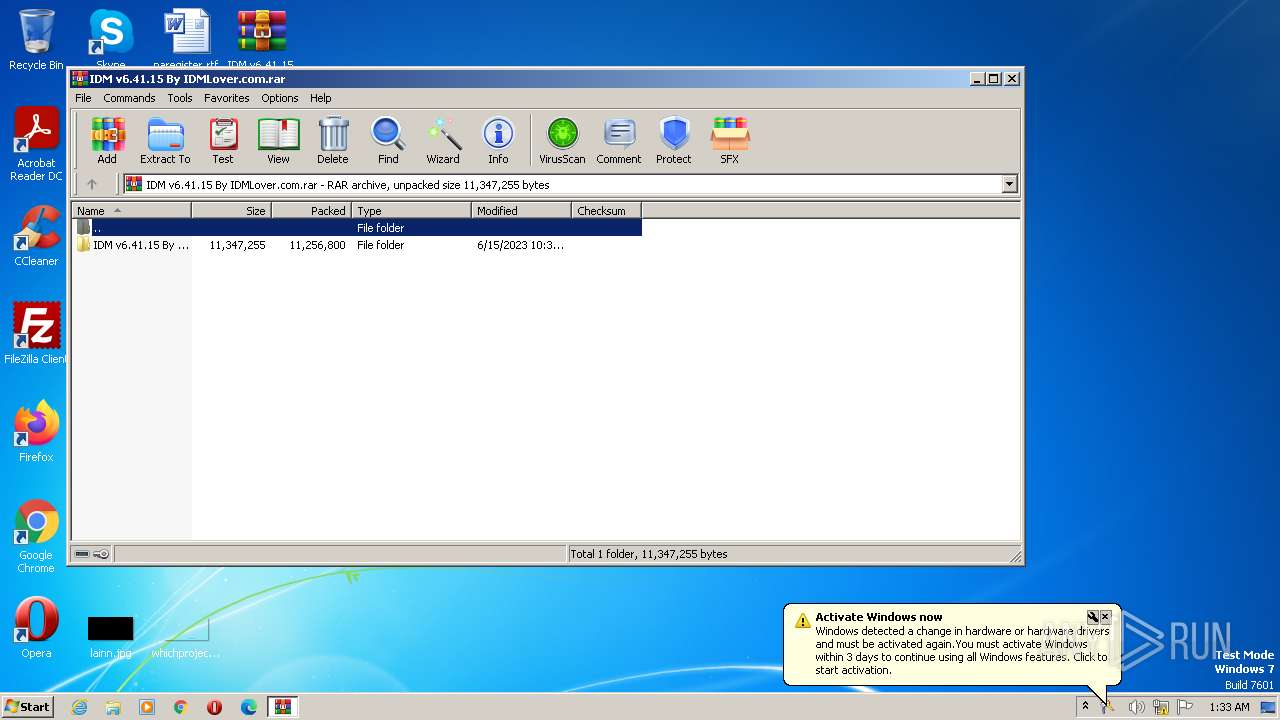
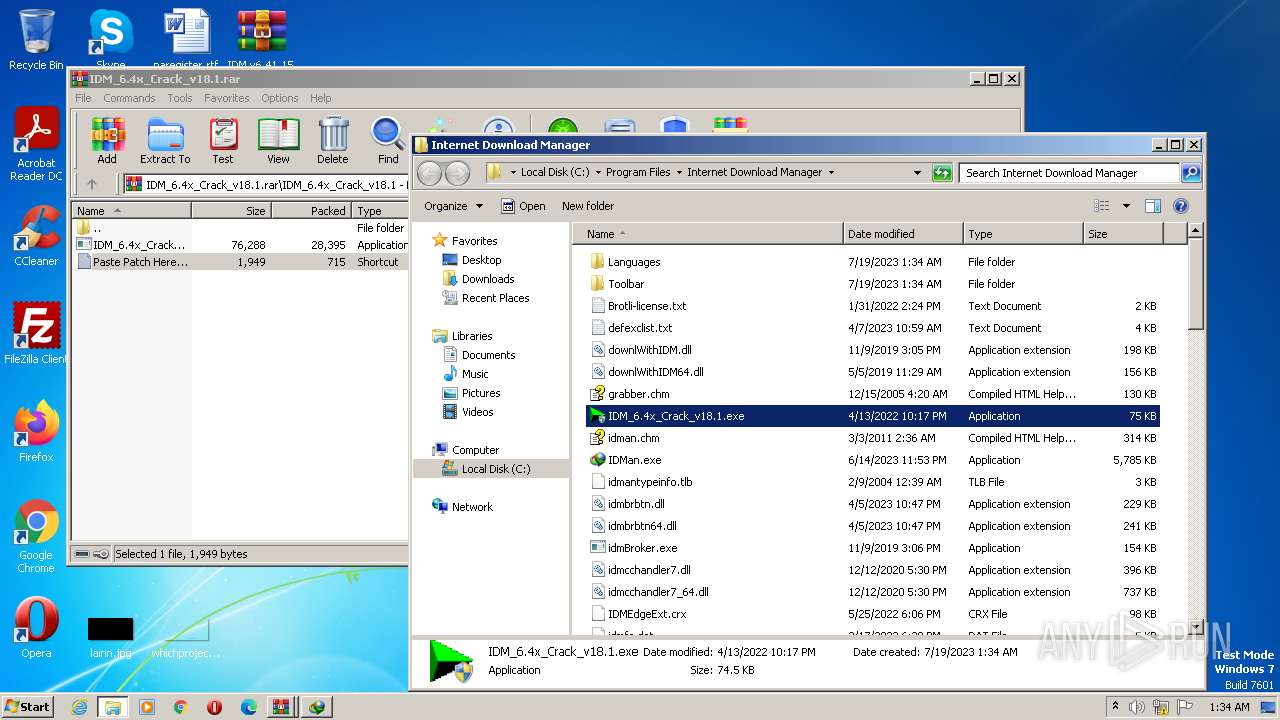
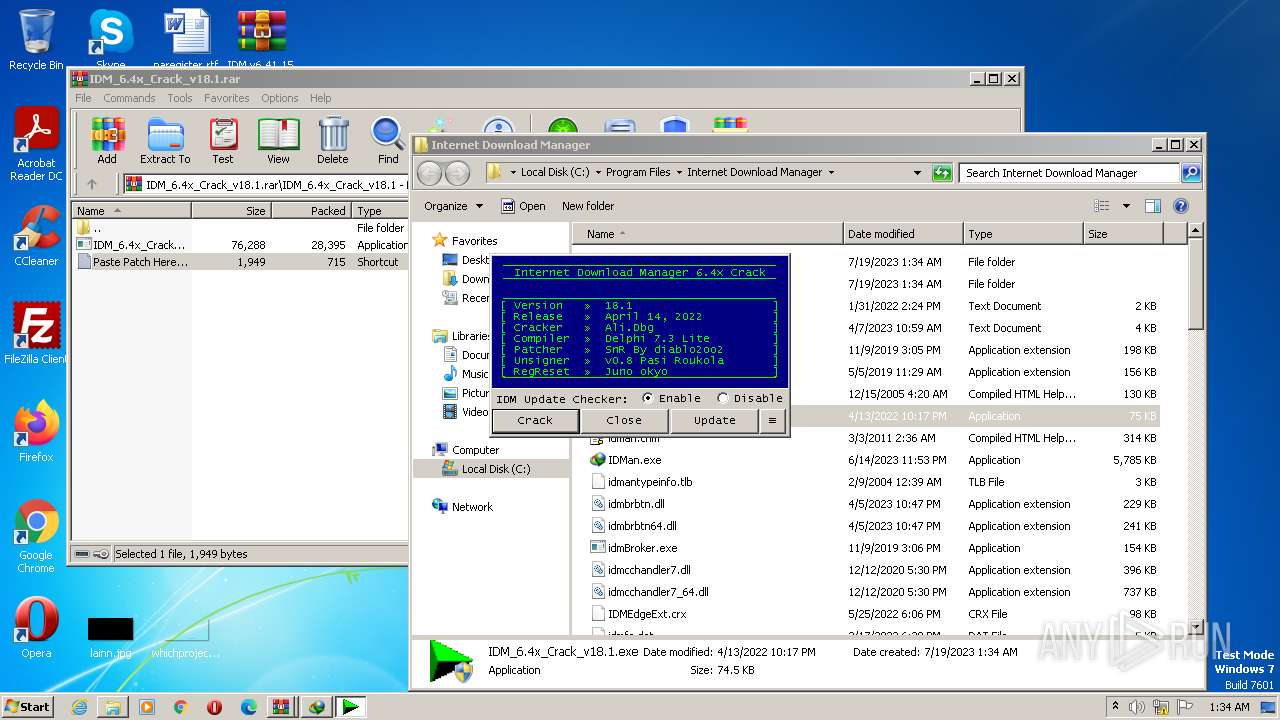
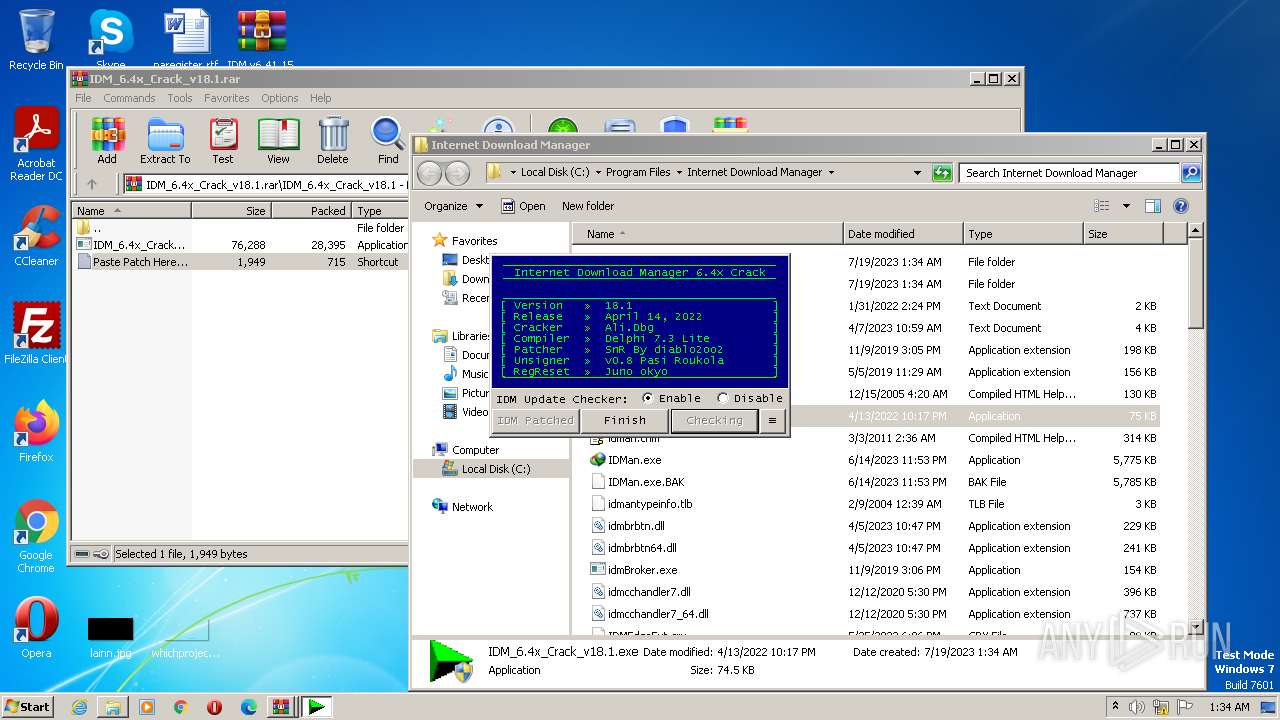
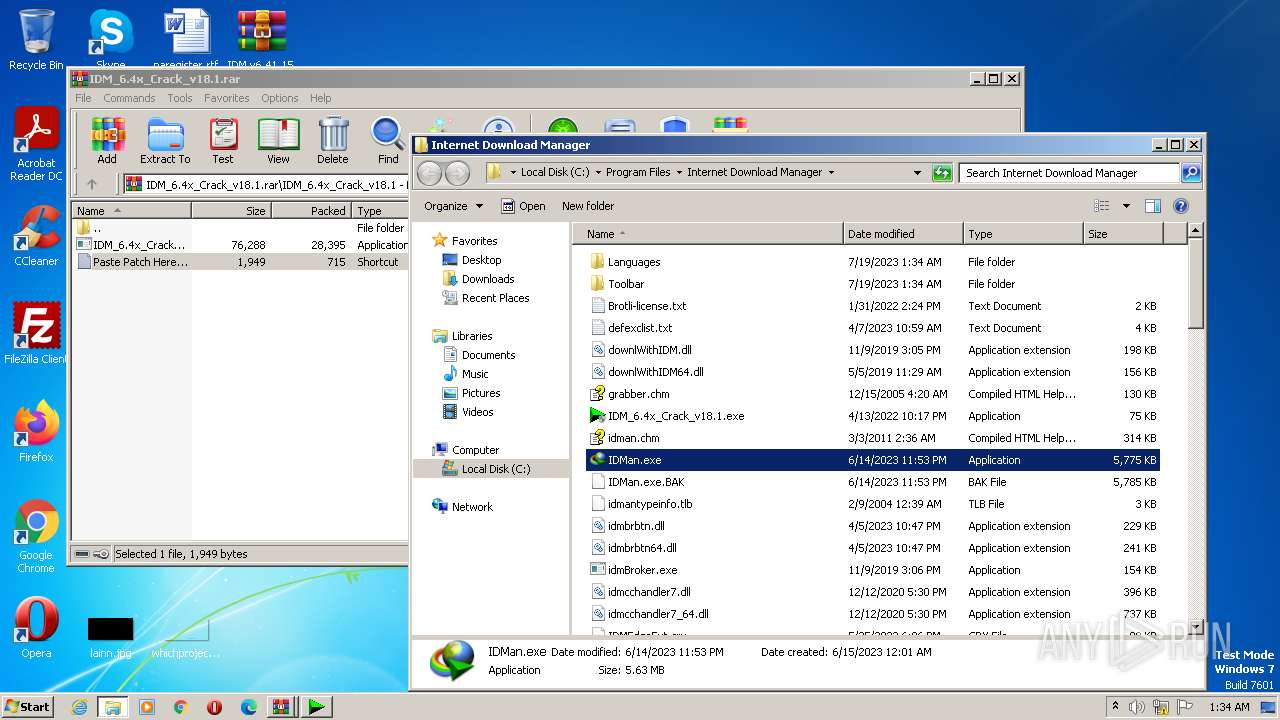
| File name: | IDM v6.41.15 By IDMLover.com.rar |
| Full analysis: | https://app.any.run/tasks/06968c17-1546-406e-bcfe-e40dbf0cfdde |
| Verdict: | Malicious activity |
| Analysis date: | July 19, 2023, 00:33:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | EDD22F17F18B9CD1B62B798C74AD2EC3 |
| SHA1: | 8CDB0AF7B0F5C57C8E6BDACC06594D990B879994 |
| SHA256: | 3F20D1E8B0A481D11617060B08A9FD850083DE25C8BBB16D58110474F648B45D |
| SSDEEP: | 196608:koKSBUib1GLp8jVTdjZxu5+khccBJ9or+fV1XDPNveeOPuvhIeu:kscmd1I5+WJ9orUDhhvy |
MALICIOUS
Application was dropped or rewritten from another process
- idman641build15.exe (PID: 2180)
- idman641build15.exe (PID: 1632)
- IDM_6.4x_Crack_v18.1.exe (PID: 3932)
- IDM_6.4x_Crack_v18.1.exe (PID: 3020)
- UnSigner.exe (PID: 3924)
- IDMan.exe (PID: 3704)
- IDMan.exe (PID: 2828)
Unusual connection from system programs
- wscript.exe (PID: 4036)
Creates a writable file the system directory
- rundll32.exe (PID: 3528)
Starts NET.EXE for service management
- net.exe (PID: 3448)
- Uninstall.exe (PID: 1348)
Actions looks like stealing of personal data
- IDMan.exe (PID: 2828)
SUSPICIOUS
Starts application with an unusual extension
- idman641build15.exe (PID: 1632)
The process creates files with name similar to system file names
- IDM1.tmp (PID: 2468)
Reads the Internet Settings
- IDM1.tmp (PID: 2468)
- IDMan.exe (PID: 1184)
- IDM_6.4x_Crack_v18.1.exe (PID: 3020)
- wscript.exe (PID: 4036)
- IDMan.exe (PID: 3704)
- IDMan.exe (PID: 2828)
- Uninstall.exe (PID: 1348)
- runonce.exe (PID: 3876)
Reads security settings of Internet Explorer
- IDMan.exe (PID: 1184)
- IDMan.exe (PID: 3704)
- IDMan.exe (PID: 2828)
Checks Windows Trust Settings
- IDMan.exe (PID: 1184)
- IDMan.exe (PID: 3704)
- IDMan.exe (PID: 2828)
Reads settings of System Certificates
- IDMan.exe (PID: 1184)
- IDMan.exe (PID: 3704)
- IDMan.exe (PID: 2828)
Creates/Modifies COM task schedule object
- IDMan.exe (PID: 1184)
- Uninstall.exe (PID: 1348)
Application launched itself
- WinRAR.exe (PID: 3624)
- cmd.exe (PID: 3128)
Executable content was dropped or overwritten
- dllhost.exe (PID: 1760)
- IDM_6.4x_Crack_v18.1.exe (PID: 3020)
- wscript.exe (PID: 3416)
- UnSigner.exe (PID: 3924)
- IDMan.exe (PID: 2828)
- rundll32.exe (PID: 3528)
Searches for installed software
- IDM_6.4x_Crack_v18.1.exe (PID: 3020)
The process executes VB scripts
- IDM_6.4x_Crack_v18.1.exe (PID: 3020)
Uses TASKKILL.EXE to kill process
- IDM_6.4x_Crack_v18.1.exe (PID: 3020)
Uses REG/REGEDIT.EXE to modify registry
- IDM_6.4x_Crack_v18.1.exe (PID: 3020)
- cmd.exe (PID: 3128)
Starts CMD.EXE for commands execution
- IDM_6.4x_Crack_v18.1.exe (PID: 3020)
- cmd.exe (PID: 3128)
Executing commands from a ".bat" file
- IDM_6.4x_Crack_v18.1.exe (PID: 3020)
Identifying current user with WHOAMI command
- cmd.exe (PID: 2804)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3128)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 1348)
Drops a system driver (possible attempt to evade defenses)
- rundll32.exe (PID: 3528)
Creates or modifies Windows services
- Uninstall.exe (PID: 1348)
Adds/modifies Windows certificates
- IDM_6.4x_Crack_v18.1.exe (PID: 3020)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3624)
- WinRAR.exe (PID: 2528)
Checks supported languages
- idman641build15.exe (PID: 1632)
- IDM1.tmp (PID: 2468)
- IDMan.exe (PID: 1184)
- idmBroker.exe (PID: 3484)
- IDM_6.4x_Crack_v18.1.exe (PID: 3020)
- UnSigner.exe (PID: 3924)
- IDMan.exe (PID: 3704)
- IDMan.exe (PID: 2828)
- Uninstall.exe (PID: 1348)
- IEMonitor.exe (PID: 1664)
Reads the machine GUID from the registry
- IDM1.tmp (PID: 2468)
- IDMan.exe (PID: 1184)
- IDMan.exe (PID: 3704)
- IDMan.exe (PID: 2828)
Creates files in the program directory
- IDM1.tmp (PID: 2468)
- IDMan.exe (PID: 1184)
- wscript.exe (PID: 3416)
Create files in a temporary directory
- IDM1.tmp (PID: 2468)
- idman641build15.exe (PID: 1632)
- IDMan.exe (PID: 1184)
- IDM_6.4x_Crack_v18.1.exe (PID: 3020)
- IDMan.exe (PID: 3704)
- IDMan.exe (PID: 2828)
Creates files or folders in the user directory
- IDM1.tmp (PID: 2468)
- IDMan.exe (PID: 1184)
- IDMan.exe (PID: 2828)
Reads the computer name
- IDM1.tmp (PID: 2468)
- IDMan.exe (PID: 1184)
- IDM_6.4x_Crack_v18.1.exe (PID: 3020)
- IDMan.exe (PID: 3704)
- IDMan.exe (PID: 2828)
- Uninstall.exe (PID: 1348)
- IEMonitor.exe (PID: 1664)
The process checks LSA protection
- IDM1.tmp (PID: 2468)
- IDMan.exe (PID: 1184)
- dllhost.exe (PID: 1760)
- taskkill.exe (PID: 3832)
- IDM_6.4x_Crack_v18.1.exe (PID: 3020)
- IDMan.exe (PID: 3704)
- IDMan.exe (PID: 2828)
- Uninstall.exe (PID: 1348)
- runonce.exe (PID: 3876)
Manual execution by a user
- IDM_6.4x_Crack_v18.1.exe (PID: 3020)
- IDM_6.4x_Crack_v18.1.exe (PID: 3932)
- IDMan.exe (PID: 3704)
- IDMan.exe (PID: 2828)
- chrome.exe (PID: 3632)
Checks proxy server information
- wscript.exe (PID: 4036)
- IDMan.exe (PID: 2828)
Reads the time zone
- runonce.exe (PID: 3876)
Creates files in the driver directory
- rundll32.exe (PID: 3528)
Application launched itself
- chrome.exe (PID: 3632)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
356
Monitored processes
282
Malicious processes
10
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | reg query "HKLM\Software\Classes\Wow6432Node\CLSID\{E8CF4E59-B7A3-41F2-86C7-82B03334F22A}" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 240 | REG DELETE "HKCU\Software\Classes\CLSID\{5ED60779-4DE2-4E07-B862-974CA4FF2E9C}" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 268 | REG DELETE "HKLM\Software\Classes\CLSID\{5ED60779-4DE2-4E07-B862-974CA4FF2E9C}" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 268 | reg query "HKLM\Software\Classes\Wow6432Node\CLSID\{7B8E9164-324D-4A2E-A46D-0165FB2000EC}" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1008,7983023398584137582,7380707213871232107,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2548 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 276 | reg query "HKLM\Software\Internet Download Manager" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 280 | REG DELETE "HKLM\Software\Classes\Wow6432Node\CLSID\{9C9D53D4-A978-43FC-93E2-1C21B529E6D7}" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 304 | REG ADD "HKLM\Software\Internet Download Manager" /v "AdvIntDriverEnabled2" /t REG_DWORD /d "1" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 308 | reg query "HKLM\Software\Wow6432Node\Download Manager" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 308 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1008,7983023398584137582,7380707213871232107,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=2536 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
41 501
Read events
40 981
Write events
391
Delete events
129
Modification events
| (PID) Process: | (3624) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
18
Suspicious files
152
Text files
141
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3624.32376\IDM v6.41.15 By IDMLover.com\idman641build15.exe | executable | |
MD5:868E7C026169D53150BDB41C70B57536 | SHA256:C70D80FE3C94371FB693572697CD8627452519D1855D23B1C680DC21B50B2059 | |||
| 3624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3624.32376\IDM v6.41.15 By IDMLover.com\IDM_6.4x_Crack_v18.1.rar | compressed | |
MD5:85A9726C8A9D3EA5FE5BADC944645337 | SHA256:80D3D5AADE8B4215E51F429492DE91F42E757205868005DD4A8EFA413DF383C3 | |||
| 3624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3624.32376\IDM v6.41.15 By IDMLover.com\Read Me First.txt | text | |
MD5:ADCD7C3BC537B9211754E8C24E939680 | SHA256:3EE34D99A071D09BD8AD8F62BEF42E2998E6F33B40AB5D0FB57AC1E878241A49 | |||
| 2468 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\IDM Help.lnk | binary | |
MD5:F242B0CEE9021ED1E58E057B9A179A1A | SHA256:C3521F35490BDDF54C06DB353945813798CF82164294A5F3CF86CBA705C8FDC4 | |||
| 2468 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Uninstall IDM.lnk | binary | |
MD5:8509E3D131527E5338A7941480B94228 | SHA256:8A740718C89D960F2B53C399291768636E441D2D1F42339DDD5A800C1B2E2874 | |||
| 2468 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\license.lnk | binary | |
MD5:D76FF02C129030D717DFBAF4A6884082 | SHA256:8016EDA684C2B4B6A04C964D27F91230F550F990834848FF7509C29A72181DA3 | |||
| 2468 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\license.lnk | binary | |
MD5:031D754985206FACBCF65E62AD8080B3 | SHA256:CFF4F10D23C74369C2A69FB0FBD1963C66986B81C1004A40F337A6EFD173E476 | |||
| 2468 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Internet Download Manager.lnk | binary | |
MD5:BE41FCBC8EF0BF0D381B4752583B9593 | SHA256:CFE9D0755DEF1AF8FDF50287A38CD864D3BAB6CF2B4C12229E8EE53715912FCF | |||
| 2468 | IDM1.tmp | C:\Users\admin\AppData\Local\Temp\IDM_Setup_Temp\IDMSetup2.log | binary | |
MD5:1C92BCB479B9EE7BBC5F5E6754B125B2 | SHA256:95EFFBCC2269DB3E96C984D8249D14DBCDD8D4CF6A43143CBA0D7D20F96DF991 | |||
| 2468 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\IDM Help.lnk | binary | |
MD5:E11C2329096E5BB8821B5CAEB4988AC6 | SHA256:3AC65160929AF3BB8D835D280D678048E7EEB0991F5FBB7B01A3301B56643E50 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
74
DNS requests
48
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
864 | svchost.exe | HEAD | 403 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/fessmlfzcgvxcvvlvzjb5y3pia_9.46.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.46.0_all_j3wc2ia5cvmxcar5vj37bzshkm.crx3 | US | — | — | whitelisted |
1184 | IDMan.exe | GET | — | 8.238.178.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?f0df1028874abfc6 | US | — | — | whitelisted |
864 | svchost.exe | GET | — | 142.250.179.206:80 | http://dl.google.com/release2/chrome_component/fessmlfzcgvxcvvlvzjb5y3pia_9.46.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.46.0_all_j3wc2ia5cvmxcar5vj37bzshkm.crx3 | US | — | — | whitelisted |
864 | svchost.exe | HEAD | 200 | 142.250.179.206:80 | http://dl.google.com/release2/chrome_component/fessmlfzcgvxcvvlvzjb5y3pia_9.46.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.46.0_all_j3wc2ia5cvmxcar5vj37bzshkm.crx3 | US | — | — | whitelisted |
— | — | POST | 200 | 172.64.111.33:80 | http://9anime.to/cdn-cgi/challenge-platform/h/b/flow/ov1/1346836141:1689722941:K-2Y_po2_e1fdmhgsy-F_KWCa-NIETu7bOS8IpleVq8/7e8ee6cb4d38b930/efce9c01dafa5af | US | text | 6.98 Kb | whitelisted |
— | — | GET | 200 | 74.125.100.106:80 | http://r5---sn-5hnekn7z.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx?cms_redirect=yes&mh=e_&mip=192.42.116.16&mm=28&mn=sn-5hnekn7z&ms=nvh&mt=1689726743&mv=m&mvi=5&pl=22&shardbypass=sd&smhost=r5---sn-5hneknes.gvt1.com | US | binary | 242 Kb | whitelisted |
— | — | GET | 200 | 172.64.111.33:80 | http://9anime.to/favicon.ico | US | compressed | 55.5 Kb | whitelisted |
— | — | GET | 200 | 172.64.111.33:80 | http://9anime.to/favicon.ico | US | compressed | 55.5 Kb | whitelisted |
— | — | GET | 403 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | text | 37 b | whitelisted |
— | — | GET | 200 | 172.64.111.33:80 | http://9anime.to/favicon.ico | US | compressed | 2.01 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2640 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1068 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1184 | IDMan.exe | 8.238.178.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
4036 | wscript.exe | 172.67.164.61:443 | idm.ckk.ir | CLOUDFLARENET | US | unknown |
3704 | IDMan.exe | 8.238.178.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
4036 | wscript.exe | 8.238.178.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
4036 | wscript.exe | 142.251.36.3:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3632 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
idm.ckk.ir |
| unknown |
test.internetdownloadmanager.com |
| whitelisted |
secure.internetdownloadmanager.com |
| whitelisted |
www.internetdownloadmanager.com |
| whitelisted |
mirror3.internetdownloadmanager.com |
| whitelisted |
mirror5.internetdownloadmanager.com |
| whitelisted |
registeridm.com |
| suspicious |
ocsp.pki.goog |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET DNS Query for .to TLD |