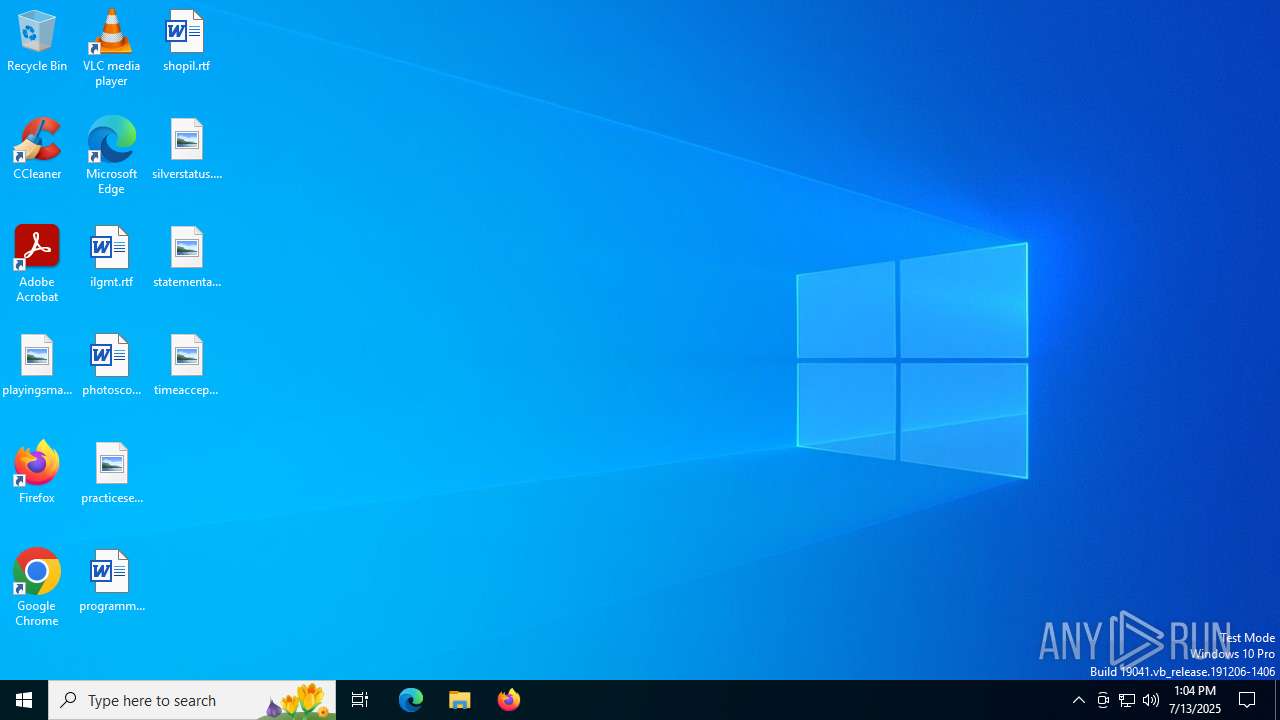
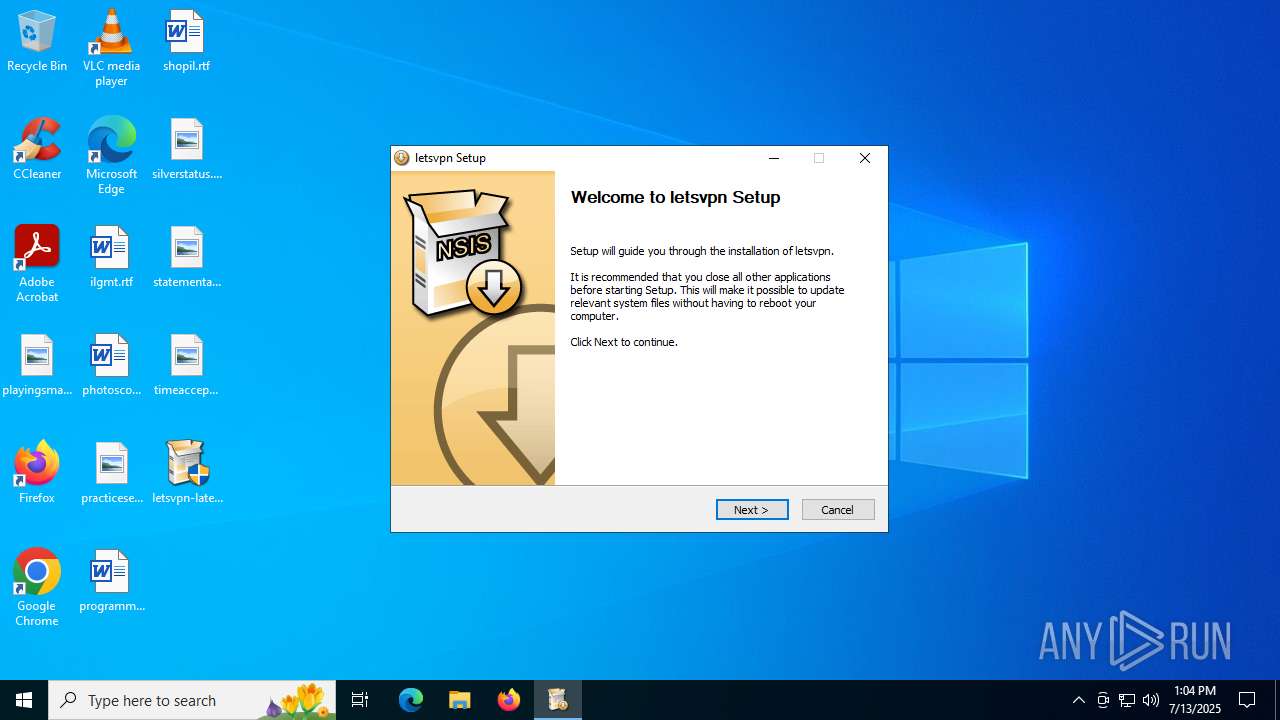
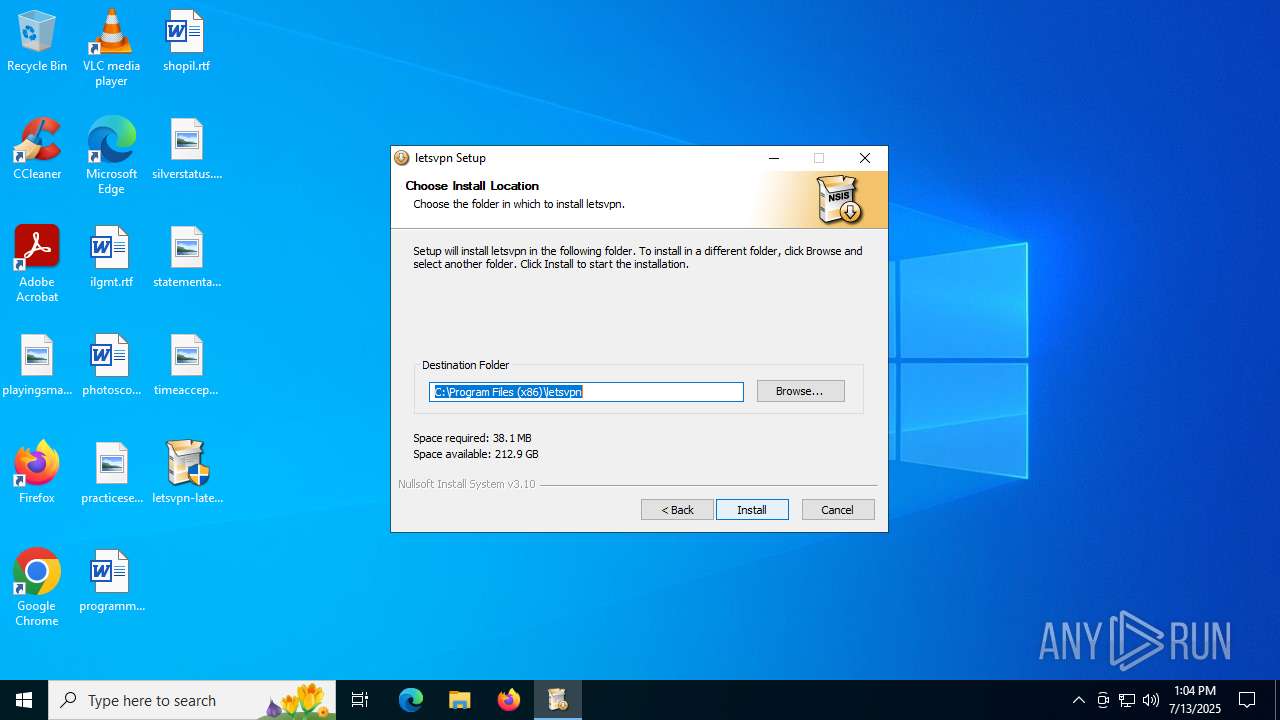
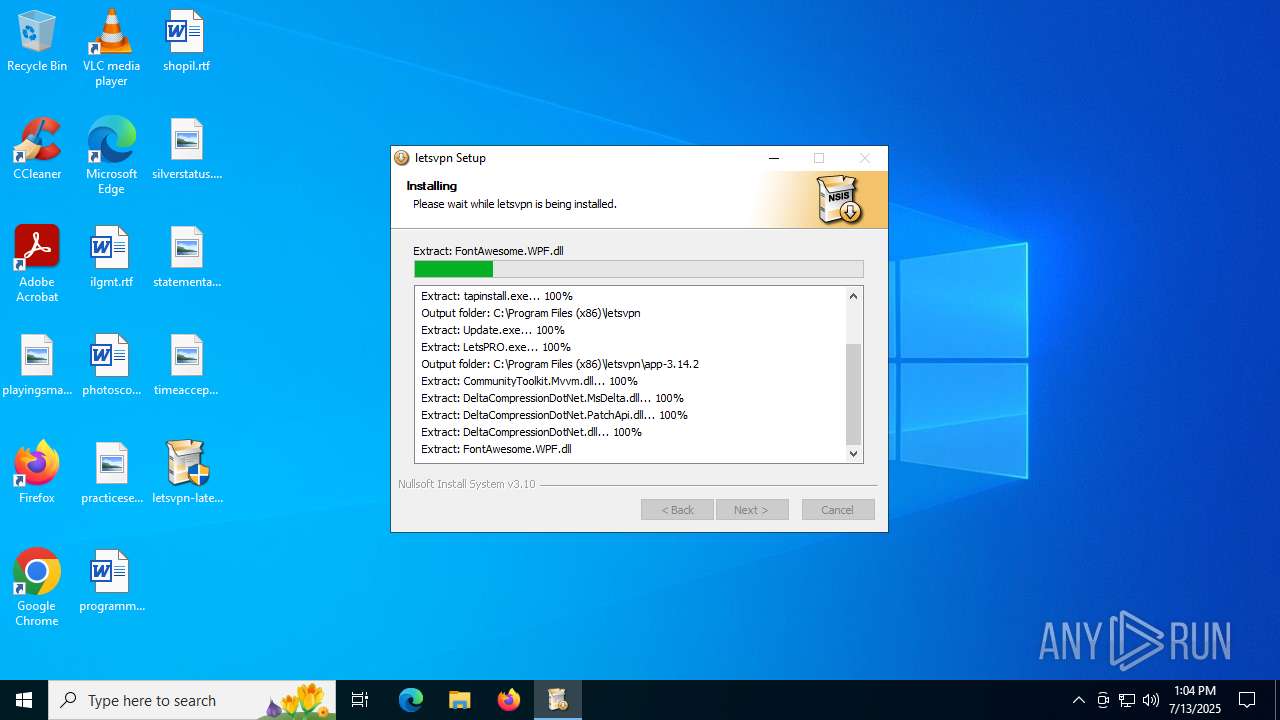
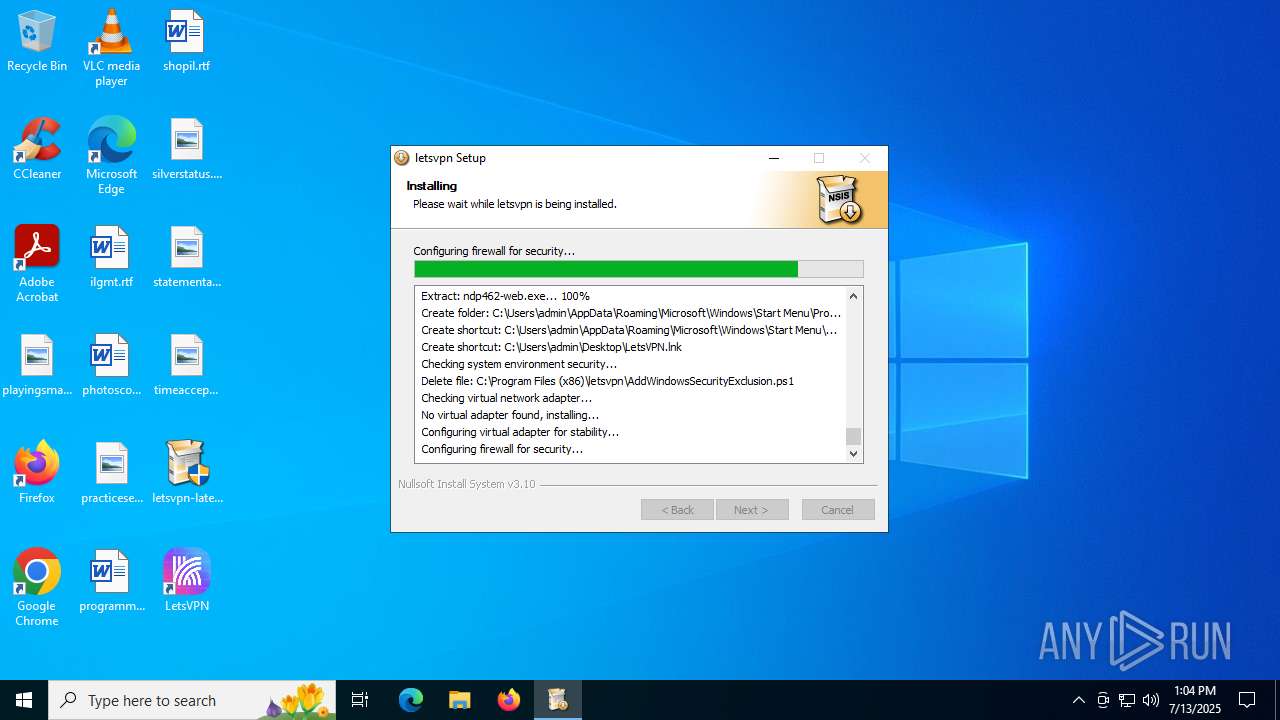
| File name: | letsvpn-latest.exe |
| Full analysis: | https://app.any.run/tasks/54043afe-df4c-4ef1-a26d-d8bcd356cf1c |
| Verdict: | Malicious activity |
| Analysis date: | July 13, 2025, 13:04:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 73E488B8090341EC8ED56A422462CD12 |
| SHA1: | AD6DD720AF8A08A7B76BB11044B442A1FA69F3F2 |
| SHA256: | 3EF70AD5805B82BAAE9AA2ED92C1D2D463B0142166C7B0AC6578D2B8BCAD2D40 |
| SSDEEP: | 98304:cqYWgxgzS6EdT92JQpUSvqMk3Cd5ErqHYfxQr1giOax7qPAk3d3IiCYU2mAG//fI:/lNk+pBnVk7p5zPPsaPNzcIkzaw5 |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 5456)
Changes powershell execution policy (Bypass)
- letsvpn-latest.exe (PID: 3756)
SUSPICIOUS
Executable content was dropped or overwritten
- letsvpn-latest.exe (PID: 3756)
- tapinstall.exe (PID: 2044)
- drvinst.exe (PID: 3860)
- drvinst.exe (PID: 4804)
The process creates files with name similar to system file names
- letsvpn-latest.exe (PID: 3756)
Malware-specific behavior (creating "System.dll" in Temp)
- letsvpn-latest.exe (PID: 3756)
Drops a system driver (possible attempt to evade defenses)
- letsvpn-latest.exe (PID: 3756)
- tapinstall.exe (PID: 2044)
- drvinst.exe (PID: 3860)
- drvinst.exe (PID: 4804)
Process drops legitimate windows executable
- letsvpn-latest.exe (PID: 3756)
There is functionality for taking screenshot (YARA)
- letsvpn-latest.exe (PID: 3756)
Starts POWERSHELL.EXE for commands execution
- letsvpn-latest.exe (PID: 3756)
The process executes Powershell scripts
- letsvpn-latest.exe (PID: 3756)
Reads security settings of Internet Explorer
- tapinstall.exe (PID: 2044)
Creates files in the driver directory
- drvinst.exe (PID: 3860)
- drvinst.exe (PID: 4804)
Starts CMD.EXE for commands execution
- letsvpn-latest.exe (PID: 3756)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 4084)
- cmd.exe (PID: 4216)
- cmd.exe (PID: 2668)
- cmd.exe (PID: 1828)
- cmd.exe (PID: 6016)
Creates a software uninstall entry
- letsvpn-latest.exe (PID: 3756)
Creates or modifies Windows services
- drvinst.exe (PID: 4804)
INFO
The sample compiled with english language support
- letsvpn-latest.exe (PID: 3756)
- tapinstall.exe (PID: 2044)
- drvinst.exe (PID: 3860)
- drvinst.exe (PID: 4804)
Checks supported languages
- letsvpn-latest.exe (PID: 3756)
- tapinstall.exe (PID: 2044)
- tapinstall.exe (PID: 1728)
- drvinst.exe (PID: 3860)
- drvinst.exe (PID: 4804)
- tapinstall.exe (PID: 4132)
- LetsPRO.exe (PID: 3740)
- LetsPRO.exe (PID: 2072)
Reads the computer name
- letsvpn-latest.exe (PID: 3756)
- tapinstall.exe (PID: 2044)
- drvinst.exe (PID: 3860)
- drvinst.exe (PID: 4804)
- LetsPRO.exe (PID: 2072)
Create files in a temporary directory
- letsvpn-latest.exe (PID: 3756)
- tapinstall.exe (PID: 2044)
Creates files in the program directory
- letsvpn-latest.exe (PID: 3756)
- LetsPRO.exe (PID: 2072)
Creates files or folders in the user directory
- letsvpn-latest.exe (PID: 3756)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5456)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5456)
Reads the software policy settings
- tapinstall.exe (PID: 2044)
- drvinst.exe (PID: 3860)
- slui.exe (PID: 592)
Reads the machine GUID from the registry
- tapinstall.exe (PID: 2044)
- drvinst.exe (PID: 3860)
- LetsPRO.exe (PID: 2072)
Checks proxy server information
- slui.exe (PID: 592)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:30 16:55:15+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 139776 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x351c |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.14.2.0 |
| ProductVersionNumber: | 3.14.2.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Letsgo Network Incorporated |
| FileDescription: | LetsVPN Setup EXE |
| FileVersion: | 3.14.2.0 |
| LegalCopyright: | Copyright (c) 2024 |
| ProductName: | LetsVPN |
| ProductVersion: | 3.14.2.0 |
Total processes
169
Monitored processes
30
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 432 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 592 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 620 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1336 | netsh advfirewall firewall Delete rule name=LetsPRO | C:\Windows\SysWOW64\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1728 | "C:\Program Files (x86)\letsvpn\driver\tapinstall.exe" findall tap0901 | C:\Program Files (x86)\letsvpn\driver\tapinstall.exe | — | letsvpn-latest.exe | |||||||||||
User: admin Company: Windows (R) Win 7 DDK provider Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 6.1.7600.16385 built by: WinDDK Modules
| |||||||||||||||
| 1828 | cmd /c netsh advfirewall firewall Delete rule name=LetsPRO | C:\Windows\SysWOW64\cmd.exe | — | letsvpn-latest.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2044 | "C:\Users\admin\Desktop\letsvpn-latest.exe" | C:\Users\admin\Desktop\letsvpn-latest.exe | — | explorer.exe | |||||||||||
User: admin Company: Letsgo Network Incorporated Integrity Level: MEDIUM Description: LetsVPN Setup EXE Exit code: 3221226540 Version: 3.14.2.0 Modules
| |||||||||||||||
| 2044 | "C:\Program Files (x86)\letsvpn\driver\tapinstall.exe" install "C:\Program Files (x86)\letsvpn\driver\OemVista.inf" tap0901 | C:\Program Files (x86)\letsvpn\driver\tapinstall.exe | letsvpn-latest.exe | ||||||||||||
User: admin Company: Windows (R) Win 7 DDK provider Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 6.1.7600.16385 built by: WinDDK Modules
| |||||||||||||||
| 2072 | "C:\Program Files (x86)\letsvpn\app-3.14.2\LetsPRO.exe" checkNetFramework | C:\Program Files (x86)\letsvpn\app-3.14.2\LetsPRO.exe | — | LetsPRO.exe | |||||||||||
User: admin Integrity Level: HIGH Description: LetsVPN Exit code: 0 Version: 3.14.2 Modules
| |||||||||||||||
| 2668 | cmd /c netsh advfirewall firewall Delete rule name=LetsPRO.exe | C:\Windows\SysWOW64\cmd.exe | — | letsvpn-latest.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 273
Read events
17 209
Write events
57
Delete events
7
Modification events
| (PID) Process: | (3756) letsvpn-latest.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\lets |
| Operation: | write | Name: | InstallTimeStamp |
Value: 20250713130440.858 | |||
| (PID) Process: | (3756) letsvpn-latest.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\lets |
| Operation: | write | Name: | InstallNewVersion |
Value: 3.14.2 | |||
| (PID) Process: | (2044) tapinstall.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\SetupapiLogStatus |
| Operation: | write | Name: | setupapi.dev.log |
Value: 4096 | |||
| (PID) Process: | (4804) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\tap0901 |
| Operation: | write | Name: | Owners |
Value: oem1.inf | |||
| (PID) Process: | (4804) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup\PnpLockdownFiles\%SystemRoot%/System32/drivers/tap0901.sys |
| Operation: | write | Name: | Owners |
Value: oem1.inf | |||
| (PID) Process: | (4804) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_662fd96dfdced4ae\Descriptors\tap0901 |
| Operation: | write | Name: | Configuration |
Value: tap0901.ndi | |||
| (PID) Process: | (4804) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_662fd96dfdced4ae\Descriptors\tap0901 |
| Operation: | write | Name: | Manufacturer |
Value: %provider% | |||
| (PID) Process: | (4804) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_662fd96dfdced4ae\Descriptors\tap0901 |
| Operation: | write | Name: | Description |
Value: %devicedescription% | |||
| (PID) Process: | (4804) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_662fd96dfdced4ae\Configurations\tap0901.ndi |
| Operation: | write | Name: | Service |
Value: tap0901 | |||
| (PID) Process: | (4804) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_662fd96dfdced4ae\Configurations\tap0901.ndi |
| Operation: | write | Name: | ConfigScope |
Value: 5 | |||
Executable files
226
Suspicious files
15
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3756 | letsvpn-latest.exe | C:\Users\admin\AppData\Local\Temp\nse6591.tmp\modern-header.bmp | image | |
MD5:5ACF495828FEAE7F85E006B7774AF497 | SHA256:6CFEBB59F0BA1B9F1E8D7AA6387F223A468EB2FF74A9ED3C3F4BB688C2B6455E | |||
| 3756 | letsvpn-latest.exe | C:\Users\admin\AppData\Local\Temp\nse6591.tmp\System.dll | executable | |
MD5:192639861E3DC2DC5C08BB8F8C7260D5 | SHA256:23D618A0293C78CE00F7C6E6DD8B8923621DA7DD1F63A070163EF4C0EC3033D6 | |||
| 3756 | letsvpn-latest.exe | C:\Users\admin\AppData\Local\Temp\nse6591.tmp\modern-wizard.bmp | image | |
MD5:7F8E1969B0874C8FB9AB44FC36575380 | SHA256:076221B4527FF13C3E1557ABBBD48B0CB8E5F7D724C6B9171C6AADADB80561DD | |||
| 3756 | letsvpn-latest.exe | C:\Program Files (x86)\letsvpn\driver\tap0901.cat | binary | |
MD5:F73AC62E8DF97FAF3FC8D83E7F71BF3F | SHA256:CC74CDB88C198EB00AEF4CAA20BF1FDA9256917713A916E6B94435CD4DCB7F7B | |||
| 3756 | letsvpn-latest.exe | C:\Program Files (x86)\letsvpn\app-3.14.2\Hardcodet.Wpf.TaskbarNotification.dll | executable | |
MD5:F0A5355563F4E251ED26A65862F05A94 | SHA256:5B4BC4F88A323C734F83D3B08FD2145B1D2CCAC554C3AB796FA062CF13A8A5C0 | |||
| 3756 | letsvpn-latest.exe | C:\Program Files (x86)\letsvpn\app-3.14.2\DeltaCompressionDotNet.MsDelta.dll | executable | |
MD5:DB70A0B1DCDBA504E1A0E96DE032C14C | SHA256:82AED3D761C79FEAB0A97D320C2EC29A3060C829B45D7C3C88F3AE60CABA08C5 | |||
| 3756 | letsvpn-latest.exe | C:\Program Files (x86)\letsvpn\app-3.14.2\DeltaCompressionDotNet.PatchApi.dll | executable | |
MD5:7609F3756A786A46E747ED04C1F32205 | SHA256:25AA370DBF3463C2B06D1A371B5E2290F394CDDDA81DC450916299E051E95F66 | |||
| 3756 | letsvpn-latest.exe | C:\Program Files (x86)\letsvpn\app-3.14.2\LetsPRO.exe | executable | |
MD5:7683276A949187A5780980F422AC56EE | SHA256:E59813036981FB64B457D2470AED215FA6673262CF712A1F50D201132CAB266F | |||
| 3756 | letsvpn-latest.exe | C:\Program Files (x86)\letsvpn\driver\tap0901.sys | executable | |
MD5:C10CCDEC5D7AF458E726A51BB3CDC732 | SHA256:589C5667B1602837205DA8EA8E92FE13F8C36048B293DF931C99B39641052253 | |||
| 3756 | letsvpn-latest.exe | C:\Users\admin\AppData\Local\Temp\nse6591.tmp\nsDialogs.dll | executable | |
MD5:B7D61F3F56ABF7B7FF0D4E7DA3AD783D | SHA256:89A82C4849C21DFE765052681E1FAD02D2D7B13C8B5075880C52423DCA72A912 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
39
TCP/UDP connections
56
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7152 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 4.175.87.197:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
2212 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7152 | RUXIMICS.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2212 | SIHClient.exe | GET | 200 | 2.16.241.14:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.32.134:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 20.106.86.13:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.106.86.13:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7152 | RUXIMICS.exe | 20.106.86.13:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
7152 | RUXIMICS.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |