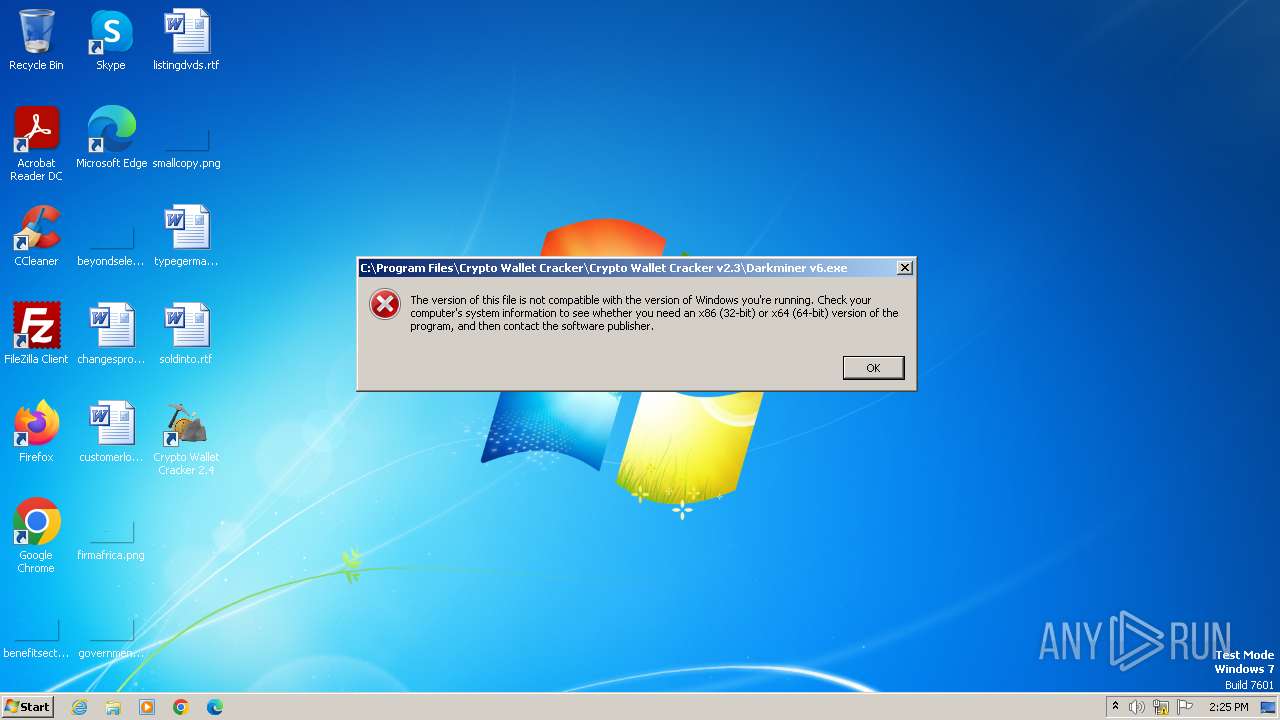
| File name: | Crypto Wallet Cracker v2.3.msi |
| Full analysis: | https://app.any.run/tasks/8c46a291-4a7d-4622-854a-22978bcd7b44 |
| Verdict: | Malicious activity |
| Analysis date: | December 03, 2023, 14:25:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Create Time/Date: Mon Jun 21 08:00:00 1999, Name of Creating Application: Windows Installer, Security: 1, Code page: 1252, Template: Intel;1033, Number of Pages: 200, Revision Number: {140A9090-6D9B-4E59-ADC9-2D5792C47FCB}, Title: Crypto Wallet Cracker, Author: Crypto Wallet Cracker, Number of Words: 2, Last Saved Time/Date: Tue Oct 17 19:42:57 2023, Last Printed: Tue Oct 17 19:42:57 2023 |
| MD5: | 0AA7BC441695F50C63F180B6BB8A084D |
| SHA1: | 256ECD5A3F3D74FBE9C52243D6F755B7D9829989 |
| SHA256: | 3F061D6733F9BF1F147C2FEB0768F8FE992957C5AB2895BBF01D16C9E7A16C32 |
| SSDEEP: | 98304:CiRM47UCKIRHdDADAzmkiOLQeyjWF+YFcOgc5yrG4ALjYOChRP/1gZjOOZoUP7KL:F9o |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 2740)
SUSPICIOUS
Process drops legitimate windows executable
- msiexec.exe (PID: 3060)
- msiexec.exe (PID: 2740)
Executes as Windows Service
- VSSVC.exe (PID: 1996)
INFO
Checks supported languages
- msiexec.exe (PID: 2740)
- msiexec.exe (PID: 1924)
- msiexec.exe (PID: 3176)
Reads the computer name
- msiexec.exe (PID: 2740)
- msiexec.exe (PID: 1924)
- msiexec.exe (PID: 3176)
Drops the executable file immediately after the start
- msiexec.exe (PID: 3060)
Application launched itself
- msiexec.exe (PID: 2740)
Reads the machine GUID from the registry
- msiexec.exe (PID: 2740)
- msiexec.exe (PID: 1924)
- msiexec.exe (PID: 3176)
Create files in a temporary directory
- msiexec.exe (PID: 2740)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (90.2) |
|---|---|---|
| .msp | | | Windows Installer Patch (8.4) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CreateDate: | 1999:06:21 07:00:00 |
|---|---|
| Software: | Windows Installer |
| Security: | Password protected |
| CodePage: | Windows Latin 1 (Western European) |
| Template: | Intel;1033 |
| Pages: | 200 |
| RevisionNumber: | {140A9090-6D9B-4E59-ADC9-2D5792C47FCB} |
| Title: | Crypto Wallet Cracker |
| Subject: | - |
| Author: | Crypto Wallet Cracker |
| Keywords: | - |
| Comments: | - |
| Words: | 2 |
| ModifyDate: | 2023:10:17 18:42:57 |
| LastPrinted: | 2023:10:17 18:42:57 |
Total processes
43
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1924 | C:\Windows\system32\MsiExec.exe -Embedding 24B1AD0E5CF899E981A585AAC41CDC4E C | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1996 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2740 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3060 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\Crypto Wallet Cracker v2.3.msi" | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3176 | C:\Windows\system32\MsiExec.exe -Embedding A7A0CE5254434718465745207435F4D0 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 973
Read events
2 947
Write events
16
Delete events
10
Modification events
| (PID) Process: | (2740) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000F2B487BA16B0D901C80700002C0A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2740) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000F2B487BA16B0D901C80700002C0A0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2740) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 72 | |||
| (PID) Process: | (2740) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000008C62D6BA16B0D901C80700002C0A0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2740) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Leave) |
Value: 400000000000000064514ABC16B0D901C80700002C0A0000D3070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2740) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppAddInterestingComponents (Enter) |
Value: 400000000000000064514ABC16B0D901C80700002C0A0000D4070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2740) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppAddInterestingComponents (Leave) |
Value: 400000000000000034645DBC16B0D901C80700002C0A0000D4070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2740) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Leave) |
Value: 4000000000000000781D5ABD16B0D901C80700002C0A0000D0070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2740) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Leave) |
Value: 4000000000000000781D5ABD16B0D901C80700002C0A0000D5070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2740) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore |
| Operation: | write | Name: | FirstRun |
Value: 0 | |||
Executable files
8
Suspicious files
13
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2740 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3060 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI6BDE.tmp | executable | |
MD5:B77A2A2768B9CC78A71BBFFB9812B978 | SHA256:F74C97B1A53541B059D3BFAFE41A79005CE5065F8210D7DE9F1B600DC4E28AA0 | |||
| 2740 | msiexec.exe | C:\Windows\Installer\MSIA358.tmp | executable | |
MD5:B77A2A2768B9CC78A71BBFFB9812B978 | SHA256:F74C97B1A53541B059D3BFAFE41A79005CE5065F8210D7DE9F1B600DC4E28AA0 | |||
| 2740 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{54ce3c4e-fb21-4d8a-9f91-b45564d09dba}_OnDiskSnapshotProp | binary | |
MD5:F15C41E8D5A1A93FCAC2924817D6EECD | SHA256:4C43C1196B734483F5B5E02FDE575FFB5F41DD00F85C505D6006A5D6681EB9FA | |||
| 2740 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:F15C41E8D5A1A93FCAC2924817D6EECD | SHA256:4C43C1196B734483F5B5E02FDE575FFB5F41DD00F85C505D6006A5D6681EB9FA | |||
| 2740 | msiexec.exe | C:\Windows\Installer\MSIA3A7.tmp | executable | |
MD5:B77A2A2768B9CC78A71BBFFB9812B978 | SHA256:F74C97B1A53541B059D3BFAFE41A79005CE5065F8210D7DE9F1B600DC4E28AA0 | |||
| 2740 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DFA750959F76B99918.TMP | binary | |
MD5:6FD2BC529733115E9B54517DFBE6783A | SHA256:B840CAF759BF9DE763100F1A981D05332FD73397925C4B954F46BEE71048BDF1 | |||
| 2740 | msiexec.exe | C:\Windows\Installer\20a0e8.ipi | binary | |
MD5:CB2A18B34809579E9A9DE34FAA60AC4D | SHA256:155FBB02315A80CD1F7056836C66DA1BAF3FFDA604DC4FBD83EF419C6C1A014A | |||
| 2740 | msiexec.exe | C:\Windows\Installer\MSIA4B2.tmp | binary | |
MD5:C3AAF6C64D95743504AF8452C1005D85 | SHA256:16C2B430672634AB3AB88E3E68EE4618B89EC15D76EBFAE3AA63F2D353A91A1B | |||
| 2740 | msiexec.exe | C:\Windows\Installer\20a0e7.msi | executable | |
MD5:0AA7BC441695F50C63F180B6BB8A084D | SHA256:3F061D6733F9BF1F147C2FEB0768F8FE992957C5AB2895BBF01D16C9E7A16C32 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |