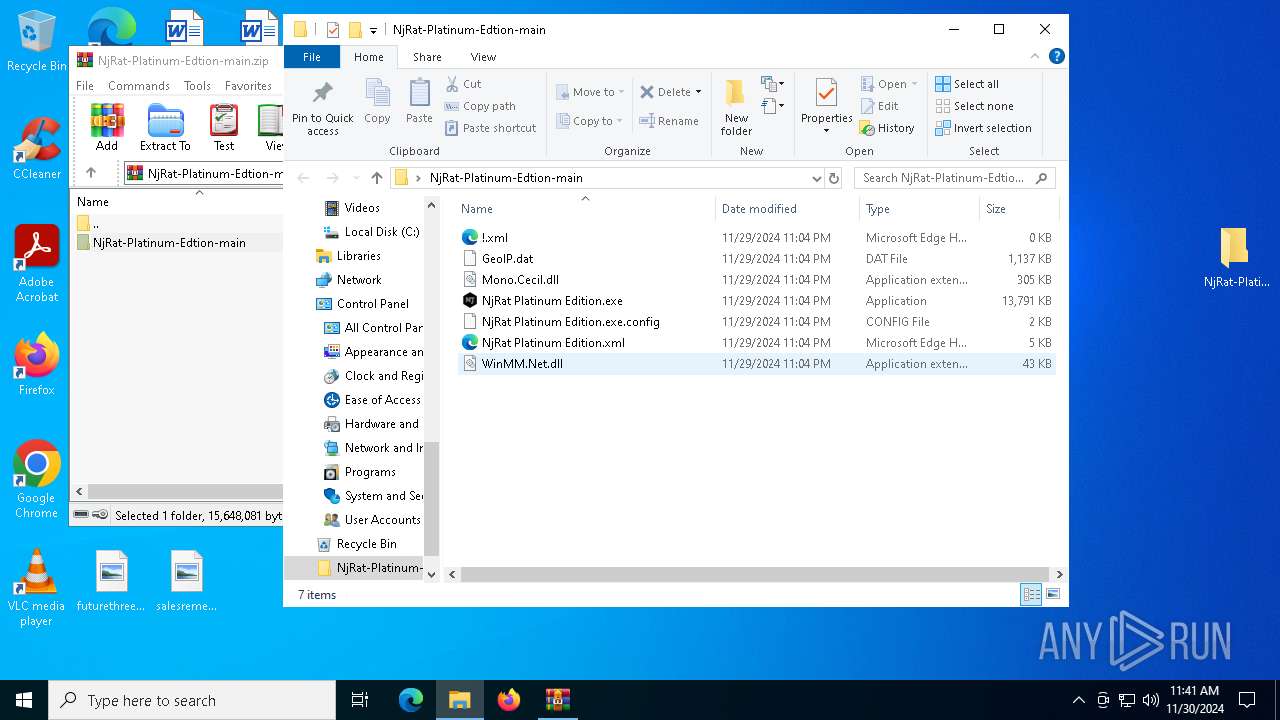
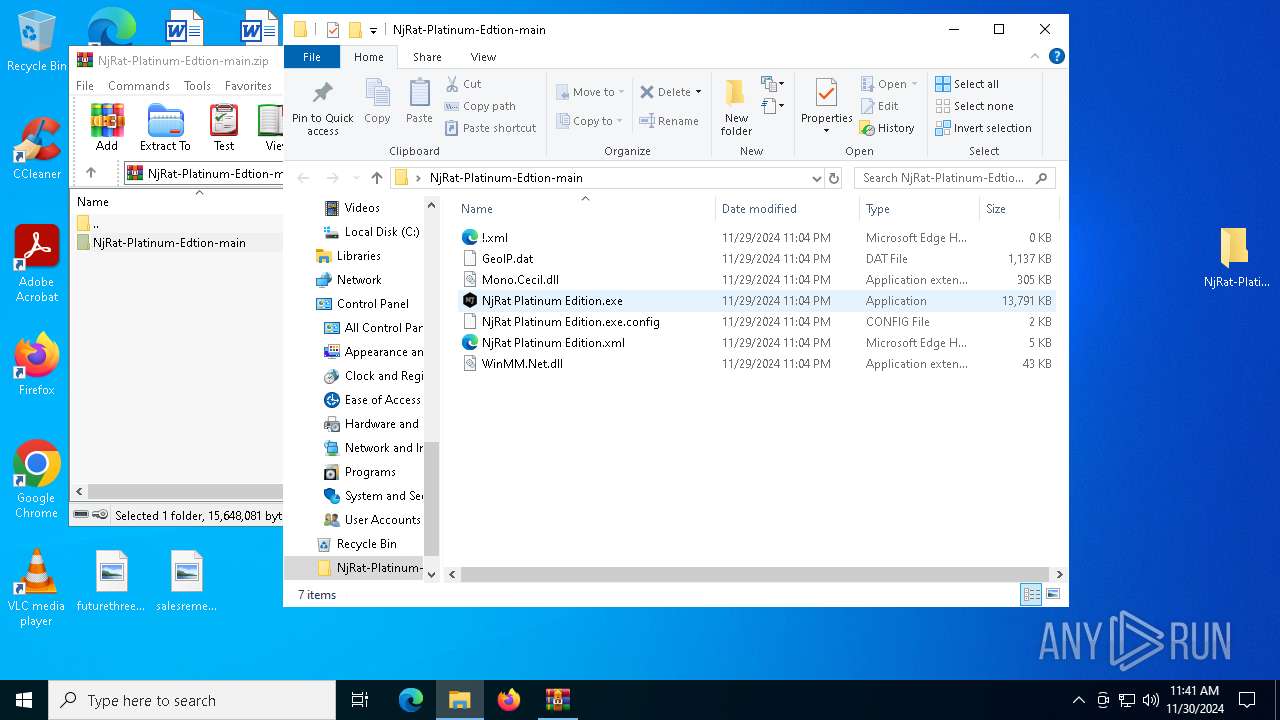
| File name: | NjRat-Platinum-Edtion-main.zip |
| Full analysis: | https://app.any.run/tasks/a7601507-0f7f-4ebc-a0f0-da6b70464097 |
| Verdict: | Malicious activity |
| Analysis date: | November 30, 2024, 11:41:22 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 8E2E40E372E68C8A7C47C8BF4D44F373 |
| SHA1: | EBA133F255DC411B3495ECA8EEE38641DE7CA760 |
| SHA256: | 3F10DA55368841FDCDCC2D172D8B908D1763539B10EE1A42782F8DB546636CE6 |
| SSDEEP: | 196608:IQT6k2W88OpGNS5lluhaAfYeaMZYl6aEMA:t6k2x/llu0oRrZYlnO |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
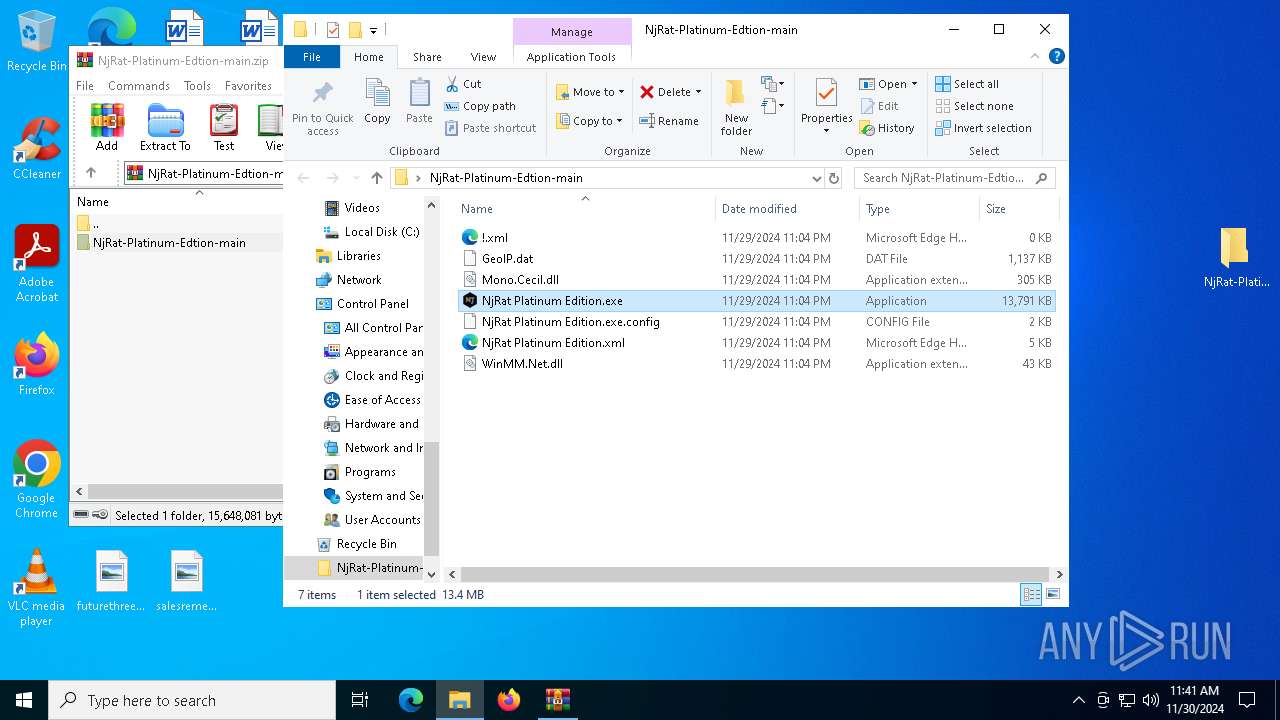
- NjRat Platinum Edition.exe (PID: 7080)
Process drops legitimate windows executable
- NjRat Platinum Edition.exe (PID: 7080)
Application launched itself
- NjRat Platinum Edition.exe (PID: 7080)
The process drops C-runtime libraries
- NjRat Platinum Edition.exe (PID: 7080)
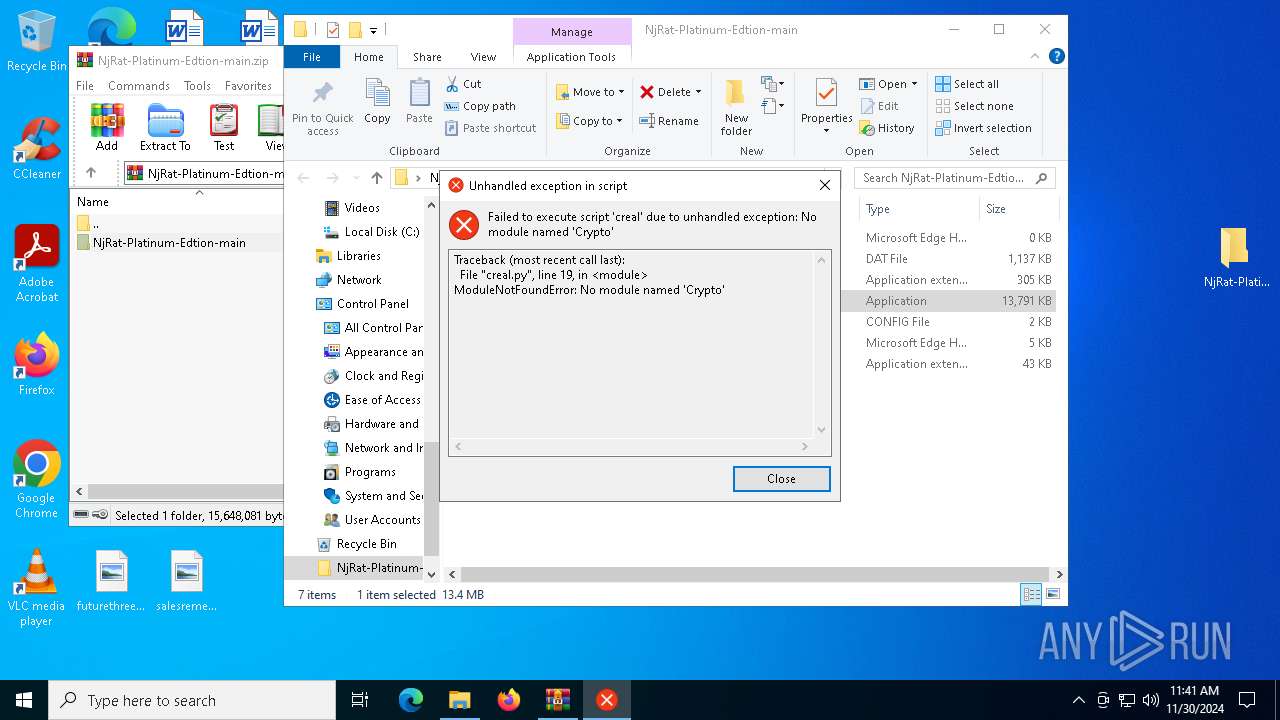
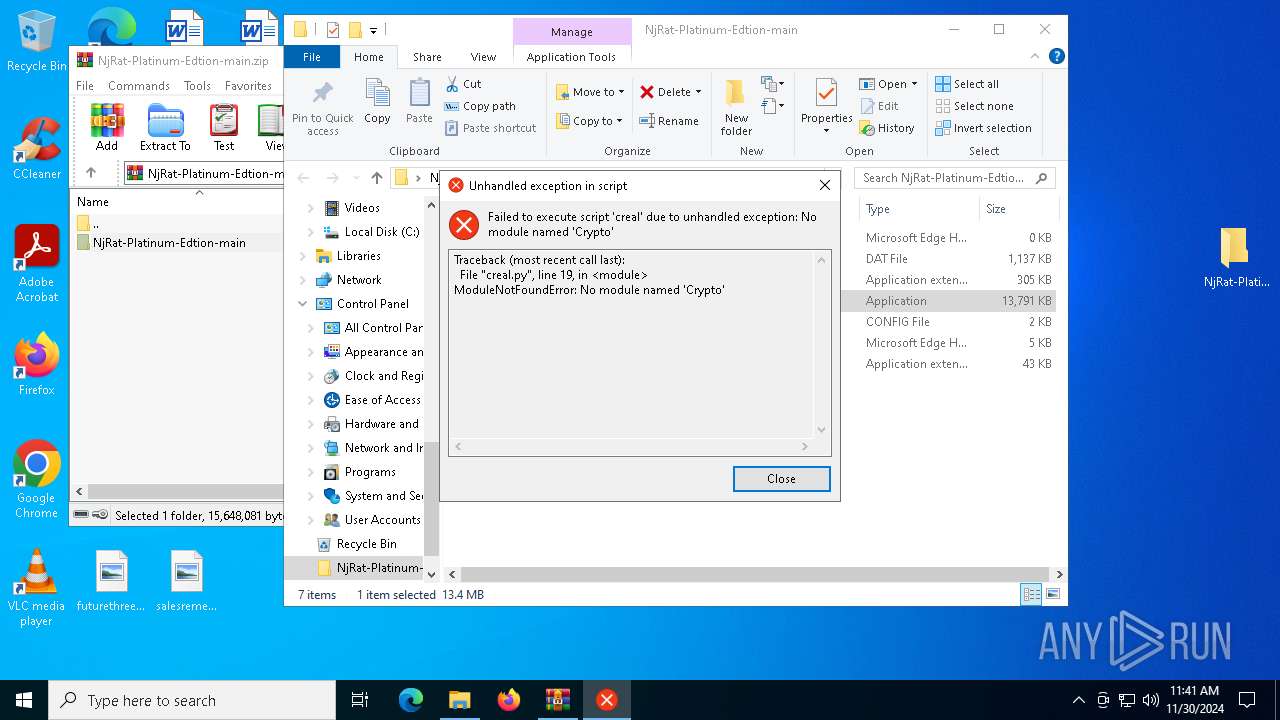
Process drops python dynamic module
- NjRat Platinum Edition.exe (PID: 7080)
Loads Python modules
- NjRat Platinum Edition.exe (PID: 7100)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6808)
Checks supported languages
- NjRat Platinum Edition.exe (PID: 7080)
- NjRat Platinum Edition.exe (PID: 7100)
Reads the computer name
- NjRat Platinum Edition.exe (PID: 7080)
- NjRat Platinum Edition.exe (PID: 7100)
The process uses the downloaded file
- WinRAR.exe (PID: 6808)
Create files in a temporary directory
- NjRat Platinum Edition.exe (PID: 7080)
Manual execution by a user
- NjRat Platinum Edition.exe (PID: 7080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:11:29 15:04:32 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | NjRat-Platinum-Edtion-main/ |
Total processes
127
Monitored processes
4
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6808 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\NjRat-Platinum-Edtion-main.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7040 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7080 | "C:\Users\admin\Desktop\NjRat-Platinum-Edtion-main\NjRat Platinum Edition.exe" | C:\Users\admin\Desktop\NjRat-Platinum-Edtion-main\NjRat Platinum Edition.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 7100 | "C:\Users\admin\Desktop\NjRat-Platinum-Edtion-main\NjRat Platinum Edition.exe" | C:\Users\admin\Desktop\NjRat-Platinum-Edtion-main\NjRat Platinum Edition.exe | — | NjRat Platinum Edition.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
Total events
1 489
Read events
1 481
Write events
8
Delete events
0
Modification events
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\NjRat-Platinum-Edtion-main.zip | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
69
Suspicious files
2
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6808.21047\NjRat-Platinum-Edtion-main\NjRat Platinum Edition.exe | executable | |
MD5:1D756AD44006FB65CF7814FF37BA4100 | SHA256:9D87C3740849853EA177065A10BE3E88861F4A1C81917EE020E4432DA53F3BBF | |||
| 7080 | NjRat Platinum Edition.exe | C:\Users\admin\AppData\Local\Temp\_MEI70802\VCRUNTIME140_1.dll | executable | |
MD5:68156F41AE9A04D89BB6625A5CD222D4 | SHA256:82A2F9AE1E6146AE3CB0F4BC5A62B7227E0384209D9B1AEF86BBCC105912F7CD | |||
| 7080 | NjRat Platinum Edition.exe | C:\Users\admin\AppData\Local\Temp\_MEI70802\_brotli.cp313-win_amd64.pyd | executable | |
MD5:5ED46A7126DBDB70F3C60530E35BA035 | SHA256:67DFA82DCAED04ED3F358D84B18D1375D59126161DE92E00164D36087B179D4D | |||
| 7080 | NjRat Platinum Edition.exe | C:\Users\admin\AppData\Local\Temp\_MEI70802\_bz2.pyd | executable | |
MD5:CB8C06C8FA9E61E4AC5F22EEBF7F1D00 | SHA256:FC3B481684B926350057E263622A2A5335B149A0498A8D65C4F37E39DD90B640 | |||
| 6808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6808.21047\NjRat-Platinum-Edtion-main\Mono.Cecil.dll | executable | |
MD5:851EC9D84343FBD089520D420348A902 | SHA256:CDADC26C09F869E21053EE1A0ACF3B2D11DF8EDD599FE9C377BD4D3CE1C9CDA9 | |||
| 6808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6808.21047\NjRat-Platinum-Edtion-main\NjRat Platinum Edition.exe.config | xml | |
MD5:DA15A1D8D770B57356DDD384342B3034 | SHA256:C45C9D1D30F940289498BE2AF978D74178A5C24CEB7755C2648F6C7A89353813 | |||
| 6808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6808.21047\NjRat-Platinum-Edtion-main\NjRat Platinum Edition.xml | xml | |
MD5:0F2EE4833BFBF61F404BB982C40BA249 | SHA256:25FDF1BF3806EF92E022C6085F63D44EE314764CB053B9456AD0C8D86ABD1301 | |||
| 6808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6808.21047\NjRat-Platinum-Edtion-main\GeoIP.dat | binary | |
MD5:A0A228C187329AD148F33C81DDB430BB | SHA256:B4BFD1EBC50F0EAAB3D3F4C2152FEAE7AA8EFAD380B85064153A6BFD006C6210 | |||
| 7080 | NjRat Platinum Edition.exe | C:\Users\admin\AppData\Local\Temp\_MEI70802\_ctypes.pyd | executable | |
MD5:A55E57D7594303C89B5F7A1D1D6F2B67 | SHA256:F63C6C7E71C342084D8F1A108786CA6975A52CEFEF8BE32CC2589E6E2FE060C8 | |||
| 7080 | NjRat Platinum Edition.exe | C:\Users\admin\AppData\Local\Temp\_MEI70802\_queue.pyd | executable | |
MD5:1C03CAA59B5E4A7FB9B998D8C1DA165A | SHA256:B9CF502DADCB124F693BF69ECD7077971E37174104DBDA563022D74961A67E1E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
28
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.53.40.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6384 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2736 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2736 | SIHClient.exe | GET | — | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.53.40.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 104.126.37.145:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1076 | svchost.exe | 23.218.210.69:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |