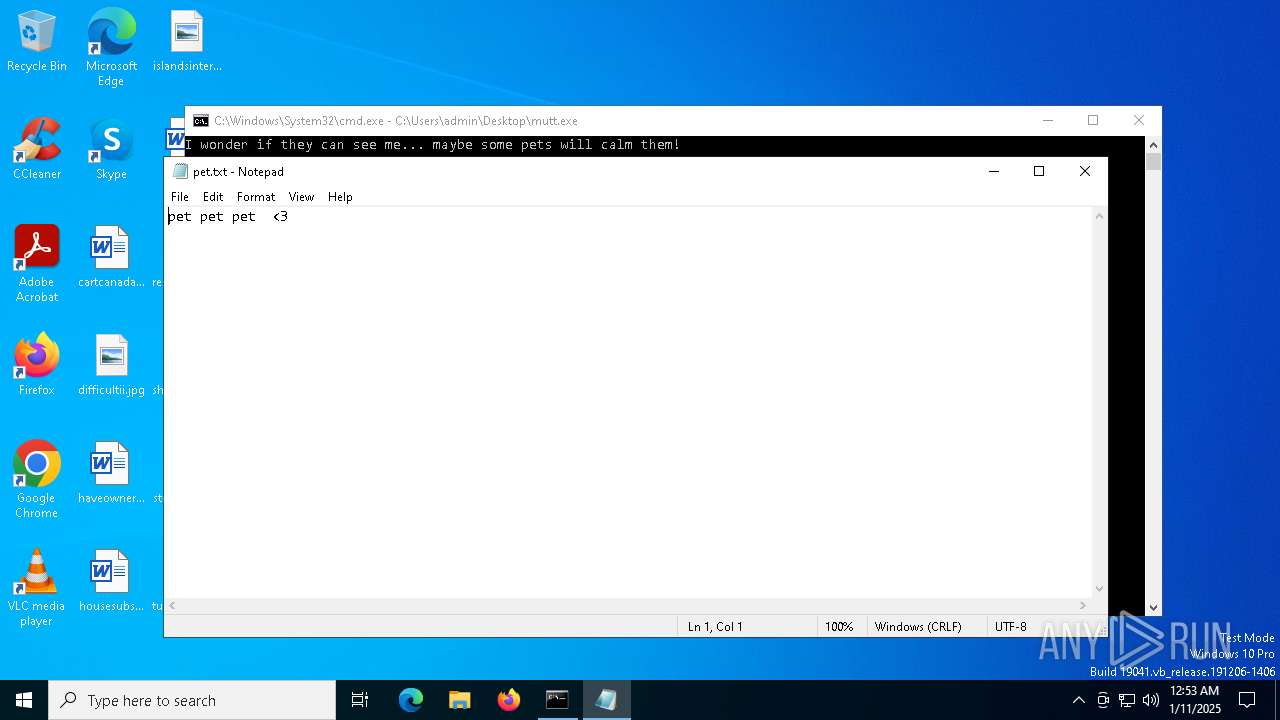
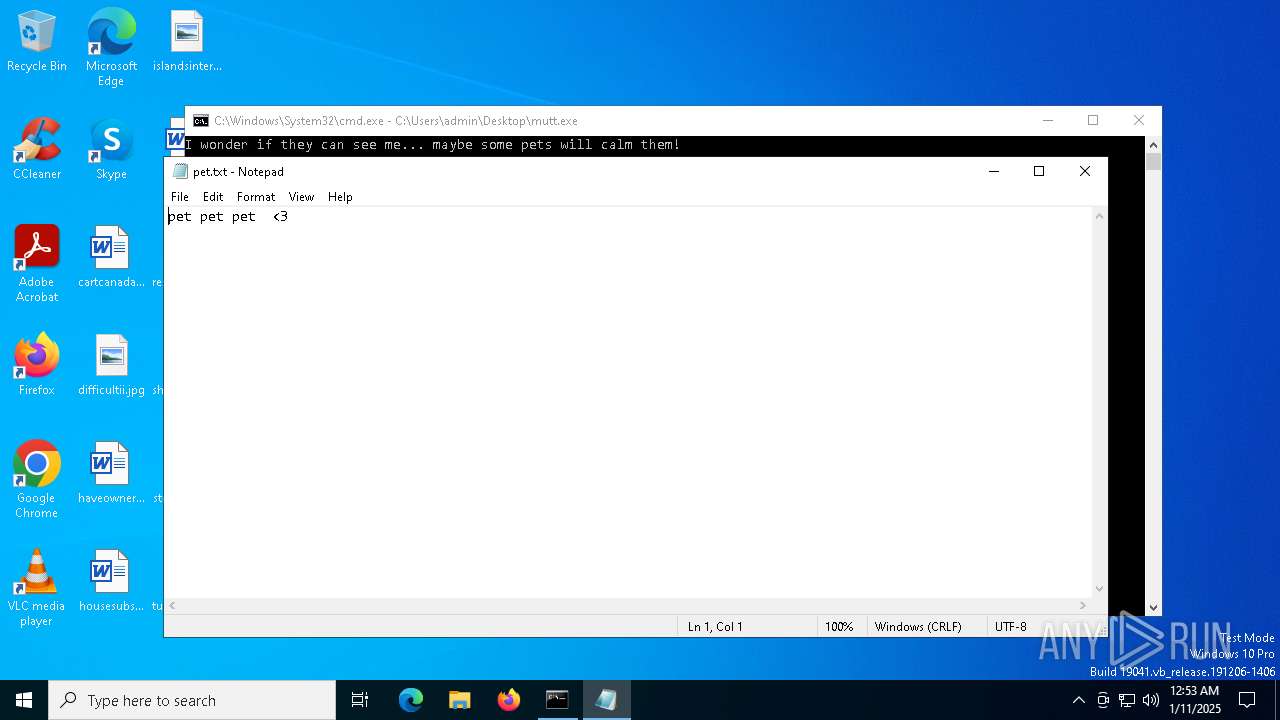
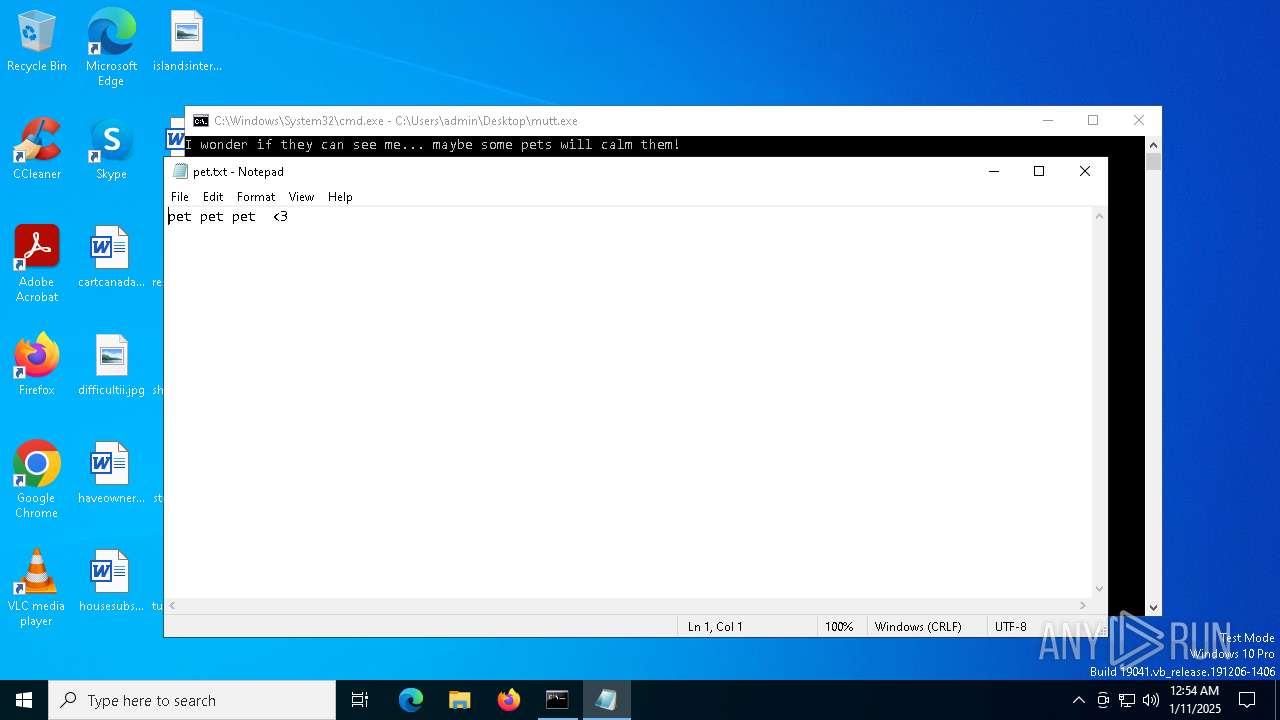
| File name: | mutt.exe |
| Full analysis: | https://app.any.run/tasks/f4b0a3ee-f052-45f7-b2f3-5ca2993a4549 |
| Verdict: | Malicious activity |
| Analysis date: | January 11, 2025, 00:53:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 5 sections |
| MD5: | A87C5D3B94FA60FDD87BF7C26B2E41DD |
| SHA1: | 07C3D50AC1FC48109A3758AA5DB88FC4E32E35D1 |
| SHA256: | 3EA69FC85F1FDD759CF103375DBE2B754ECB8B1088068C8CFAD384FE0D739969 |
| SSDEEP: | 3072:zCYa+0Nu6vQAkQ5S7JmyxCbBKhiTbMtxzEGG:AQLi8NiTbKXG |
MALICIOUS
Create files in the Startup directory
- cmd.exe (PID: 5828)
SUSPICIOUS
Executing commands from a ".bat" file
- mutt.exe (PID: 2096)
Starts CMD.EXE for commands execution
- mutt.exe (PID: 2096)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5828)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 5828)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 5312)
The system shut down or reboot
- cmd.exe (PID: 5828)
Reads security settings of Internet Explorer
- StartMenuExperienceHost.exe (PID: 5416)
- GameBar.exe (PID: 5500)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 5416)
INFO
Checks supported languages
- mutt.exe (PID: 2096)
- PLUGScheduler.exe (PID: 5312)
- GameBar.exe (PID: 5500)
- StartMenuExperienceHost.exe (PID: 5416)
- SearchApp.exe (PID: 4776)
Reads Microsoft Office registry keys
- cmd.exe (PID: 5828)
Create files in a temporary directory
- mutt.exe (PID: 2096)
Reads security settings of Internet Explorer
- cmd.exe (PID: 5828)
- notepad.exe (PID: 5308)
- notepad.exe (PID: 6728)
- notepad.exe (PID: 5316)
- dllhost.exe (PID: 6156)
The process uses the downloaded file
- cmd.exe (PID: 5828)
Creates files or folders in the user directory
- cmd.exe (PID: 5828)
- dllhost.exe (PID: 6156)
Creates files in the program directory
- PLUGScheduler.exe (PID: 5312)
Reads the computer name
- PLUGScheduler.exe (PID: 5312)
- GameBar.exe (PID: 5500)
- StartMenuExperienceHost.exe (PID: 5416)
- SearchApp.exe (PID: 4776)
Checks proxy server information
- SearchApp.exe (PID: 4776)
Sends debugging messages
- StartMenuExperienceHost.exe (PID: 5416)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 4776)
Process checks computer location settings
- StartMenuExperienceHost.exe (PID: 5416)
- SearchApp.exe (PID: 4776)
Reads the software policy settings
- SearchApp.exe (PID: 4776)
Reads Environment values
- SearchApp.exe (PID: 4776)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:07:30 08:52:45+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 70656 |
| InitializedDataSize: | 27648 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
Total processes
193
Monitored processes
44
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Windows\System32\cmd.exe" /k C:\Users\admin\Desktop\mutt.exe | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 372 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 436 | timeout /t 1 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 712 | timeout /t 3 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1712 | C:\WINDOWS\System32\mobsync.exe -Embedding | C:\Windows\System32\mobsync.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Sync Center Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2060 | timeout /t 1 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | C:\Users\admin\Desktop\mutt.exe | C:\Users\admin\Desktop\mutt.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1073807364 Modules
| |||||||||||||||
| 4428 | taskkill /F /IM notepad.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4776 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4840 | timeout /t 2 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 098
Read events
14 999
Write events
98
Delete events
1
Modification events
| (PID) Process: | (5828) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.txt\OpenWithProgids |
| Operation: | write | Name: | txtfile |
Value: | |||
| (PID) Process: | (5416) StartMenuExperienceHost.exe | Key: | \REGISTRY\A\{e3ab485b-1261-c4bd-c39d-1d773b2feb39}\LocalState\DataCorruptionRecovery |
| Operation: | write | Name: | InitializationAttemptCount |
Value: 01000000F4E31A5BC363DB01 | |||
| (PID) Process: | (5500) GameBar.exe | Key: | \REGISTRY\A\{5bf95e59-093c-8a0a-eec9-1cacd4033d8e}\LocalState |
| Operation: | write | Name: | InstalledVersionMajor |
Value: 0200E8471D5BC363DB01 | |||
| (PID) Process: | (5500) GameBar.exe | Key: | \REGISTRY\A\{5bf95e59-093c-8a0a-eec9-1cacd4033d8e}\LocalState |
| Operation: | write | Name: | InstalledVersionMinor |
Value: 2200E8471D5BC363DB01 | |||
| (PID) Process: | (5500) GameBar.exe | Key: | \REGISTRY\A\{5bf95e59-093c-8a0a-eec9-1cacd4033d8e}\LocalState |
| Operation: | write | Name: | InstalledVersionBuild |
Value: 616DE8471D5BC363DB01 | |||
| (PID) Process: | (5500) GameBar.exe | Key: | \REGISTRY\A\{5bf95e59-093c-8a0a-eec9-1cacd4033d8e}\LocalState |
| Operation: | write | Name: | InstalledVersionRevision |
Value: 0000E8471D5BC363DB01 | |||
| (PID) Process: | (5500) GameBar.exe | Key: | \REGISTRY\A\{5bf95e59-093c-8a0a-eec9-1cacd4033d8e}\LocalState |
| Operation: | write | Name: | PreviousAppTerminationFromSuspended |
Value: 00E8471D5BC363DB01 | |||
| (PID) Process: | (5500) GameBar.exe | Key: | \REGISTRY\A\{5bf95e59-093c-8a0a-eec9-1cacd4033d8e}\LocalState |
| Operation: | write | Name: | CurrentDisplayMonitor |
Value: 670061006D00650000007DAB1F5BC363DB01 | |||
| (PID) Process: | (5416) StartMenuExperienceHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\TileDataModel\Migration\StartNonLayoutProperties |
| Operation: | write | Name: | Completed |
Value: 1 | |||
| (PID) Process: | (5416) StartMenuExperienceHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\TileDataModel\Migration\StartNonLayoutProperties_AppUsageData |
| Operation: | write | Name: | Completed |
Value: 1 | |||
Executable files
0
Suspicious files
90
Text files
23
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2096 | mutt.exe | C:\Users\admin\Desktop\part3.bat | text | |
MD5:1518A37B30FEC499B2DEDBA76C2FA099 | SHA256:4F77714FA361C4B21B4241F440C3658E39E55DDCA6138EB09FF0B834C0B074D2 | |||
| 5828 | cmd.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\part3.bat | text | |
MD5:1518A37B30FEC499B2DEDBA76C2FA099 | SHA256:4F77714FA361C4B21B4241F440C3658E39E55DDCA6138EB09FF0B834C0B074D2 | |||
| 5312 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.038.etl | binary | |
MD5:5EA68411BF8E9EAF4621BAF73F61449E | SHA256:9D4CA5A1D871F819C139A498BB910A63576C2FE6367853544F8D172D8B6EBFF7 | |||
| 5312 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.036.etl | binary | |
MD5:FED961067F664B5381B65A534B7AB728 | SHA256:652F31A8284AE812D1D9D24192BC800976BF74C240591C6AC443A28C4709FB7C | |||
| 5312 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.037.etl | binary | |
MD5:A23907B6FDD47DCABFDFD7CF2FCD7671 | SHA256:0C9C33FE9E984A2E5A70EBA51F36B9929A86199E424AF2F8080E1267B87DC970 | |||
| 5312 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.035.etl | binary | |
MD5:A7A21FBC9D00F33F186B34A50E170C13 | SHA256:64CAC91E46D4FC832958232A658431CBF9D8D9F265653ACA2BEB32428D4688EC | |||
| 5312 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.043.etl | binary | |
MD5:2F36C598EBFF5B5CDD898C9691D6BCCB | SHA256:8900C5931ED8E0D1B68082B45CF2F4E8C1025D36825508E0804C916D781B9F50 | |||
| 5312 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.047.etl | binary | |
MD5:FA358BFEE9B4E1FFB7394D13CBBC4898 | SHA256:6FF97BBF8A56286A4C71623829514CC14B7F8CBBCF09748D939F733968478A22 | |||
| 5312 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.034.etl | binary | |
MD5:89BD161BF7B46C9078937CF832786737 | SHA256:2B83DF5532E9F54ED301C8F82E2CDD489799C8D5222A2D44C97DCB151A96FAA9 | |||
| 5312 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.032.etl | binary | |
MD5:8A2BDE0EAFA7E946196A1B114AB636E9 | SHA256:1C338CBDD9316D7FD8F208341466FEDC554A04D489B3A86C736EC3831A2F2BA2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
35
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6248 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2796 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2796 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5208 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |