| download: | 0bs4-l1c5x-ypgzxqk |
| Full analysis: | https://app.any.run/tasks/033f2319-063b-4c67-a86c-2443a608fd3b |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | March 14, 2019, 17:19:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
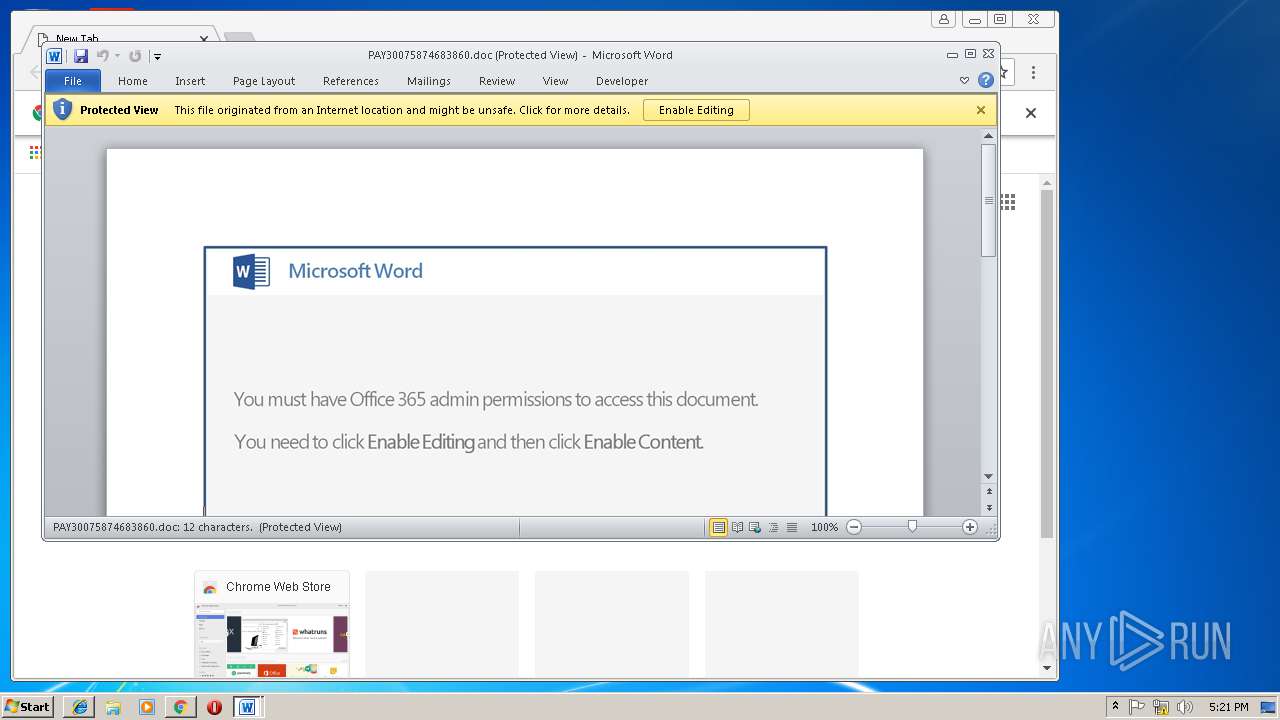
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Thu Mar 14 14:23:00 2019, Last Saved Time/Date: Thu Mar 14 14:23:00 2019, Number of Pages: 1, Number of Words: 2, Number of Characters: 13, Security: 0 |
| MD5: | F3F0C3AB525F0E91098B4CBE6908F31A |
| SHA1: | 41B93E49AAF303FB455E7198A65EBCF3FA65C4F4 |
| SHA256: | 3EB82A4222E85A3BF961D094C19520E14F28142B9B58CC0AD165AAA219C788B8 |
| SSDEEP: | 6144:o77HUUUUUUUUUUUUUUUUUUUT52Vz/8mReBU7sFD0ZKL+eft20L:o77HUUUUUUUUUUUUUUUUUUUTCDReBU7+ |
MALICIOUS
Application was dropped or rewritten from another process
- wabmetagen.exe (PID: 3564)
- 272.exe (PID: 2728)
- 272.exe (PID: 3984)
- wabmetagen.exe (PID: 2260)
Emotet process was detected
- wabmetagen.exe (PID: 3564)
Changes the autorun value in the registry
- wabmetagen.exe (PID: 2260)
Connects to CnC server
- wabmetagen.exe (PID: 2260)
EMOTET was detected
- wabmetagen.exe (PID: 2260)
Downloads executable files from the Internet
- powershell.exe (PID: 3412)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 3412)
Executable content was dropped or overwritten
- powershell.exe (PID: 3412)
- 272.exe (PID: 3984)
Starts itself from another location
- 272.exe (PID: 3984)
Application launched itself
- 272.exe (PID: 2728)
- WINWORD.EXE (PID: 3332)
- wabmetagen.exe (PID: 3564)
Starts Microsoft Office Application
- chrome.exe (PID: 3684)
- WINWORD.EXE (PID: 3332)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3332)
- WINWORD.EXE (PID: 3716)
- WINWORD.EXE (PID: 2964)
Creates files in the user directory
- WINWORD.EXE (PID: 3332)
- iexplore.exe (PID: 1488)
- iexplore.exe (PID: 3404)
Reads Internet Cache Settings
- iexplore.exe (PID: 1488)
- chrome.exe (PID: 3684)
Changes internet zones settings
- iexplore.exe (PID: 3404)
Application launched itself
- iexplore.exe (PID: 3404)
- chrome.exe (PID: 3684)
Reads internet explorer settings
- iexplore.exe (PID: 1488)
Reads settings of System Certificates
- chrome.exe (PID: 3684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | - |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:03:14 14:23:00 |
| ModifyDate: | 2019:03:14 14:23:00 |
| Pages: | 1 |
| Words: | 2 |
| Characters: | 13 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 14 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
56
Monitored processes
21
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1488 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3404 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1932 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=916,15861722945708167285,6705186899220858722,131072 --enable-features=PasswordImport --service-pipe-token=029E925BF38D01BB8511CC5EAA6E4D79 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=029E925BF38D01BB8511CC5EAA6E4D79 --renderer-client-id=3 --mojo-platform-channel-handle=2036 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2060 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=916,15861722945708167285,6705186899220858722,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=F114DEE4908F3A916D2510DA5DEE4767 --mojo-platform-channel-handle=4420 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2260 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | wabmetagen.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Executable Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2452 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=68.0.3440.106 --initial-client-data=0x78,0x7c,0x80,0x74,0x84,0x6dbf00b0,0x6dbf00c0,0x6dbf00cc | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2580 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=916,15861722945708167285,6705186899220858722,131072 --enable-features=PasswordImport --service-pipe-token=A95F076E50B588126E142A7CBAF4F0B6 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=A95F076E50B588126E142A7CBAF4F0B6 --renderer-client-id=5 --mojo-platform-channel-handle=1904 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2584 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=916,15861722945708167285,6705186899220858722,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=87724A4684B6062780D52DBFAEFB6C89 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=87724A4684B6062780D52DBFAEFB6C89 --renderer-client-id=8 --mojo-platform-channel-handle=3952 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2708 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=916,15861722945708167285,6705186899220858722,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=6FE2C11E5C9D36B0E72A860EAD454E2D --mojo-platform-channel-handle=3980 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2728 | "C:\Users\admin\272.exe" | C:\Users\admin\272.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Executable Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2964 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
2 977
Read events
2 444
Write events
517
Delete events
16
Modification events
| (PID) Process: | (3332) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | ..& |
Value: 2E2E2600040D0000010000000000000000000000 | |||
| (PID) Process: | (3332) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3332) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3332) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1315831838 | |||
| (PID) Process: | (3332) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1315831952 | |||
| (PID) Process: | (3332) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1315831953 | |||
| (PID) Process: | (3332) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 040D0000BA7A76238ADAD40100000000 | |||
| (PID) Process: | (3332) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | %/& |
Value: 252F2600040D000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3332) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | %/& |
Value: 252F2600040D000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3332) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
2
Suspicious files
50
Text files
60
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3332 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR862E.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3412 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\8IB79KD1ILXNRXV3ZG0D.temp | — | |
MD5:— | SHA256:— | |||
| 3404 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3404 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3684 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\8a58682a-6a8a-4e64-b5c4-b263c2fe4057.tmp | — | |
MD5:— | SHA256:— | |||
| 3684 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3684 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3332 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3332 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$s4-l1c5x-ypgzxqk.doc | pgc | |
MD5:— | SHA256:— | |||
| 3684 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
23
DNS requests
16
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3412 | powershell.exe | GET | 200 | 178.128.41.189:80 | http://turningspeech.com/rm44r5z/usg/ | GR | executable | 182 Kb | suspicious |
2260 | wabmetagen.exe | GET | 200 | 187.233.152.78:443 | http://187.233.152.78:443/ | MX | binary | 132 b | malicious |
3404 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3404 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3412 | powershell.exe | 178.128.41.189:80 | turningspeech.com | Forthnet | GR | suspicious |
2260 | wabmetagen.exe | 187.233.152.78:443 | — | Uninet S.A. de C.V. | MX | malicious |
1488 | iexplore.exe | 112.213.89.123:443 | utit.vn | SUPERDATA | VN | suspicious |
3684 | chrome.exe | 172.217.16.163:443 | www.google.de | Google Inc. | US | whitelisted |
3684 | chrome.exe | 172.217.22.35:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3684 | chrome.exe | 172.217.23.131:443 | www.google.no | Google Inc. | US | whitelisted |
3684 | chrome.exe | 112.213.89.123:443 | utit.vn | SUPERDATA | VN | suspicious |
3684 | chrome.exe | 216.58.206.10:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3684 | chrome.exe | 216.58.208.35:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
turningspeech.com |
| suspicious |
www.bing.com |
| whitelisted |
utit.vn |
| suspicious |
www.gstatic.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.google.de |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3412 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3412 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3412 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2260 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
1 ETPRO signatures available at the full report