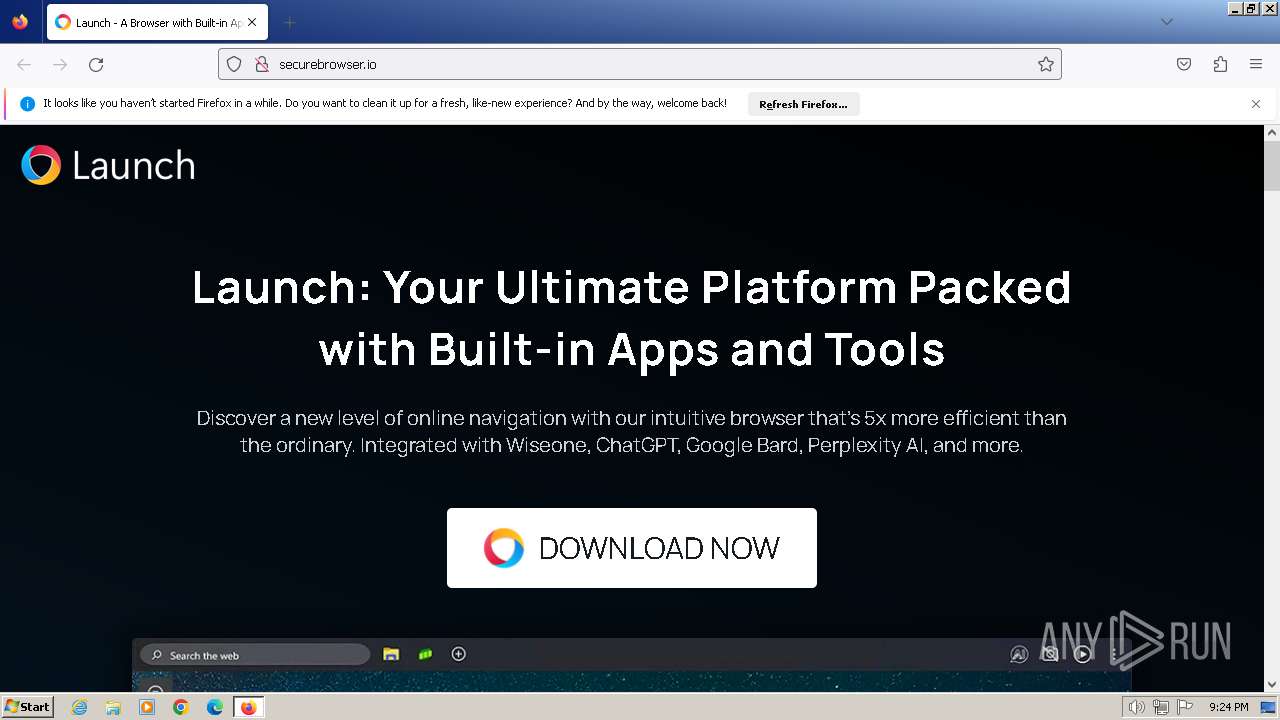
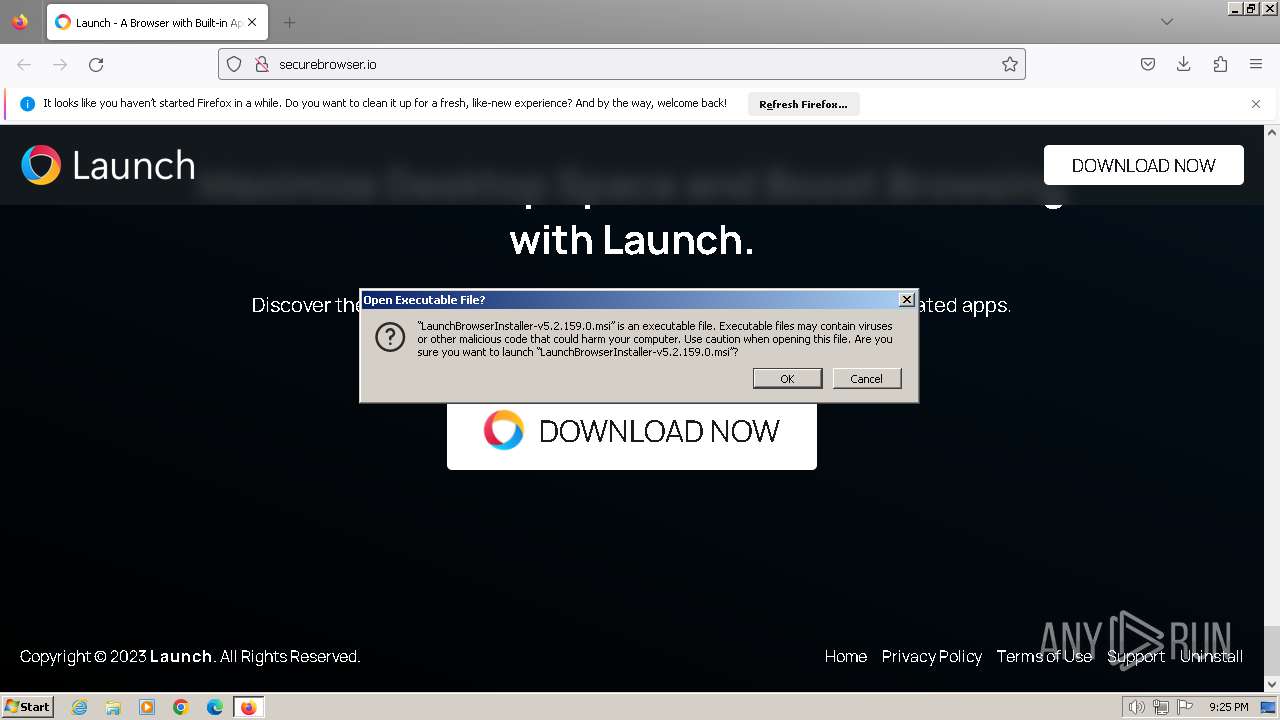
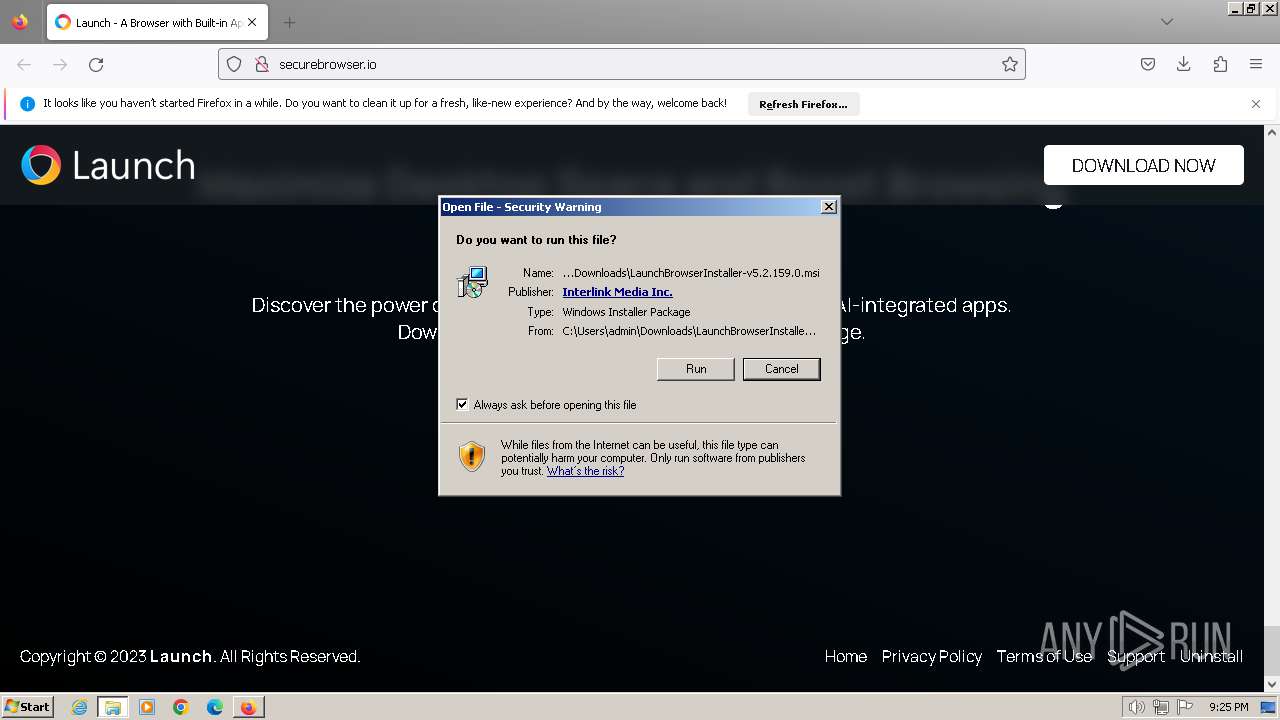
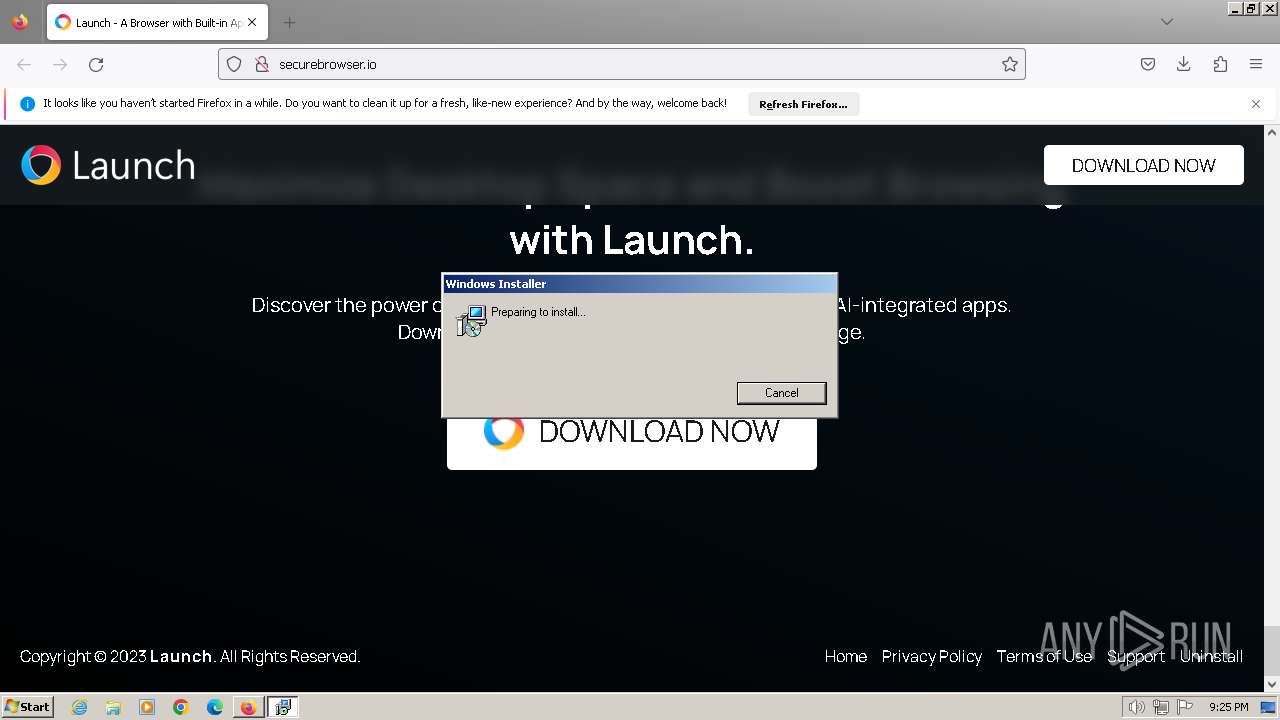
| URL: | securebrowser.io |
| Full analysis: | https://app.any.run/tasks/fba2cdd0-4bea-4292-a65a-b6837ee39358 |
| Verdict: | Malicious activity |
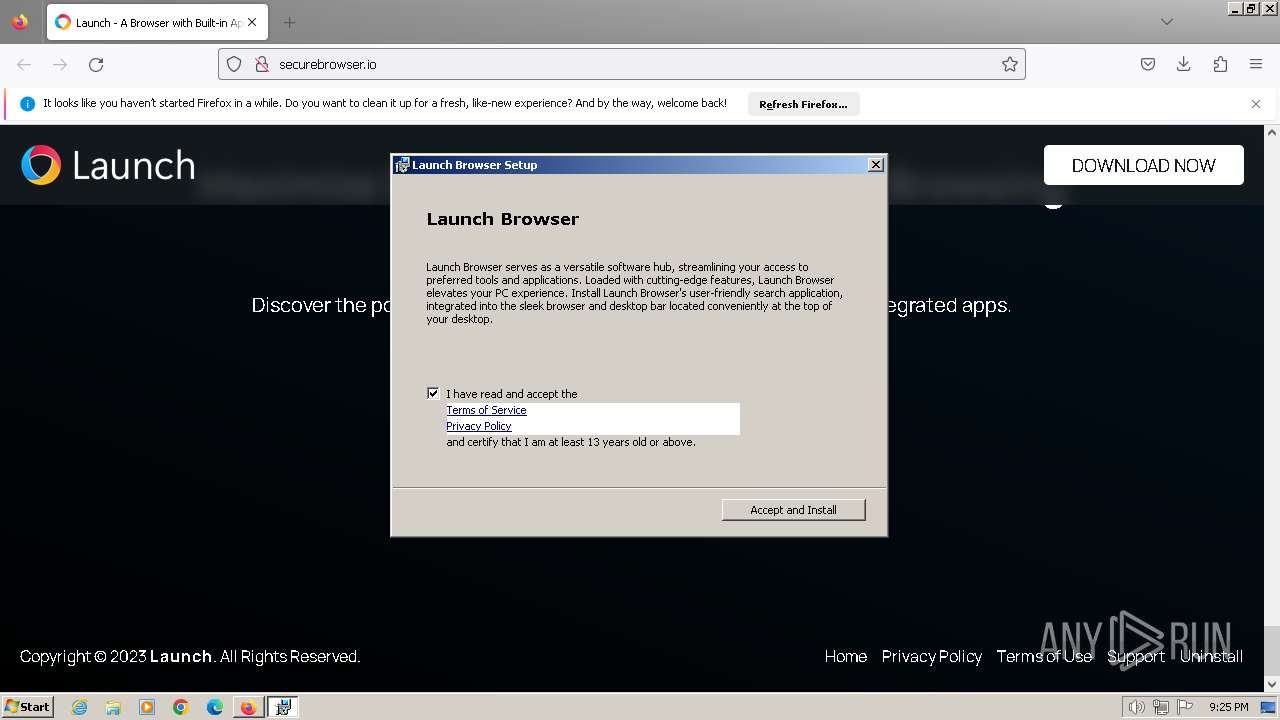
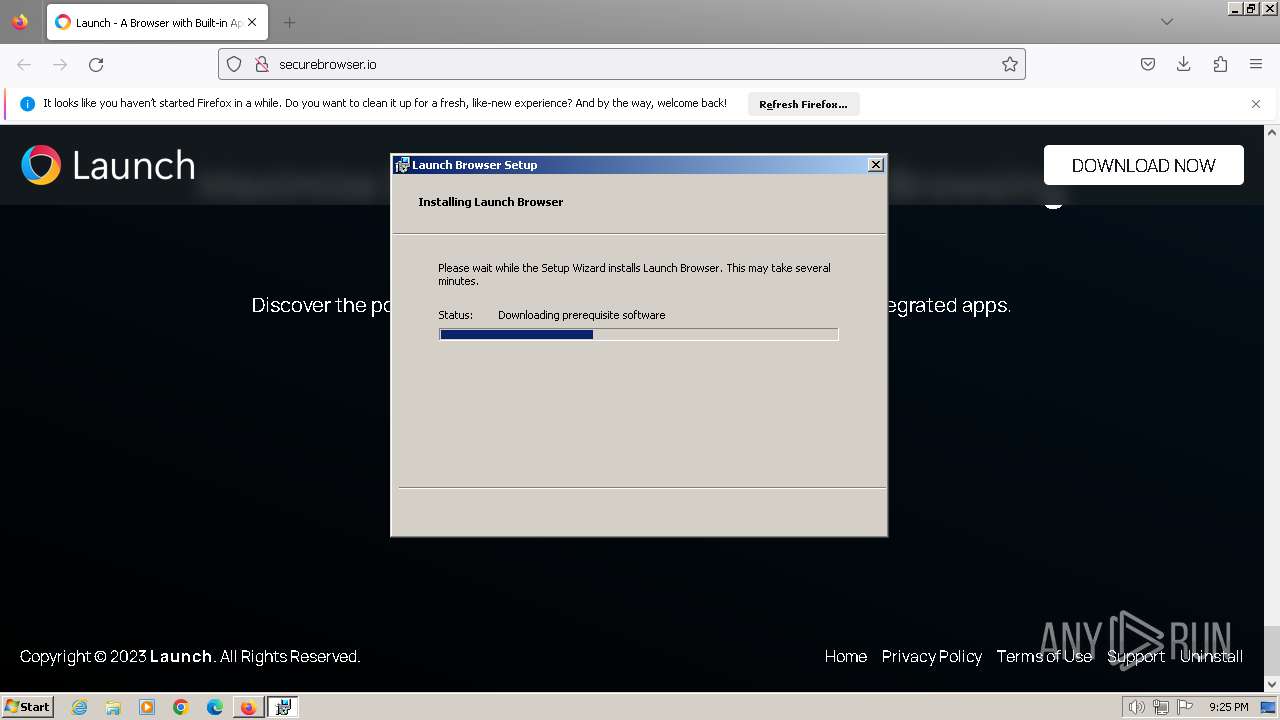
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | January 07, 2024, 21:24:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C13F1C1F6975355A16EA85A28FB9D90C |
| SHA1: | 8AC78076946E1CEC3EEA26F747D149F101C0F032 |
| SHA256: | 3F327CE05D8FBFA11F03C27B529CA33309F6CD5117DB0A2FC28B6A492FD3C318 |
| SSDEEP: | 3:Xioy4K:SohK |
MALICIOUS
Changes powershell execution policy (Bypass)
- msiexec.exe (PID: 3756)
- msiexec.exe (PID: 2184)
- msiexec.exe (PID: 3500)
Bypass execution policy to execute commands
- powershell.exe (PID: 3996)
- powershell.exe (PID: 2316)
- powershell.exe (PID: 2952)
- powershell.exe (PID: 4048)
- powershell.exe (PID: 3836)
- powershell.exe (PID: 1848)
- powershell.exe (PID: 2452)
- powershell.exe (PID: 3172)
- powershell.exe (PID: 3320)
- powershell.exe (PID: 3108)
- powershell.exe (PID: 3892)
- powershell.exe (PID: 1808)
- powershell.exe (PID: 1560)
- powershell.exe (PID: 452)
- powershell.exe (PID: 2928)
- powershell.exe (PID: 2100)
- powershell.exe (PID: 3744)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 3756)
- msiexec.exe (PID: 2184)
- msiexec.exe (PID: 3500)
The process executes Powershell scripts
- msiexec.exe (PID: 3756)
- msiexec.exe (PID: 2184)
- msiexec.exe (PID: 3500)
The process hide an interactive prompt from the user
- msiexec.exe (PID: 3756)
- msiexec.exe (PID: 2184)
- msiexec.exe (PID: 3500)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 3756)
- msiexec.exe (PID: 2184)
- msiexec.exe (PID: 3500)
Reads the Internet Settings
- powershell.exe (PID: 2316)
- powershell.exe (PID: 2952)
- msiexec.exe (PID: 3756)
- powershell.exe (PID: 3836)
- powershell.exe (PID: 1848)
- powershell.exe (PID: 2452)
- DBar.exe (PID: 1736)
- powershell.exe (PID: 3172)
- powershell.exe (PID: 3320)
- powershell.exe (PID: 3108)
- powershell.exe (PID: 3892)
- powershell.exe (PID: 1808)
- powershell.exe (PID: 1560)
- powershell.exe (PID: 452)
- powershell.exe (PID: 3744)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 3704)
The process creates files with name similar to system file names
- msiexec.exe (PID: 3704)
Reads settings of System Certificates
- DBar.exe (PID: 1736)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 3892)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 3756)
Checks Windows Trust Settings
- msiexec.exe (PID: 3704)
INFO
Application launched itself
- firefox.exe (PID: 2040)
- firefox.exe (PID: 124)
- msiexec.exe (PID: 3704)
- msiexec.exe (PID: 3756)
Manual execution by a user
- msiexec.exe (PID: 3540)
Checks supported languages
- msiexec.exe (PID: 3704)
- msiexec.exe (PID: 3756)
- msiexec.exe (PID: 2184)
- DBar.exe (PID: 1736)
- msiexec.exe (PID: 3500)
- msiexec.exe (PID: 3772)
The process uses the downloaded file
- firefox.exe (PID: 124)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 3540)
- powershell.exe (PID: 3996)
- powershell.exe (PID: 4048)
- powershell.exe (PID: 2316)
- powershell.exe (PID: 2952)
- powershell.exe (PID: 3836)
- powershell.exe (PID: 2452)
- powershell.exe (PID: 1848)
- powershell.exe (PID: 3172)
- powershell.exe (PID: 3320)
- powershell.exe (PID: 3108)
- powershell.exe (PID: 3892)
- powershell.exe (PID: 1808)
- powershell.exe (PID: 1560)
- powershell.exe (PID: 452)
- powershell.exe (PID: 2928)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 2100)
Drops the executable file immediately after the start
- msiexec.exe (PID: 3540)
- firefox.exe (PID: 124)
- msiexec.exe (PID: 3704)
Reads the machine GUID from the registry
- msiexec.exe (PID: 3704)
- msiexec.exe (PID: 3756)
- msiexec.exe (PID: 2184)
- DBar.exe (PID: 1736)
- msiexec.exe (PID: 3500)
- msiexec.exe (PID: 3772)
Create files in a temporary directory
- msiexec.exe (PID: 3756)
- powershell.exe (PID: 4048)
- powershell.exe (PID: 2316)
- powershell.exe (PID: 3996)
- powershell.exe (PID: 2952)
- powershell.exe (PID: 3836)
- msiexec.exe (PID: 2184)
- powershell.exe (PID: 1848)
- msiexec.exe (PID: 3704)
- powershell.exe (PID: 2452)
- powershell.exe (PID: 3172)
- powershell.exe (PID: 3320)
- msiexec.exe (PID: 3500)
- powershell.exe (PID: 3108)
- powershell.exe (PID: 3892)
- powershell.exe (PID: 1808)
- powershell.exe (PID: 2928)
- powershell.exe (PID: 1560)
- powershell.exe (PID: 452)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 2100)
Reads the computer name
- msiexec.exe (PID: 3756)
- msiexec.exe (PID: 3704)
- msiexec.exe (PID: 2184)
- DBar.exe (PID: 1736)
- msiexec.exe (PID: 3500)
- msiexec.exe (PID: 3772)
Reads Environment values
- msiexec.exe (PID: 3756)
- msiexec.exe (PID: 2184)
- DBar.exe (PID: 1736)
- msiexec.exe (PID: 3500)
Creates files or folders in the user directory
- powershell.exe (PID: 4048)
- msiexec.exe (PID: 3756)
- msiexec.exe (PID: 3704)
Unusual connection from system programs
- powershell.exe (PID: 2316)
- powershell.exe (PID: 2952)
- powershell.exe (PID: 3836)
- powershell.exe (PID: 1848)
- powershell.exe (PID: 2452)
- powershell.exe (PID: 3172)
- powershell.exe (PID: 3320)
- powershell.exe (PID: 3108)
- powershell.exe (PID: 452)
- powershell.exe (PID: 1808)
- powershell.exe (PID: 1560)
- powershell.exe (PID: 3744)
Checks proxy server information
- msiexec.exe (PID: 3756)
The process drops C-runtime libraries
- msiexec.exe (PID: 3704)
Process drops legitimate windows executable
- msiexec.exe (PID: 3704)
Executes as Windows Service
- VSSVC.exe (PID: 1548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
95
Monitored processes
39
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Mozilla Firefox\firefox.exe" securebrowser.io | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 452 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pss76C6.tmp.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1044 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="124.1.910292409\1264707787" -parentBuildID 20230710165010 -prefsHandle 1420 -prefMapHandle 1416 -prefsLen 28600 -prefMapSize 244195 -appDir "C:\Program Files\Mozilla Firefox\browser" - {5eacf525-a8b9-427a-8ec5-af305ac92794} 124 "\\.\pipe\gecko-crash-server-pipe.124" 1432 ef1e9d0 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 1392 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="124.0.78731527\967713355" -parentBuildID 20230710165010 -prefsHandle 1108 -prefMapHandle 1100 -prefsLen 28523 -prefMapSize 244195 -appDir "C:\Program Files\Mozilla Firefox\browser" - {5f8cca67-5412-432a-b04e-a9d2427b5d4e} 124 "\\.\pipe\gecko-crash-server-pipe.124" 1180 d4a8790 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 1544 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="124.2.56266124\2124039718" -childID 1 -isForBrowser -prefsHandle 1844 -prefMapHandle 1812 -prefsLen 24491 -prefMapSize 244195 -jsInitHandle 916 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {38649056-3bb4-4fe3-bea7-6e1452b8ea53} 124 "\\.\pipe\gecko-crash-server-pipe.124" 2004 12a89560 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 1548 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1560 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pss84CD.ps1" -propFile "C:\Users\admin\AppData\Local\Temp\msi84BA.txt" -scriptFile "C:\Users\admin\AppData\Local\Temp\scr84BB.ps1" -scriptArgsFile "C:\Users\admin\AppData\Local\Temp\scr84CC.txt" -propSep " :<->: " -lineSep " <<:>> " -testPrefix "_testValue." | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1736 | "C:\Users\admin\AppData\Roaming\LaunchBrowserBar\bar\DBar.exe" /RegisterOnly | C:\Users\admin\AppData\Roaming\LaunchBrowserBar\bar\DBar.exe | msiexec.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: DBar Exit code: 0 Version: 1.10.28.21718 Modules
| |||||||||||||||
| 1808 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pss71F0.tmp.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1848 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pss31C2.tmp.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
45 134
Read events
44 914
Write events
184
Delete events
36
Modification events
| (PID) Process: | (2040) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 2166C0A101000000 | |||
| (PID) Process: | (124) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 044CC1A101000000 | |||
| (PID) Process: | (124) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (124) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (124) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (124) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (124) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (124) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (124) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SetDefaultBrowserUserChoice |
Value: 1 | |||
| (PID) Process: | (124) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|AppLastRunTime |
Value: D14E5F3C23B0D901 | |||
Executable files
78
Suspicious files
232
Text files
113
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 124 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:B7A3C61D0C144CC5E166B1E769CA8F8C | SHA256:7FADCB77FFACA6B9E9F15C6F1CD3AAD4C20DCD90FA92429A627A3A7110CA2644 | |||
| 124 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 124 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | text | |
MD5:60E0DE9E05EC76C749D80F0D15A81B21 | SHA256:08252FA62CCCCD316474E20CC7317A6B5C932B2C972234318E8CCDA39EC2EF48 | |||
| 124 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 124 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 124 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 124 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 124 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 124 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 124 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage.sqlite-journal | binary | |
MD5:E87B4A70CBF63022EA69A8509979F151 | SHA256:4232BC81273E69745DFBE25E44CD863F745A7BF8E4B98900B916DEFF46503248 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
54
TCP/UDP connections
86
DNS requests
160
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
124 | firefox.exe | GET | 200 | 13.32.27.46:80 | http://securebrowser.io/ | unknown | html | 9.56 Kb | unknown |
124 | firefox.exe | GET | — | 13.32.27.46:80 | http://securebrowser.io/images/launch-chromium-new.png | unknown | — | — | unknown |
124 | firefox.exe | GET | — | 13.32.27.46:80 | http://securebrowser.io/images/launch-apps-new.png | unknown | — | — | unknown |
124 | firefox.exe | POST | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 471 b | unknown |
124 | firefox.exe | GET | — | 13.32.27.46:80 | http://securebrowser.io/images/launch-dock-new.png | unknown | — | — | unknown |
124 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | text | 90 b | unknown |
124 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | text | 8 b | unknown |
124 | firefox.exe | POST | 200 | 184.24.77.48:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
124 | firefox.exe | POST | 200 | 184.24.77.48:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
124 | firefox.exe | GET | 200 | 13.32.27.46:80 | http://securebrowser.io/css/styles.css | unknown | image | 92.6 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
124 | firefox.exe | 13.32.27.46:80 | securebrowser.io | AMAZON-02 | US | unknown |
124 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
124 | firefox.exe | 34.117.237.239:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
124 | firefox.exe | 44.215.47.169:443 | spocs.getpocket.com | AMAZON-AES | US | unknown |
124 | firefox.exe | 34.149.100.209:443 | firefox.settings.services.mozilla.com | GOOGLE | US | unknown |
124 | firefox.exe | 184.24.77.48:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
124 | firefox.exe | 172.217.16.202:443 | fonts.googleapis.com | — | — | whitelisted |
124 | firefox.exe | 142.250.186.67:443 | fonts.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
securebrowser.io |
| unknown |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| shared |
proxyserverecs-1736642167.us-east-1.elb.amazonaws.com |
| shared |
firefox.settings.services.mozilla.com |
| whitelisted |
r3.o.lencr.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
124 | firefox.exe | Not Suspicious Traffic | INFO [ANY.RUN] Global content delivery network (unpkg .com) |
3 ETPRO signatures available at the full report