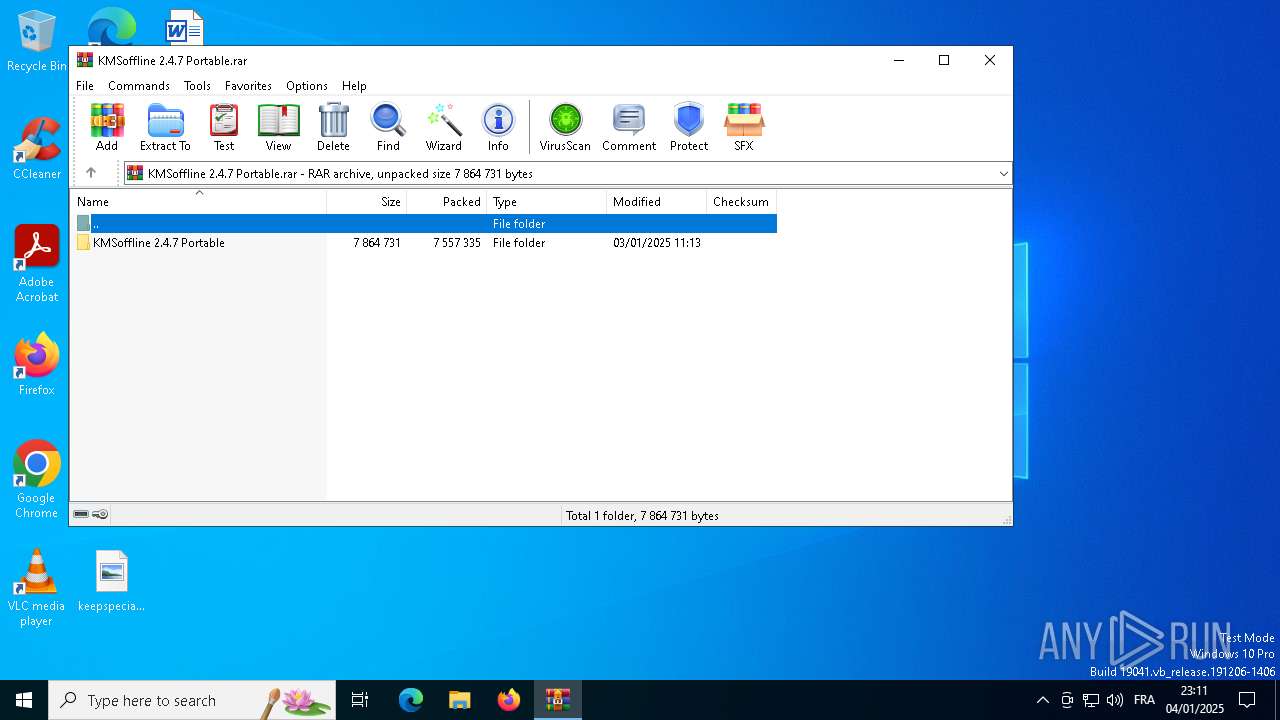
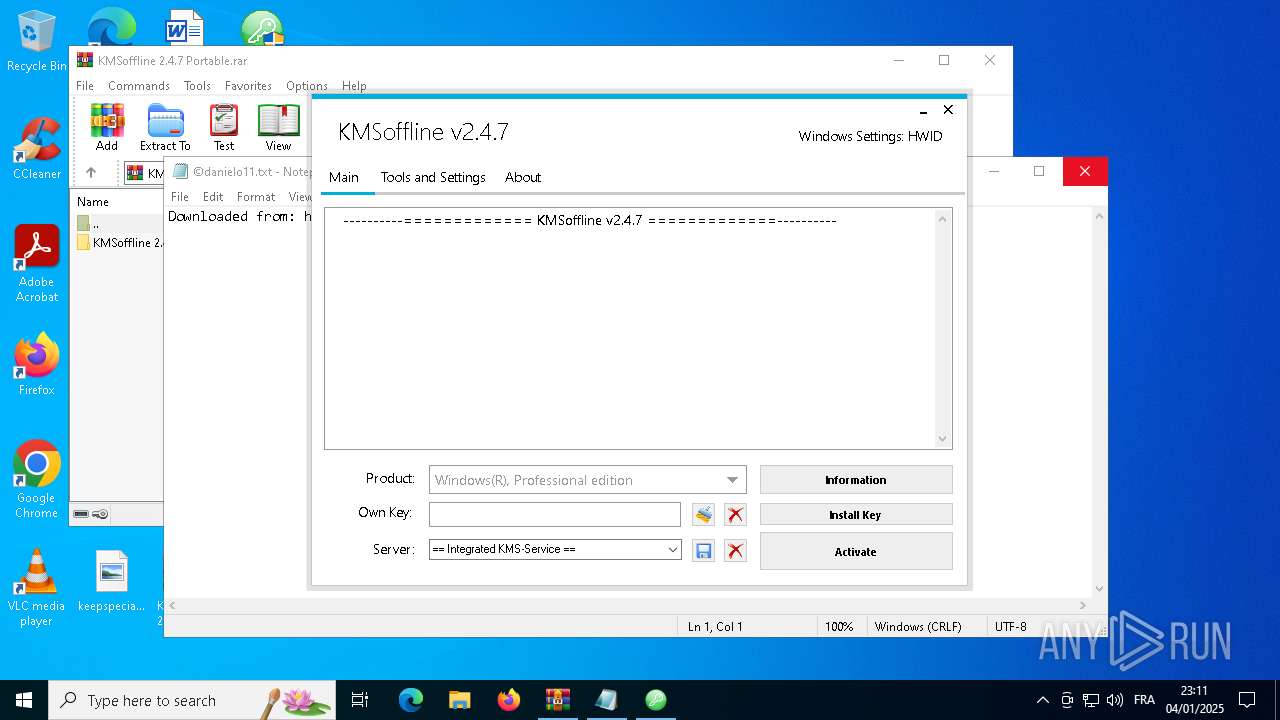
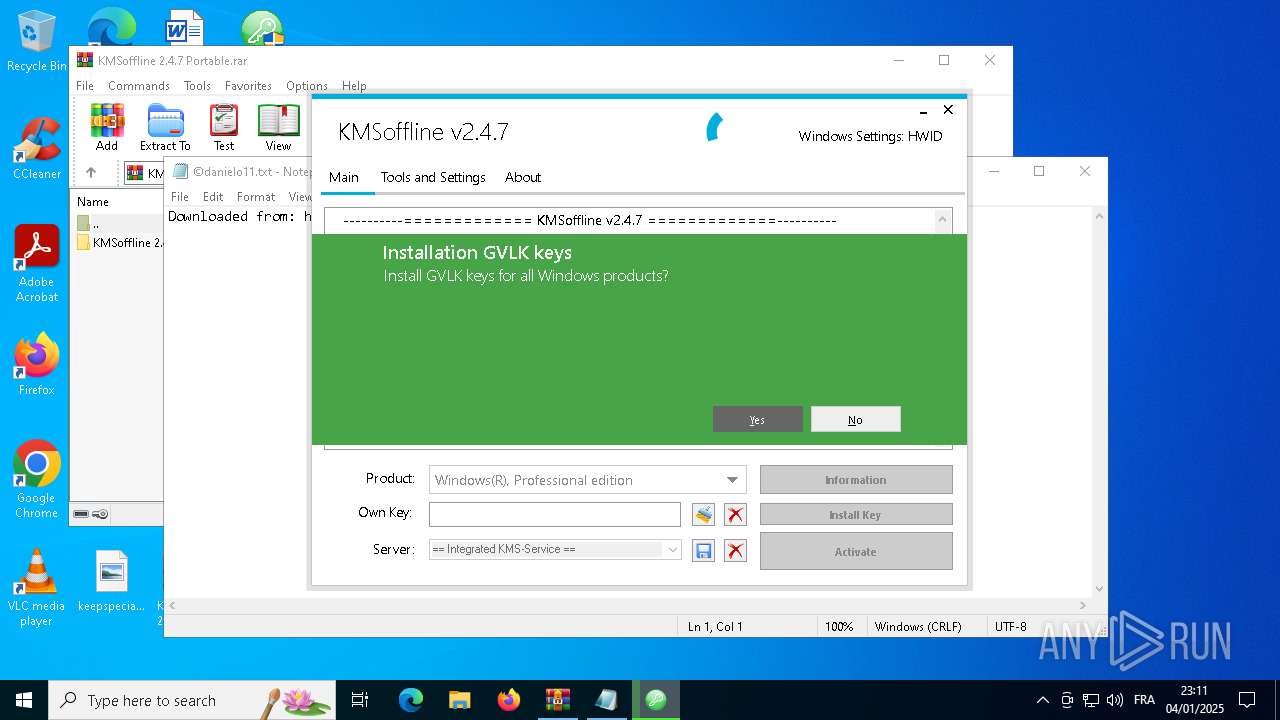
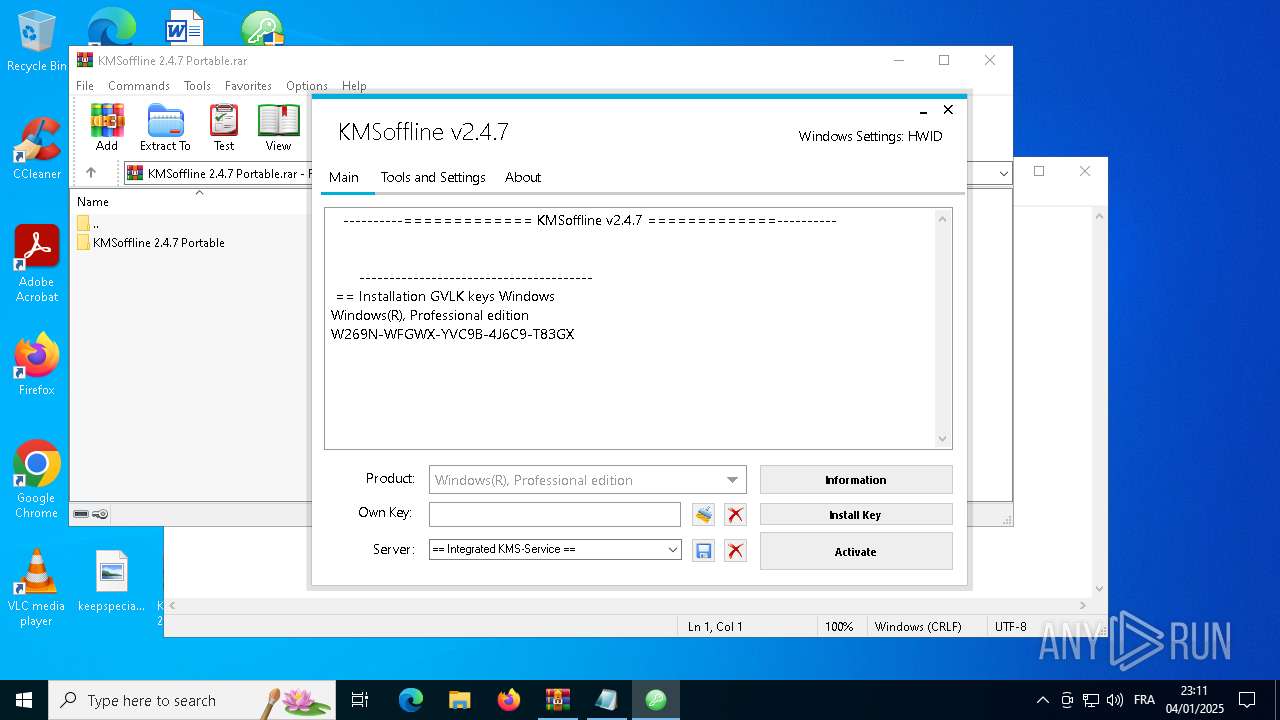
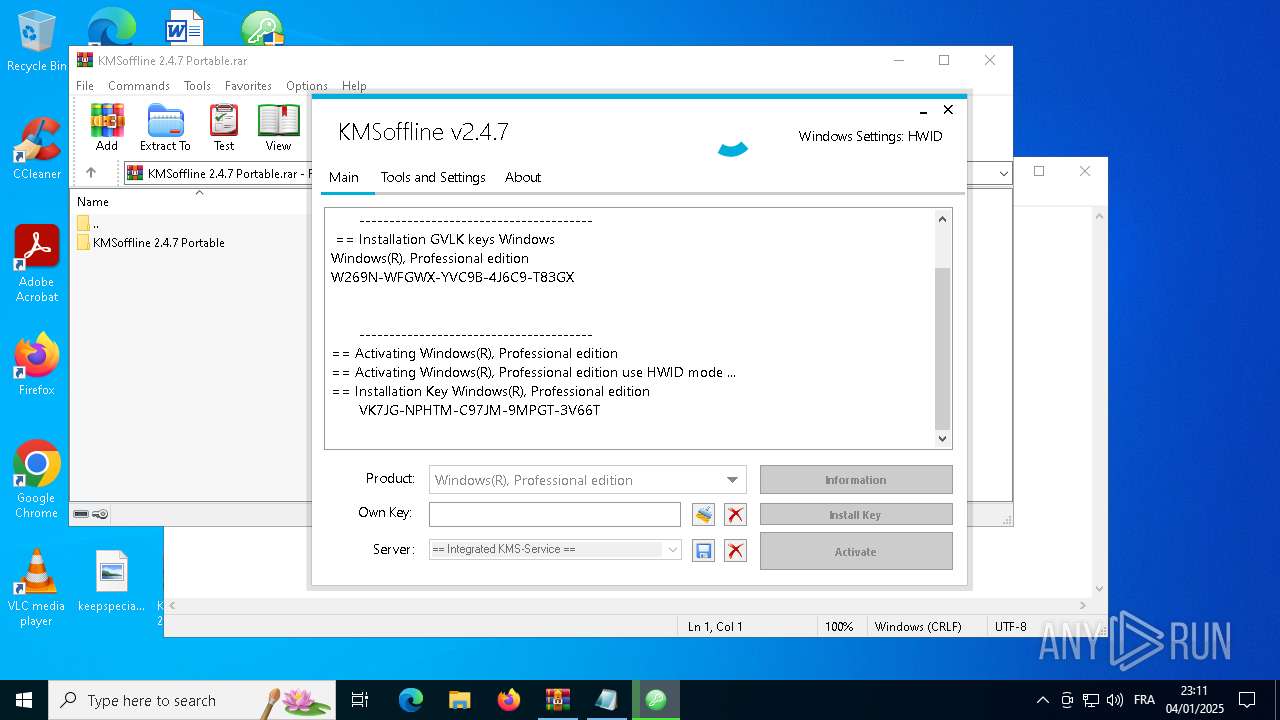
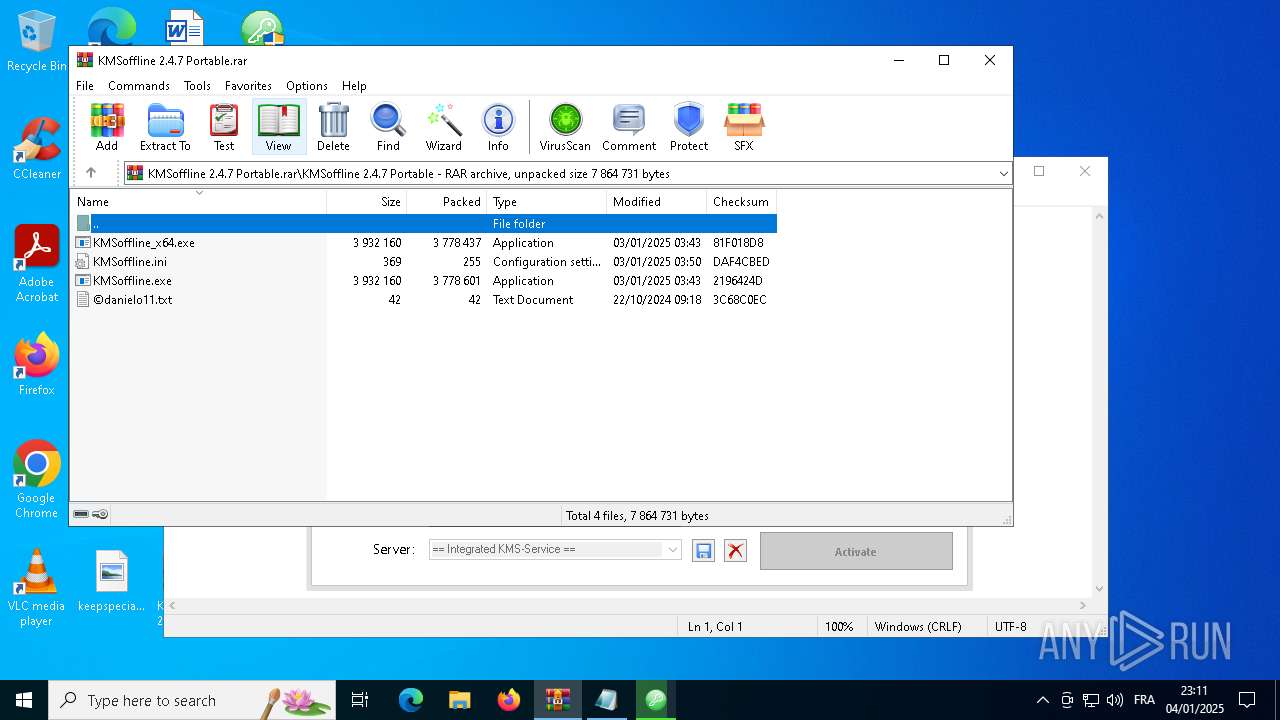
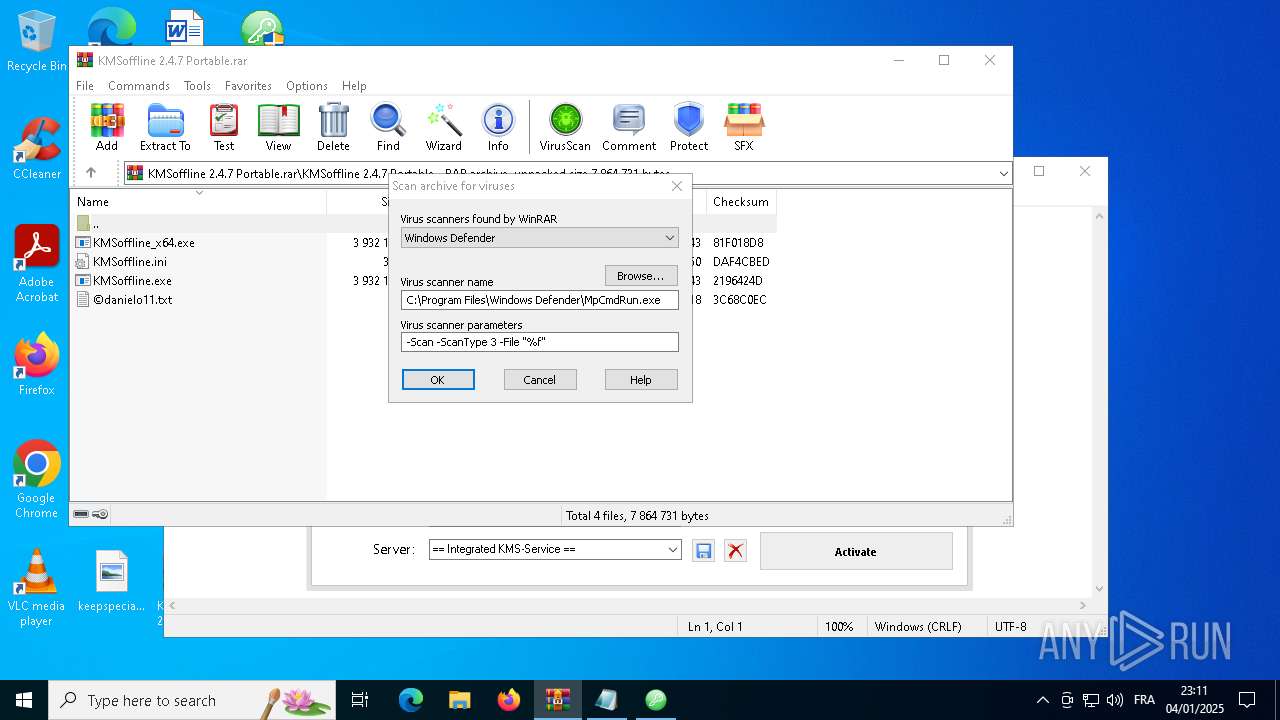
| File name: | KMSoffline 2.4.7 Portable.rar |
| Full analysis: | https://app.any.run/tasks/cae2d83c-4000-416b-ae99-7fca7a807e28 |
| Verdict: | Malicious activity |
| Analysis date: | January 04, 2025, 22:10:42 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 0255A40C6AD242488D66058171BD3B58 |
| SHA1: | D4B66A35C8FA0FF43C402416EC9D4995FB680460 |
| SHA256: | 3EEE7F8F219B75ED89853D873E0BF92B1FF7036DAEB0E2D239E55EC4E26423DA |
| SSDEEP: | 98304:1BggyN4NOwRYVNmqcaYVvgcWXK5ifVRQe7XR43STJqpI3lpun/0oyjVHZvbgT9b6:1bv72SUMVl/FSZVOmB |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4328)
SUSPICIOUS
Reads security settings of Internet Explorer
- KMSoffline.exe (PID: 3296)
- WinRAR.exe (PID: 4328)
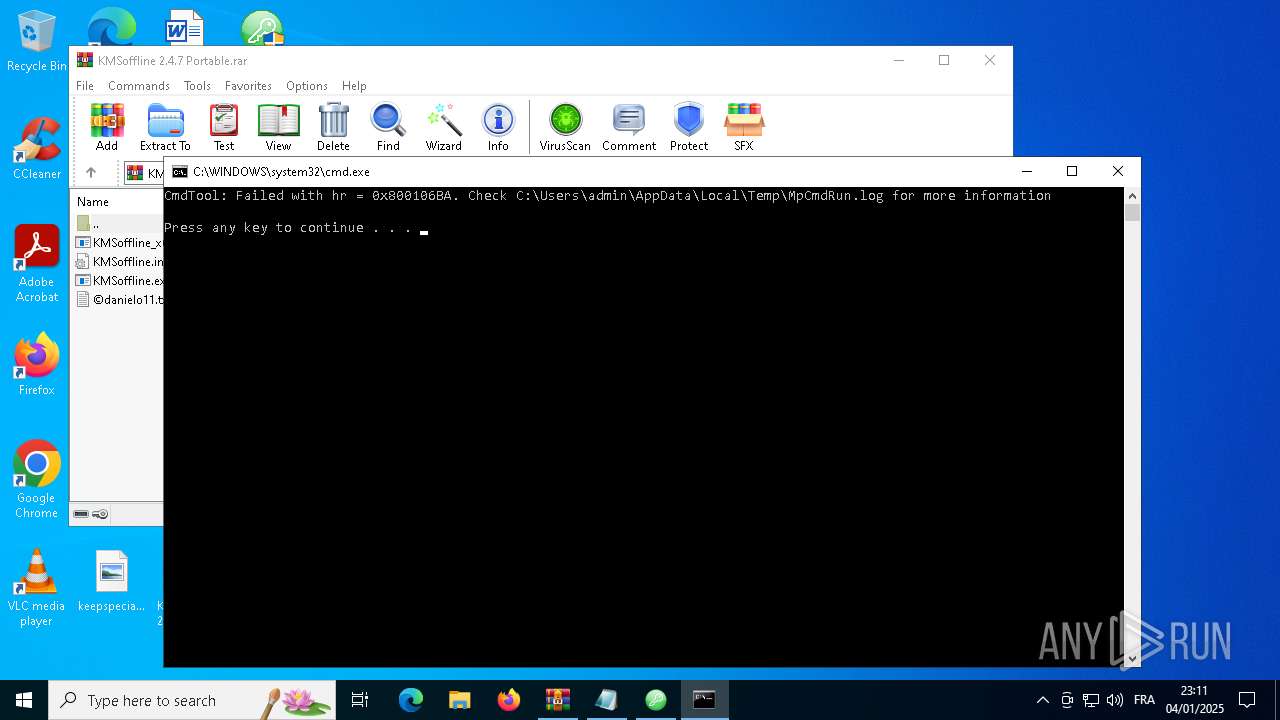
Executing commands from a ".bat" file
- WinRAR.exe (PID: 4328)
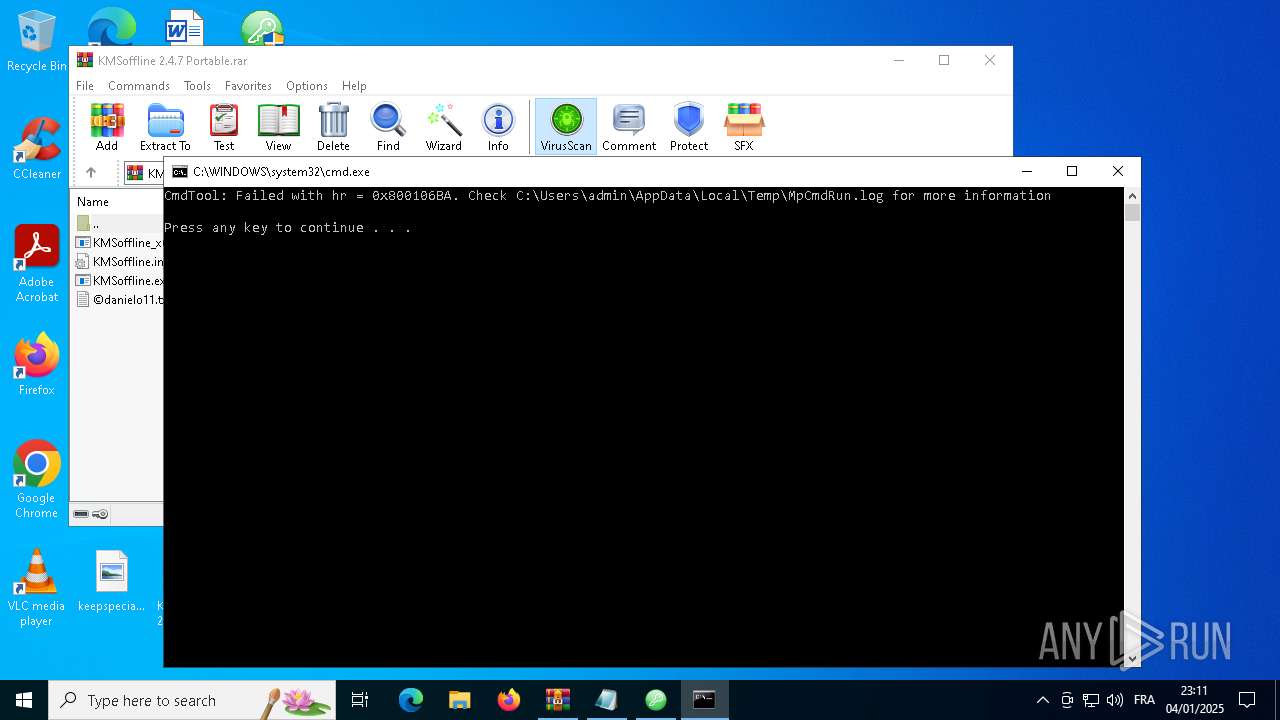
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 4328)
INFO
Manual execution by a user
- KMSoffline.exe (PID: 3296)
- KMSoffline.exe (PID: 2776)
- notepad.exe (PID: 540)
- notepad.exe (PID: 4392)
Checks supported languages
- KMSoffline.exe (PID: 3296)
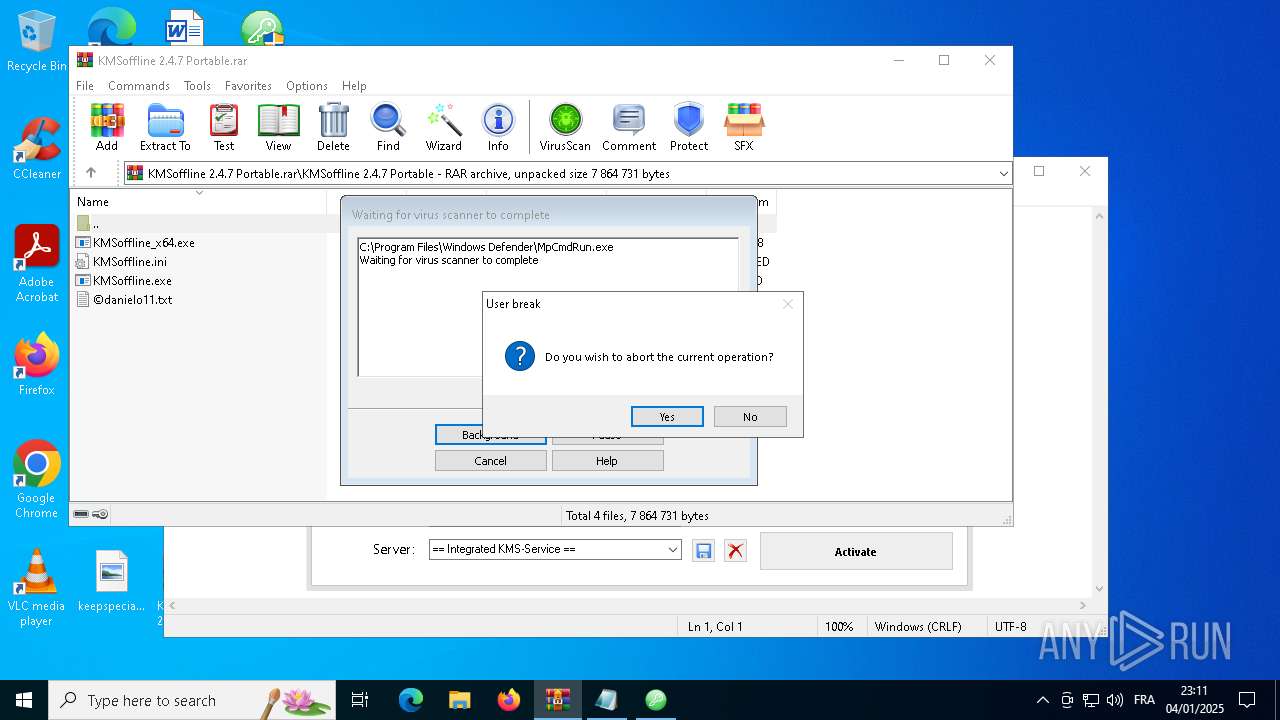
- MpCmdRun.exe (PID: 1536)
Reads the machine GUID from the registry
- KMSoffline.exe (PID: 3296)
The process uses the downloaded file
- WinRAR.exe (PID: 4328)
- KMSoffline.exe (PID: 3296)
Reads security settings of Internet Explorer
- notepad.exe (PID: 4392)
- notepad.exe (PID: 540)
Reads Environment values
- KMSoffline.exe (PID: 3296)
Create files in a temporary directory
- MpCmdRun.exe (PID: 1536)
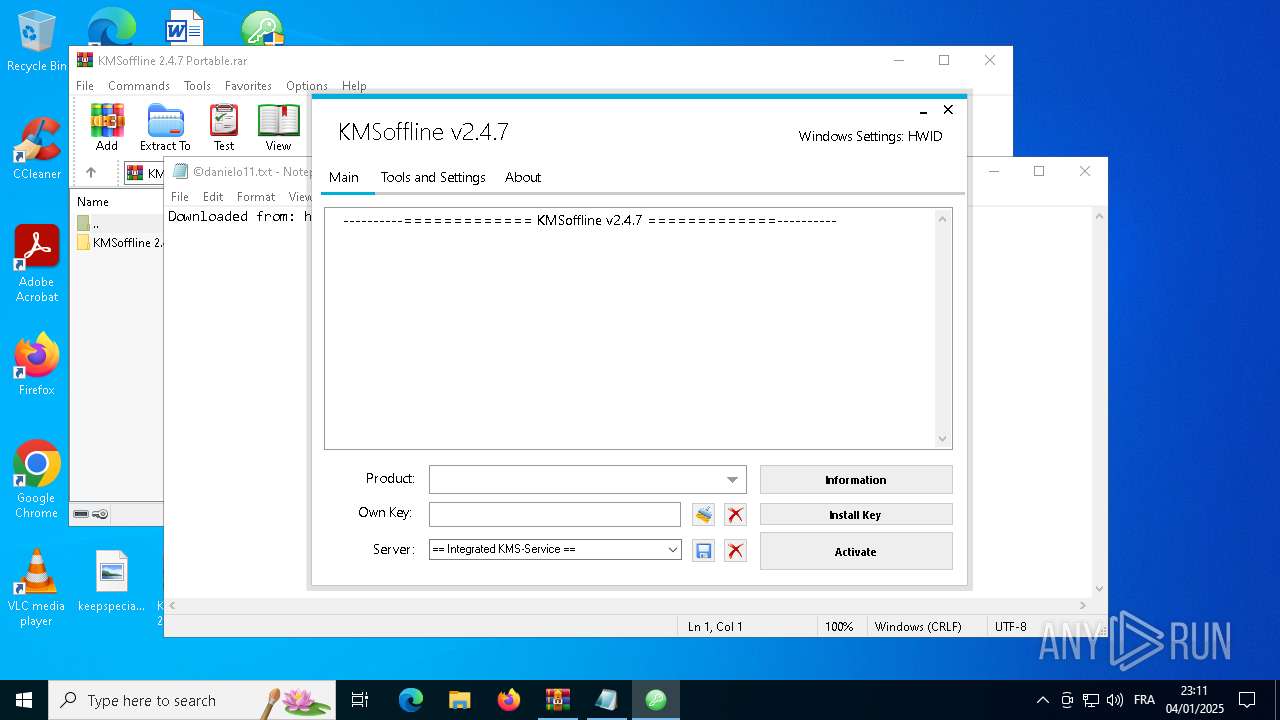
.NET Reactor protector has been detected
- KMSoffline.exe (PID: 3296)
Reads product name
- KMSoffline.exe (PID: 3296)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4328)
Reads the computer name
- MpCmdRun.exe (PID: 1536)
- KMSoffline.exe (PID: 3296)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 3778601 |
| UncompressedSize: | 3932160 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | KMSoffline 2.4.7 Portable/KMSoffline.exe |
Total processes
121
Monitored processes
8
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\KMSoffline.ini | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1536 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR4328.49687" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2680 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR4328.49687\Rar$Scan26932.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2776 | "C:\Users\admin\Desktop\KMSoffline.exe" | C:\Users\admin\Desktop\KMSoffline.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: KMSoffline Exit code: 3221226540 Version: 2.4.7.0 Modules
| |||||||||||||||
| 3296 | "C:\Users\admin\Desktop\KMSoffline.exe" | C:\Users\admin\Desktop\KMSoffline.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: KMSoffline Version: 2.4.7.0 Modules
| |||||||||||||||
| 4328 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\KMSoffline 2.4.7 Portable.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4392 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\©danielo11.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 231
Read events
3 219
Write events
12
Delete events
0
Modification events
| (PID) Process: | (4328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\KMSoffline 2.4.7 Portable.rar | |||
| (PID) Process: | (4328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
| (PID) Process: | (4328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 0 | |||
Executable files
2
Suspicious files
0
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
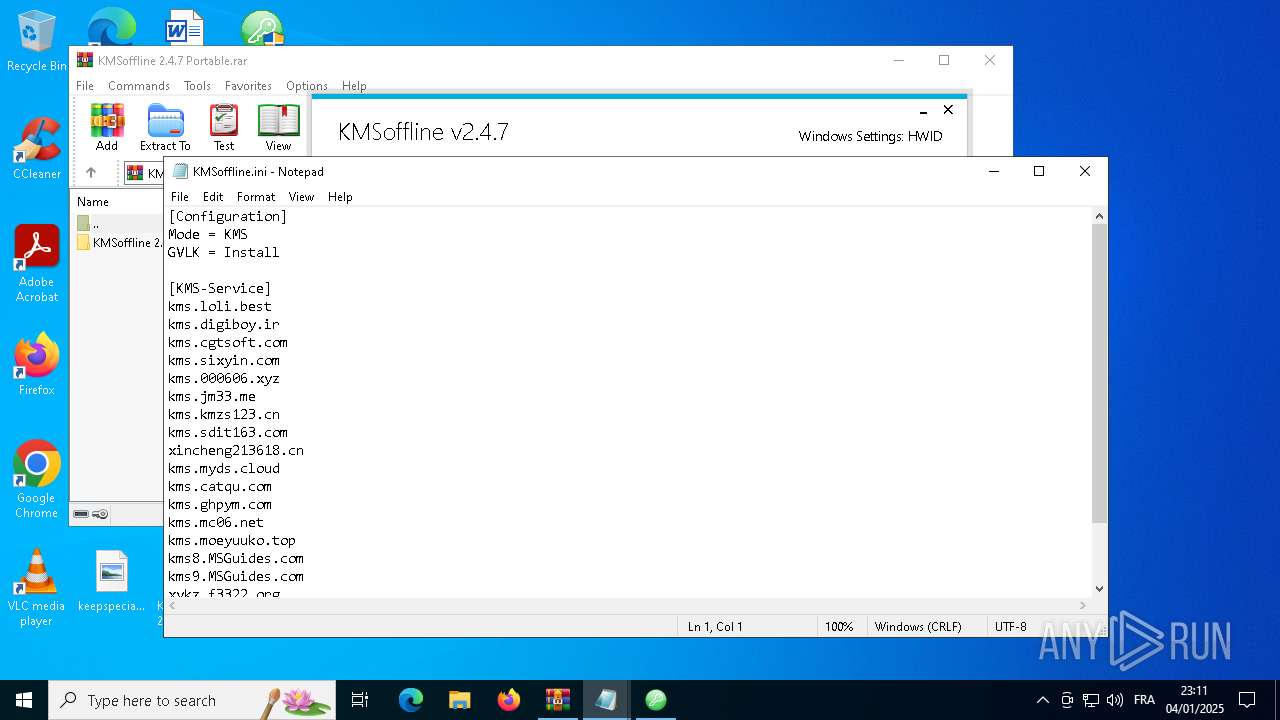
| 3296 | KMSoffline.exe | C:\Users\admin\Desktop\KMSoffline.ini | text | |
MD5:1353E6DBB94A36C74958634258BA1857 | SHA256:78D7BB6CDED6169DBA4350C7450C5DA45BA95C5E4E94E7716B21777EDD62A2A7 | |||
| 4328 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4328.49687\KMSoffline 2.4.7 Portable.rar\KMSoffline 2.4.7 Portable\©danielo11.txt | text | |
MD5:B3ED180EE551D0C10A0B73E565317AB1 | SHA256:5CC3CA457938CEB84245C24F7A555FF60CE0E7AC6A3B2D83526B93FFBC456911 | |||
| 1536 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | text | |
MD5:C3FD420D4194E44A450541D35C78434D | SHA256:058A0D450AC6026C2DCD679FC54A6F735EB4B8AAC0BA80D3532F317266A10277 | |||
| 4328 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4328.49687\KMSoffline 2.4.7 Portable.rar\KMSoffline 2.4.7 Portable\KMSoffline_x64.exe | executable | |
MD5:F2BF56AE769F3BCE08618506646E3E7A | SHA256:CDBF1D999E71A6162ABFEFA69E41C995887EB157BD54ECFD556FDF5D12B68783 | |||
| 4328 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4328.49687\KMSoffline 2.4.7 Portable.rar\KMSoffline 2.4.7 Portable\KMSoffline.exe | executable | |
MD5:314DC7558C2F493F568B63D33EE9080E | SHA256:5AD85A6781A37567898D772427FDBF12DBADA151A222EC58376D060FF4B4FC24 | |||
| 4328 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4328.49687\KMSoffline 2.4.7 Portable.rar\KMSoffline 2.4.7 Portable\KMSoffline.ini | text | |
MD5:26DBDE6B244434F9B3F3780361E2CBEA | SHA256:1B079472DF1154A22A5672117BB16E47015AEB7458C2B27CC9B8B70D10FAC257 | |||
| 4328 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4328.49687\Rar$Scan26932.bat | text | |
MD5:177EF9B29501C697AA77789CADC89E0A | SHA256:EC863E713B286F04EFC1451DBB74A25C4A9D08085A26A173D03A02E4FC77A3EC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
17
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
736 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
736 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
736 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
736 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |