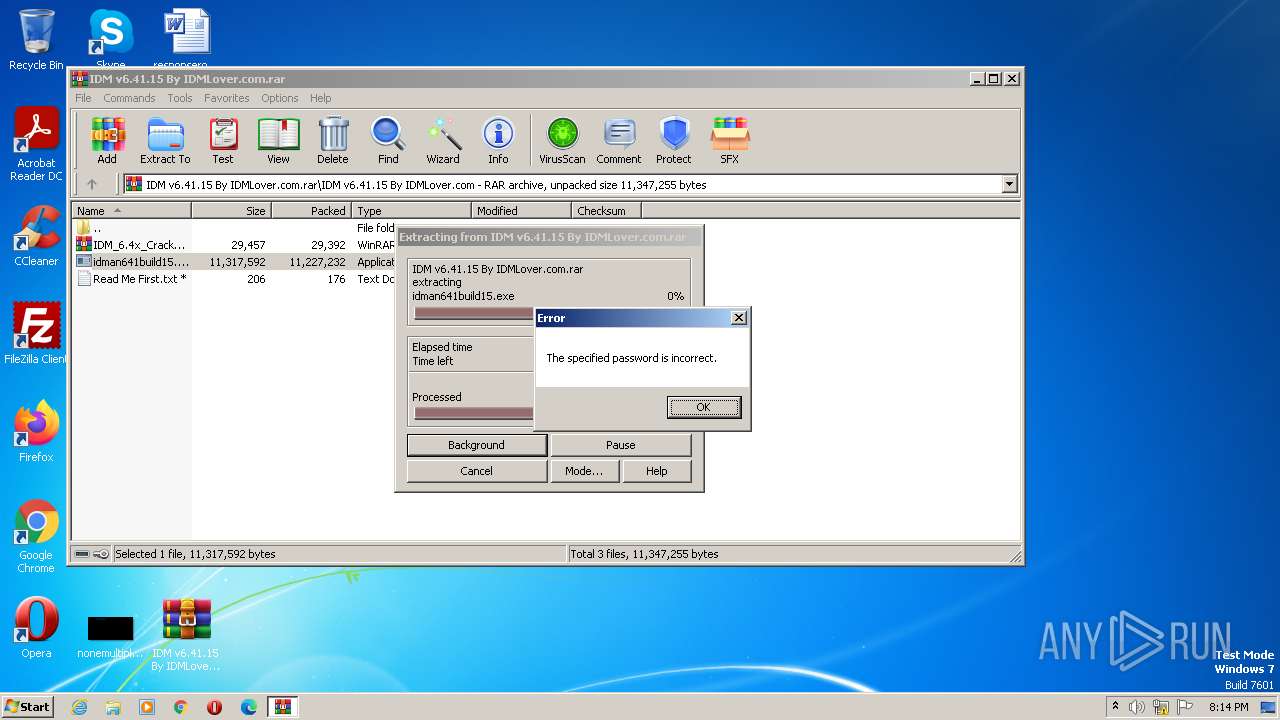
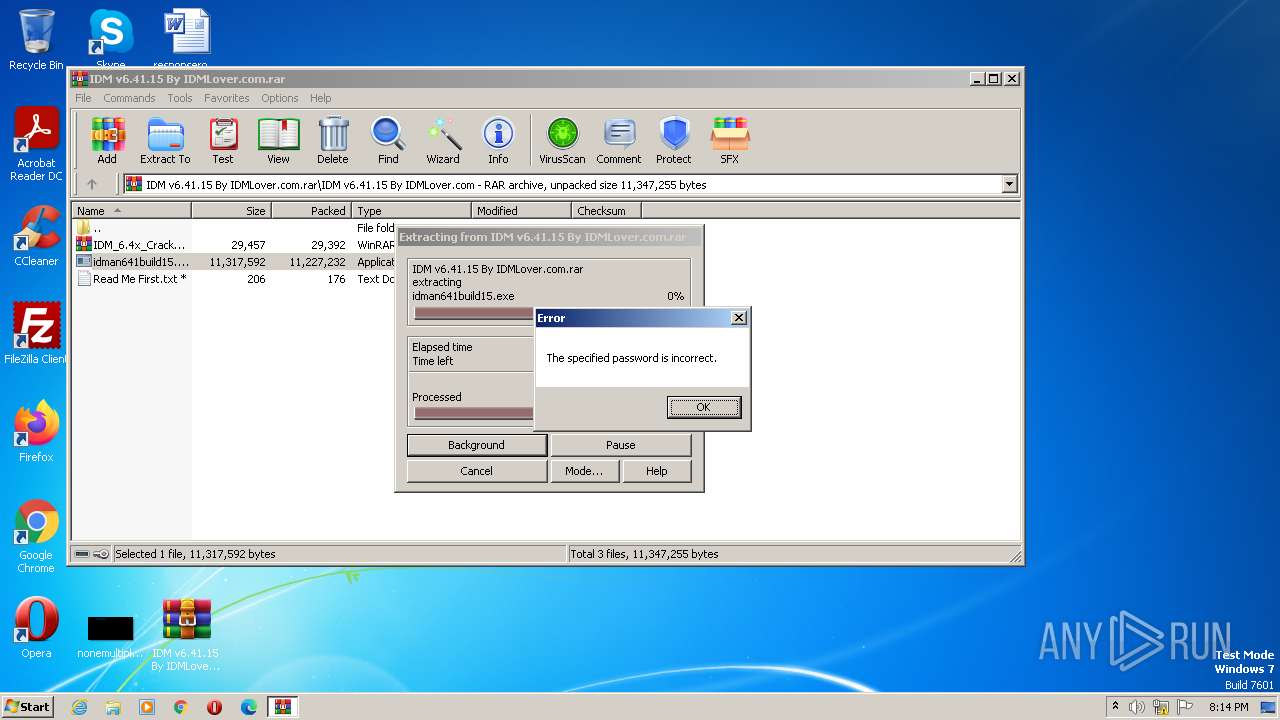
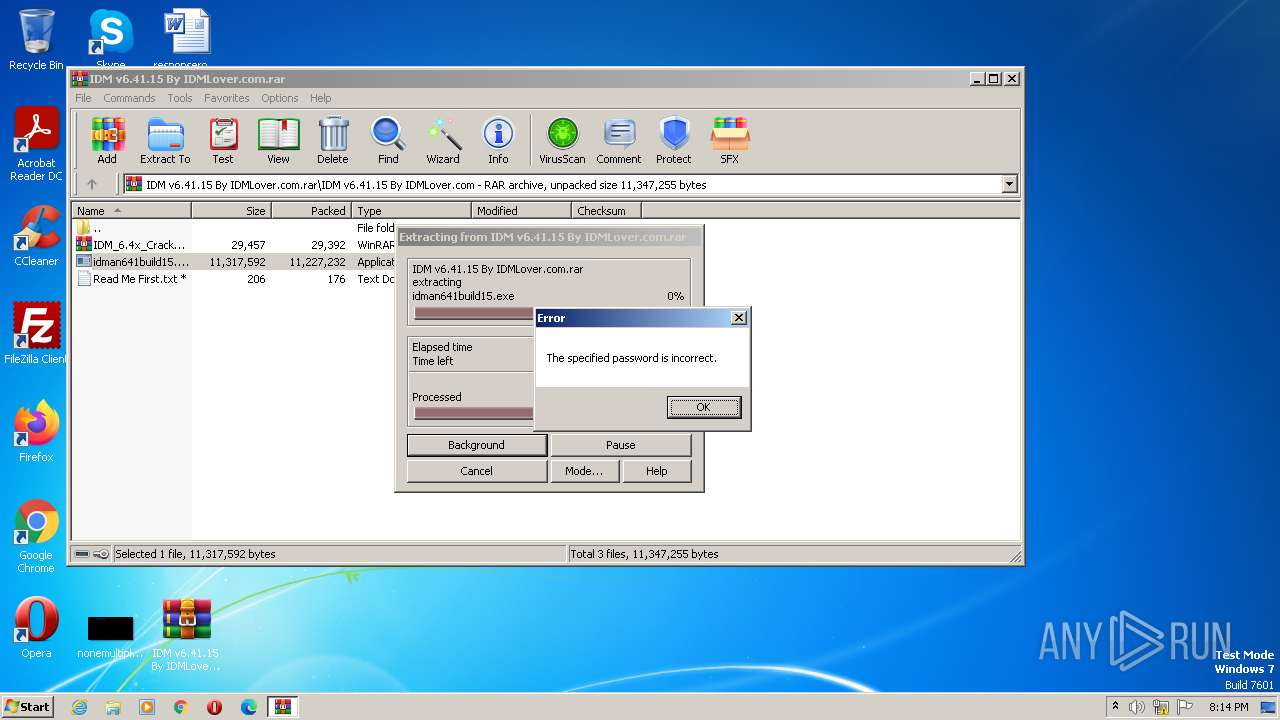
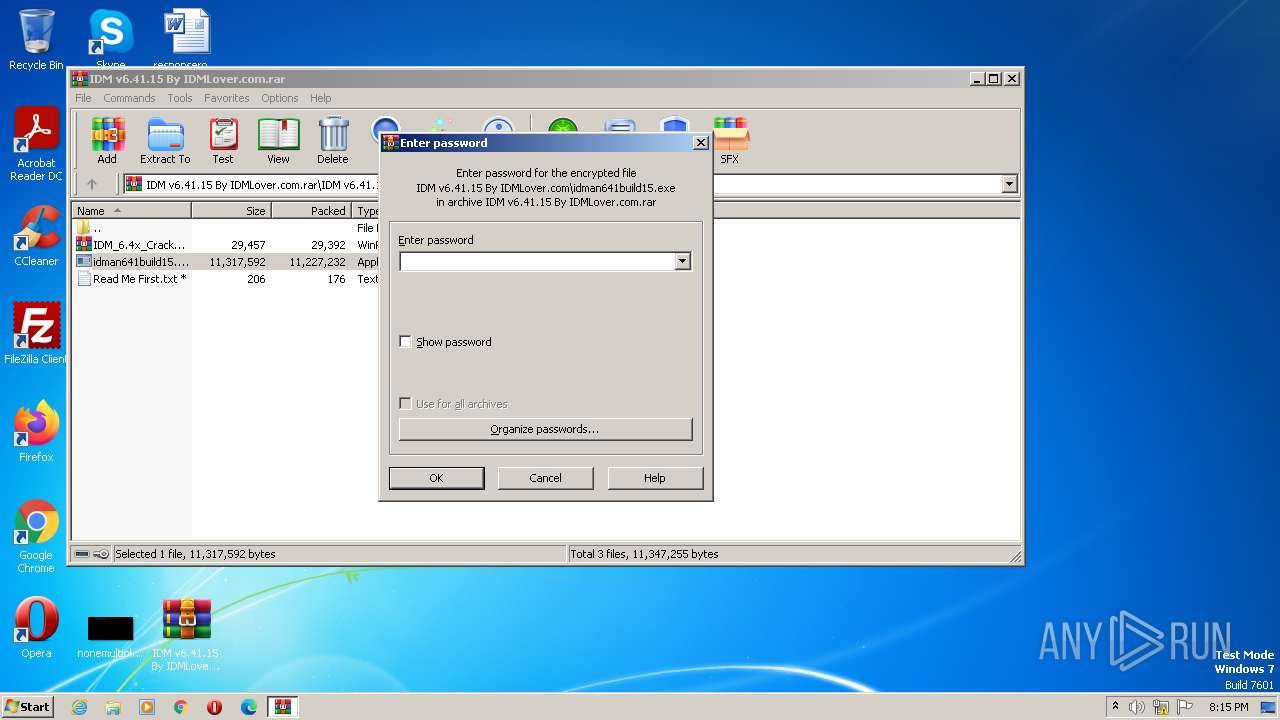
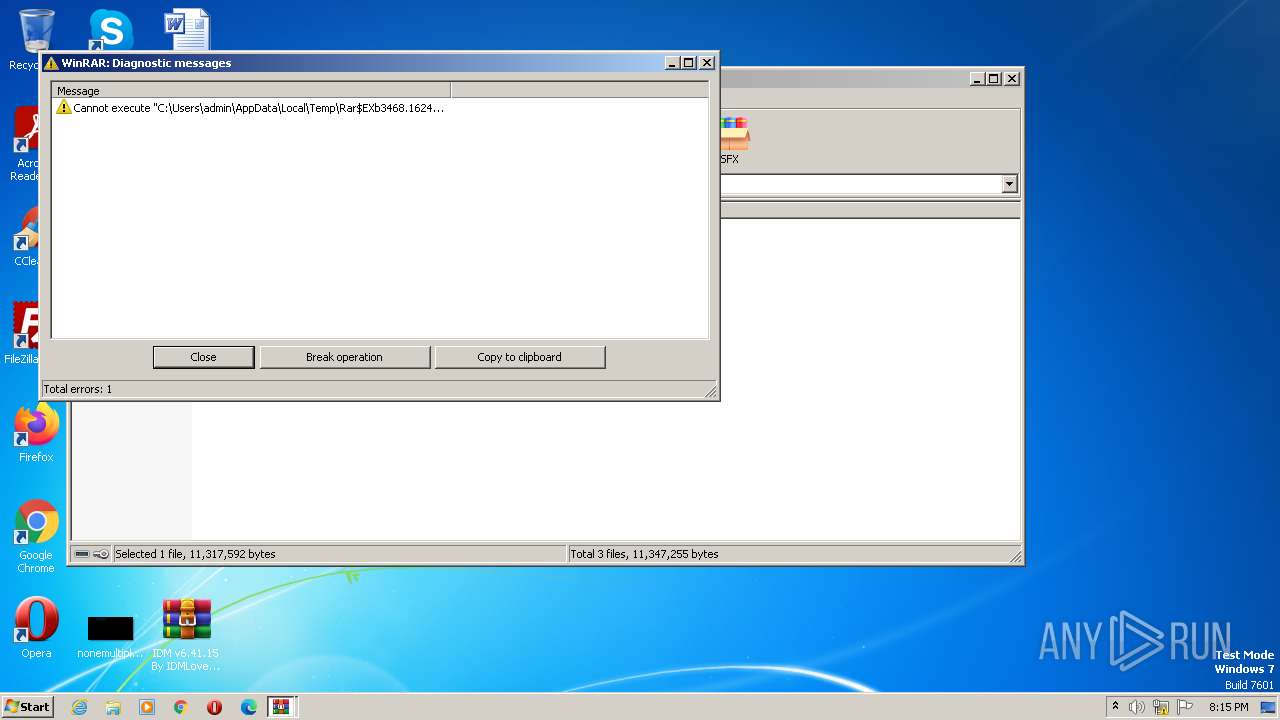
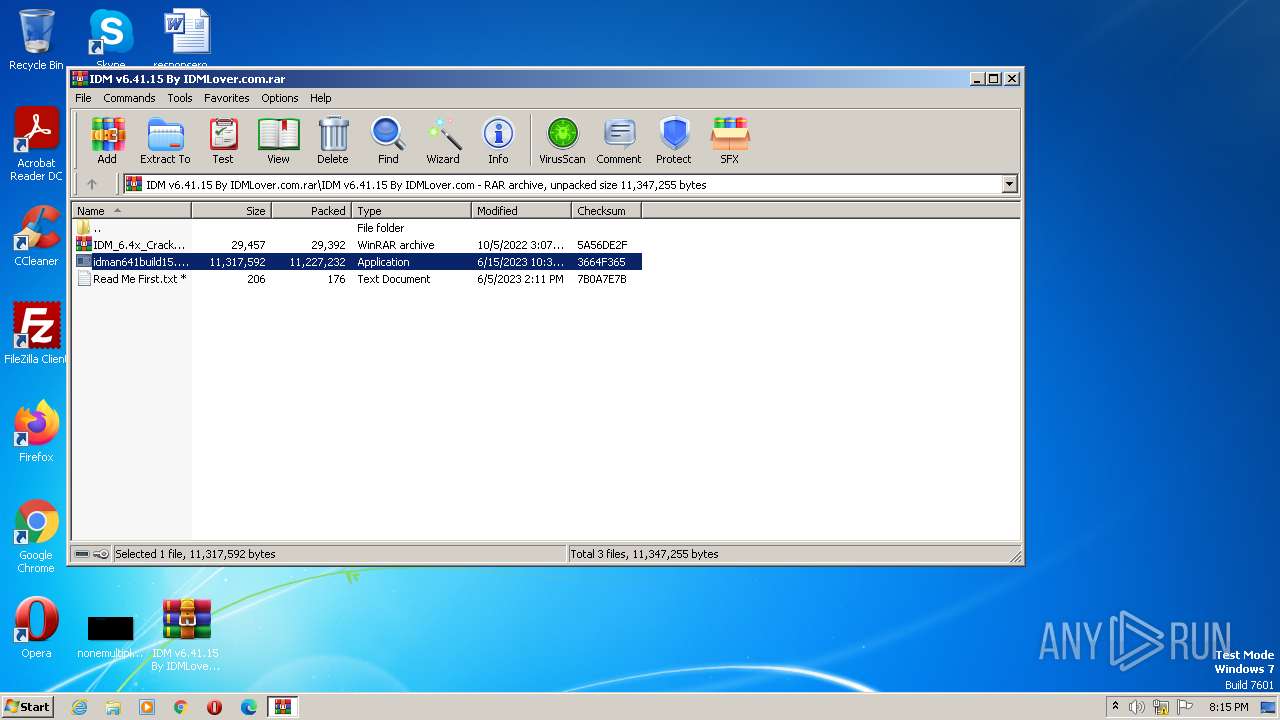
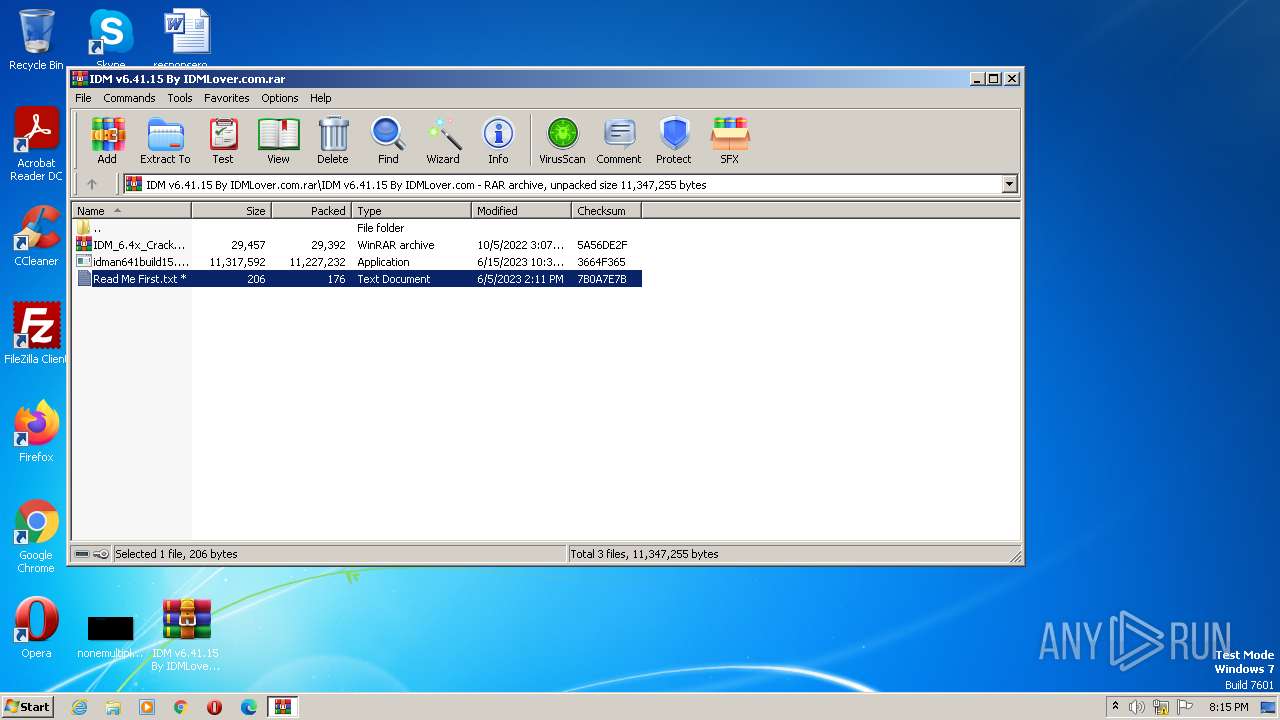
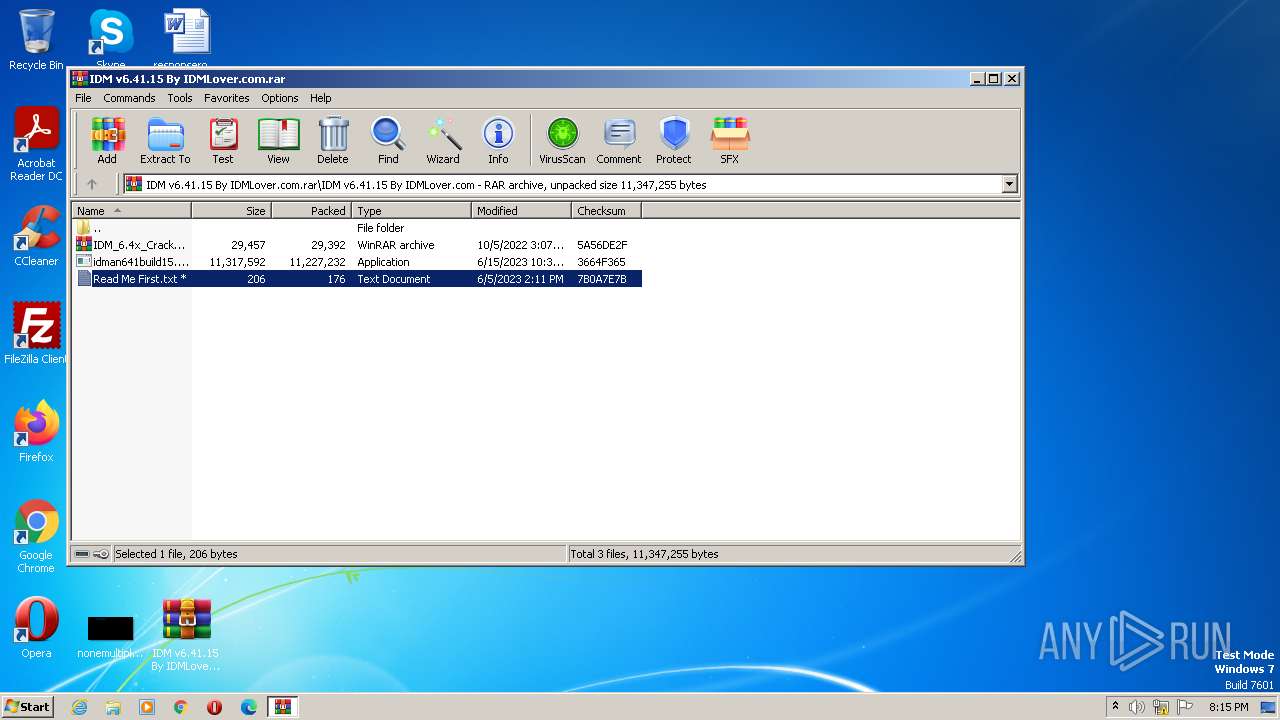
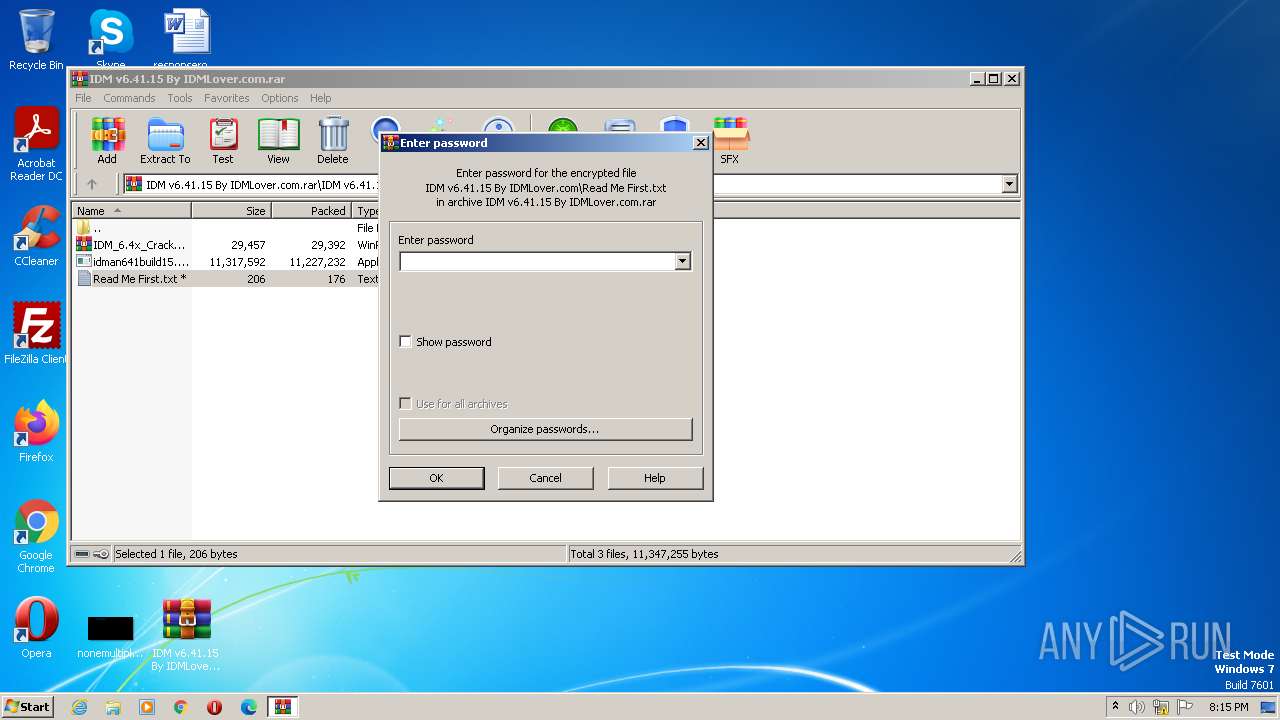
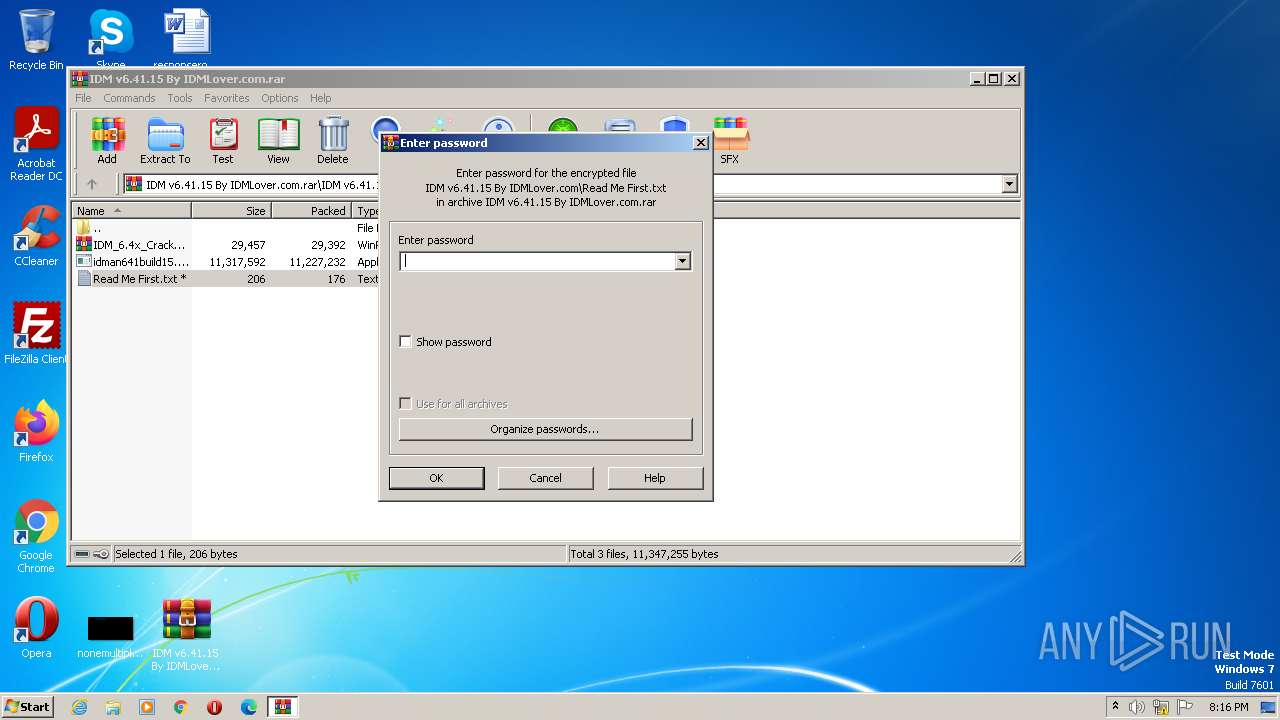
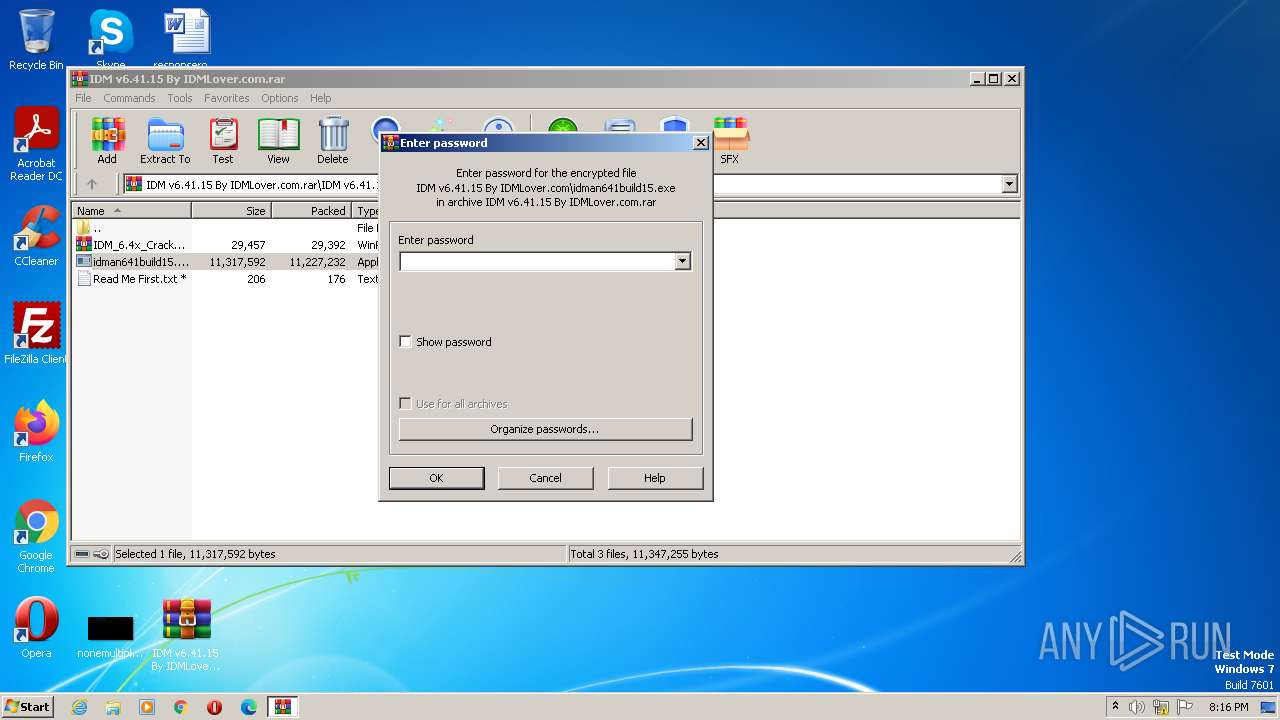
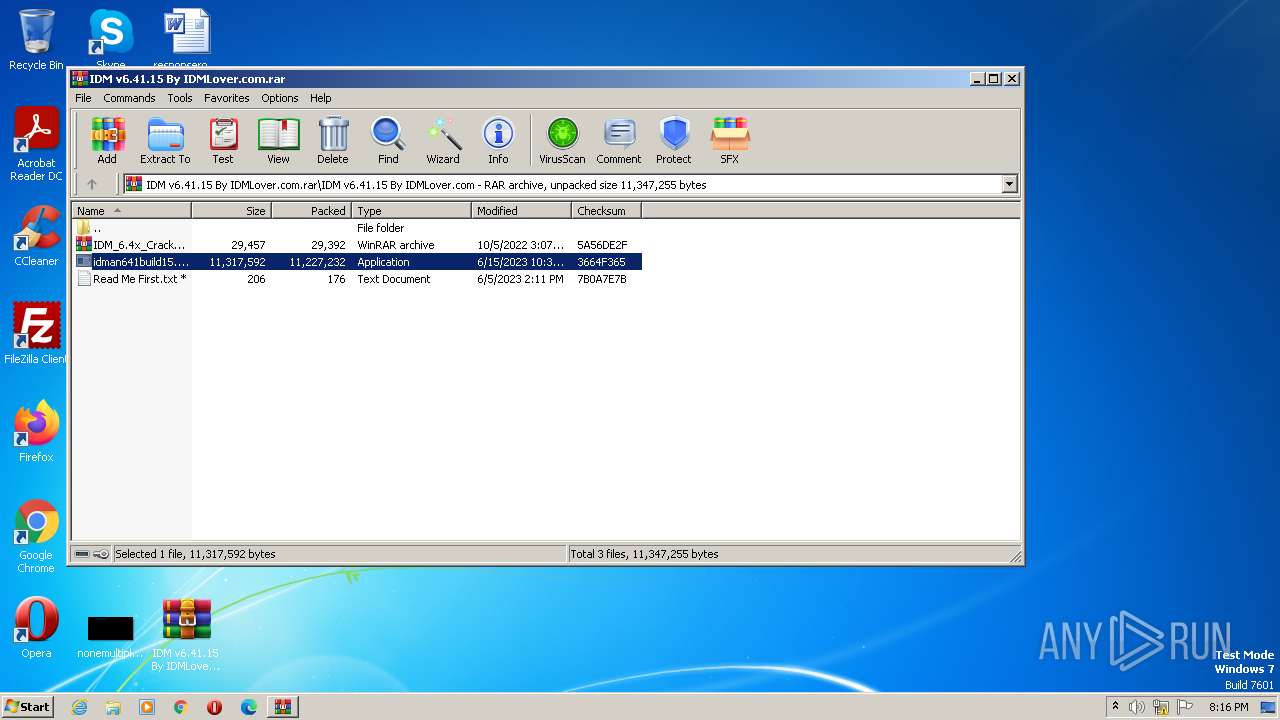
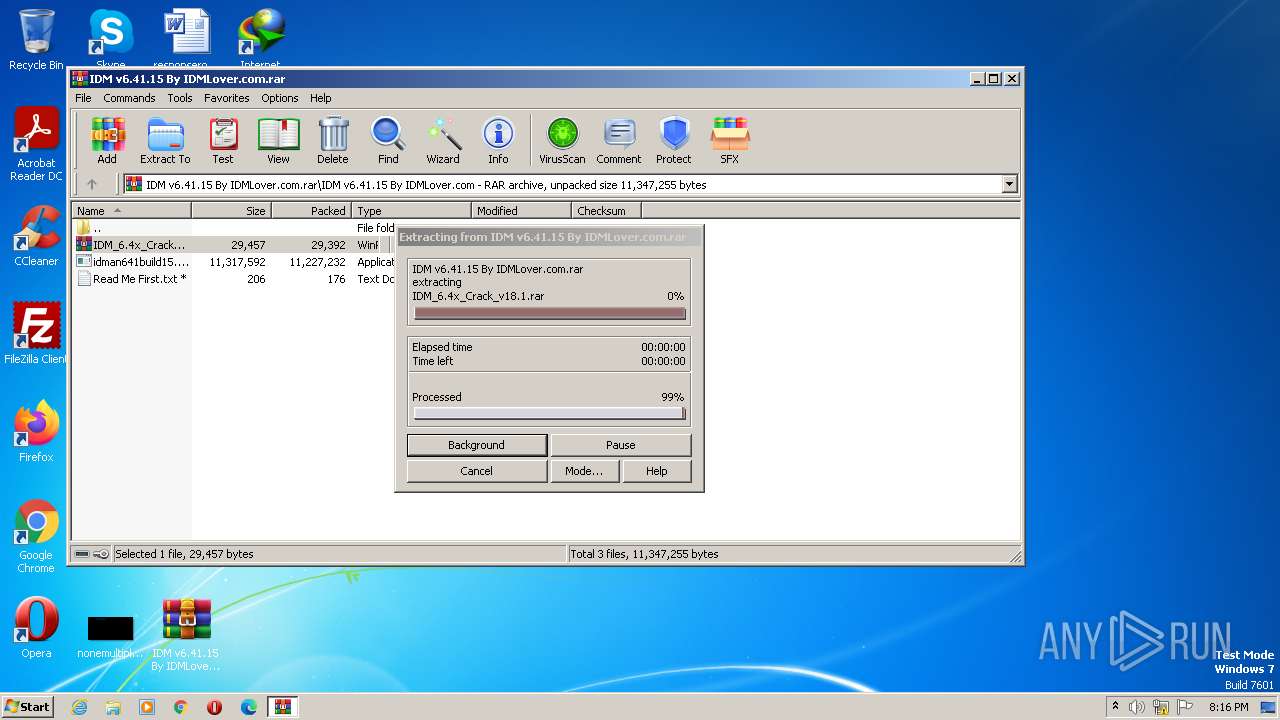
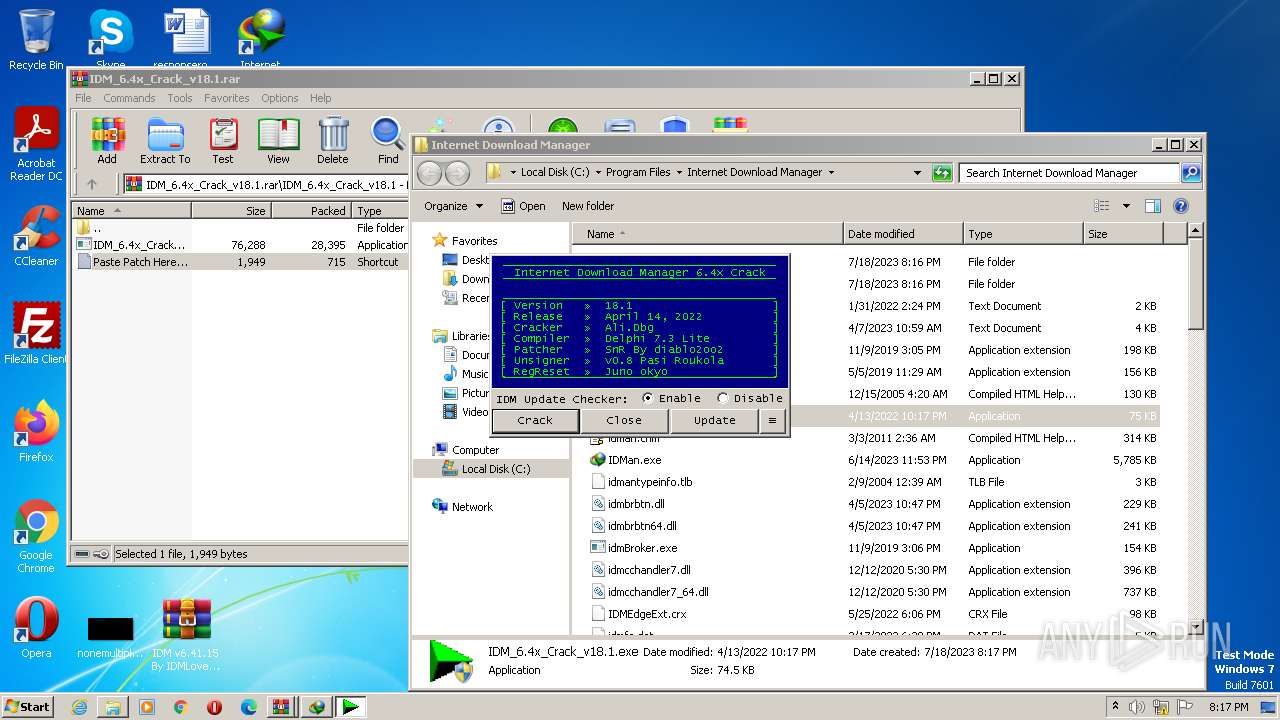
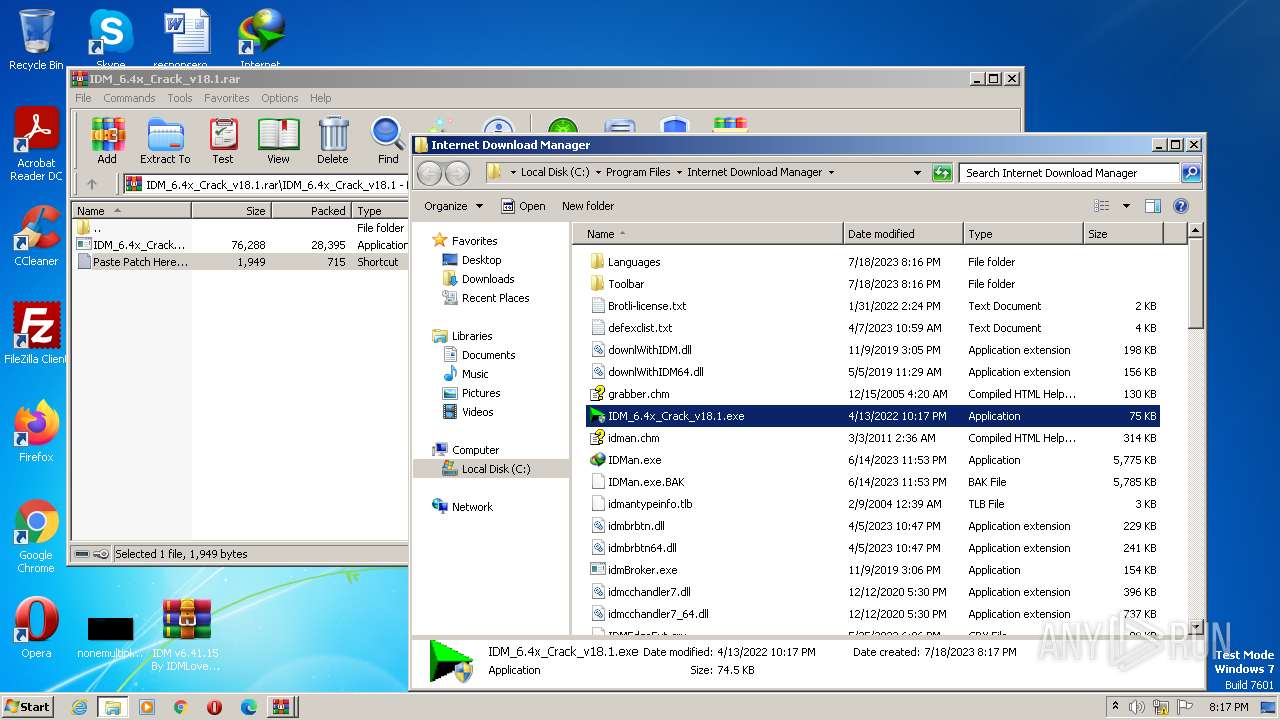
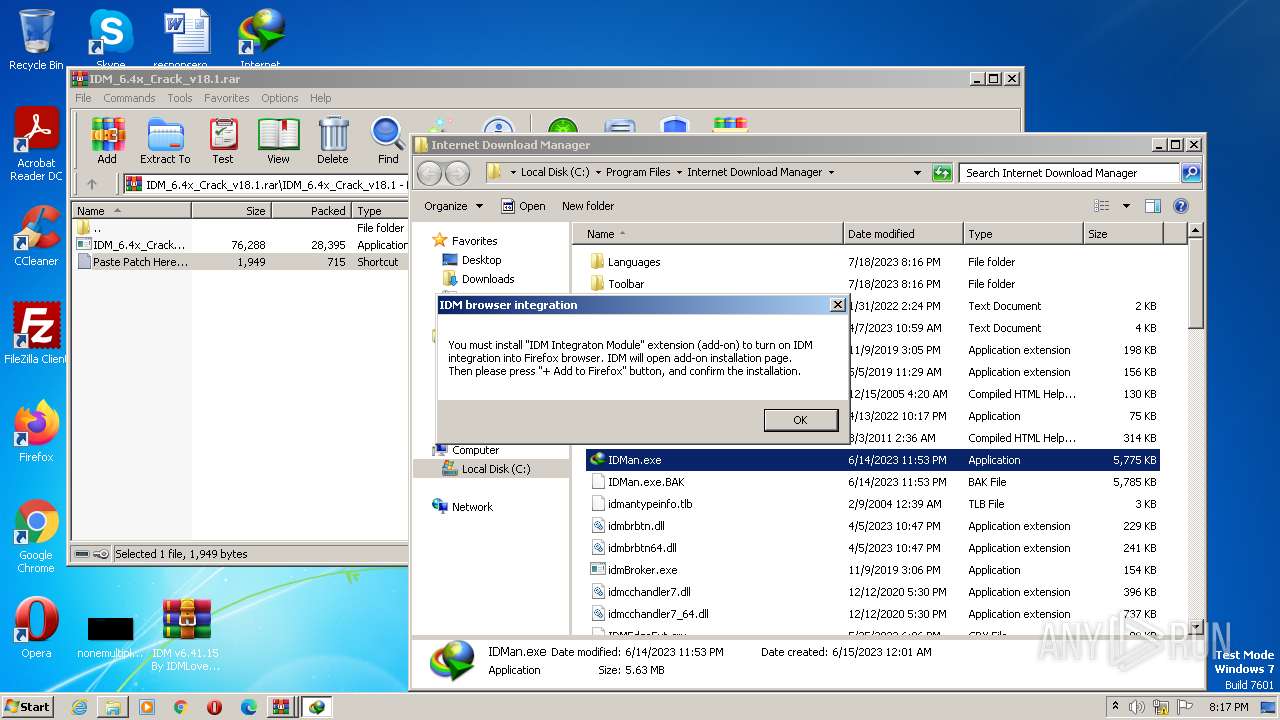
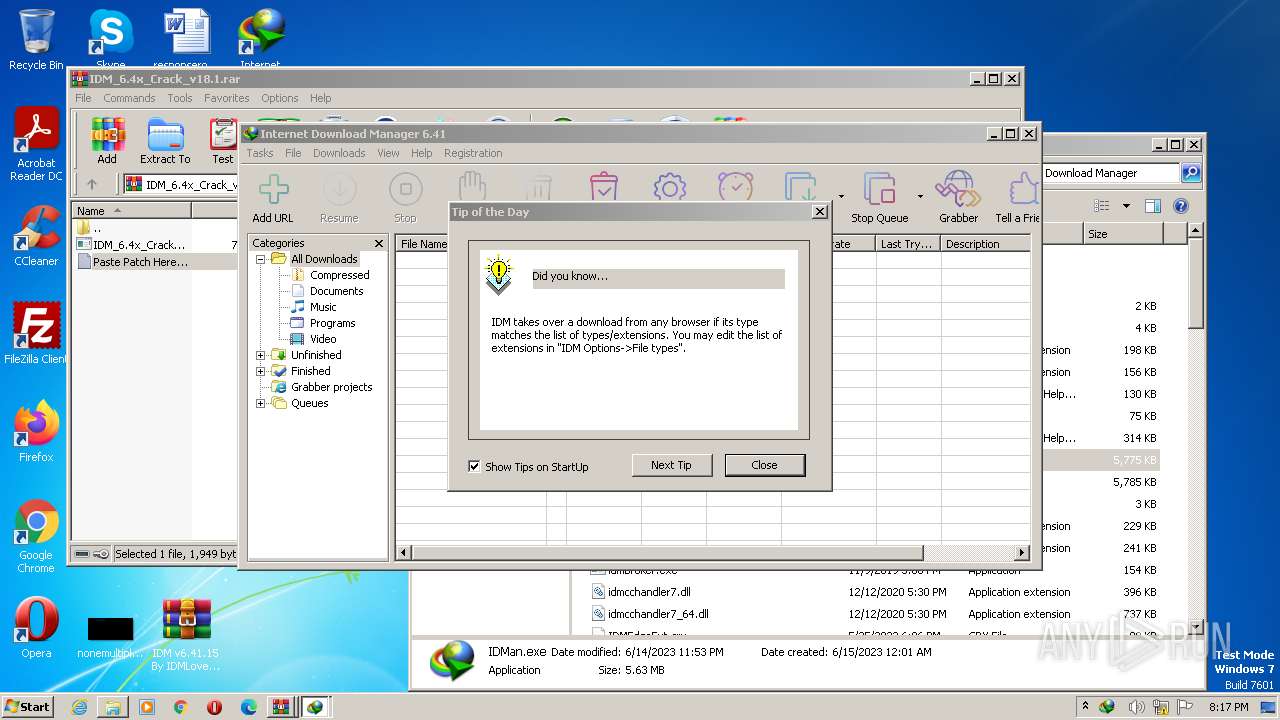
| File name: | IDM v6.41.15 By IDMLover.com.rar |
| Full analysis: | https://app.any.run/tasks/770b931c-416f-4d92-85df-9733b2f7645f |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2023, 19:14:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | EDD22F17F18B9CD1B62B798C74AD2EC3 |
| SHA1: | 8CDB0AF7B0F5C57C8E6BDACC06594D990B879994 |
| SHA256: | 3F20D1E8B0A481D11617060B08A9FD850083DE25C8BBB16D58110474F648B45D |
| SSDEEP: | 196608:koKSBUib1GLp8jVTdjZxu5+khccBJ9or+fV1XDPNveeOPuvhIeu:kscmd1I5+WJ9orUDhhvy |
MALICIOUS
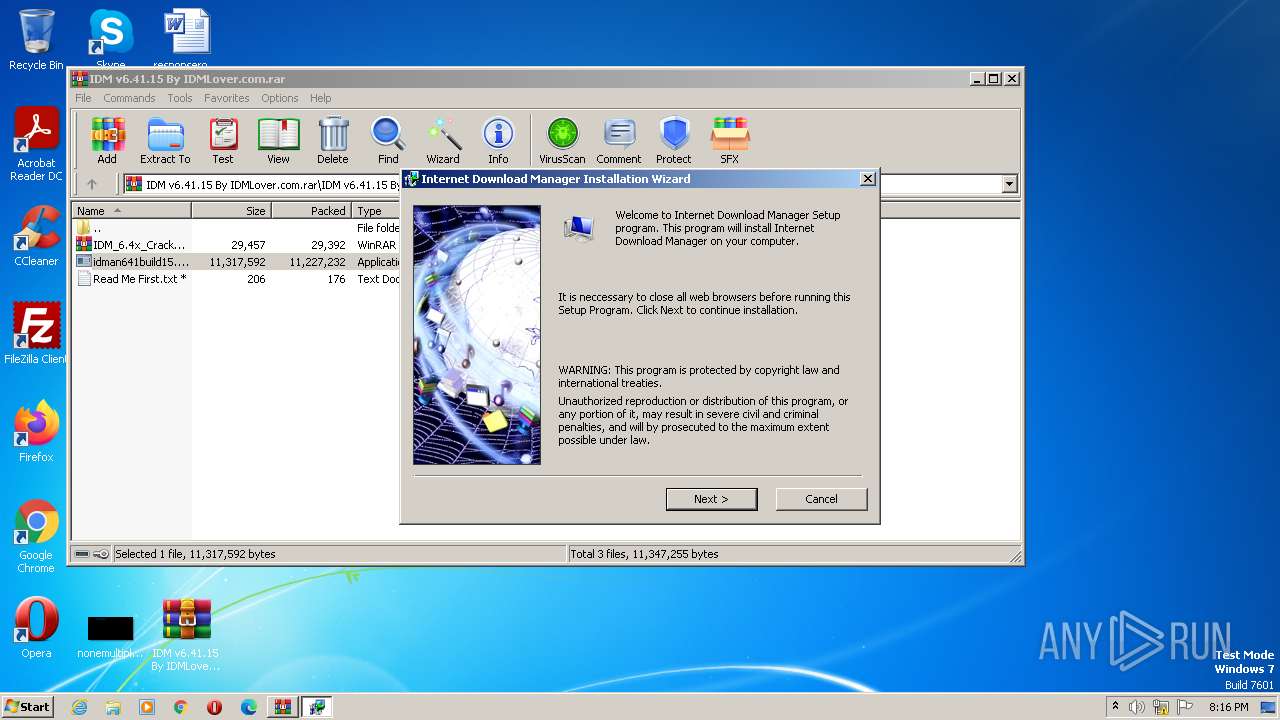
Application was dropped or rewritten from another process
- idman641build15.exe (PID: 1864)
- idman641build15.exe (PID: 1236)
- IDM_6.4x_Crack_v18.1.exe (PID: 2848)
- UnSigner.exe (PID: 2388)
- IDMan.exe (PID: 2128)
- IDM_6.4x_Crack_v18.1.exe (PID: 1804)
Unusual connection from system programs
- wscript.exe (PID: 1032)
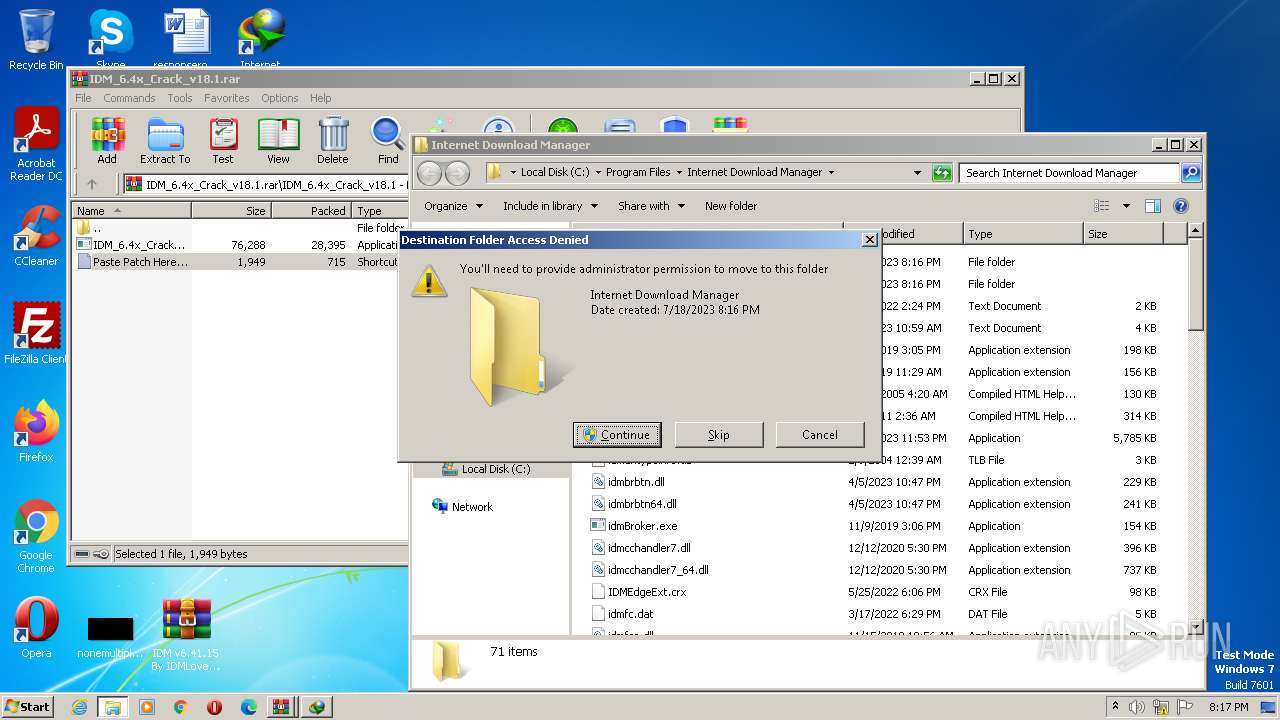
Creates a writable file the system directory
- rundll32.exe (PID: 556)
Starts NET.EXE for service management
- net.exe (PID: 2976)
- Uninstall.exe (PID: 240)
SUSPICIOUS
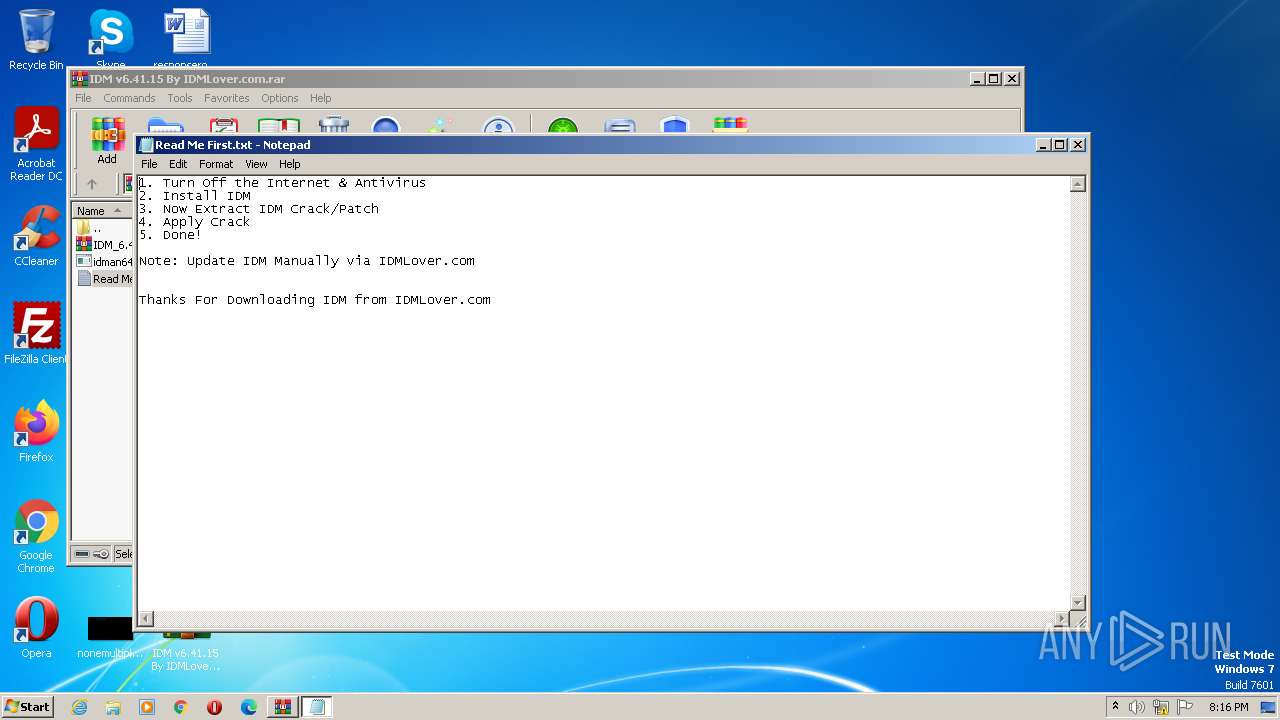
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 3468)
Starts application with an unusual extension
- idman641build15.exe (PID: 1236)
Reads the Internet Settings
- IDM1.tmp (PID: 3436)
- IDMan.exe (PID: 2300)
- hh.exe (PID: 2900)
- wscript.exe (PID: 1032)
- IDM_6.4x_Crack_v18.1.exe (PID: 1804)
- IDMan.exe (PID: 2128)
- Uninstall.exe (PID: 240)
- runonce.exe (PID: 1780)
The process creates files with name similar to system file names
- IDM1.tmp (PID: 3436)
Reads security settings of Internet Explorer
- IDMan.exe (PID: 2300)
- IDMan.exe (PID: 2128)
Checks Windows Trust Settings
- IDMan.exe (PID: 2300)
- IDMan.exe (PID: 2128)
Creates/Modifies COM task schedule object
- IDMan.exe (PID: 2300)
- Uninstall.exe (PID: 240)
Reads settings of System Certificates
- IDMan.exe (PID: 2300)
- IDMan.exe (PID: 2128)
Application launched itself
- WinRAR.exe (PID: 3468)
- cmd.exe (PID: 2320)
Reads Microsoft Outlook installation path
- hh.exe (PID: 2900)
Reads Internet Explorer settings
- hh.exe (PID: 2900)
Searches for installed software
- IDM_6.4x_Crack_v18.1.exe (PID: 1804)
The process executes VB scripts
- IDM_6.4x_Crack_v18.1.exe (PID: 1804)
Executable content was dropped or overwritten
- IDM_6.4x_Crack_v18.1.exe (PID: 1804)
- UnSigner.exe (PID: 2388)
- wscript.exe (PID: 2004)
Adds/modifies Windows certificates
- IDM_6.4x_Crack_v18.1.exe (PID: 1804)
Uses TASKKILL.EXE to kill process
- IDM_6.4x_Crack_v18.1.exe (PID: 1804)
Uses REG/REGEDIT.EXE to modify registry
- IDM_6.4x_Crack_v18.1.exe (PID: 1804)
- cmd.exe (PID: 2320)
Starts CMD.EXE for commands execution
- IDM_6.4x_Crack_v18.1.exe (PID: 1804)
- cmd.exe (PID: 2320)
Executing commands from a ".bat" file
- IDM_6.4x_Crack_v18.1.exe (PID: 1804)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2320)
Identifying current user with WHOAMI command
- cmd.exe (PID: 1996)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 240)
Creates or modifies Windows services
- Uninstall.exe (PID: 240)
INFO
Create files in a temporary directory
- idman641build15.exe (PID: 1236)
- IDM1.tmp (PID: 3436)
- IDMan.exe (PID: 2300)
- hh.exe (PID: 2900)
- IDM_6.4x_Crack_v18.1.exe (PID: 1804)
- IDMan.exe (PID: 2128)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3468)
- WinRAR.exe (PID: 3204)
Checks supported languages
- idman641build15.exe (PID: 1236)
- IDM1.tmp (PID: 3436)
- IDMan.exe (PID: 2300)
- idmBroker.exe (PID: 3732)
- IDM_6.4x_Crack_v18.1.exe (PID: 1804)
- UnSigner.exe (PID: 2388)
- IDMan.exe (PID: 2128)
- Uninstall.exe (PID: 240)
- IEMonitor.exe (PID: 3260)
The process checks LSA protection
- IDM1.tmp (PID: 3436)
- IDMan.exe (PID: 2300)
- dllhost.exe (PID: 2588)
- hh.exe (PID: 2900)
- taskkill.exe (PID: 2344)
- IDM_6.4x_Crack_v18.1.exe (PID: 1804)
- IDMan.exe (PID: 2128)
- Uninstall.exe (PID: 240)
- runonce.exe (PID: 1780)
Reads the computer name
- IDM1.tmp (PID: 3436)
- IDMan.exe (PID: 2300)
- IDM_6.4x_Crack_v18.1.exe (PID: 1804)
- IDMan.exe (PID: 2128)
- Uninstall.exe (PID: 240)
- IEMonitor.exe (PID: 3260)
Reads the machine GUID from the registry
- IDM1.tmp (PID: 3436)
- IDMan.exe (PID: 2300)
- hh.exe (PID: 2900)
- IDMan.exe (PID: 2128)
Creates files in the program directory
- IDM1.tmp (PID: 3436)
- IDMan.exe (PID: 2300)
- wscript.exe (PID: 2004)
Creates files or folders in the user directory
- IDM1.tmp (PID: 3436)
- IDMan.exe (PID: 2300)
- hh.exe (PID: 2900)
- IDMan.exe (PID: 2128)
Manual execution by a user
- hh.exe (PID: 2900)
- IDM_6.4x_Crack_v18.1.exe (PID: 2848)
- IDMan.exe (PID: 2128)
- IDM_6.4x_Crack_v18.1.exe (PID: 1804)
Checks proxy server information
- hh.exe (PID: 2900)
- wscript.exe (PID: 1032)
Application launched itself
- firefox.exe (PID: 2476)
- firefox.exe (PID: 3368)
Creates files in the driver directory
- rundll32.exe (PID: 556)
Reads the time zone
- runonce.exe (PID: 1780)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
331
Monitored processes
272
Malicious processes
11
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | REG DELETE "HKCU\Software\Classes\Wow6432Node\CLSID\{07999AC3-058B-40BF-984F-69EB1E554CA7}" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 188 | REG DELETE "HKCU\Software\Classes\CLSID\{79873CC5-3951-43ED-BDF9-D8759474B6FD}" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 240 | "C:\Program Files\Internet Download Manager\Uninstall.exe" -instdriv | C:\Program Files\Internet Download Manager\Uninstall.exe | IDMan.exe | ||||||||||||
User: admin Company: Tonec Inc. Integrity Level: HIGH Description: Internet Download Manager installer Exit code: 1 Version: 6, 41, 9, 1 Modules
| |||||||||||||||
| 268 | reg query "HKU\.DEFAULT\Software\Classes\Wow6432Node\CLSID\{9C9D53D4-A978-43FC-93E2-1C21B529E6D7}" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 272 | reg query "HKCU\Software\Classes\Wow6432Node\CLSID\{07999AC3-058B-40BF-984F-69EB1E554CA7}" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 280 | reg query "HKCU\Software\Classes\CLSID\{9C9D53D4-A978-43FC-93E2-1C21B529E6D7}" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 280 | REG DELETE "HKU\.DEFAULT\Software\Classes\Wow6432Node\CLSID\{7B8E9164-324D-4A2E-A46D-0165FB2000EC}" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 292 | reg query "HKLM\Software\Classes\CLSID\{79873CC5-3951-43ED-BDF9-D8759474B6FD}" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 556 | "C:\Windows\System32\rundll32.exe" SETUPAPI.DLL,InstallHinfSection DefaultInstall 128 C:\Program Files\Internet Download Manager\idmwfp.inf | C:\Windows\System32\rundll32.exe | — | Uninstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 644 | REG DELETE "HKCU" /v "Therad" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
23 446
Read events
23 177
Write events
194
Delete events
75
Modification events
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
5
Suspicious files
33
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3436 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Internet Download Manager.lnk | binary | |
MD5:16A6555338E46AF00D371E5E43A3213C | SHA256:33B631C6D8BD12E7D7DB7CEAF29417DAD04DBD3F9FED01DB1ED2318C8359F6E1 | |||
| 3436 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\TUTORIALS.lnk | binary | |
MD5:EFBC9604C52CEB0148688B299C9F6E43 | SHA256:CEE8B5BD5402E2A24FA3EC6EF9D52D01F6D8C5F001041A8CE346FD016DFA2360 | |||
| 3436 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Uninstall IDM.lnk | binary | |
MD5:01C5F501EB039F03460FB764521A65A4 | SHA256:CDDA69B518938FADD1FAEDB5FEC21D6E8136DC0C2CFDCAB8950A237677A7FCB2 | |||
| 3436 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\IDM Help.lnk | binary | |
MD5:3AA1533E3064B84A5BD4E68B700A66A9 | SHA256:A3802052631CA9281F7726CEA9EAEE6BE2D8A507B946AAF71B2AE8636CD41770 | |||
| 3436 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\IDM Help.lnk | binary | |
MD5:1323A676C2473369456907A73BDE55E3 | SHA256:FE2B7805B4C5687F958D721BADC29047B2556A593C37EC98FD8C6B547B94CF06 | |||
| 3436 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\license.lnk | binary | |
MD5:7FB3801ED3F934092333B0330C4315DC | SHA256:01742415FEB3517040B59D428EB261573C52F611612E2056F9EF35AB7DBDCCC4 | |||
| 3436 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\TUTORIALS.lnk | binary | |
MD5:FFBEB1624F116355360F5F09DA991913 | SHA256:7E3855AE4E8E79FABB72B6A2233922ABB04F840E0A793A08F24D496624933CEC | |||
| 3436 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\license.lnk | binary | |
MD5:4A6D1195F35D2B2FB8F1527382C301D0 | SHA256:97067BE42FDCC196844AF54C0880E6DE115D377A877DE88E552B671F3C3E2E54 | |||
| 3436 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Internet Download Manager.lnk | binary | |
MD5:84FD6C166F4035D70CF363EDA8EB593B | SHA256:89766AB82852DCCAEAD274102422CE755711899ED1540EBA6868C5356BA06BFB | |||
| 3436 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Grabber Help.lnk | binary | |
MD5:E156D85204FFA5D0A3BAFB64FC2E3D3C | SHA256:54D6A6A86D0900F774C6F40CACCD0B12DC6F37086EA8C130FF287483072897C8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
35
DNS requests
91
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2128 | IDMan.exe | GET | 304 | 87.248.202.1:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?b0c9fd048082a3f6 | IT | — | — | whitelisted |
1032 | wscript.exe | GET | 200 | 142.251.36.35:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | binary | 1.41 Kb | whitelisted |
2300 | IDMan.exe | GET | 200 | 87.248.202.1:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e7d4fa4708cc5d39 | IT | compressed | 62.3 Kb | whitelisted |
1032 | wscript.exe | GET | 200 | 87.248.202.1:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c6523dad30338f86 | IT | compressed | 4.70 Kb | whitelisted |
3368 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | US | binary | 471 b | whitelisted |
3368 | firefox.exe | POST | 200 | 95.101.74.202:80 | http://r3.o.lencr.org/ | NL | binary | 503 b | shared |
3368 | firefox.exe | POST | 200 | 18.239.100.55:80 | http://ocsp.r2m02.amazontrust.com/ | US | binary | 471 b | whitelisted |
3368 | firefox.exe | POST | 200 | 95.101.74.202:80 | http://r3.o.lencr.org/ | NL | binary | 503 b | shared |
— | — | POST | — | 142.251.36.35:80 | http://ocsp.pki.goog/gts1c3 | US | — | — | whitelisted |
3368 | firefox.exe | POST | 200 | 95.101.74.202:80 | http://r3.o.lencr.org/ | NL | binary | 503 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2640 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1068 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1032 | wscript.exe | 142.251.36.35:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3368 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
3368 | firefox.exe | 34.117.237.239:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | suspicious |
3368 | firefox.exe | 3.229.85.40:443 | spocs.getpocket.com | AMAZON-AES | US | unknown |
3368 | firefox.exe | 169.61.27.133:443 | secure.internetdownloadmanager.com | SOFTLAYER | US | suspicious |
3368 | firefox.exe | 35.201.103.21:443 | normandy.cdn.mozilla.net | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
idm.ckk.ir |
| unknown |
ocsp.pki.goog |
| whitelisted |
test.internetdownloadmanager.com |
| whitelisted |
secure.internetdownloadmanager.com |
| whitelisted |
www.internetdownloadmanager.com |
| whitelisted |
mirror3.internetdownloadmanager.com |
| whitelisted |
mirror5.internetdownloadmanager.com |
| whitelisted |
registeridm.com |
| suspicious |
detectportal.firefox.com |
| whitelisted |