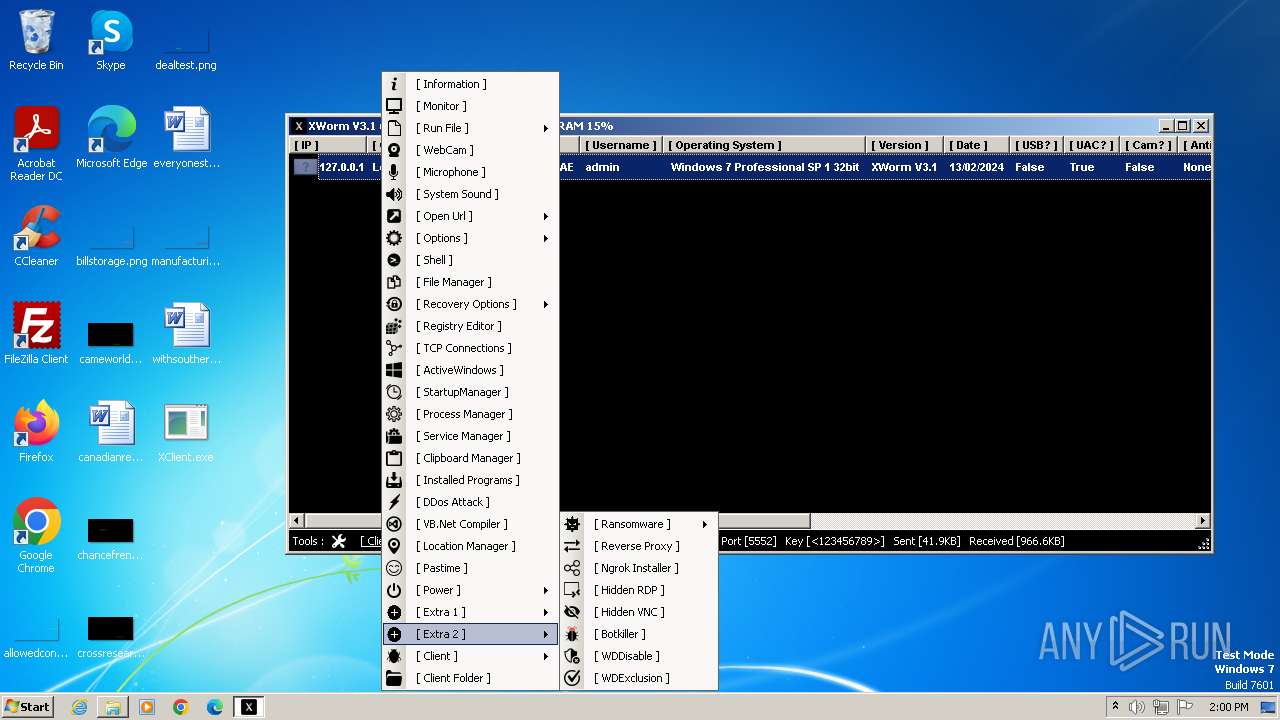
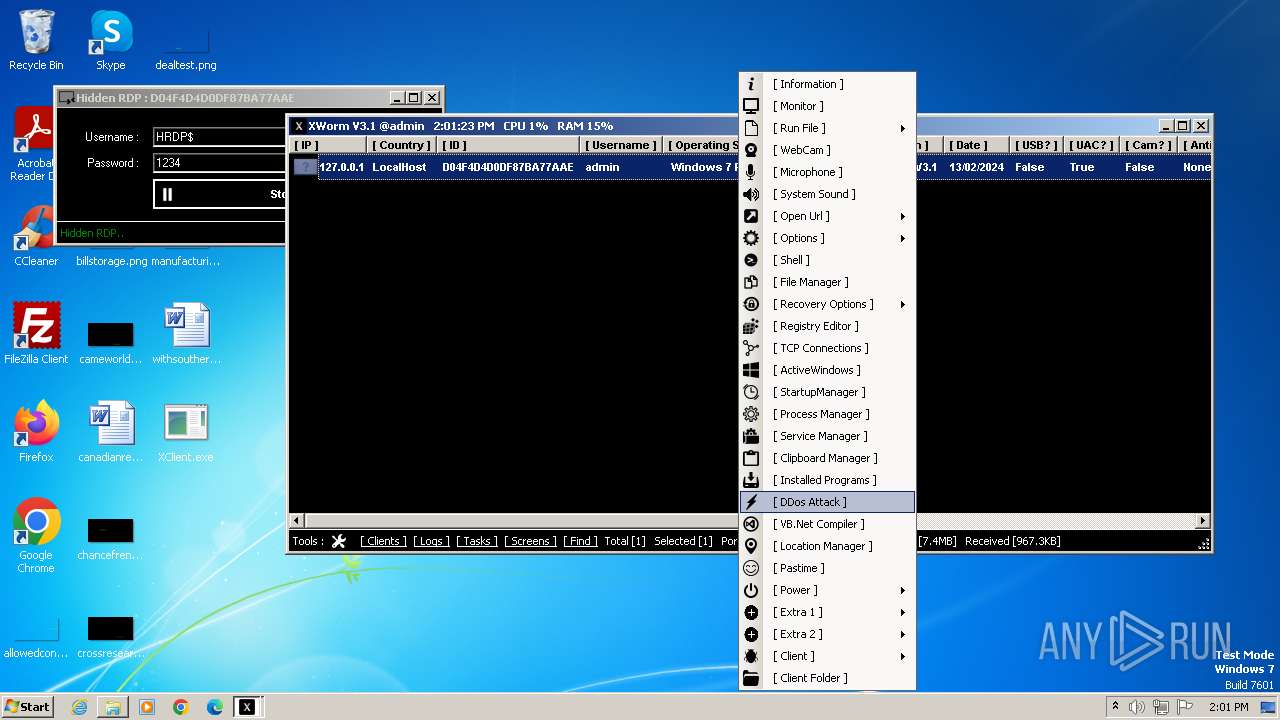
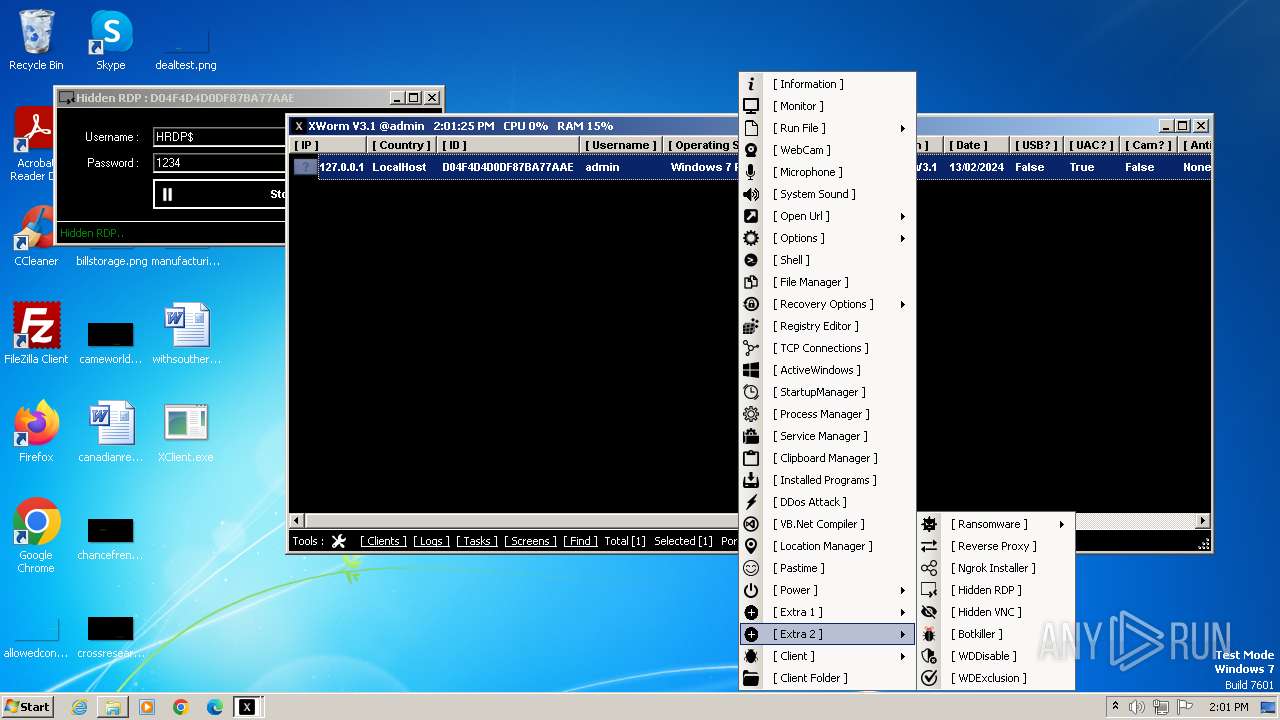
| Threats: | XWorm is a remote access trojan (RAT) sold as a malware-as-a-service. It possesses an extensive hacking toolset and is capable of gathering private information and files from the infected computer, hijacking MetaMask and Telegram accounts, and tracking user activity. XWorm is typically delivered to victims' computers through multi-stage attacks that start with phishing emails. |
| Analysis date: | February 13, 2024, 13:56:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 682A5F08434F49B044671E702C6C7CCA |
| SHA1: | 6A64A37E69D28B5DE139ACCD8D3C668FF51C62B9 |
| SHA256: | 3F35B42C46C73A8A56BF6FB75AC319B23AE1CB6727DD58AD2034B8E354797624 |
| SSDEEP: | 3:N8tEdstRGGpI4FkO9JOGRJAKIRKfYwJn:2u6tYGm1gOGXvIRKAwJn |
MALICIOUS
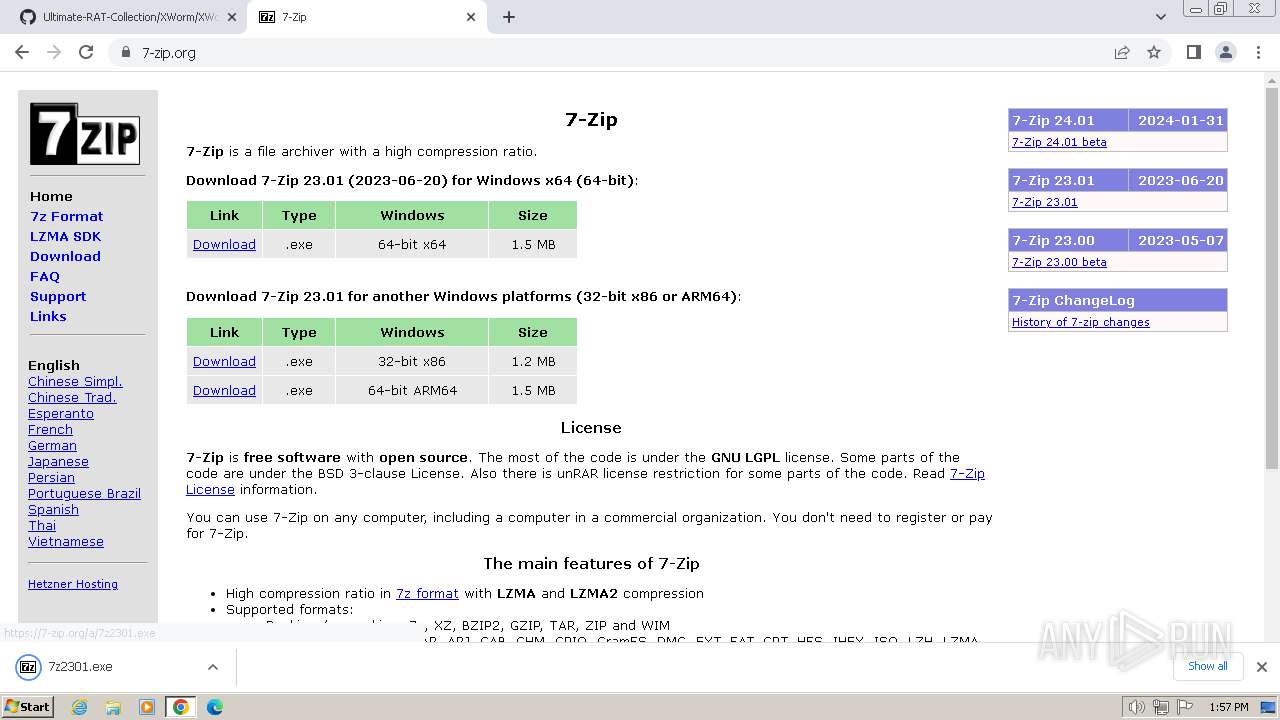
Drops the executable file immediately after the start
- 7z2301.exe (PID: 3468)
- 7zG.exe (PID: 1784)
- vbc.exe (PID: 2804)
- XClient.exe (PID: 3044)
- RDPWInst.exe (PID: 1832)
Actions looks like stealing of personal data
- cvtres.exe (PID: 296)
Changes the autorun value in the registry
- XClient.exe (PID: 3044)
Create files in the Startup directory
- XClient.exe (PID: 3044)
XWORM has been detected (YARA)
- XClient.exe (PID: 3044)
Creates or modifies Windows services
- RDPWInst.exe (PID: 1832)
SUSPICIOUS
Drops 7-zip archiver for unpacking
- chrome.exe (PID: 3864)
- 7z2301.exe (PID: 3468)
Creates a software uninstall entry
- 7z2301.exe (PID: 3468)
Executable content was dropped or overwritten
- 7zG.exe (PID: 1784)
- 7z2301.exe (PID: 3468)
- vbc.exe (PID: 2804)
- XClient.exe (PID: 3044)
- RDPWInst.exe (PID: 1832)
Creates/Modifies COM task schedule object
- 7z2301.exe (PID: 3468)
The process executes VB scripts
- XWorm V3.1.exe (PID: 3524)
Reads the Internet Settings
- XWorm V3.1.exe (PID: 3524)
- XClient.exe (PID: 3044)
The process creates files with name similar to system file names
- 7zG.exe (PID: 1784)
The process executes via Task Scheduler
- XClient.exe (PID: 2940)
- XClient.exe (PID: 3076)
Reads security settings of Internet Explorer
- XClient.exe (PID: 3044)
Starts POWERSHELL.EXE for commands execution
- cvtres.exe (PID: 296)
Uses TASKKILL.EXE to kill process
- XClient.exe (PID: 3044)
Uses NETSH.EXE to add a firewall rule or allowed programs
- RDPWInst.exe (PID: 1832)
Reads settings of System Certificates
- ngrok.exe (PID: 2132)
Adds/modifies Windows certificates
- ngrok.exe (PID: 2132)
INFO
Checks supported languages
- 7z2301.exe (PID: 3468)
- XWorm V3.1.exe (PID: 3524)
- 7zG.exe (PID: 1784)
- vbc.exe (PID: 2804)
- cvtres.exe (PID: 2592)
- XClient.exe (PID: 3044)
- cvtres.exe (PID: 296)
- XClient.exe (PID: 2940)
- ngrok.exe (PID: 1776)
- XClient.exe (PID: 3076)
- RDPWInst.exe (PID: 1832)
- wmpnscfg.exe (PID: 1892)
- ngrok.exe (PID: 2132)
- wmpnscfg.exe (PID: 3768)
- wmpnscfg.exe (PID: 1220)
- cvtres.exe (PID: 2372)
Drops the executable file immediately after the start
- chrome.exe (PID: 3864)
Executable content was dropped or overwritten
- chrome.exe (PID: 3864)
The process uses the downloaded file
- chrome.exe (PID: 2560)
- chrome.exe (PID: 3864)
- chrome.exe (PID: 2544)
- chrome.exe (PID: 3404)
- chrome.exe (PID: 2660)
Creates files in the program directory
- 7z2301.exe (PID: 3468)
- XClient.exe (PID: 3044)
- RDPWInst.exe (PID: 1832)
Reads the computer name
- 7zG.exe (PID: 1784)
- XWorm V3.1.exe (PID: 3524)
- 7z2301.exe (PID: 3468)
- XClient.exe (PID: 3044)
- cvtres.exe (PID: 296)
- XClient.exe (PID: 2940)
- RDPWInst.exe (PID: 1832)
- ngrok.exe (PID: 1776)
- XClient.exe (PID: 3076)
- wmpnscfg.exe (PID: 1892)
- wmpnscfg.exe (PID: 3768)
- ngrok.exe (PID: 2132)
- wmpnscfg.exe (PID: 1220)
- cvtres.exe (PID: 2372)
Manual execution by a user
- XWorm V3.1.exe (PID: 3524)
- explorer.exe (PID: 2268)
- 7zG.exe (PID: 1784)
- XClient.exe (PID: 3044)
- firefox.exe (PID: 4056)
- wmpnscfg.exe (PID: 1220)
- wmpnscfg.exe (PID: 1892)
- wmpnscfg.exe (PID: 3768)
- firefox.exe (PID: 1316)
Application launched itself
- chrome.exe (PID: 3864)
- firefox.exe (PID: 4056)
- firefox.exe (PID: 4032)
- firefox.exe (PID: 1316)
- firefox.exe (PID: 3800)
Create files in a temporary directory
- XWorm V3.1.exe (PID: 3524)
- cvtres.exe (PID: 2592)
- vbc.exe (PID: 2804)
- XClient.exe (PID: 3044)
Reads the machine GUID from the registry
- vbc.exe (PID: 2804)
- cvtres.exe (PID: 2592)
- XClient.exe (PID: 3044)
- XWorm V3.1.exe (PID: 3524)
- cvtres.exe (PID: 296)
- XClient.exe (PID: 2940)
- XClient.exe (PID: 3076)
- ngrok.exe (PID: 2132)
- cvtres.exe (PID: 2372)
Reads Environment values
- XWorm V3.1.exe (PID: 3524)
- XClient.exe (PID: 3044)
Reads Microsoft Office registry keys
- XWorm V3.1.exe (PID: 3524)
Creates files or folders in the user directory
- XClient.exe (PID: 3044)
- cvtres.exe (PID: 296)
- ngrok.exe (PID: 1776)
Reads security settings of Internet Explorer
- explorer.exe (PID: 3496)
Reads the Internet Settings
- explorer.exe (PID: 3496)
Reads the software policy settings
- ngrok.exe (PID: 2132)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
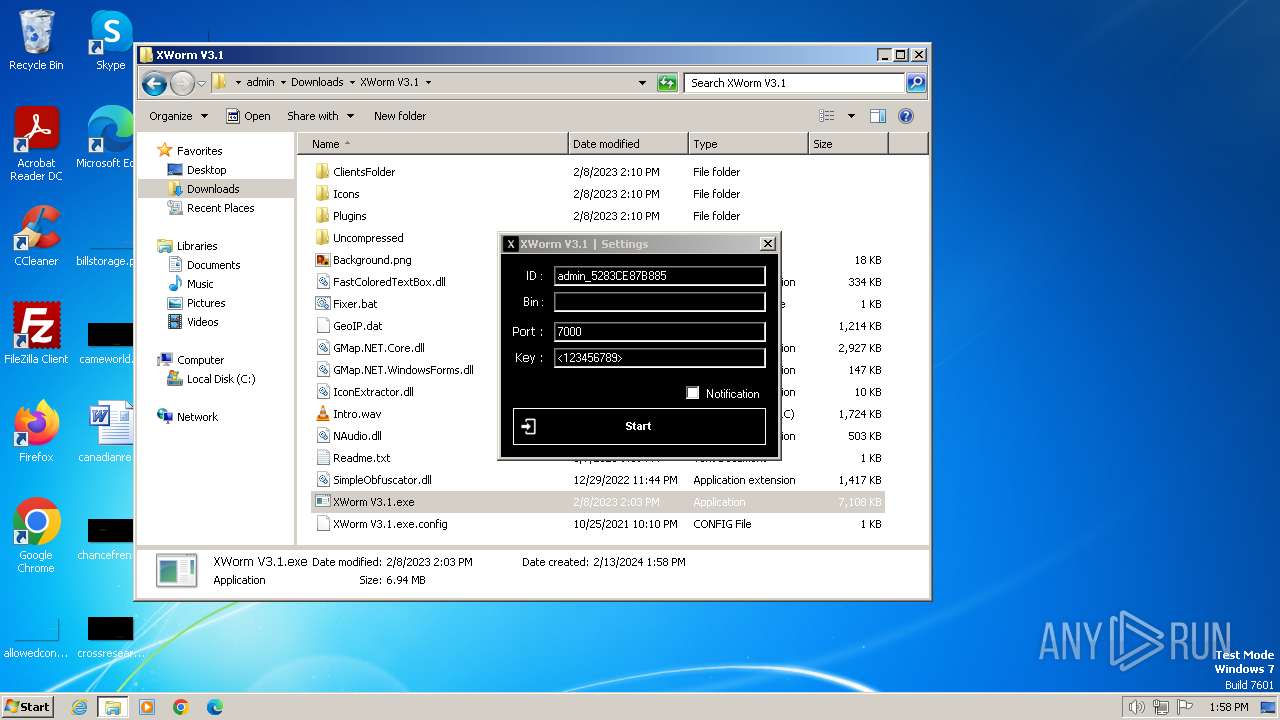
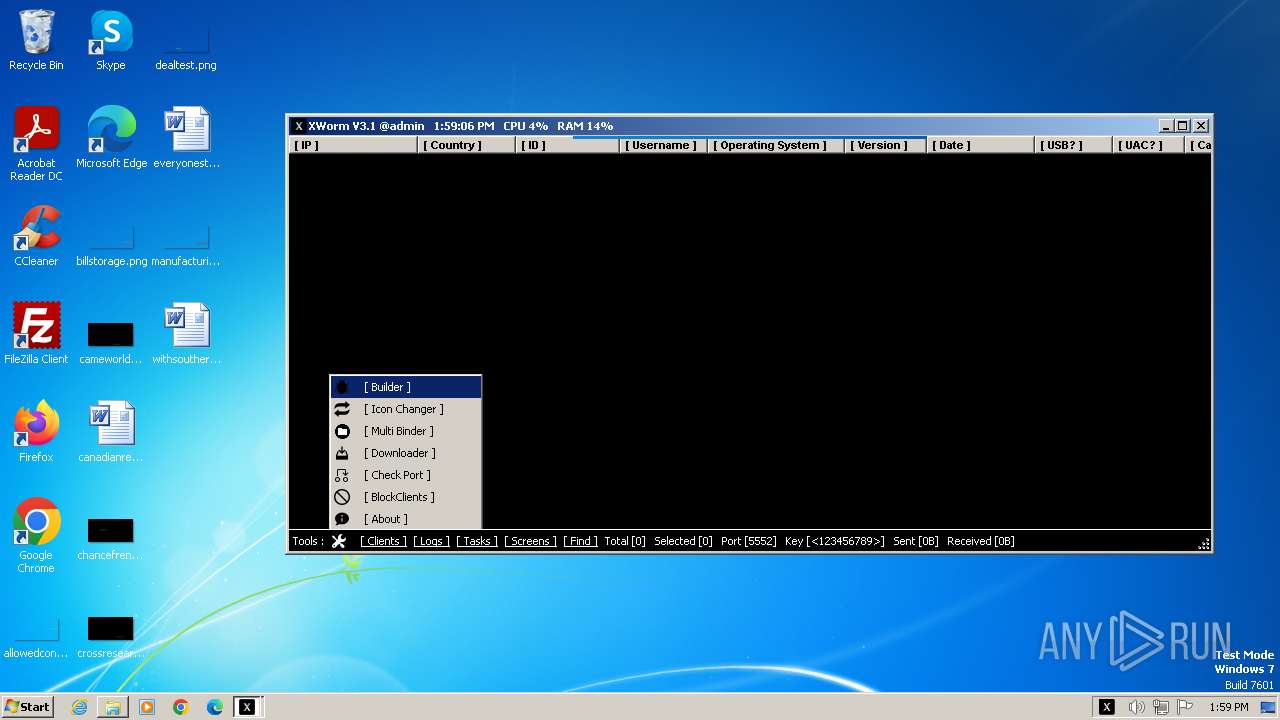
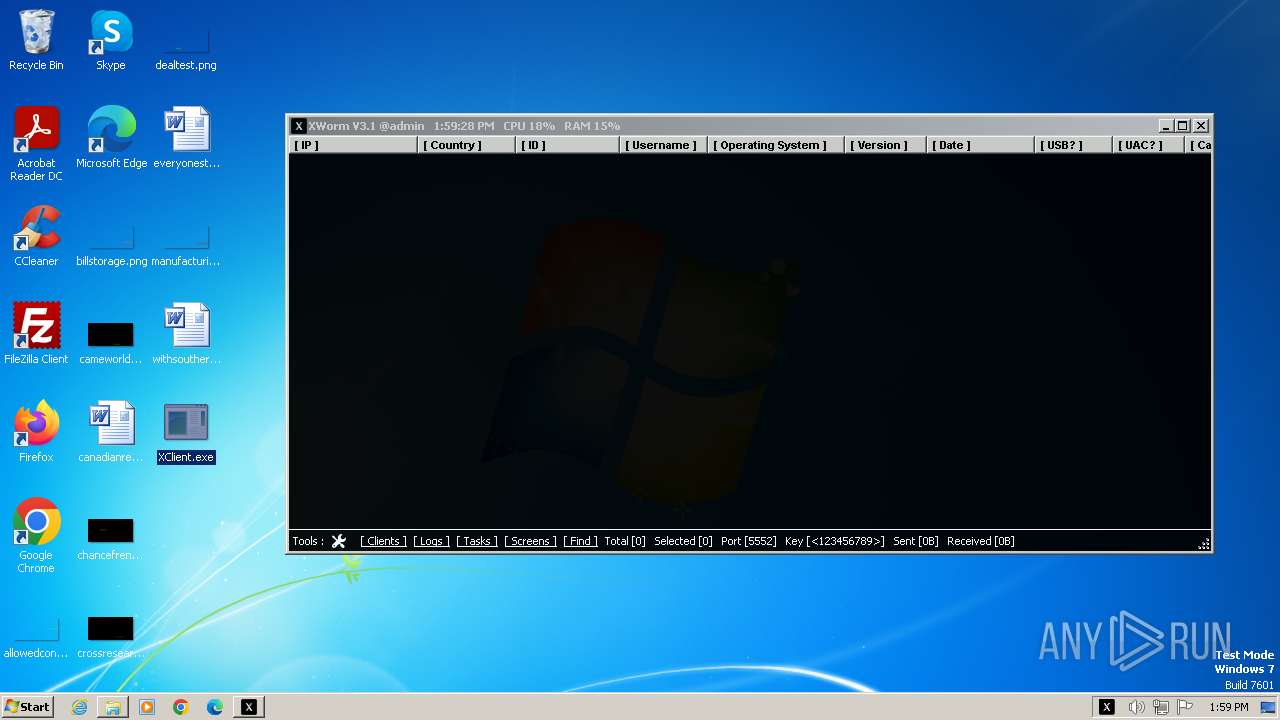
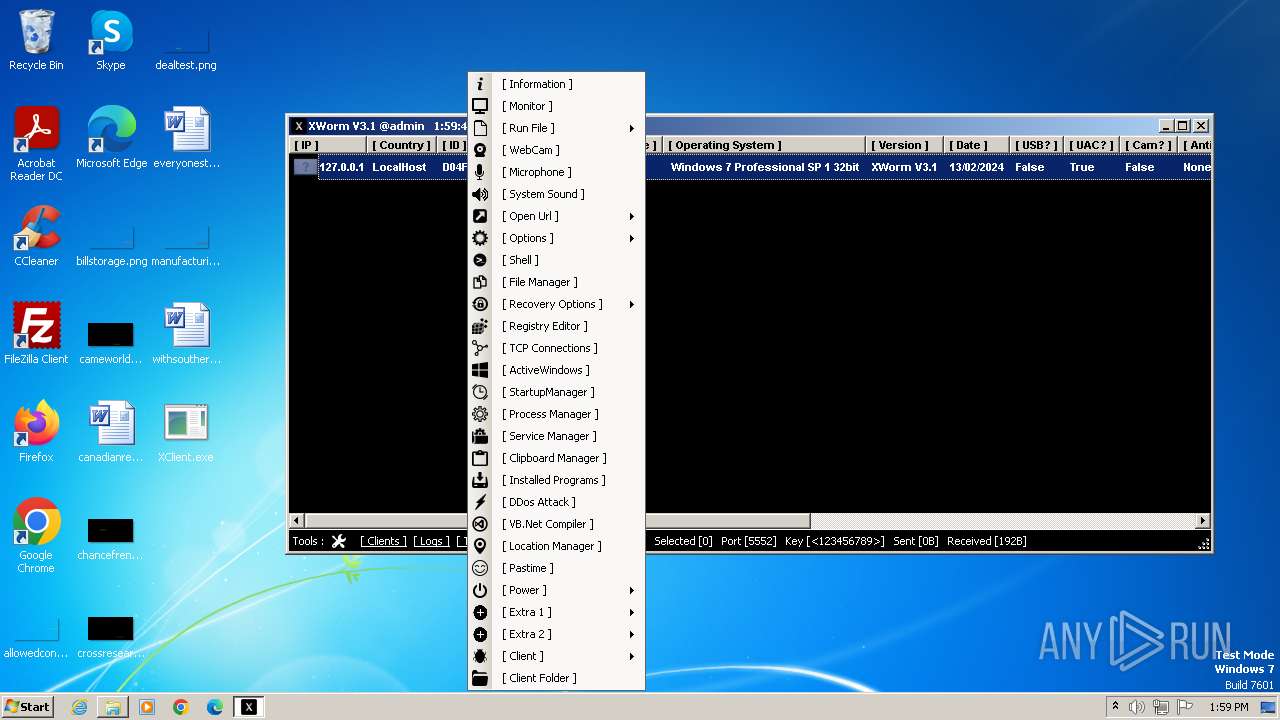
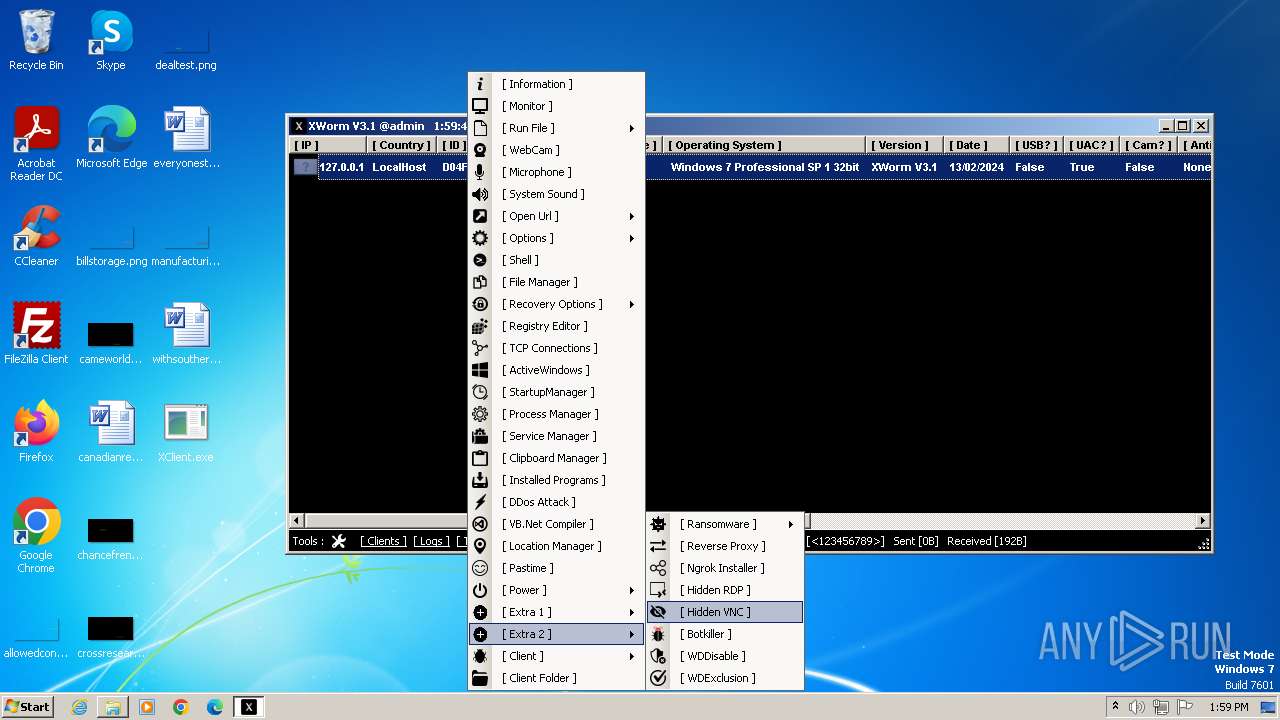
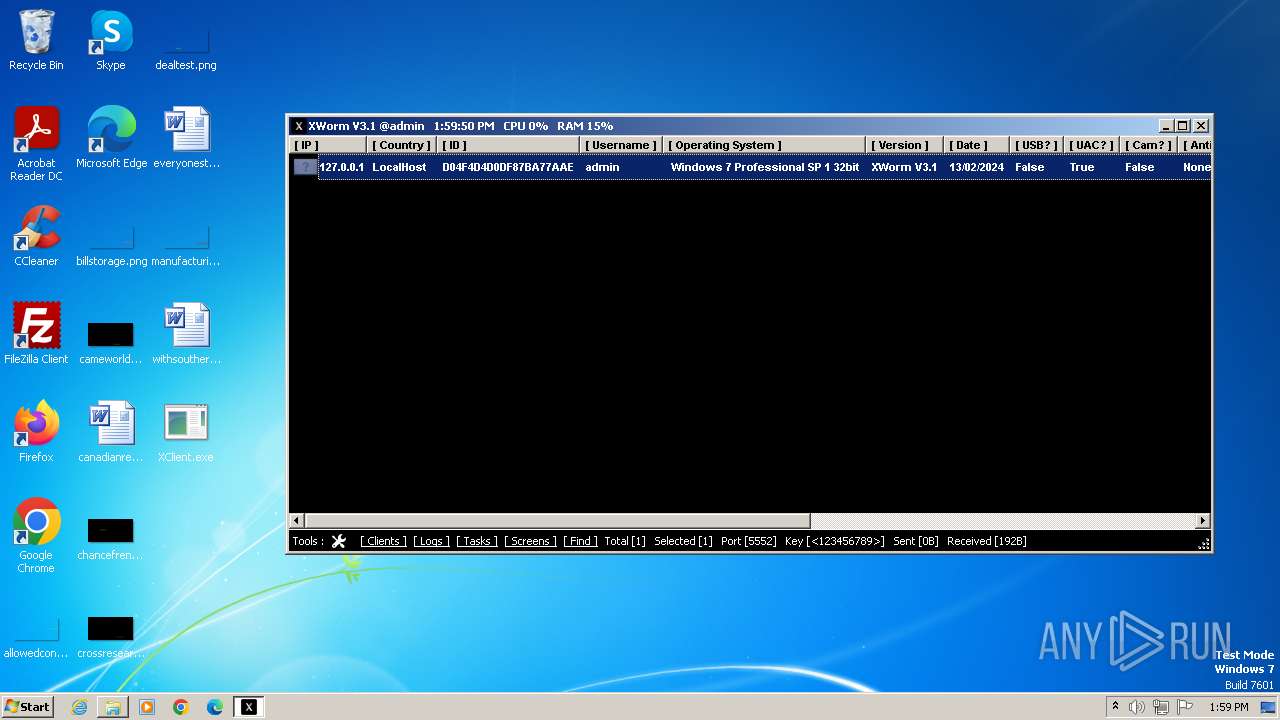
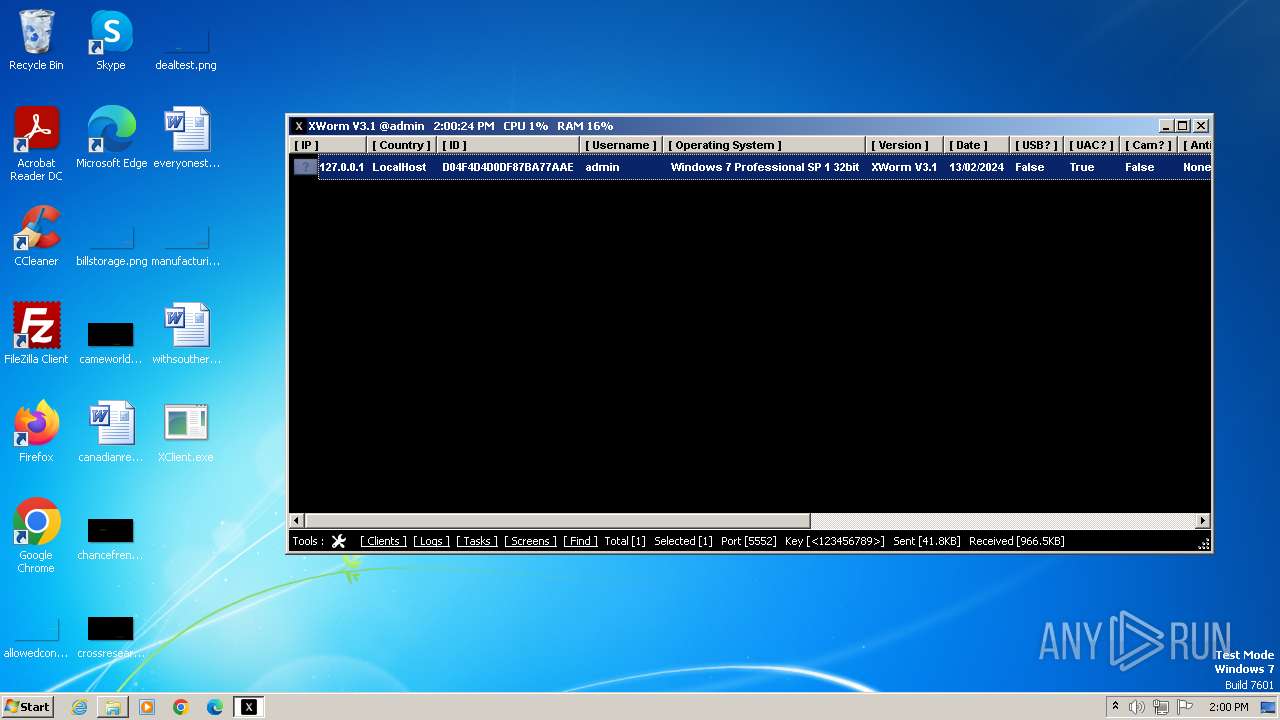
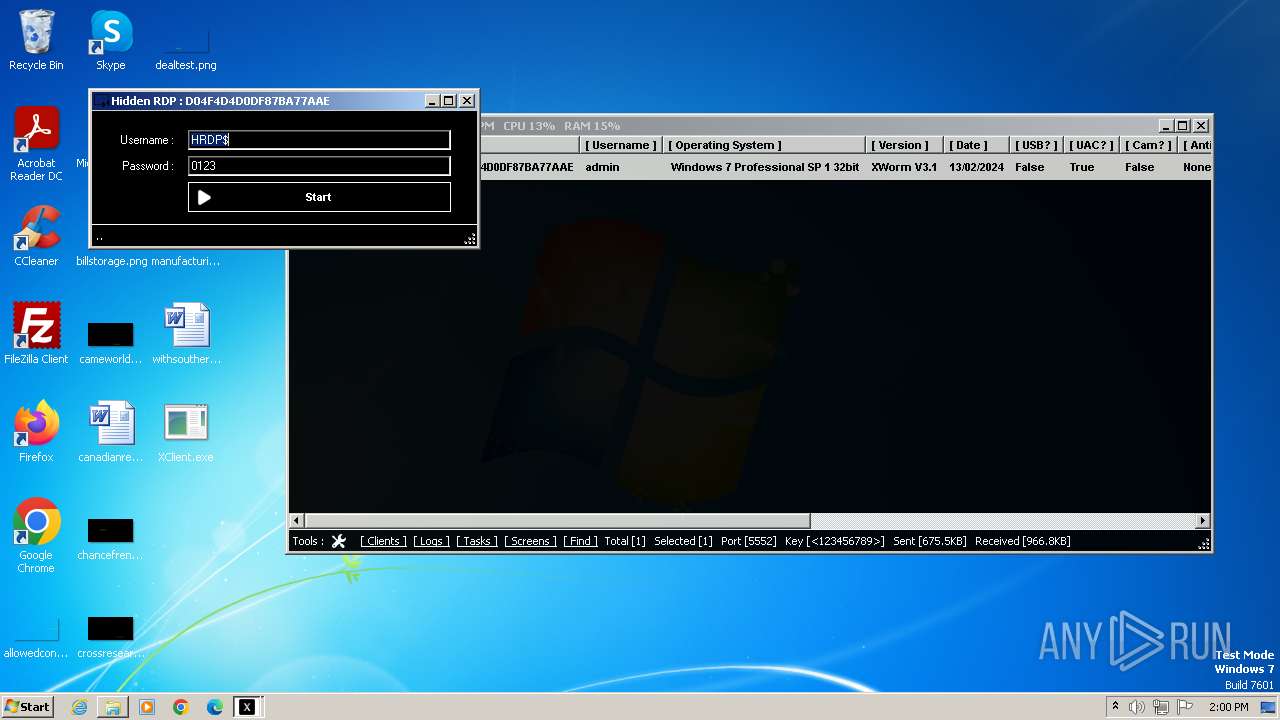
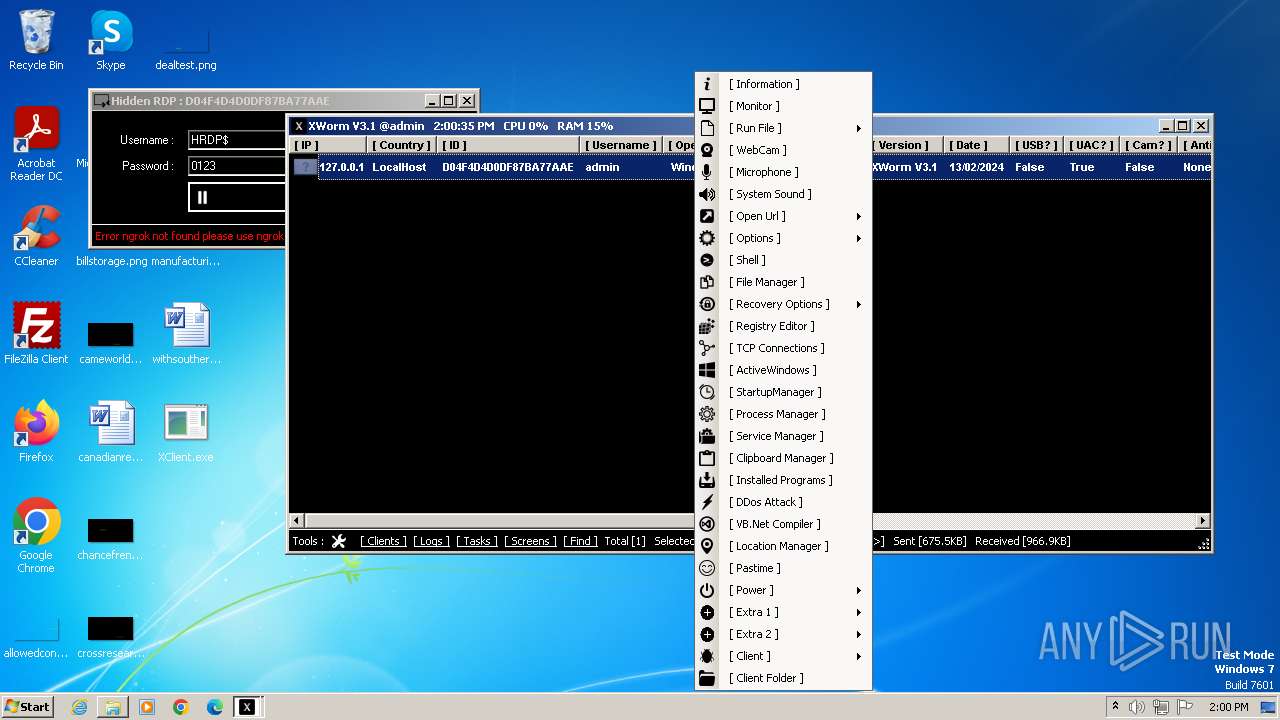
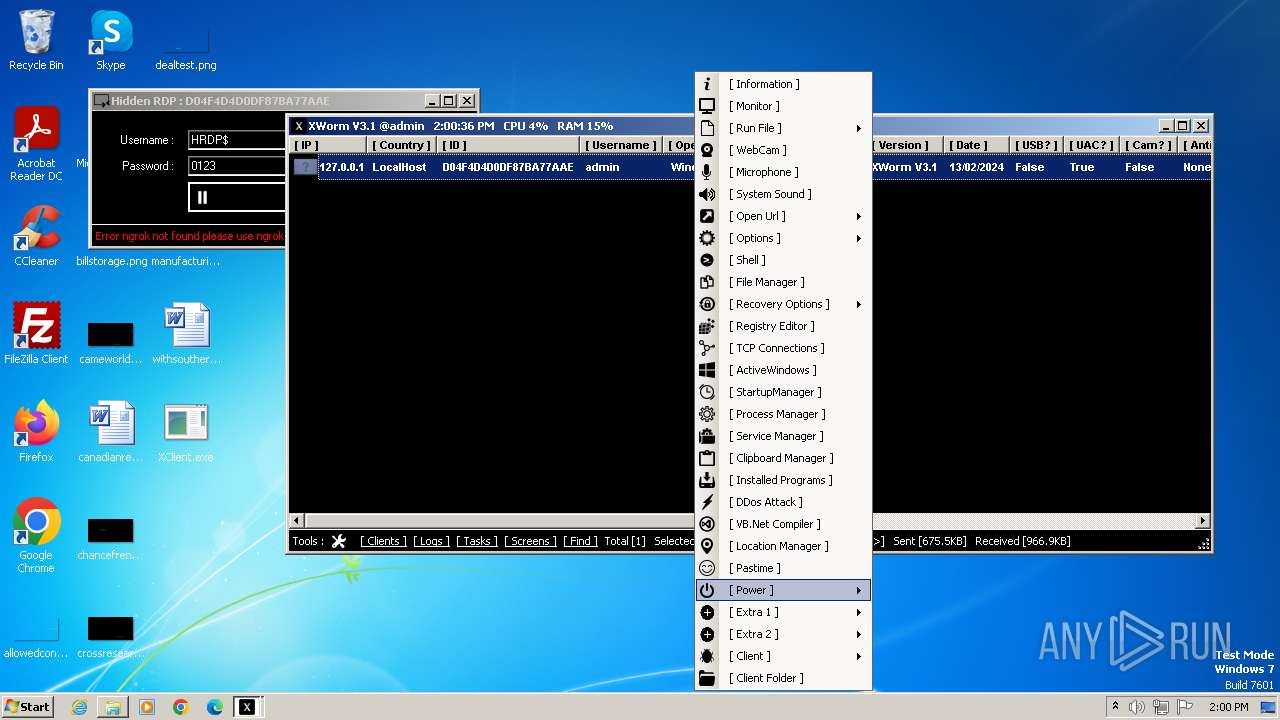
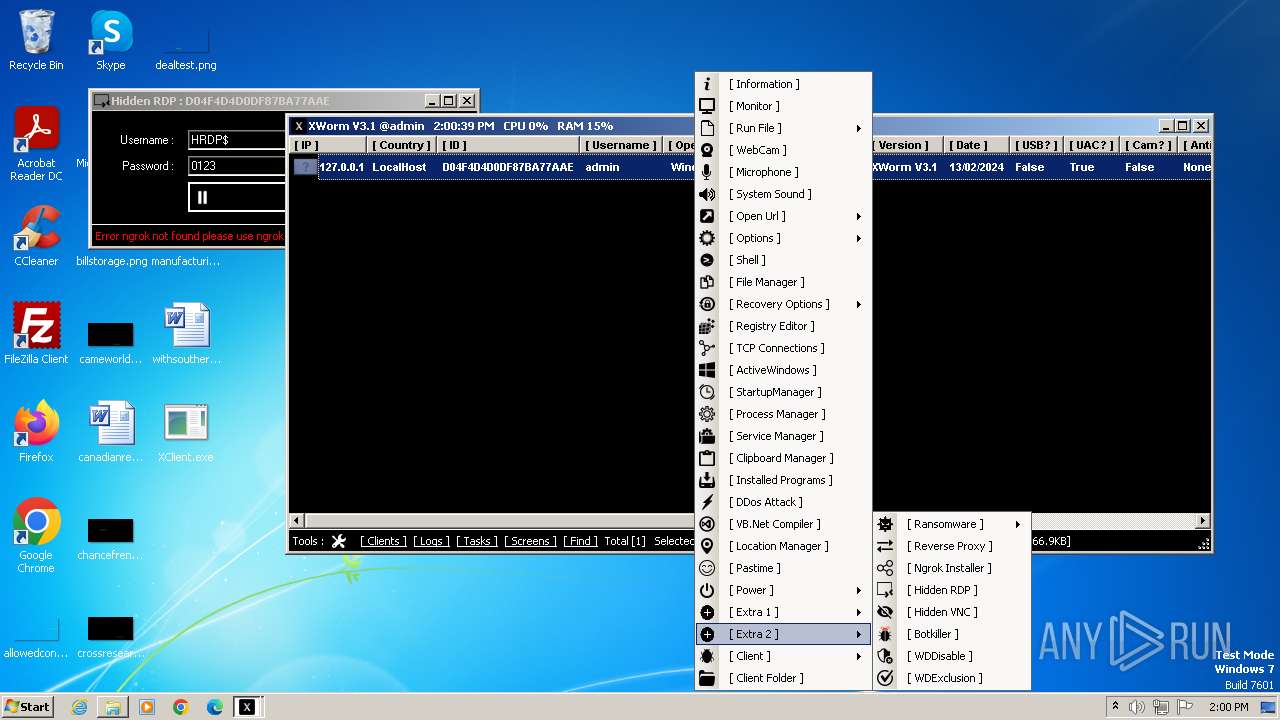
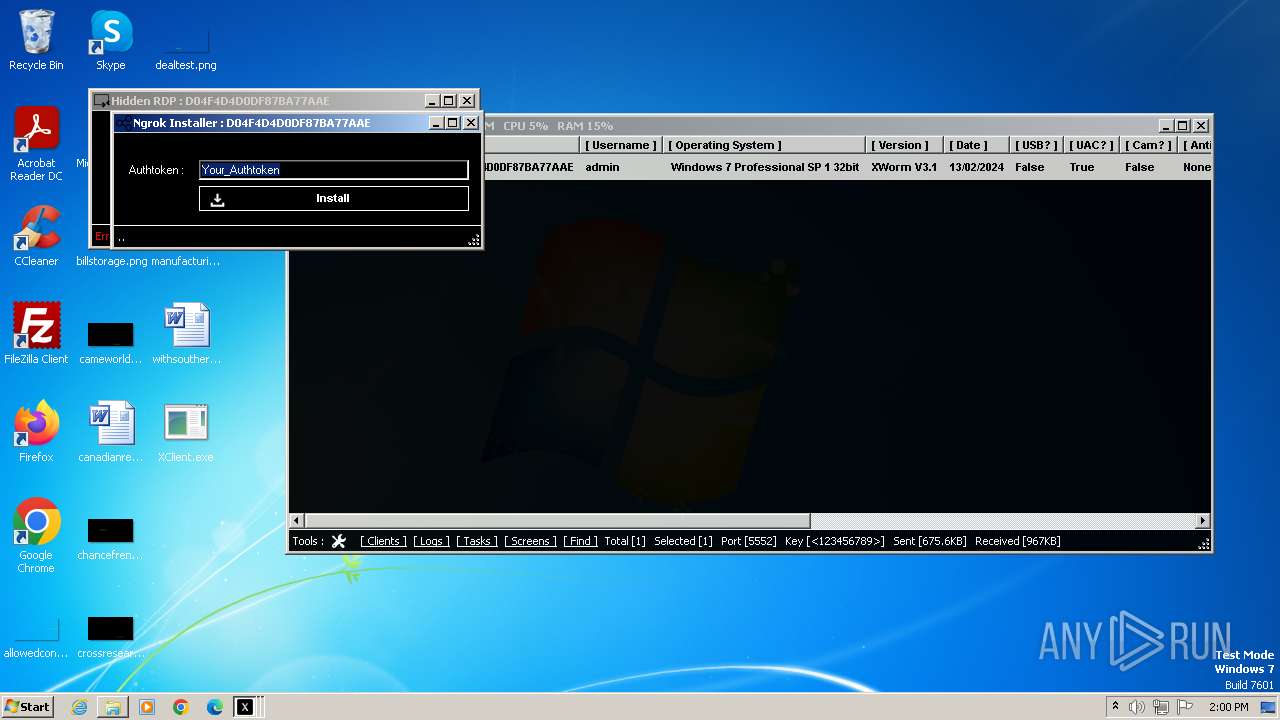
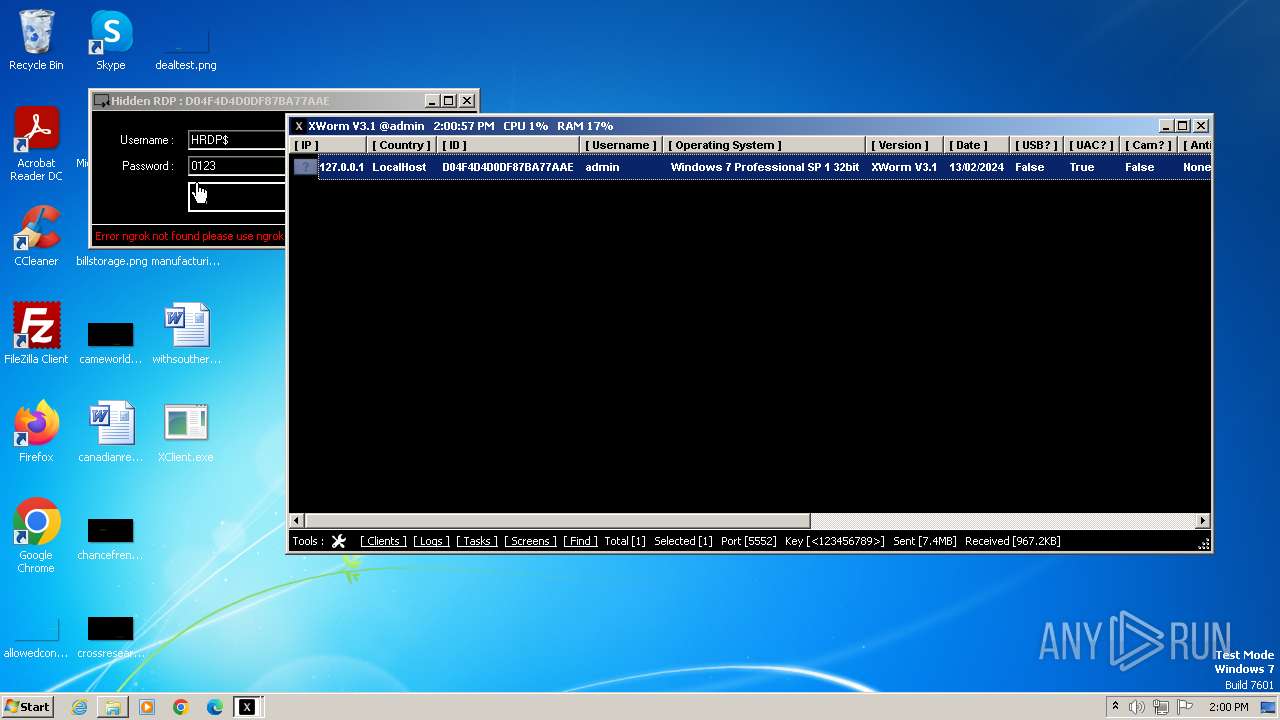
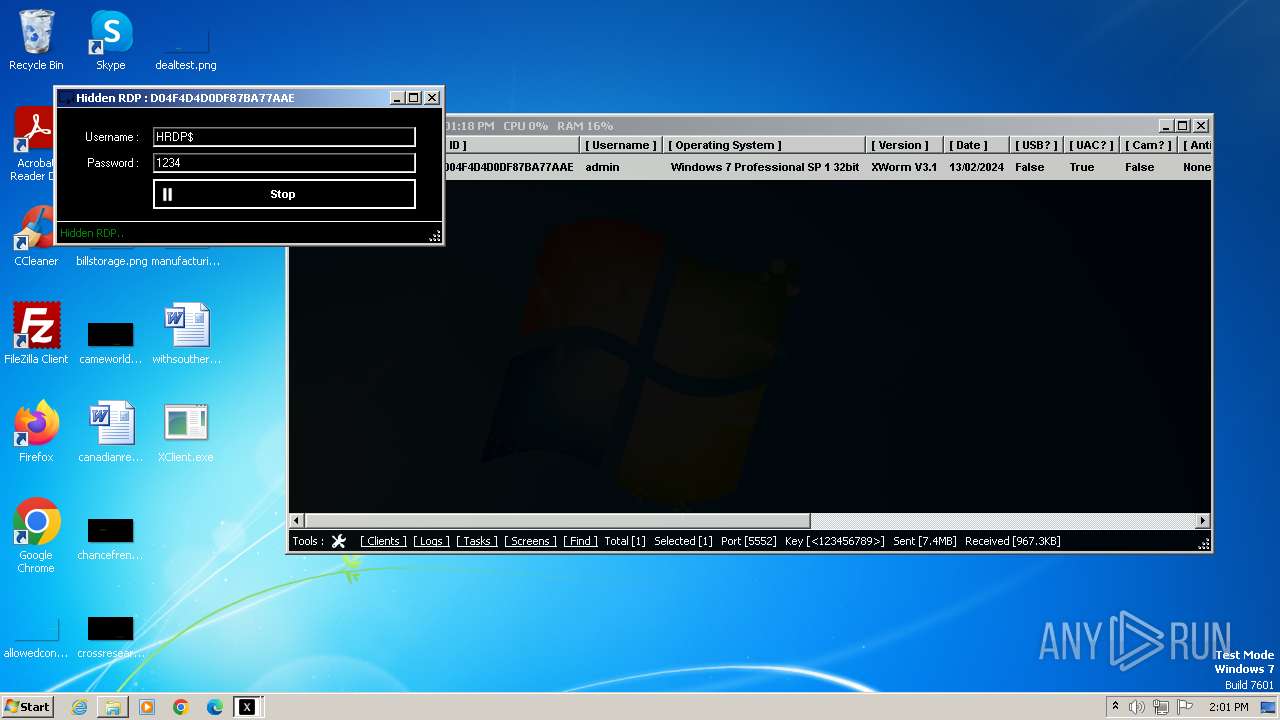
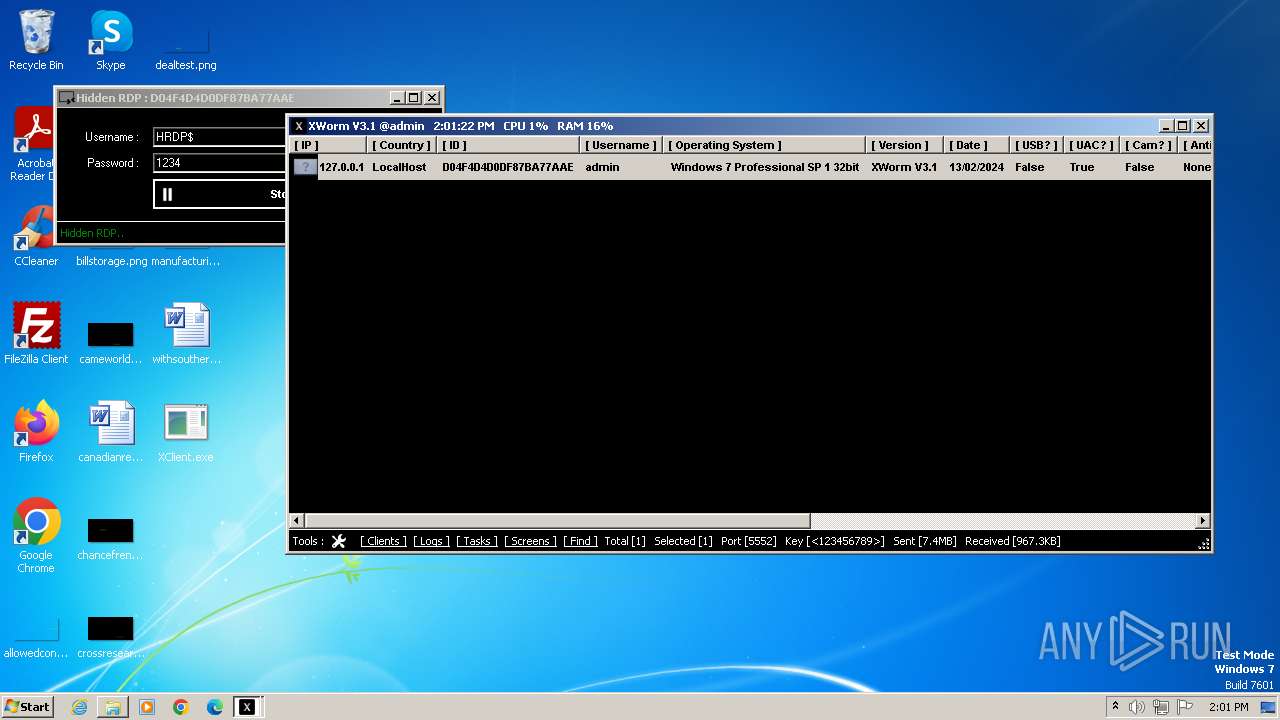
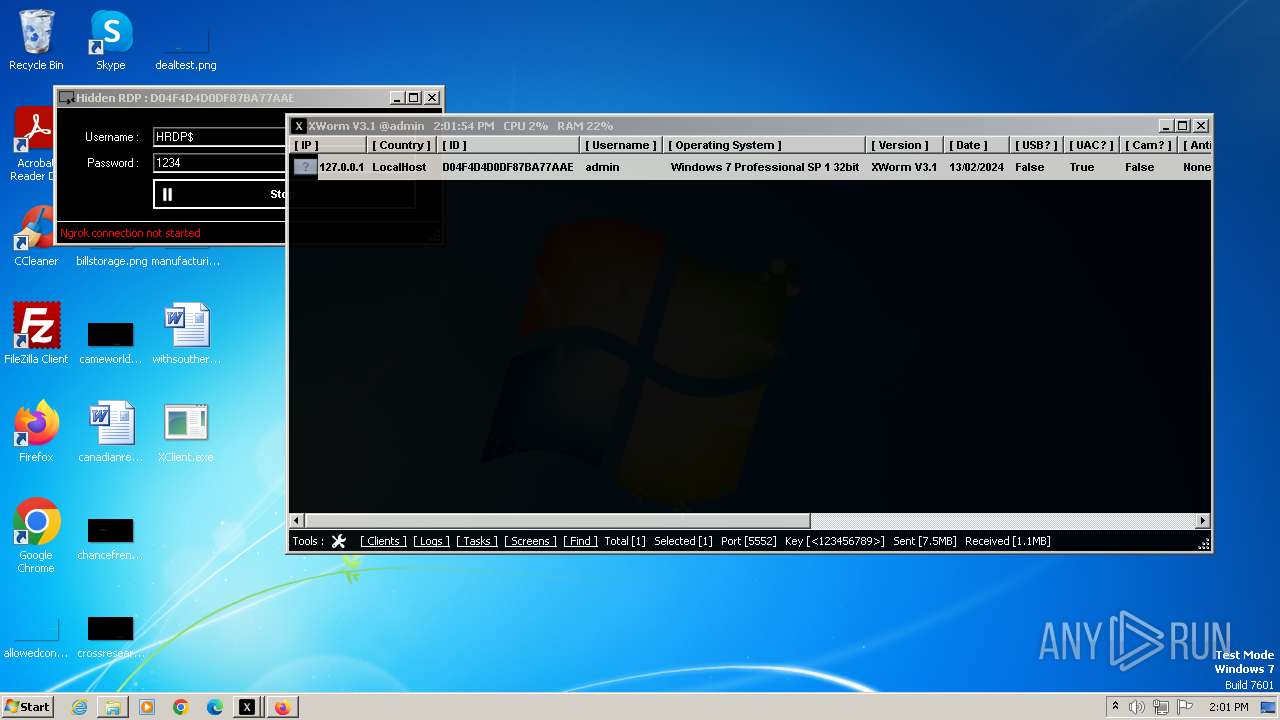
XWorm
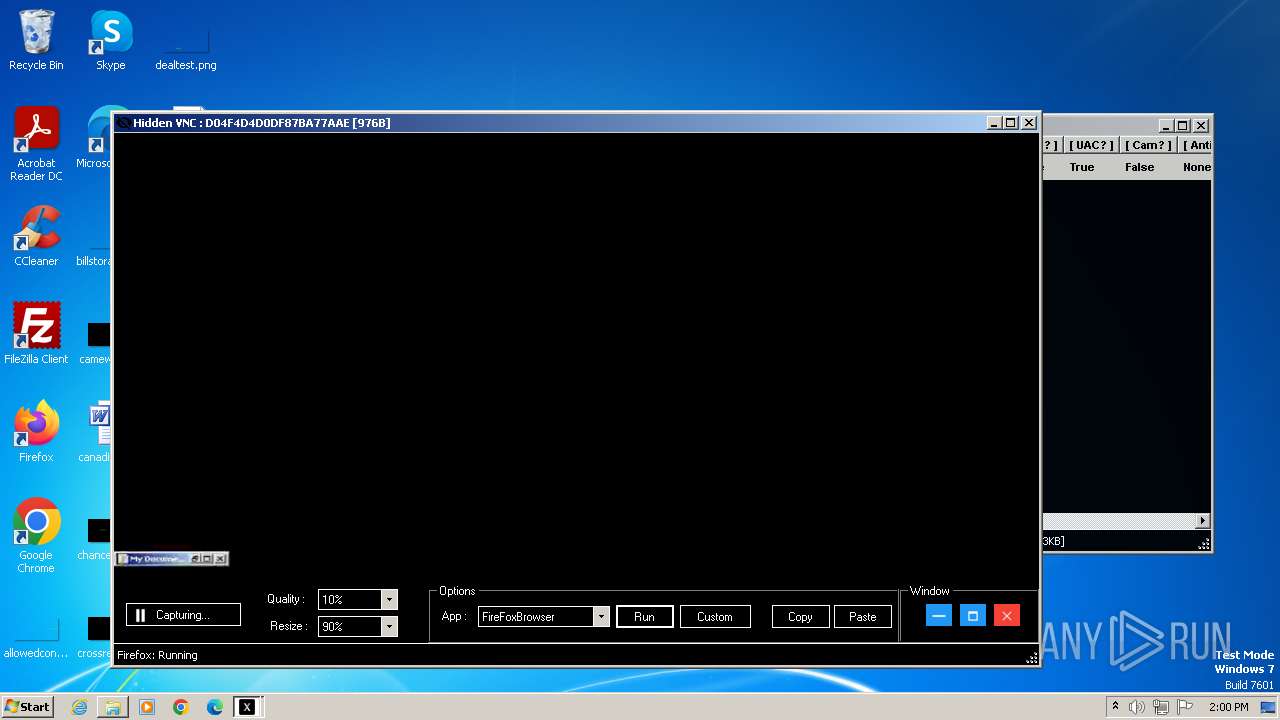
(PID) Process(3044) XClient.exe
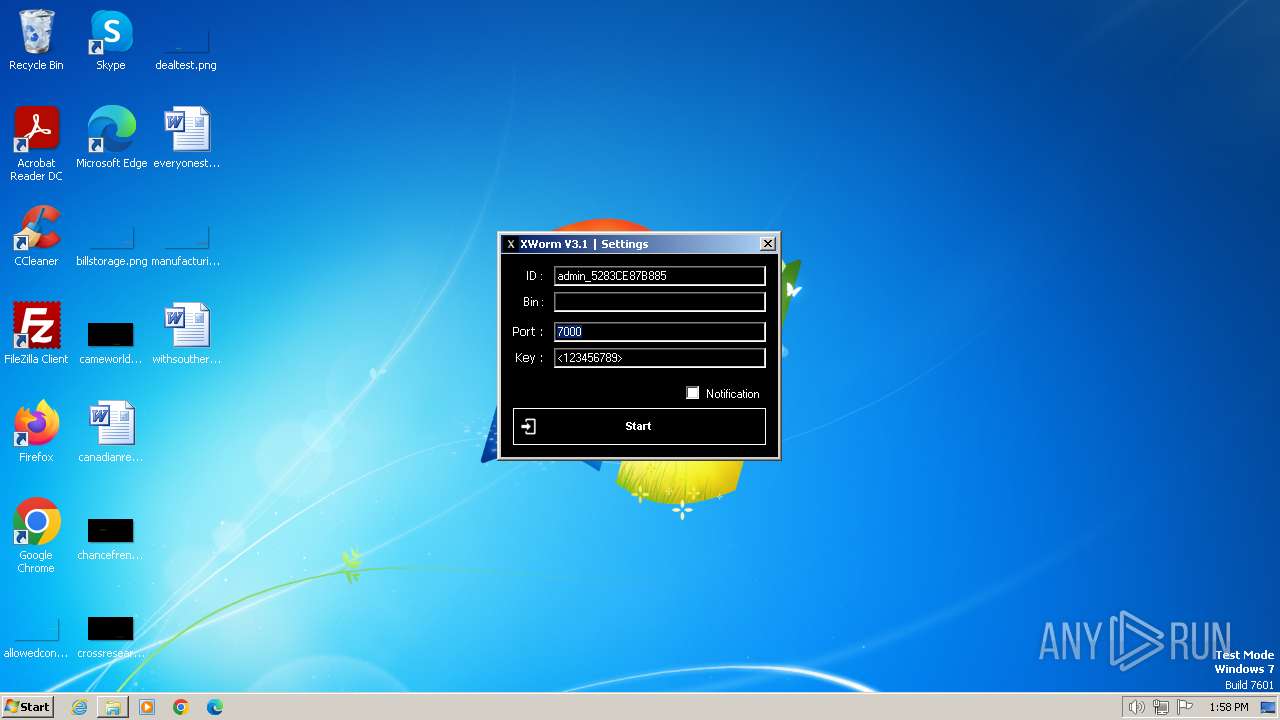
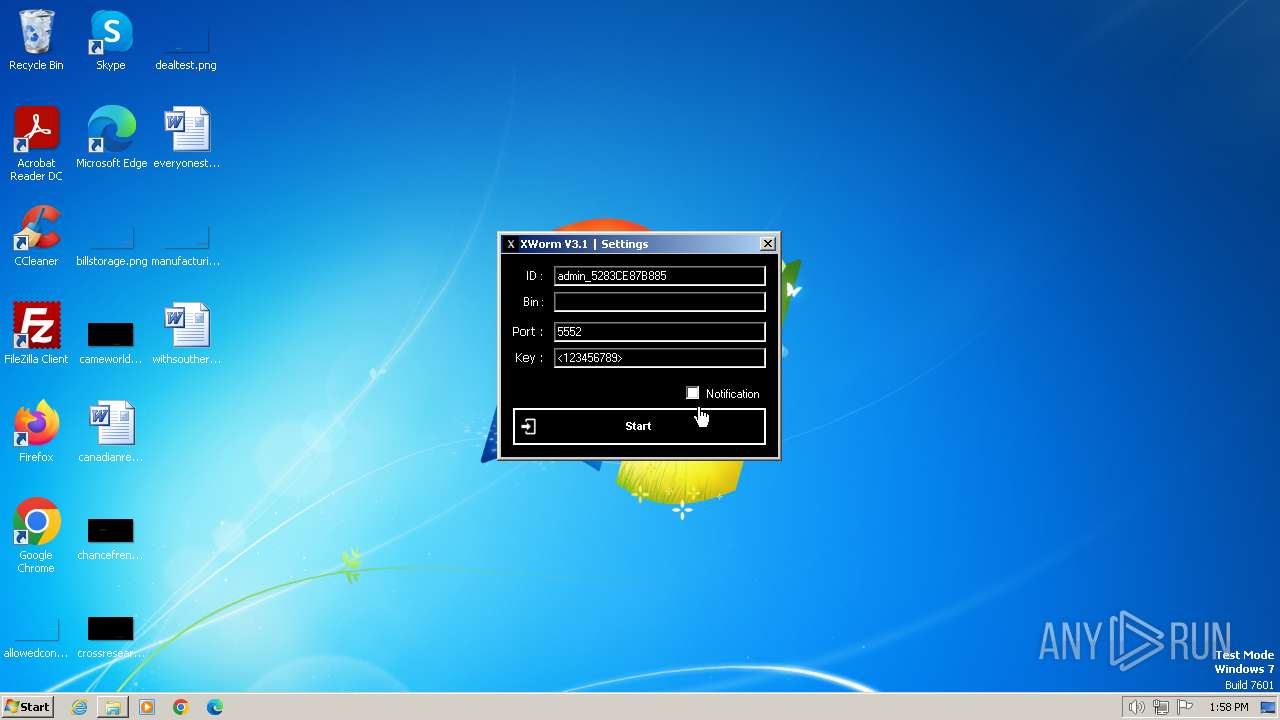
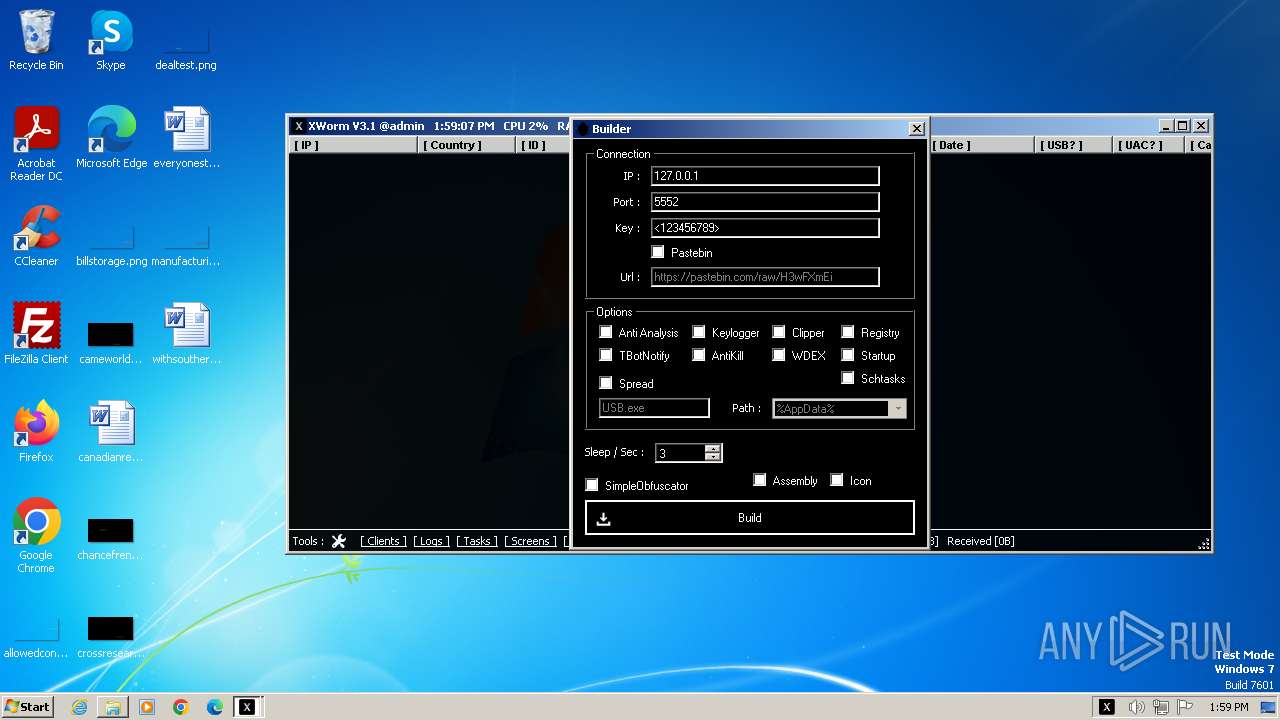
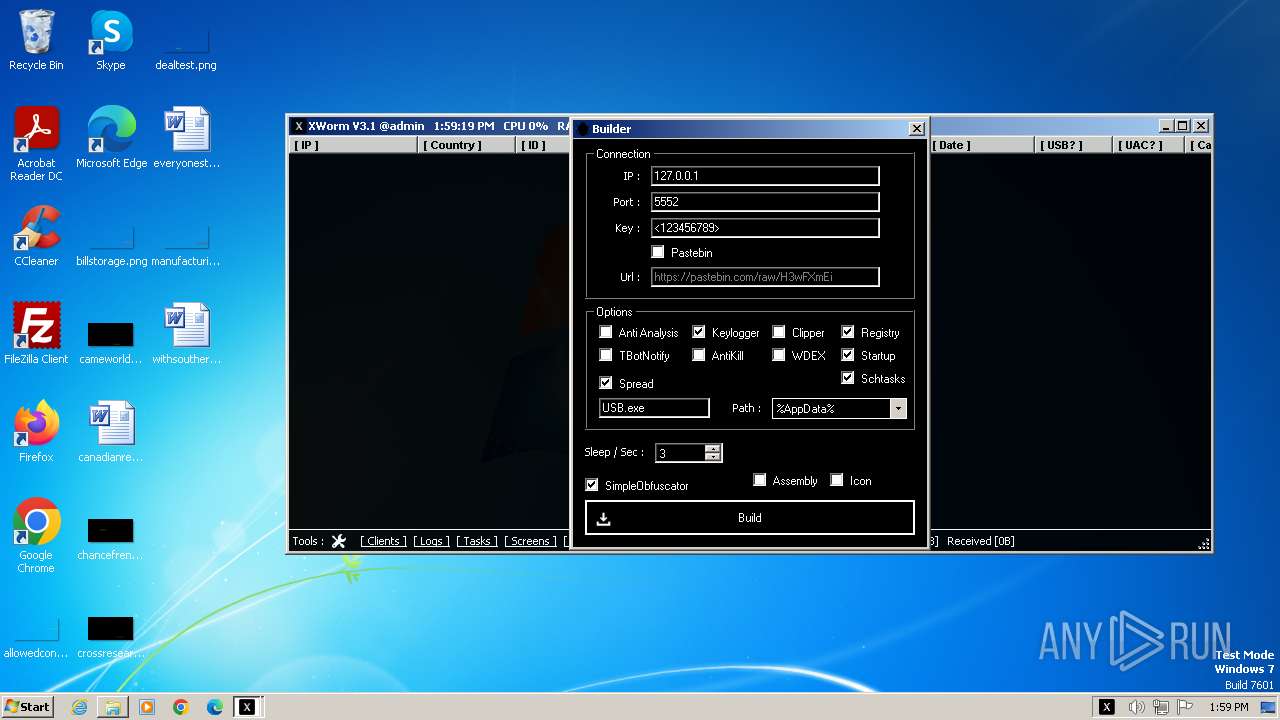
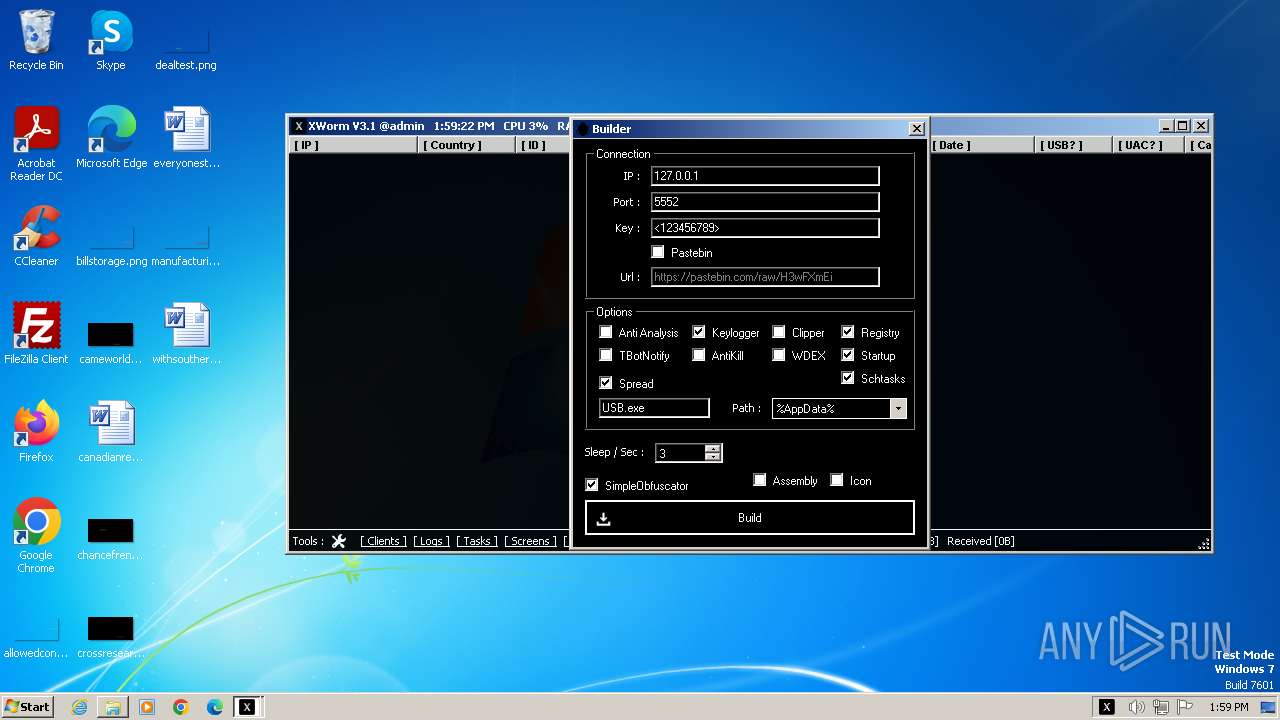
C2127.0.0.1:5552
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
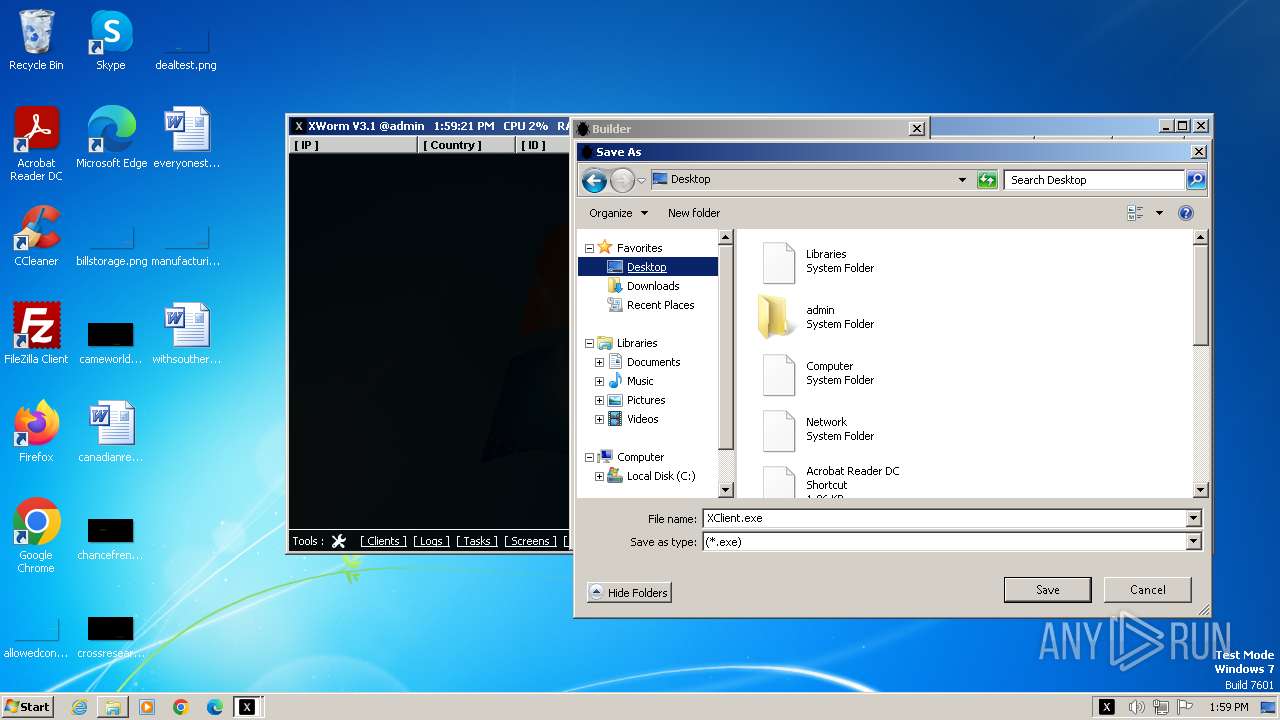
USB drop nameUSB.exe
MutexgMg6FfZNiwnyj3xJ
Total processes
143
Monitored processes
80
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 296 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe" 127.0.0.1 5552 <123456789> D04F4D4D0DF87BA77AAE | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | XClient.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.10.25028.0 built by: VCTOOLSD15RTM Modules
| |||||||||||||||
| 952 | "C:\Program Files\Mozilla Firefox\pingsender.exe" https://incoming.telemetry.mozilla.org/submit/telemetry/ff2dee31-8a9e-407b-aaa7-c2d495132821/event/Firefox/115.0.2/release/20230710165010?v=4 "C:\Users\admin\AppData\Local\Mozilla\Firefox\FireFox Data\saved-telemetry-pings\ff2dee31-8a9e-407b-aaa7-c2d495132821" | C:\Program Files\Mozilla Firefox\pingsender.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Foundation Integrity Level: MEDIUM Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 1220 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1264 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3800.1.1233474015\1682525484" -parentBuildID 20230710165010 -prefsHandle 1520 -prefMapHandle 1516 -prefsLen 25853 -prefMapSize 241425 -appDir "C:\Program Files\Mozilla Firefox\browser" - {ed389b9c-f68b-4f5a-9108-8301da506ca6} 3800 "\\.\pipe\gecko-crash-server-pipe.3800" 1532 f5e5710 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 1316 | "C:\Program Files\Mozilla Firefox\firefox.exe" -no-remote -profile "C:\Users\admin\AppData\Local\Mozilla\Firefox\FireFox Data" --attempting-deelevation | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 1544 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3800.6.830265841\872799123" -childID 5 -isForBrowser -prefsHandle 4040 -prefMapHandle 4044 -prefsLen 26511 -prefMapSize 241425 -jsInitHandle 932 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {acf98477-5734-4ac5-86b2-10e5f54a606d} 3800 "\\.\pipe\gecko-crash-server-pipe.3800" 4020 214b6280 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 1608 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --mojo-platform-channel-handle=3544 --field-trial-handle=1136,i,6887228852201500062,1204649824360669997,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1636 | powershell.exe -c explorer shell:::{3080F90E-D7AD-11D9-BD98-0000947B0257} | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cvtres.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1696 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3084 --field-trial-handle=1136,i,6887228852201500062,1204649824360669997,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1776 | C:\Users\admin\AppData\Local\Temp\ngrok.exe config add-authtoken 1234 | C:\Users\admin\AppData\Local\Temp\ngrok.exe | — | XClient.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
76 943
Read events
76 213
Write events
629
Delete events
101
Modification events
| (PID) Process: | (3864) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3864) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3864) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3864) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3864) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3864) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3864) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3864) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3864) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3864) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
56
Suspicious files
476
Text files
270
Unknown types
269
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3864 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF17f30a.TMP | — | |
MD5:— | SHA256:— | |||
| 3864 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3864 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:358570F689377CE6838812643E03734B | SHA256:5B41FCC2E1A843AEAB9437B06E27B798870FF10D86A51B163BF48862BCD32590 | |||
| 3864 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 3864 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 3864 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | text | |
MD5:E53573A93829681410D5E7DBB1B61C78 | SHA256:A82D28F2C1E22A2AE0ABC5F5AF0CC8EE7AD913BAB3A0BF84CE6D8D23F67E06A3 | |||
| 3864 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF17fec2.TMP | — | |
MD5:— | SHA256:— | |||
| 3864 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3864 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF17f32a.TMP | text | |
MD5:05CF4C3C5148DA6355D3561A9EAA5E8A | SHA256:8D720243F6876898E4F197C8867C4CEE69F1C7335C55B8A29C120B1028D93E41 | |||
| 3864 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\AutofillStrikeDatabase\LOG.old~RF181056.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
52
TCP/UDP connections
124
DNS requests
238
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYTBmQUFZUHRkSkgtb01uSGNvRHZ2Tm5HQQ/1.0.0.15_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | unknown |
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acf5iuk6pnjlc6lnxtqm5ki6eoqq_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win_aclnpjhtsv44pze3qmxsxb7fq66q.crx3 | unknown | binary | 3.07 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acf5iuk6pnjlc6lnxtqm5ki6eoqq_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win_aclnpjhtsv44pze3qmxsxb7fq66q.crx3 | unknown | binary | 40.9 Kb | unknown |
856 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYTBmQUFZUHRkSkgtb01uSGNvRHZ2Tm5HQQ/1.0.0.15_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | binary | 3.07 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acf5iuk6pnjlc6lnxtqm5ki6eoqq_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win_aclnpjhtsv44pze3qmxsxb7fq66q.crx3 | unknown | binary | 32.9 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acf5iuk6pnjlc6lnxtqm5ki6eoqq_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win_aclnpjhtsv44pze3qmxsxb7fq66q.crx3 | unknown | binary | 29.9 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acf5iuk6pnjlc6lnxtqm5ki6eoqq_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win_aclnpjhtsv44pze3qmxsxb7fq66q.crx3 | unknown | binary | 44.3 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acf5iuk6pnjlc6lnxtqm5ki6eoqq_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win_aclnpjhtsv44pze3qmxsxb7fq66q.crx3 | unknown | binary | 23.4 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acf5iuk6pnjlc6lnxtqm5ki6eoqq_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win_aclnpjhtsv44pze3qmxsxb7fq66q.crx3 | unknown | binary | 168 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acf5iuk6pnjlc6lnxtqm5ki6eoqq_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win_aclnpjhtsv44pze3qmxsxb7fq66q.crx3 | unknown | binary | 84.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3864 | chrome.exe | 239.255.255.250:1900 | — | — | — | unknown |
3948 | chrome.exe | 64.233.167.84:443 | accounts.google.com | GOOGLE | US | unknown |
3948 | chrome.exe | 140.82.121.4:443 | github.com | GITHUB | US | unknown |
3948 | chrome.exe | 185.199.109.154:443 | github.githubassets.com | FASTLY | US | unknown |
3948 | chrome.exe | 142.250.185.74:443 | safebrowsing.googleapis.com | GOOGLE | US | whitelisted |
3948 | chrome.exe | 185.199.108.133:443 | avatars.githubusercontent.com | FASTLY | US | unknown |
3948 | chrome.exe | 142.250.184.202:443 | content-autofill.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
github.com |
| shared |
github.githubassets.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
avatars.githubusercontent.com |
| whitelisted |
github-cloud.s3.amazonaws.com |
| shared |
user-images.githubusercontent.com |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
collector.github.com |
| whitelisted |
www.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1336 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query to a *.ngrok domain (ngrok.com) |
Process | Message |
|---|---|
XWorm V3.1.exe | Obfuscated!
|
cvtres.exe | MouseMove :281;693
|
cvtres.exe | MouseMove :367;567
|
cvtres.exe | MouseMove :375;552
|
cvtres.exe | MouseMove :375;551
|
cvtres.exe | MouseMove :387;544
|
cvtres.exe | MouseMove :394;541
|
cvtres.exe | MouseMove :401;538
|
cvtres.exe | MouseMove :476;504
|
cvtres.exe | MouseMove :555;469
|