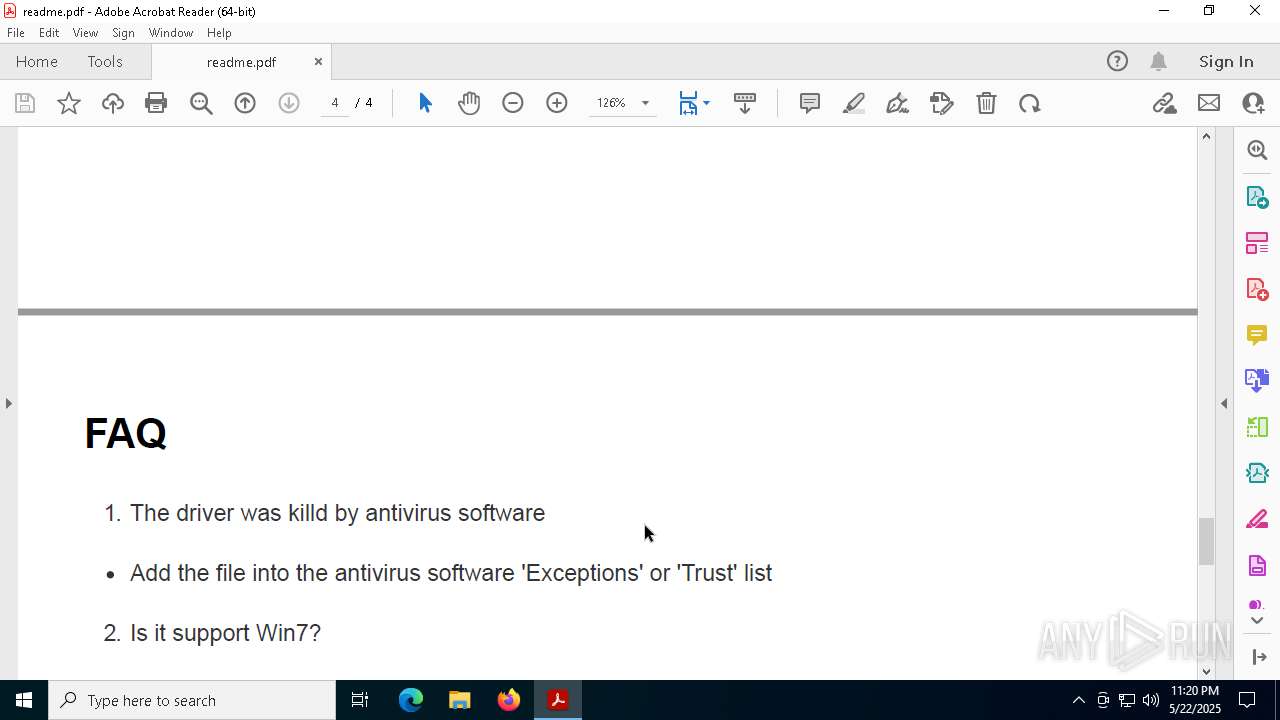
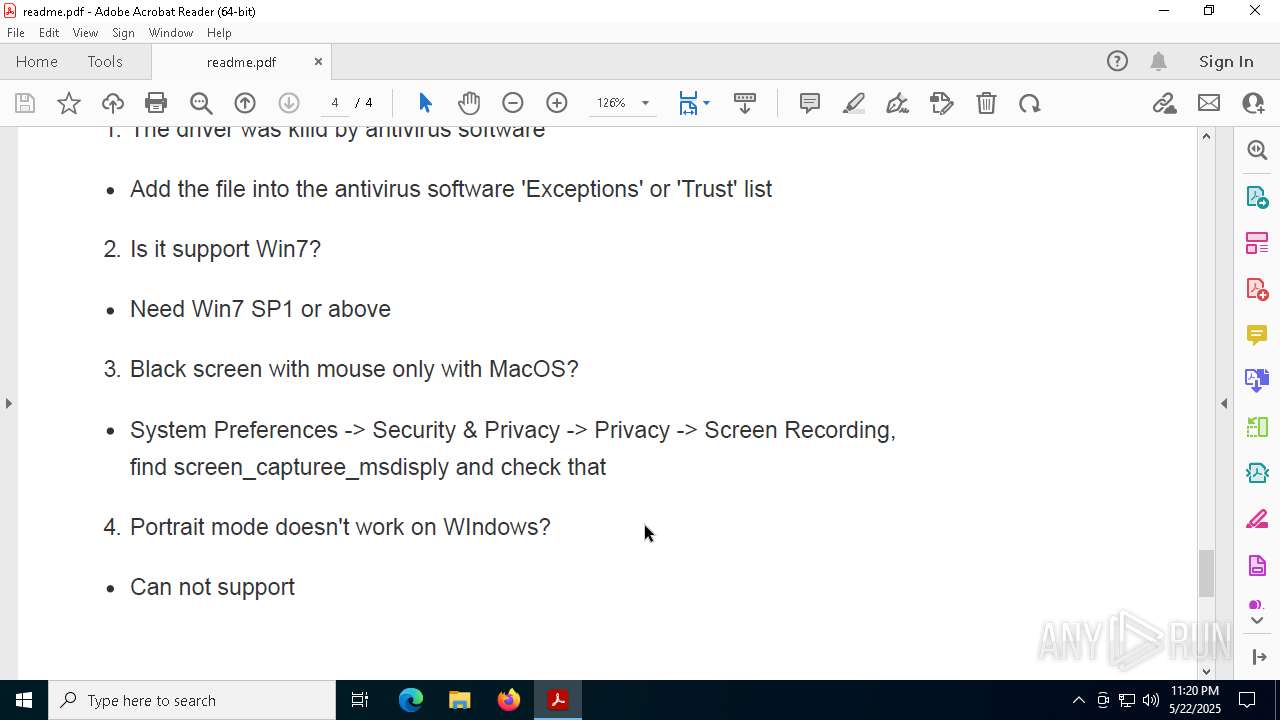
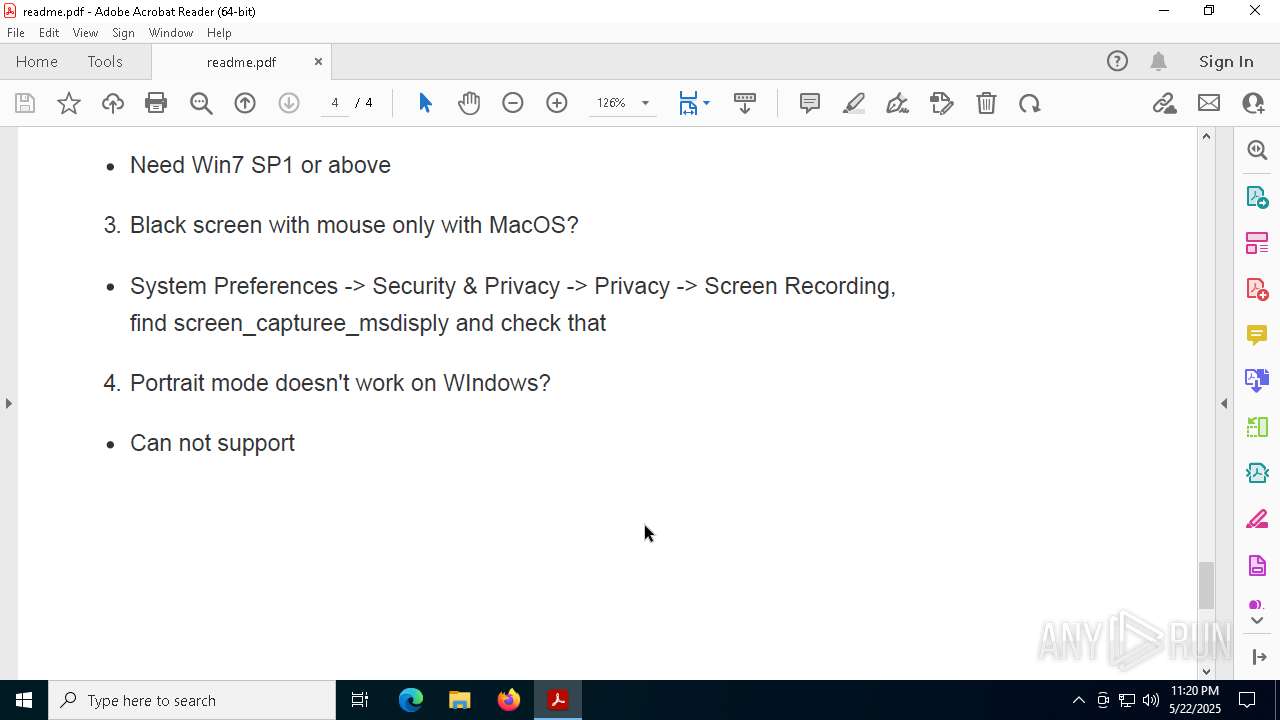
| File name: | readme.pdf |
| Full analysis: | https://app.any.run/tasks/2c2d5006-885d-4890-aa53-7046c21ebcf3 |
| Verdict: | Malicious activity |
| Analysis date: | May 22, 2025, 23:20:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.4, 4 page(s) |
| MD5: | 722CE9E26CB0E10243505FA279F0B671 |
| SHA1: | 4FEC3F23B4EBEFC7C58FFFFE7789419EA9CAE2A5 |
| SHA256: | 3EFA806C3F175E8CCE087811E02B62D4707F4B80514C0CA4F4420D5D7966C9D3 |
| SSDEEP: | 1536:ME7BAqc4nq6sTLTChCThyoGaUkqyghbvJjPzcW32:jaqcxnLTChSyoGaxgrjPz2 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Found IP address in command line
- powershell.exe (PID: 9040)
Starts POWERSHELL.EXE for commands execution
- OpenWith.exe (PID: 8740)
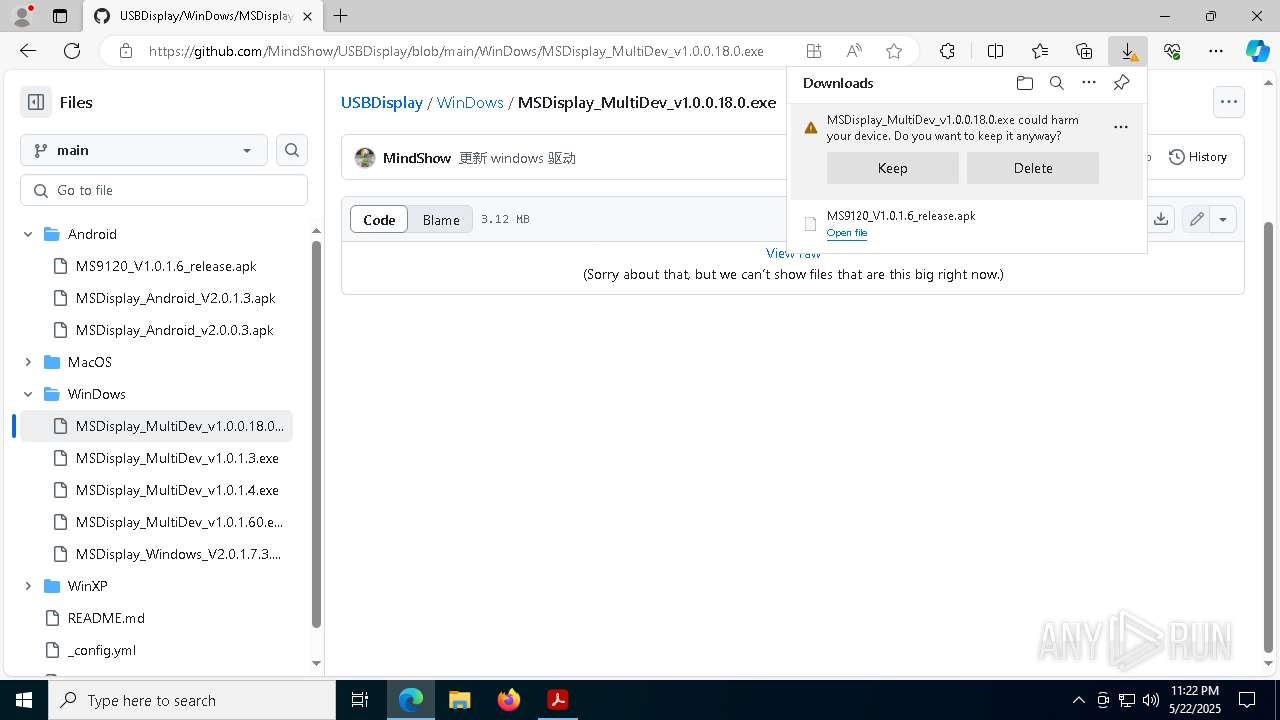
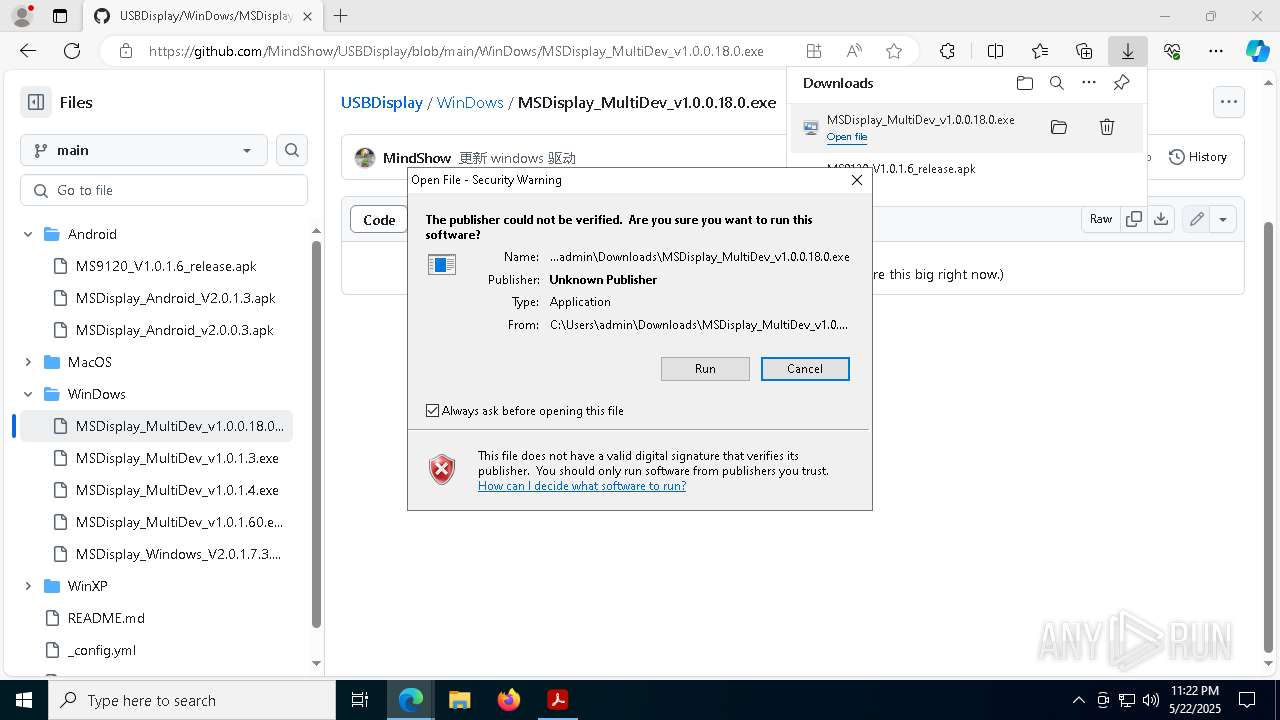
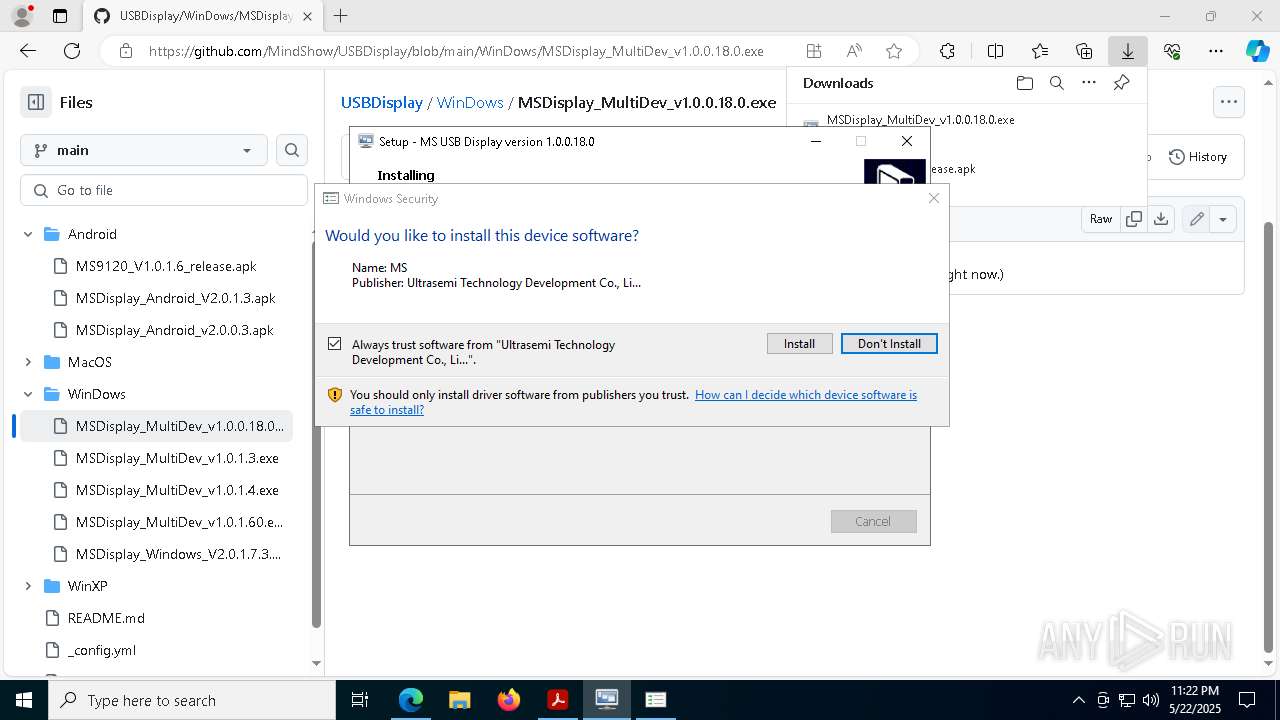
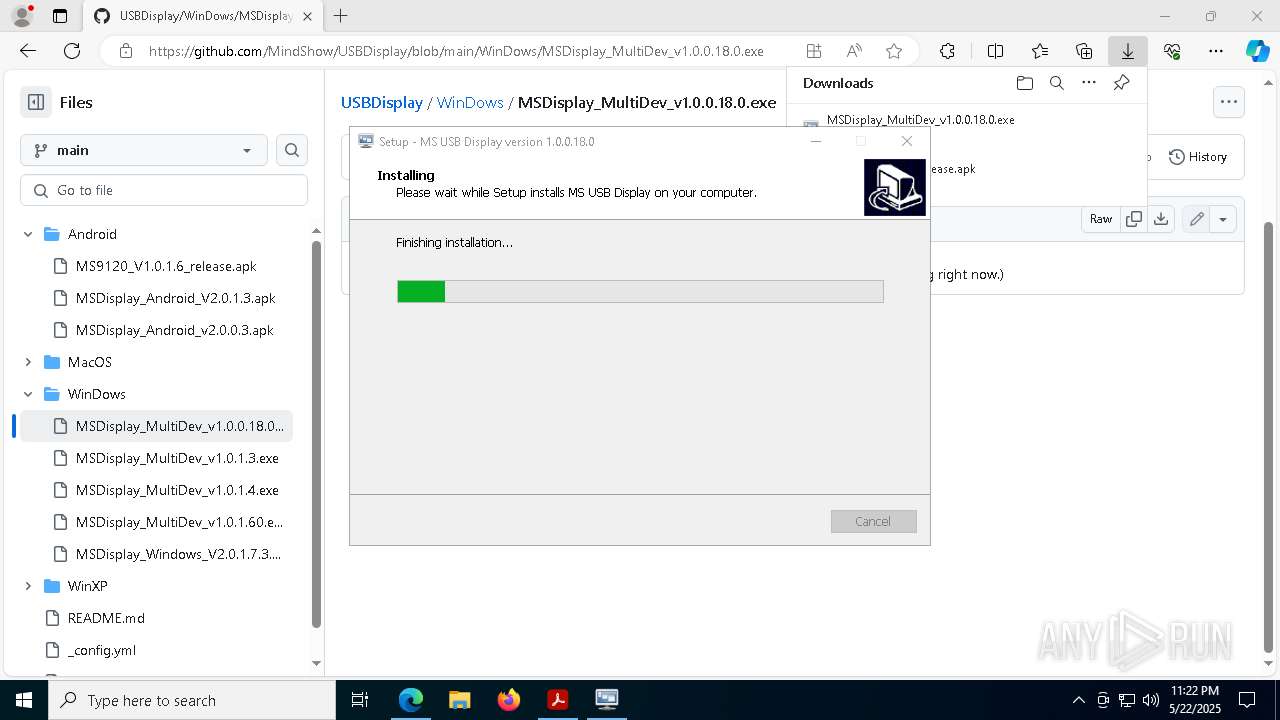
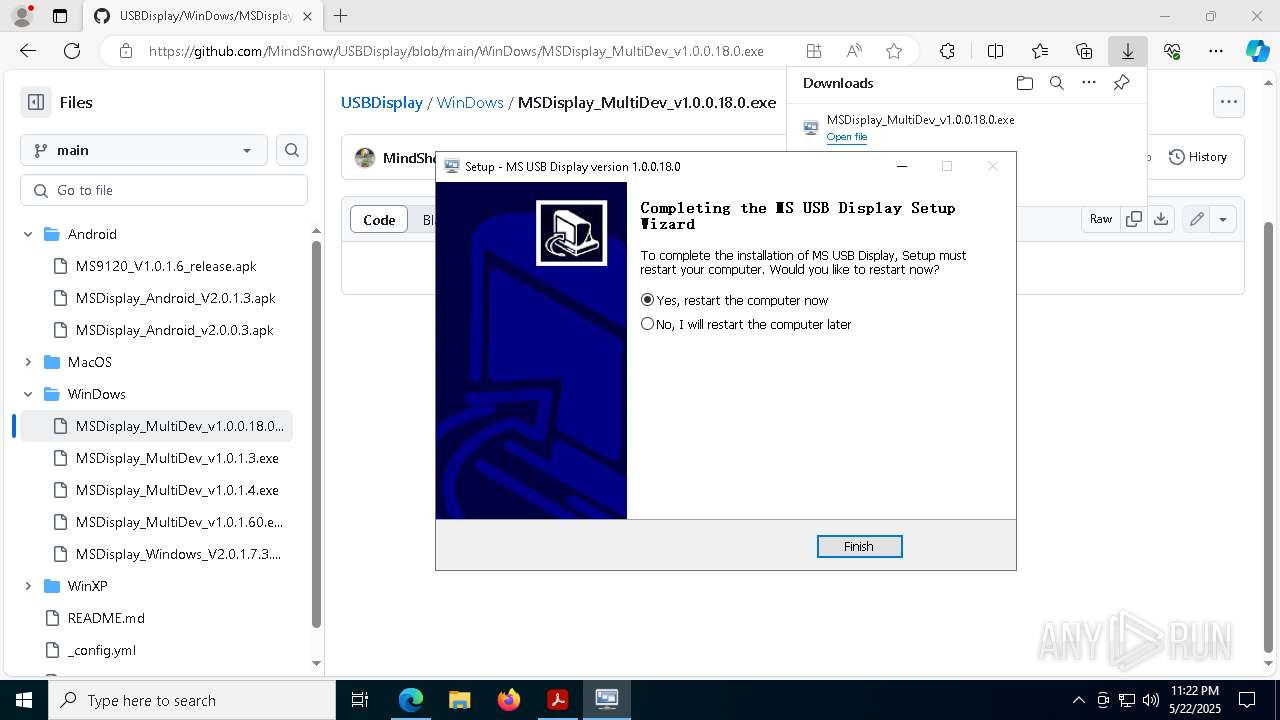
Executable content was dropped or overwritten
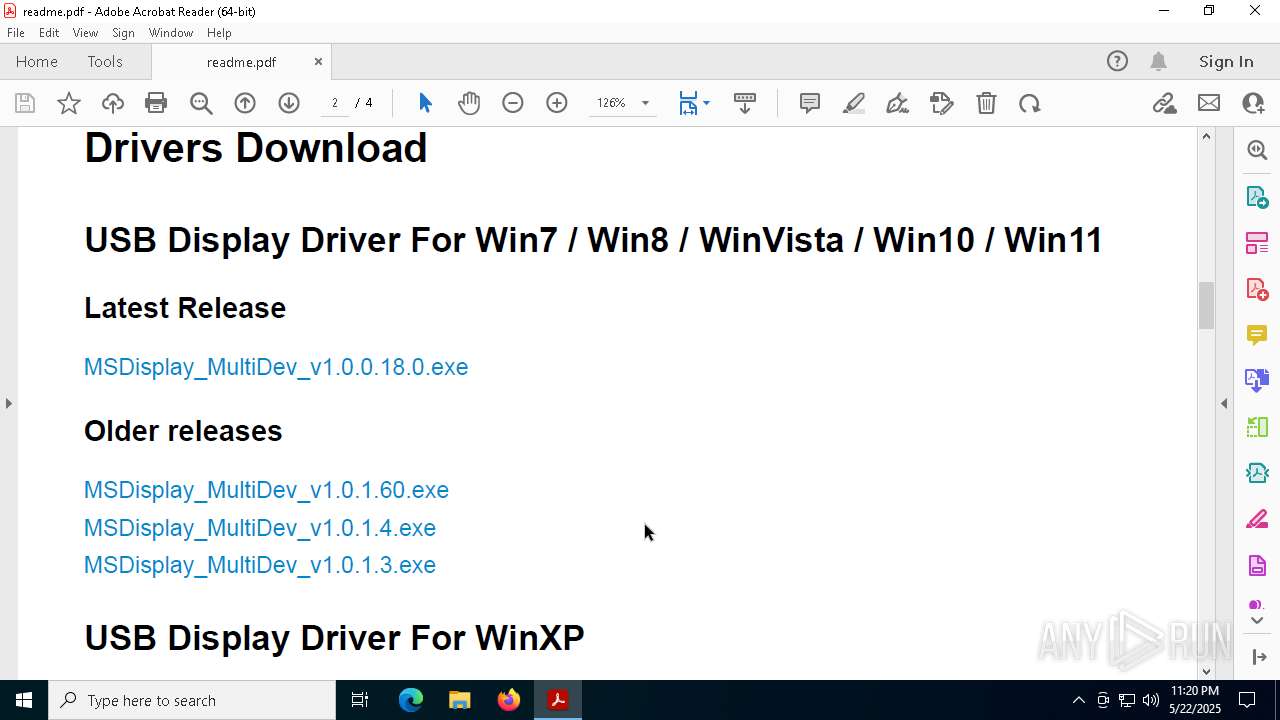
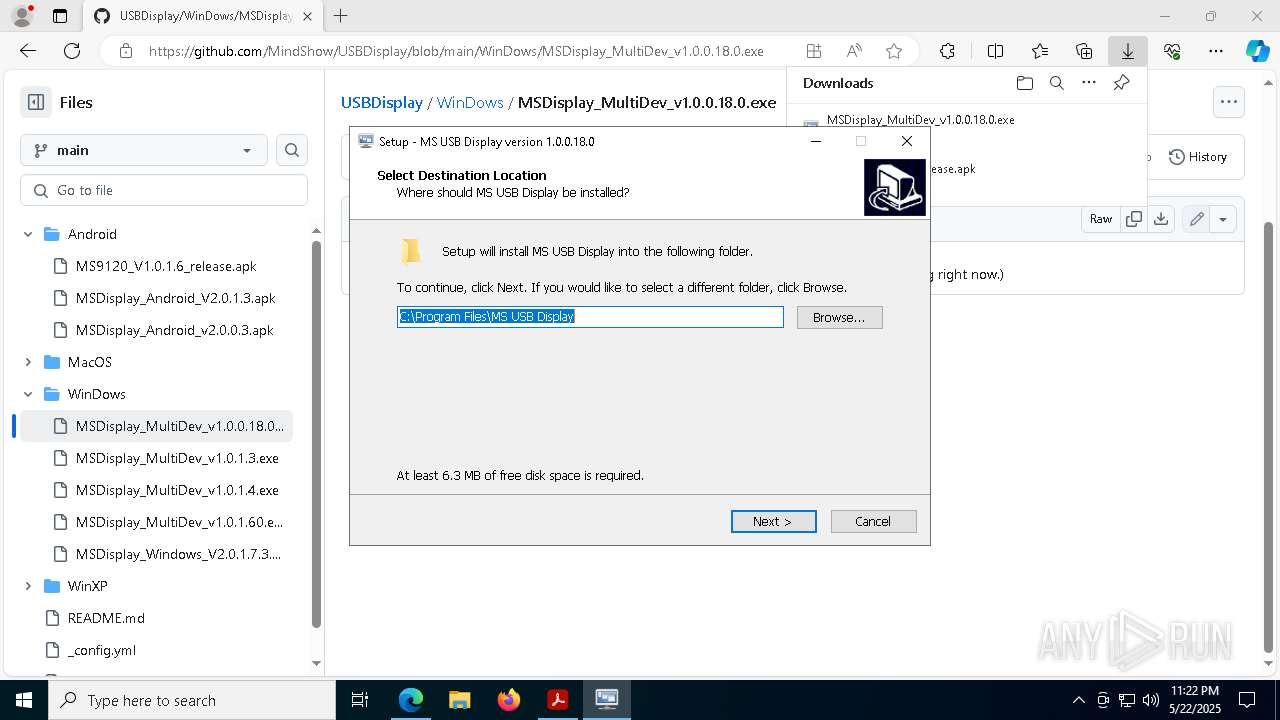
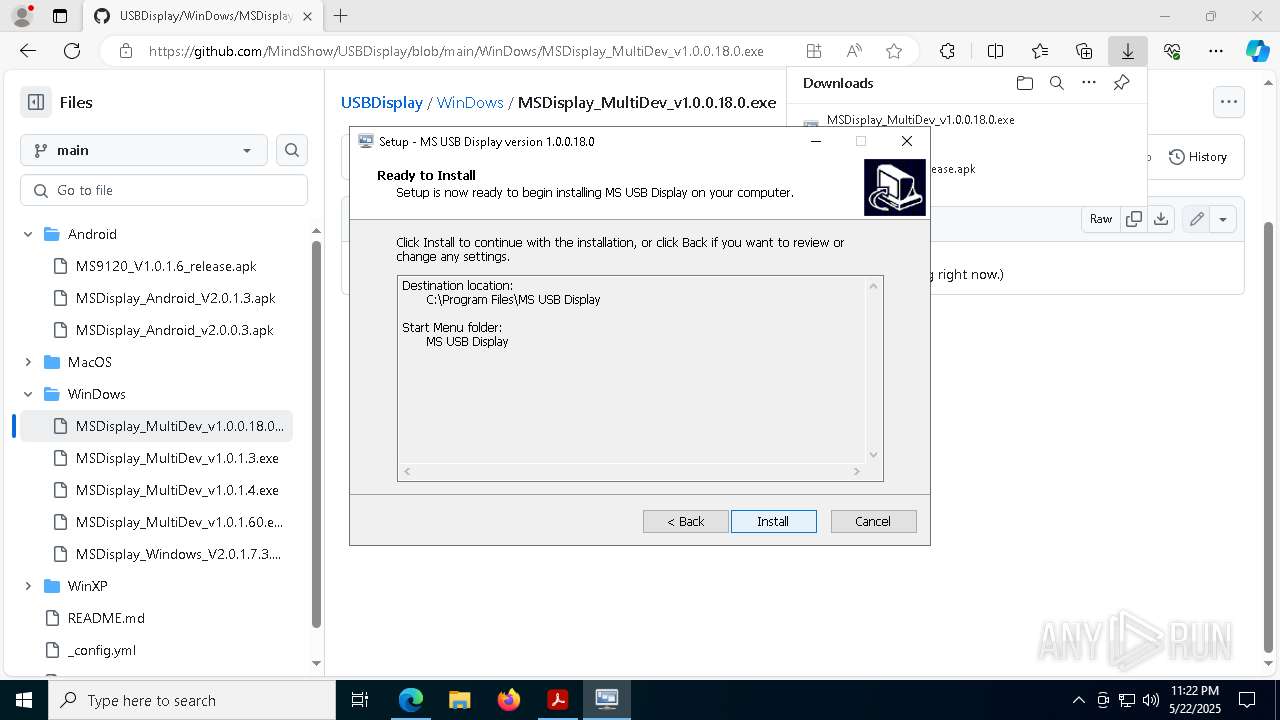
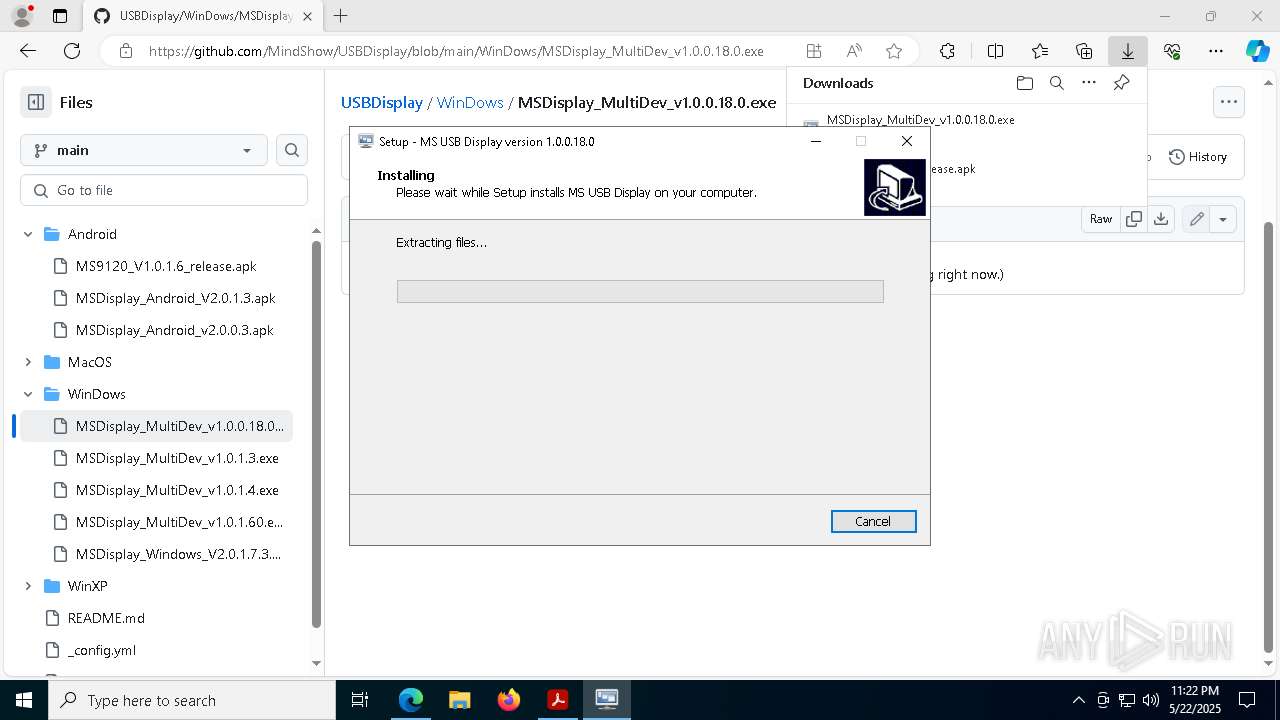
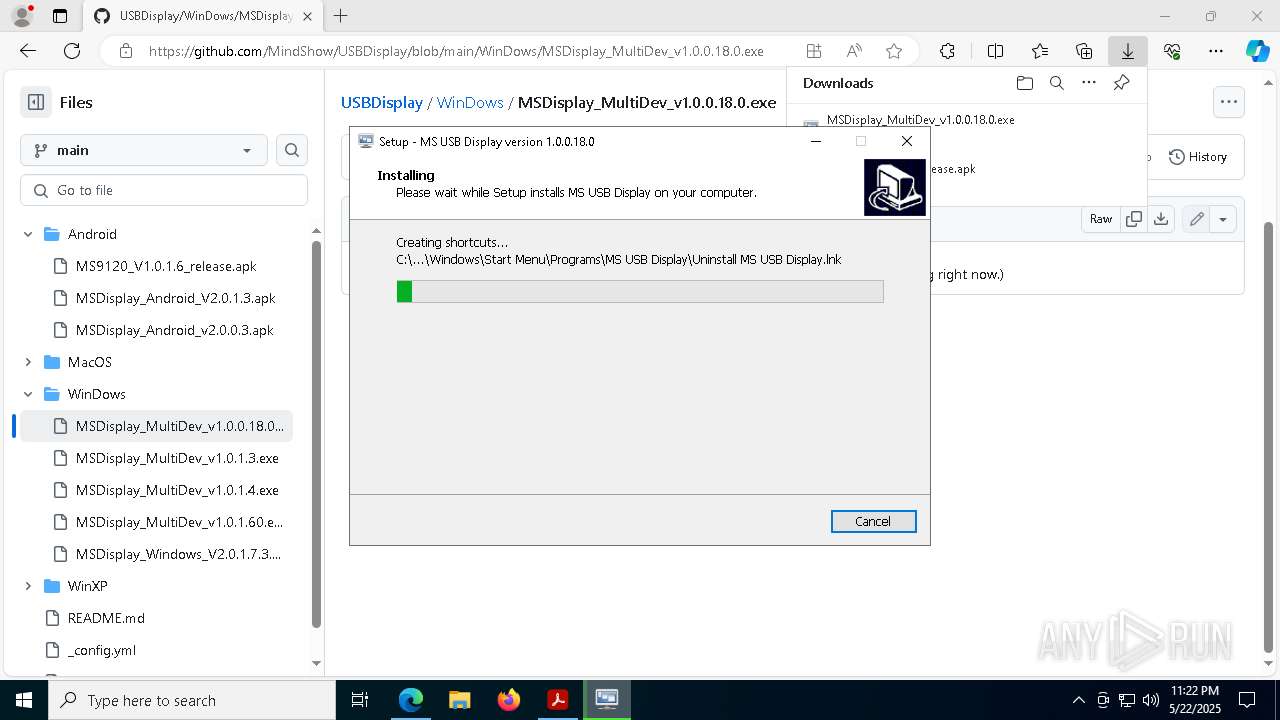
- MSDisplay_MultiDev_v1.0.0.18.0.tmp (PID: 3304)
- MSDisplay_MultiDev_v1.0.0.18.0.exe (PID: 7176)
- MSDisplay_MultiDev_v1.0.0.18.0.exe (PID: 3968)
- devcon.exe (PID: 7660)
- drvinst.exe (PID: 8432)
- drvinst.exe (PID: 9104)
- devcon.exe (PID: 7696)
- drvinst.exe (PID: 3124)
- devcon.exe (PID: 8880)
- drvinst.exe (PID: 968)
- drvinst.exe (PID: 9012)
- drvinst.exe (PID: 8364)
- drvinst.exe (PID: 6652)
- devcon.exe (PID: 7296)
- drvinst.exe (PID: 776)
- devcon.exe (PID: 8304)
- drvinst.exe (PID: 4528)
The process drops C-runtime libraries
- MSDisplay_MultiDev_v1.0.0.18.0.tmp (PID: 3304)
Drops a system driver (possible attempt to evade defenses)
- MSDisplay_MultiDev_v1.0.0.18.0.tmp (PID: 3304)
- drvinst.exe (PID: 968)
- drvinst.exe (PID: 8432)
- drvinst.exe (PID: 9104)
- devcon.exe (PID: 8880)
- devcon.exe (PID: 7660)
There is functionality for taking screenshot (YARA)
- AcroCEF.exe (PID: 1240)
Process drops legitimate windows executable
- MSDisplay_MultiDev_v1.0.0.18.0.tmp (PID: 3304)
Executes as Windows Service
- WUDFHost.exe (PID: 5232)
- WUDFHost.exe (PID: 8856)
- WUDFHost.exe (PID: 240)
- WUDFHost.exe (PID: 7364)
- WUDFHost.exe (PID: 8888)
- WUDFHost.exe (PID: 6940)
- WUDFHost.exe (PID: 684)
- WUDFHost.exe (PID: 9212)
- WUDFHost.exe (PID: 7436)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4356)
INFO
Application launched itself
- Acrobat.exe (PID: 5124)
- AcroCEF.exe (PID: 6456)
- msedge.exe (PID: 8136)
Checks supported languages
- identity_helper.exe (PID: 7672)
An automatically generated document
- Acrobat.exe (PID: 5124)
Reads the computer name
- identity_helper.exe (PID: 7672)
Reads Environment values
- identity_helper.exe (PID: 7672)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 8740)
- OpenWith.exe (PID: 5796)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 8740)
Reads the software policy settings
- slui.exe (PID: 644)
The sample compiled with english language support
- MSDisplay_MultiDev_v1.0.0.18.0.tmp (PID: 3304)
- MSDisplay_MultiDev_v1.0.0.18.0.exe (PID: 3968)
- MSDisplay_MultiDev_v1.0.0.18.0.exe (PID: 7176)
- drvinst.exe (PID: 968)
- devcon.exe (PID: 7660)
- devcon.exe (PID: 8880)
- drvinst.exe (PID: 8432)
- drvinst.exe (PID: 9104)
The sample compiled with chinese language support
- MSDisplay_MultiDev_v1.0.0.18.0.tmp (PID: 3304)
- msedge.exe (PID: 7668)
- msedge.exe (PID: 8136)
Executable content was dropped or overwritten
- msedge.exe (PID: 8136)
- msedge.exe (PID: 7668)
Manual execution by a user
- WinUsbDisplay.exe (PID: 6512)
- mspaint.exe (PID: 6420)
- WINWORD.EXE (PID: 3188)
- mspaint.exe (PID: 6688)
- mspaint.exe (PID: 6712)
- WINWORD.EXE (PID: 4508)
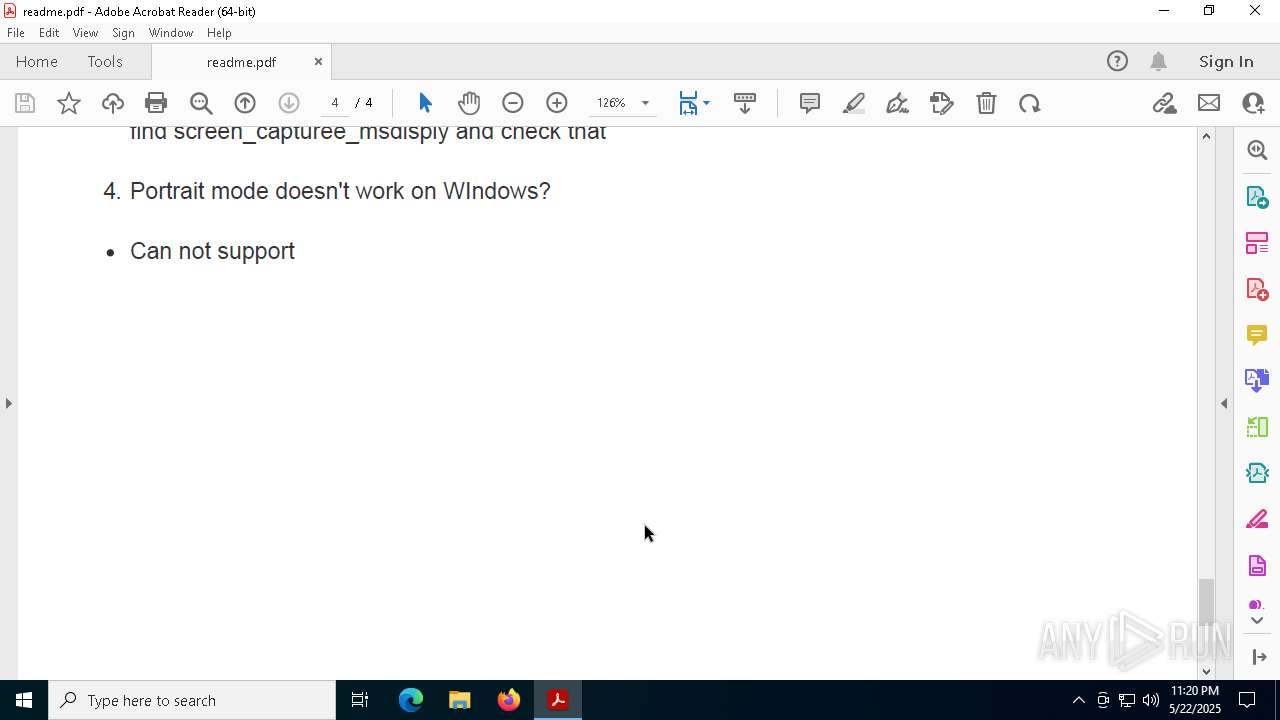
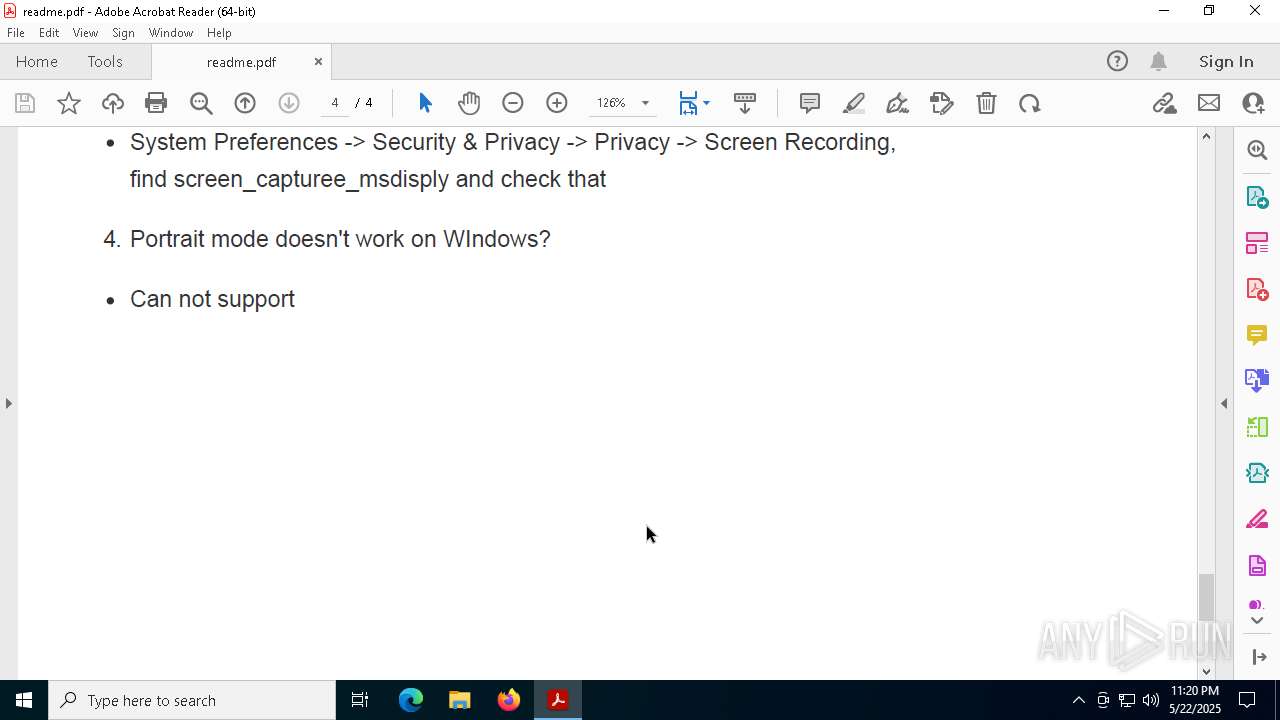
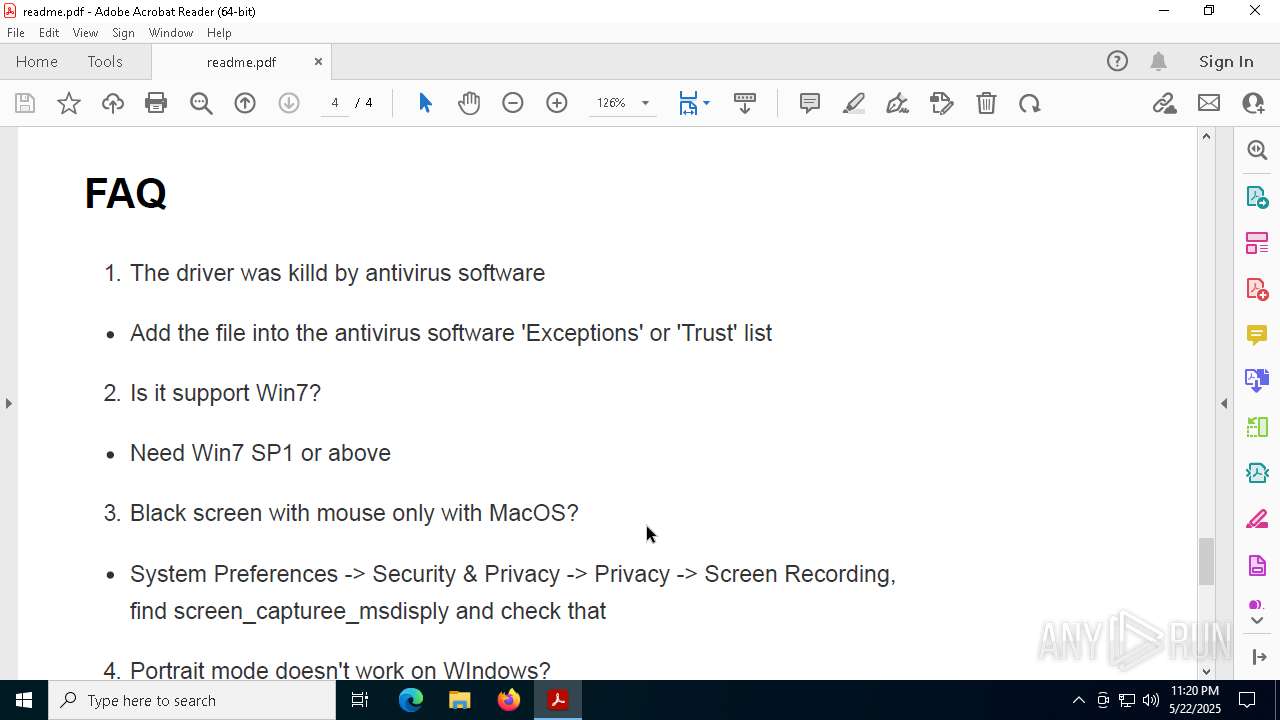
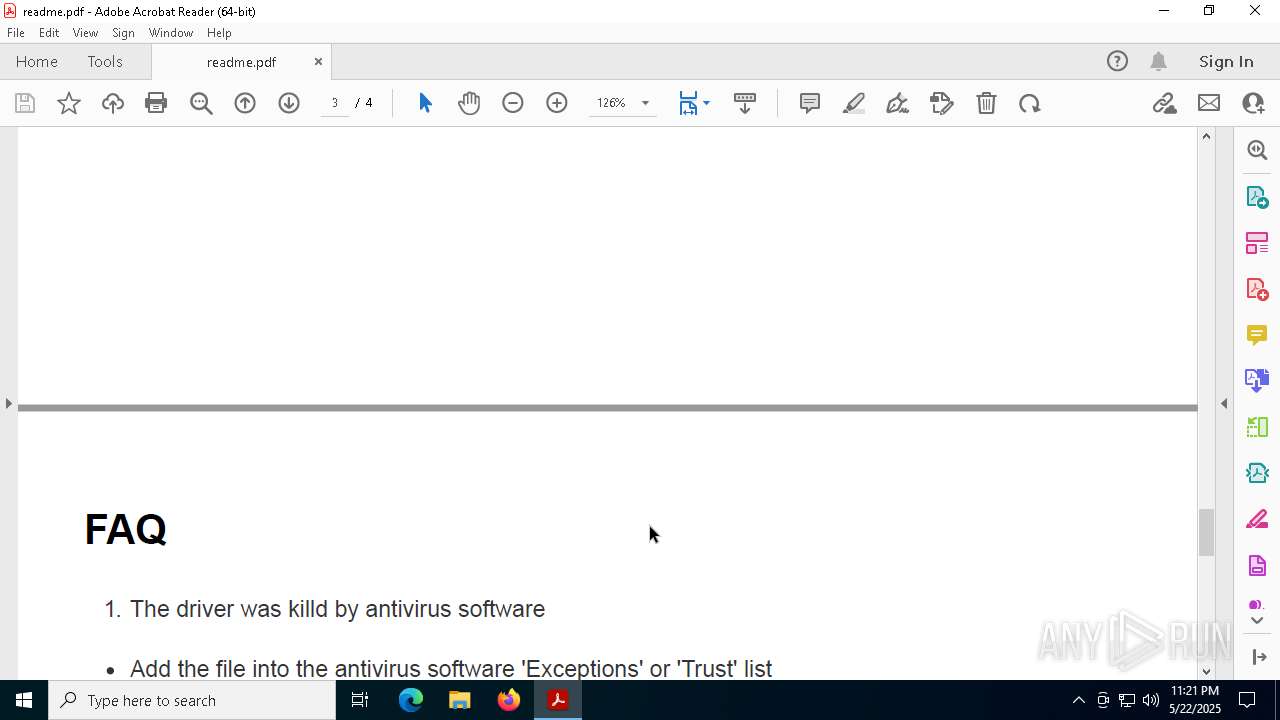
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.4 |
|---|---|
| Linearized: | No |
| PageCount: | 4 |
| TaggedPDF: | Yes |
| Creator: | Chromium |
| Producer: | Skia/PDF m97 |
| CreateDate: | 2022:01:12 14:31:32+00:00 |
| ModifyDate: | 2022:01:12 14:31:32+00:00 |
Total processes
390
Monitored processes
105
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Windows\System32\WUDFHost.exe" -HostGUID:{193a1820-d9ac-4997-8c55-be817523f6aa} -IoEventPortName:\UMDFCommunicationPorts\WUDF\HostProcess-36e0d1fb-cd60-4b52-83b9-a0281c4124b0 -SystemEventPortName:\UMDFCommunicationPorts\WUDF\HostProcess-001c22f3-7b83-4760-bd16-45b7e5e26334 -IoCancelEventPortName:\UMDFCommunicationPorts\WUDF\HostProcess-04b082da-640c-47d0-be74-82130fb940ad -NonStateChangingEventPortName:\UMDFCommunicationPorts\WUDF\HostProcess-f4cb1807-4c97-43e8-bfbf-4b39bc33ed81 -LifetimeId:017a0c24-d896-4a0f-bfe7-1e1bf49bf015 -DeviceGroupId:IddSampleDriverGroup2 -HostArg:0 | C:\Windows\System32\WUDFHost.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Driver Foundation - User-mode Driver Framework Host Process Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 444 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4124 --field-trial-handle=2412,i,627414890588583453,12990780809952049569,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 644 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | "C:\Windows\System32\WUDFHost.exe" -HostGUID:{193a1820-d9ac-4997-8c55-be817523f6aa} -IoEventPortName:\UMDFCommunicationPorts\WUDF\HostProcess-db00139e-6fe7-4062-ad36-99aa0838f793 -SystemEventPortName:\UMDFCommunicationPorts\WUDF\HostProcess-6dc52e10-8d9e-4a86-9006-bfdbf2e8f968 -IoCancelEventPortName:\UMDFCommunicationPorts\WUDF\HostProcess-ac39b6b5-deab-4833-b702-bfa33e20ac41 -NonStateChangingEventPortName:\UMDFCommunicationPorts\WUDF\HostProcess-19938963-337c-472b-aa92-43aa1285e517 -LifetimeId:ce1f7f45-5de2-489d-bbac-bbe4fdcafe12 -DeviceGroupId:IddSampleDriverGroup -HostArg:0 | C:\Windows\System32\WUDFHost.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Driver Foundation - User-mode Driver Framework Host Process Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4972 --field-trial-handle=2412,i,627414890588583453,12990780809952049569,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 776 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{e10cdd4f-312f-f247-8d4e-35a47b7e4c6e}\indirectdisplaydriver2.inf" "9" "47de959af" "000000000000018C" "WinSta0\Default" "0000000000000200" "208" "c:\program files\ms usb display\idd\indirectdisplaydriver2" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4896 --field-trial-handle=2412,i,627414890588583453,12990780809952049569,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 968 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{5f653dff-1b65-4142-9005-74c5f82c193a}\MSUSBDisplay.inf" "9" "410771dbb" "00000000000001CC" "WinSta0\Default" "00000000000001DC" "208" "C:\Program Files\MS USB Display\lib_usb" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 972 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "6825392D-F27A-466C-B5BF-7E0774AB8051" "2A5388EB-5264-4E4C-BF91-3758E938384D" "3188" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 1184 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_xpay_wallet.mojom.EdgeXPayWalletService --lang=en-US --service-sandbox-type=utility --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4584 --field-trial-handle=2412,i,627414890588583453,12990780809952049569,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
87 324
Read events
85 685
Write events
1 494
Delete events
145
Modification events
| (PID) Process: | (5124) Acrobat.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Mappings\S-1-15-2-2034283098-2252572593-1072577386-2659511007-3245387615-27016815-3920691934 |
| Operation: | write | Name: | DisplayName |
Value: Adobe Acrobat Reader Protected Mode | |||
| (PID) Process: | (6192) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (6192) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVEntitlement |
| Operation: | write | Name: | sProductGUID |
Value: 4143524F4241545F475549445F4E474C5F44554D4D5900 | |||
| (PID) Process: | (6192) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVEntitlement |
| Operation: | write | Name: | sProductGUID |
Value: 4143524F5F5245534944554500 | |||
| (PID) Process: | (6192) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVEntitlement |
| Operation: | write | Name: | bSynchronizeOPL |
Value: 0 | |||
| (PID) Process: | (6192) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | uLastAppLaunchTimeStamp |
Value: | |||
| (PID) Process: | (6192) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | iNumAcrobatLaunches |
Value: 7 | |||
| (PID) Process: | (6192) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\ToolsSearch |
| Operation: | write | Name: | iSearchHintIndex |
Value: 3 | |||
| (PID) Process: | (5124) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AdobeViewer |
| Operation: | delete value | Name: | ProductInfoCache |
Value: | |||
| (PID) Process: | (6192) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AdobeViewer |
| Operation: | delete value | Name: | ProductInfoCache |
Value: | |||
Executable files
147
Suspicious files
651
Text files
77
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6192 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\SOPHIA.json | binary | |
MD5:837C1211E392A24D64C670DC10E8DA1B | SHA256:8013AC030684B86D754BBFBAB8A9CEC20CAA4DD9C03022715FF353DC10E14031 | |||
| 6456 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\LOG.old | text | |
MD5:2EF1F7C0782D1A46974286420D24F629 | SHA256:D3A9BB7E09E1F4B0C41FF7808E930DDACF5DB3BACD98ECCF5BC7DB4863D1FCF5 | |||
| 6192 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SharedDataEvents | binary | |
MD5:537FC562FFC865581B6CF13A1DA8163C | SHA256:905646CDADF685F0A9F8DE52475008DA0F1F328E5DC7685725034AD8AD020BDD | |||
| 6192 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\TESTING | binary | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 6192 | Acrobat.exe | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\NGL\NGLClient_AcrobatReader123.1.20093.6 2025-05-22 23-20-38-396.log | text | |
MD5:460C6041966002D8384A18C895A65EB0 | SHA256:C83EC6E8FB3EC62481289C033238C1D9B08DB8076EAAD304099FD7A7F594F1B9 | |||
| 6192 | Acrobat.exe | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\acroNGLLog.txt | text | |
MD5:648E8FE57425A2890B09C4C968BE66A2 | SHA256:6F6E4264E00CAC3EF9FDB720F6E2687801AEA33B9E5A9BEC986542260DB32904 | |||
| 6456 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Session Storage\LOG.old~RF11ec32.TMP | text | |
MD5:7383516745DEC1E86152192435F92D1F | SHA256:E22D34BBD915EEB277D4F4138D176EACE5577CF035EF7C2C80A4BC4D9B6C0E1D | |||
| 6456 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\72d9f526d2e2e7c8_0 | binary | |
MD5:A43ED83779FBE87245012026034ED4BF | SHA256:E009921DEF2DDAF233C6C1F5DD440F8B4288C6AF84C3EA6E18681FB788300010 | |||
| 6192 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SharedDataEvents-journal | binary | |
MD5:29C0A1299206034539A249EFA300A324 | SHA256:9A8D2417464A9A418959AD171037360197E610C6AE1419B5143583357BE9A631 | |||
| 6456 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Session Storage\LOG.old | text | |
MD5:EB1590F2607E1CE46DBF6A521F772EA0 | SHA256:4355D9A8A115BA4E41178B456A8A5578846EB1F7EC9509249C2405F758F31731 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
163
DNS requests
108
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5124 | Acrobat.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | — | — | whitelisted |
6228 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6228 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7720 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/241074c3-f448-482a-8c90-855c388ea76a?P1=1748180557&P2=404&P3=2&P4=SgtWXwZSGoqku6szYuuTLrBfM%2fb26rKwG6aHe4wFsFYY4T5qkVEpw7eOzBpwVSykm2slRQWY9UFVRbHJGik2zA%3d%3d | unknown | — | — | whitelisted |
7720 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/241074c3-f448-482a-8c90-855c388ea76a?P1=1748180557&P2=404&P3=2&P4=SgtWXwZSGoqku6szYuuTLrBfM%2fb26rKwG6aHe4wFsFYY4T5qkVEpw7eOzBpwVSykm2slRQWY9UFVRbHJGik2zA%3d%3d | unknown | — | — | whitelisted |
7720 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/241074c3-f448-482a-8c90-855c388ea76a?P1=1748180557&P2=404&P3=2&P4=SgtWXwZSGoqku6szYuuTLrBfM%2fb26rKwG6aHe4wFsFYY4T5qkVEpw7eOzBpwVSykm2slRQWY9UFVRbHJGik2zA%3d%3d | unknown | — | — | whitelisted |
7720 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/241074c3-f448-482a-8c90-855c388ea76a?P1=1748180557&P2=404&P3=2&P4=SgtWXwZSGoqku6szYuuTLrBfM%2fb26rKwG6aHe4wFsFYY4T5qkVEpw7eOzBpwVSykm2slRQWY9UFVRbHJGik2zA%3d%3d | unknown | — | — | whitelisted |
7720 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/241074c3-f448-482a-8c90-855c388ea76a?P1=1748180557&P2=404&P3=2&P4=SgtWXwZSGoqku6szYuuTLrBfM%2fb26rKwG6aHe4wFsFYY4T5qkVEpw7eOzBpwVSykm2slRQWY9UFVRbHJGik2zA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
7736 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
8188 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5036 | AcroCEF.exe | 95.100.184.205:443 | geo2.adobe.com | AKAMAI-AS | FR | whitelisted |
5036 | AcroCEF.exe | 107.22.247.231:443 | p13n.adobe.io | AMAZON-AES | US | whitelisted |
5036 | AcroCEF.exe | 23.219.148.205:443 | armmf.adobe.com | AKAMAI-AS | CL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
armmf.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
7668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
7668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
7668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
5800 | svchost.exe | Generic Protocol Command Decode | SURICATA STREAM TIMEWAIT ACK with wrong seq |